Security teams strive to be on the offensive by identifying emerging threats before they surface and have a chance to do damage. Such threat detection strategies are used across the board in multiple industries, including finance, government and healthcare.
Unfortunately, using a standard approach to threat intelligence and threat hunting often puts them on the defensive, as they’re forced to sift through outdated intelligence that eats into their response time.
Given that only 2% of global threat infrastructure is being tracked in cybersecurity at any given time, organizations simply don’t have the ability to obtain a complete view of any given threat landscape, and are forced to reactively mitigate attacks that originate from the hidden 98%.
In this blog, we’ll explain how to plan an offensive strategy with a complete view of attacker infrastructure to protect your organization, and describe how Silent Push facilitates fast, accurate proactive threat detection using Indicators of Future Attack (IOFA)™.
What is the Difference Between Proactive vs. Reactive Threat Detection?
Proactive threat detection locates and stops carefully orchestrated cyber attacks before they cause damage.
In boxing, there’s an old saying – “hit and don’t get hit”. A fighter who has the ability to be on the offensive minimizes the amount of hits their opponent can make, causing them to become preoccupied with defending themselves rather than attacking.
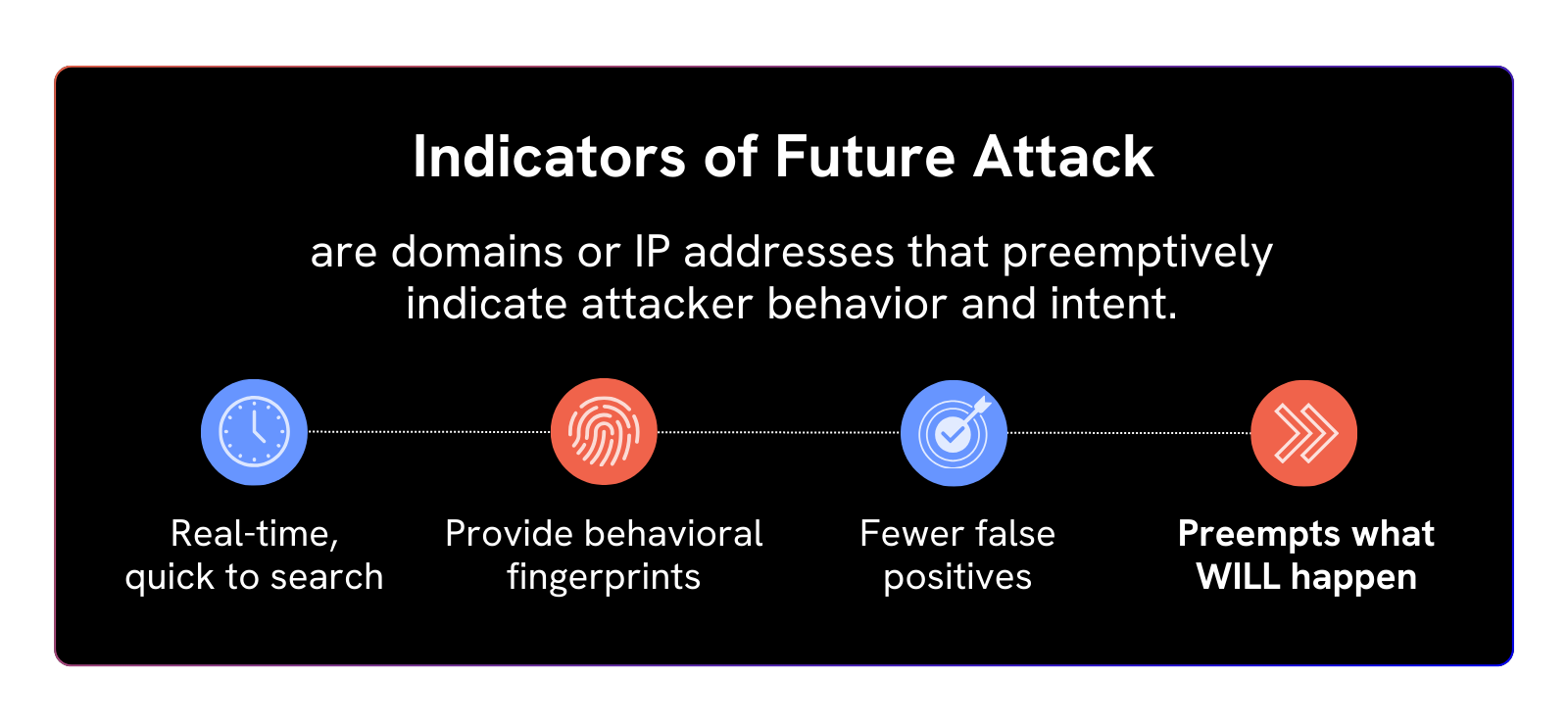
A proactive security team doesn’t sit back and wait for the punches to come to them. They understand their attack surface, they know how they’re going to be targeted – and by who – and they take the fight to the threat actor by shutting down digital assaults before they’re launched with industry-leading Indicators of Future Attack (IOFA)™.
Reactive security teams fight behind their gloves, and hope for the best by dealing with incidents at the perimeter, rather than going out on the attack and proactively locating threat infrastructure. Sooner or later, one of those punches will get through, and that’s when the knockout blow comes in the form of a breach.
They rely on stale lists of post-breach IOCs that only serve to inform defenders about where an attack has come from, rather than where it’s going to be.
Reactive teams formulate a defense as a REACTION to an attack that has occurred elsewhere. They aren’t able to ascertain where an adversary is going to strike before they attack, and in the dark about the infrastructure being set up.
If your teams aren’t proactively tracking and monitoring both emerging and active threat infrastructure, the knockout blow is just around the corner, your potential exposure to an attack increases, and with it the chances of a costly breach.
Proactively Identify Threat Actor Tactics
Preemptive threat intelligence allows you to proactively identify threat infrastructure as it’s being set up, and before an adversary launches an attack.
It’s the only reliable way to outsmart adversaries and take control back.
Security teams need to do away with a reactive, IOC-led approach to threat intelligence and focus on the underlying tactics and strategies used by threat actors that tracks the deployment of infrastructure, rather than simply dealing with the individual domains and IPs used in a previous attack.
How Does Silent Push Help You Develop an Offensive Approach to Protect Your Organization?
Silent Push is the first and only threat intelligence solution to deliver IOFA™ and create a unique digital fingerprint of adversary behavior that allow teams to adopt a fully proactive stance by eliminating incoming attacks before they’re launched.
Our feeds and intelligence streams aren’t made up of retrospective, reactive indicators of previous threat activity. IOFA™ provide your teams with a glimpse into the future, so that you can anticipate and react to emerging threats way before they reach your organization.
We are the only solution to understand the full attack landscape, and provide this to SOC and IR teams in a way that’s immediately actionable, and doesn’t take up precious time and resources to further investigate and validate before it’s useable.
Click here to get access to an exclusive report that outlines 4 key cyber threat trends to keep ahead of in 2025, and learn about:
- How and where threat actors use these tactics
- Named adversaries and intent
- How to combat threats with Indicators of Future Attack (IOFA)™
Learn more about our unique approach to Preemptive Threat Intelligence
Find out how your organization can use Preemptive Threat Intelligence to outsmart adversaries and stop attacks before they’re launched.
Contact us here for more information.




