In this blog, we’ll show you how to use Silent Push Community Edition‘s WHOIS scanning feature to locate and traverse threat infrastructure, using a WHOIS fingerprint that enables fast and accurate tracking of attacker Tactics, Techniques and Procedures (TTPs).
We’ll start by explaining the concept of WHOIS data and how security teams can utilize WHOIS intelligence to defend against attacks, before showing you how to pivot across data with a simple WHOIS scan that uses a domain owner’s email address as the starting point.
Sign-up to Silent Push Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense tool, featuring a range of advanced queries and lookups, that outputs known and hidden threat infrastructure.
What is WHOIS data?
WHOIS is a publicly accessible database containing information on the ownership, registration, and administrative details of a domain.
When someone registers a domain (the “registrant”), they need to provide contact details and other relevant information to the company that facilitates the registration (the “registrar”).
This data is then made available through various WHOIS lookup tools, which allow any interested parties – including security teams – to query a domain name, and retrieve details about the registration.
The global WHOIS system performs three key functions:
- Accountability: Ensures that domain owners can be contacted in case of legal, technical, or business issues.
- Cybersecurity and threat hunting: Tracking illegal activities related to domain usage, including domain spoofing, fraud, or copyright infringement.
- Technical support: Diagnosing domain-related issues, and DNS problems.
WHOIS data privacy
“WHOIS privacy” is a service offered by registrars that masks a domain owners’ personal information in the public WHOIS database, by using a proxy service to hide the real owner’s details and display generic responses in its place.
The legitimate purpose of WHOIS privacy is to counteract spam, identity theft, and harassment, but threat actors use the facility to evade detection and prevent security teams from tracking their activity.
How is WHOIS scanning used in cybersecurity?
Security Operations Centre (SOC) and Incident Response (IR) teams use WHOIS data to identify and analyze malicious domains, and gather intelligence that can be used to perform additional scans that reveal even more threat infrastructure.
Lets take a look at some common use cases…
Identifying linked threat activity
WHOIS data includes information on the domain owner – such as the email they used to register the domain – and any nameservers associated with a domain.
Threat hunters use this data to locate other domains registered by the domain owner, or hosted on the same IP infrastructure using additional DNS queries.
If a domain shares the same WHOIS or DNS characteristics as a known malicious domain, this can be an indication of linked threat activity.
Correlating registration dates and patterns
Security teams use domain registration and expiration dates to detect suspicious activity, based on how long a domain has been in operation.
Recently registered domains are more likely to be used in an attack. Threat actors register new domains for short-term campaigns to counteract traditional IOC-based defense mechanisms that rely on lists of publicly known infrastructure.
Short-lived domains that are quickly registered and then allowed to expire (or disappear after use) are often used as disposable domains in a variety of threat campaigns, such as brand impersonation and typosquatting attacks.
Targeting suspicious domain registrars
Certain domain registrars are used by threat actors because they have lax verification procedures, and operate with poor security policies that ignore domain takedown requests.
Such registrars also allow the purchase of domains at low cost and in bulk, allowing threat actors to deploy large amounts of domains in a single campaign that hinders detection.
Threat hunters are able to identify these registrars, and traverse across elements of their hosting infrastructure to locate malicious infrastructure.
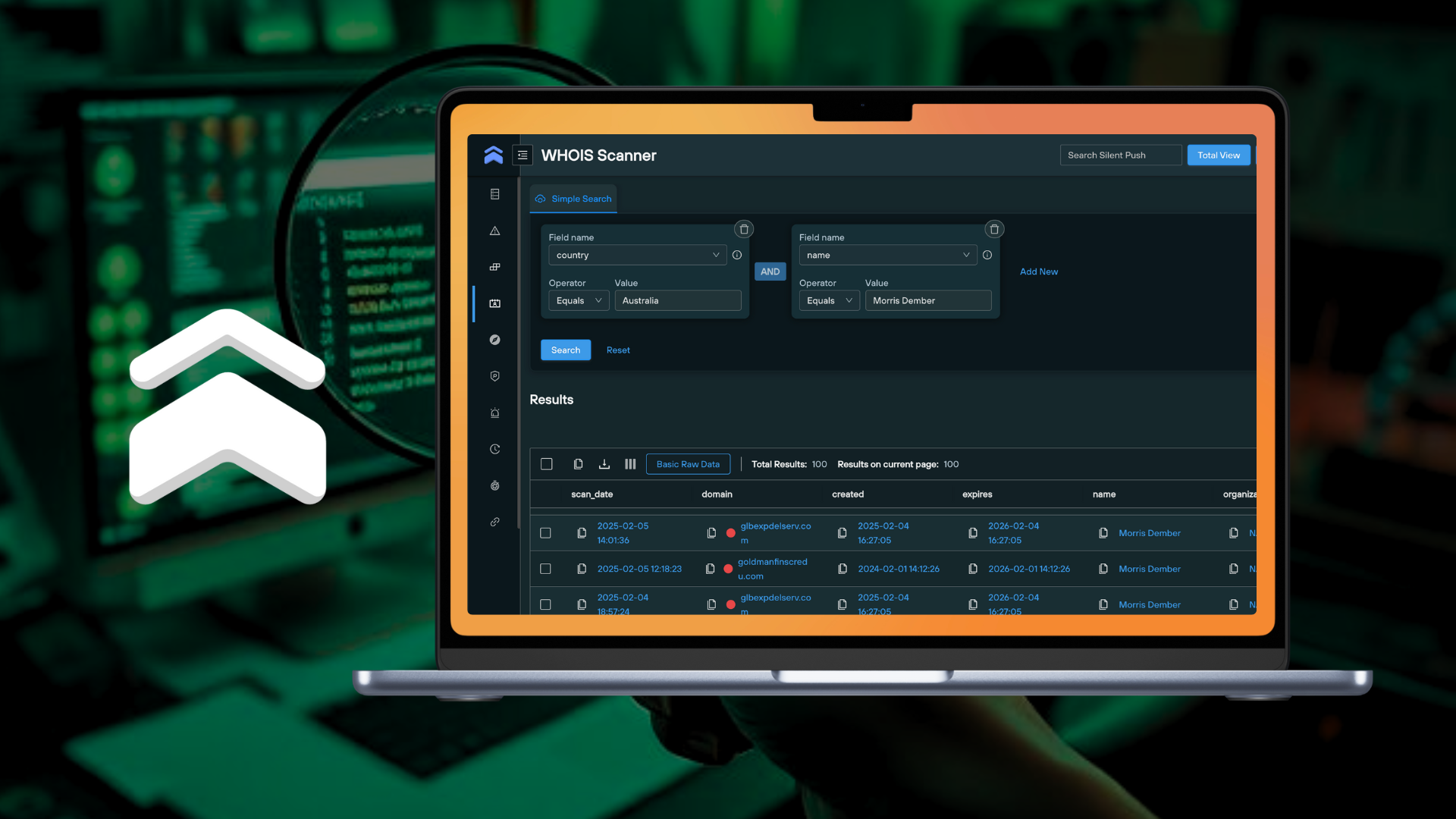
WHOIS scanning with Silent Push
WHOIS information is a useful starting point in an investigation into named or unknown threat activity, but retrieving and using WHOIS data at scale, in a way that makes it easy to perform additional DNS and content-based pivots across an enriched dataset that complements the original scan, can be difficult to achieve.
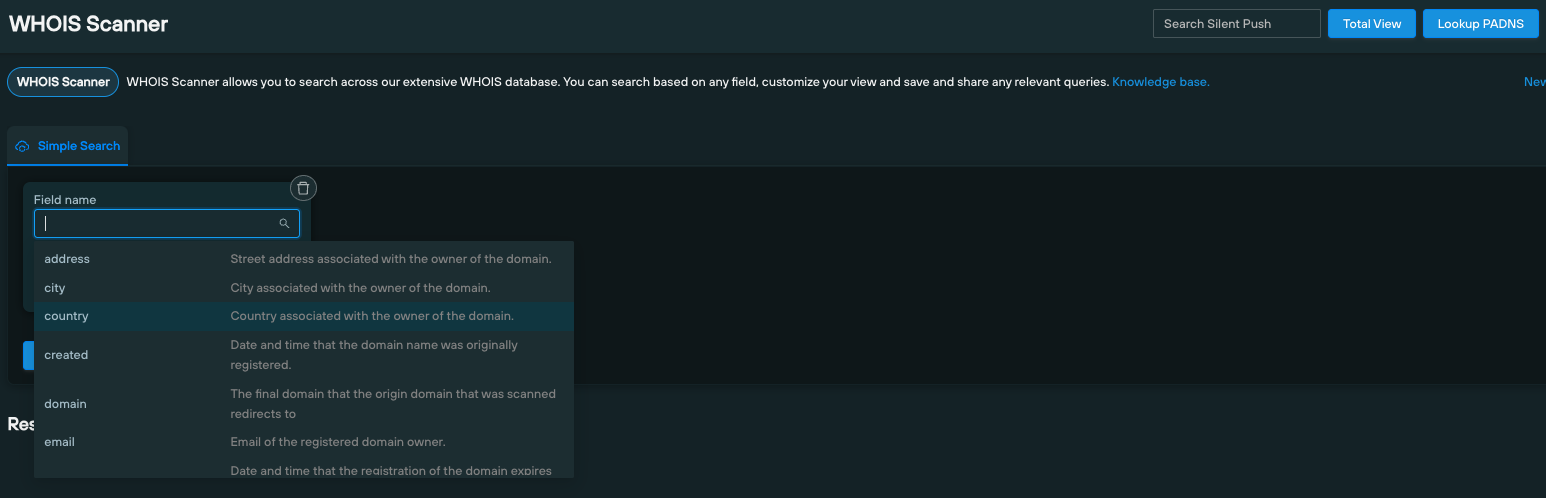
All Silent Push subscription tiers – including Community Edition – feature a built-in WHOIS Scanner, than returns WHOIS infrastructure using a combination of the following data types:
address: Address associated with the owner, including fields for each line of the address (e.g. state and zip_code)created: Date and time the domain was registered ondomain: The final domain the the original domain resolves toemail: Email of the registered domain ownerexpires: Date and time the domain is set to expire, unless it’s renewedname: Given name of the domain registrantnameserver: The nameserver used to connect the domain name to the hosts IPns_hash: Searchable hash of the nameserver and domainorganization: Name of the organization that the domain is associated withregistrar: Registrar associated with the domainscan_date: Date the domain was scanned by Silent Push
Once you’ve executed a scan, you can one-click pivot across the results set to reveal additional intelligence linked to your original scanning parameters – including all associated DNS records and IP addresses – or drill down into the results by including or excluding key pieces of data.
WHOIS scanning example: registrant email address
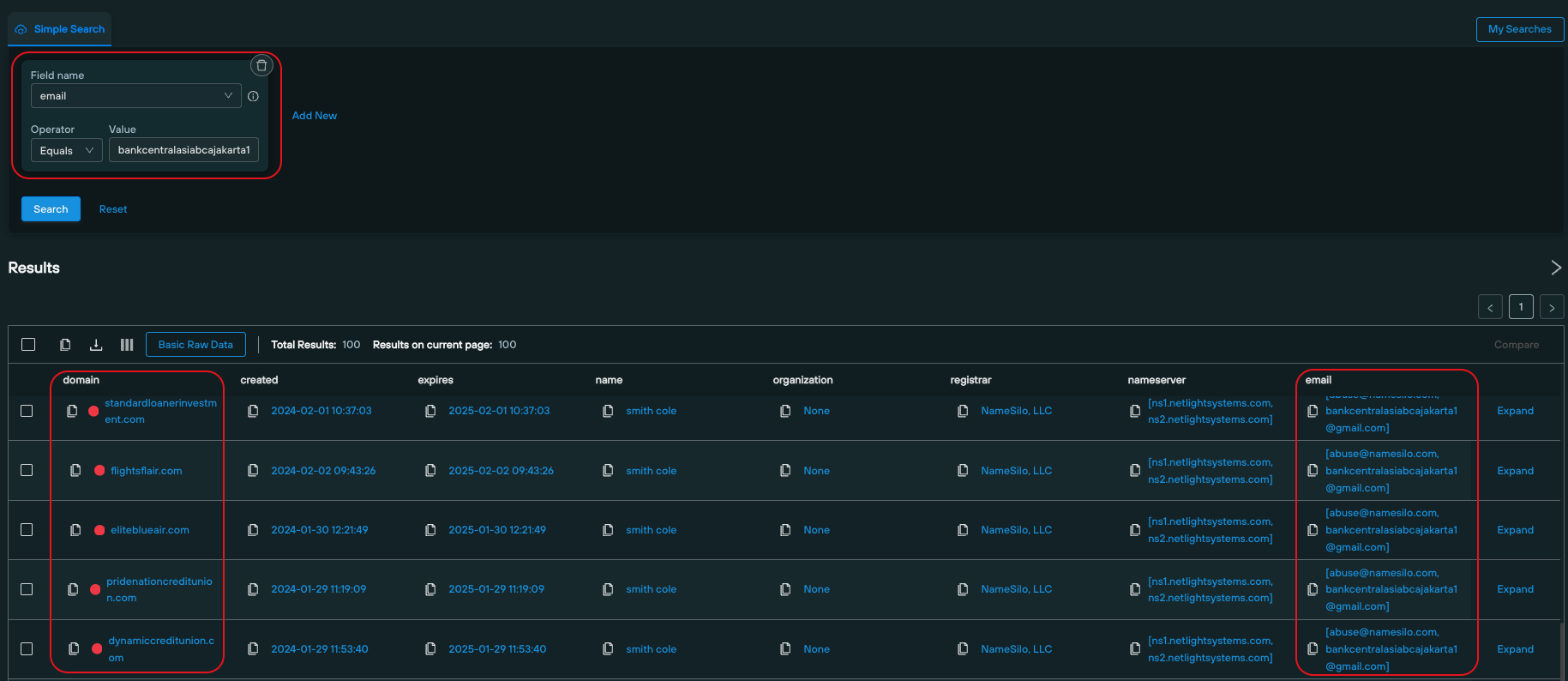
The registrant email [email protected] is associated with financial scams that attempt to spoof known and fake credit unions, and banking sites.
Executing a WHOIS Scan on the email address reveals a timestamped list of domains set up by the threat actor, mostly via a legitimate registrar (NameSilo), with Silent Push risk scores attached to each returned domain.
All of these domains are involved in financial threat activity, linked to the same registrant email address:
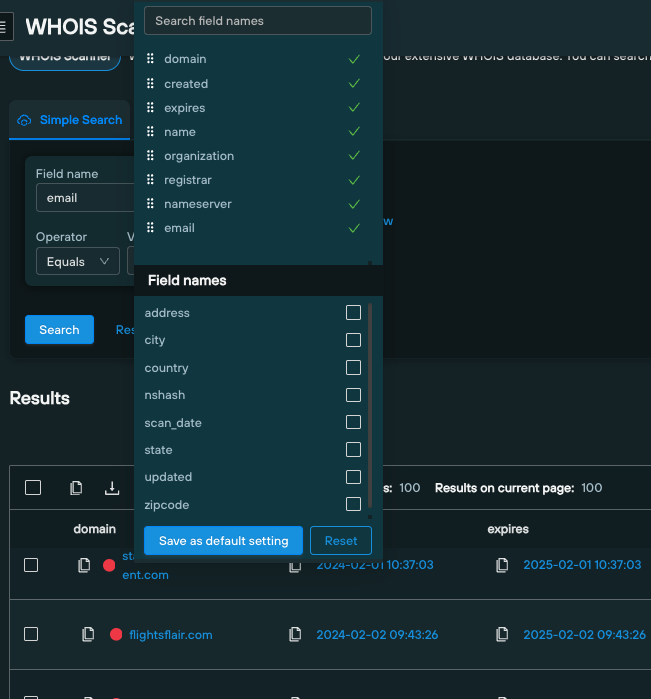
You can use the column view to display or omit data fields from the results table:
Executing a Live Scan on one such domain (phoenixvaultcreditunion.com) from within the WHOIS scanning results table reveals live infrastructure, with an expandable screenshot and additional data, including the domain’s HTML title and a favicon (if present):
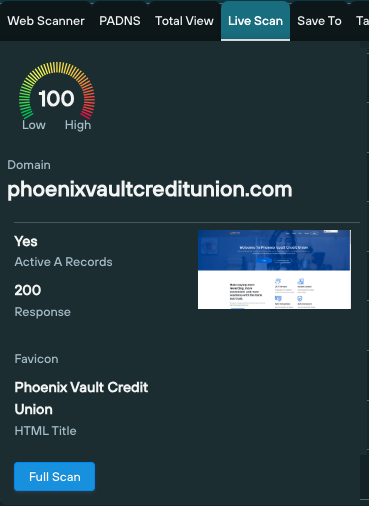
You can use the same pivot box to execute a range of additional queries and lookups that provide a wealth of additional information on the target domain, without leaving the WHOIS scanning screen:
- Web Scanner: A powerful tool that uses 150+ data fields to discover infrastructure that shares the same set of characteristics – including HTML body data, certificate information, favicons, server-returned data, and a lot more
- Passive DNS: Get an immediate and complete list of all current and historic DNS records associated with the domain
- Total View: Provides a detailed overview of all the infrastructure associated with the domain, including how it’s moved across the global IP space over time
- Save To: Add the domain to an existing or new IOFA Feed
- Takedown: Request that the domain be taken down, based on its status as an IOFA™
WHOIS scanning history
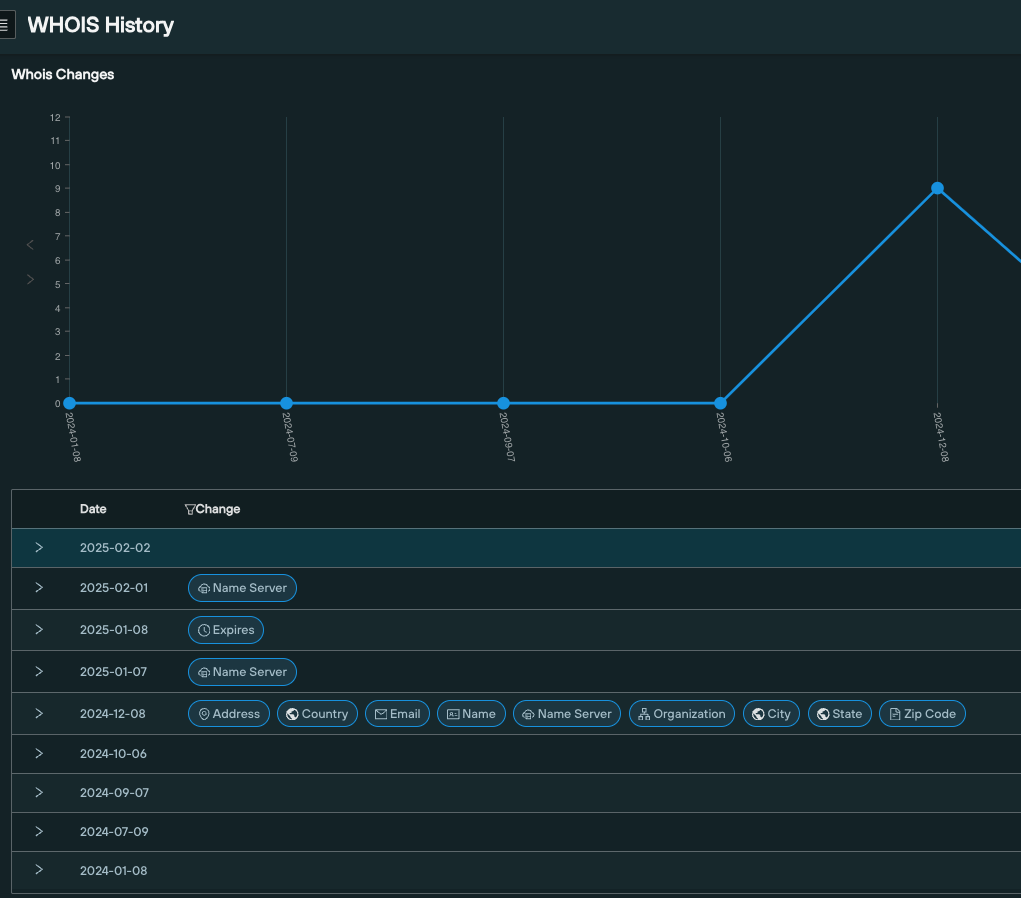
Once you’ve identified a malicious domain, you can quickly jump into the WHOIS History feature to get a timestamped table of changes to the domain’s WHOIS records.
This allows you to evaluate the Tactics, Techniques and Procedures (TTPs) used by a threat actor as they deploy their infrastructure, track similar patterns, and proactively blocks attacks.
Here’s the WHOIS history for phoenixvaultcreditunion.com, with WHOIS changes displayed as the data type, and date of the change underneath a graphical timeline:
Sign-up to Silent Push Community Edition
WHOIS Scanning is included in Silent Push Community Edition, a free threat hunting and cyber defense tool featuring a range of advanced queries and lookups, that allows users to locate known and hidden threat infrastructure.