Silent Push uncovers “refund” phishing scams targeting former customers of several bankrupt crypto platforms (Voyager, Celsius).
Key points
- Silent Push Analysts use proprietary scanning to uncover consumer phishing domains linked to bankrupt crypto platforms.
- Threat actors actively targeting former customers of Voyager and Celsius Network with asset recovery emails offering a full refund.
- Malicious redirects used to steal assets and harvest credentials from local crypto wallets by spoofing legitimate domains.
Background
Threat actors often follow trending news topics to construct bespoke campaigns that impersonate specific organizations, and their current or former customers, with outcomes that range from monetary fraud to wholesale credential and identity theft.
Earlier this year, we published a blog that detailed how threat actors took advantage of the collapse of Silicon Valley Bank by deploying a series of domains that used a refund lure to propagate credential theft.
Our Threat Analysts have tracked a campaign that attempts to trick former customers of two bankrupt crypto firms – asset brokerage Voyager, and the Celsius lender network – into giving attackers access to their crypto wallet and stored credentials.
Voyager shut down on August 15, and the Federal Trade Commission (FTC) has banned Celsius from handling customer assets, along with charging three former executives with lying about its affairs.
Threat actors are targeting former customers of both companies with phishing emails and malicious content that attempts to fool former customers of the ill-fated companies into connecting their crypto wallets with scam domains, in an effort to “recover” lost assets.
Voyager Phishing Campaign
Our research begun with a phishing email from “Stretto & Kirkland” – a fictitious amalgam of two names involved in the bankruptcy proceedings, namely Kirkland & Ellis LLP, Counsel to Voyager Digital Holdings, and Stretto, the debtors’ noticing agent – that claims to provide the recipient with a means to transfer funds from their defunct Voyager account to a “designated crypto wallet”.
Attackers often legitimise phishing campaigns by offering real-world financial institutions and well-known interested parties as bait. Both Kirkland Ellis and Stretto are mentioned in Voyager proceedings held at the United States Bankruptcy Court, in the Southern District of New York:
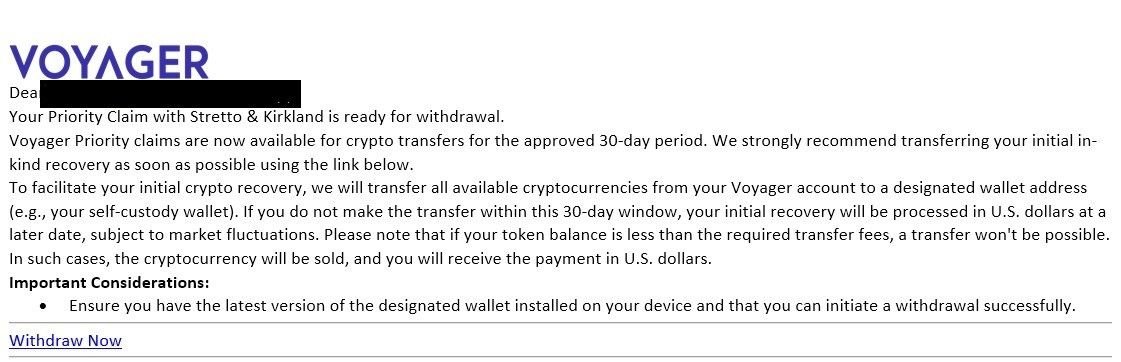
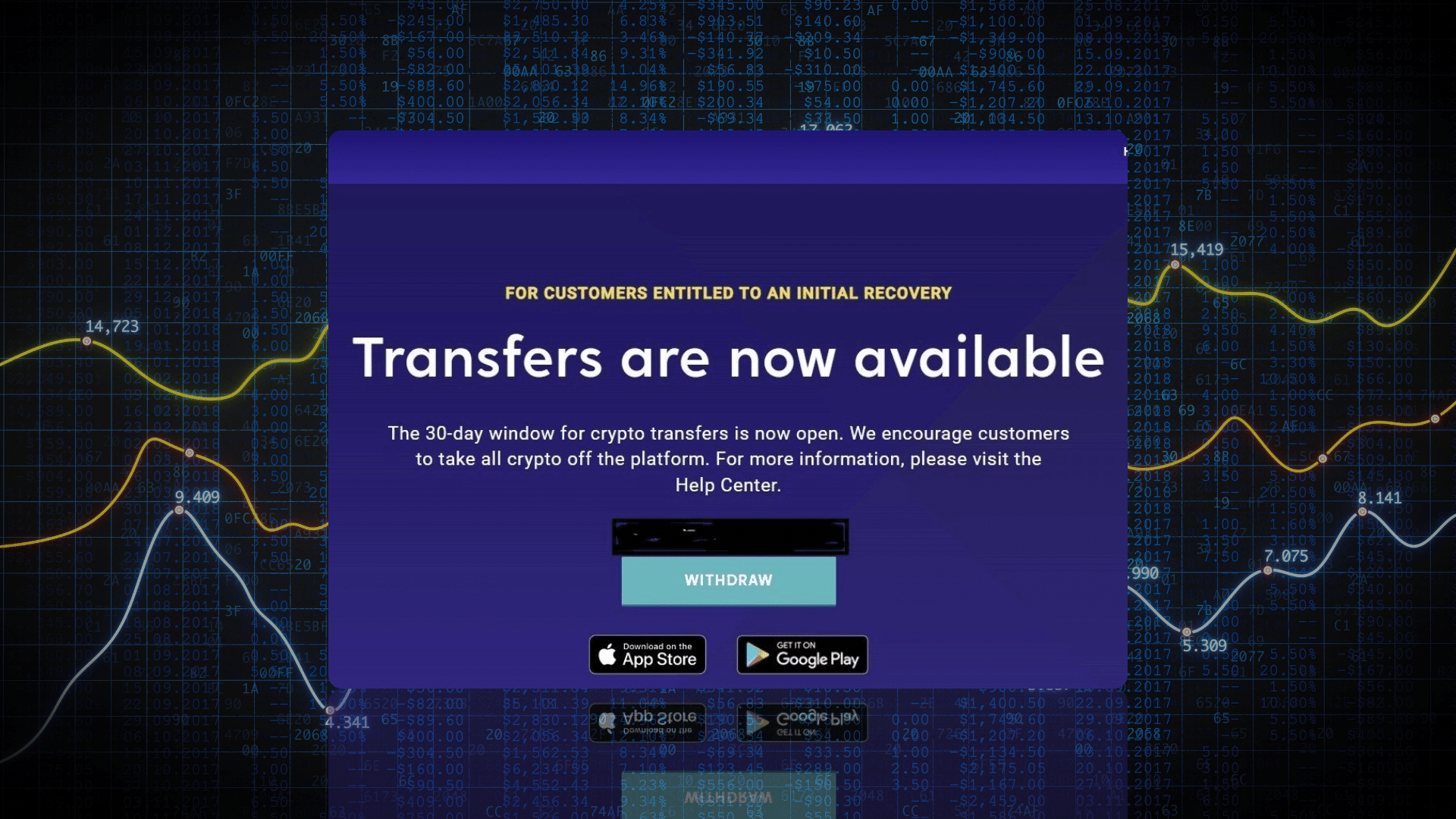
Fig. 1 – Phishing Email observed with a ‘Withdraw Now’ link at bottom
The email urges the recipient to complete the transfer within a 30-day window, in order to avoid the need for the transaction to be carried out in USD, and provides a link to a URL in order to complete the transfer.
If clicked, the link redirects users from bigbrandaid.bigphew[.]com to investivoyager[.]com, which impersonates the legitimate domain investvoyager[.]com.
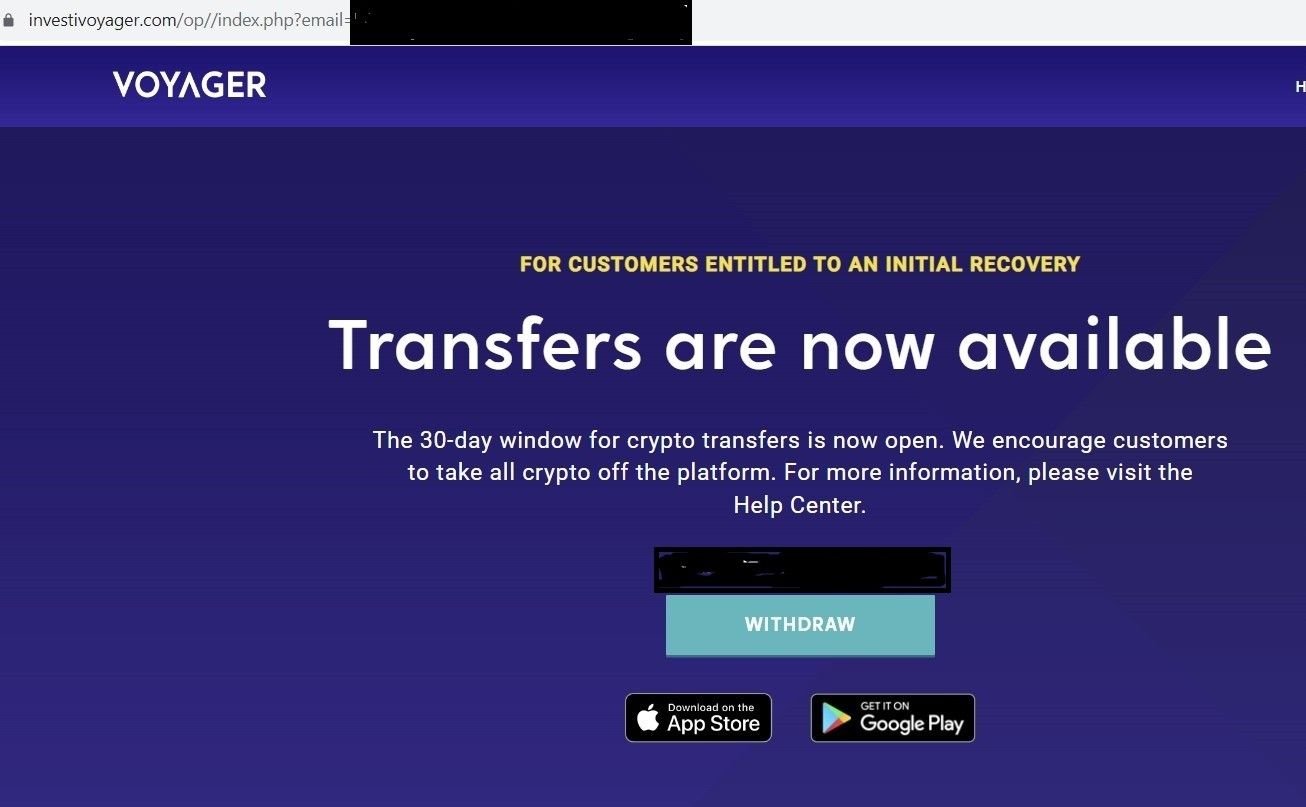
Fig. 2 – Fake Voyager domain with ‘WITHDRAW’ button
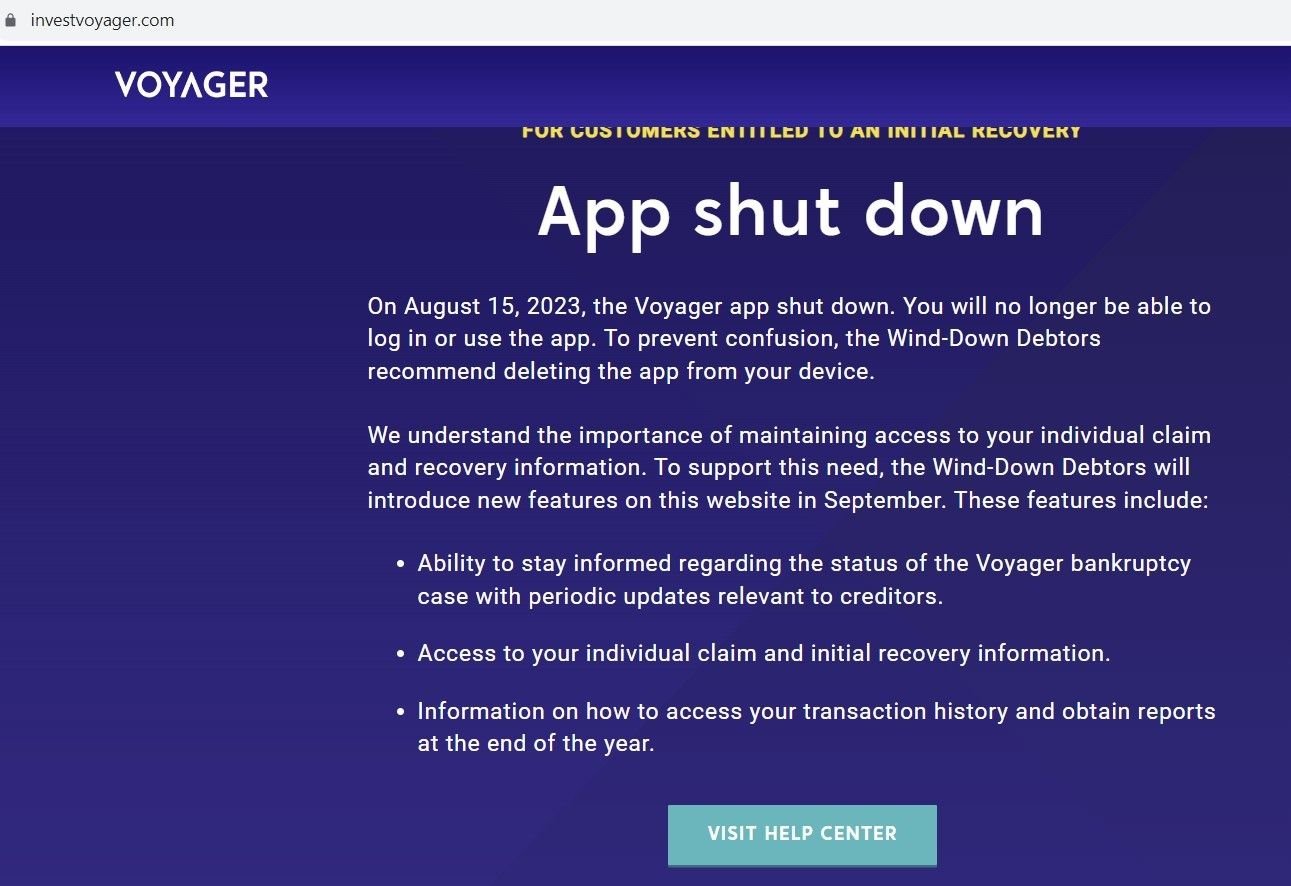
Fig. 3 – Legitimate Voyager domain with shutdown message
Once a user clicks on the “WITHDRAW” link on the phishing domain, the website attempts to establish a connection with a local crypto wallet, such as MetaMask, in an attempt to steal assets and/or credentials:
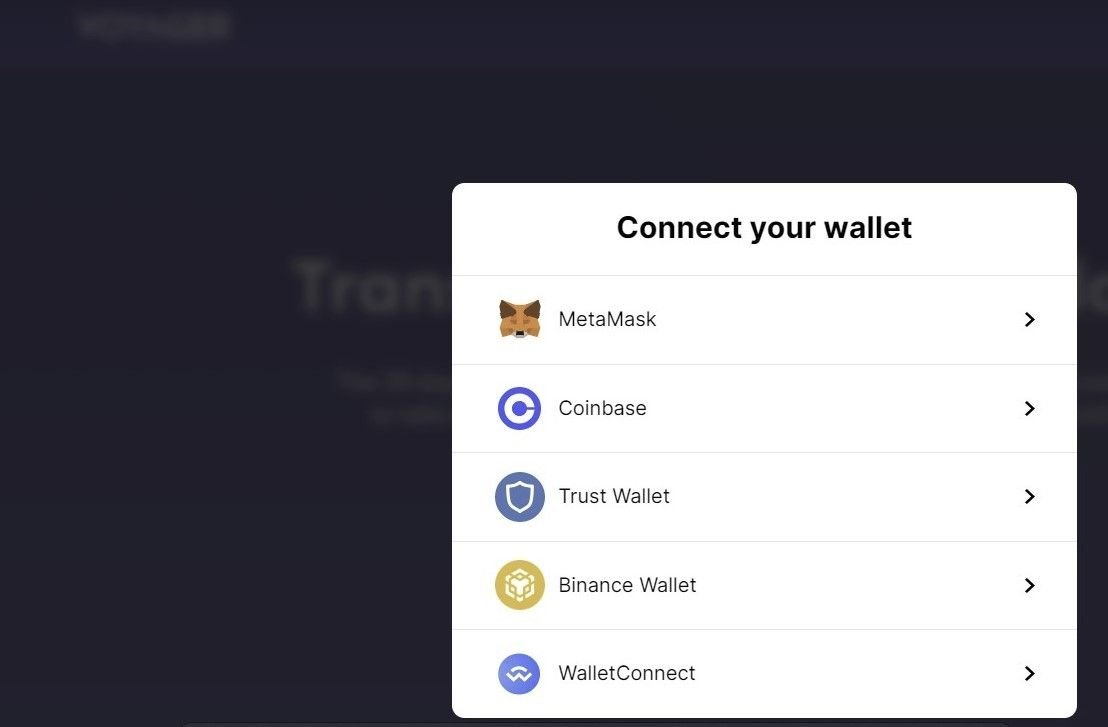
Fig. 4 – Malicious domain connecting a crypto wallet
Exploring Linked Infrastructure
The initial redirect domain – bigbrandaid.bigphew[.]com – uses an open directory with a ‘voy’ section that leads to the phishing domain:
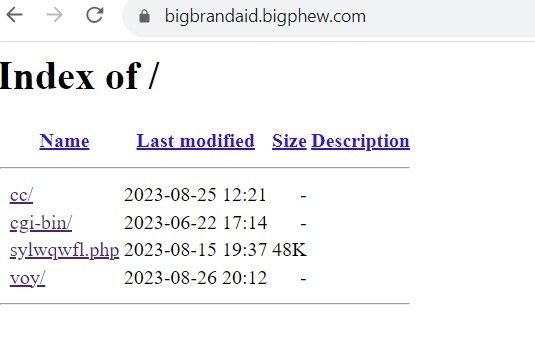
Fig 4. – Open directory on redirect domain
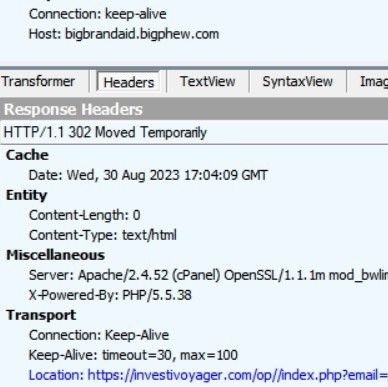
Fig. 5 – Redirection to phishing site
Celsius Network Phishing Campaign
Using the Silent Push platform, we were able to pinpoint other infrastructure linked to the phishing domain investivoyager[.]com, including other crypto phishing domains presumably being operated by the same threat group, including domains targeting the aforementioned Celsius Network:
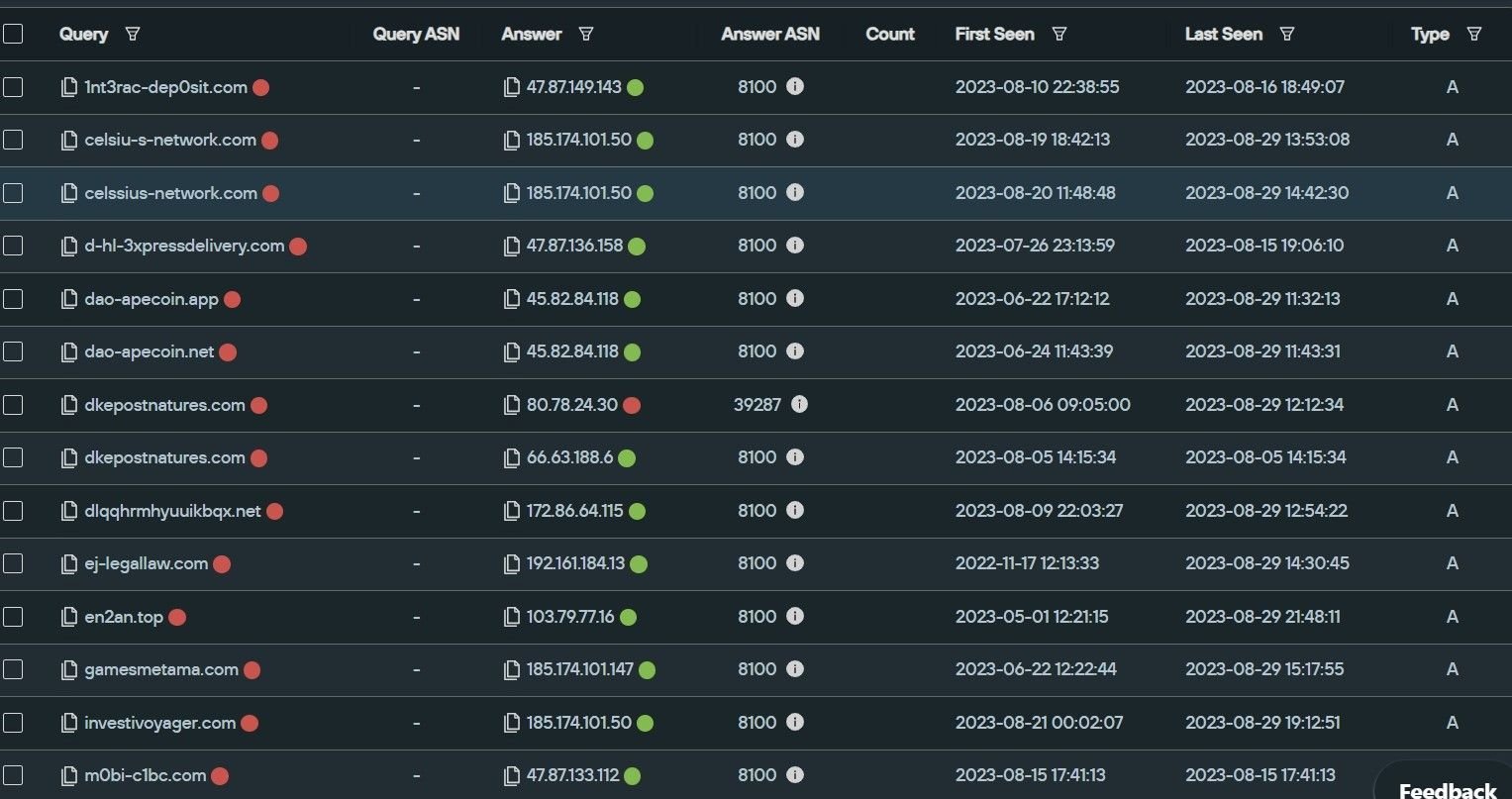
Fig. 6 – Crypto-related infrastructure linked to the same threat actor
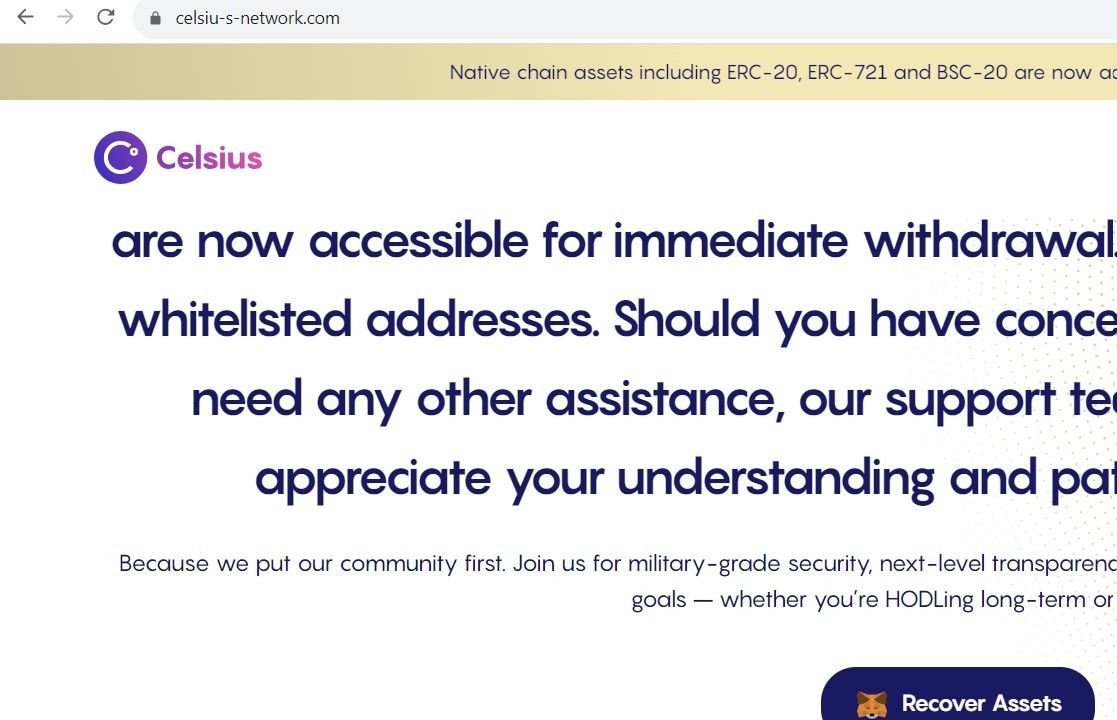
Fig. 7 – Scam domain targeting Celsius customers with “asset recovery” services
It is highly likely that either these domains are being used in conjunction with similar phishing emails to those observed in the Voyager campaign, or threat actors are awaiting the outcome of the creditor vote to approve the Celsius Network’s bankruptcy plan.
Not all of the additional domains our team discovered are related to crypto fraud, but the ones that engage in phishing domains seem to focus solely on crypto platforms.
PayPal USD Phishing Campaign
For example, the below domain impersonates PayPal USD – a stable coin backed by the U.S. dollar – and attempts to trick victims into connecting a local crypto wallet:
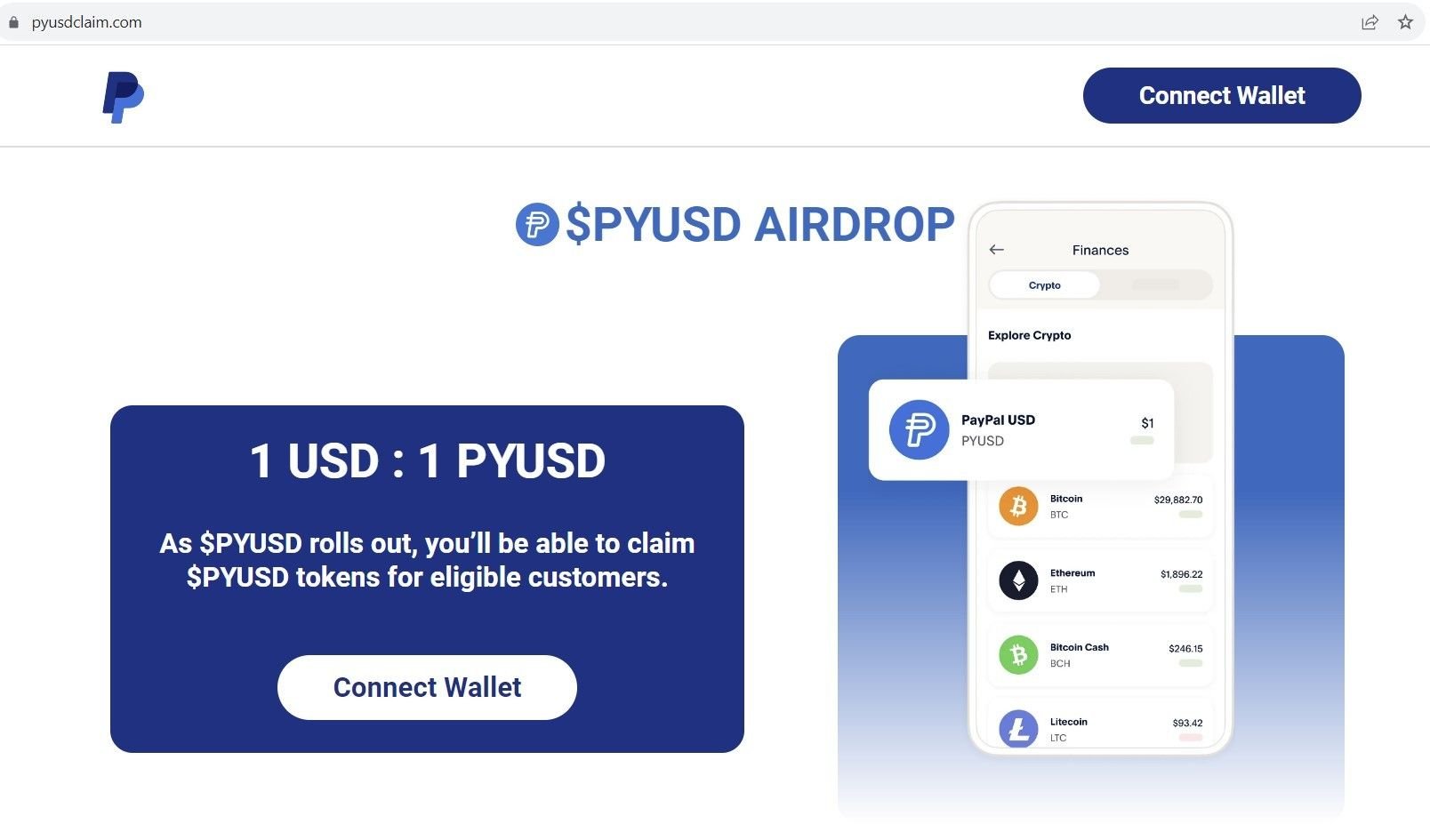
Fig. 8 – Scam domain impersonating PayPal USD
The same threat actor also hosts a phishing domain using a Doge coin theme, in an attempt to inject a local coin miner that’s passed off as a crypto wallet:
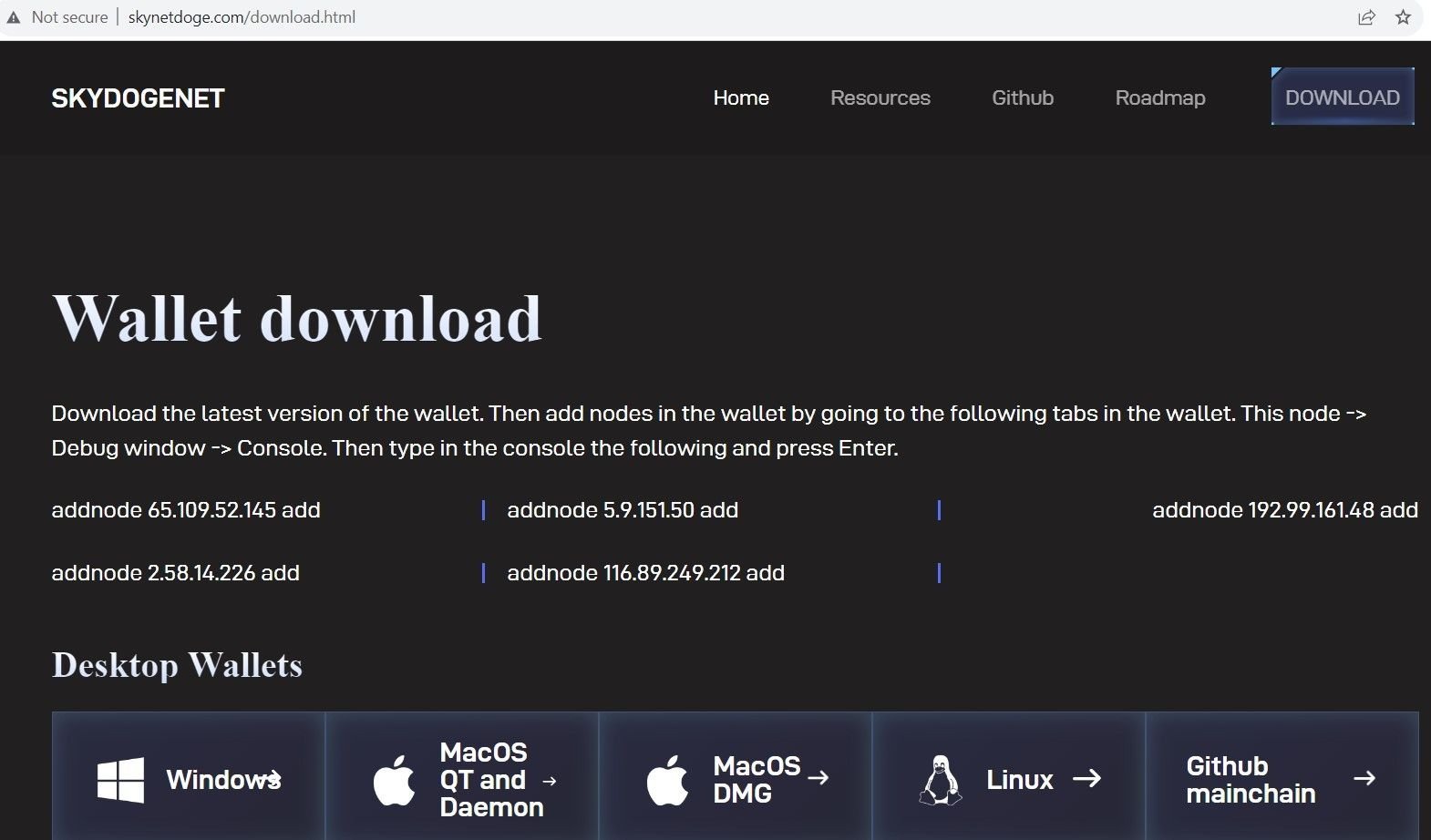
Fig. 9 – Doge coin scam domain
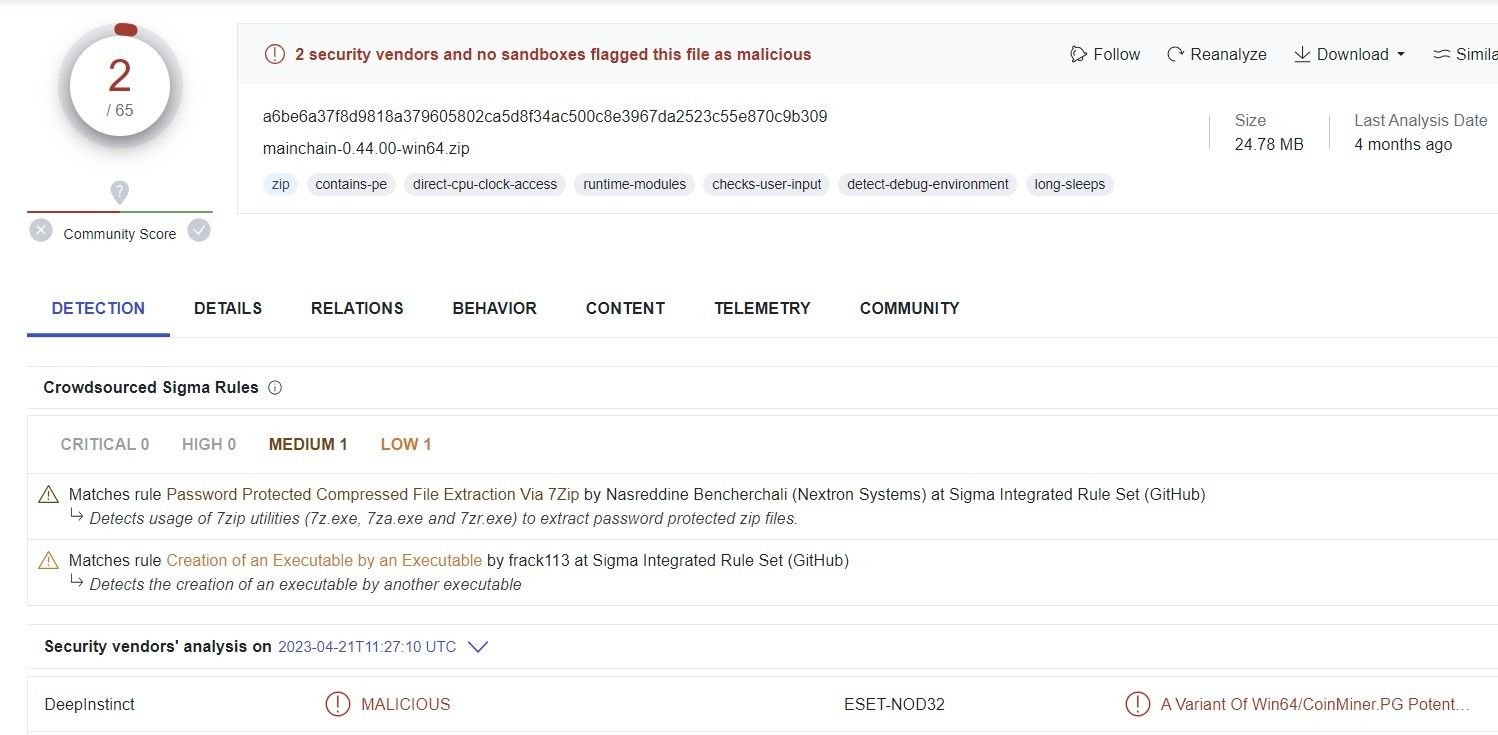
Fig. 10 – Analysis of Doge malware
Conclusion
In the wake of the FTX scandal, as the crypto industry continues to experience significant financial disruption well into 2023, crypto investors are viewed as low-hanging fruit by opportunistic threat groups seeking to take advantage of the chaos that ensues when a prominent asset platform goes bust, leaving thousands of users out of pocket with little hope of a full refund.
Silent Push Enterprise users benefit from a curated early warning feed that contains a full list of IOCs, including thousands of domains linked to crypto scams, eWallet fraud and fake trading apps.
The free Silent Push Community Edition features many of the tools, lookups and advanced queries that we used to research the Voyager and Celsius scams outlined in this blog. Use the link below to register.
IOCs
- 185.174.101[.]50
- bigbrandaid.bigphew[.]com
- investivoyager[.]com
- celssius-network[.]com


