“ViserBank” website templates for sale on Envato being used to spoof big-name banks. 2000+ phishing domains discovered targeting Capital One, Santander, BNP Paribas, Wells Fargo, Bank of America, and JP Morgan Chase.
Key Findings
- “ViserBank” templates, sold on Envato, are being used to create scam banking websites
- Brands impersonated include Capital One, Wells Fargo, Bank of America, JPMorgan Chase, Santander Bank, and Virgin Money
- Domains discovered in the wild attempting to harvest identity data and login information
Executive summary
Silent Push Threat Analysts have discovered that Envato – one of the largest digital asset marketplaces in the world – are selling suspect e-banking templates under the name of ViserBank.
The templates are being used to spoof big-name banks including Capital One, Wells Fargo, Bank of America, JPMorgan Chase, Santander Bank, and Virgin Money, among others.
Most of the websites built using the templates are extremely low quality, and are engaged in active phishing campaigns attempting to harvest sensitive information, including identity documents and users’ banking information.
Silent Push are tracking ViserBank-related activity via proprietary content scans using Silent Push Web Scanner. Actionable ViserBank intelligence is being provided to Silent Push Enterprise customers via two dedicated IOFA feeds.
Background
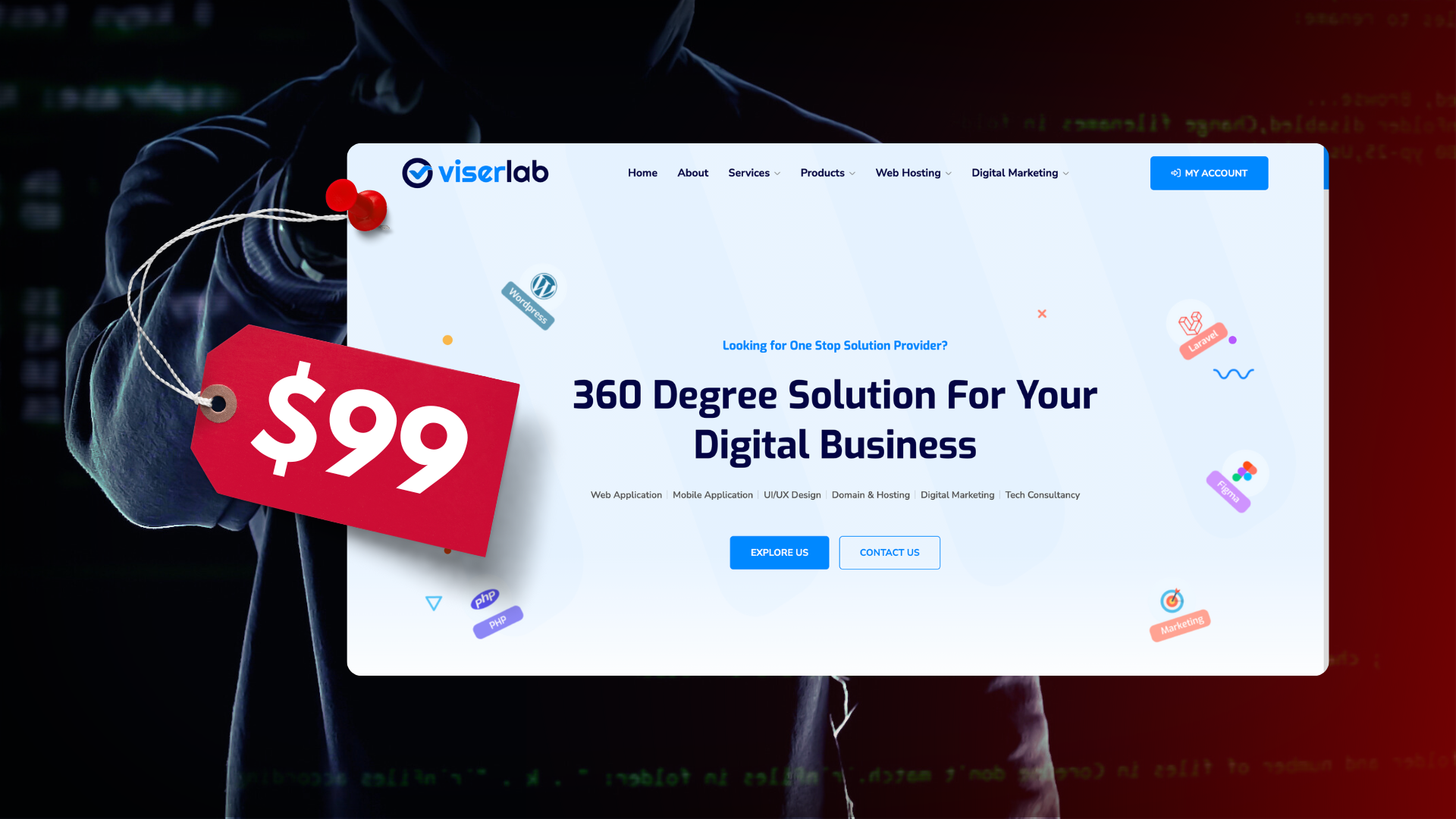
“ViserBank” website templates are marketed on Envato’s CodeCanyon marketplace as a $99 solution for building “cross-platform digital banking systems”:
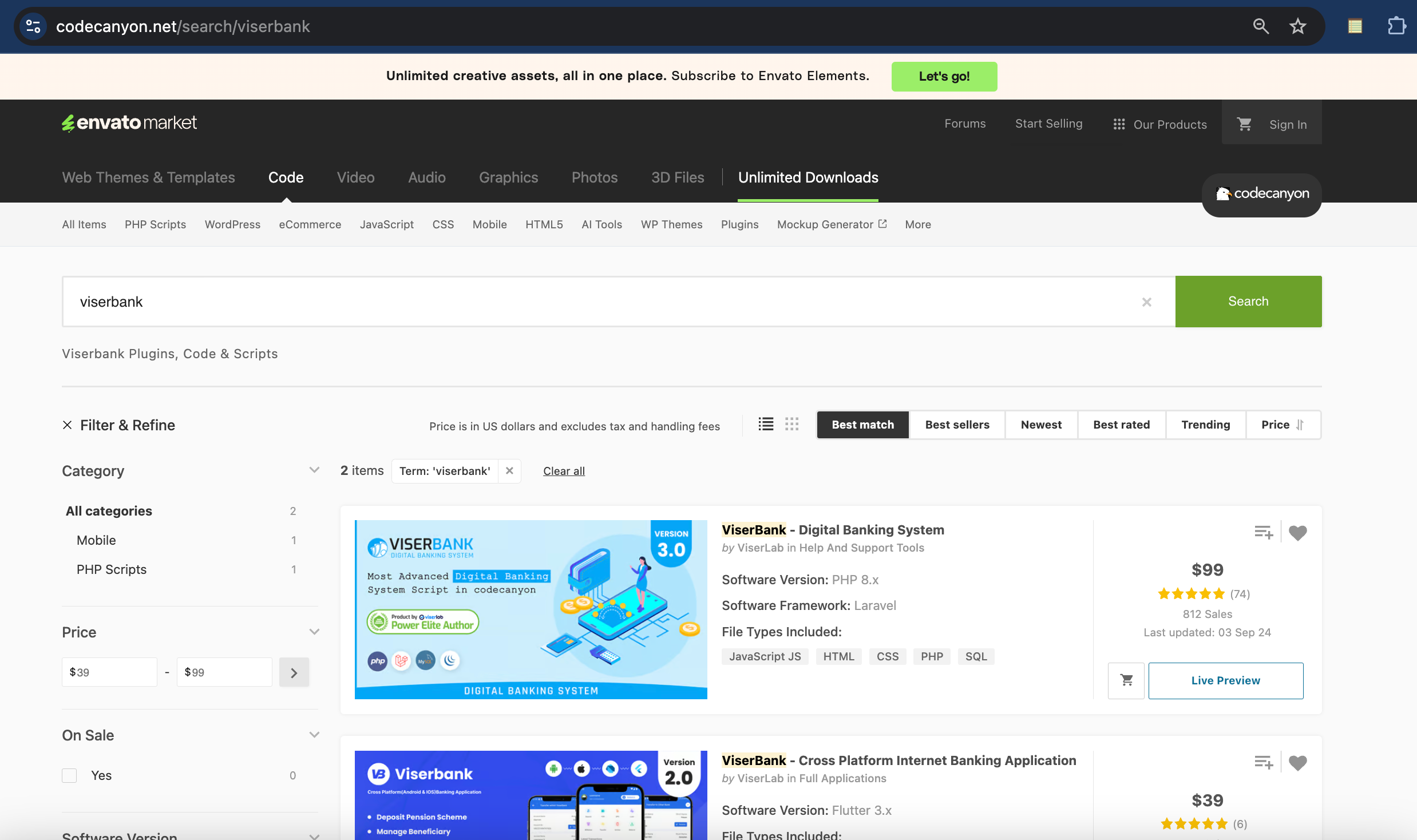
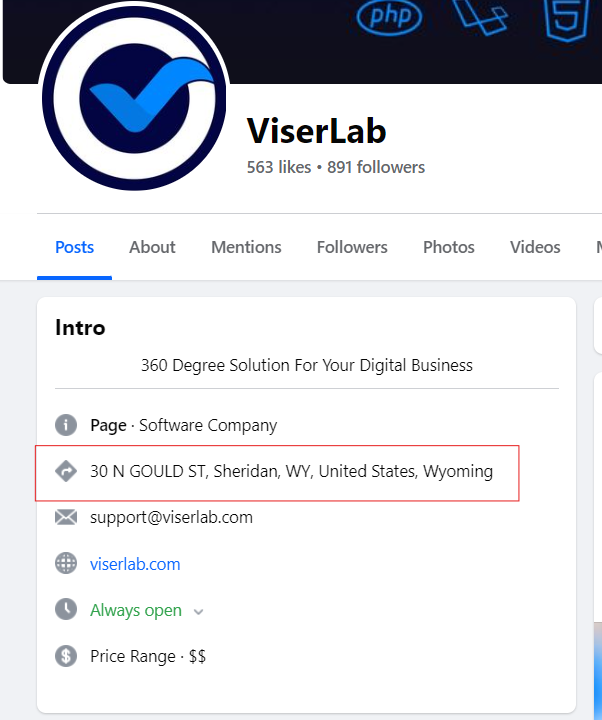
Last year, Reuters published an investigation on how cybercriminals are using Wyoming shell companies for global hacks. ViserLab – the development company behind ViserBank – claims to be headquartered in Wyoming.
Additional information
This blog contains a public overview of how we located and tracked the deployment of ViserBank templates, and the corresponding fake banking websites.
Certain key data types and threat-hunting techniques have been omitted for operational security reasons.
Sign-up for a free Silent Push Community account
Register for our free Community Edition to use all of the tools and queries mentioned in this blog.
Initial discovery
We recently noticed several websites, including onecapitalschoicebank[.]com, santender[.]net, and eastwestpremeircorp[.]com shared similar content traits, even though the domains themselves and the corresponding websites were unrelated.
![Phishing site @ onecapitalschoicebank[.]com](https://www.silentpush.com/wp-content/uploads/image-120.png)
ViserBank content re-use
After analyzing this domain grouping, we found a specific phrase being reused across all domains. We then used a proprietary Silent Push hash value to search the internet for related sites sharing the same language.
One of the domains we uncovered was vinancebk[.]com, which references “Viser bank” within the HTML:
![vinancebk[.]com](https://www.silentpush.com/wp-content/uploads/image-121.png)
Pivoting on ViserBank content
We identified a series of alphanumeric phrases that we used to track links to dozens of low-quality banking websites by constructing a custom scraping algorithm in the Silent Push Web Scanner, that identified new domains.
All of the returned domains featured a bank or financial service, with some names that appeared to have been made up.
While checking the source code of a few of the URLs, we noticed several references to “viserbank”:
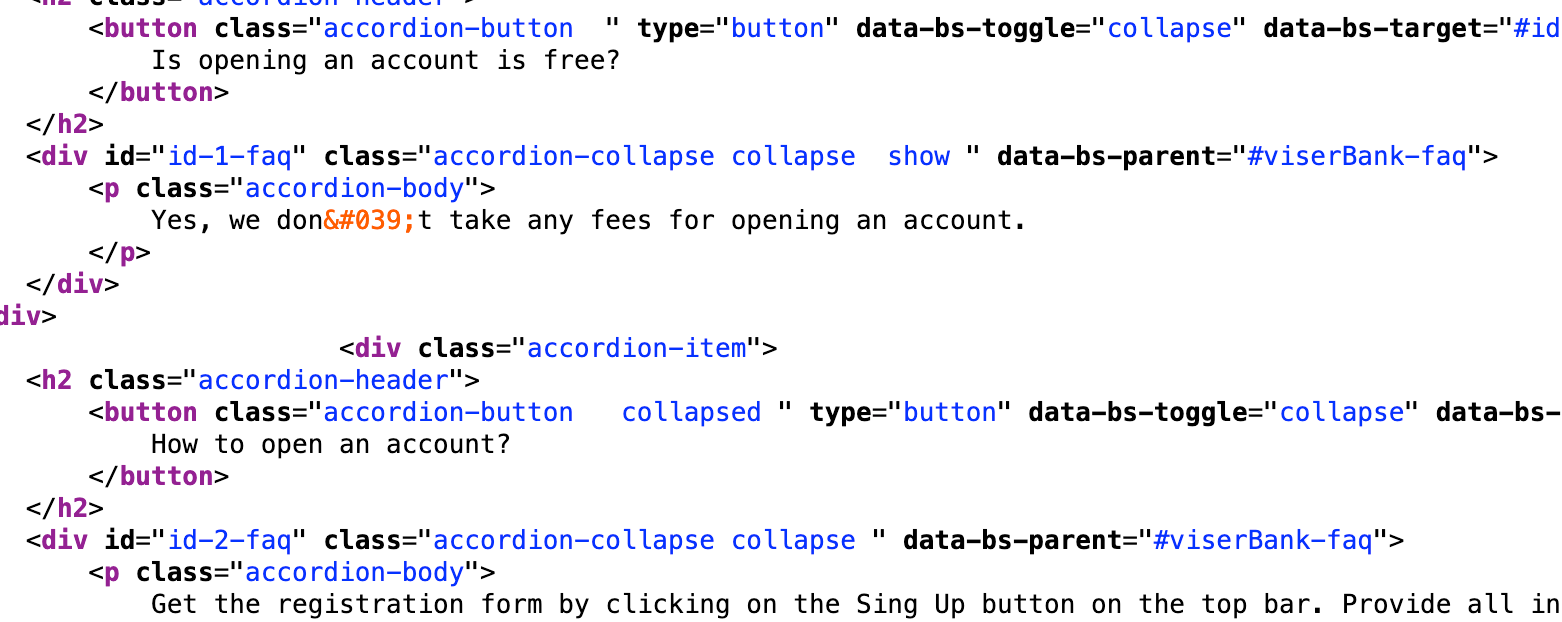
Further investigation revealed that different sites built using ViserBank use slightly different libraries.
Traversing ViserBank infrastructure
Combining several more ViserBank Web Scanner parameters, we discovered more than 2,000 unique domains and IPs, all using the same questionable platform, with many of them impersonating major brands.
Here’s a few examples. The phishing domain wellsfargo-inc[.]com attempts to steal Wells Fargo banking credentials:
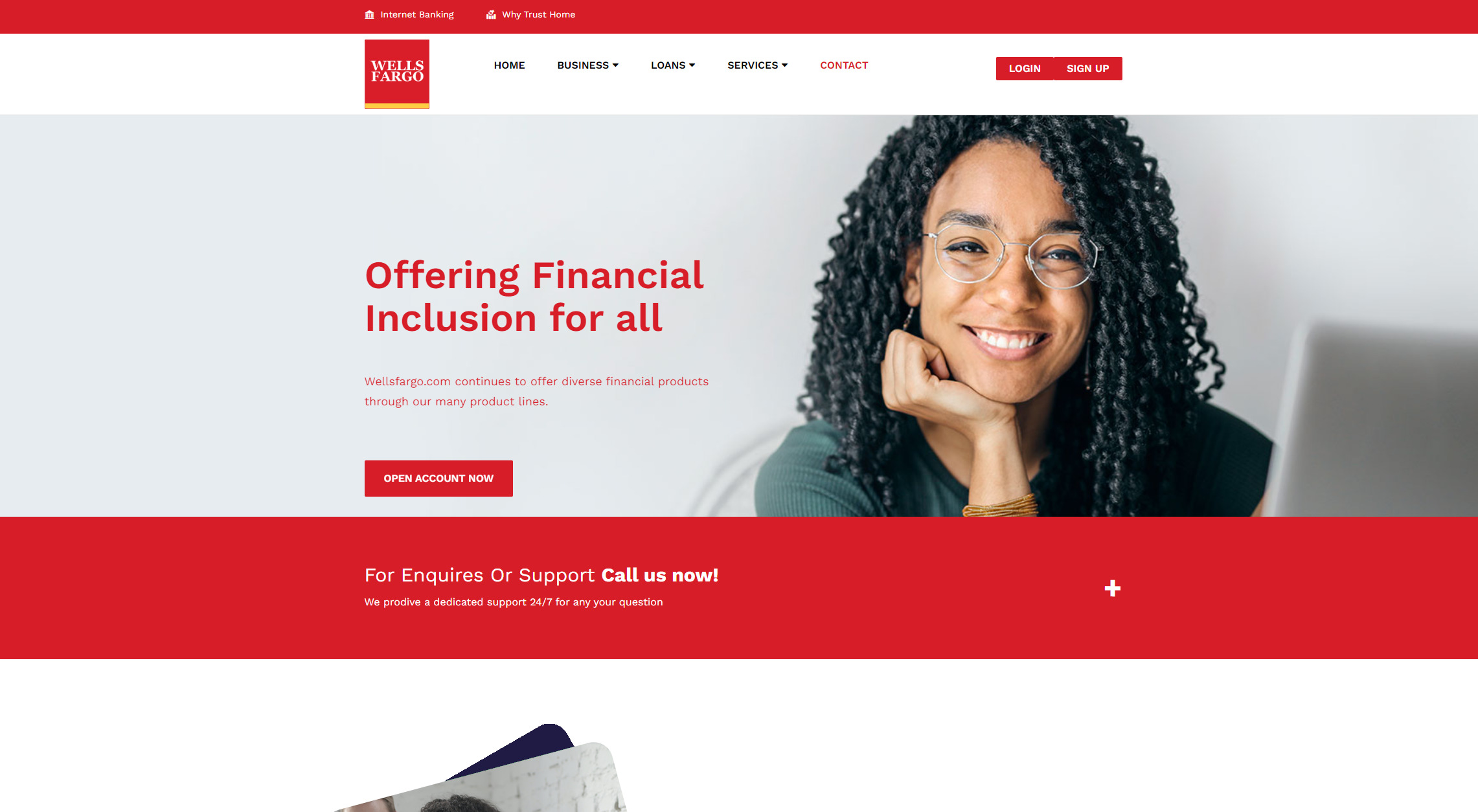
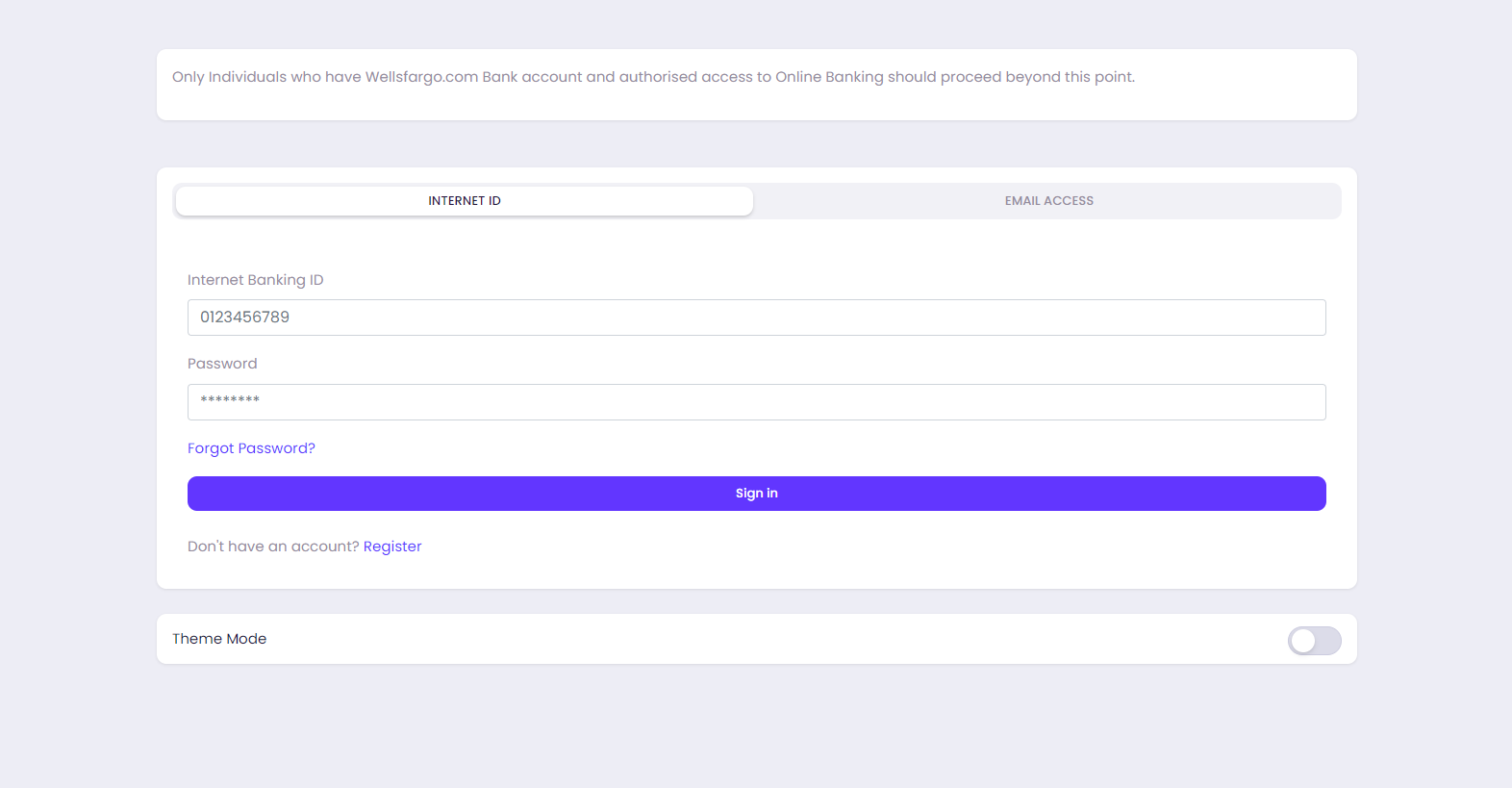
The domain features a form that asks for a “Wells Fargo Banking ID”, and the user’s password:
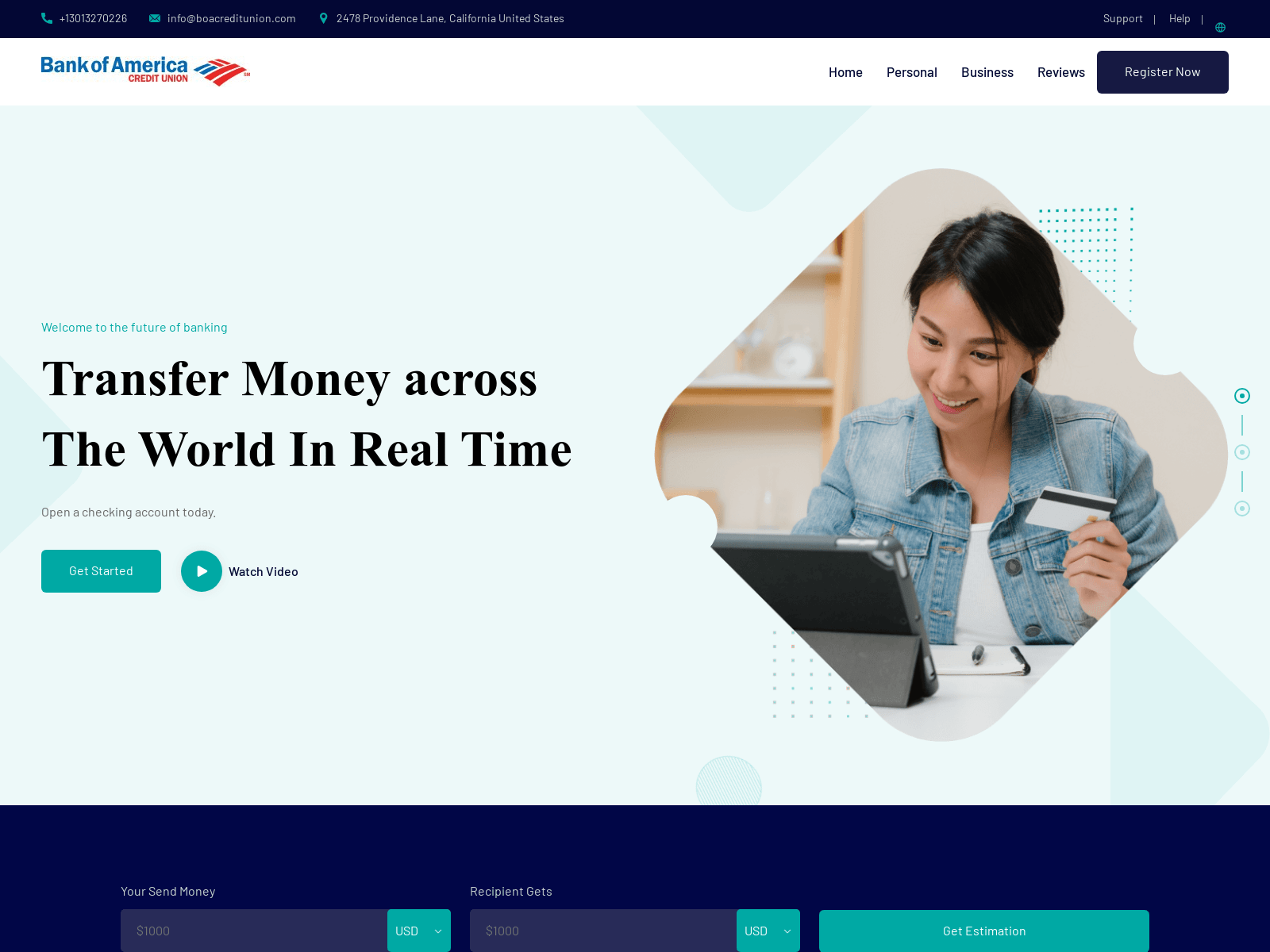
Here’s another phishing domain, boacreditunion[.]com, targeting Bank of America customers:
XBANK
As well as spoofing legitimate brands, threat actors are using ViserBank templates to trick users into signing up for obscure banking services, and handing over private data at point of registration.
An “XBANK” registration form hosted on one such phishing domain – xactverse[.]com – includes a prompt to include the user’s name, address, phone number, social security number, and passport photo:
![Phishing page @ xactverse[.]com](https://www.silentpush.com/wp-content/uploads/image-129.png)
!["Registration form" @ xactverse[.]com](https://www.silentpush.com/wp-content/uploads/image-130.png)
Mitigating ViserBank activity
We’ve constructed two Silent Push IOFA Feeds containing all the scam ViserBank domains and IP addresses gathered during our investigation, available to Silent Push Enterprise users.
Silent Push Community and Enterprise users can also use proprietary Web Scanner fields to track ViserBank content, and pinpoint pre-weaponized infrastructure.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.
Click here to sign up for a free account.
IOFAs
- boacreditunion[.]com
- onecapitalschoicebank[.]com
- vinancebk[.]com
- wellsfargo-inc[.]com
- xactverse[.]com

