The Enemy Within: Threat Actors Target Subdomains of Trusted Global Brands in Mass Open Redirect Abuse.

Key points
- Silent Push has uncovered open redirect phishing campaigns utilizing spoofed Microsoft and DocuSign notifications.
- Prominent email marketing services are being exploited.
- Over 6,000 subdomains identified as being vulnerable to open redirect exploitation.
- URL manipulation used to direct traffic to attacker-controlled infrastructure.
- Popular brands used as lures to avoid email blacklisting.
Background
We recently published research that explored open redirect vulnerabilities. In the blog, we discussed how a subdomain of citi[.]com using CHEETA-Mail infrastructure was redirecting users to phishing pages targeting Microsoft 365 login pages.
Our Threat Analysts have continued their research, and we’ve encountered more phishing campaigns targeting enterprise users with fake notifications from prominent tech companies including Microsoft and DocuSign, luring users into clicking malicious links that redirect to attacker-controlled infrastructure:

DocuSign phishing email
We’ve observed a growing trend of cloud-based email marketing service subdomains being targeted by threat actors seeking to exploit consumer trust in big name brands by propagating global phishing campaigns.
Microsoft credential phishing
During our investigation, we discovered a phishing email using a spoofed notification from “ServiceDesk” that attempted to fool users into clicking on a link entitled “Clear Cache”.
The email uses a hyperlink embedded in an image to direct the user to a URL involved in a threat campaign that spoofs a Microsoft login page hosted on the third-party service glitch[.]me:
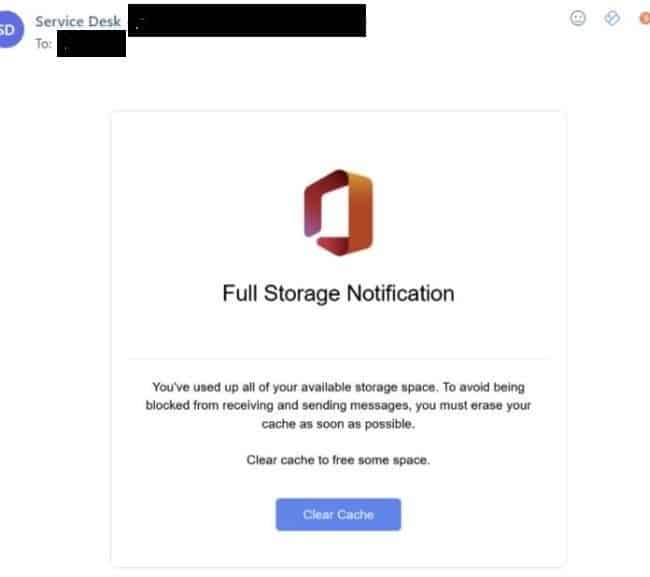
M365 phishing email
The original landing page from the email belonged to links.makeit.usfoods[.]com. The URL uses two hops to redirect users to the intended phishing page:
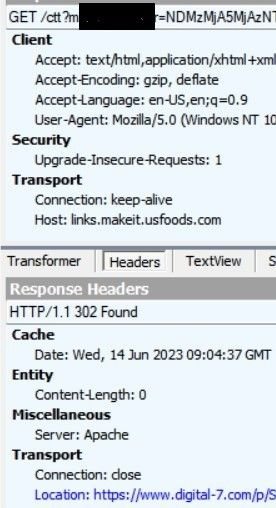
URL analysis 1
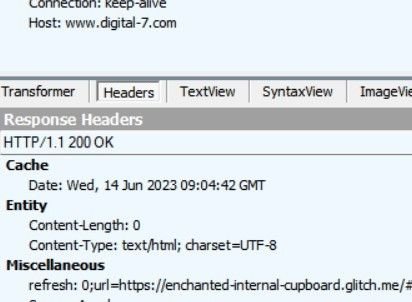
URL analysis (2)
We continued to observe different Microsoft 365 and DocuSign spoofing emails using the same tactics, with similar URLs. Emails redirect to domains hosting malicious AiTM proxy kits for Microsoft credential phishing. We explored the phishing process in our previous blog, so let’s focus on the abuse of vulnerable infrastructure via open redirects.
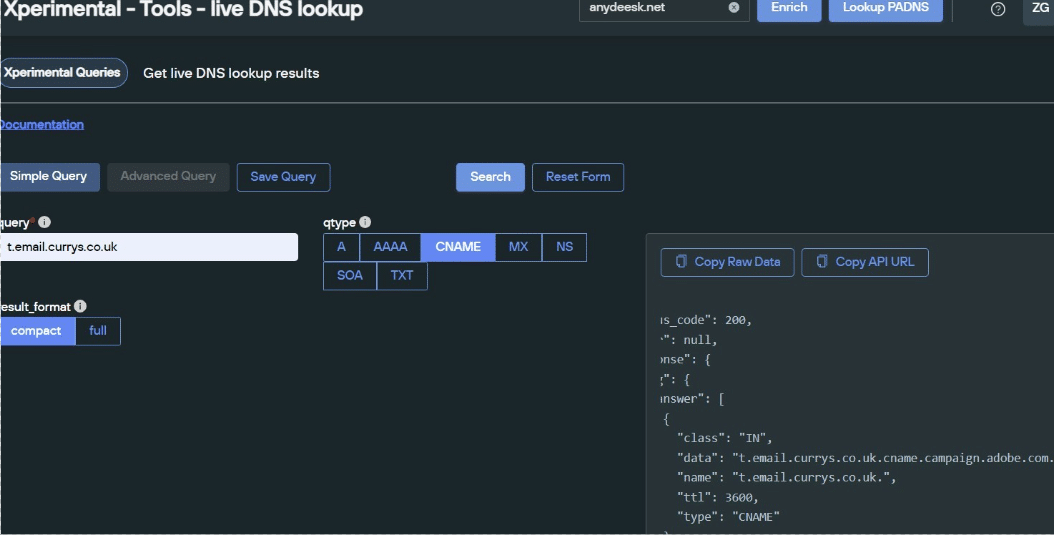
Using Silent Push to execute a live DNS lookup, we were able identify a CNAME record associated with the domain (recp.rm02[.]net):
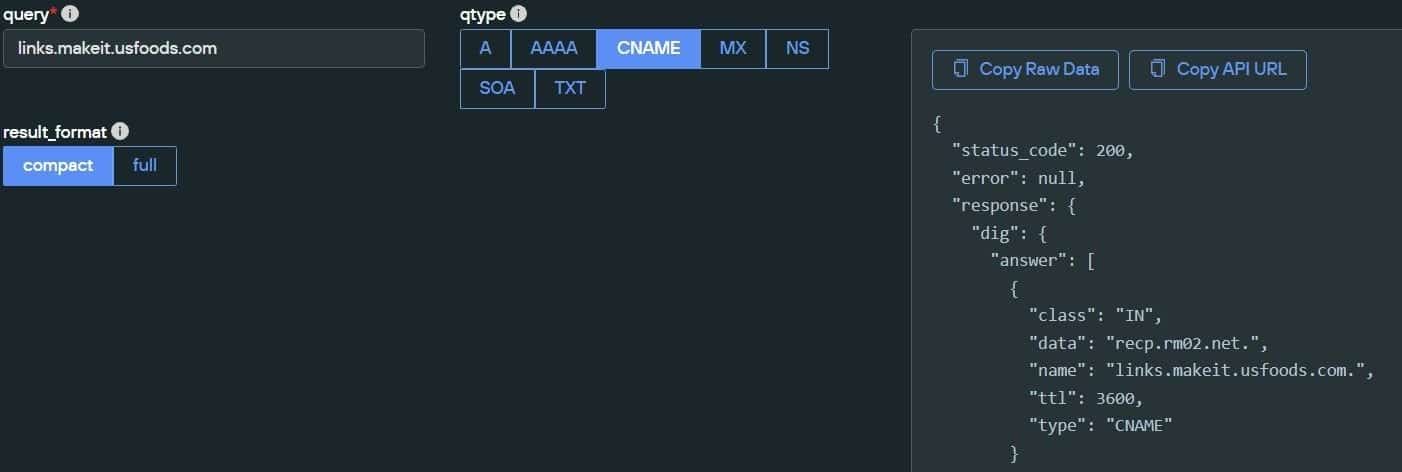
Identifying a CNAME record
We observed another phishing email containing a spoofed Microsoft 365 notification with a URL belonging to the above CNAME domain ‘recpmrm02[.]net’ i.e – hxxps://recp[.]rm02[.]net/ctt?m=<REDACTED>&r=NDMzMjA5MjAzNTUxS0&b=0&j=<REDACTED>&k=reviewCTA&kx=1&kt=12&kd=hxxps://thelittlebluerocketship[.]com/p/
<REDACTED>/<REDACTED>@<REDACTED>.
The URL pattern observed matches links.makeit.usfoods[.]com. We performed further research into infrastructure sharing the CNAME recp[.]rm02[.]net. Our investigation showed that all domains with the associated CNAME were vulnerable to open redirect exploits that involved changing a redirect to any attacker-controlled domain.
The scope of the problem
By analyzing meta data from rm02[.]net, we were able to identify more than six thousand similar subdomains. The infrastructure is associated with ‘Acoustic Marketing Cloud’ (formerly Silverpop). The URL structure also resembles an example shared by the platform on their support page (https://help.goacoustic[.]com/hc/en-us/articles/360043608853-Send-your-email). We discovered subdomains associated with a wide range of brands, from trading and financial platforms to tobacco companies and retail organisations, among others.
Pivoting through URL data
Consider the URL we received for links.makeit.usfoods[.]com – links.makeit.usfoods[.]com/ctt?m=&r=NDMzMjA5MjAzNTUxS0&b=0&j=&k=PrivacyPolicy&kx=1&kt=1&kd=hxxps://www.digital-7[.]com/p//
If we replace the subdomain portion of links.makeit.usfoods[.]com with any of the 6,000+ subdomains found, whilst keeping the rest of the URL intact and changing the last ‘REDACTED’ portion with any email address of our choice (or supply a different phishing domain than www.digital-7[.]com), the redirect still works.
Example pivot
For example, if we take links.email.myparliament[.]com and replace the original email address with theking@buckinghampalace[.]com, while keeping rest of URL the same, the open redirect still leads to digital-7[.]com, which eventually redirects to phishing pages as seen here:

Phishing page re-direction analysis (1)
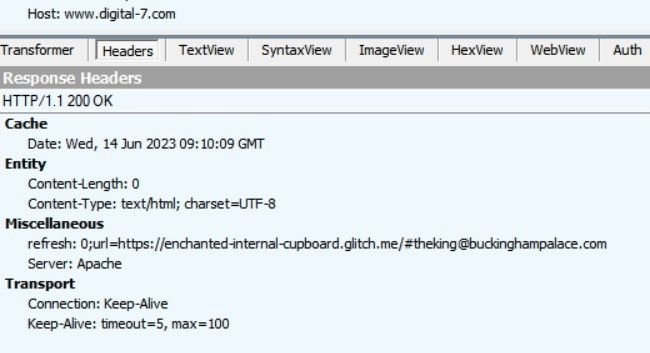
Phishing page redirection analysis (2)
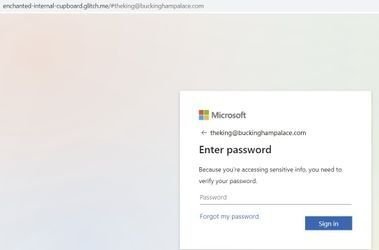
Destination page
Similarly, a threat actor intending to initiate a phishing attack against an employee from Schwab could use the subdomain emailservices.schwab[.]com and append the remaining URL to redirect targeted users to any web page of their choice.
Additional email marketing abuse
Alongside phishing emails pointing to malicious infrastructure, we’ve also discovered subdomains of legitimate brands, with CNAME records linked to trusted email marketing services, that are being exploited using open redirects which lead to Microsoft 365 login pages and spoofing/credential phishing operations.
Key observations
One of the more prominent cases involved subdomains with a CNAME belonging to Adobe’s marketing service campaign.adobe[.]com.
We also observed multiple submissions by different users to public sandboxes such as tria[.]ge and Joe Sandbox, where some subdomains belonging to Adobe, subdomains of popular hotel brands and the prominent UK electronics retailer, Currys, are being used to redirect to attacker-controlled phishing pages:
Currys subdomain redirection
The URL format constructed for the marketing newsletters are similar but are being abused by threat actors to propagate illegal activity. We were able to re-use the links to confirm the presence of open redirect vulnerabilities. Changing the final page destination to a benign address like facebook[.]com redirects to the same domain.
Example exploit using facebook[.]com
Let’s look at an example. The following URL was available publicly on ‘Joe Sandbox’, and likely sent to an employee of the State Government of Maine (64bit encoded email addresses redacted for privacy).
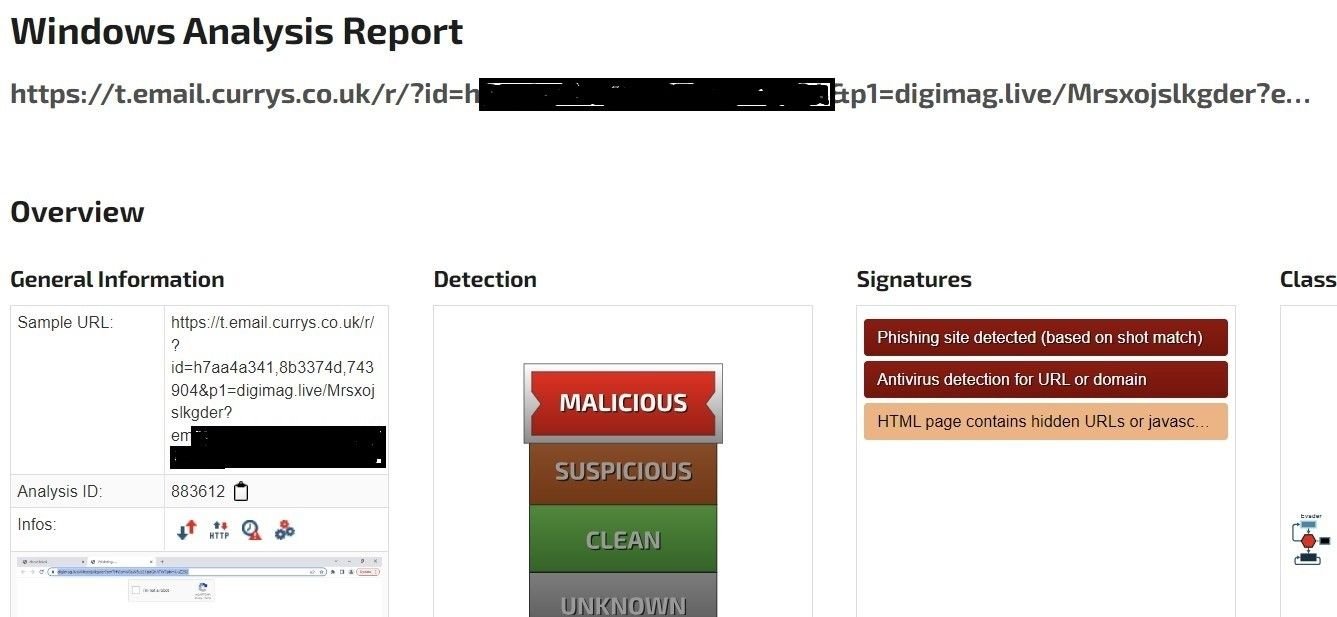
Currys – Analysis report
If we change the part of the URL after ‘&p1=’ to facebook[.]com, we are successfully redirected to Facebook’s home page, confirming the URL structure is susceptible to open redirects, as seen from following screengrabs:
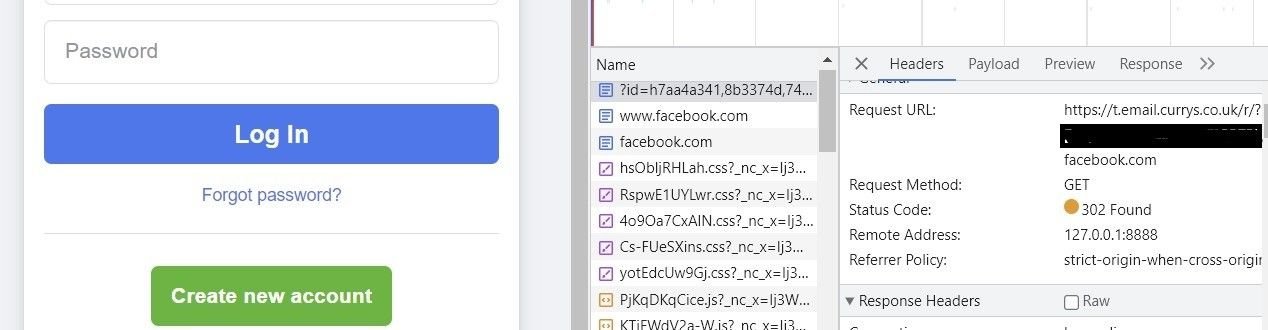
Facebook redirect
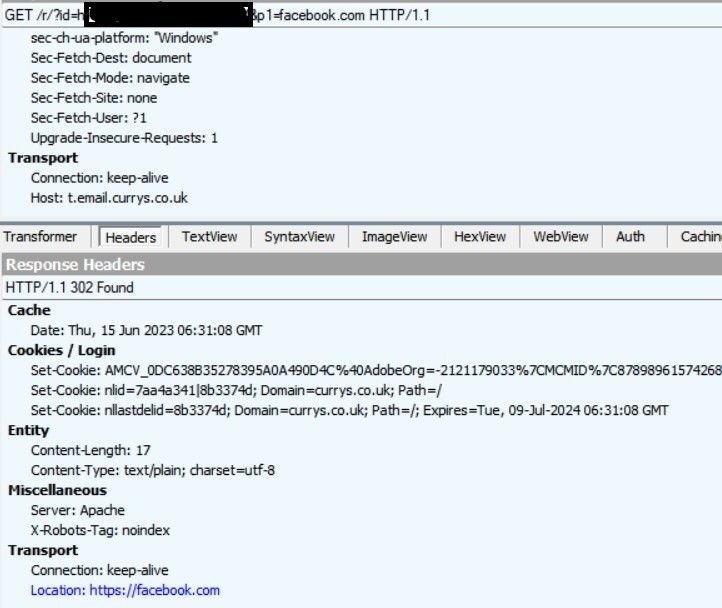
Redirect analysis
Additional example
Whilst hunting for similar abuse on Joe Sandbox, we also discovered a Swiss insurance company’s subdomain with a similar URL structure that was susceptible to an open redirect also. Let’s repeat the scenario of a domain name change to facebook[.]com using the insurance company’s URL:
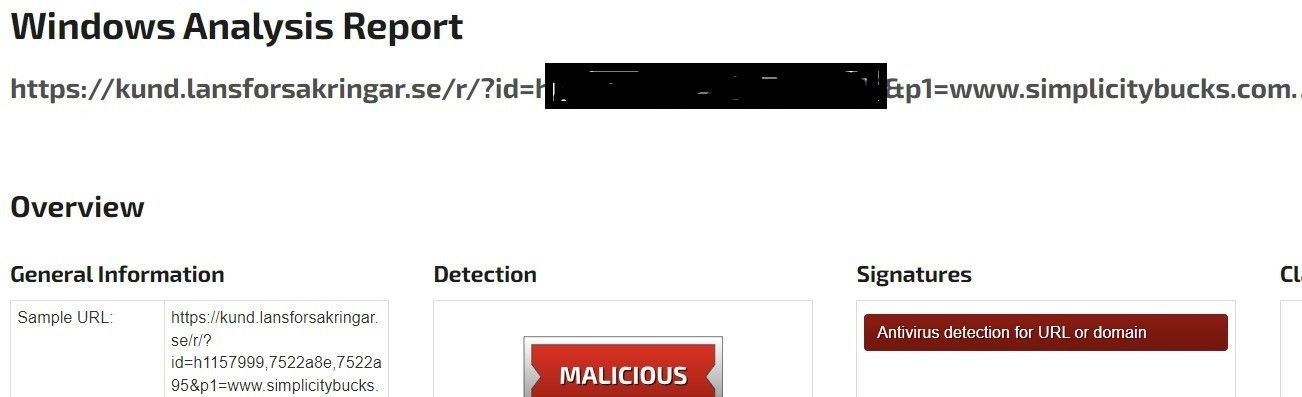
Insurance company URL analysis
Although the URL structure is similar, with valid open redirect abuse, we were not able to verify any link to campaign.adobe[.]com.
Using Silent Push to protect against open redirect abuse
Threat actors are using abusing email marketing services by targeting enterprise domains with open redirect vulnerabilities that open the door for phishing emails, with Microsoft credentials being the attack vector of choice.
Companies need to offer awareness training to their employees that educate users about the types of phishing campaigns used in open redirect exploits. Users need to be doubly sure that login information is being used on trusted infrastructure. For years, organizations have trained their employees to be wary of suspicious URLs. Our research shows that the scope of the problem has now extended to legitimate subdomains.
At present, there are an unknown number of domains with CNAME records that are open for abuse. We’ve created a dataset for Silent Push customers that can be used to identify elements of an organization’s public DNS presence that’s susceptible to an open redirect exploit.
Enterprise users can download the data by navigating to ‘Advanced Query Builder > Feeds Queries > Get download link’ and choosing the feed name ‘redirect_vulnerable_domains.txt’.
We’ve observed open redirect phishing campaigns using third party hosting sites to host malicious content, so we’ve created feeds that list the domains involved in intermediate redirects between marketing subdomains and the phishing page. These IoCs can be accessed by Enterprise users through the ‘Phishing Domains’ early detection feed.
Register for the Silent Push Community Edition to get access to a free set of specialized resources and enriched data that helps your organization combat the growing trend of open redirect exploitation.
Explore Silent Push Enterprise to benefit from pre-weaponized threat intelligence, enhanced security stack integration, enriched observables, and dedicated campaign feeds.
Indicators of Compromise
- midi-safe-quiver.glitch[.]me
- digital-7[.]com
- blkslzaa[.]online
- lkalzzop[.]online


