Silent Push uses content similarity scanning to map out Telegram phishing campaign targeting Eastern Europe and Central Asia
CyberHUB-AM, an Armenian cyber security organization supporting regional NGO’s and journalists, recently published research about a Telegram phishing campaign conducted throughout 2023 and 2024.
Silent Push Threat Analysts have used this information to identify and monitor phishing infrastructure targeting Armenian and Uzbekistani Telegram users, including live phishing domains and portal spoofing infrastructure.
Delivery Method
The attack chain begins with an Armenian Telegram message asking the user to cast a vote for the sender in a contest they claim to be participating in, and asking them to follow a link.
The link appears to resolve to the non-existent URL daxcearm[.]wve (there is no .wve top-level domain), but actually uses the cutt[.]ly URL shortener to send the user to a final malicious URL – https://dolbaebshesp[.]in/.
The final URL hosts a Telegram phishing page in the Uzbek language. 2023 phishing kits previously reported on by CyberHUB-AM used Armenian.
This recent campaign could indicate a unique threat actor, or an updated campaign using the wrong language on the landing page. Although it is unclear why a message in Armenian would link to an Uzbek phishing page, these kinds of mistakes are fairly commonplace in regional cybercrime.
Tracking the Telegram phishing pages
Threat actors deploy their infrastructure to a set of definable (and searchable) parameters.
Our analysts were able to isolate the phishing infrastructure involved in the campaign using proprietary fingerprinting that maps out malicious domains, using a combination of content similarity checks, and the Silent Push Live Scan feature.
Using these methods, we discovered 26 phishing domains, three of which are still live at the point of investigation: uzgolos[.]shop, uzvvots[.]shop, and vote-uzbekistan48[.]top.
![Screenshot of vote-uzbekistan48[.]top using the Silent Push 'Live Scan' screenshot feature.](https://www.silentpush.com/wp-content/uploads/image-20240423-120846.png)
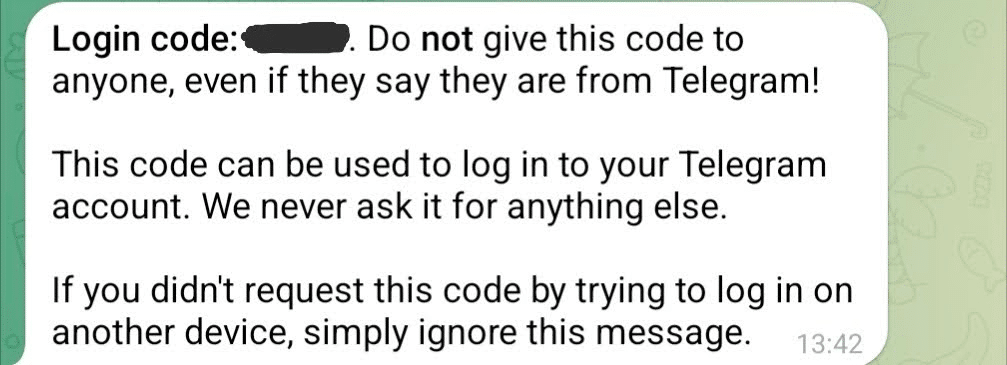
We confirmed the domains were actively phishing for Telegram login codes by accessing the URL in a browser, entering a phone number linked to a Telegram account, after which a code was sent to that account:
Though the three live URLs, and other domain names in the campaign, suggest that Uzbekistan is the geographic region that’s being targeted, we also discovered older URLs from August and September 2023 that can be reasonably linked to the same campaign.
These domain names, including tajikistan-vote[.]site, arm-vote[.]space, and ukr-vote[.]site, and the likely related http://uz-golos[.]shop/, suggest active targeting of other countries too.
Here’s a list of the domains involved:
- amnezisep[.]org
- animraov[.]cc
- beriishovoz[.]space
- berishovoz[.]pw
- dismashep[.]in
- dolbaebshesp[.]in
- dubproduction[.]org
- hilupfoxs[.]ru
- ihavdick[.]lol
- losntinster[.]lol
- mudkoskonkine[.]in
- osding-mosting[.]in
- ovber[.]pro
- ovoz-berish[.]co
- ovozberishuz[.]space
- ovoziberish[.]lol
- rahmatgolos[.]cc
- sudoko-inline[.]org
- tables-mite[.]info
- uzbek1voits3[.]lol
- uzbgolos[.]co
- uzgolos[.]shop
- uzsimkarta[.]space
- uzvvots[.]shop
- vinorozoavos[.]in
- vote-uzbekistan48[.]top
Telegram phishing mitigation with Silent Push
The domains that are currently live have been added to a threat feed that is available to Silent Push Enterprise users – Phishing – Telegram Phishing Targeting Eastern Europe and Central Asia.
New domains that match the signature will be automatically added to the feed.
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push ‘Web Scanner’ and ‘Live Scan’ that we used to track the phishing campaign in this blog.
Click here to sign-up for a free Community Edition account.


