Challenge: Detecting a Brand Impersonation Attack in Motion
At a recent conference, our team was approached by a multi-national media organization to help them investigate a threat campaign spoofing the Okta Identity and Access Management (IAM) platform, via subdomains.
Each online service the organization provides, across all the apex domains it uses, requires multiple subdomains to operate – everything from a customer or employee portal, to integrations with third-party technology, and retail services.
The organization’s security team needed to ensure that they had all bases covered by understanding how exposed they were – including the many thousands of subdomains they use – so that they could deal with any vulnerabilities, and minimize the chances of a breach.
Solution: Complete Discovery of Associated Threat Infrastructure
No other vendor has a better view of Internet-facing infrastructure than us, powered by a proprietary DNS and web content scanning and aggregation engine that leaves no stone unturned in the hunt for vulnerable infrastructure or attack points.
To get at this data, Silent Push features a range of queries that allow you to quickly and accurately map out your organization’s presence online, including timestamped results of all associated subdomains.
Mapping out vulnerable infrastructure
One of these tools – “Discover ShadowIT” – returns a comprehensive list of third-party services set up in an organization’s name, that have the potential to be exploited.
To reveal the full extent of the Okta attack, we executed a ShadowIT query using the apex domain, and received a list of 20,000+ subdomains the organization was using to facilitate third-party services, and the IP addresses they were mapped to.
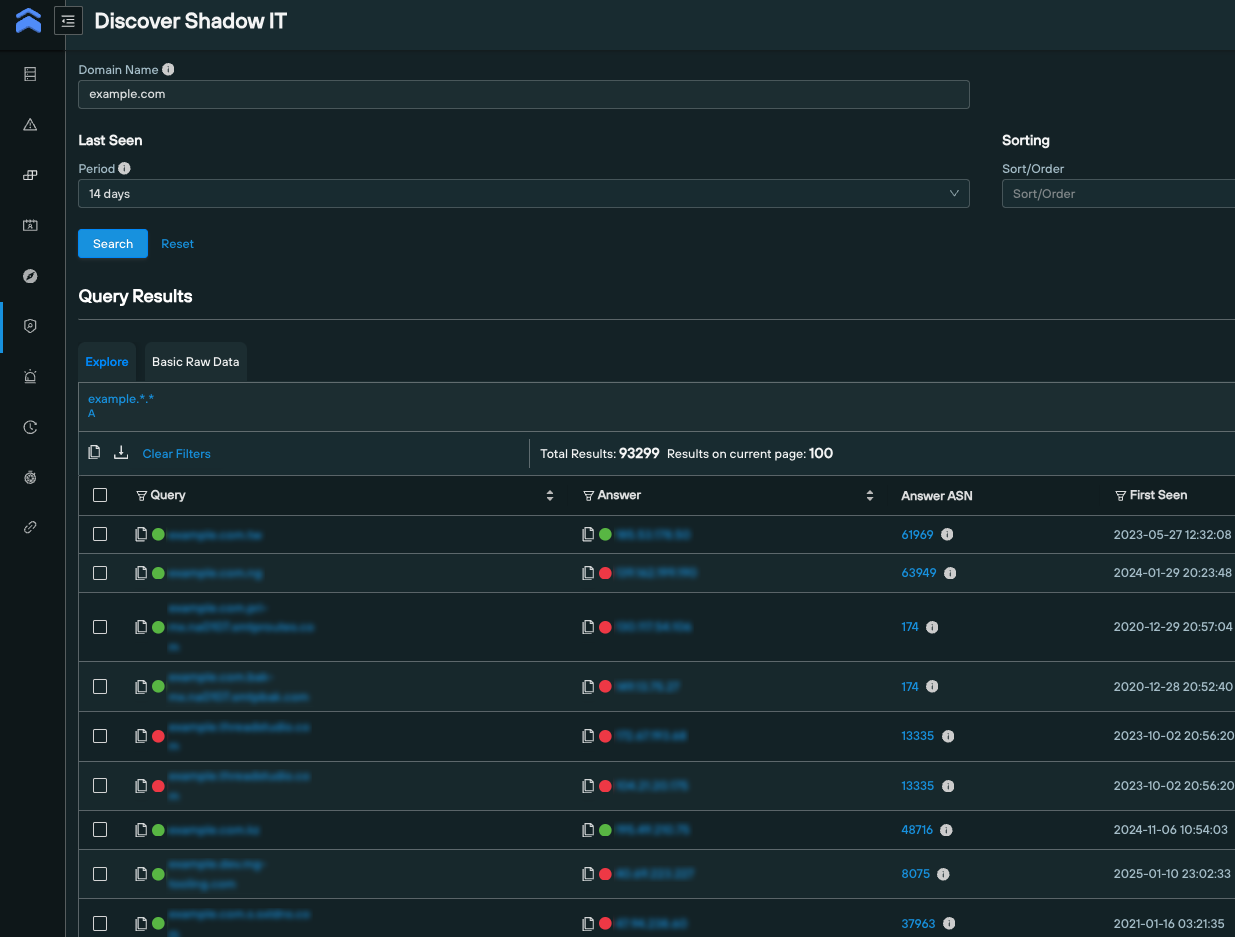
We quickly pivoted across the results for any mention of “Okta”, and discovered subdomains that were not only involved in an emerging attack, but were not on the security team’s radar to begin with.
The organization was able to quickly identify all the linked threat infrastructure, and took immediate steps to close the door on future attacks.
We were also able to improve the organization’s internal workflows by ensuring that the infrastructure team were able to more effectively communicate potential vulnerabilities to the security team, allowing for a better all-around cyber defense posture.
The Silent Push Difference: Ready-made SOC and IR Intelligence
Our team was able to provide the organization with an actionable list of subdomains that their own internal workflows had yet to flag as vulnerable, that did not require additional time-consuming pivots to verify as genuine.
The end result was a new customer, and a happy security team who were able to detect and mitigate what could have been an extremely damaging attack, and gain valuable insight into their public DNS presence that they used elsewhere in their cybersecurity operation.
How were they able to achieve this? Simple. We know more about Internet–facing infrastructure than any other threat intelligence vendor, which gives our customers the ability to fully enumerate any given attack surface or threat landscape.
Not only this, but the platform makes it easy for teams to make critical decisions in high-pressure situations, quickly analyze and validate crucial intelligence datasets, and relay information more effectively between internal teams tasked with protecting an organization’s network.
Learn More About Our Unique Approach to Preemptive Threat Intelligence
Find out how Silent Push helps you to locate hidden and known threat infrastructure, and stop digital assaults at source before they occur using Indicators of Future Attack (IOFAs)™ – domain and IP datapoints that preemptively pinpoint adversary intent BEFORE an attack is launched, and reveal searchable fingerprints of attacker activity.
Contact us here for more information.
Further Resources
We’ve published extensive research on Scattered Spider APT activity that uses Okta in the attack chain to steal data and propagate all of attacks using compromised credentials.
Click here to read our blog.



