Silent Push uncovers a large trojan operation featuring Amazon, Microsoft, Geek Squad, McAfee, Norton, and Paypal domains.
Our Threat Intelligence Team was on the lookout for PayPal typosquatting domains, when one particular domain (paypalsec[.]us) led them to a far larger discovery – an entire network of threat activity, masquerading as numerous global brand names and infecting machines with a malicious file disguised as a remote monitoring tool – WinDesk.Client.exe.
The initial discovery
We found the domain (registered through NameSilo on 2022-08-18) using the Silent Push Live Unsanctioned Assets query – an A record search by qanswer, netmask and various other network parameters.
The domain had some text and images that mimicked Paypal’s actual website, but most of the content populated as unrelated placeholders, which suggested that the site had been built using a multi-purpose template, rather than coded from scratch.
Threat actors aren’t in the business of coding individual websites for hundreds of malicious domains, and sometimes rely on communal site builders to put together phishing websites that target different brands.
The ‘Cancel Now’ button on this particular domain prompted a download of an executable file – WinDesk.Client.exe – that we offer further analysis of below.
The delivery method
Once we’d confirmed the identity of the domain, we analyzed WHOIS, IP and PADNS data in an attempt to find out what other activity it was linked to, leading us to another domain connected to the same Paypal phishing website – help01[.]us (also registered through NameSilo on 2022-08-18).
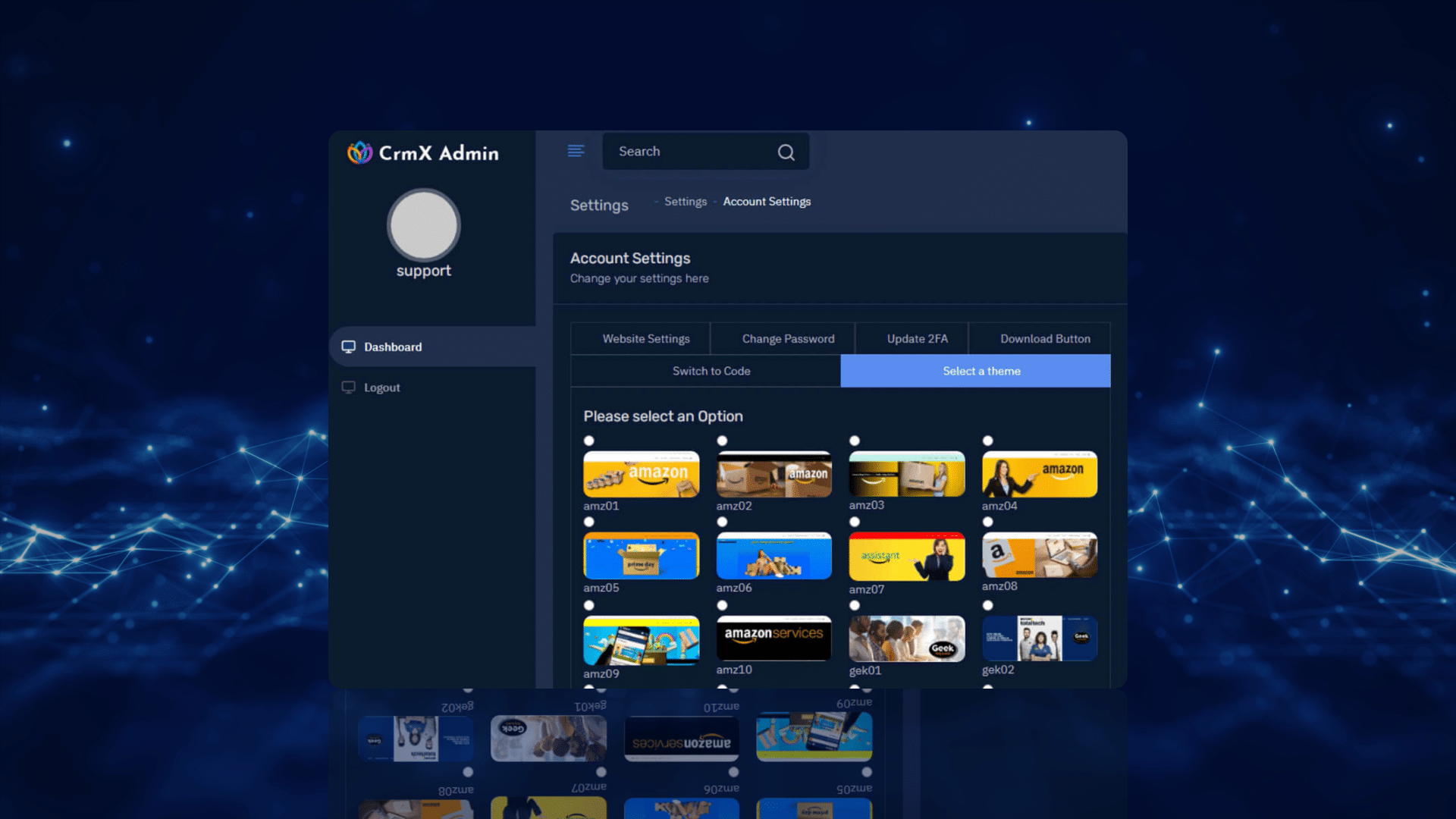
We repeated the process for the IP address associated with help01[.]us, and discovered 30 other domains connected to similar phishing websites, impersonating big name brands such as Amazon, Microsoft, Geek Squad, and Paypal, using the same basic phishing techniques with some subtle differences (see IoC list at the bottom of this article).
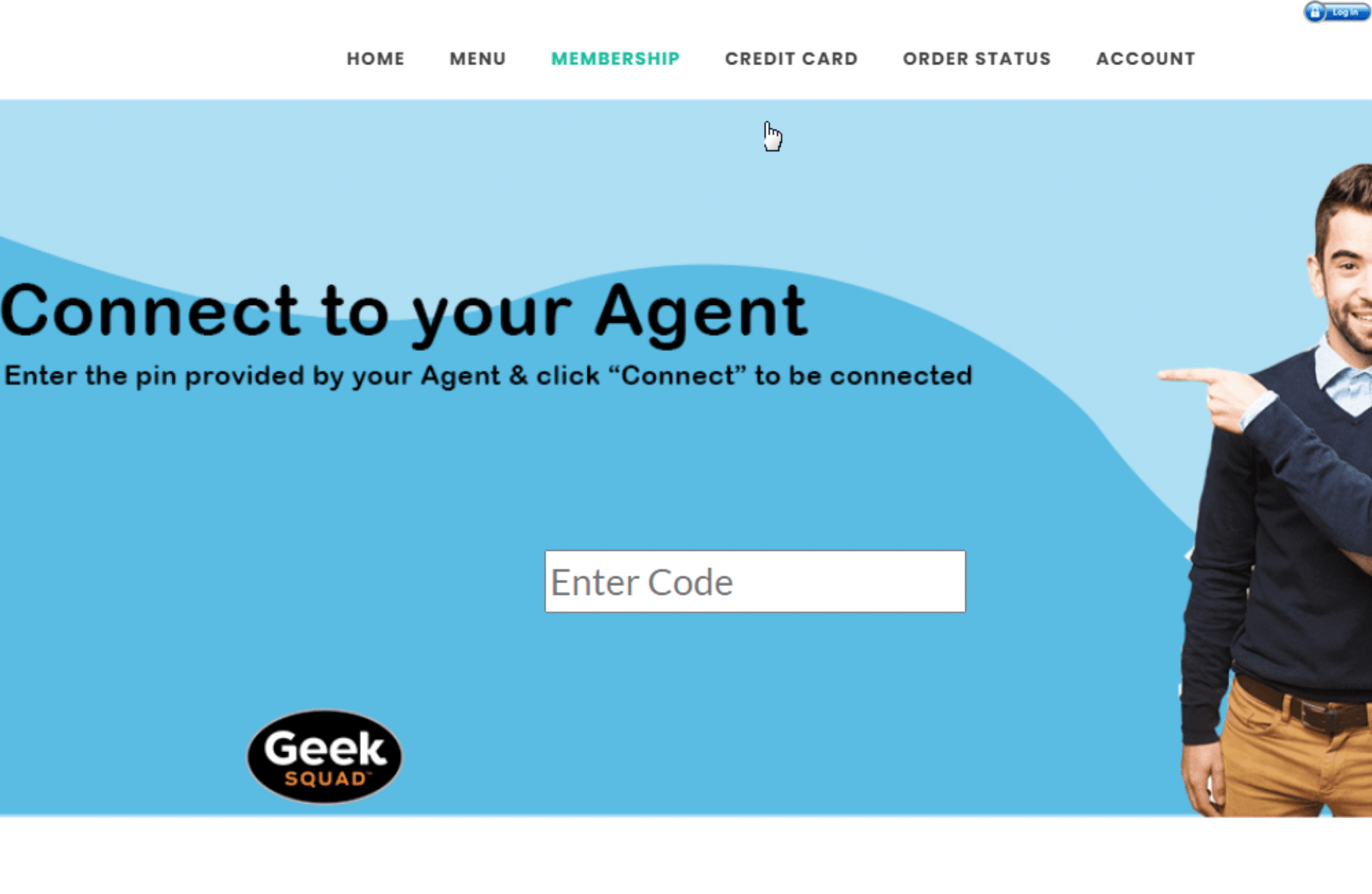
Instead of a ‘Cancel Now’ button, these websites featured an ‘Enter Code’ field.
After a few attempts, we entered a code that was accepted as valid, which started the download of WinDesk.Client.exe.

Analysing the trojan
WinDeskClient.Exe actively tries to stop itself from being run in a sandbox environment, using a combination of debugging restrictions and sleep timers, but our Threat Analysts were able to run it in a test environment in order to ascertain what the file actually does, and more importantly, where it sends information to.
Once run, WinDesk.Client.exe facilitates the install of a parent process – dfsvc.exe – with two further executables initiated from the level above:
> dfsvc.exe
> ScreenConnect.WindowsClient.exe
> screenconnect.clientservice.exe
In its legitimate guise, ScreenConnect.WindowsClient.exe is an executable file which belongs to the ScreenConnect platform (now known as ConnectWise Control), a widely-used remote access tool for customers of ConnectWise.
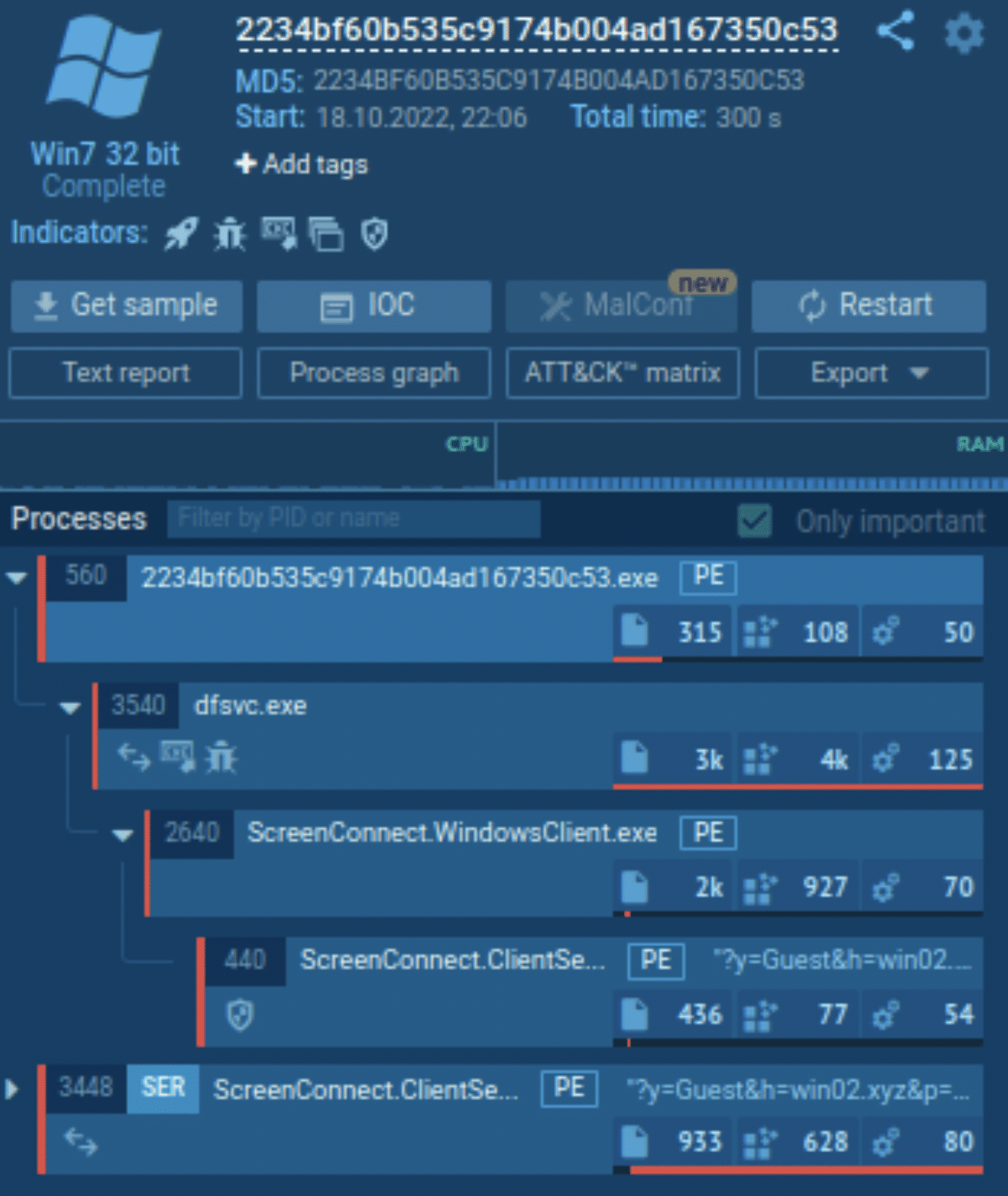
ScreenConnect.WindowsClient.exe does have the potential to record keystrokes, but its the final drop – screenconnect.clientservice.exe – that reveals the most information.
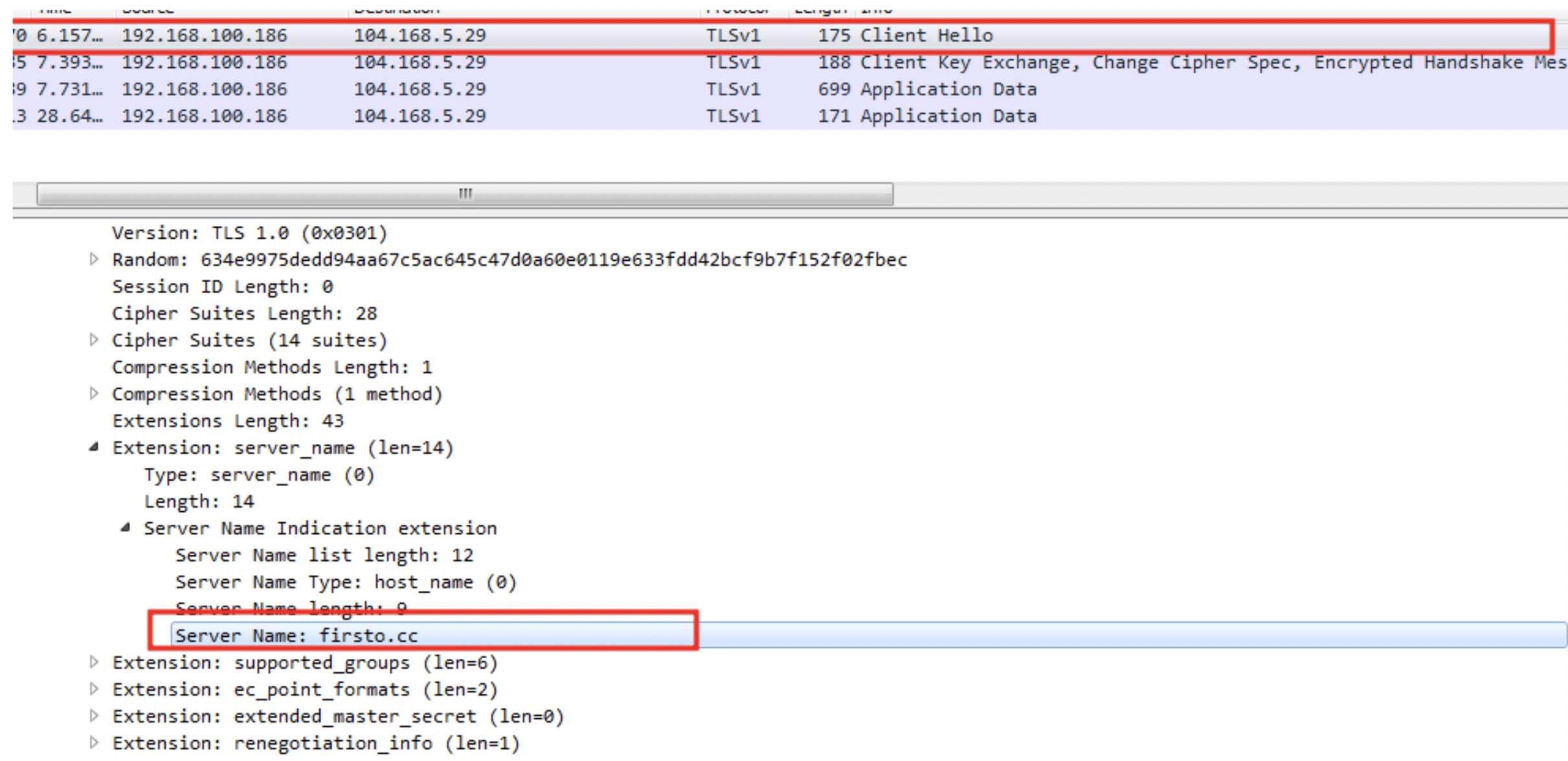
The service attemps to establish a connection with 104.168.5[.]29, which resolves to firsto[.]cc.
We weren’t able to ascertain precisely what data the client process is attempting to send, but the security implications are clear and obvious.
Links to Norton and GeekSupport scams
A passive DNS replication check shows that the server is linked to to another IP – 198.23.212[.]167 – which is connected to phishing sites that are actively impersonating brands such as Norton and GeekSupport:
- firsto[.]top
- firsto[.]cc
- mslxt[.]xyz
- ncareback[.]xyz
- backup02[.]xyz
- gkscare[.]com
- geeksupportcare[.]com
- xpchelps[.]us
- support2norton[.]us
- xpchelp[.]us
The attack vector likely originates via email, with threat actors gaining the trust of users before fooling them into entering a code (usually via a telephone conversation) that prompts the download.
A few weeks ago, GeekSquad customers fell victim to a scam featuring a fake website, that asked them to contact a phone number to cancel a fake subscription. Norton customers experienced the same basic scam in June,
It’s safe to assume that the version of WinDeskClient.Exe we analysed, and where it’s attempting to send information to, was an integral part of both scams.
Further investigation uncovered over 350 domains hosted among 42 IP addresses over the last month, impersonating not just Norton and GeekSquad, but big names such as Amazon and MacAfee (see IoC list at the bottom of this article).
The majority of these domains had three things in common:
- They were all registered on NameSilo;
- The used *.dnsowl.com nameservers;
- The were hosted on low-density IP addresses on AS-COLOCROSSING(30823)
Thankfully, this particular group of threat actors spent too much time playing fast and loose with legitimate websites, and failed to secure their own internal infrastructure, leading us to some interesting discoveries.
The front end operation
We’ve already blogged about open directories – they’re the ultimate quick win for anyone looking to secure entry into restricted file systems, without having to worry about phishing, social engineering or payloads.
Using the Silent Push Open Directory search, we quickly discovered an open index on 192.227.173.35, that contained a single compressed file – desk.zip.
The file contained a directory of website assets, including images, components, and, crucially, a database with username and password tables for accessing the control panel of the phishing page builder used to construct the malicious websites we’d already uncovered.

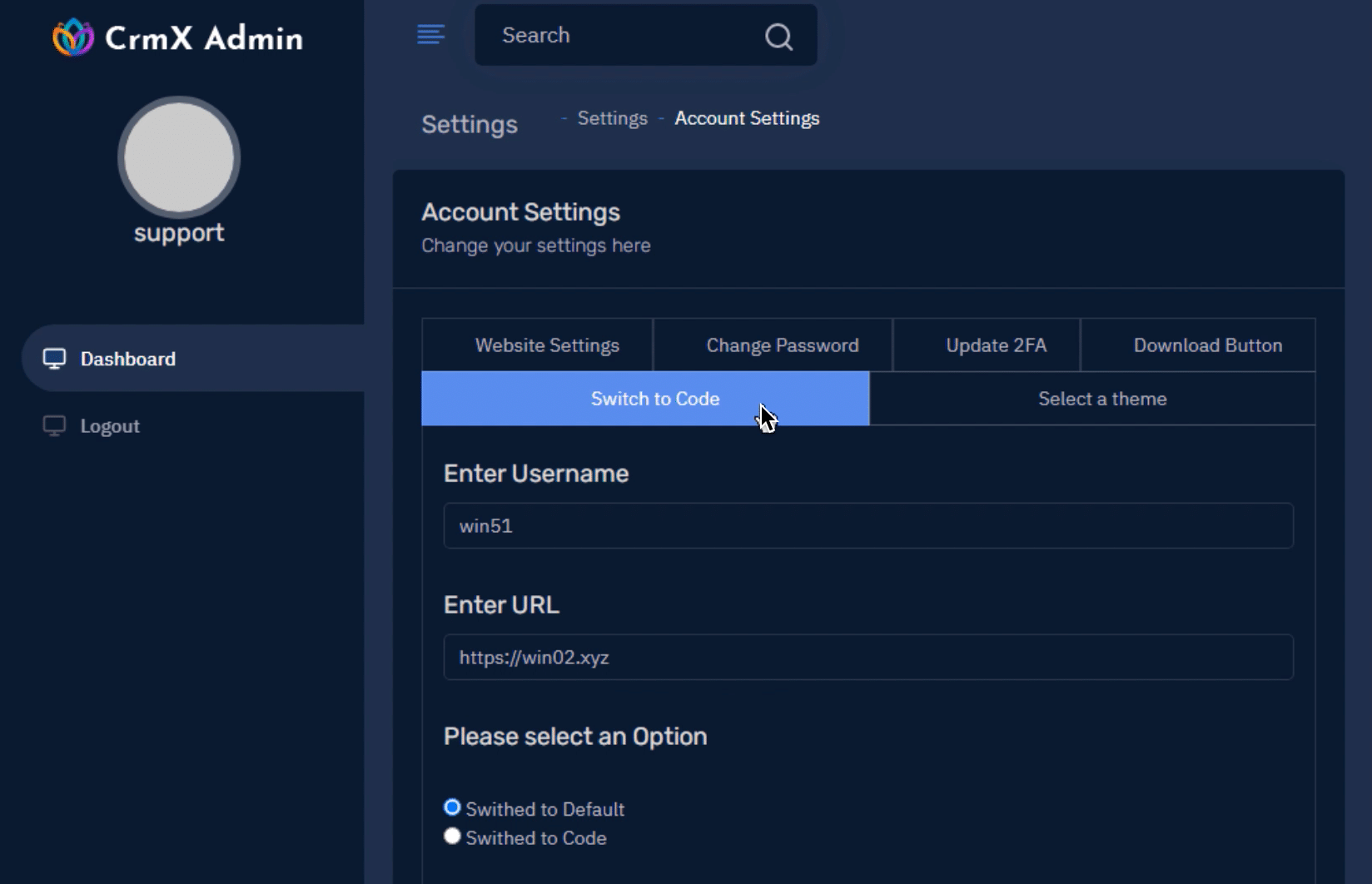
Unfortunately, we didn’t uncover anything further on the front end of the control panels, besides different variations of the phishing website and the domains used to download the malware (which we’d already uncovered), but nonetheless, it was an interesting insight into how threat actors put together their operation, and provided us with a significant amount of intel to pass on to our customers.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.
Indicators of Compromise
This list will not be updated after the initial blog post. For live tracking of malicious infrastructure subscribe to our enterprise service. Sign up for a trial.
Payload download domains
win01[.]xyz
win02[.]xyz
win03[.]xyz
win04[.]xyz
IP addresses
45.153.242[.]179
107.172.73[.]169
23.94.159[.]191
107.172.75[.]132
192.3.122[.]191
192.3.13[.]36
192.3.122[.]146
107.173.229[.]163
107.173.143[.]41
192.227.173[.]35
192.3.247[.]180
107.173.229[.]143
192.210.149[.]241
107.174.138[.]194
172.245.27[.]14
23.95.34[.]123
198.46.132[.]181
198.12.89[.]38
192.3.239[.]7
198.12.89[.]4
198.12.89[.]36
104.168.33[.]58
23.94.174[.]165
107.172.13[.]160
172.245.27[.]38
172.245.119[.]64
104.168.32[.]32
198.23.213[.]50
192.227.173[.]103
45.147.231[.]233
23.95.85[.]185
104.168.33[.]61
107.173.143[.]27
198.23.207[.]31
23.95.85[.]181
198.12.84[.]71
198.23.145[.]147
192.3.22[.]14
198.12.107[.]216
192.3.141[.]133
192.210.219[.]54
198.23.174[.]109
198.23.212[.]164
198.23.212[.]193
104.168.5[.]29
Phishing domains
firsto[.]top
firsto[.]cc
mslxt[.]xyz
ncareback[.]xyz
backup02[.]xyz
gkscare[.]com
geeksupportcare[.]com
xpchelps[.]us
support2norton[.]us
xpchelp[.]us
1001[.]to
247bestbuy[.]cc
247bestbuy[.]info
247gscare[.]info
247help[.]live
247support[.]cc
247support[.]live
247supportme[.]live
247supportme[.]us
9115[.]to
91158[.]to
9190[.]us
9199[.]us
9220[.]us
acare[.]cc
acareme[.]cc
acaresupport[.]us
ahelp[.]care
ahelps[.]us
amaznhelp[.]us
amazonserver[.]us
amjhelp[.]cc
amzcare[.]cc
amzcare[.]info
amzcare[.]uk
amzhelp[.]cc
amzhelp[.]live
amzhelp[.]uk
amzhelps[.]us
amzndesk[.]info
amzndesk[.]us
amznsupport[.]me
amzsupport[.]cc
amzsupport[.]top
amzsupports[.]us
appsdesk[.]us
asecures[.]top
ask4support[.]cc
ask4support[.]us
asupport[.]care
asupport[.]me
asupport[.]services
asupports[.]cc
asupports[.]info
asupports[.]live
asupports[.]us
azhelpdesk[.]us
bankingcare[.]us
bbbrefund[.]live
bbbrefund[.]us
bbhelp[.]live
bbhelp[.]us
bcare[.]cc
bcares[.]us
bestbuyhelp[.]us
bhelp[.]cc
bhelp[.]info
billingform[.]info
billingsdept[.]us
billingteam[.]cc
billingteam[.]info
billingteam[.]online
billingteams[.]us
bsupport[.]live
bsupports[.]live
bteam[.]live
buggu[.]info
cancel1[.]us
cancel2[.]us
cancel3[.]cc
cancel786[.]us
cancelforms[.]live
cancell[.]cc
cancell[.]us
cancellationsupport[.]live
cancellationsupport[.]us
cancellationsupprts[.]live
cancelnow[.]live
cancels[.]services
cancels[.]support
carehelp[.]us
cform[.]live
cform[.]online
chelp[.]care
chelp[.]cc
cscare[.]live
cscare[.]us
csupport[.]cc
cxsupport[.]cc
cxsupports[.]us
dcare[.]live
deskcare[.]live
deskcareme[.]cc
deskcares[.]cc
deskcares[.]online
deskhelps[.]cc
desksupports[.]cc
desksupports[.]live
desksupports[.]net
desksupports[.]us
dsupport[.]info
dsupport[.]live
esupport[.]cc
fcare[.]cc
fcare[.]live
fhelp[.]cc
fhelps[.]live
formlive[.]cc
formlive[.]info
forms911[.]us
formslive[.]cc
formslive[.]info
formslive[.]online
fsupport[.]cc
fsupport[.]info
fsupport[.]live
fsupport[.]online
fsupports[.]live
gcare[.]cc
gcare[.]live
gcares[.]us
gchelps[.]live
gchelps[.]us
geekcancel[.]us
geekcare[.]cc
geekhelp[.]us
geekhelps[.]us
geekrefund[.]live
geekrefund[.]online
geeksqad[.]cc
getforms[.]live
getforms[.]us
gethelpdesks[.]live
gethelpsupport[.]us
getset[.]cc
getset[.]info
ghelp[.]cc
ghelp[.]info
grefund[.]live
grefund[.]us
gscare[.]info
gscare[.]live
gscare[.]us
gsrefund[.]us
gssquads[.]us
gsupport[.]live
help01[.]us
help4support[.]live
helpcares[.]support
helpcares[.]us
helpcenter[.]top
helpcenters[.]cc
helpcenters[.]live
helpdeskme[.]live
helpdeskme[.]us
helpdesksupport[.]live
helpline247[.]cc
helpline247[.]live
helpline247[.]us
helplive[.]cc
helplive[.]us
helplives[.]cc
helplives[.]us
helpme159[.]live
helpnortn[.]us
helpnorton[.]us
helpnsupport[.]us
helpsupports[.]live
helpsupports[.]us
helptechme[.]info
helptechme[.]live
helptechme[.]us
hservice[.]cc
hsupport[.]live
hsupports[.]live
ihelp[.]care
isupport[.]info
isupport247[.]cc
isupport247[.]us
isupports[.]live
itcares[.]info
itcares[.]live
itcares[.]us
itdesk[.]cc
itdesks[.]cc
itdesks[.]live
itdesks[.]online
itdesks[.]us
jcare[.]us
jsupport[.]us
khelp[.]live
ksupport[.]live
liveforms[.]us
login08[.]info
login08[.]top
mcare[.]live
mcfee247[.]cc
mcfee247[.]live
mcfhelp[.]us
mcfsupport[.]cc
mcfsupport[.]cloud
mcfsupport[.]live
mcfsupport[.]online
mcfsupport[.]us
mhelp[.]cc
mnsupport[.]info
mnsupports[.]live
mnsupports[.]us
mscare[.]me
mscare[.]online
mscares[.]cc
mscares[.]info
mscares[.]live
mscares[.]us
mshelp[.]cc
mshelp[.]me
mshelp[.]us
mshelpcare[.]cc
mshelpcare[.]info
mshelpcare[.]live
mshelpcare[.]us
mshelps[.]info
mshelps[.]live
mshelps[.]us
msjkp[.]top
msjkp[.]xyz
mskf[.]life
msn365[.]live
mssupport[.]cc
mssupports[.]live
mssupports[.]us
mstool[.]cc
mstool[.]info
mstool[.]live
msupport[.]cc
msupport[.]live
msupport[.]tech
msupports[.]info
msupports[.]live
msupports[.]online
msupports[.]us
myhelpcare[.]top
myhelpcares[.]info
myhelpcares[.]live
myhelpcares[.]us
myhelpdesk[.]cc
myhelpdeskme[.]us
myrefunds[.]live
mywebsecure[.]cc
mywebsecure[.]live
mywebsecure[.]us
ncares[.]online
nhelp[.]cc
nhelpcare[.]cc
nhelpcare[.]us
nllcancel[.]us
nortan[.]online
nortan360[.]us
nortancxs[.]us
nortanpro360[.]us
nortn[.]us
norton247[.]us
nortonpro[.]live
nortonpro[.]us
nrtsupport[.]online
nrtsupport[.]us
nsupport[.]cc
nsupport360[.]cc
nsupport360[.]us
nsupportme[.]us
ntcare[.]cc
ntcare[.]info
ntcare[.]live
ntcare[.]us
ntcares[.]live
onlinesupport[.]top
osupport[.]us
paycare[.]cc
paypalcare[.]cc
paypalcare[.]us
paypalhelp[.]cc
paypalhelp[.]live
paypalsec[.]us
paysupports[.]cc
paysupports[.]info
pcare[.]live
pchelps[.]cc
pchelps[.]live
pchelps[.]vip
pcservers[.]us
pcsupport[.]cc
phelp[.]info
primesupports[.]live
prsupport[.]cc
prsupport[.]live
pserver[.]cc
pserver[.]live
pserver[.]us
psupport[.]live
qhelp[.]cc
qhelp[.]live
qhelps[.]info
qhelps[.]live
qhelps[.]us
qsupport[.]live
refundassists[.]us
refundform[.]info
refundforms[.]us
refundhelp[.]us
refundscare[.]us
refundsnow[.]us
refundteam[.]us
rfundcare[.]cc
rfundcare[.]live
rfundcare[.]us
rhelp[.]live
securesupport[.]live
service247[.]us
support247[.]live
support99[.]cc
support99[.]live
support99[.]us
supportcancel[.]info
supportcancel[.]live
supportcancels[.]us
supportcare[.]cc
supportcares[.]cc
supportcares[.]live
supportcares[.]us
supportclients[.]cc
supportclients[.]top
supportcx[.]info
supportdesks[.]live
supportdesks[.]us
supporthelp[.]info
supportlive[.]cc
supportme11[.]live
supportme247[.]live
supportme247[.]us
supportpay[.]live
supports[.]win
supports[.]work
supports247[.]us
supports24x7[.]us
supportshelp[.]cc
supportslive[.]us
supportsx[.]info
supportsx[.]live
supportteams[.]live
supportus[.]us
supportusa[.]cc
suvfix[.]cc
suvfix[.]info
techamerica[.]live
techcare[.]live
techcares[.]cc
techcares[.]live
techhelps[.]live
techhelps[.]support
techhelps[.]win
techhelpsme[.]cc
techhelpsme[.]live
techhelpsme[.]online
techhelpsme[.]us
test01[.]cloud
testapp101[.]xyz
tservers[.]live
tservers[.]top
tsupport[.]cc
uscybersquad[.]live
vfix[.]info
vsupport[.]cc
waso[.]cc
waso[.]info
windesk[.]live
windowsupport[.]cc
windowsupport[.]info
winsupport[.]live
wnsupport[.]us
wservice[.]live
wsupport[.]cc
wsupport[.]us
ysupport[.]us
zsupport[.]cc
zsupport[.]info
zsupport[.]live


