Silent Push Context Similarity search: a CTI "easy button" that reveals matching infrastructure from a standing start

Security teams often begin their investigations from a standing start, with little to no intel on a suspect indicator.
A domain has appeared in your organization’s detection mechanisms, and warrants an investigation. Where do you go from here?
The Silent Push Context Similarity search displays a list of malicious domains that have been set up and managed in a similar fashion to an unknown target domain, at the click of a button, with zero prior analysis required.
Why is it useful?
The speed and simplicity of a Context Similarity search allows security teams – where resources are often stretched – to make fast, efficient value judgments on the likelihood of a domain being involved in malicious activity, what that activity is, and where to look next.
Context Similarity removes the burden of performing extended DNS and TTP analysis on an unknown indicator, and offers Community and Enterprise users an “easy button” for generating meaningful insights on a piece of infrastructure they’ve never encountered before, and have zero prior intelligence on.
How does it work?
The Context Similarity tool harnesses the power of the Silent Push collection and aggregation engine and provides what we call “directionality” to an initial threat investigation – an instructive process that shows teams where to look next, based on a single input point (i.e. a suspect domain).
Context Similarity works by applying over 50 characteristics to every malicious domain we encounter in a Silent Push IOFA Feed, and uses those characteristics to ascertain how similar two domains are to each other, in their underlying management and deployment.
Characteristics include (but aren’t limited to) the use of shared infrastructure such as nameservers and ASNs, how certificates are managed, reputation scores, and the presence of open directories.
We’re able to do this because we source, own and control all of our own DNS and web content data. We don’t rely on any third-party collection, storage or aggregation methods, which allows us to create self-contained searchable datasets that are designed to fulfil a specific use case, such as providing context to an unknown observable.
Generating a set of results
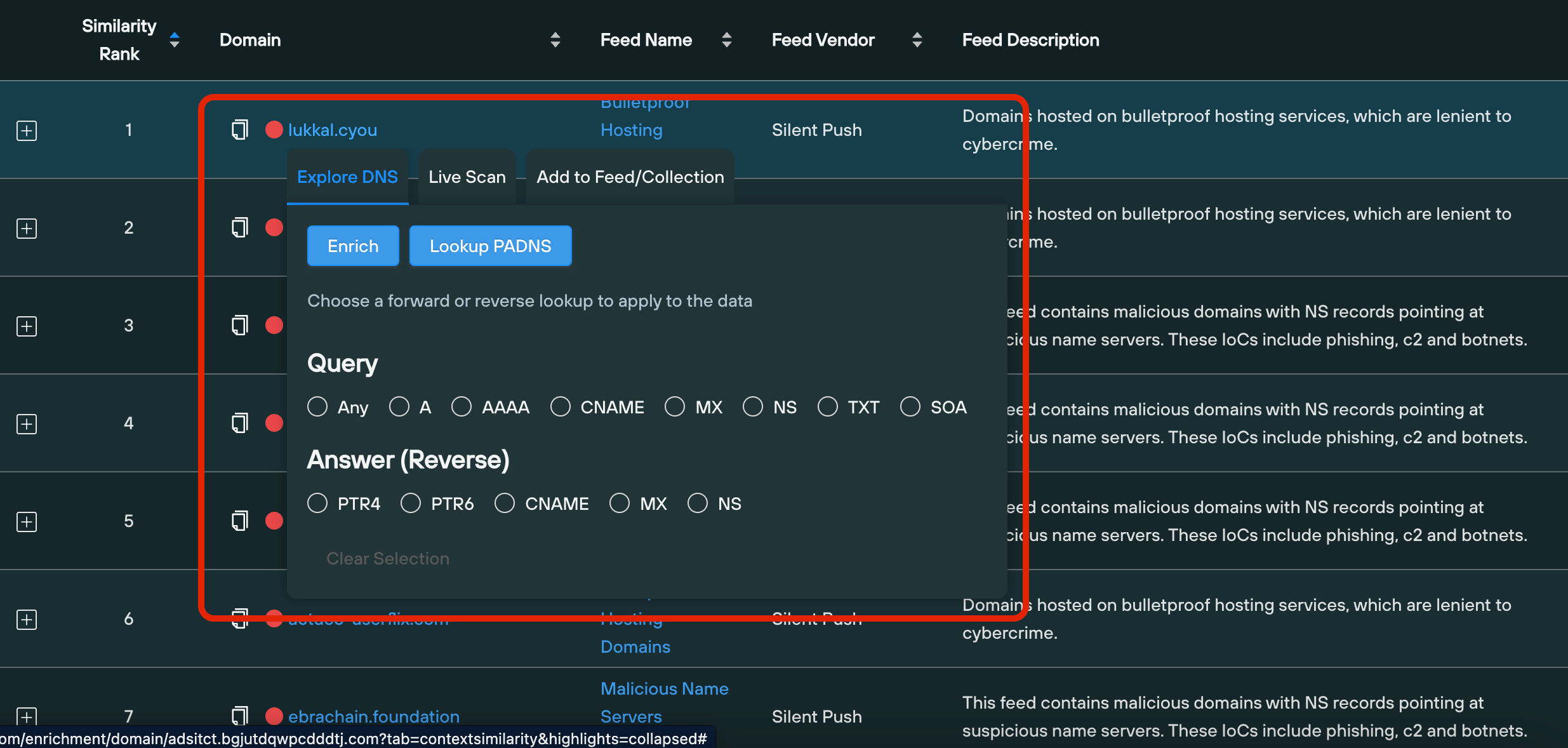
Context Similarity is accessed via a tab on the Total View screen.
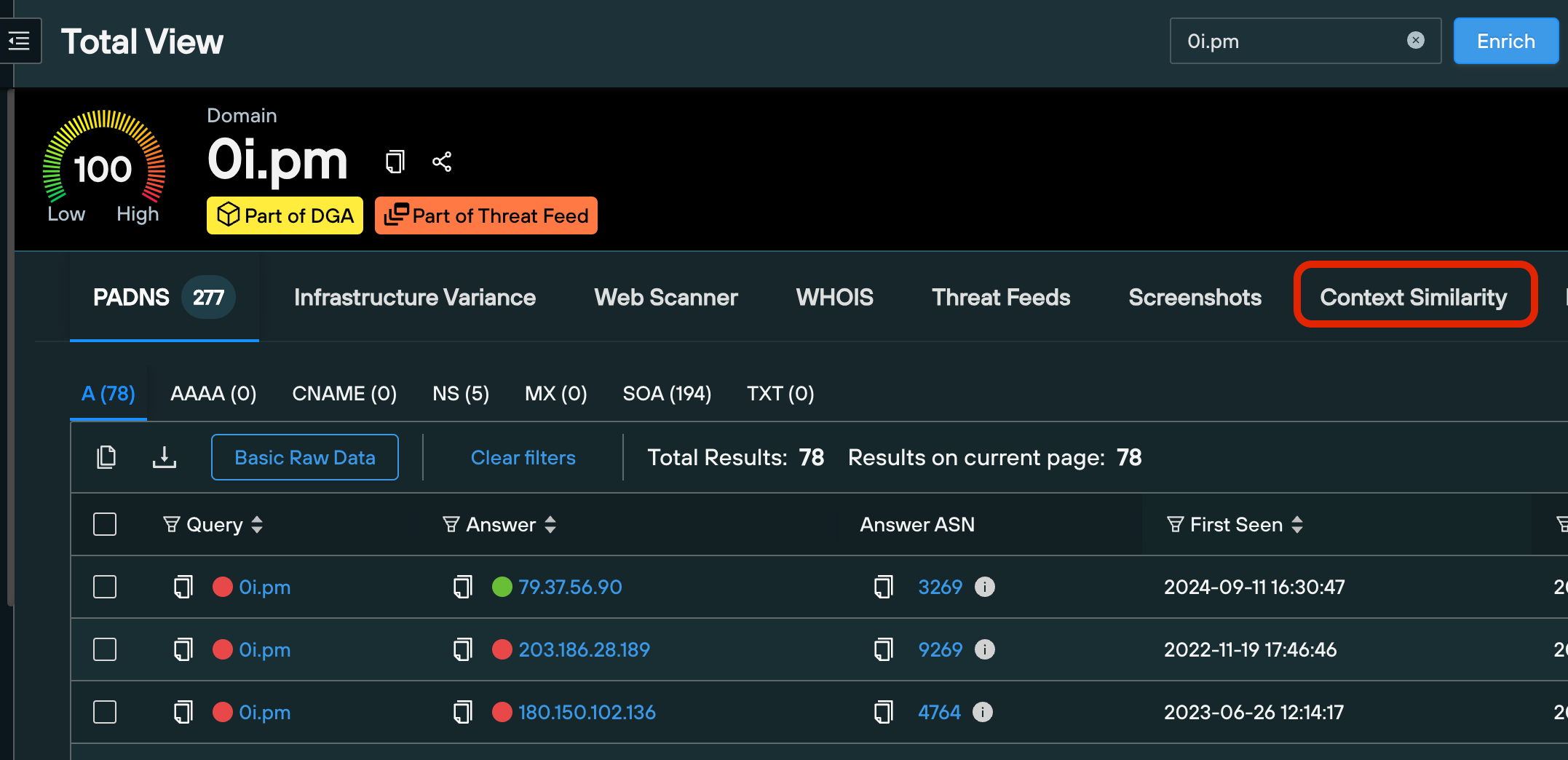
Total View combines 10 Community and Enterprise tools into one screen, at the click of a button, without the need to perform additional DNS, infrastructure, feed-based or web content pivots.
To generate a set of Context Similarity results, simply enter a suspect domain into the main search bar, click Enrich to bring up the Total View screen, and click the Context Similarity tab.
Example search
Context Similarity takes the inputted domain, and displays known malicious domains within Silent Push IOFA Feeds that have been setup and managed (“Context”) in a similar fashion (“Similarity”).
Here’s a Context Similarity search run on the suspect domain adsitct.bgjutdqwpcdddtj[.]com:
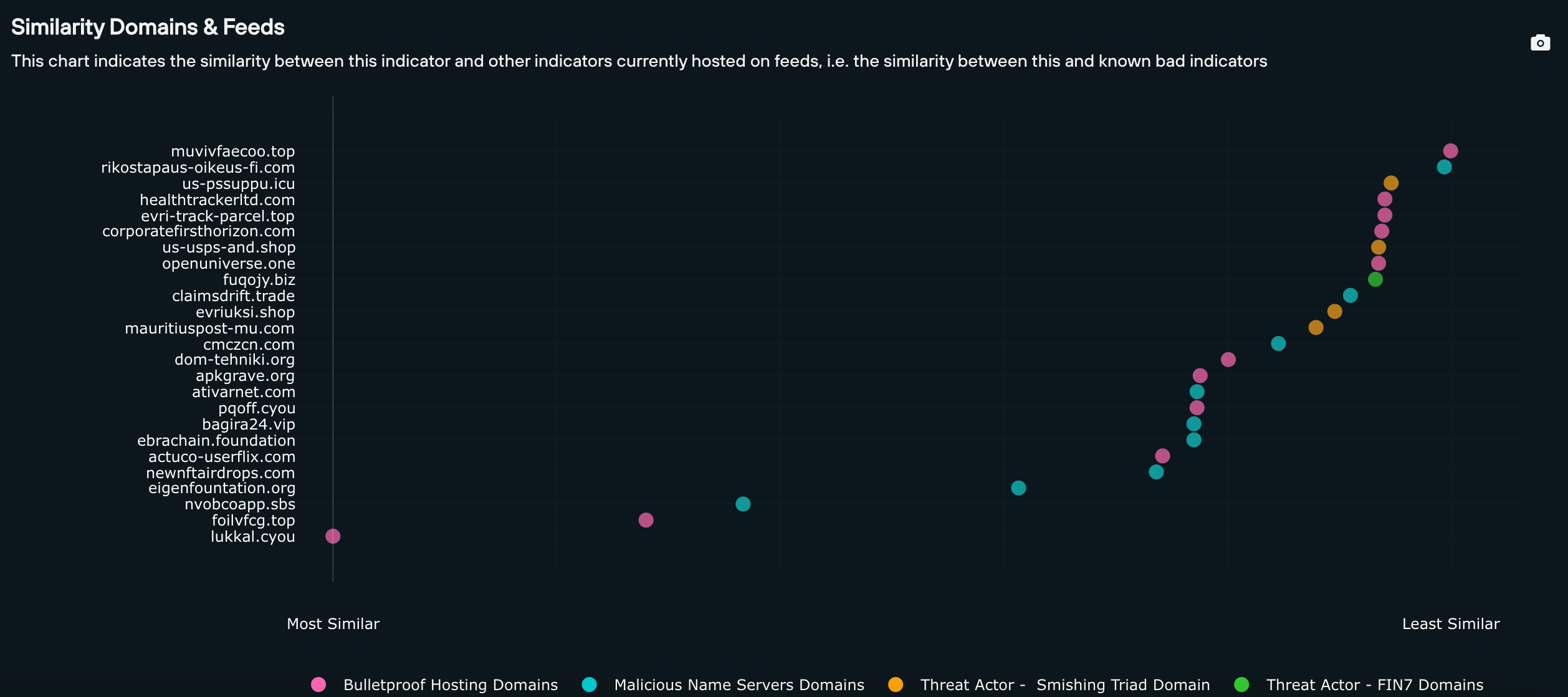
The coloured dots indicate how similar the target domain is to other malicious domains, working from left to right in the order of most similar to least similar.
Every domain returned is featured on a Silent Push IOFA Feed. Different colours represent different IOFA Feeds. Hovering over the dots will provide the feed that the returned domain is contained within.
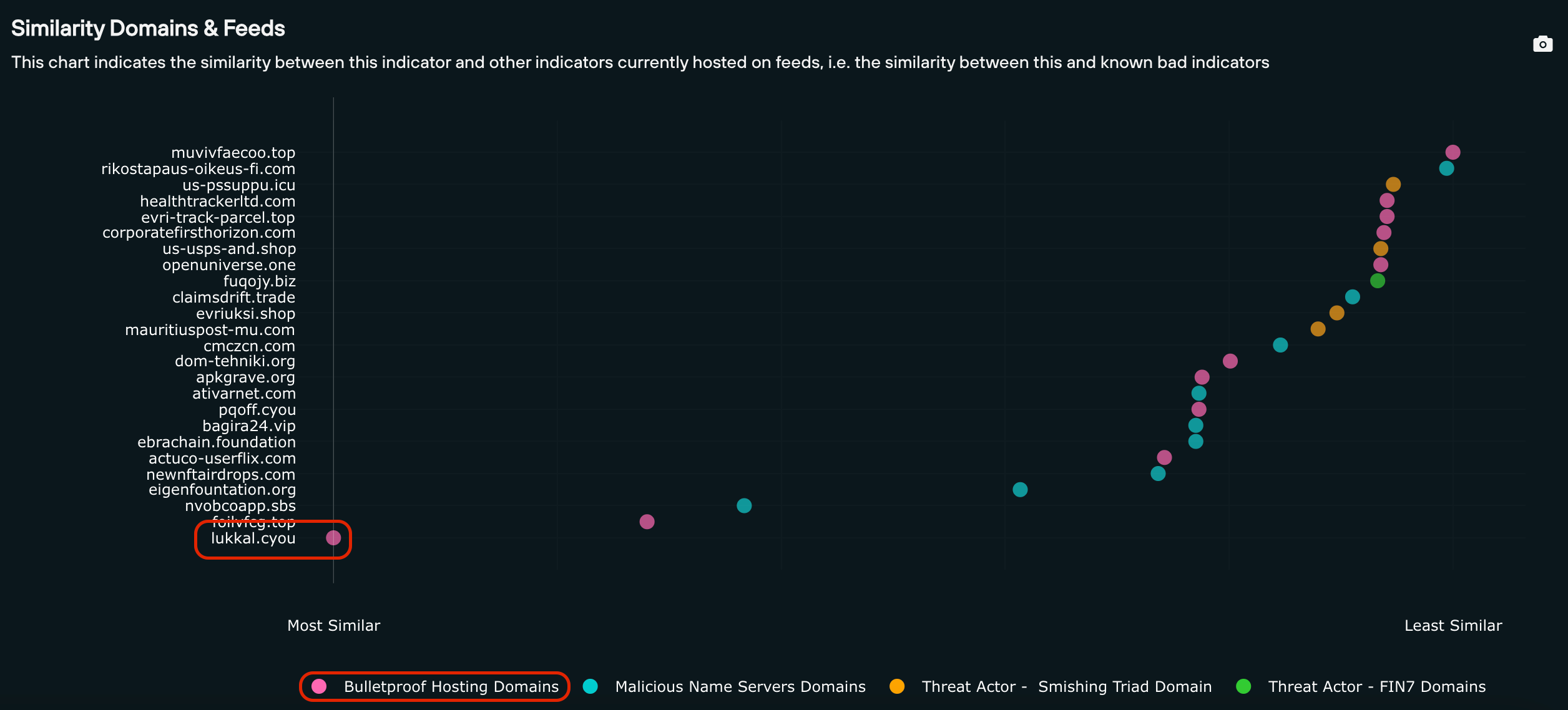
In the below example, the domain lukkal[.]cyou – appearing as the first domain on the returned list, with a dot on the extreme left, and contained within the IOFA Feed “Bulletproof Hosting Feeds” – is deemed to be the most similar domain to the target domain adsitct.bgjutdqwpcdddtj[.]com.
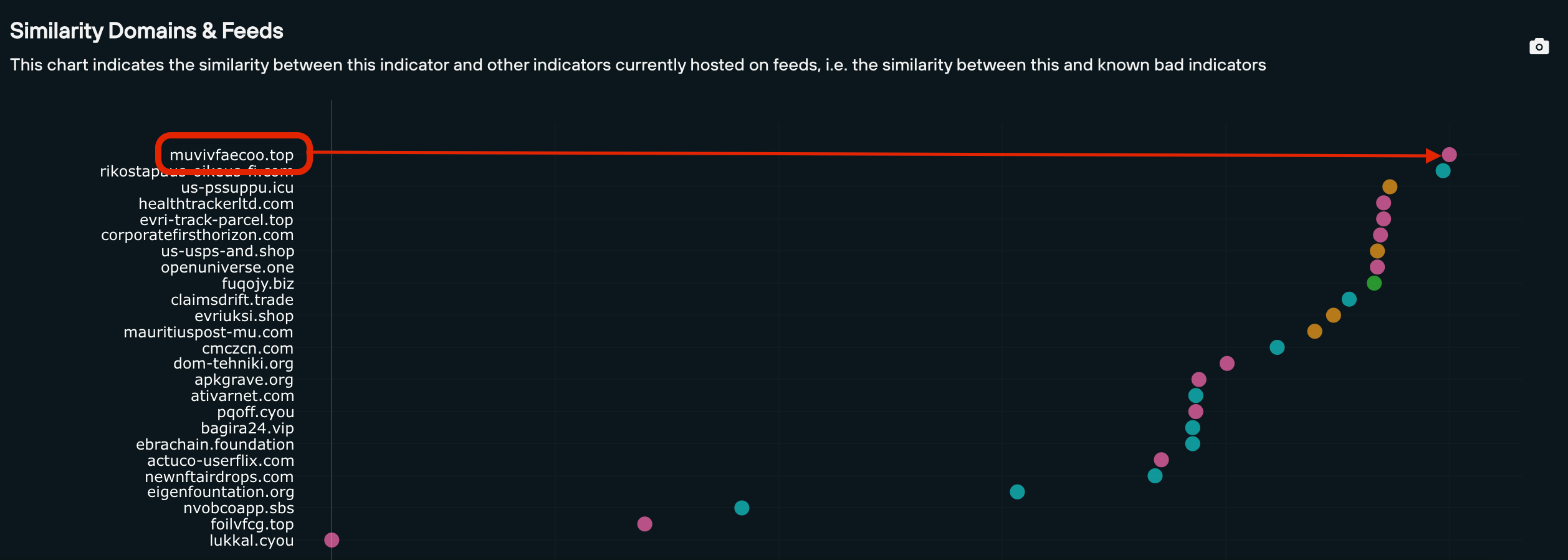
The domain muvisfaeco[.]top is deemed to be the least similar domain to the target domain (whilst still warranting inclusion), with a dot on the extreme right:
Working with Context Similarity results
The Silent Push console is designed to provide users with a centralized management space that can be used to gather the maximum amount of intelligence on a given indicator, without the need to navigate off the page and perform endless additional queries before receiving a set of useful results.
Each domain returned can be expanded to show the list of characteristics used to calculate similarity, so that users can make value judgements based on other sources of intel available to them, with differential data clearly displayed in red and green.
Once you’ve generated a set of results, a table populates below the similarity chart containing all the displayed indicators, ordered by similarity rank, from which you can one-click pivot across DNS records, or perform a Live Scan of the domain that returns a snapshot of realtime infrastructure.
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform used by researchers, defenders and threat hunters, featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Context Similarity.
Sign-up for a free account here.


