Russian Intelligence Service-backed Campaigns Impersonate the CIA to Target Ukraine Sympathizers, Russian Citizens and Informants

Key Findings
- Silent Push Threat Analysts have discovered a phishing campaign using website lures to gather information against Russian individuals sympathetic to defending Ukraine. Anti-war actions are illegal in the Russian Federation, and participating citizens are regularly arrested and charged.
- Our team strongly believes this campaign is likely the work of either Russian Intelligence Services or a threat actor with similarly aligned motives.
- We found the campaign consists of four major phishing clusters, impersonating the CIA, the Russian Volunteer Corps, Legion Liberty, and Hochuzhit—“I Want to Live,” an appeals hotline for Russian service members in Ukraine operated by the Main Directorate of Intelligence of Ukraine (also known as the Defense Intelligence of Ukraine).
- The official Liberty of Russia Legion made an X (formerly known as Twitter) post on March 14, 2024: “We remind you that the only official telegram channel of the Legion is listed on our website: hxxps://legionliberty[.]army Do not be fooled by fakes. Do not fall into the traps of the security forces of the Putin regime!”
- All campaign clusters appear to share a common objective: collecting personal information from site visitors/victims for the benefit of the threat actor.
Table of Contents
- Key Findings
- Executive Summary
- Russian Intelligence Agency Phishing Tactics, Techniques, and Procedures
- Background on the Russian Intelligence Agency Phishing Campaign
- Initial Intelligence Gathering
- Cluster 1 – Russian Volunteer Corps
- Finding Similar Domains
- Searching for Additional Domains
- Cluster 2 – Legion Liberty
- Pivot: Further Wildcarding
- Cluster 3 – The “CIA”
- Cluster 4 – Hochuzhit – “I Want to Live”
- Latest Adversaries
- Mitigation
- Register for Community Edition
- Sample Indicator of Future Attack (IOFA) List
Executive Summary
The rise in cyberattacks during ongoing conflicts of war has become a significant concern in recent years, especially as cyber capabilities are increasingly being leveraged as a form of modern warfare. Motivations behind these cyberattacks vary, from disrupting an opponent’s operations and causing widespread panic to gathering intelligence and creating strategic advantages.
Silent Push Threat Researchers have identified phishing pages on a known bulletproof hosting provider, Nybula LLC, ASN 401116, but a financial motive has not yet been found for the threat actor group. The phishing pages appear to impersonate the official websites of multiple organizations, including the U.S. Central Intelligence Agency (CIA), the Russian Volunteer Corps (RVC), Legion Liberty, and the appeals hotline group Hochuzhit.
An anti-Putin group, the RVC is a Ukrainian Army unit consisting of Russian citizens (some living in Ukraine who left Russia and joined after the war had started). Participation in such anti-war actions is considered illegal in the Russian Federation, and citizens who get involved or volunteer face arrest.
All the campaigns our threat analysts observed have had similar traits and shared a common objective: collecting personal information from site-visiting victims. Based on this and a number of factors we’ll cover in this blog, our team strongly believes these phishing honeypots are likely the work of either Russian Intelligence Services or a threat actor aligned to Russian interests.
Russian Intelligence Agency Phishing Tactics, Techniques, and Procedures
Russian Intelligence Agency Phishing TTPs
We observed the following TTPs that are common across this threat actor’s activity:
- Phishing pages impersonating the Russian Volunteer Corps (rusvolcorps[.]com) and the official websites of the Legion Liberty, the CIA, and Hochuzhit—“I Want to Live,” an appeals hotline for Russian service members in Ukraine.
- Reconnaissance and resource development of research targeting organizations and individuals involved in protesting the war that poses a threat against the Russian government.
- Acquisition of web services and domains to use for phishing.
- Phishing pages to gather personal information from victims using website forms or Google Forms that the threat actors actually managed.
Background on the Russian Intelligence Agency Phishing Campaign
Silent Push Threat Researchers discovered phishing pages on a bulletproof hosting provider, Nybula LLC (ASN 401116), that appear to impersonate rusvolcorps[.]com. Following the initial pivot on 81.161.238[.]212 that detected a phishing page, we determined there were several clusters of interconnected campaigns. Listed below is one example domain for each of the four phishing clusters that Silent Push Threat Analysts found:
- rusvolcorps[.]net
- legiohliberty[.]army
- ciagov[.]icu
- hochuzhitlife[.]com
The campaigns were impersonating the corresponding legitimate sites of four official groups:
- rusvolcorps[.]com: The Russian Volunteer Corps (RVC)
- legionliberty[.]army: The Legion Liberty (Freedom of the Russian Legion)
- cia[.]gov: The U.S. Central Intelligence Agency (CIA)
- hochuzhit[.]com: An appeals hotline for Russian service members in Ukraine, operated by the Defense Intelligence of Ukraine.
All four campaigns were interconnected through various infrastructure management and fingerprinting methods. The sites that were online provided our threat analysts with key information, enabling us to observe the threat actor’s motives behind the various campaigns. Fingerprints based on technical similarity tied the campaigns together, consisting of correlations between the WHOIS organization name “Semen Gerda” and other metadata IP addresses, registration via the NiceNIC registrar, similarities in content, and external sources.
We determined the phishing pages were designed to lure potential victims into submitting their personal information, ultimately leading to a breach of their personal data. Below is a pair of timeline infographics that further illustrate the expanding scope and persistent evolution of this campaign:
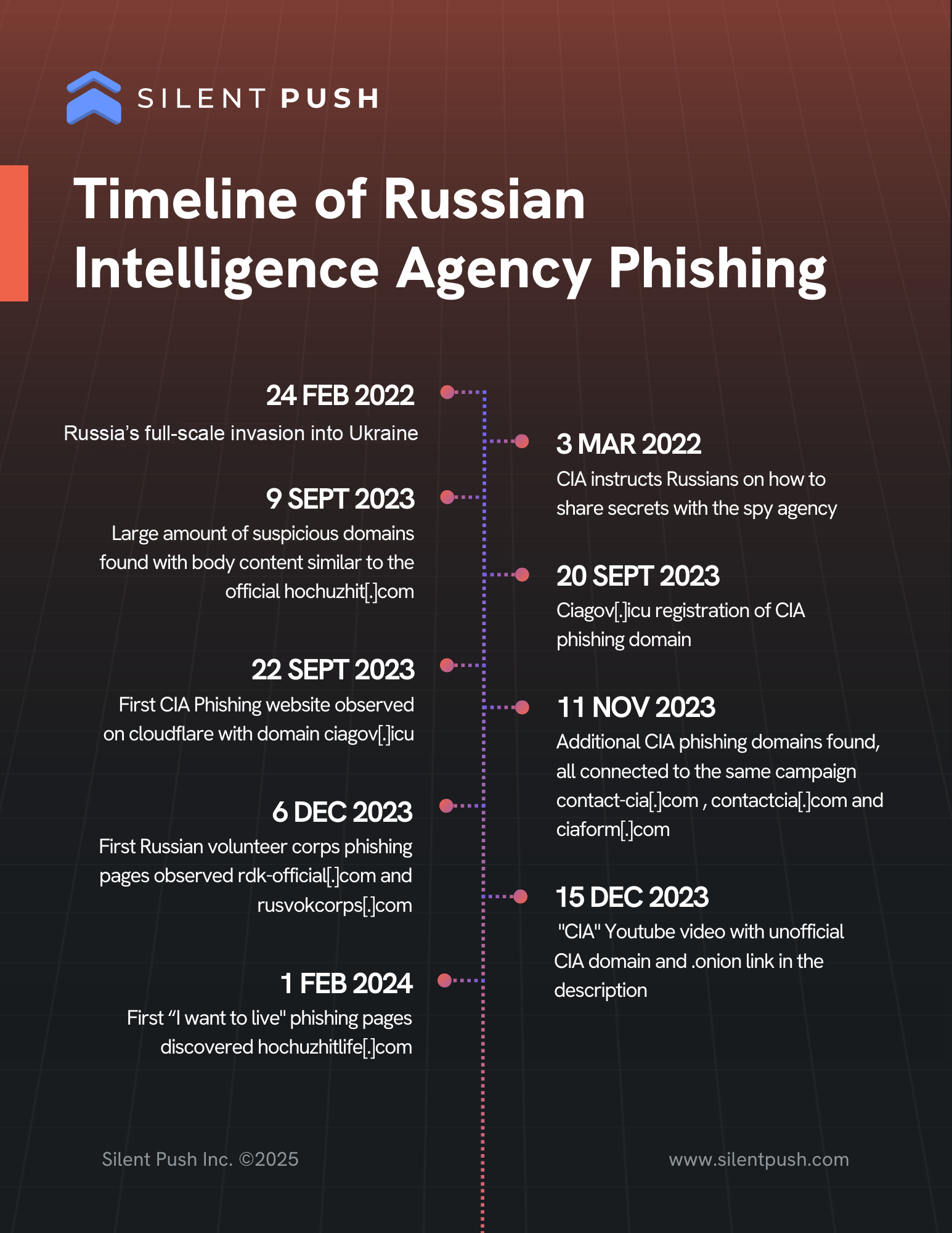
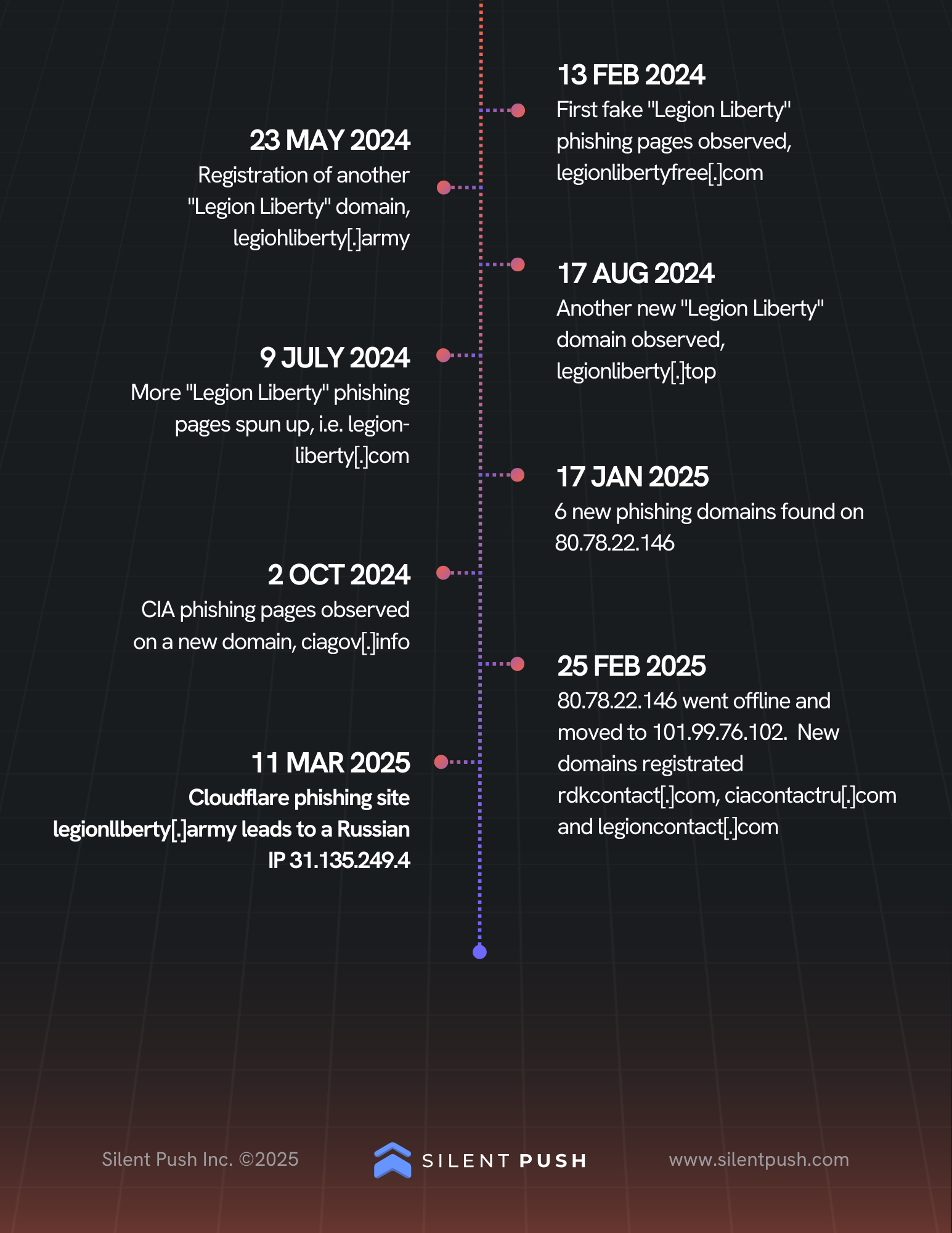
Associated phishing pages on rusvolcorps[.]net have been luring victims sympathetic to defending Ukraine into providing personal information to the threat actors via the website, using tactics such as responding to emails or filling out Google Forms.
In brief, the primary supporting evidence we can share here is:
- Persistent, long-term targeting of Ukrainian entities, pro-Ukrainian Russians, and Russian-speaking informants
- Previous reporting tying Federal Security Service of the Russian Federation (FSB) efforts to conduct the same type of operations, with similar patterns to those observed here
- Sustained impersonation of the U.S Central Intelligence Agency (CIA) in Russian, with no apparent financial motive behind it
Initial Intelligence Gathering
Cluster 1 – Russian Volunteer Corps
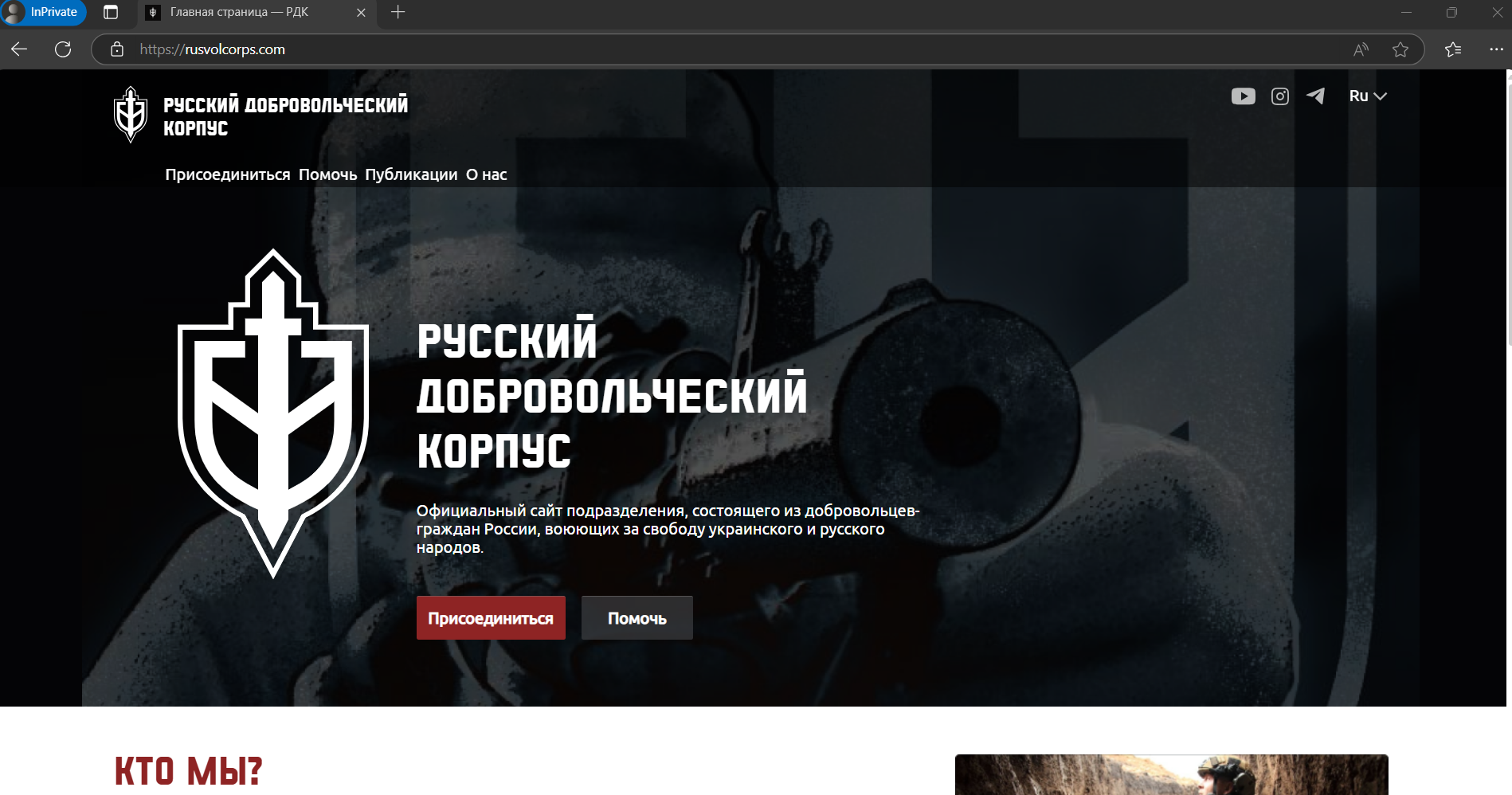
Examining the potential phishing page on rusvolcorps[.]net, our researchers found historical information about Russian Volunteer Corps phishing pages.
Legitimate site: rusvolcorps[.]com
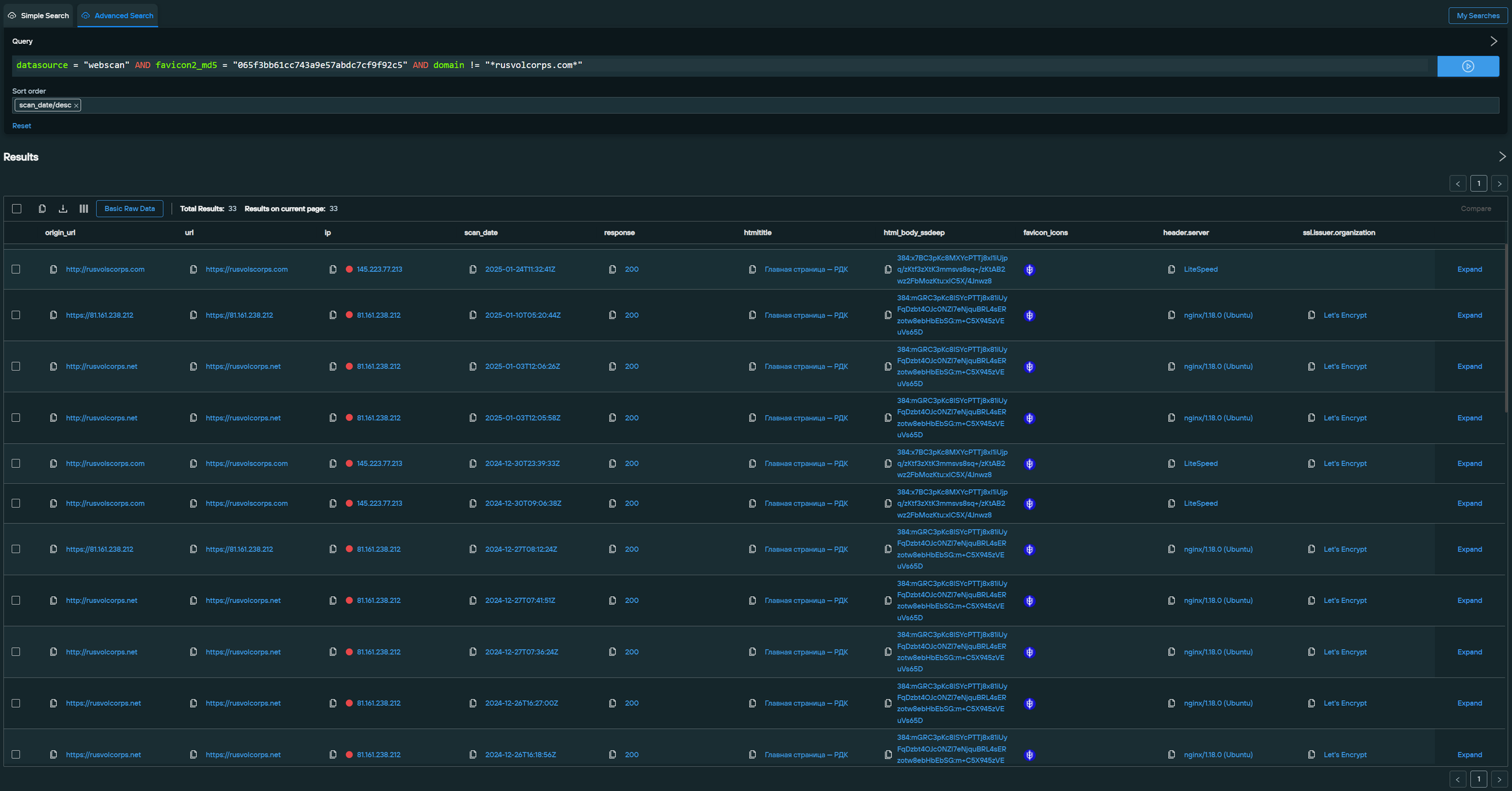
We performed a Web Scanner search on the legitimate Russian Volunteer Corps site favicon, filtering the domain to be any except rusvolcorps[.]com. By conducting a search on the legitimate RVC favicon and excluding the legitimate domain, we were able to easily generate an initial pool of suspicious domains.
- datasource = “webscan” AND favicon2_md5 = “065f3bb61cc743a9e57abdc7cf9f92c5” AND domain != “*Главная страница — РДК *”
On the phishing page rusvolcorps[.]net, potential victims are lured to click a red button requesting them to “Join Here,” which then takes them to a new phishing page:

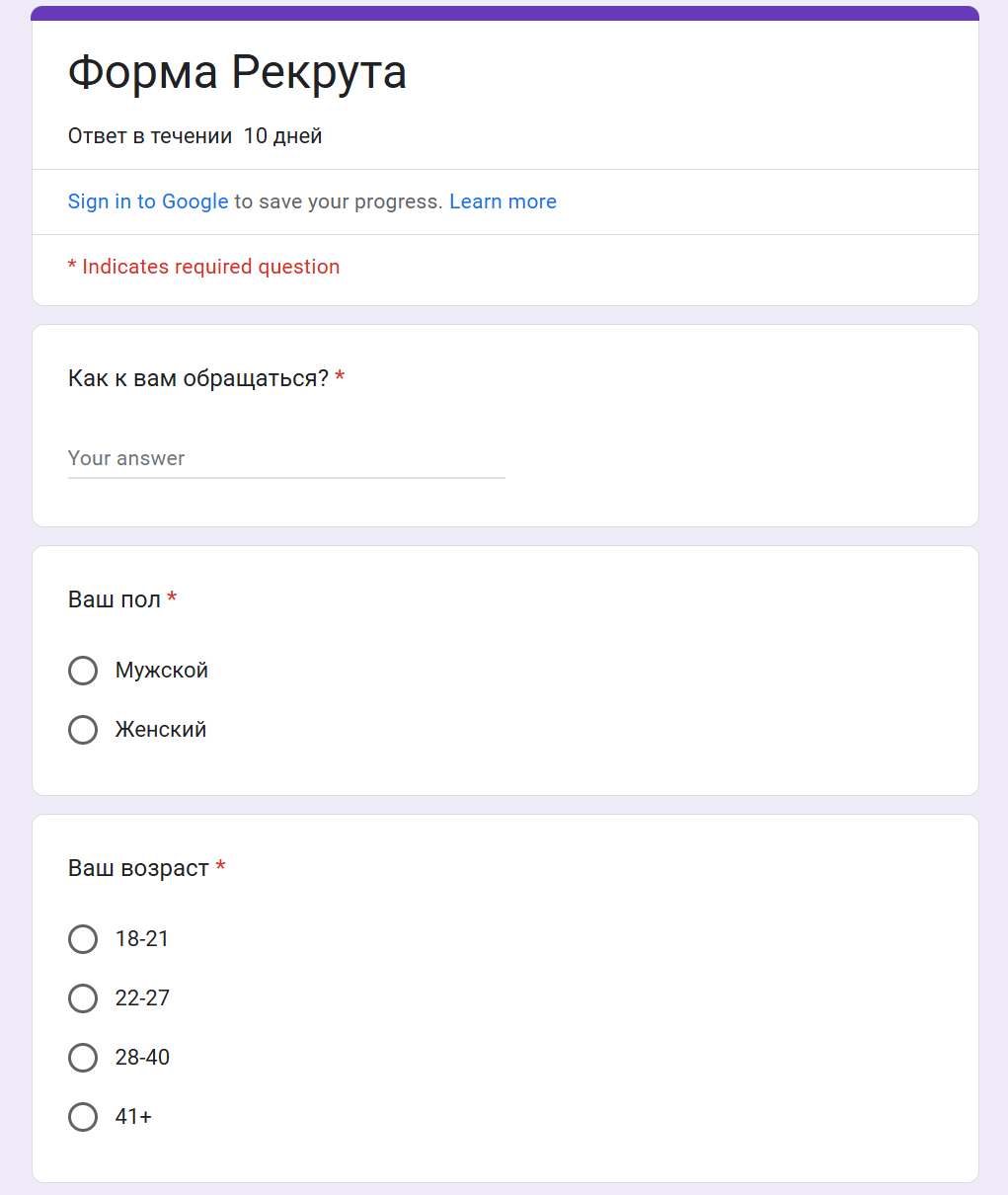
Visitors to the Google Form were then instructed to provide their personal information:
- How should I address you?
- Your gender
- Your age
- Country of Location
- Citizenship
- Legality of stay in the country
- Experience in the Armed Forces
- Your political views
- Your motivation for joining our division
- Tell us about yourself (Physical fitness, state of health, do you consider yourself psychologically stable?)
- Do you have bad habits?
- Contact for feedback – your Telegram via @
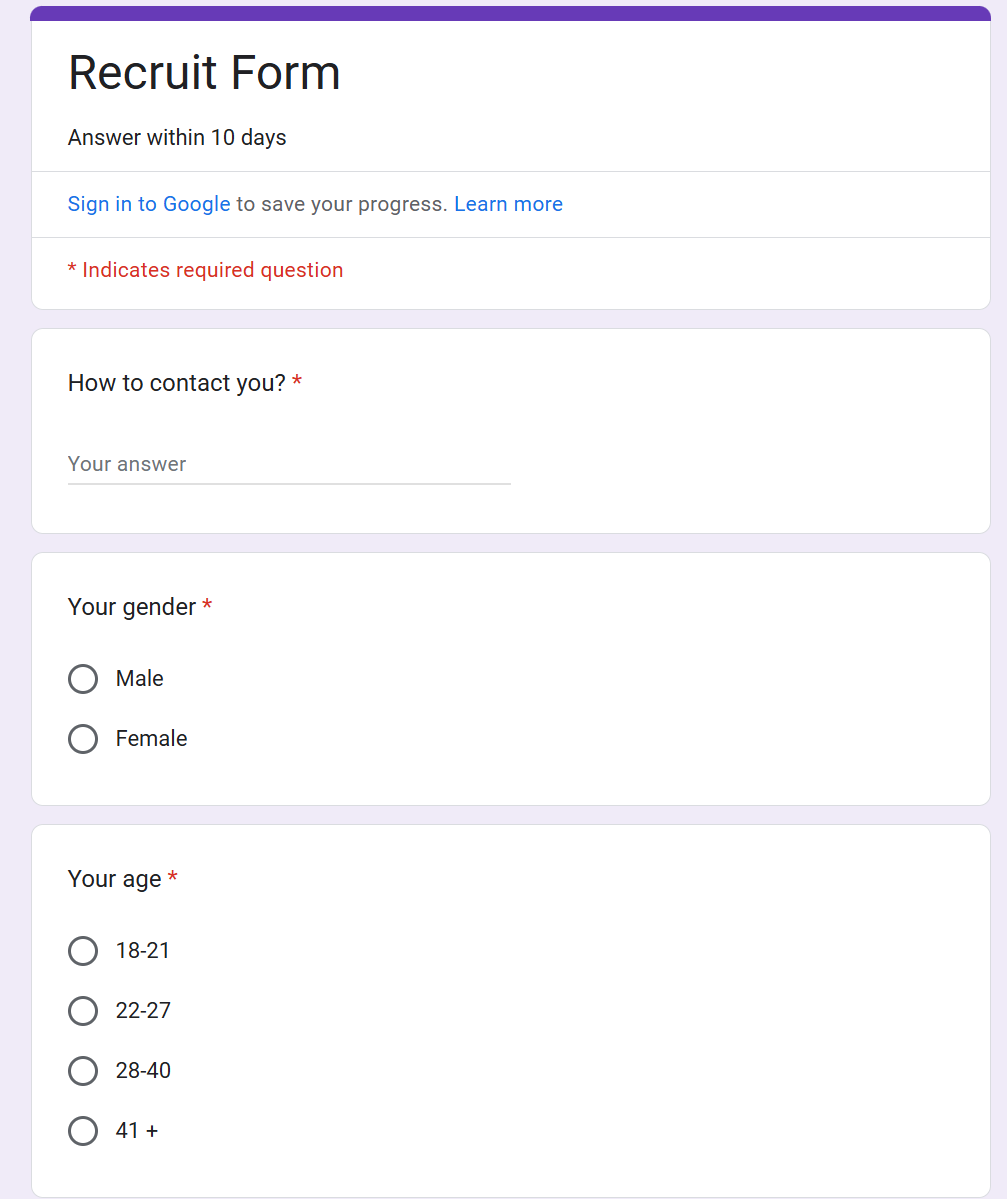
It’s important to note that the legitimate Legion of Russian website legionliberty[.]army also uses Google Forms for communicating with potential volunteers. Their form is also prominently promoted on their website:
Analyzing the newly retrieved domains and IPs led our threat team to a Twitter/X post in Russian on August 14, 2024, where Russian opposition activist and security researcher Artem Tamoian tweeted (translated into English):
“The story of how Yandex directly helps the FSB imprison Russians for decades. To begin with, look carefully at the Google vs. Yandex search results for the same query about the Freedom of Russia legion:”
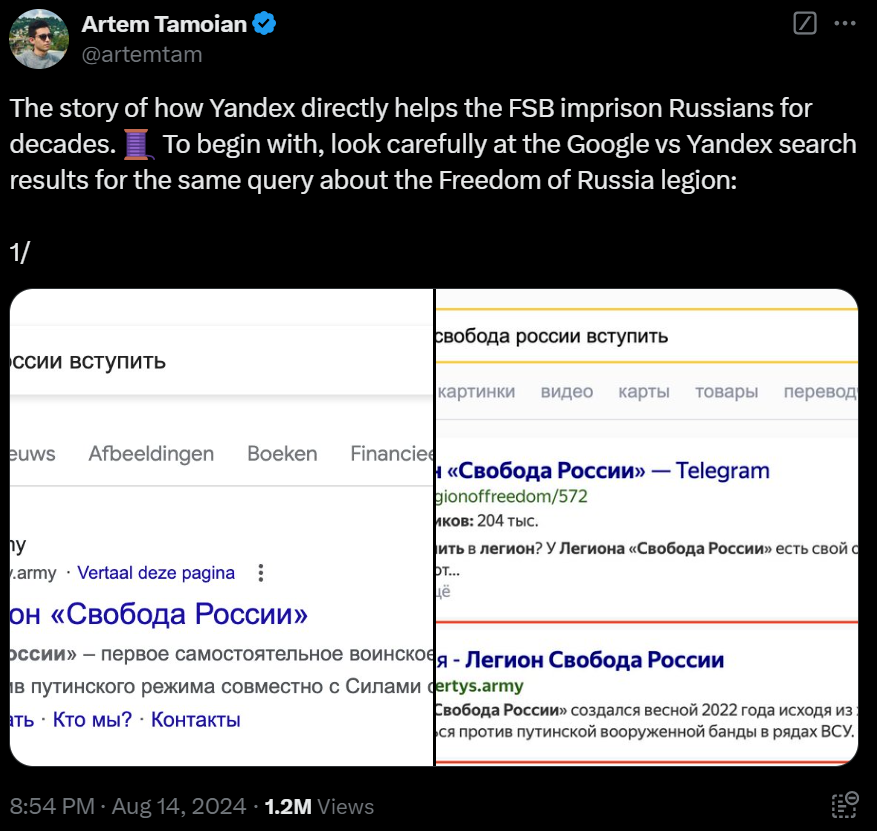
The thread from Tamoian continues with details about suspicious domains and motives:
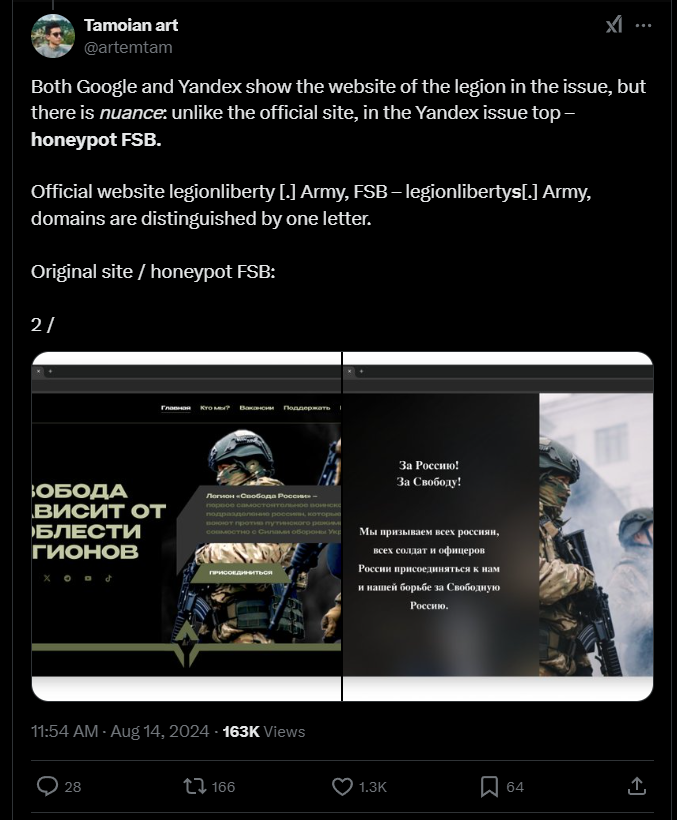
Tamoian had also noticed similar behavior from an additional pool of domains:
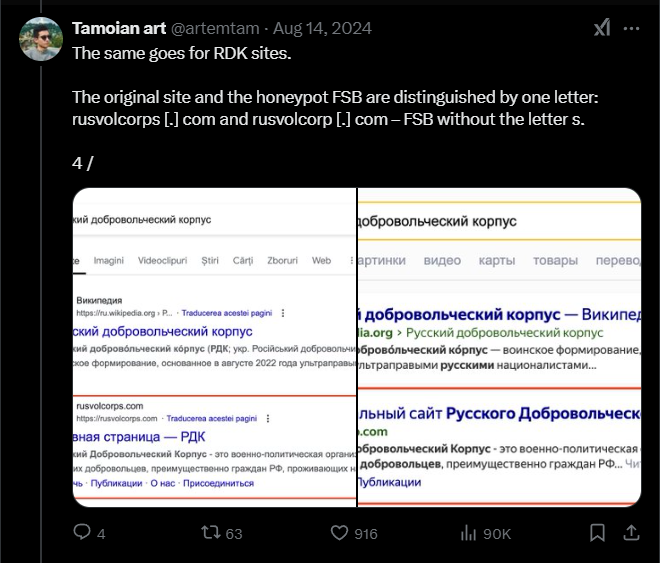
Finding Similar Domains
Based on what we observed on the malicious ruvolcorps[.]com phishing domain, our team then looked to see if we could find more phishing domains with similar names:
Our search yielded several suspicious domains which stood out:
- rusvolcorps[.]icu
- rusvolcorps[.]net
- rusvokcorps[.]com
- rusvokcorps[.]cc
Searching for Additional Domains
Looking for additional fingerprints, we found several other domains that aligned with the original results. Combing through the results yielded two new suspicious domains:
- rdk[.]social
- ruvolcor[.]com
Alongside the two newly identified domains, by clicking on “Expand” in the results, in this case for the “rusvokcorps[.]cc” domain, our team was able to find two Telegram channels embedded in the HTML body. Specifically, in our “body_analysis.telegram” field: “t[.]me/russvolcorps” and “t[.]me/rdkfaq_bot”.
Both appear to be official Telegram accounts associated with the Russian Volunteer Corps. However, threat actors often lure victims to fake Telegram accounts to collect information or carry out scams. In this instance, Silent Push Threat Analysts believe the threat actors were keeping the legitimate Telegram accounts from the official site to make their phishing pages appear safe and thus evade suspicion.
Cluster 2 – Legion Liberty
The second cluster we identified was focused on impersonating Legion Liberty.
We looked into an additional cluster flagged in the Artem Tamoian Twitter thread that included two new domains:
- legion-liberty[.]com
- rdk-official[.]com
Examination of the Legion Liberty official site: legionliberty[.]army revealed information on their Telegram:
Due to the obvious similarity between “legion-liberty[.]com” (spoofed) and “legionliberty[.]army” (real), our researchers began looking for domains that included “legionliberty” without a dash.
Pivot: Further Wildcarding
We performed a DNS data search on “*legionliberty*” and omitted the legitimate domain from the results.
- datasource = “whois” AND domain = “*legionliberty*” AND domain != “*legionliberty.army*”
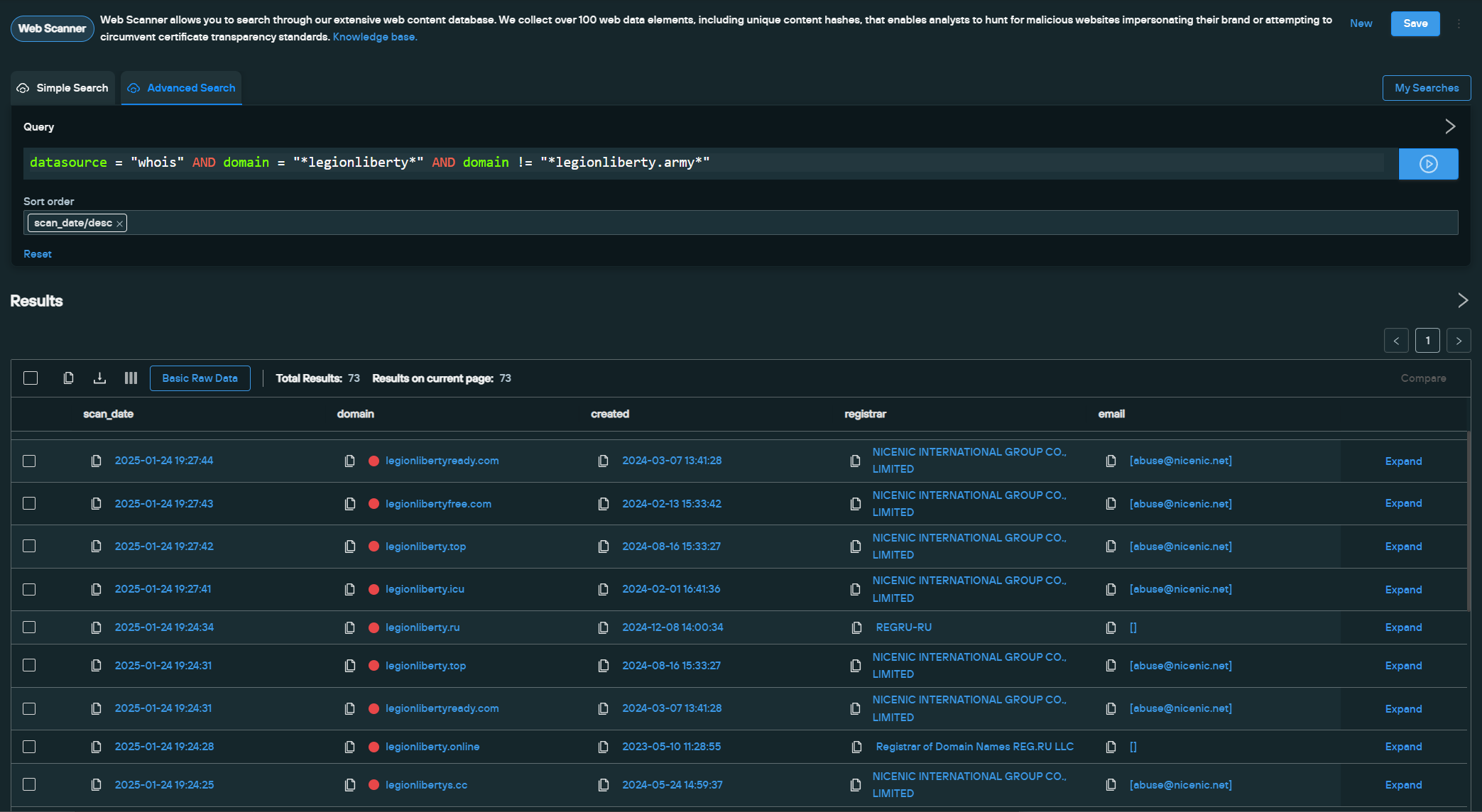
Our search uncovered seven domains:
- legionliberty[.]cc
- legionliberty[.]com
- legionliberty[.]info
- legionliberty[.]top
- legionlibertyfree[.]com
- legionlibertyready[.]com
- legionlibertys[.]cc
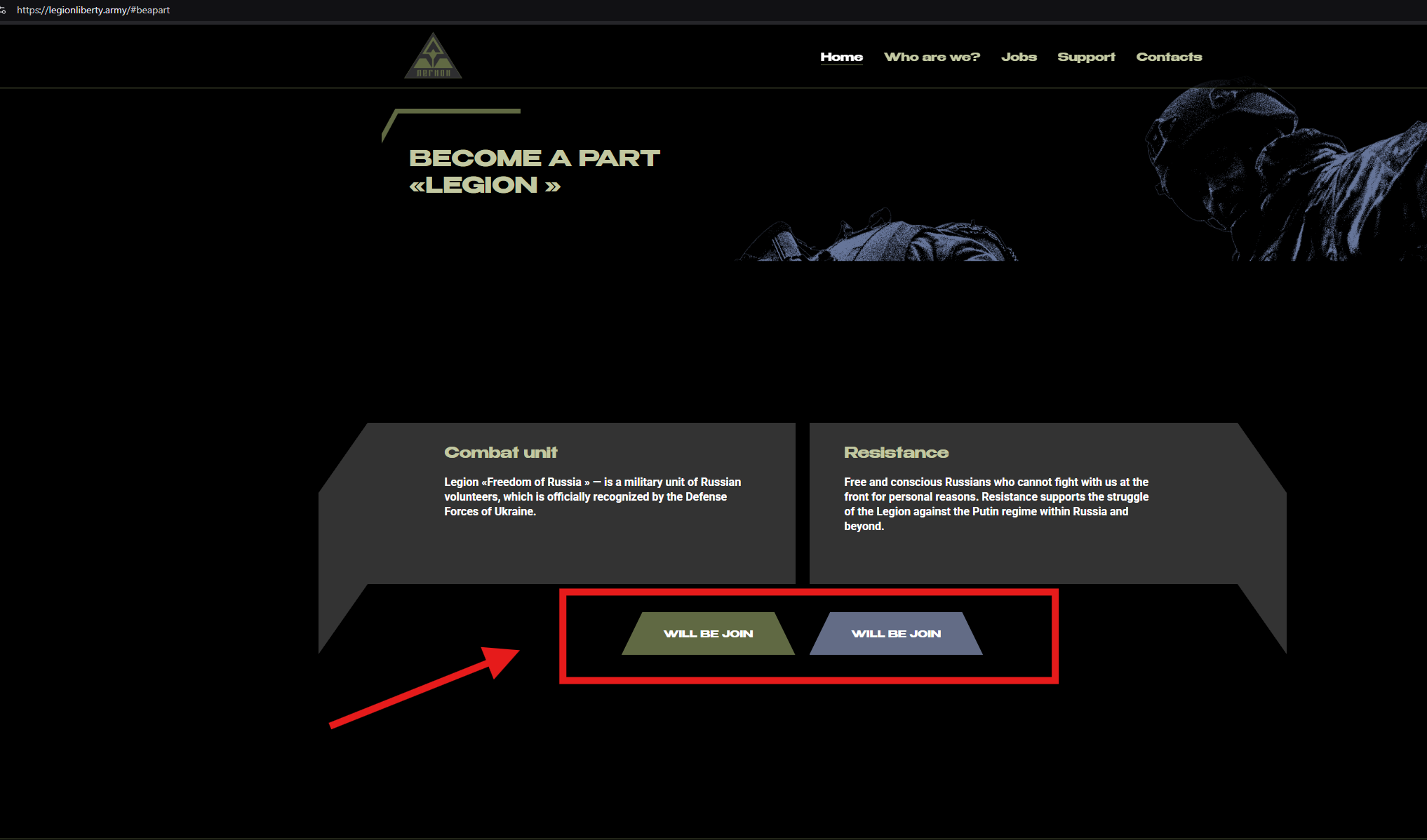
Exploring legionliberty[.]top took us to this phishing page:
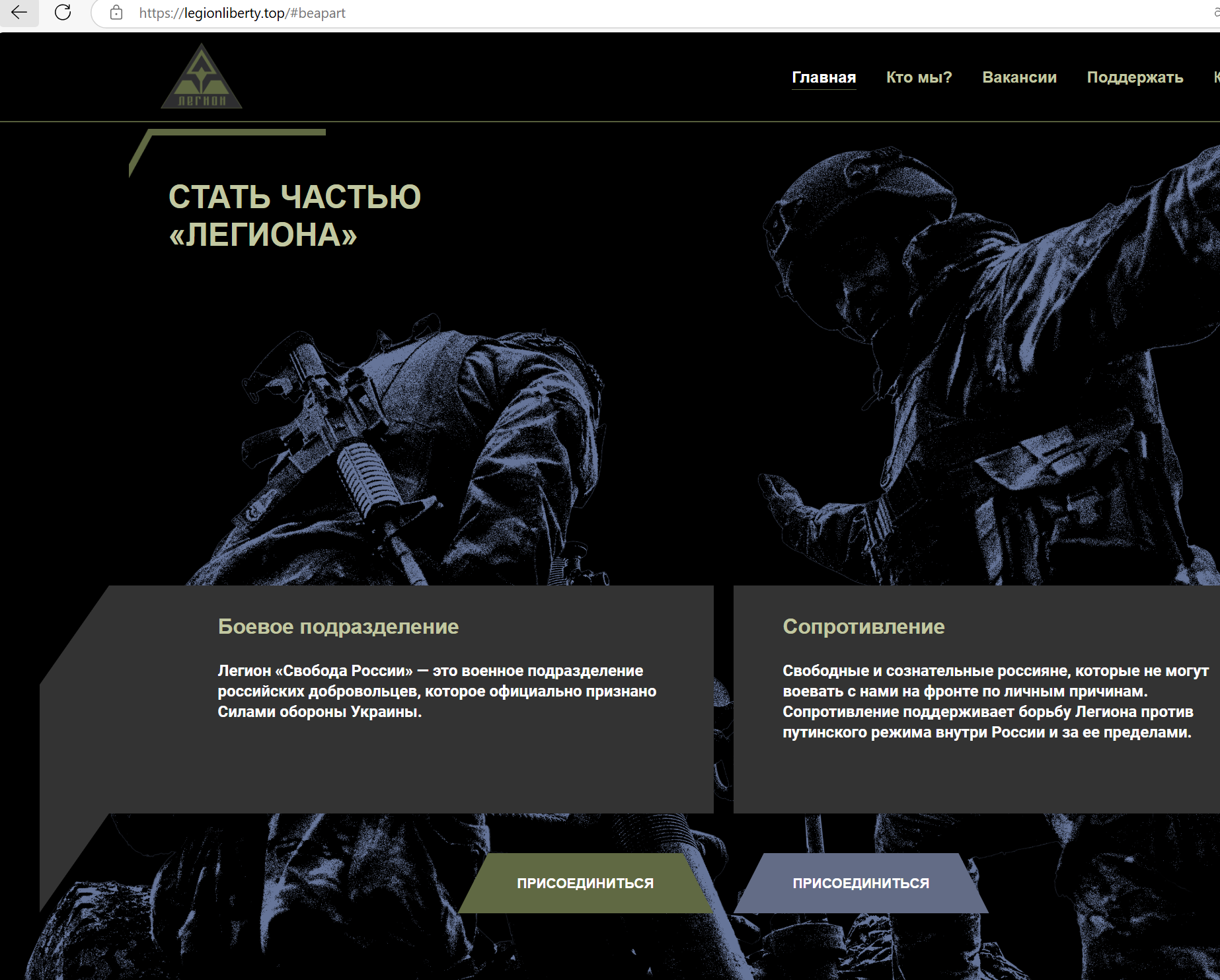
When initially testing the seemingly illegitimate website legionliberty[.]top, the blue “Join” button linked to the real Google Form currently being used by the Freedom of Russia Legion. In the translation, this is for those who wish to support resistance efforts but can’t fight.
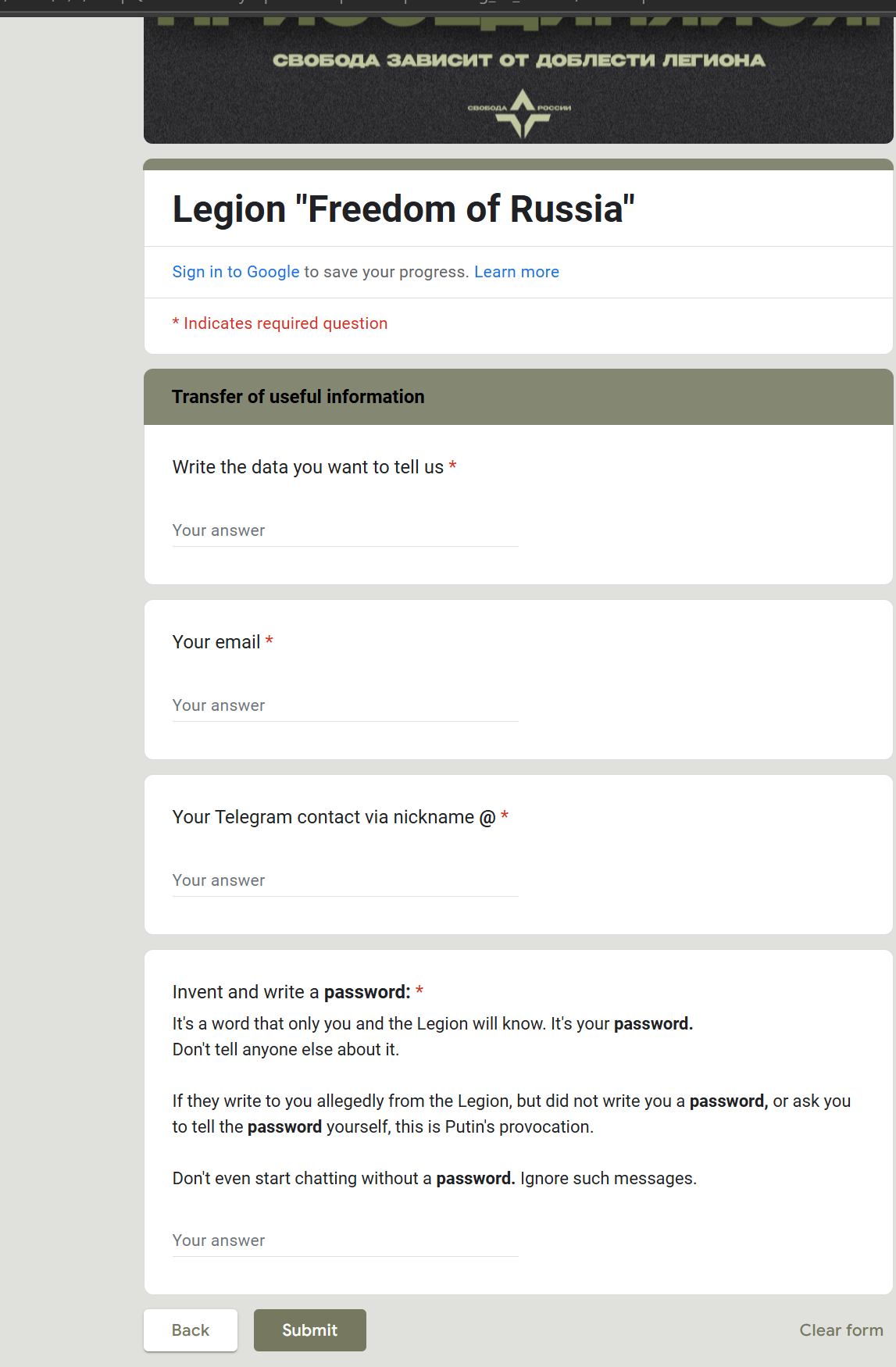
Whereas clicking the green button (signing up for a “Combat unit”) brings the potential victim to a Google Form that asks several “required” questions with the actual goal of capturing the victim’s personal information. Notably, this Google Form is controlled by the threat actors:
The page (translated from Russian to English):
While looking for more information on rusvolcorp[.]com, Twitter led us to a thread from cybersecurity expert Alexander Litreev, who highlighted the email used on the malicious site legionlibertys[.]army was dvizheniesrs[@]proton[.]me.
Litreev’s post helpfully highlighted that this email is different from the official email address in having one extra “s” character before the “@”. You can see the real email address from this screenshot of the official contact page.
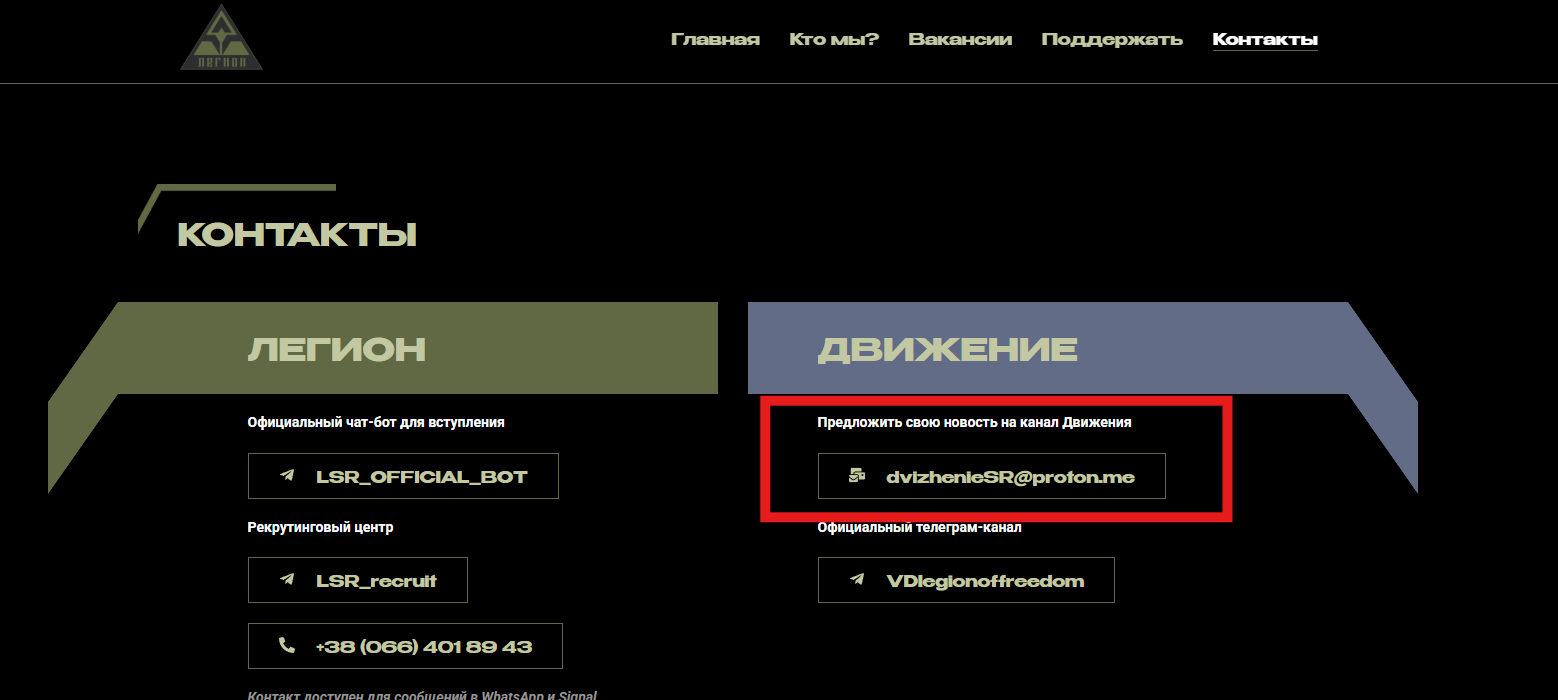
This information provided us with a new domain: legionsliberty[.]army, where again the “s” is the single letter difference from the official domain.
A slight variation in the content of the site libertylegion[.]cc gave us a new option to find similar infrastructure. Our search yielded three domains that all had the same unique content, each spoofing the legitimate site:
- legionliberty[.]top
- legiohliberty[.]army
- libertylegion[.]cc
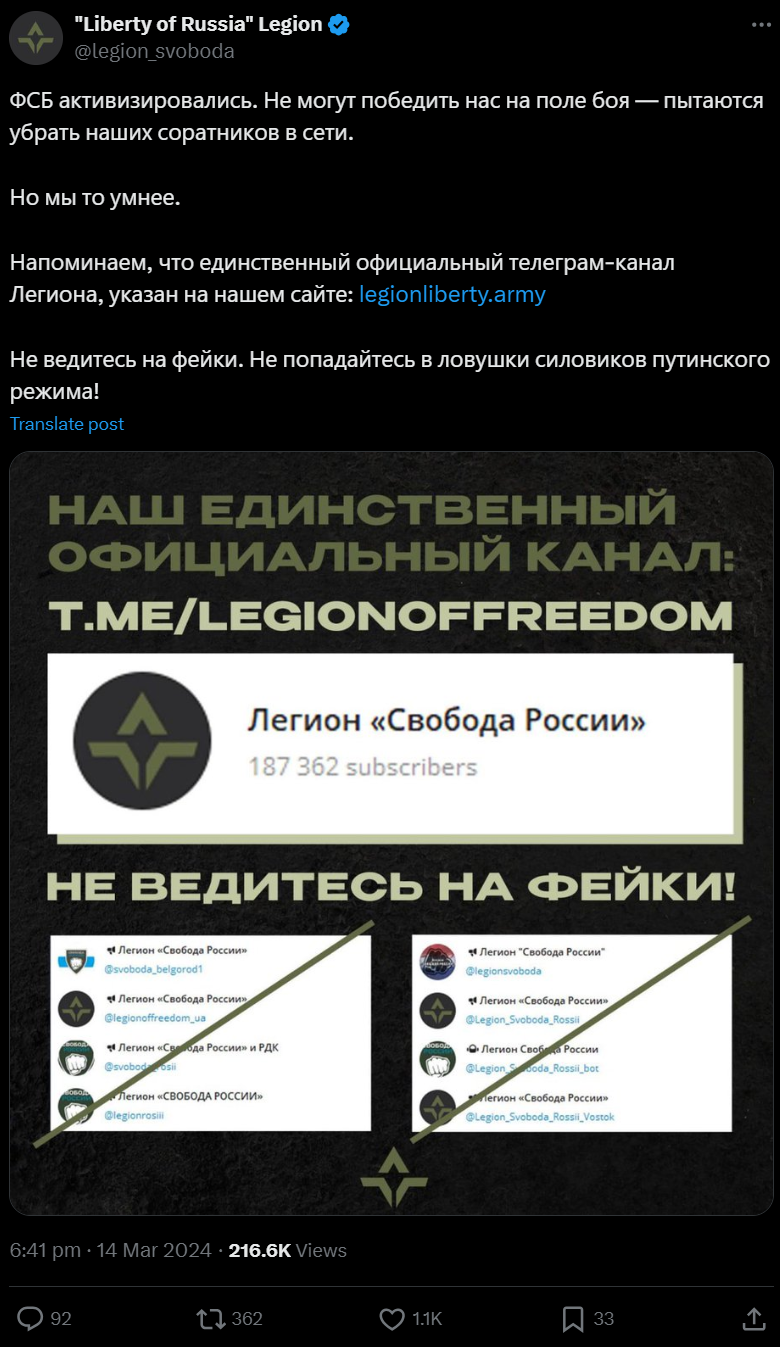
The official Liberty of Russia Legion made an X (formerly known as Twitter) post on March 14, 2024.
“The FSB became more active. They cannot defeat us on the battlefield – they are trying to remove our comrades from the network.
But we are smarter.
We remind you that the only official telegram channel of the Legion is listed on our website: hxxps://legionliberty[.]army
Do not be fooled by fakes. Do not fall into the traps of the security forces of the Putin regime!”
Further investigation revealed that two of the three domains were most recently hosted on 80.78.22[.]146. The shared content on each gave us confidence that they match our Legion Liberty cluster and additional domains for Cluster 3, which targeted the CIA.
Moving forward, we’ll explore this connection further.
Cluster 3 – The “CIA”
Dedicated IPs such as 80.78.22[.]146 helped us connect the various clusters at play here, giving us two more suspected domains targeting the CIA. Each of these was observed around the same period that the fake Russian Volunteer Corp sites were found.
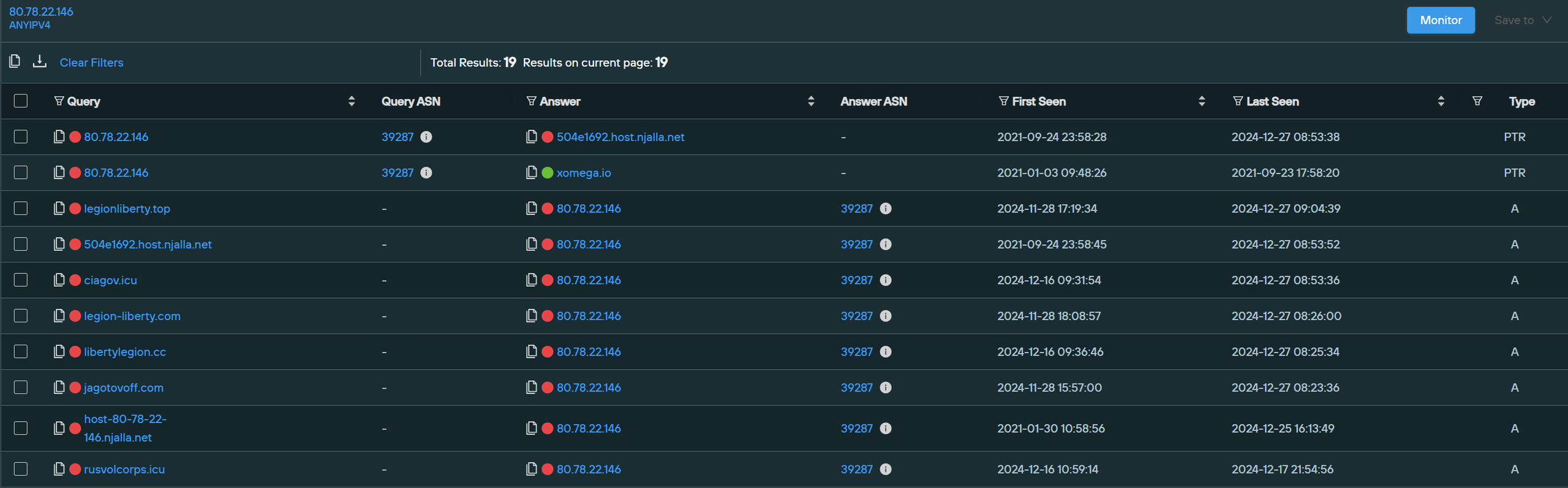
Both ciagov[.]icu and jagotovoff[.]com were found to be impersonating the actual CIA website. They were also noted to be on the same IP address as the other phishing pages.
While reviewing ciagov[.]icu, our team noticed there was a working “Report Information” link that generated a suspicious “Submission Reference ID” when using the form:
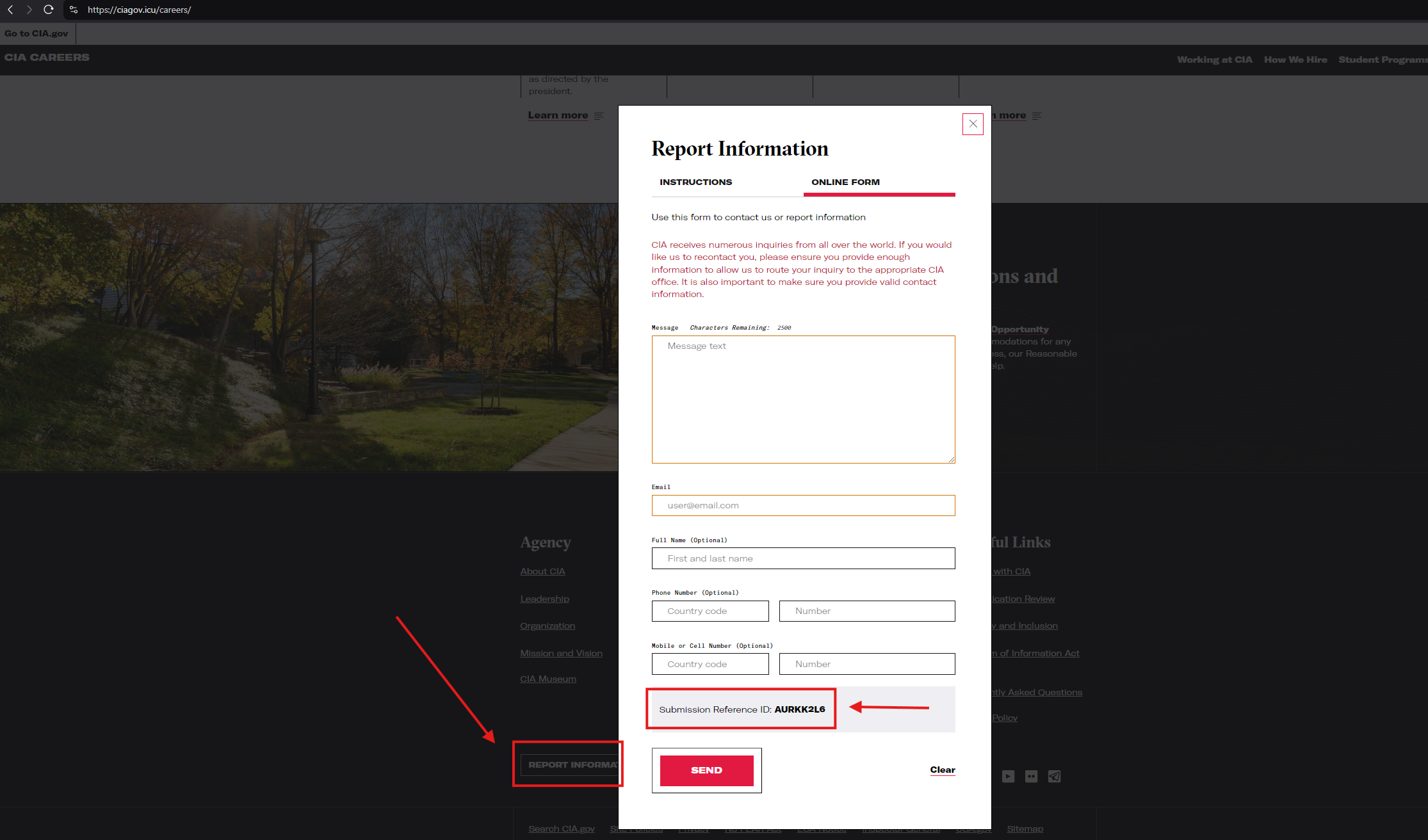
After submitting the form, a pop-up in Russian appears:
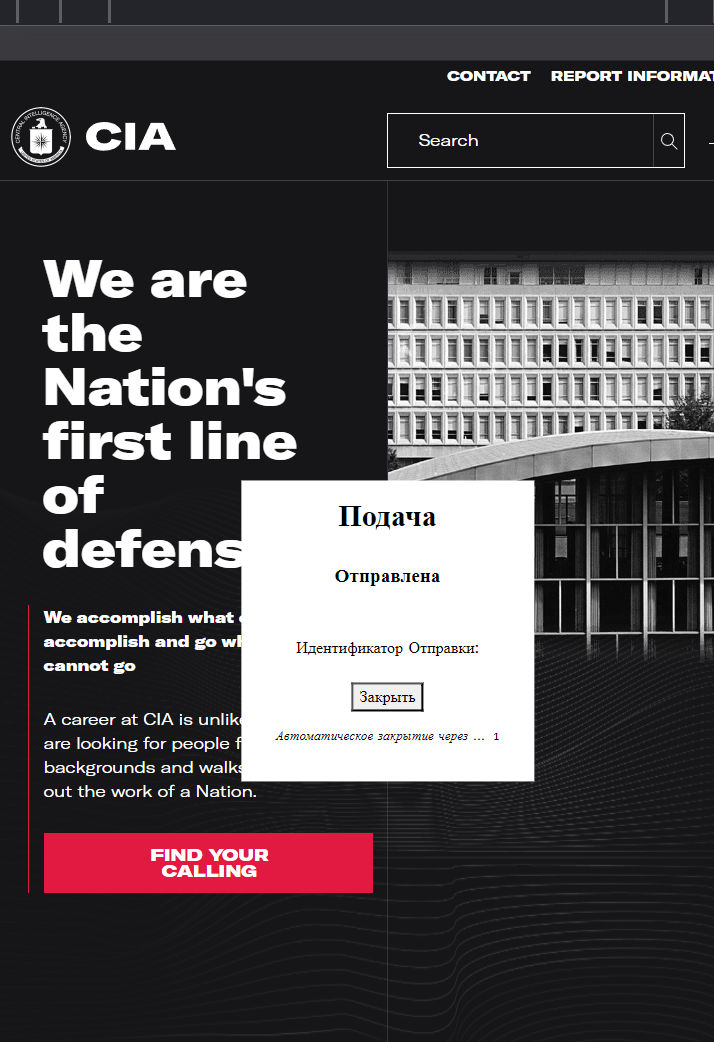
The pop-up translates to:
XXX Sent
Submission ID:
Automatic closing after… 1
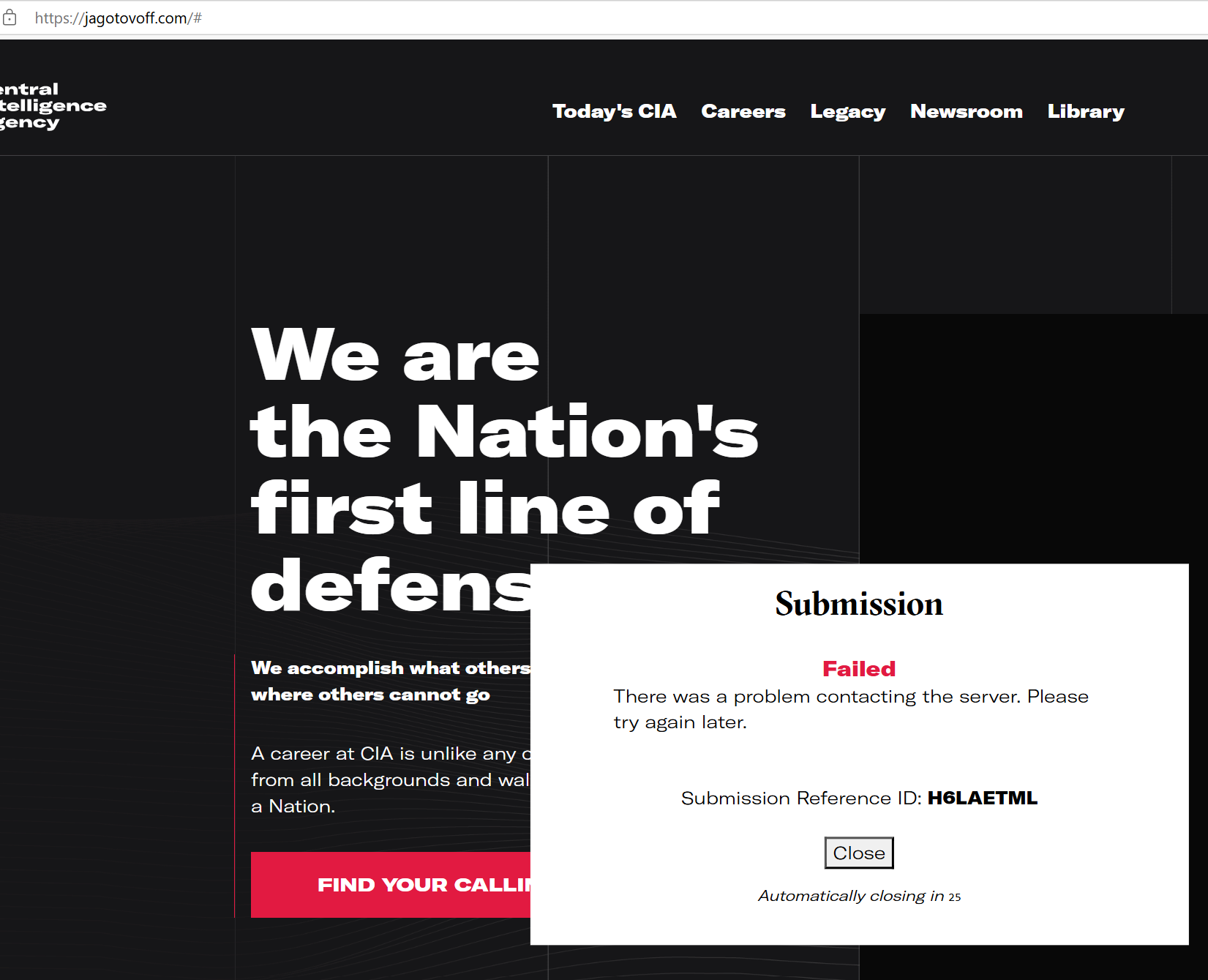
Interestingly, the jagotovoff[.]com page responds in English with the message:
In reviewing the metadata captured in the Web Scanner for ciagov[.]icu, we found it was linking to the legitimate Telegram URL for the CIA, but the embedded .onion URL—easily found (and searched against) via our “body_analysis.onion” field, as seen below—was not the official Tor website for the CIA.
Note: The “.onion” top-level domain (TLD) referenced here is a specialized TLD used by the Tor project to anonymously host sites commonly referred to as the “dark web.” Its goal is to ensure a high degree of privacy and security for both users and service operators.
- datasource = “webscan” AND body_analysis.onion = “ciagovlgmxiyo7qapr6km536svznpsygmqdeen5hpg5xce7b4zav54ad.onion”
This same “.onion” link has also been observed on ciagov[.]ltd and ciagov[.]info.
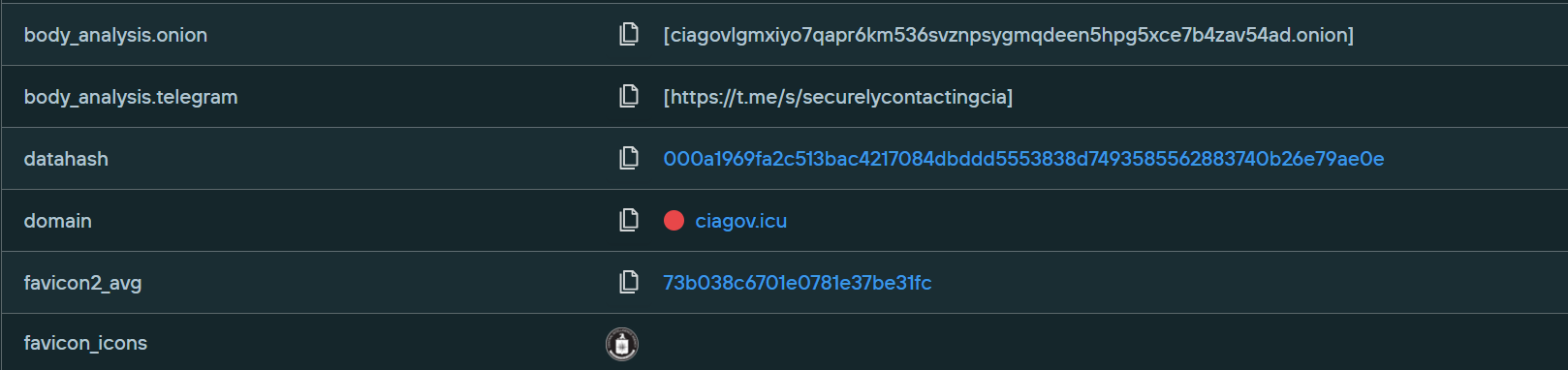
Silent Push Threat Analysts were able to correlate the ciagov[.]icu and ciagov[.]info domains in this cluster, as well as additional clusters, through the use of a unique WHOIS “organization” field, “Semen Gerda,” being used across each.
This clearly demonstrated the level of effort these threat actors have invested in crafting their phishing campaigns.
In the screenshot of the YouTube video titled “How do I contact the CIA? Report Information to the CIA.” (below), the threat actor stripped the official video posted by the CIA and replaced it with the ciagov[.]icu phishing domain and .onion top-level domain TLD within the video’s description.
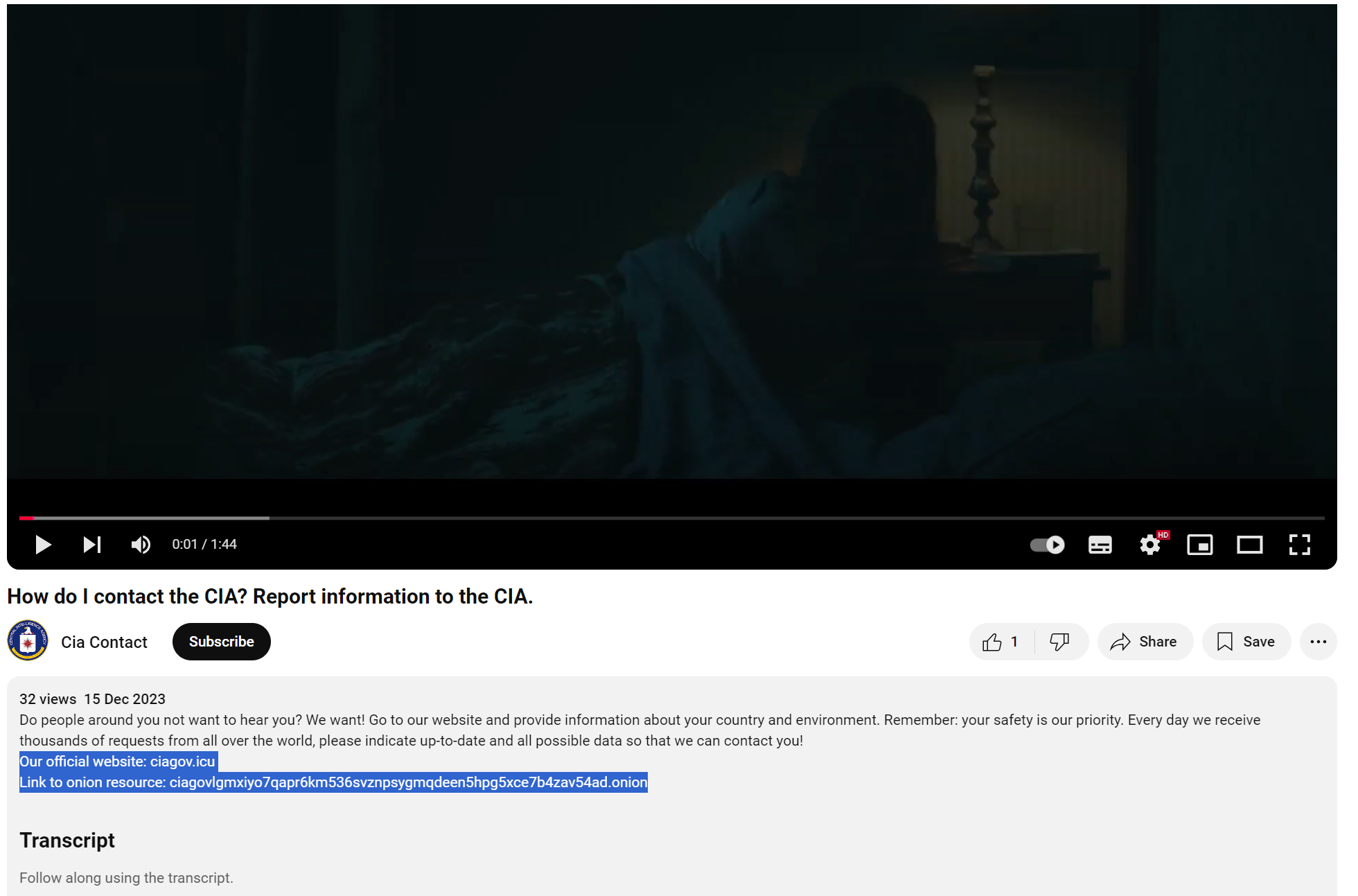
While the “.onion” link was no longer active, through OSINT, we discovered a YouTube channel: youtube[.]com/@contactciaofficial that refers to both ciagov[.]icu and ciagovlgmxiyo7qapr6km536svznpsygmqdeen5hpg5xce7b4zav54ad[.]onion.
Many of the CIA pages we observed appear to be malicious, and Silent Push has confirmed that several CIA-themed phishing pages were connected to this threat group.
The CIA established a presence on Telegram to reach individuals in countries with no access to other social media or independent media. Here, we see the inadvertent new risks this creates for both sides, as those in opposition to such communication see such risks as opportunities for deception and covert cyber tactics.
Our team found that the following domains, ciagov[.]info, ciagov[.]ltd, ciagov[.]icu, and jagotovoff[.]com, were all linked to Clusters 1, 2, and 4 and created with malicious intent.
Cluster 4 – Hochuzhit – “I Want to Live”
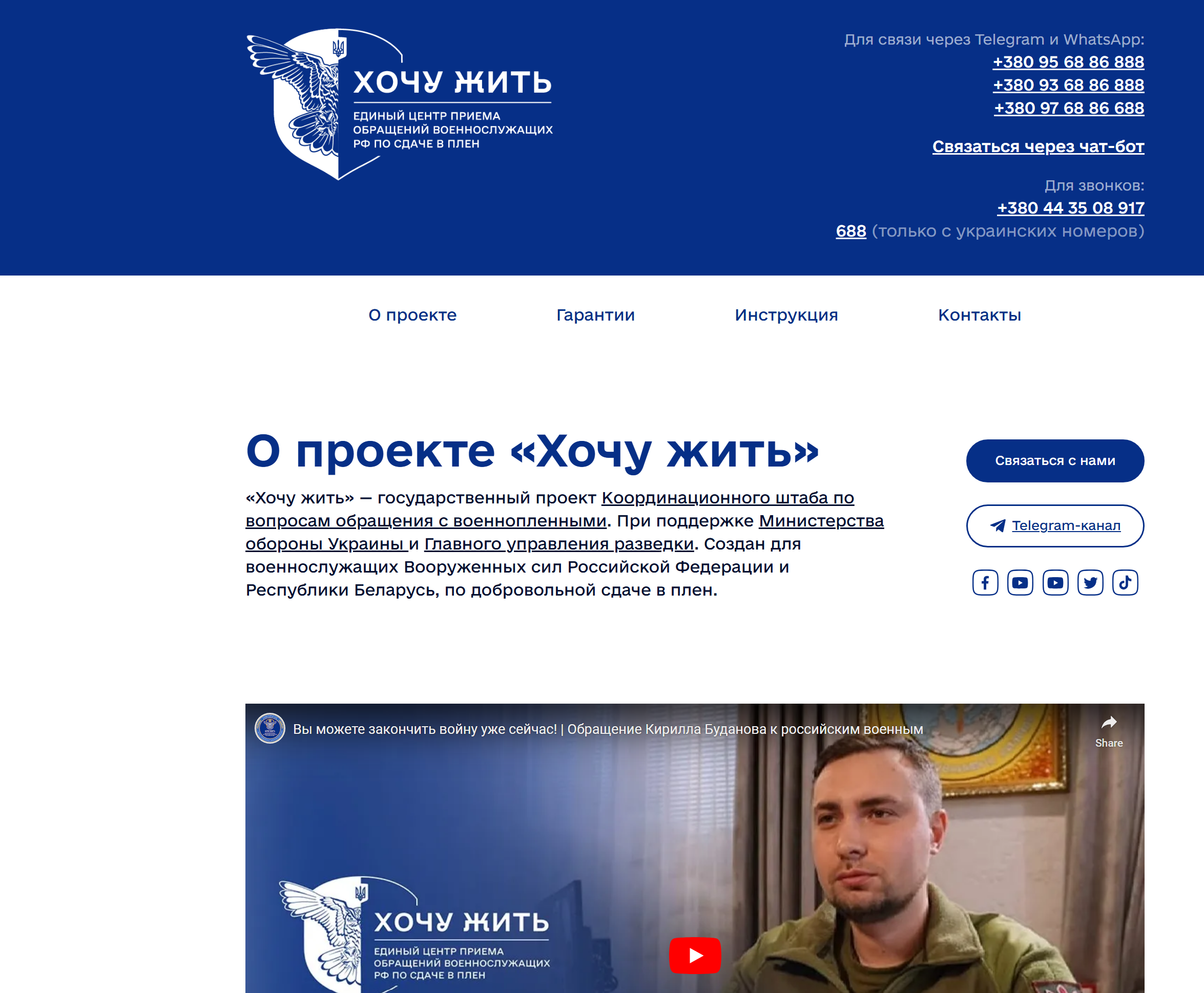
The official domain hochuzhit[.]com – “I Want to Live” (Ukrainian: “Хочу жити“) is a hotline for receiving appeals from Russian service members in Ukraine.
Operated by the Defense Intelligence of Ukraine, this service is designed to help Russian service members who don’t want to participate in the Russian invasion of Ukraine to safely surrender to the Ukrainian Armed Forces. The project guarantees the detention of surrendering military personnel “In accordance with the Geneva Convention.”
During our research, we continued to return to the same pivot discussed earlier—the “Semen Gerda” organization name seen in WHOIS data. This indicated a strong connection between the clusters, pointing to shared creation by a single threat actor.
- datasource = “whois” AND organization = “*Semen Gerda*”
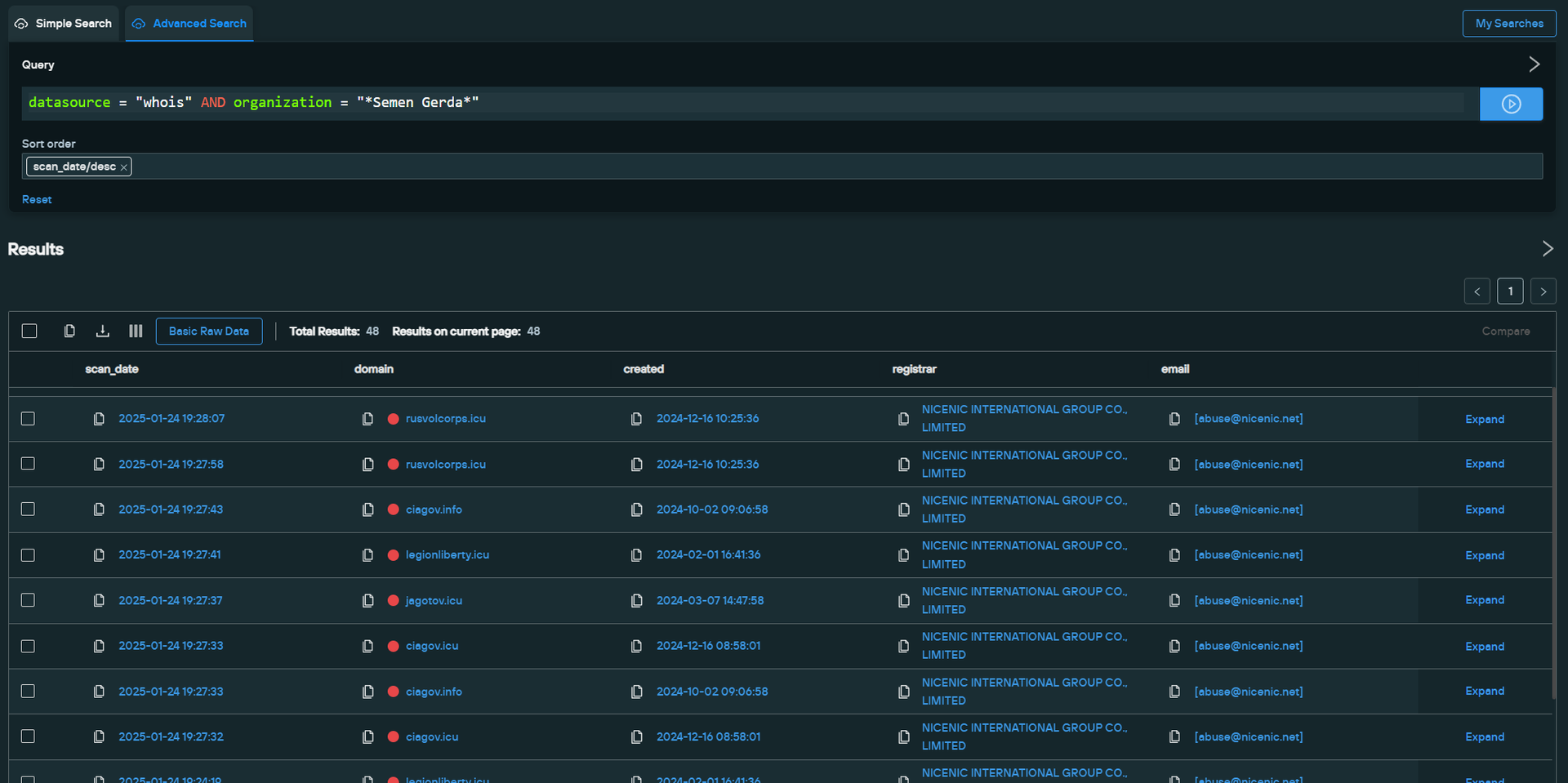
We discovered several new domains:
- xn—–7kcdeekd2agaz3andbd9alja[.]com*
- contactcia[.]com
- jagotov[.]icu
- hochuzhitlife[.]com
- hochuzhit[.]life
The last two domains, hochuzhitlife[.]com and hochuzhit[.]life, appeared to be registered by the same threat actor group that was impersonating the official site “hochuzhit[.]com”, referenced previously.
Latest Adversaries
Through the technical fingerprints we had in place, we discovered four new domains confirmed to be related to this campaign: legionliberty[.]icu, rdkcontact[.]com, ciacontactru[.]com, and legioncontact[.]com.
We also discovered that rusvolcorp[.]net was registered and hosted with Hostinger. While the domain remained highly suspicious, it could no longer be fully attributed to Russian Intelligence.
When visiting the site ciacontactru[.]com directly, it displayed the following content:
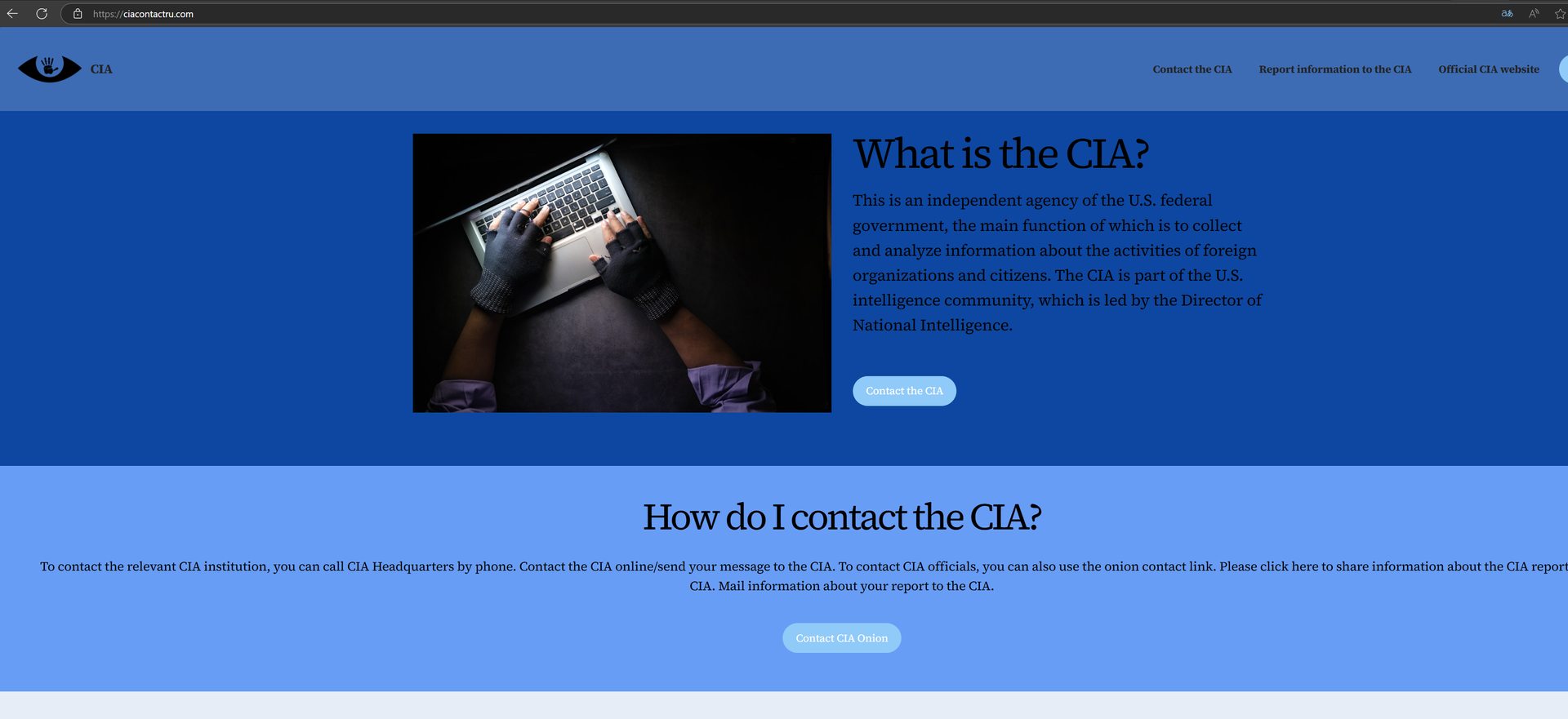
A Google search of the “ciacontactru[.]com” domain results in the official CIA logo and a site page that looks completely different from the official CIA website. Clicking on the result leads you to ciagov[.]icu, which, as previously mentioned, is connected to the phishing campaign. This indicates that the threat actor is either doing this for SEO purposes or to avoid detection from threat analysts and defending scanners.
![Screenshot of a Google search for ciacontactru[.]com phishing site](https://www.silentpush.com/wp-content/uploads/russ-blog-google-search-cia-image-27.png)
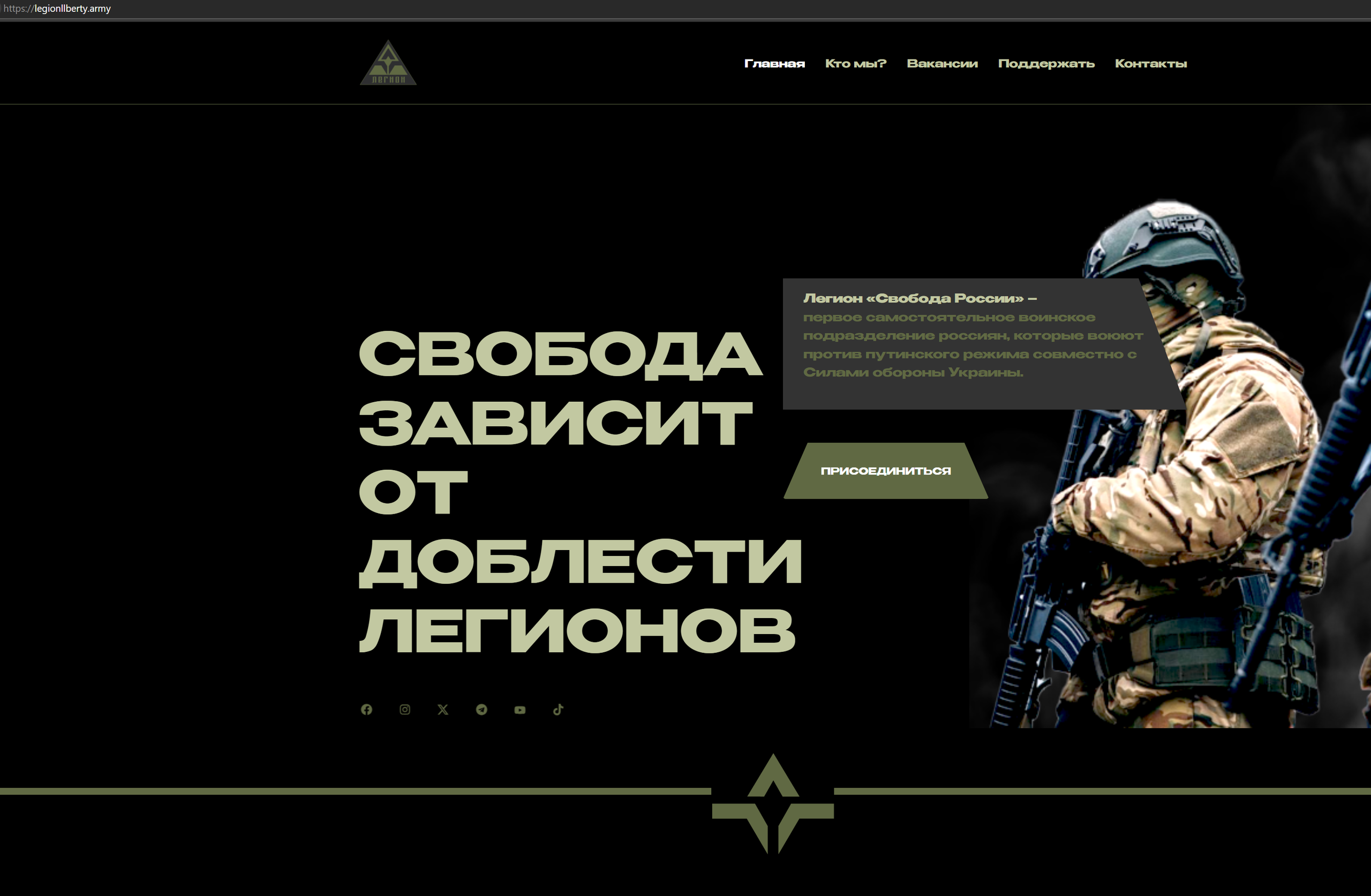
Silent Push Threat Analysts collaborated with the initial finder, Artem Tamoian, to discover a previously registered domain, legionllberty[.]army, hosted on Cloudflare for the first time on March 11, 2024. The domain is registered with NiceNIC, which we have seen used with almost all the domains involved in the phishing campaign.
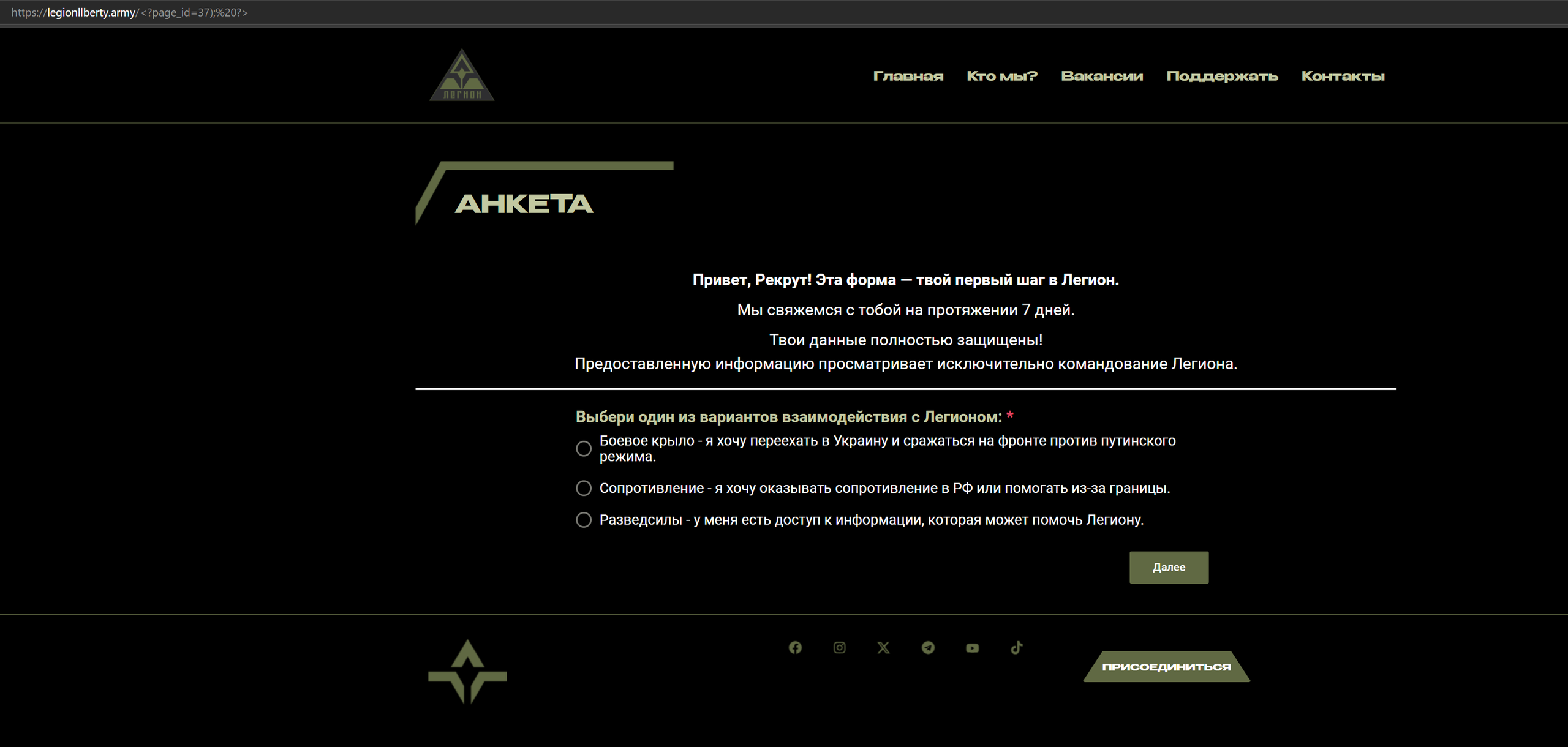
Below, you can see that the form has changed and is no longer with Google Forms.
Mitigation
Silent Push believes all domains related to the Russian Intelligence Agency may offer some level of risk.
Silent Push IOFA Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign up for a free account.
Sample Indicator of Future Attack (IOFA) List
The table below provides a sample list of IOFAs. Our full list is available for enterprise users. Silent Push Enterprise clients have access to a domain and IP feed containing the Russian Intel Agency’s infrastructure.
| IOFAs – Webscan | Domains | ASN | Subnet | AS Name |
|---|---|---|---|---|
| 80.78.22[.]146 | legionliberty[.]top jagotovoff[.]com legion-liberty[.]com ciagov[.]icu libertylegion[.]cc rusvolcorps[.]icu504e1692.host.njalla[.]net ciacontacts[.]com ciarucontacts[.]com legion-libertys[.]com rdk-contact[.]com rusvokcorps[.]cc | 39287 | 80.78.16.0/20 | ABSTRACT, FI |
| 81.161.238[.]212 | rusvolcorps[.]net | 401116 | 81.161.238.0/24 | NYBULA, US |
| 94.103.183[.]7 | ciagov[.]live collection-xyz[.]live cirkus-novosibirsk[.]ru cirkus-novosibirskiy[.]ru | 212913 | 94.103.183.0/24 | TIMEHOST-AS, UA |
| 95.183.10[.]181 | rusvolcorps[.]net | 210079 | 95.183.10.0/24 | EUROBYTE, RU |
| 103.113.71[.]190 | ruvolcorps[.]com | 133973 | 103.113.71.0/24 | NETCONNECTWIFI-AS Net Connect Wifi Pvt Ltd, IN |
| 104.168.138[.]186 | n/a | 54290 | 104.168.128.0/17 | HOSTWINDS |
| 147.45.44[.]53 | n/a | 215789 | 147.45.44.0/24 | karina-rashkovska |
| 195.201.37[.]78 | www.hochuzhit[.]life ciacontactofficial[.]com ciaform[.]com contact-cia[.]com | 24940 | 195.201.0.0/16 | HETZNER-AS, DE |
Other IOFAs
- 7kcdeekd2agaz3andbd9alja[.]com
- ciacontactru[.]com
- ciagov[.]info
- ciagov[.]ltd
- ciagovlgmxiyo7qapr6km536svznpsygmqdeen5hpg5xce7b4zav54ad[.]onion
- contactcia[.]com
- hochuzhit[.]life
- hochuzhitlife[.]com
- jagotov[.]icu
- legiohliberty[.]army
- legioncontact[.]com
- legionliberty[.]cc
- legionliberty[.]com
- legionliberty[.]icu
- legionliberty[.]info
- legionliberty[.]top
- legionlibertyfree[.]com
- legionlibertyready[.]com
- legionlibertys[.]army
- legionlibertys[.]cc
- legionllberty[.]army
- legionsliberty[.]army
- rdk-official[.]com
- rdk[.]social
- rdkcontact[.]com
- rusvokcorps[.]com
- rusvolcorp[.]com
- rusvolcorp[.]net
- rusvolcorps[.]net
- ruvolcor[.]com


