This article is being updated to try and reflect current events. Both the Conti gang and Ghostwriter have been added to our ‘russo’ tagging.
Threat Intelligence Requirements and current fears of Russian state activity. How to gather and disseminate intel.
Threat Intelligence requirements can change quickly because of an urgent request brought on by world events or recent press coverage. Log4J would be a prior example where many teams would have received a sudden change of priorities from management due to an event. NotPetya is another example.

Fears of Russian Cyber Attacks
Unfolding events between the Ukraine and Russia and the resulting warnings are a good reason to change priorities . How can a threat intelligence team (or an organization that doesn’t have such a team) react to this type of event quickly. There is a need to give the larger organization some assurance that,
- the Threat Intelligence team is well aware of the event and
- they have taken action to reduce the organizations risk by performing some actions
- those actions include collecting pertinent information and taking risk reduction measures including pushing some observables to security infrastructure.
Lets take Russian State threat actors as an example as it is a complex task. There are three parts to this task.
- Known groups and known infrastructure
- Known groups on unknown infrastructure(intelligence based)
- Services for hire that may be utilized by the known groups or begin to be used by nationalistic supporters.
Let’s begin with known groups. Then we will move into other directions that we expect to be taken. These are the known Russian groups.
1.APT28 , (Other Names: STRONTIUM, Sofacy, Zebrocy, Sednit, Pawn Storm, TG-4127, Tsar-Team, Iron Twilight, Swallowtail, SNAKEMACKEREL, Frozen Lake, Fancy Bear)
Recent reports include this one from BushidoToken .
This is a well documented ,high performing, state actor APT group with extremely good operational security. Attacks can come from free hosting providers and dynamic domain providers. It is worth treating this type of traffic with extreme suspicion if your organization does not need it operationally.
2. APT29 (Aliases are;Dukes, Group 100, Cozy Duke, CozyDuke, EuroAPT, CozyBear, CozyCar, Cozer, Office Monkeys, OfficeMonkeys, APT29, Cozy Bear, The Dukes, Minidionis, SeaDuke, Hammer Toss, YTTRIUM, Iron Hemlock, Grizzly Steppe) and recent reports of activity include one from the French CERT , an article in Security affairs about the targeting of French Organizations, and Microsofts MSTIC team have provided a github account with updated indicators . There are behavioral patterns that threat intelligence organizations are tracking to keep an eye on future campaigns and the infrastructure expected to be used. We include this in our very small and curated “Suspect APT29” feed. This takes undisclosed behavioral patterns of this group to track where their next attack is coming from.
3. Actinium/Gamaredon/. (Primitive Bear (CrowdStrike), Winterflouder (iDefence), BlueAlpha (RecordedFuture), BlueOtso (PWC), IronTiden (SecureWorks), SectorC08 (Red Alert), and Callisto (NATO Association of Canada)). There are many articles on activities for the last year. For example. This report just came out from Microsoft on the targeting of Ukranian organizations . Closely followed by another. The Ukranian SSU released this report on them (this link may be down when you read this as they are under DDOS attack as I write).
4. Lorec53/UAC-0056 as identified by CERT Ukraine . Also in this report from nfocus
5. Turla/Snake (other aliases or associated names:Group 88, Belugasturgeon, Waterbug, WhiteBear, VENOMOUS BEAR, Snake, Krypton) This group is rarely detected and is called out in this report from Talos Intelligence
6. Sandworm. (Also Called; ELECTRUM, Telebots, IRON VIKING, BlackEnergy (Group), Quedagh, VOODOO BEAR) Renowned for some big events including NotPetya. Currently very active with new advisories just released from both CISA and the UK’s NCSC on the new Cyclops Blink modular malware framework targeting SOHO network devices.
7. Neighbouring Belarus are allied with Russia and have their own group called Ghostwriter which has been actively used in this conflict and the run up to this conflict.
What information is available regarding these groups that can be used today? Lets look at open source first and then what we can provide. Well there are some recent reports covering all of these groups, a number of them are linked above. Whether these cover most of the associated infrastructure or not is unlikely. TTP (Tactics Techniques and Procedures) based intelligence is useful to multiply the effectiveness of your defenses and try and get ahead of the Threat Intelligence time lag.
There is always a question as to which additional outsourced groups/services may be used in a time of war by the aggressor or may join in the conflict for other reasons. There are many offensive services for hire so the future attacks are not restricted to these groups normally associated with Russian state intent. People get very nationalistic in times of conflict and it is quite possible that Russian crimeware groups will do the same. Over exuberant use of Ransomware or Wiperware could be on the cards.
There can be two types of observables in feeds pertaining to these groups. Firstly, Indicators of Compromise from a known breach or attempted breach which may come from a variety of sources including sandboxes and other security products (IOC based). Secondly, suspect infrastructure and assets taken from intelligence gathered on the adversary and their tactics techniques and procedures (TTP based). The second type is very difficult to get, but very valuable. It is more difficult for the attacker to change their TTPs than to change the detected indicators. So, for example, it is easy to change the IP address, but it is difficult to change the process for how you register and manage your domains over time.
Collecting The Information
To get started you can gather all associated known infrastructure with whatever Threat Intelligence Management platform you use. With us, we would start building that with an advanced filter like this
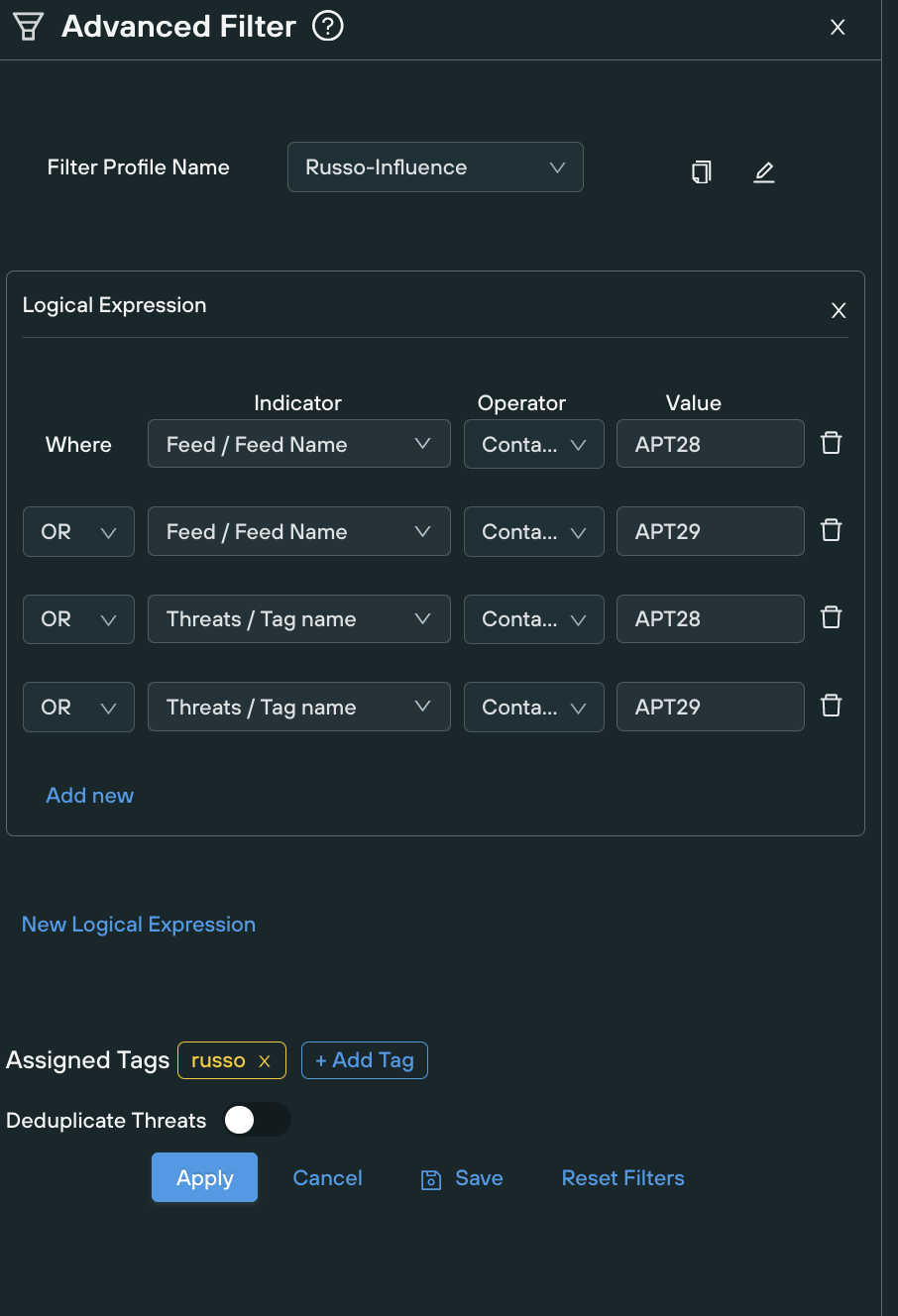
Then continue to add all the groups you are looking for. For customer convenience, we have tagged all the observables of the groups mentioned with the tag ‘russo’, so you can just do the simpler task of using that tag search.
One tag ‘russo’ is used to cover the state actors including predictive TTP based intelligence
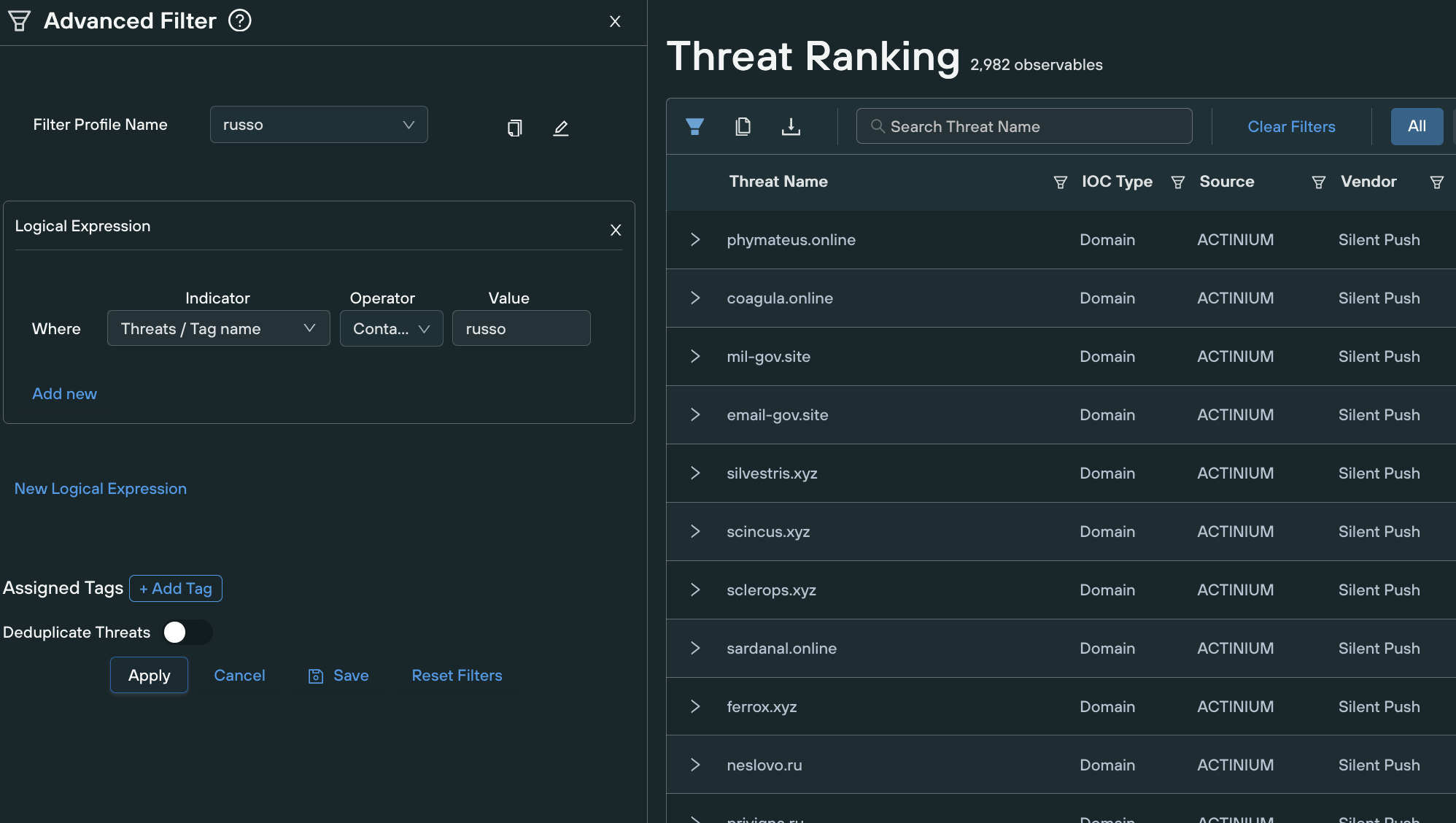
When you save that filter it creates a dynamic API endpoint that you can paste into any other product, like your SIEM and you can pull the updated feed on a schedule as you see fit.
Outsourced Groups
However, the next task for the Threat Intel team is to deal with the fact that in a quickly evolving situation like the present one it is very likely that ‘for hire’ or crime groups will be part of the activity. That means you will need to broaden your scope from the more obvious groups and feeds and look at mixed malicious infrastructure services used by different groups.
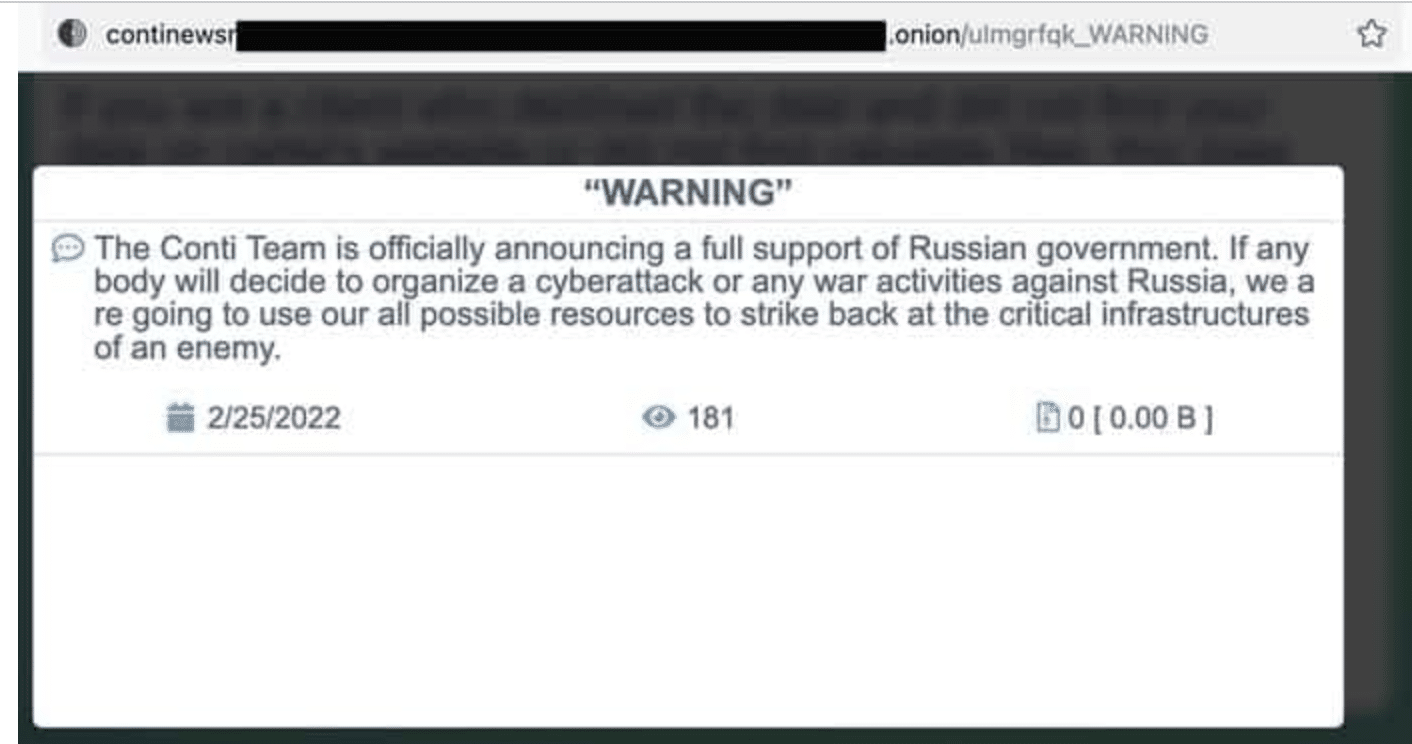
The Conti group have just announced full support for Russia in this conflict. They are now also tagged with our ‘russo’ tag.
The one that comes to mind first for us is our Sasha BPH domains and IPs. This malicious infrastructure provider is used by many groups and that makes things difficult. You will see many phishing domains mixed in with DDoS, spam campaigns, and a catalog of ransomware variants. All of these will be useful in the coming tensions. This service provides a dynamic infrastructure that moves not just across IP space but across cloud providers as well. Here’s a domain that is only a couple of days old as it appears in our IP Diversity graph.
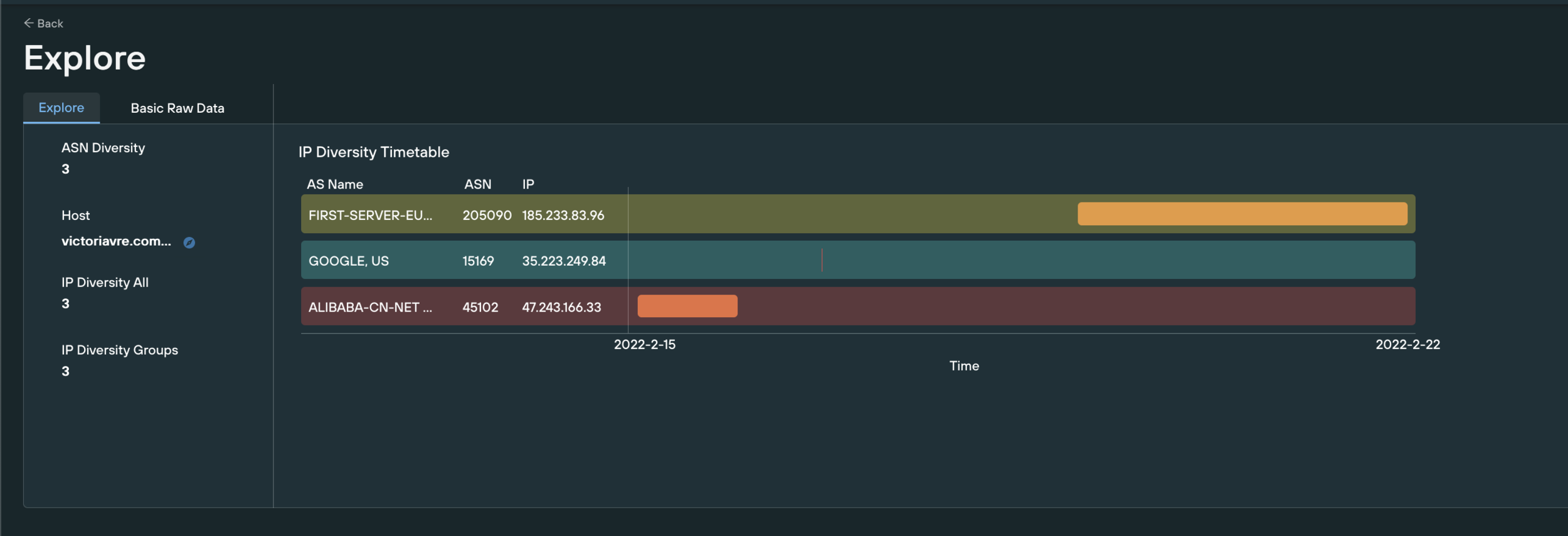
This complicates things for the defender as there are many infrastructure-for-hire groups and all of it needs to be blocked. It is useful to pick the more Russian-centric ones like the Sasha BPH as a good starting point but considerations should also be made as to who would also be allied with the adversary and whether that opens the door to another group or groups to worry about.
An example of how one thing may lead to another is this article showing the credential stealing campaign targeting Governemnt suppliers in order to gain access, was then followed by this alert about Russian state sponsored actors targeting defense contractors
Some posts we’ve written that could be relevant for this task
https://www.silentpush.com/blog/phishing-sites-on-bulletproof-hosting-infrastructure
https://www.silentpush.com/blog/phishing-infrastructure-used-to-target-us-government-contractors
https://www.silentpush.com/blog/bad-ases – this is worth thinking about, we have created a new “Convergence Ranked Feed” which combines a number of these reputation factors to highlight the providers consistently used by a variety of adversarial groups.
https://www.silentpush.com/blog/targeted-attacks-and-generic-defense-dont-match
Along the same lines of covering off popular methods that may become a part of this in the coming months we would recommend including observables around access brokers like IcedID, this is available in our Frozen Passport Domains and Frozen Passport IP lists. Tooling specific feeds should also be used like our Cobalt Strike feeds (used by APT 29 and others https://attack.mitre.org/software/S0154/ ), there are a number of these in the portal.
CISA have an advisory on the Russian Cyber Threat https://www.cisa.gov/uscert/russia
And on government contractors being targeted https://www.cisa.gov/uscert/ncas/alerts/aa22-047a
A resource set up to show how cyber crime groups are lining up in support of each side is here.
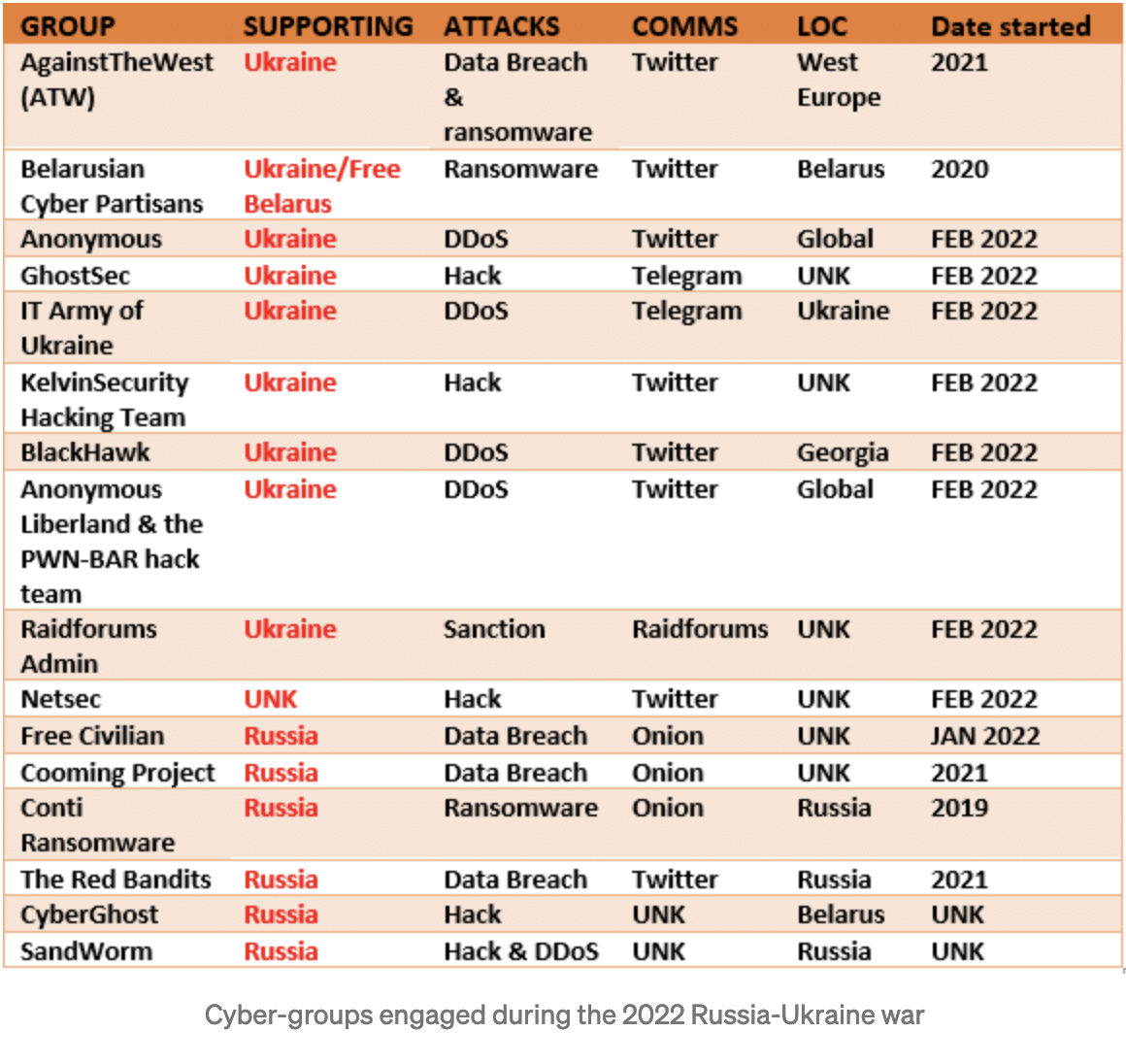
https://github.com/curated-intel/Ukraine-Cyber-Operations Curated Intel are providing links to many recent reports.
“Image resource: Depositphotos”. This article has been designed using images from depositphotos.com. All other information including product screen shots are copyrighted by Silent Push Inc. 2022


