‘The Dead Russian Poets Society’: Silent Push uses behavioural fingerprinting, content scans and a 128-year old Russian poem to uncover 150+ new ACTIVE Lumma C2 servers and admin panels.

Key points
- Behavioural fingerprinting and content similarity scans used to reveal 150+ new Lumma C2 IOCs.
- Administrator TTPs and new malware iterations used to reveal an new pre-attack landscape.
- New Lumma domain administrator email addresses discovered.
Background
Lumma (also known as LummaC2) is an information stealer with strong links to Russian threat activity, that’s been available on the dark web as a MaaS platform since 2022.
The malware – available for between $250-$1,000 per month – steals system data and sensitive information from infected machines, including browser data, stored credentials, and cryptocurrency data.
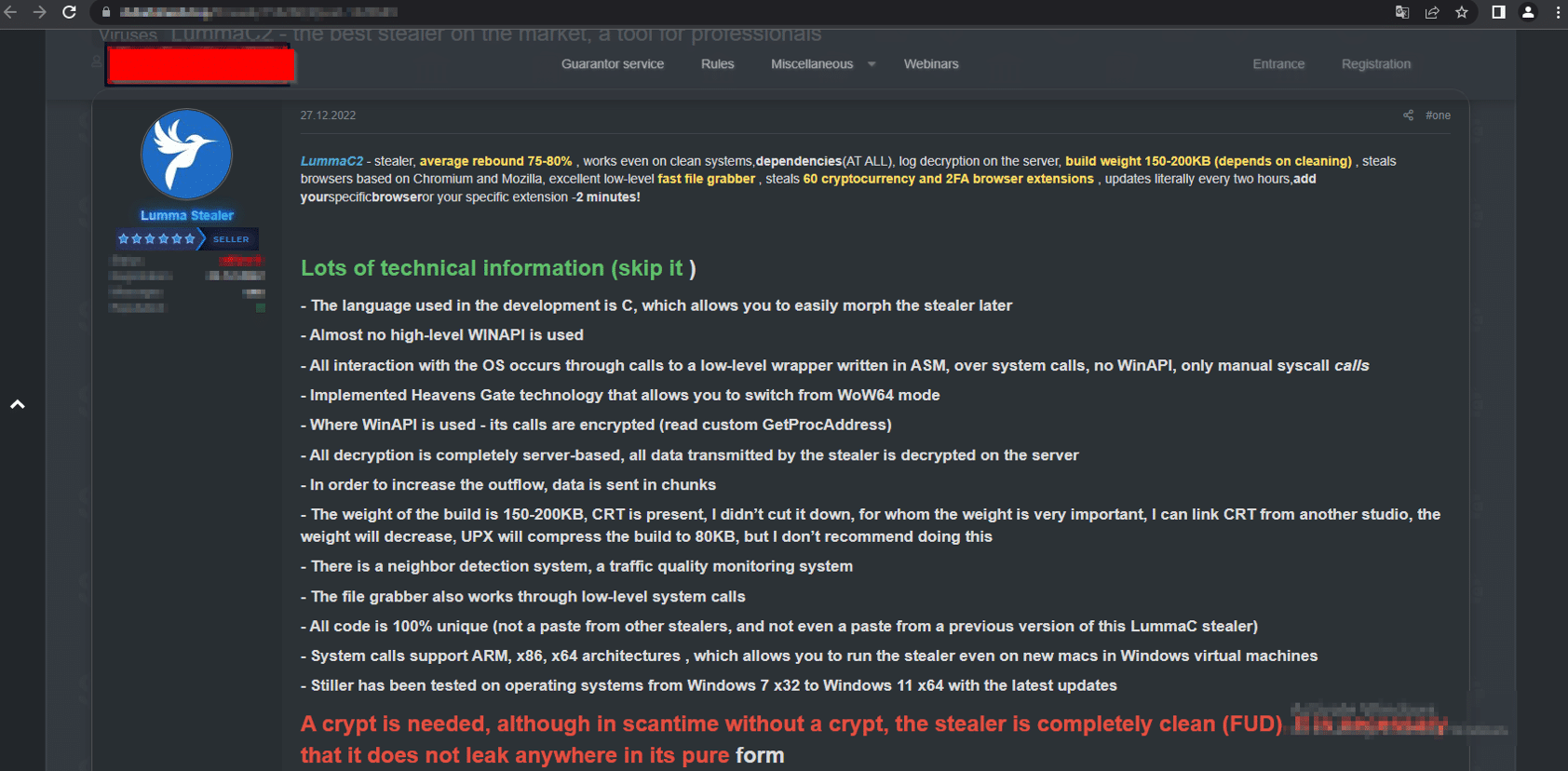
Lumma advertisement on a dark web forum (Source: cyble[.]com)
Previous Russian research
In December 2022 we published research on the Ursnif/Gozi banking trojan – an early C2 progenitor with its roots in the Russian criminal underworld, distributed via AnyDesk phishing pages.
We followed this up in February 2023 with a blog on how we uncovered a Russian infostealing campaign that distributed malware (including the Burmilia infostealer) via hijacked YouTube channels.
Despite a renewed focus on Russian APT activity that came as a result of private sector research – itself a validation of the FBI’s vision for private and public sector collaboration announced at mWise this month – Lumma has remained a persistent threat. Our Analysts remained on the trail of Russian C2 infrastructure throughout the summer, and kept abreast of emerging threats into the fall.
Investigation summary
In this blog, we’ll take a look at Lumma’s delivery methods, before showing how we used a single HTTP header to map over 150 previously unknown Lumma C2 servers, pinpointing new attack vectors and using the attackers’ own TTPs against them to reveal a previously unexplored threat landscape… all with the help of a Russian poet that’s been dead for nearly a century.
If that sounds weird, we can explain…
Delivery method
Before we delve into how we tracked the new infrastructure, let’s take a brief look at thin end of the wedge – the malware itself.
How Lumma ends up on a user’s machine depends entirely on the motives and tactics of the operator who purchased the infostealer from its administrators, but generally speaking the payload is distributed via two methods:
- Spear phishing campaigns featuring malicious email attachments, and social engineering tactics that lure victims into executing the payload.
- Malvertisement campaigns and cracked software links – particularly within YouTube video descriptions, and gaming content.
As we’ll go on to discuss, the new version of Lumma also features steganographic PNGs that hide malicious content within embedded image files.
Case study – Distributing the Lumma infostealer via YouTube video descriptions
We published research earlier this the year that explored how Russian threat actors embed malware in the video descriptions of hijacked YouTube channels. This delivery method remains popular, especially among the gaming community. Here’s an example of a YouTube channel – @simbatplay – with 82,000 subscribers, hosting multiple videos that advertise hacks, scripts and tools for popular online games:

@simbat YouTube channel
Video descriptions contain a link to URL shortener, that redirects to file hosting service such as mediafire[.]com, stating an alternate ‘mirror’ domain:
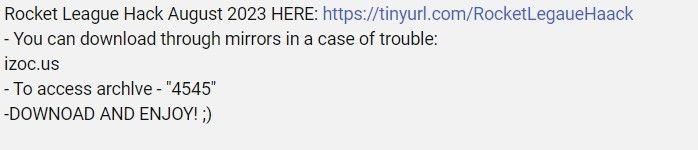
@simbat video description with malware link
Executable behaviour
Mirrored domains use VirusTotal themed colours to host the same file, with an inactive ‘Visit VirusTotal’ link placed next to a ‘Download’ button:
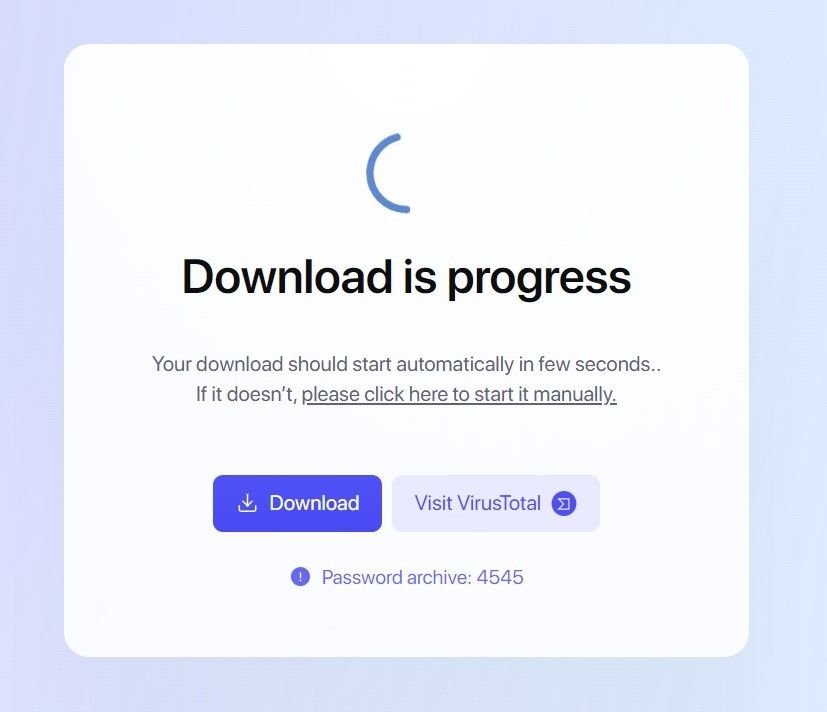
Lumma download content from izoc[.]us
The ‘Download’ button leads to password protected .rar files, containing executables and DLL files.
The executables are artificially inflated into larger file sizes with binary padding techniques that counteract submissions into public sandbox tools – behaviour consistent with the campaigns that have been observed earlier in the year.
Once executed, the malware attempts to read an array of on-device data, including local cryptowallet data, browser data, and stored credentials:
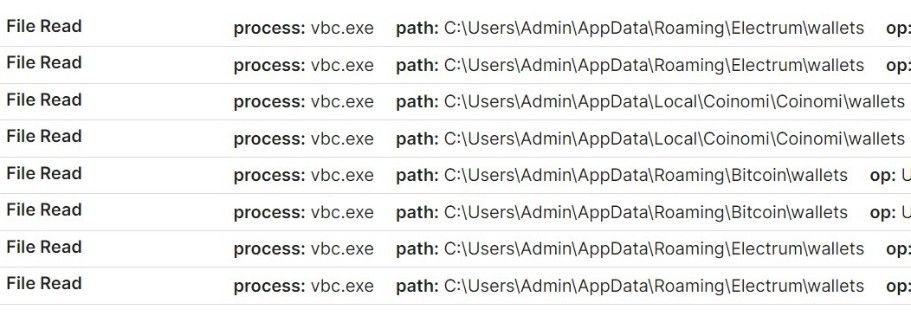
Attempted malicious cryptowallet file reads
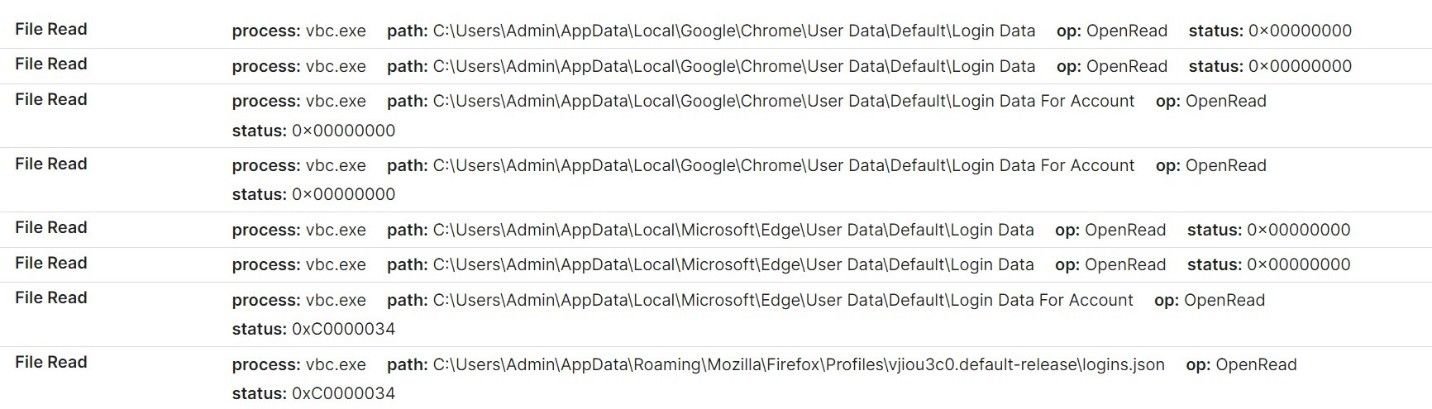
Attempted credential harvesting
POST request
Once user data has been collected, the malware attempts to establish a connection with associated C2 domains, and sends information via unencrypted archive files.
The malware also retrieves a config list from the C2 server, which means that extracted data is not embedded within the infostealer itself.
Here’s a HTTP POST request to a Lumma C2 server that we’ve identified – erorblackday[.]xyz – registered by kippjosephc@gmail.com, an email address associated with multiple C2 servers that we’ll talk about a little later on.

Lumma POST request to erorblackday[.]xyz
Discovering new infrastructure
Early reports from security researchers matched Lumma C2 activity to the HTML title “LummaC2 | Вход”.
Silent Push scans the Internet’s entire IPv4 range and collects granular data on every observable we come across, including HTML data, allowing us to form a top down picture of attacker TTPs, rather than relying on isolated IOCs.
We took the above HTML title and executed a content similarity scan, which unearthed 6 Lumma C2 IPs active sometime between January-May 2023, with identical HTML titles:
- 144.76.173[.]247
- 195.123.226[.]91
- 45.9.74[.]78
- 77.73.134[.]68
- 82.117.255[.]127
- 82.118.23[.]50
The hunt begins…
Further analysis revealed an associated HTML header that was slightly different to the one that was already widely known: “Вход” (login in Russian), without the “Lumma C2” prefix.
Pivoting on both the long and short title failed to produce a reliable set of results, so instead of utilizing header data, we used the platform to execute a content scan across the entire IPv4 space:
These new search parameters proved fruitful – 33 new IP addresses used as Lumma C2s, including interval data and title information.
2 of the 33 IPs contained active Lumma C2 control panels – 157.90.248[.]179 and 213.252.244[.]62
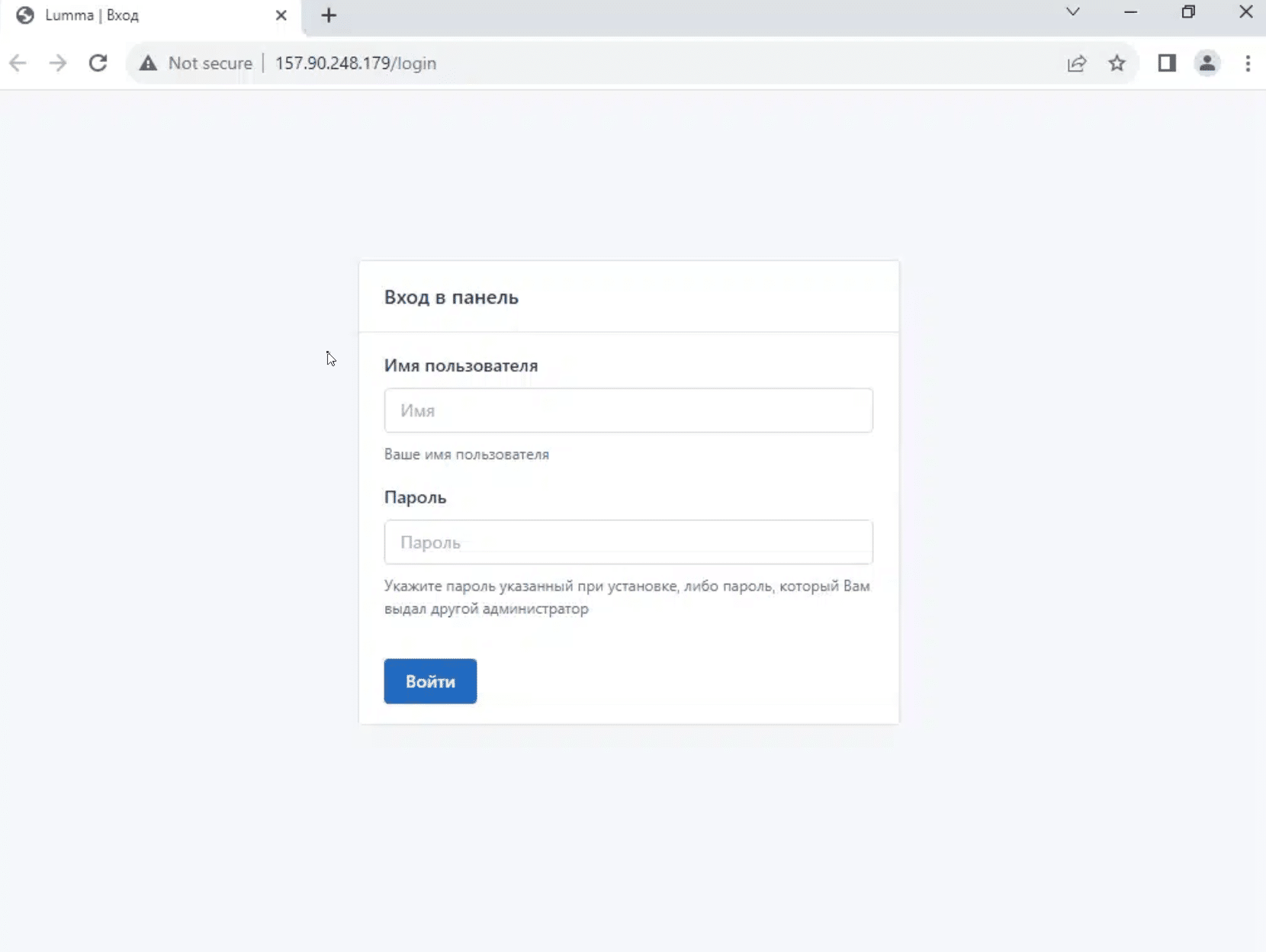
Lumma control panel on 157.90.248[.]179
Analysing C2 ASN data revealed a broad geographic spread, not limited to regions associated with Russian activity:
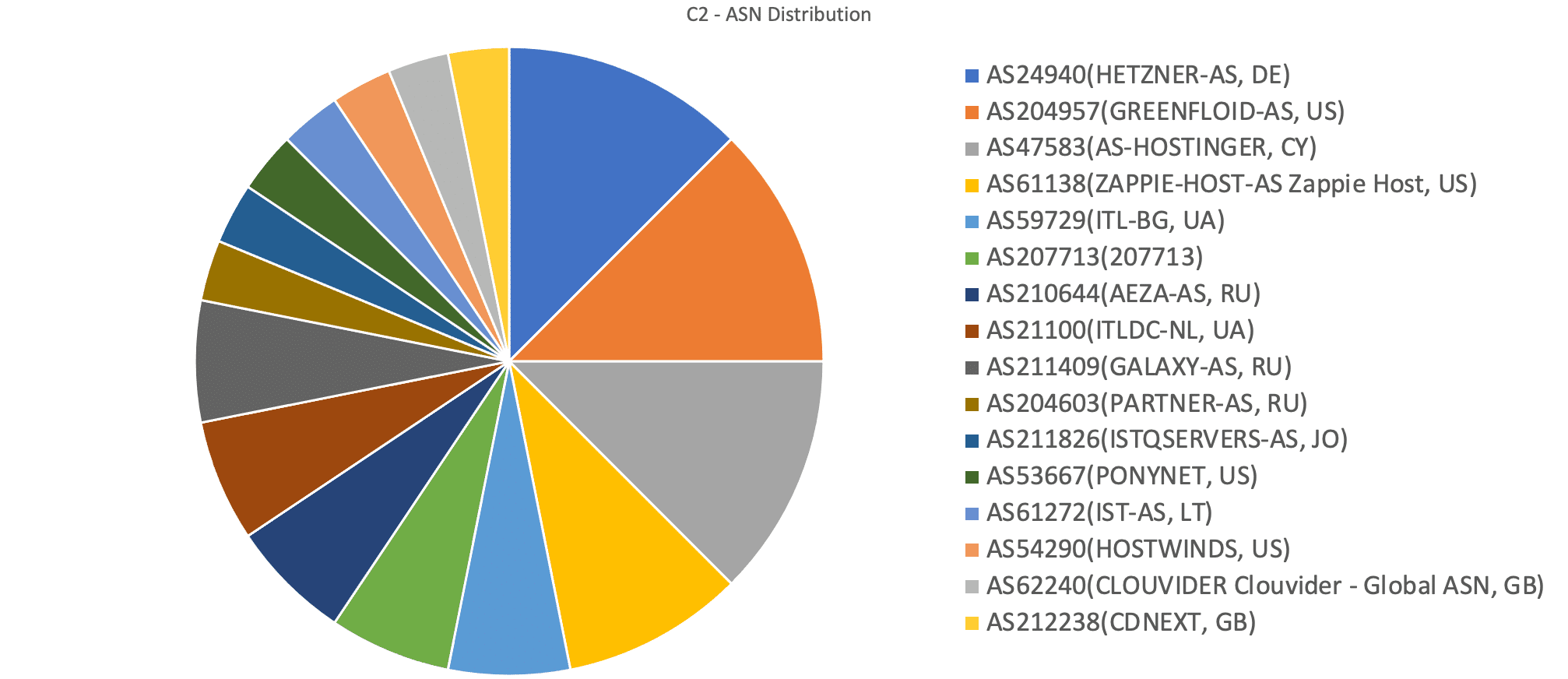
Lumma C2 ASN distribution
Discovering new MaaS control panels
30-day historic domain scans revealed 6 live domains displaying the Lumma control panel:
- gstatic-service[.]io
- scandimyth[.]xyz
- sisadmin-my[.]xyz
- stoptme[.]xyz
- privategame[.]xyz
- traftech[.]pro
Once we’d gathered this new dataset, we started to explore the DNS scanning opportunities a domain subset presents, as opposed to a list of IP addresses.
Our team noticed that all of the domains are proxied to Cloudflare besides traftech[.]pro, which is hosted on 213.252.244[.]62 – an active Lumma C2.
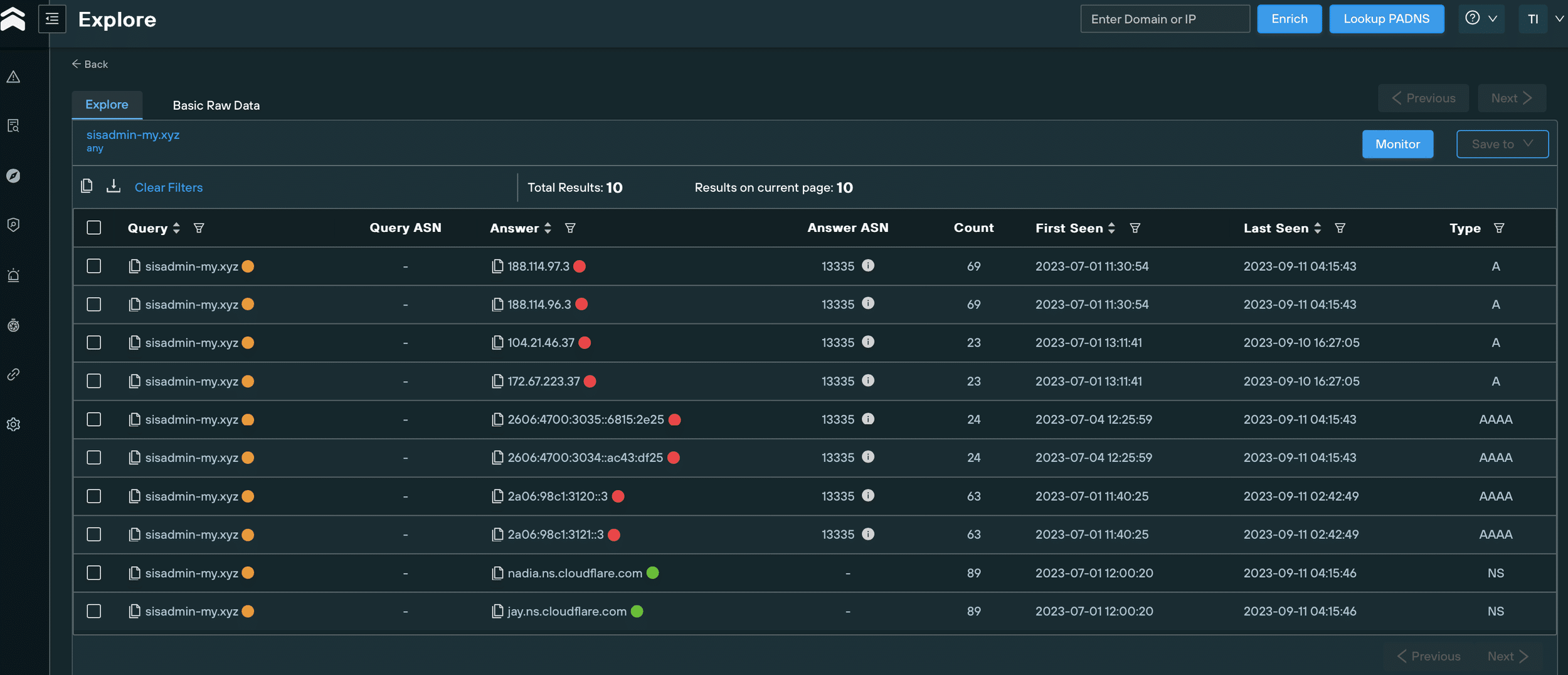
Historical DNS records for sisadmin-my[.]xyz
Historical DNS records for sisadmin-my[.]xyz
With the domain IOCs hiding behind Cloudflare, and following no obvious naming pattern aside from a reoccurring TLD (.xyz), we expanded our investigation to take in enriched WHOIS data.
We immediately noticed that some of the domains had been registered using the email levisrogers13@gmail.com:
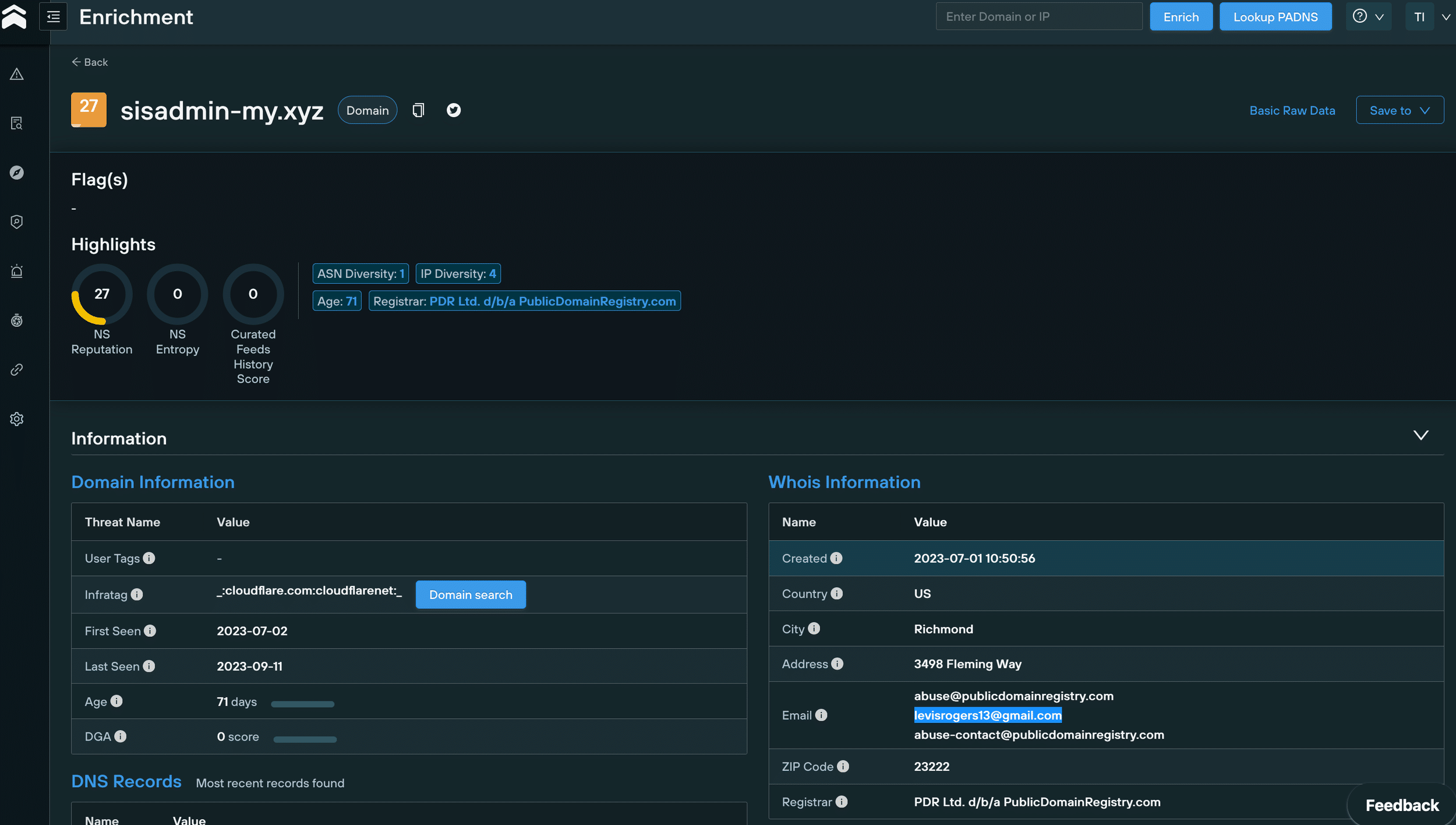
WHOIS data for sisadmin-my[.]xyz
We then used an advanced domain search query to pivot on levisrogers13@gmail.com that revealed 111 new Lumma C2 domains, 53 of which are still active.
All of these domains appear to be proxied to Cloudflare and registered from 23 June 2023 onwards:
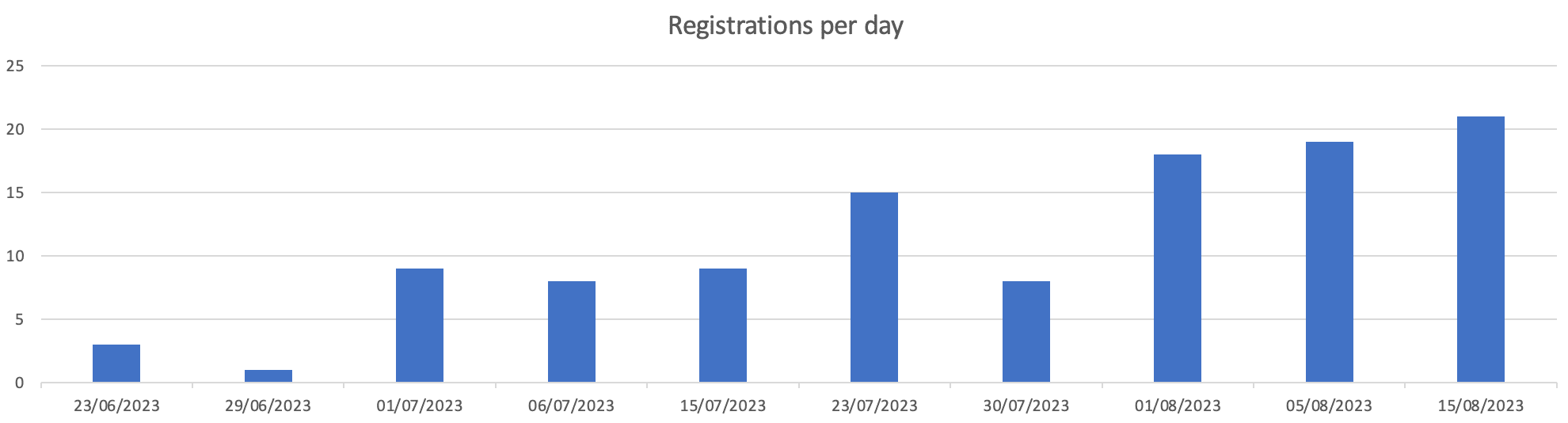
Lumma-linked domain registrations from June 23 2023 onwards
The curious case of Sergei Yesenin’s body data
It’s not just human cadavers that offer up forensic clues to intrepid investigators. Body data fom a webpage can be just as enlightening (and a lot easier to extract!).
Sergei Yesenin was a Russian poet born in 1895. Yesenin spent his days wandering the streets of Moscow and Leningrad, romanticising a rural Russia that was utterly at odds with the relentless march of industrial life in the early 20th-century.
Why is any of this relevant? Yesenin is a poster boy for modern-day Russians that harbour anti-Western sentiments, and yearn for a return to the “good old days” of Russian imperialism. America, according to Yesenin, was “a stinking place where not just art is being murdered, but with it, all the loftiest aspirations of humankind.”
Get off the fence, Sergei!
We scanned the new domains we’d gathered and noticed that, rather than containing Lumma control panels, some of them hosted a page with a poem from Yesenin, complete with a picture of the dapper young poet in his Sunday best:
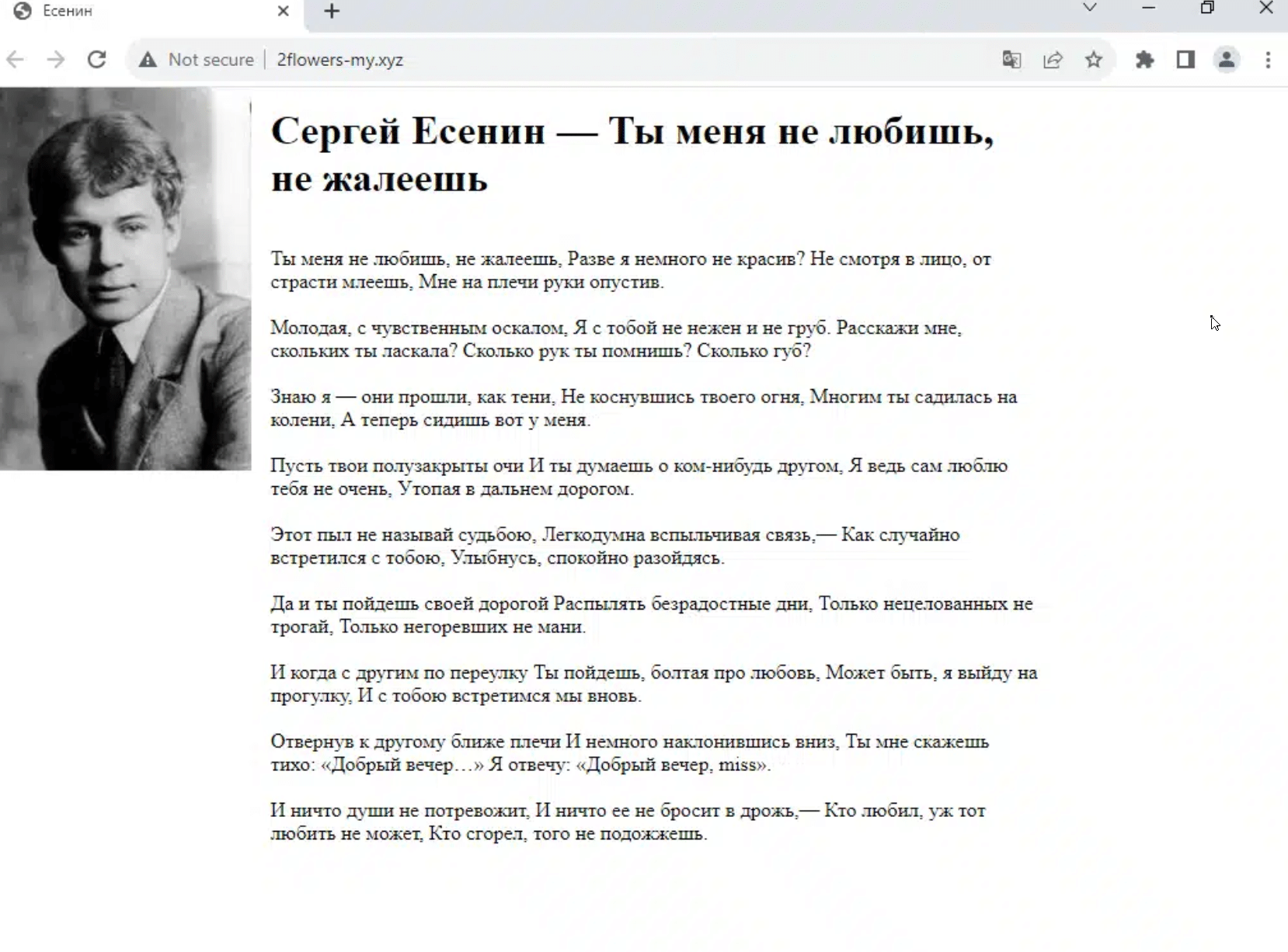
Russian-language Sergei Yesenin content on 2flowers-my[.]xyz
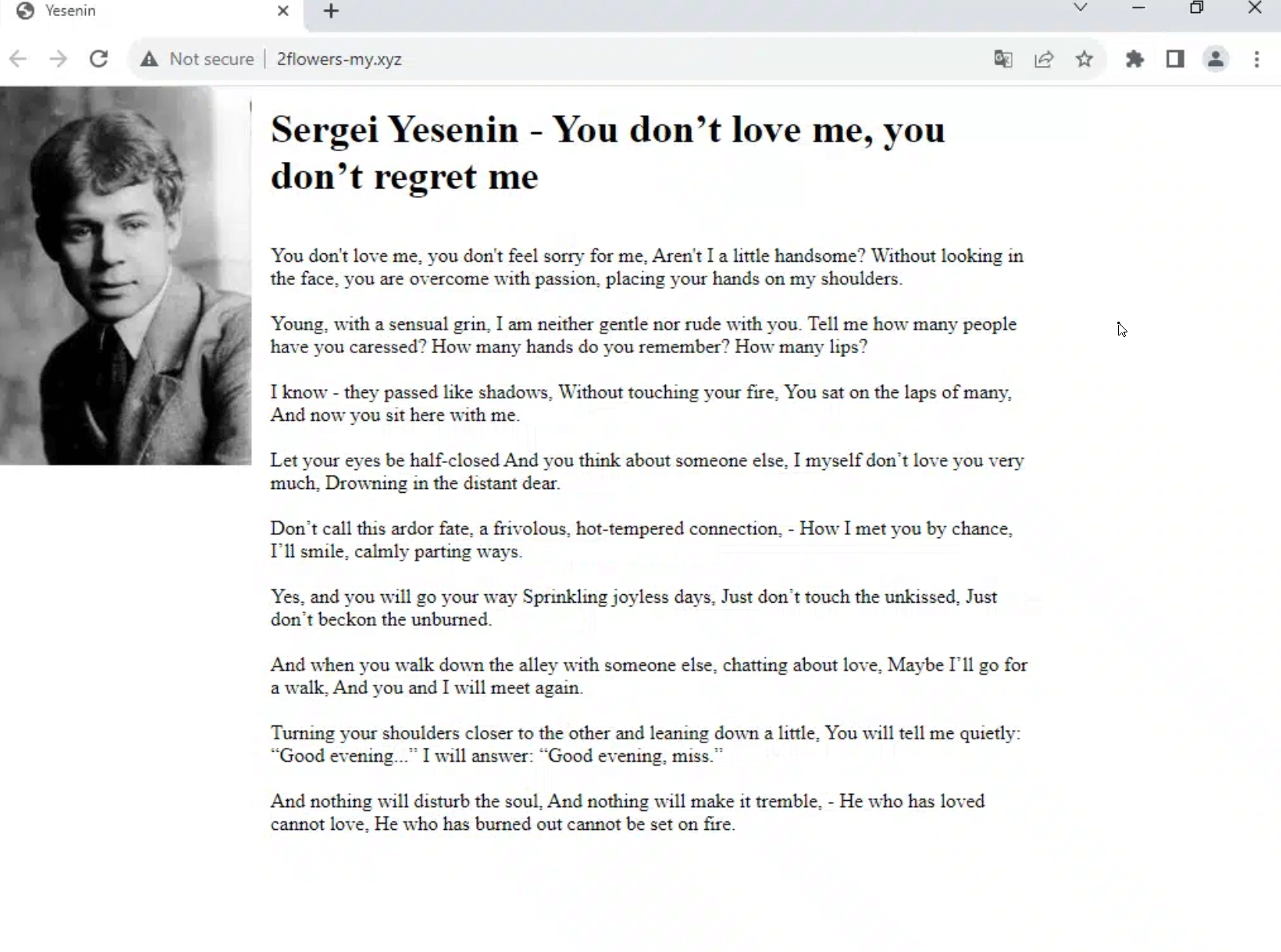
Translated Sergei Yesenin content on 2flowers-my[.]xyz
We initially hypothesized that that Lumma’s administrators had recently amended their C2 infrastructure to point at the Yesenin content to evade detection.
This piece of analysis, however, wasn’t entirely correct. Further investigation showed that some domains had actually shifted back from the Yesenin page to a Lumma control panel.
We used Sergei Yesenin’s “body” (OK, the page content, but it’s close enough!) to scan our database for Lumma C2 domains and IPs displaying the same content, leading us to 71 IOCs, 15 of which were still active.
We were able to confirm the link between these new domains and Lumma by cross referencing various pieces of DNS and WHOIS data with what we already knew about confirmed IOCs.
Most of the domains were proxied to Cloudflare, and had been registered on PDR in the past month, with a Gmail address as the registrant, but this time with a different prefix to levisrogers13 – kippjosephc@gmail.com:
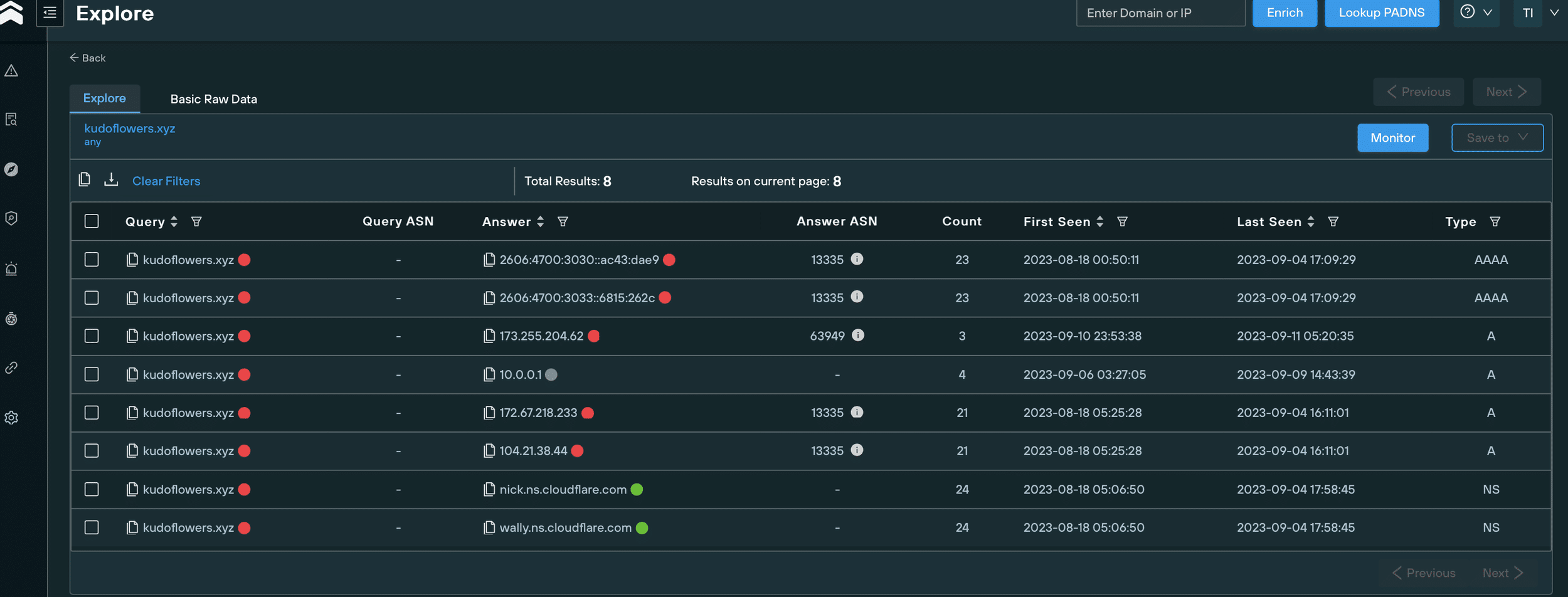
WHOIS information for Lumma C2 domain
Using a domain search query to pivot on this new email address, we uncovered 20 domains (none active) linked to Lumma, all of which had all been registered on since 19 August 2023 – as with the levisrogers13@gmail.com domains, all of them appear to be proxied to Cloudflare.
Obtaining non-proxied domain data
During our investigation, we noticed something odd about a group of 4 domains that shared a similair naming convention.
Contrary to the majority of Lumma C2 IOCs, this subset isn’t proxied to Cloudflare, which gave us all kinds of pivoting options that we weren’t able to use with the Cloudflare domains:
- lazagrc2cnk[.]xyz
- lazagrc3cnk[.]xyz
- ocmtancmi2c4t[.]life
- ocmtancmi2c5t.life
Either the attackers got sloppy, or deliberately left them unproxied for technical reasons. Either way, our old friend Mr Yesenin was able to confirm their involvement:
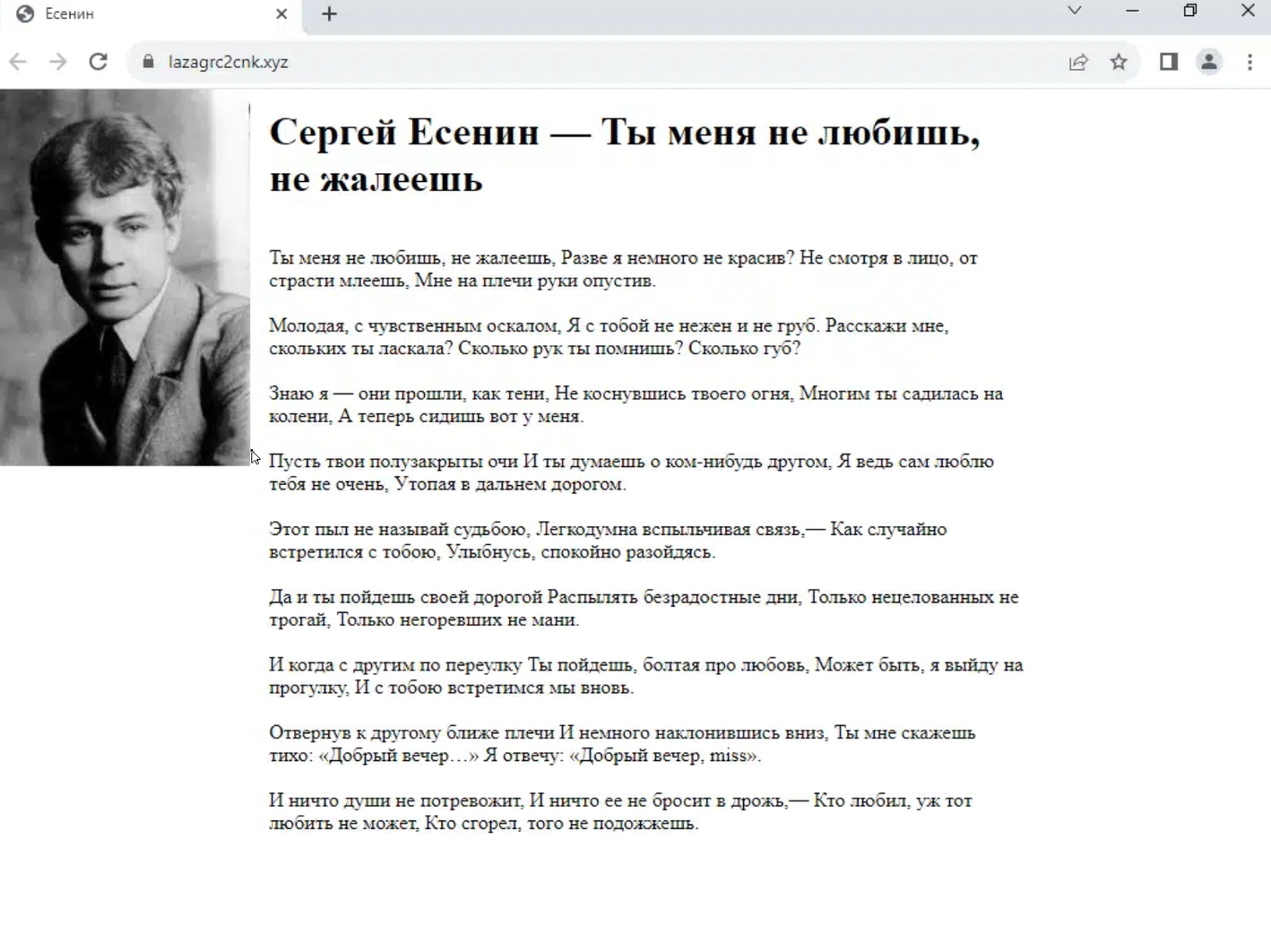
lazagrc2cnk[.]xyz unproxied C2 domain
OK, so now we had a workable subset, that we can use in conjunction with our scanned data to pivot through hosting information, and cross reference with known TTPs to locate additional infrastructure.
To begin, we took the above domain – lazagrc2cnk[.]xyz – and analyzed all the IP addresses that have ever hosted it since its creation, using the Silent Push IP diversity query:
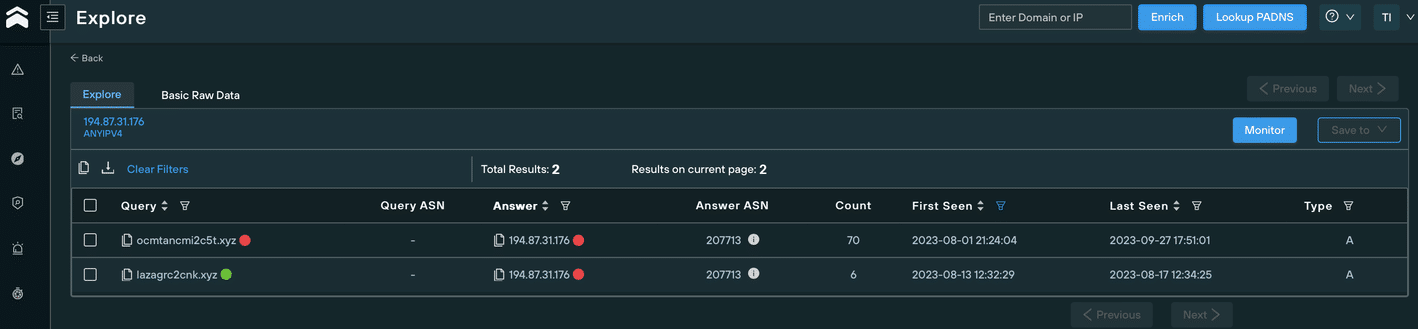
We discovered that in August 2023, it was hosted on 194.87.31[.]176, using the ASN AS207713 – GIR-AS, RU.
During the same period, another domain was hosted on the same IP and ASN that didn’t appear on the subset of 4, but still looked suspicious due to it’s similarity to known malicious domains: ocmtancmi2c5t[.]xyz.
Expanding the search with a regex
A quick regex search on ^ocmtancmi[0-9]c[0-9]t.[a-z]{1,}$ uncovered 8 new domains (a search on ^lazagrc[0-9]cnk.[a-z]{1,}$ yielded no results):
- ocmtancmi2c4t[.]live
- ocmtancmi2c4t[.]site
- ocmtancmi2c4t[.]website
- ocmtancmi2c4t[.]xyz
- ocmtancmi2c5t.[.]ive
- ocmtancmi2c5[.].ltd
- ocmtancmi2c5t[.]site
- ocmtancmi2c5t[.]website
We then started to wonder why these domains hadn’t appeared in our previous scans, detailed earlier in this blog.
The answer was immediately apparent – we hadn’t collected all of their WHOIS data, and the domains were not showing either Sergei’s poem or the Lumma control panel page, both of which we’d used to fingerprint the earlier C2 domains.
Instead of known malicious content, the domains displayed a standard 503 error:
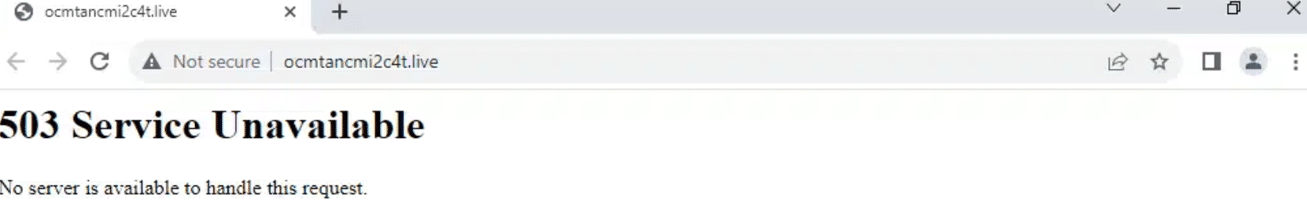
Error 503 on ocmtancmi2c4t[.]live
Traversing Lumma subdomains
We quickly noticed another differentiator that set these new domains apart from the bunch… they contained subdomains. As with the omission of a Cloudflare proxy, this afforded us even more opportunity to map out the attackers’ infrastructure.
Mass scanning of every subdomain alerted us to an open directory on stable4download.ocmtancmi2c5t[.]website, containing a new version of the infostealer:
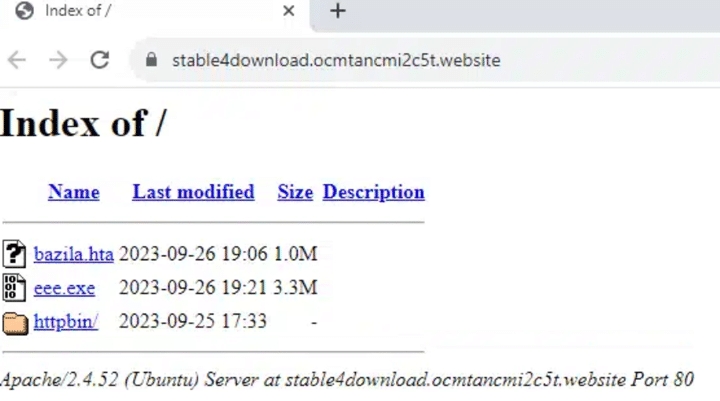
Open directory on stable4download.ocmtancmi2c5t[.]website
The open directory structure also revealed the use of malicious PNG files used for steganography purposes to deliver the payload, reminiscent of the Cold War-era microdots used to convey clandestine message between intelligence operatives.
Here’s an directory filled with microdotted PNG files on the aforementioned subdomain:
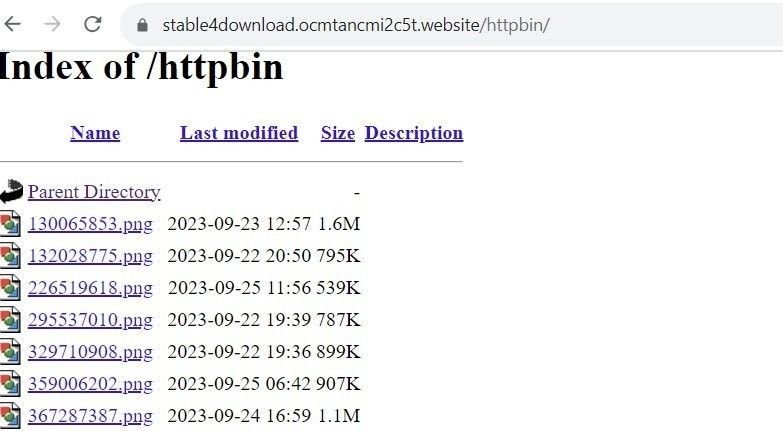
Use of steganography on stable4download.ocmtancmi2c5t[.]website
Malware analysis leads to 80+ new C2 servers
Over the past few days, several threat researchers reported the discovery of 3 new Lumma C2 domains, all proxied to Cloudflare and registered via PDR between 14-24 September 2023:
- treepledeeple[.]fun (email: lopotojoa@bk.ru)
- orkograkula[.]fun (email: kihogi-xuja49@mail.ru)
- firmpanacewap[.]fun (jabi_yipuwu39@inbox.eu)
Additional scans pinpointed two further domains, registered with the same timestamps using the same registrar (PDR), all proxied to Cloudflare:
- curtainjors[.]fun (email: lopotojoa@bk.ru)
- starblack[.]fun (email: jabi_yipuwu39@inbox.eu)
All of the above 5 domains display a “Welcome to nginx!” page:
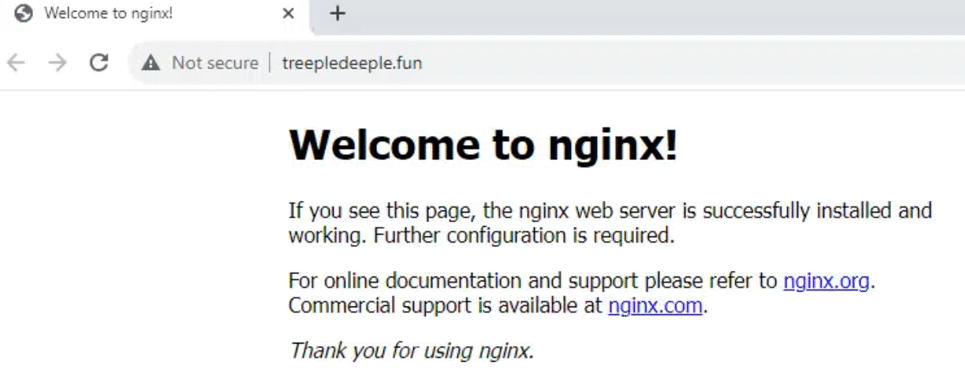
ngninx C2 page fortreepledeeple[.]fun
Earlier versions of Lumma feature a hardcoded configuration. Newer versions, however, use a different communication method.
We’re not able to divulge too much information about how we used the new infostealer version against itself, but our Threat Analysts were able to locate an entirely new threat landscape containing 86 previously unknown Lumma C2 domains operating the new version of the infostealer, all of them active, and most of them registered with personal email addresses which were sometimes shared between domains.
Not one of the discovered domains was flagged as malicious by Virus Total:
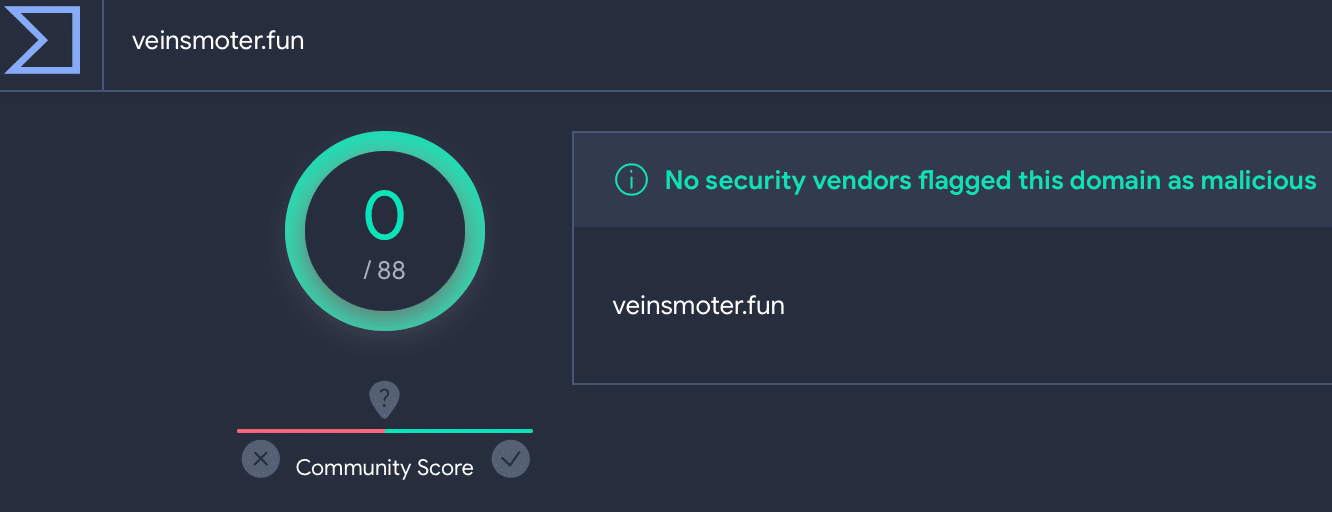
Lumma C2 veinsmoter[.] fun on VirusTotal4
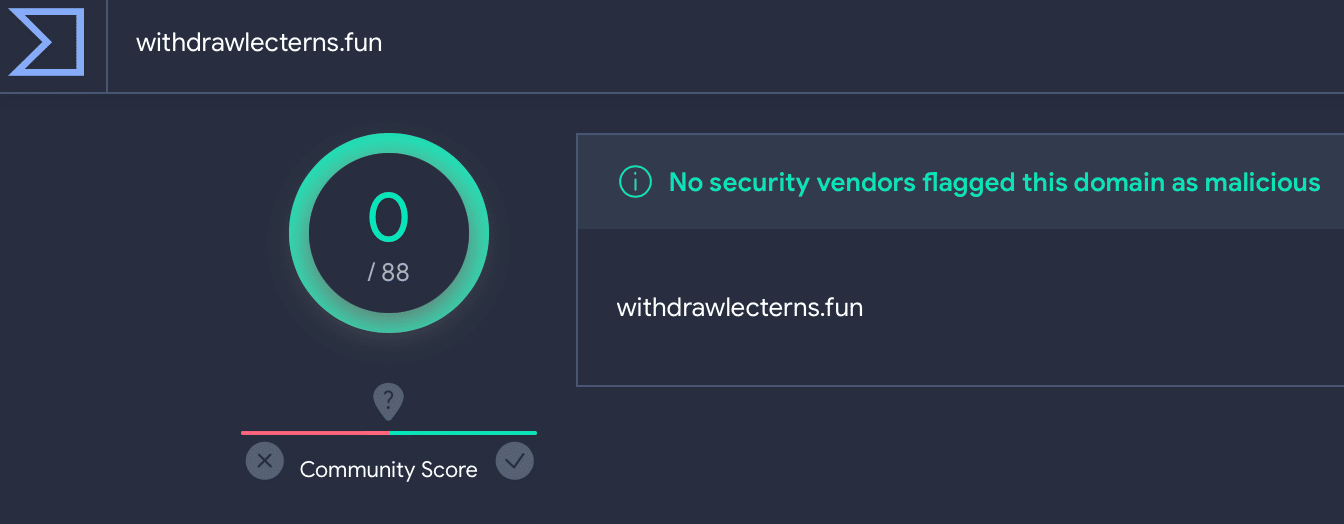
Lumma C2 withdrawlecterns[.] fun on VirusTotal
Some of the domains were hiding behind a Cloudflare captcha. Solving the captcha revealed that all of them were Lumma C2s:
Cloudflare captcha for chocomeat[.]fun
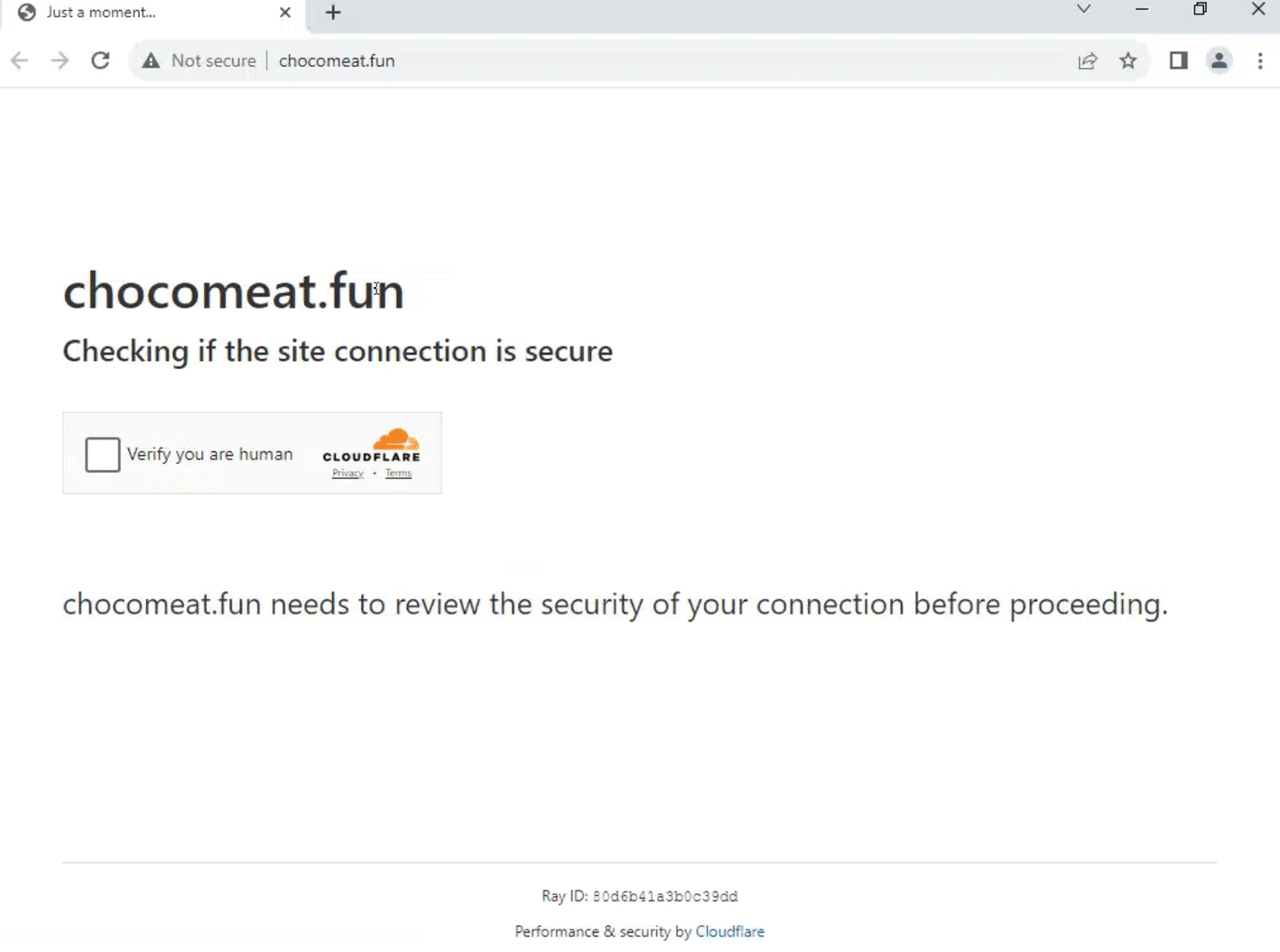
Cloudflare captcha for chocomeat[.]fun
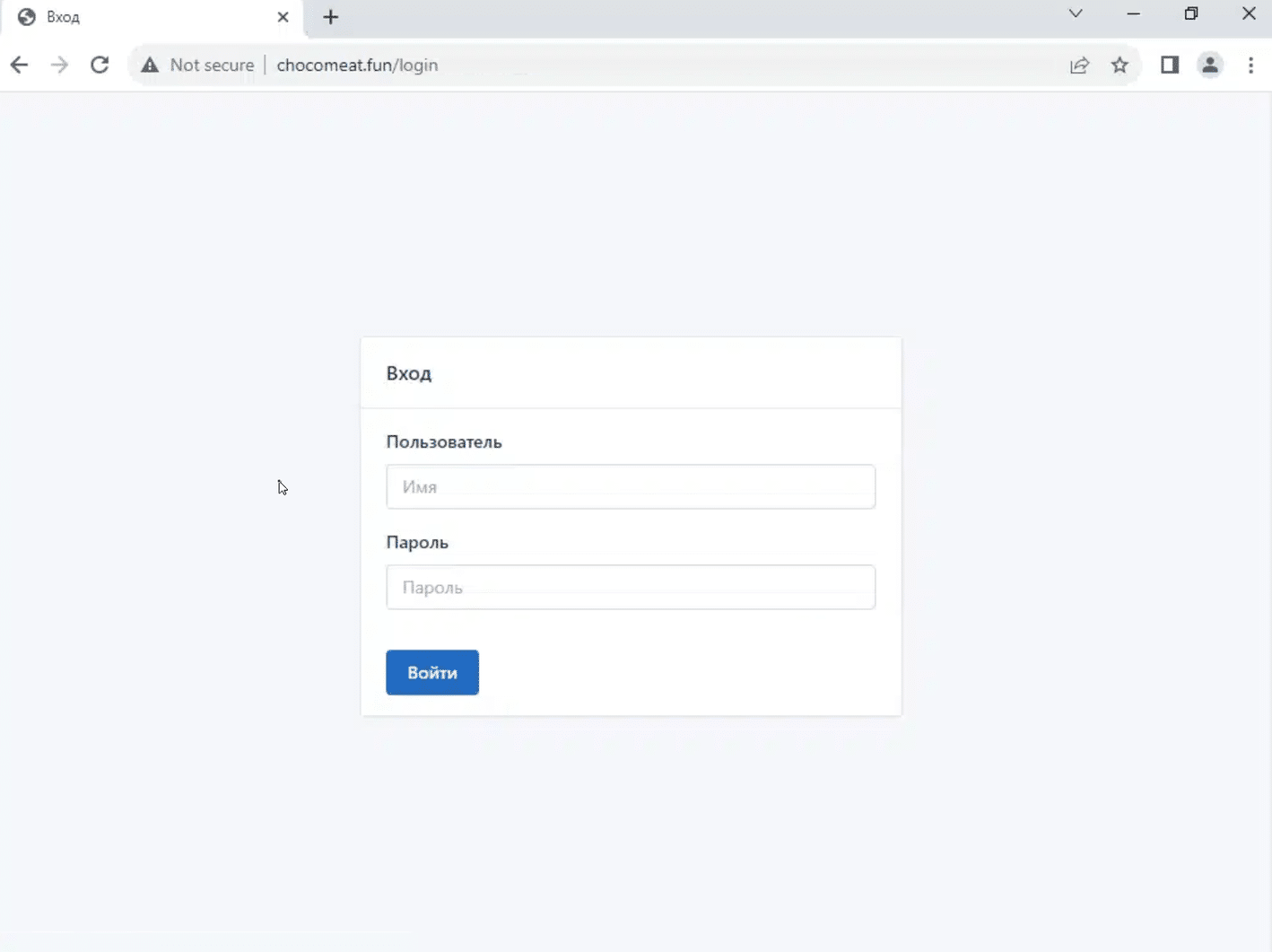
Solved Cloudflare captcha for chocomeat[.]fun/login, revealing Lumma C2
Conclusion
In this blog, we’ve shown how we took a single piece of data – a HTML header – and used our platform to extrapolate 150+ new C2 IPs, domains and control panel URLs, by focusing on how attackers deploy their infrastructure.
Malicious domains and IP addresses offer minimal insight to SOC teams and threat hunters when taken in isolation. Just like the punch that a boxer doesn’t see, the most injurious attacks originate from an unknown source.
Lumma feed data ingested into a SOAR/SIEM that relies on bare lists of C2 servers without any consideration of the underlying TTPs involved is borderline redundant once published, and it has to be said, significantly overvalued by the industry as a whole.
Lumma’s operators and administrators aren’t stupid. Immoral, but not stupid. They know full well when their infrastructure has been compromised, and they adjust their attack vectors accordingly to render most threat data relatively useless upon discovery – unless it’s part of a broader analysis that turns their own methods against them, and tracks their movement across the Internet.
That’s where we come in…
Silent Push maps attacker TTPs by building a behavioural fingerprint that’s aggregated, clustered, enriched, and scored to provide the most complete view of Lumma C2 activity available anywhere in the world.
Silent Push Enterprise customers have access to a bespoke Early Detection feed containing all the Lumma threat data we’ve referred to in this blog, plus any other Lumma IOCs we detect in subsequent scans. Email info@silentpush.com for more details.
The Silent Push Community Edition features many of the tools, lookups and queries that we used to track Lumma C2 infrastructure, including passive DNS lookups, domain pivots and a lot more. Register here for free.
Selected IOCs
Note: A full list of realtime curated IOCs is available as a feed, with a Silent Push Enterprise subscription.
157.90.248[.]179
195.123.219[.]211
195.123.219[.]212
213.252.244[.]62
89.185.84[.]37
2flowers-my[.]xyz
adavefrees[.]xyz
blockall-my[.]xyz
blockspam-my[.]xyz
bondappeal[.]xyz
boxclod[.]xyz
buyerbrand[.]xyz
catfoodbio[.]xyz
chocomeat[.]fun
cleanvr[.]xyz
cloudsnike-my[.]xyz
coinflore-my[.]xyz
coolworks[.]xyz
coolworkss[.]xyz
cosmosvr3d[.]xyz
culturalevenings[.]xyz
cvadrobox[.]xyz
damageagio[.]xyz
deeppoetry[.]xyz
demanddeal[.]xyz
diavellipromo-my[.]xyz
dogshanter[.]xyz
downloaddedattre[.]fun
downloadfiles-my[.]xyz
dromautocar[.]xyz
dropfiles-my[.]xyz
ducklingibises[.]fun
ellifotolive[.]xyz
glaziercarde[.]fun
housegrommy[.]fun
jumperstad[.]fun
lackbasinmu[.]fun
pearlbarleyhit[.]fun
politicuseles[.]fun
portlandcor[.]fun
potatomeatball[.]fun
pregnantflowers[.]fun
rarefood[.]fun
rosaryconbo[.]fun
rovengold[.]fun
royalpantss[.]fun
satanakop[.]fun
sausagerollraisin[.]fun
scruffymapleflat[.]fun
sendcyniaforeign[.]fun
shoppervik[.]fun
slimtvsocico[.]fun
socialmadness[.]fun
sodafountainpr[.]fun
startablekor[.]fun
superyupp[.]fun
talkinwhitepod[.]fun
tuberoseprod[.]fun
valleydod[.]fun
veinsmoter[.]fun
waterparkedone[.]fun
withdrawlecterns[.]fun
wolffunny[.]fun
yachtracingopt[.]fun

