Lumma Stealer Malware Thrives as Silent Push Uncovers Unique Patterns in the Infostealer's Domain Clusters

Key Findings
- We found Lumma Stealer command and control (C2) domain clusters share certain technical characteristics that enabled our team to map entire clusters of the infostealer’s infrastructure.
- Lumma Stealer logs are being shared for free on Leaky[.]pro, a relatively new hacking forum, offering billions of “URL:LOG:PASS” records with specific details tied to stolen credentials.
- The increase in malware being spread via malicious YouTube links and infected files disguised in videos, comments, or descriptions is alarming. Viewers should be skeptical of unverified sources when interacting with YouTube content, particularly when prompted to download or click on links.
Table of contents
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Account
- Lumma Stealer Background
- Exploring Lumma Stealer Practices
- Initial Intelligence: Lumma Stealer Logs’ Distribution
- The Fake Booking “ClickFix” Technique to Deliver Lumma Stealer
- Following the Surge of Malware as Fake Exploits Fuel Massive Infections through Malicious Sites and YouTube
- Unique Lumma Stealer Poem Leads to SecTopRAT Malware
- Lumma Stealer Malware Spread Through Cloudflare and MediaFire
- Lumma Stealer C2 Domain Clusters
- Additional Information: Continuing to Track Lumma Stealer
- Mitigation
- Register for Community Edition
- Sample Lumma Stealer Indicators of Future Attacks (IOFAs)
Executive Summary
Silent Push Threat Analysts recently expanded on our previous research on “Lumma Stealer” infostealer malware from January of last year. Among the new discoveries, our team found Lumma Stealer logs are being shared for free on Leaky[.]pro, a relatively new hacking forum.
Difficult to detect and prevent, Lumma Stealer malware is spread through various platforms such as video-sharing sites, file-sharing services, and directly through malicious websites. Lumma Stealer infections typically act as enablers for more extensive attacks, including the deployment of ransomware and espionage operations, where attackers gather intelligence or steal intellectual property.
Our team discovered that Lumma Stealer C2 domain clusters are frequently registered in quick succession and, in many cases, appear to be handled via an automated process. These clusters and infrastructure expansion techniques share certain characteristics that our threat analysts have combined to fingerprint Lumma Stealer infrastructure.
The ever-evolving nature of Lumma Stealer campaigns, which often lead to widespread infections, outlines the need for robust, industry-wide cybersecurity measures to mitigate the potential damage they can cause. Frequent targets include YouTube, the content delivery network (CDN) Cloudflare, and the file-sharing platform/cloud storage company MediaFire. These companies cannot fight this threat alone, however, so Silent Push Threat Analysts are sharing our latest research to help defenders mitigate and prevent the spread of Lumma Stealer infections.
Sign Up for a Free Silent Push Community Account
Register now for our free Community Edition to use all the tools and queries mentioned in this blog.
Lumma Stealer Background
Lumma Stealer was first seen on Russian-language criminal forums in 2022. It continues to be sold under the “Malware-as-a-Service” business model, with different pricing tiers for threat actor operations of varying sizes. From 2023 onward, the number of compromises linked to Lumma Stealer has risen dramatically, particularly those including the resale of stolen credentials to other criminals.
“Infostealer” malware, like Lumma Stealer, refers to malware designed primarily to collect sensitive information (login credentials, browser history, credit card details, and other personal data) from infected systems. Lumma Stealer goes even further, targeting web browser information (cookies, history, extensions, and saved passwords), chat logs, details about installed programs, stored financial information, and even cryptocurrency wallet data. Lumma also targets multiple versions of the Windows operating system.
Malware distribution mechanisms for Lumma Stealer vary greatly depending on the motivation of the specific operator deploying it. Cybercriminals use “stealer logs” (files generated by malware like Lumma Stealer with sensitive information from compromised systems) to exploit stolen data for all types of fraudulent activities, including identity theft. The most effective campaigns seen by our team thus far have also utilized “malvertising” (malicious advertisements) on popular search engines and “malspam” (malicious spam emails) containing harmful attachments.
Building on our initial research back in September of 2023, where we uncovered a trove of active Lumma C2 servers and admin panels as shared in our blog, “The Dead Russian Poets Society: Silent Push Uses Behavioral Fingerprinting, Content Scans, and a 128-year-old Russian Poem to Uncover 150+ New ACTIVE Lumma C2 Servers and Admin Panels,” our team published additional research in January 2024 on the discovery of Lumma Stealer C2 and control panels hosted on Cloudflare infrastructure.
In this latest report, our threat analysts observed that threat actors using Lumma Stealer appear to register clusters of roughly 10-20 domains at a time, some of which are used immediately and others that are left to age for up to two weeks. Knowing this, we can then search for and unearth the “aging” domains if even one of the active domains can be found.
Our team believes readers of this report should be aware of the increase in malware spread via YouTube. Malicious links and infected files are often disguised in videos, comments, or descriptions. Exercising caution and being skeptical of unverified sources when interacting with YouTube content, especially when prompted to download or click on links, can help protect against these growing threats.
Note: Our threat analysts have noticed malicious actors often change their infrastructure and tactics based on the details included in our public blog posts, so we have omitted many of the key details needed to circumvent detection from this post for operational security reasons. Enterprise customers have access to a fully detailed report on Lumma Stealer’s methods as well as IOFA feeds that enable easy blocking of all associated infrastructure.
Exploring Lumma Stealer Practices
Initial Intelligence: Lumma Stealer Logs’ Distribution
Silent Push Threat Analysts discovered a user, “zhack,” on the popular hacking forum BreachForums, who was advertising and distributing Lumma Stealer logs.
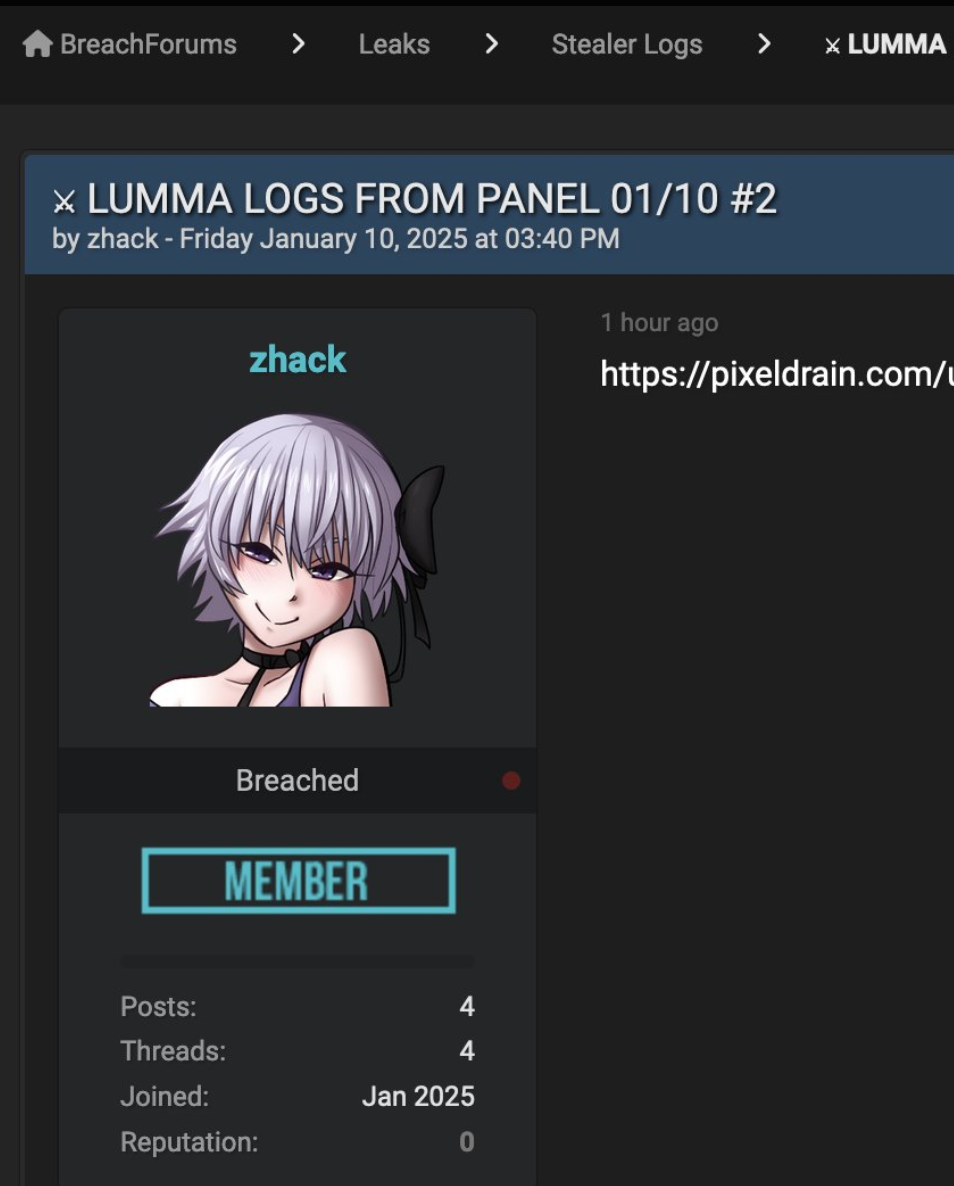
![The site leaky[.]pro was advertised within the logs](https://www.silentpush.com/wp-content/uploads/lumma-s-leaky-pro-image-2.png)
The hacking forum leaky[.]pro was relatively new. The administrator made the first post on 12/29/2024 under the name “fijiwater.”
![Screenshot of Leaky[.]pro administrator "fijiwater"](https://www.silentpush.com/wp-content/uploads/lumma-s-fijiwater-image-3.png)
The screenshot below shows a user on the Leaky[.]pro forum advertising three billion records of “URL:LOG:PASS” that refer to stealer logs with specific website URLs tied to logins (LOG) and passwords (PASS) of stolen credentials.
![A leaky[.]pro forum user advertised 3,000,000,000 URL:LOG:PASS records](https://www.silentpush.com/wp-content/uploads/lumma-s-leaky-pro-urllogpass-image-4.png)
The Fake Booking “ClickFix” Technique to Deliver Lumma Stealer
Silent Push Threat Analysts know that organizations and sites with large user bases are commonly victims of phishing and malware campaigns. Our team was able to create a proprietary fingerprint based on observation of these campaigns that detects a large number of phishing pages, including those located on a suspected bulletproof host.
Delving deeper into these suspicious booking pages our team quickly found they were delivering Lumma Stealer through a fake Cloudflare CAPTCHA, an example of which can be seen below.
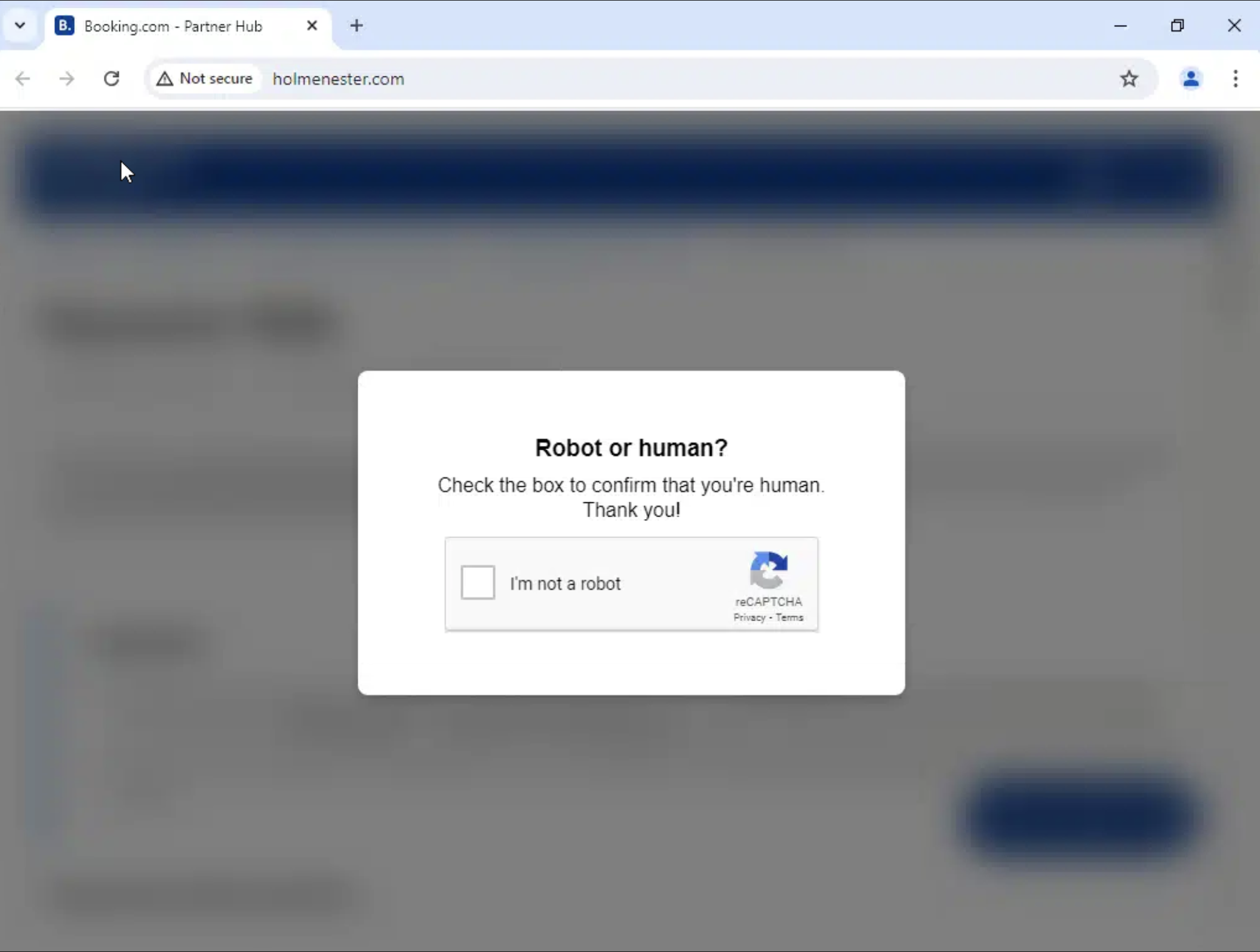
After checking the box for “I’m not a robot,” this message popped up:
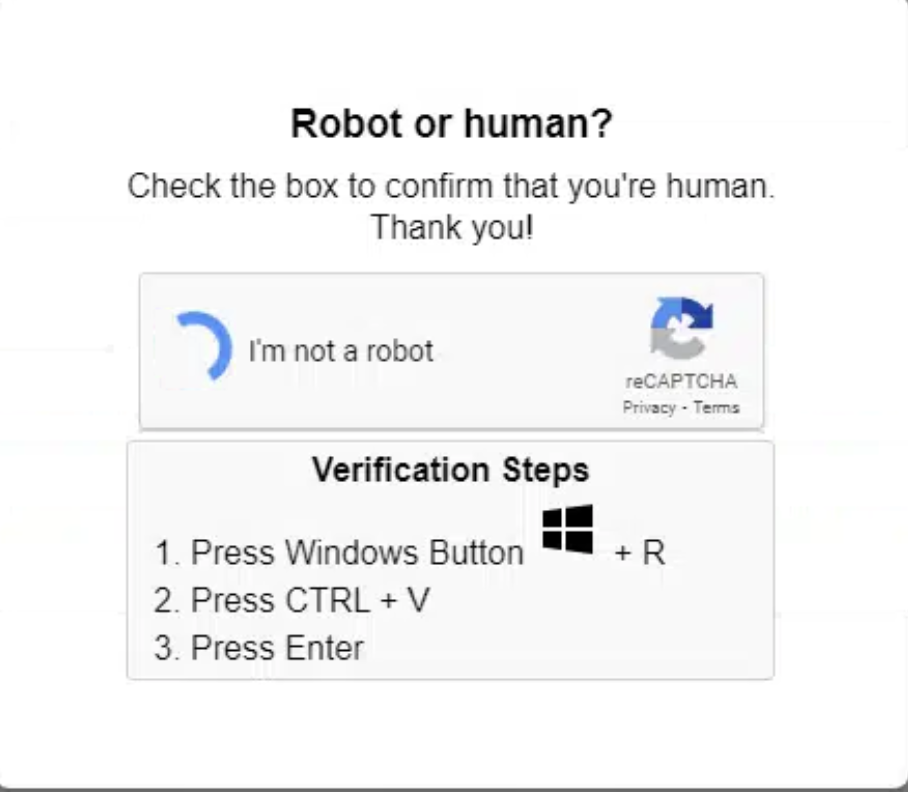
The presence of “I am not a robot – reCAPTCHA Verification ID: 8731” within the URL suggested that the malware may have attempted to deceive security systems or users by mimicking legitimate reCAPTCHA verification processes, making it appear as though the .HTA file was part of a standard web interaction.
This technique, also known as “ClickFix,” involves cybercriminals creating fake CAPTCHA pages, often mimicking Cloudflare’s verification system, to trick users into running malicious code. The malware can steal sensitive data, including login credentials, or install harmful software.
Following the Surge of Malware as Fake Exploits Fuel Massive Infections through Malicious Sites and YouTube
Silent Push Threat Analysts detected a Lumma Stealer sample being spread through the interactive online malware analysis sandbox, any[.]run. We then expanded our search within our platform and were able to pivot toward more malicious infrastructure spreading Lumma Stealer.
![We detected a Lumma Stealer sample in the any[.]run platform](https://www.silentpush.com/wp-content/uploads/lumma-s-any-run-image-7.png)
Using information derived from this sample, “roxplo1ts[.]ws:443/wave,” our team was able to create yet another proprietary fingerprint that led to more malicious infrastructure.
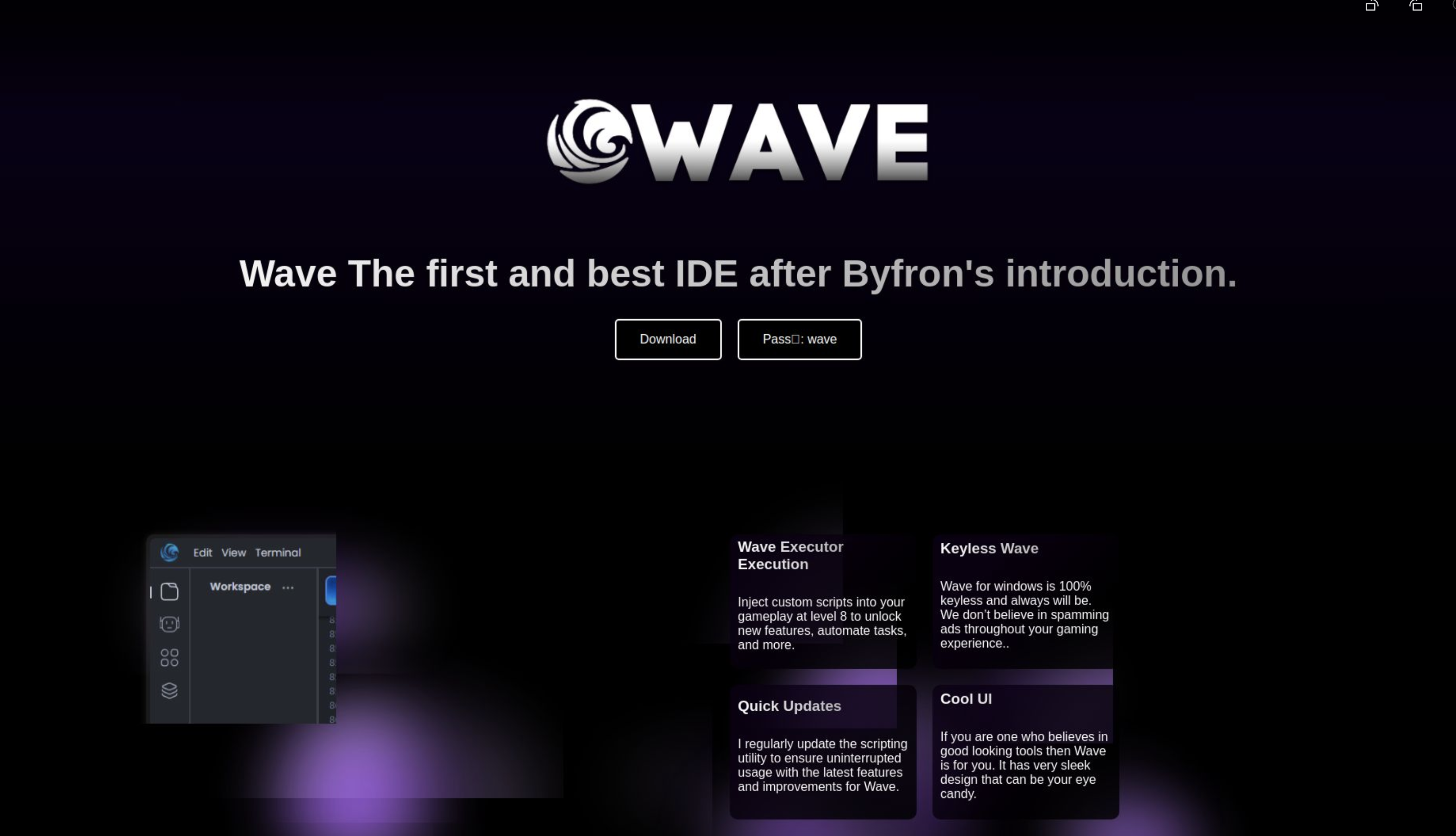
These domains revealed an interesting HTML title, “Roblox #1 Xeno Executor,” that can be readily searched upon with our Silent Push Web Scanner. This campaign appeared to be targeting children who play the Roblox game, which had roughly 164 million monthly active users in 2020. By focusing on the HTML title used here, we were able to combine additional technical details to create yet another effective fingerprint.
A YouTube search using the various pieces of information derived from our searches within the Silent Push Web Scanner revealed a disturbing number of YouTube videos spreading malware through MediaFire links. These videos also appeared to be from compromised accounts that were, themselves, victims.
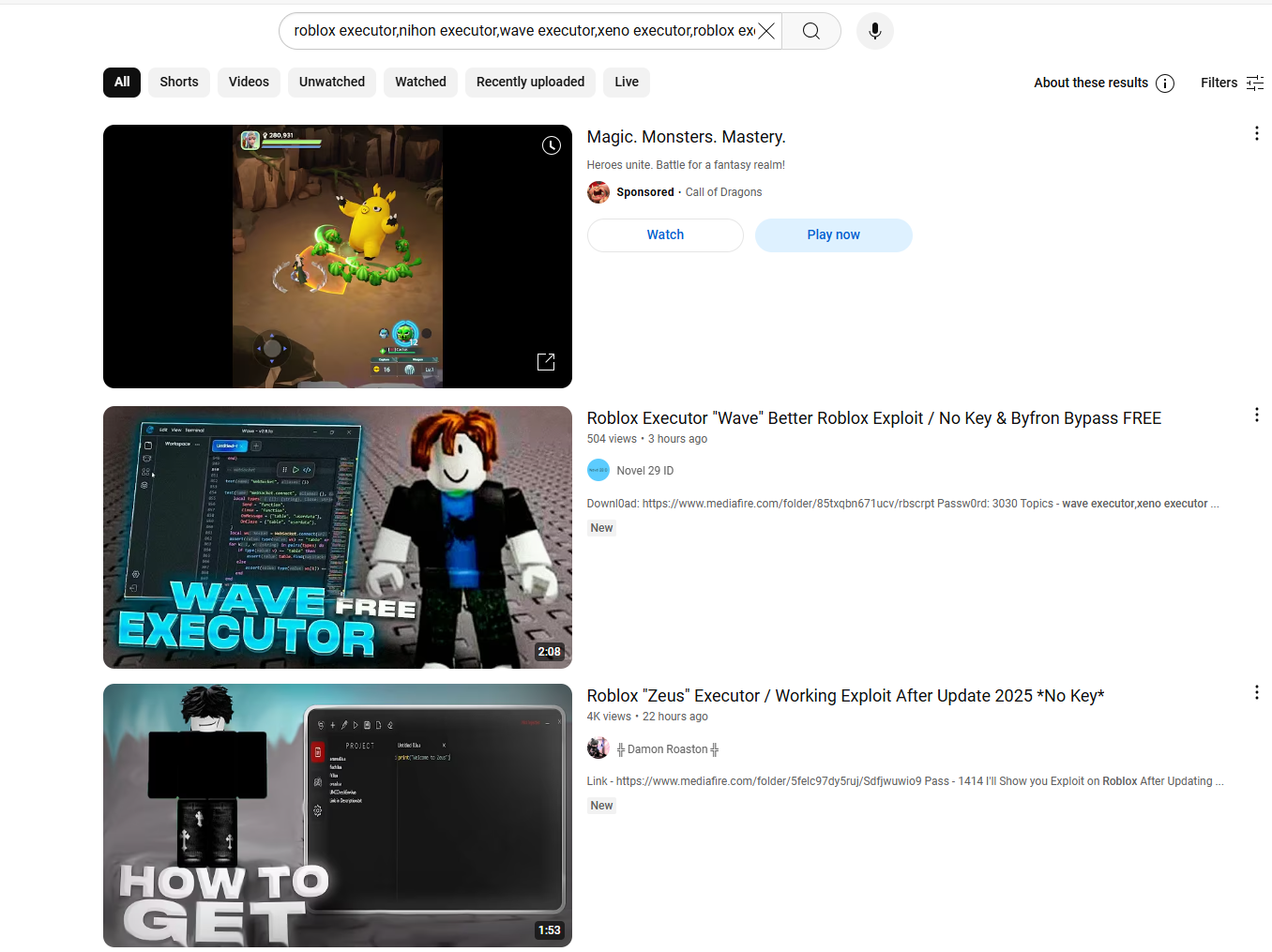
In testing one of these examples, youtube[.]com/watch?v=d_D4kgSVDIk. Our team noted a description which led potential victims to a download link hosted outside of YouTube, along with suspect hashtags included in the description. That link took victims to the external site: “deckarenids[.]com/roblox-executor”.
![Description from the suspicious video: youtube[.]com/watch?v=d_D4kgSVDIk](https://www.silentpush.com/wp-content/uploads/lumma-s-youtube-roblox-description-image-10.png)
This follows the same pattern we have previously observed with Lumma Stealer; however, in this case, before downloading the suspicious file, the victim was required to watch a YouTube video. This strongly suggested that the threat actors were using this tactic to harvest views and manipulate the YouTube algorithm.
![A visitor to lootdest[.]org/s?4d456215 was required to watch a YouTube video to unlock the content](https://www.silentpush.com/wp-content/uploads/lumma-s-declaremods-roblox-image-11.png)
We determined the suspicious file, seen here on Virus Total, was not actually Lumma Stealer. This indicated other methods are also being utilized by these actors in order to spread their campaigns. Bearing this in mind, our team was able to produce additional unique fingerprints to hunt for similarly suspect sites that may spread either Lumma Stealer or other types of malware.
Given the large scale of activity, our team is monitoring these results carefully and continuously iterating upon our fingerprinting techniques in order to stay ahead of the threat actors regardless of the type of malware used.
Unique Lumma Stealer Poem Leads to SecTopRAT Malware
In 2023, Silent Push wrote about threat actors using a Russian poem titled “The Curious Case of Sergei Yesenin’s Body Data” in our blog, “The Dead Russian Poets Society: Silent Push Uses Behavioral Fingerprinting, Content Scans, and a 128-Year-Old Russian Poem to Uncover 150+ New ACTIVE Lumma C2 Servers and Admin Panels.”
In our earlier research, we hypothesized that Lumma Stealer’s administrators amended their C2 infrastructure to point at the generic Russian poem based on some sort of personal preference. Further investigation showed that some domains shifted from the poetry page to a Lumma Stealer control panel. We thus used the content of the poetry page to scan our database for Lumma C2 domains and IP addresses displaying the same content.
What we observed is over the last few years this threat actor group has changed the unique poem we had originally (and have) been tracking.
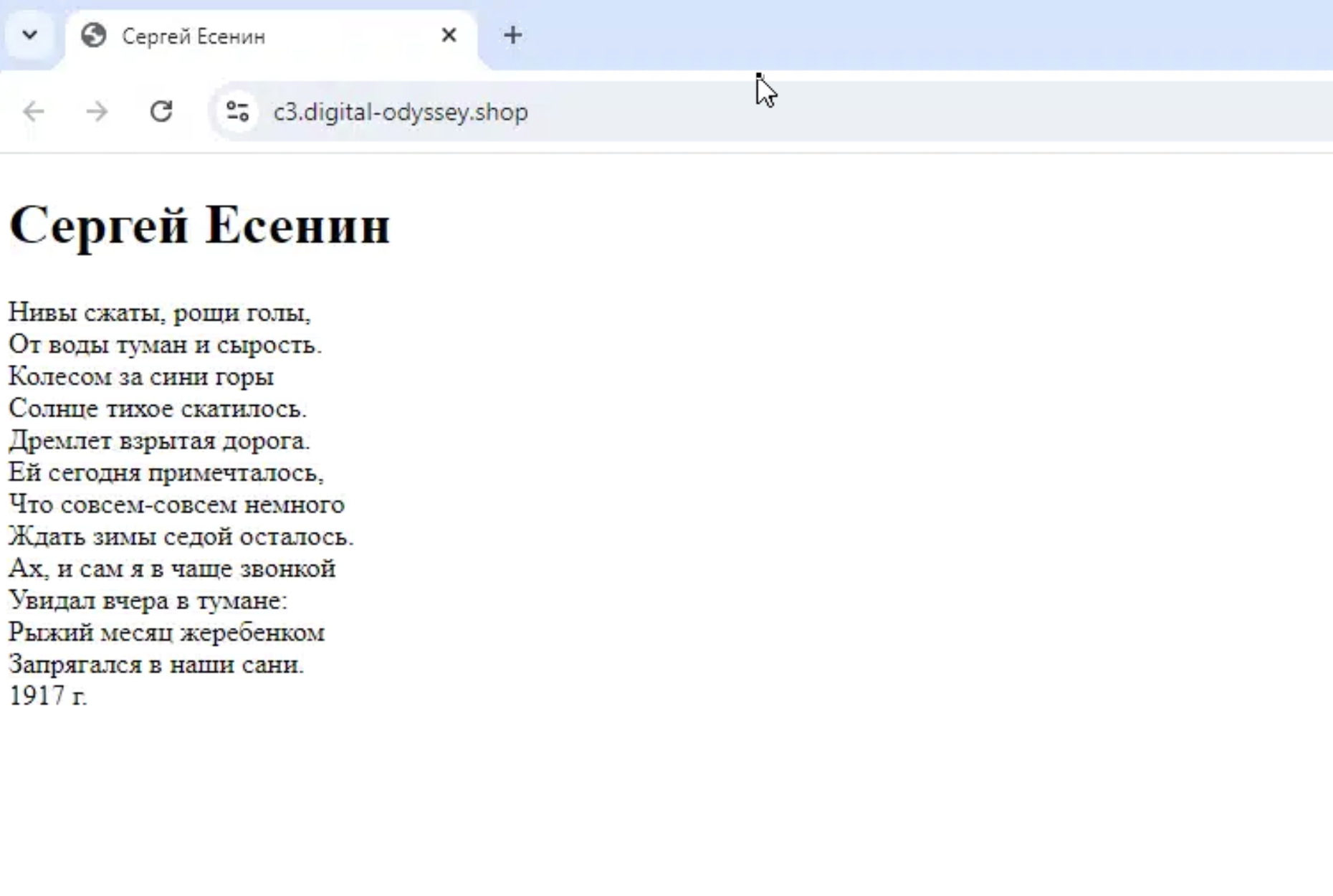
All domains identified using this Russian poem were then further analyzed, allowing us to create yet another unique fingerprint to identify Lumma Stealer infrastructure. The web page of one, “docu-signer[.]com”, began with the following information thrust up on the screen:
![Docu-signer[.]com web page](https://www.silentpush.com/wp-content/uploads/lumma-s-docu-signer-pdf-image-13.png)
In the next step, the visitors are instructed to download a malicious “PDF,” seen here in Virus Total.
![The page docu-signer[.]com downloads a malicious PDF](https://www.silentpush.com/wp-content/uploads/lumma-s-docu-signer-pdf-instrucutions-image-14.png)
This particular file is actually a Windows shortcut “LNK” file, and on further examination of the file and the associated email, our threat analysts determined it was malware that made use of SecTopRAT as a C2.
*Note: Our team is conducting an ongoing investigation to determine the connection between SecTopRAT C2 and Lumma Stealer and will share our findings as we determine more.
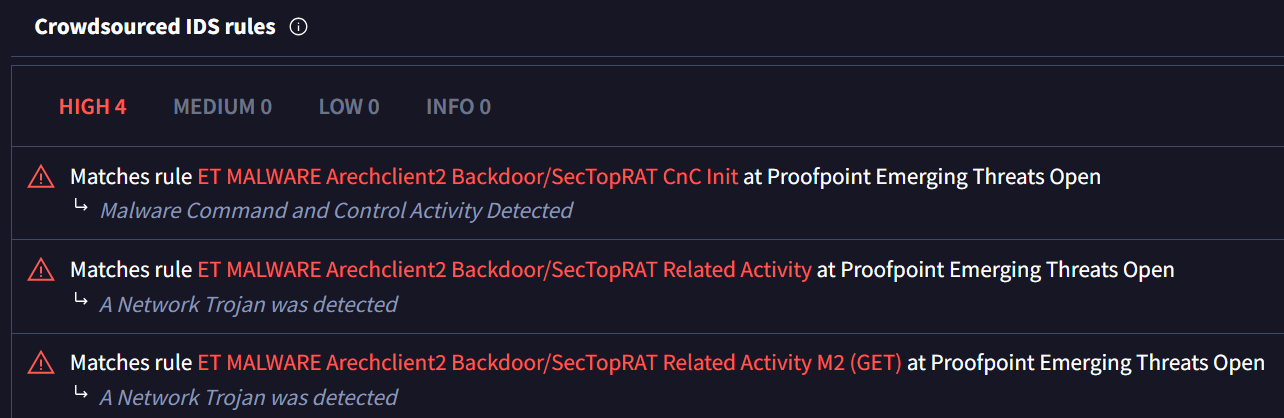
Lumma Stealer Malware Spread Through Cloudflare and MediaFire
A well-known security researcher that goes by the name of Fox_threatintel on X (formerly Twitter) (https://x.com/banthisguy9349/status/1866434351614796165) tagged the Silent Push Threat Intelligence Team in a post pointing out suspicious clusters spreading MediaFire links with password protection on the .zip archives through Cloudflare hosted sites.
Examining the associated infrastructure revealed multiple methods by which our team was able to fingerprint it, leading to further clusters of infrastructure spreading Lumma Stealer.
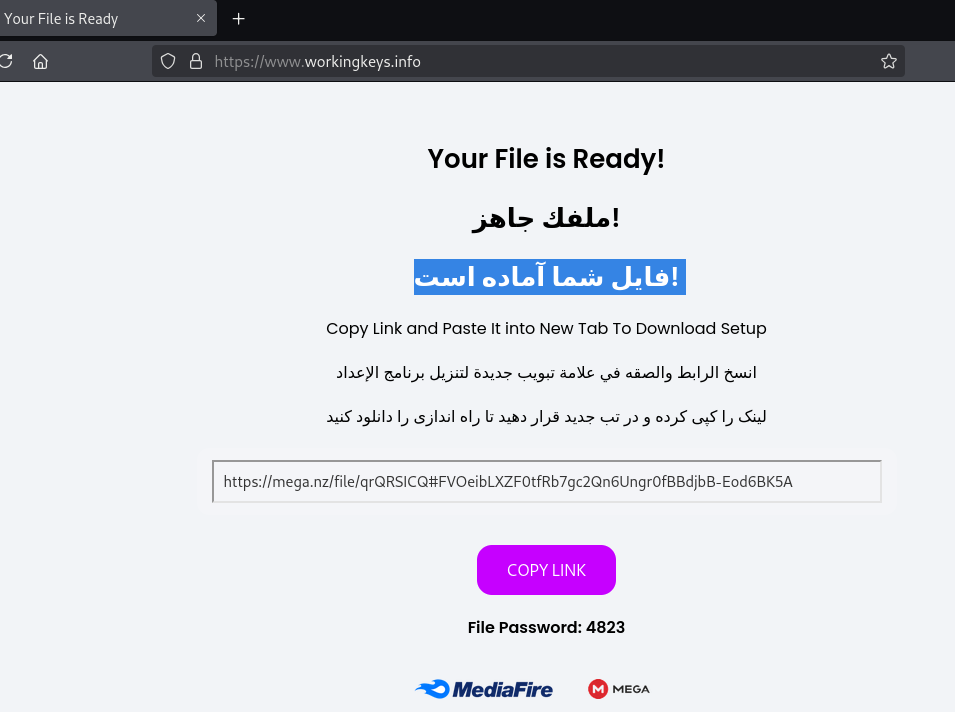
Three additional clusters were found through the information contained in the Fox_Threatintel post. From those, we were able to create unique fingerprints to identify each as they continue to spread and evolve.
![New Lumma Stealer C2 login panel on mikhail-lermontov[.]com](https://www.silentpush.com/wp-content/uploads/lumma-s-new-login-panel-image-18.png)
Said results also displayed infrastructure details consistent with those we shared in our public blog on Lumma Stealer in 2023, which was nice confirmation of the effectiveness of our current methods.
![Older version of Lumma Stealer login panel on 213.252.244[.]62](https://www.silentpush.com/wp-content/uploads/lumma-s-old-login-russian-panel-image-19.png)
Lumma Stealer C2 Domain Clusters
Pivoting on a confirmed Lumma domain within our WHOIS scanner revealed additional details our team was able to use across multiple results, many of which were marked as Lumma Stealer C2s in public sources. We noted similarities in the resulting domains’ names as well as reuse of top-level domains (TLDs) such as “.pro”, “.shop”, etc..
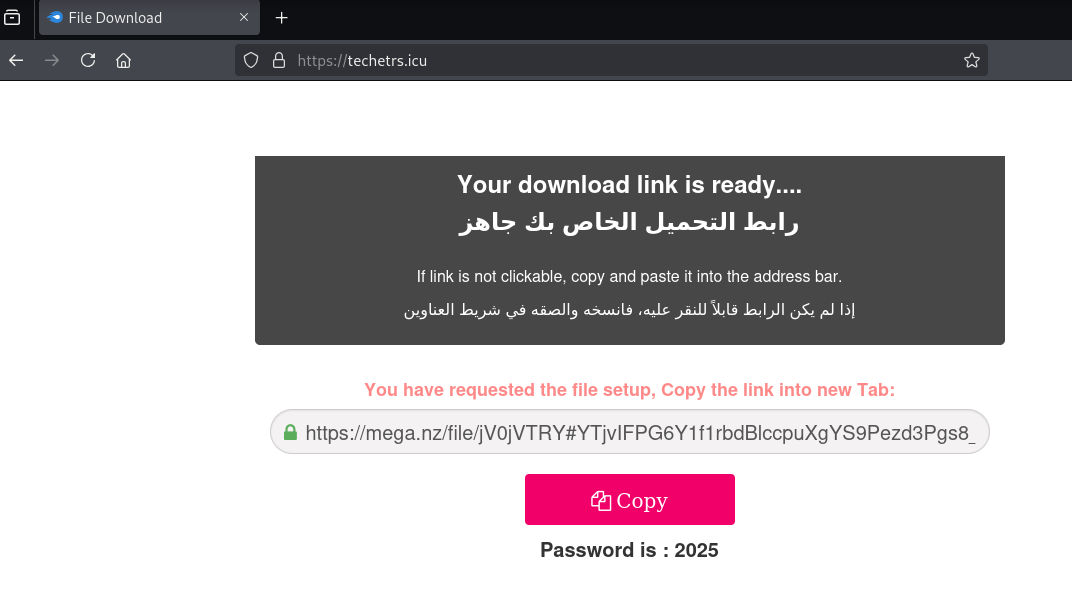
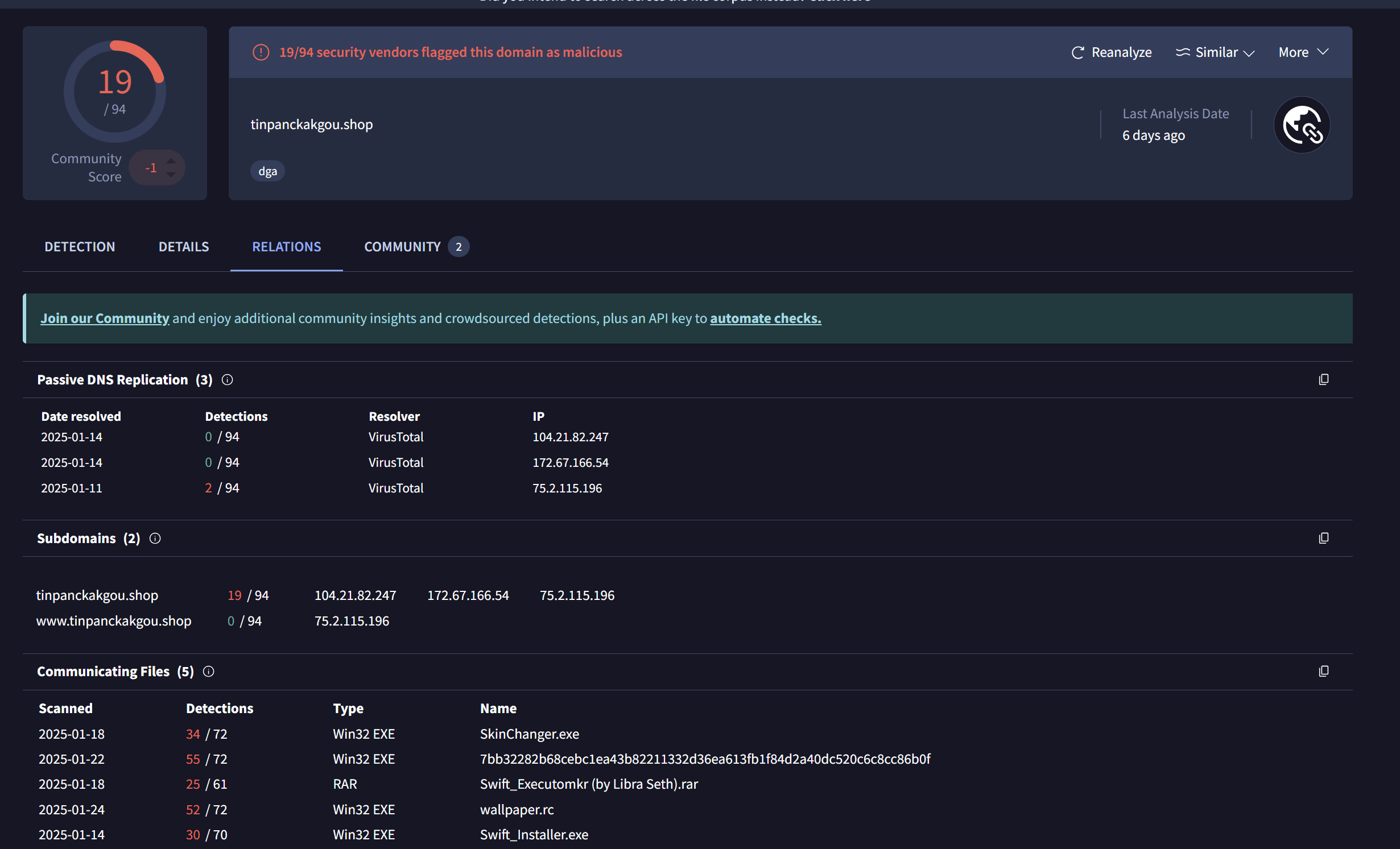
Below is an example of one of the new results, tinpanckakgou[.]shop (source: VirusTotal) that was marked as “malicious” by 19 different vendors. The domain had multiple communicating files containing Lumma Stealer. This provided additional confidence that the results of this cluster were related to Lumma Stealer.
Expanding upon that cluster revealed more than 60 results, all of them featured the same naming schema and a TLD of “.shop.” Additional discoveries were made at this stage, but are too sensitive to refer to publicly without tipping off the threat actors. Suffice to say a significant number of the new results were linked to Lumma Stealer samples, though they showed fewer hits on VirusTotal.
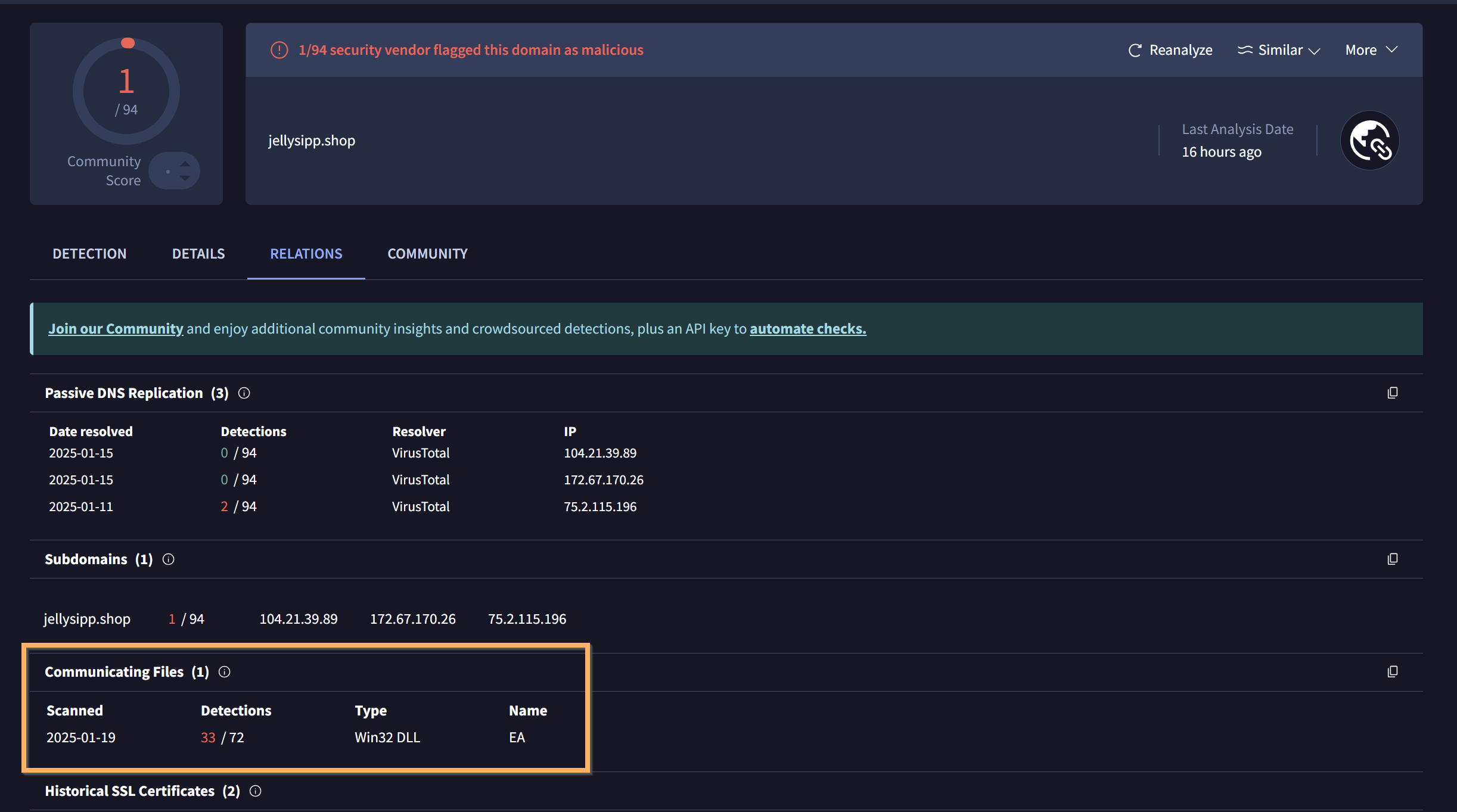
In many cases, we saw domains marked as “clean” elsewhere, which our research team was able to confirm internally as Lumma C2 domains.
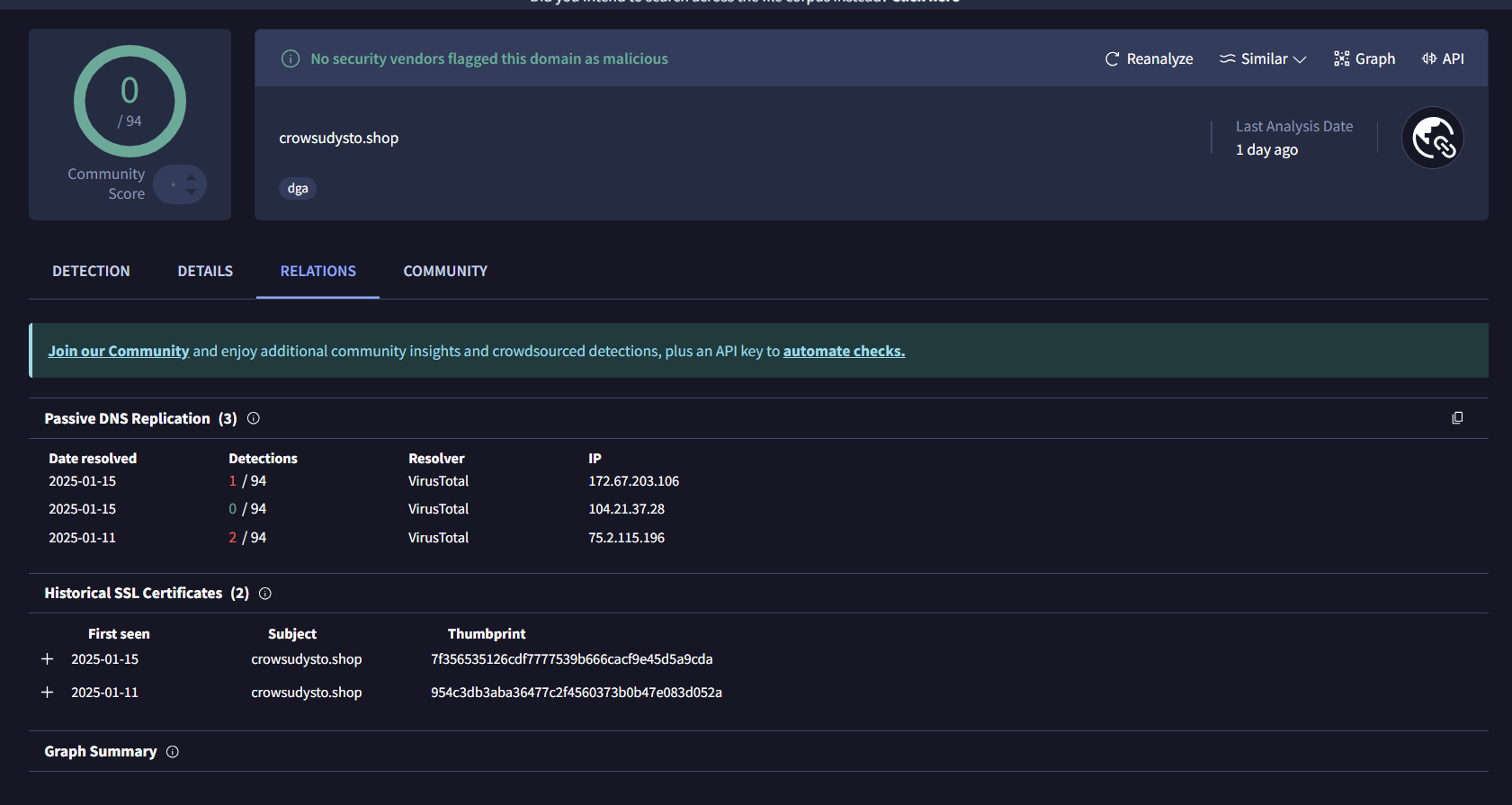
It is evident from these results that VirusTotal and other antivirus vendors are often unable to promptly or proactively flag Lumma Stealer domains. This underscores the need for pre-emptive threat intelligence, which focuses on the discovery of infrastructure prior to activation for malicious use. With our data, one can effectively detect entire clusters of Lumma Stealer C2 domains the moment they are actively weaponized.
Silent Push shines in our capability to quickly identify and respond to emerging threats, providing clients with the enhanced level of security they expect in this era of rapidly scaling and emerging threats. Rest assured that our threat analyst team continues to work to stay ahead of attackers, and our IOFA feeds are continuously updated as new tactics, techniques, and procedures (TTPs) are observed.
Additional Information: Continuing to Track Lumma Stealer
As referenced before, key technical information has been omitted from this public blog for operational security.
We have published a TLP:Amber report for our Enterprise users that contains links to the specific queries, lookups, and scans we’ve used to identify and traverse Lumma Stealer infrastructure—including proprietary parameters that we’ve omitted from this blog for security reasons.
Silent Push will continue to report on our work tracking Lumma Stealer and share new findings with the community as our research progresses throughout 2025. If you or your organization have any leads related to this effort, particularly those being used by these threat actors, we would love to hear from you.
Mitigation
Silent Push believes all Lumma Stealer-related domains present some level of risk.
Our analysts construct Silent Push IOFA Feeds that provide a growing list of Indicators of Future Attack data focused on scams supported by this technique.
Silent Push Indicators of Future Attacks (IOFA) Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.
Click here to sign up for your free account.
Sample Lumma Stealer Indicators of Future Attacks (IOFAs)
Below is a sample list of IOFAs associated with Lumma Stealer. Our full list is available for enterprise users. Silent Push Enterprise clients have access to a domain feed containing all Lumma Stealer infrastructure, several IOFA Feeds for malware sites that distribute Lumma Stealer and other malware families, and an IOFA feed built to track malicious actors spreading Lumma Stealer based on WHOIS information.
- 213.252.244[.]62
- c3.digital-odyssey[.]shop
- clsevermarketing[.]click
- crowsudysto[.]shop
- docu-signer[.]com
- holmenester[.]com
- jellysipp[.]shop
- mikhail-lermontov[.]com
- pdf-ref095vq842r70[.]com
- roxplo1tsp[.]was
- roxplo1ts[.]ws:443/wave
- techetrs[.]icu
- tinpanckakgou[.]shop
- wetransfer[.]su
- workingkeys[.]info


