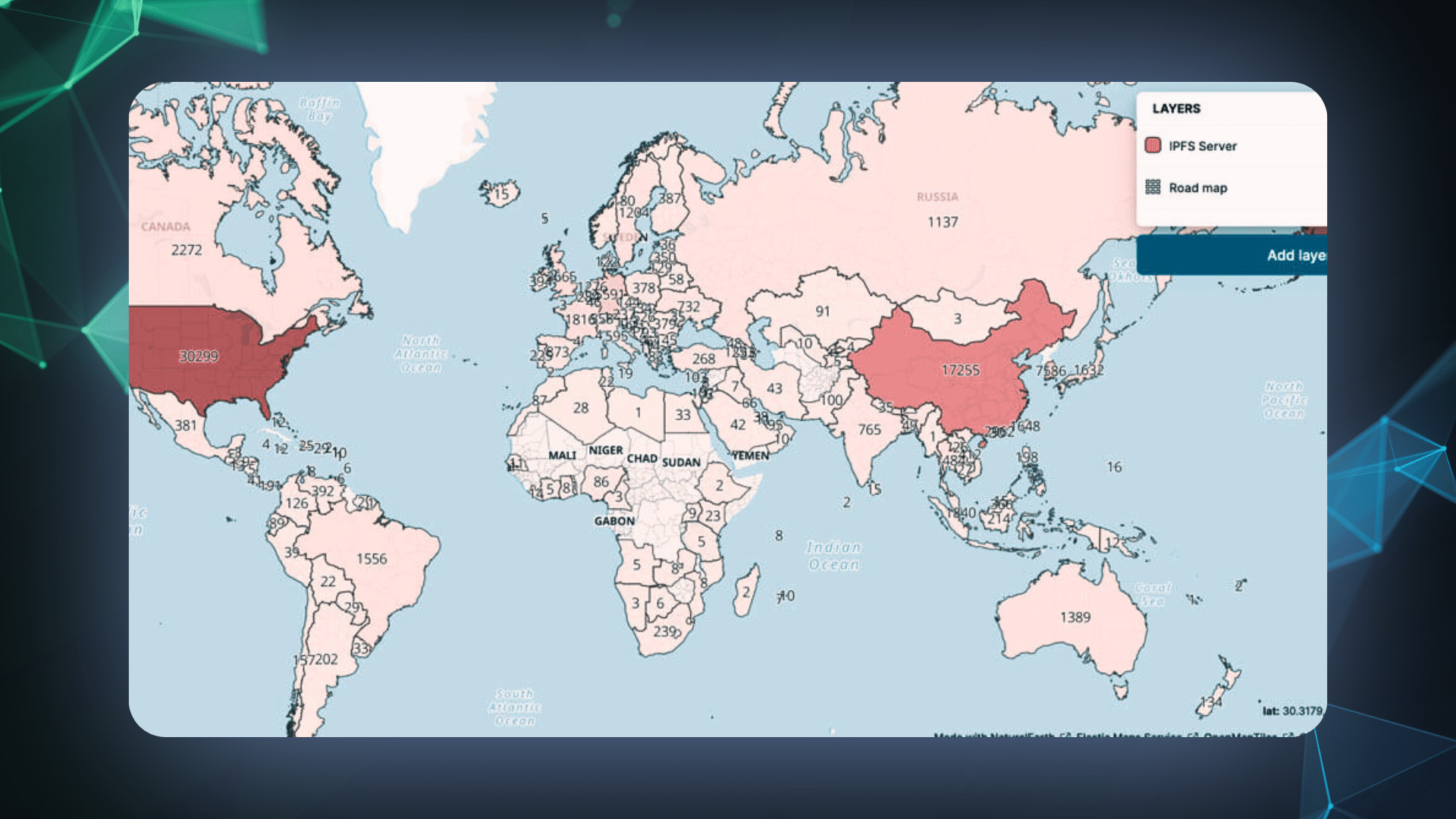
What is IPFS?
Created in May 2014 and released a year later, The InterPlanetary File System (IPFS) protocol is a method of storing and sharing files via the Internet that bypasses traditional methods of client-server connections, that uses distributed hash tables (DHTs) to identify and deliver files to you over a global peer-to-peer (P2P) network.
All that’s needed to retrieve data is a hostname and the file’s content identifier:
https://<gateway>/ipfs/<CID>Sound familiar? It should do. IPFS architecture is closely linked to that other darling of the decentralised web – Bittorrent. The similarities are there for all to see – they’re both decentralised, they both operate on P2P networks and they’re both content based – there are, however, a few subtle but important differences.
IPFS vs. Bittorrent
First of all, IPFS has the potential to replace the way that the world accesses and ‘remembers’ the Internet – the protocol can be used to host entire websites, not just distribute files, as with torrenting, and founder Jean Benet has vocalised his intent to create a fully-archived ‘permanent web’ that the Wayback Machine can only dream of.
There’s also the ‘trust’ element. IPFS doesn’t need you to download a torrent file that may or may not point to the correct data. All that’s required is an IPFS hash, and you can pretty much guarantee that you’ll be receiving the correct file.
There’s lots of other technical factors to consider – from the way IPFS manages duplicate files, to how it eliminates the ability of nodes and peers to ‘go dark’, thereby creating a far more accessible and transparent data community – but the long and short is that despite Bittorrent being around over two decades, and still commanding a significant portion of global upload traffic (as high as 10%), IPFS is proving hugely popular with tech firms and organisations that require decentralised storage (either via files or apps).
IPFS vs. centralised storage
Before you start to think about ditching your trusty file server, it’s important to note that IPFS isn’t an out-of-the-box replacement for a standard secure corporate file system, no more than torrenting is an alternate solution for accessing company HR records. It takes time, energy, resources and a fair bit of savvy to recreate the practicalities of a client-server environment within IPFS, and quite frankly, the client technology doesn’t seem to be there yet.
IPFS, as a protocol, is used for three main reasons:
- to download publicly available files – large or small, common and rare (although lesser-used files have a tendency not to survive within a global namespace);
- blockchain storage;
- as a storage method for decentralised apps (dApps) on the Ethereum blockchain (here’s a simple example).
What are the security implications of using IPFS
First of all, IPFS doesn’t require an open door onto your server architecture or workstations. Various third-party services exist that provide custom IPFS domains, separate to your standard public DNS infrastructure, that exist solely for the purpose of distributing data via IPFS. However, as we’ll go on to discuss, these services aren’t without their problems.
You also don’t need to worry about data being changed to contain malicious files once you’ve started interacting with it. IPFS uses encrypted hashes to manage content on the namespace. If any piece of data is amended, the entire address changes with it.
Organisations should, however, be on their guard. As with any emerging protocol, threat actors have started to ramp up their efforts to discover and propagate exploits across the entire IPFS network that have the potential to wreak havoc on corporate IT systems.
Two cybersecurity researchers from Piraeus University – Constantinos Patsakis & Fran Casino – have recently uncovered numerous ways through which IPFS can be used to host malicious files – or even entire botnets – without any reasonable expectation of detection, and describe how such methods can be transposed to other distributed storage systems.
Unfortunately, the concept of using IPFS for nefarious purposes is nothing new. Back in 2018, threat actors hijacked Cloudflare’s IPFS gateway (see above) to replicate an Azure Blob Storage exploit that fooled users into handing over information via what appeared to be a secure SSL site.
IPFS phishing
It may not be time to hit the panic button just yet, but the warning signs are starting to emerge. IPFS is actively being described by prominent threat intelligence brands as a ‘hotbed’ for phishing attacks, across the entire Internet, not just limited to filesharing within a global namespace.
Services from Google Weblight (an official Google service that speeds up Android browsing), to prominent cloud-based storage platforms such as Filebase, NFT repositories and the aforementioned Microsoft platforms have all been subject to IPFS-specific exploits that trick unsuspecting users into handing over information and feature the tried-and-tested techniques of URL redirection, and reputation masking.
Should I disable IPFS on my corporate network?
As with any emerging technology, it was more or less inevitable that threat levels were going to rise in direct proportion with its uptake. IPFS is experiencing a surge in popularity related to its efficacy when working with blockchain technology or decentralised file storage methodologies.
Whilst this can be interpreted as a democratisation of file distribution technology that puts even more flexibility, choice and useability in the hands of standard users, it also means that threat actors – ever on the hunt for low-hanging fruit – have a new technological landscape to explore, and more attack vectors to develop. This, coupled with the fact that the tech is still in its infancy next to established P2P methods and client-server configurations, means that we’re still getting to grips with IPFS – both as a concept, and an operational reality.
CISOs and CTOs need to make an informed decision on whether or not their organisation absolutely needs to exploit the benefits of IPFS, whilst taking on its associated risks as an emerging technology. Follow Silent Push and other trusted industry voices. Educate yourself on how IPFS is evolving, both in practical terms, and as a security risk.
What companies should definitely avoid is adoption for adoption’s sake. It’s easy to get caught up in the limitless wonderland of decentralised file storage, dApps and blockchain technology, but the question remains – is unsafe commercial traffic worth the cool factor? The answer is a resounding no.
How can Silent Push assist you in using IPFS?
We’re currently updating our app so that IPFS gateways are flagged and published in our customers’ threat intel feeds – just like we do with Tor exit nodes and other gateway infrastructure.
It’s not up to us to make a judgement on whether or not IPFS is suitable for your organization, but we’re committed to providing our customers with the most amount of information possible, gathered from our daily IPv4 and IPv6 scans of the entire Internet, so that they can make an informed choice on how their networks operate.
For more information on IPFS and the Silent Push app, book a demo today.