Indicators of Future Attack are domains, IP addresses and DNS records that act as real time, actionable, proactive indications of attacker behavior and intent.
Created using the power of our proprietary intelligence, IOFAs and their associated analytics are commonly used by security teams, analysts and researchers to improve their threat hunting efforts, proactively defend their digital assets or strengthen their security posture by integrating early detection feeds into their security stack.
As part of release 4.2, Silent Push introduced an exclusive page for its IOFA Feeds and associated feed analytics, allowing you to access timely, accurate and complete IOFA data to stop threats before they attack.
Data independence
How are we able to get IOFAs in the first place? How do we know they are trustworthy indicators? Silent Push is able to provide these indicators by using our own first-party data that’s collected, clustered, scored and delivered without third-party intervention.
The ability to create, control and map the relationship between billions of disparate domains, IPs, DNS records and content hashes to identify emerging patterns is what makes our operational threat intelligence so valuable, and highly actionable.
Curated IOFA Feeds
Curated Feeds refer to feeds made by our own threat analysis research team at Silent Push. They are free of false positives, and only include indicators associated with real threats. This is done to ensure you’re getting the realtime data you need, and nothing else.
Our IOFA Feeds specifically contain IPs, domains, and URLs gathered from our research into global threat actors, specific threat campaigns and a range of attack vectors.
Why use Silent Push feeds?
At Silent Push, we do a lot of work in the background to make sure you can instantly consume our data within the feed at the point of delivery.
Yes, we provide you with the raw data in a curated feed, but so do the other guys…
What we also provide you with simultaneously is realtime, associated context that is immediately available as actionable intelligence for your existing security stack. You are able to consume all the relevant information you need in one place, and action it, for example, by using rules to react our feeds in different ways or by using our enriched threat ranking data to inform your own internal scoring.
Summary
In this blog, we’ll walk you through how to access IOFA Feeds in Silent Push, how to interpret feed analytics, feed them into your security stack and utilize the data to improve your security posture.
How to access IOFA Feeds in Silent Push
Enterprise users have complete access to all 50+ IOFA Feeds in Silent Push.
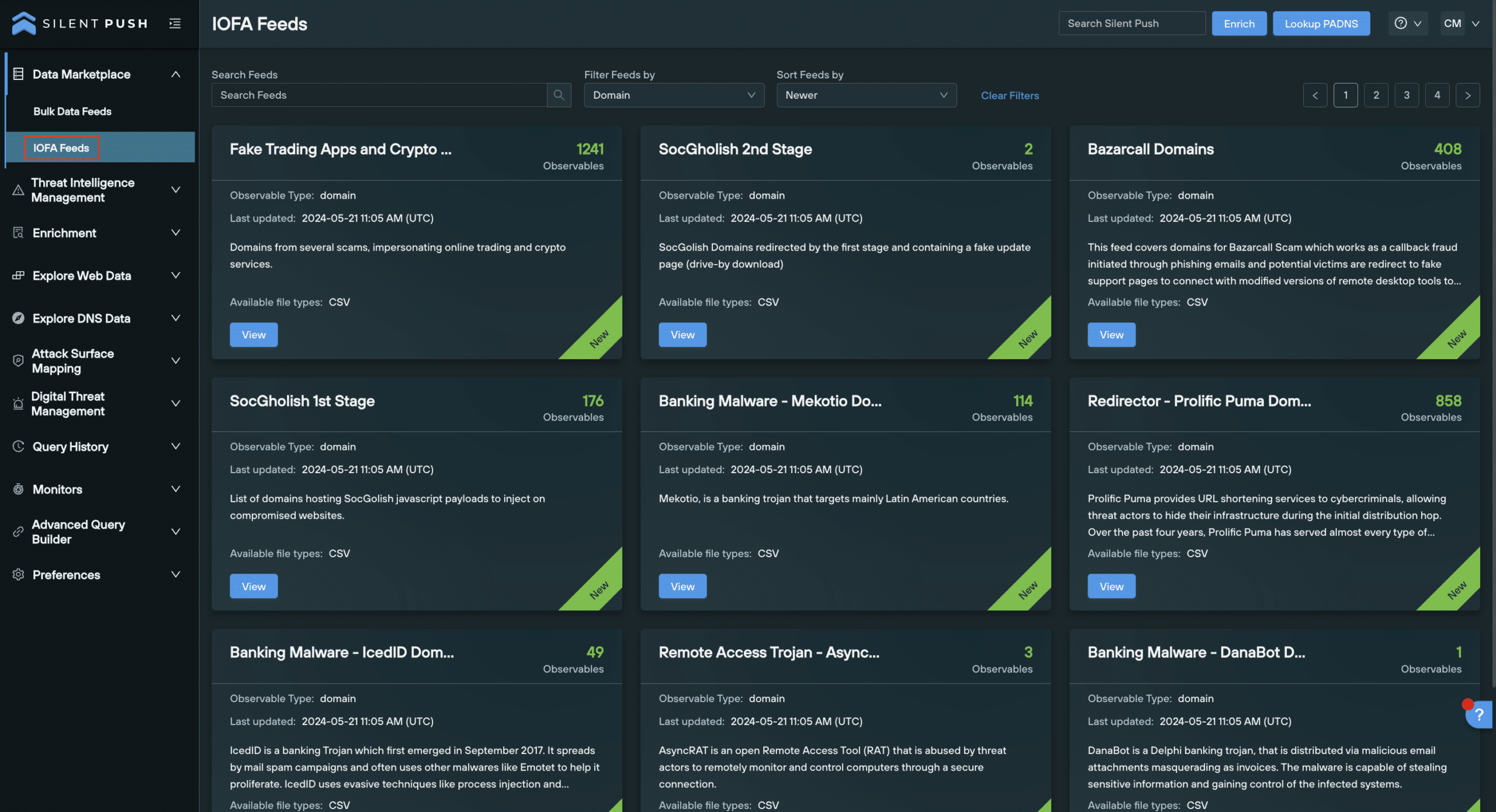
To access the IOFA Feeds, simply navigate to Data Marketplace > IOFA Feeds. This will populate all of our available IOFA Feeds as cards that can be expanded.
You are able to filter the feeds by a particular term in the search bar, filter by IPv4, IPv6, domain or URL data, and sort the feeds into newer or older order.
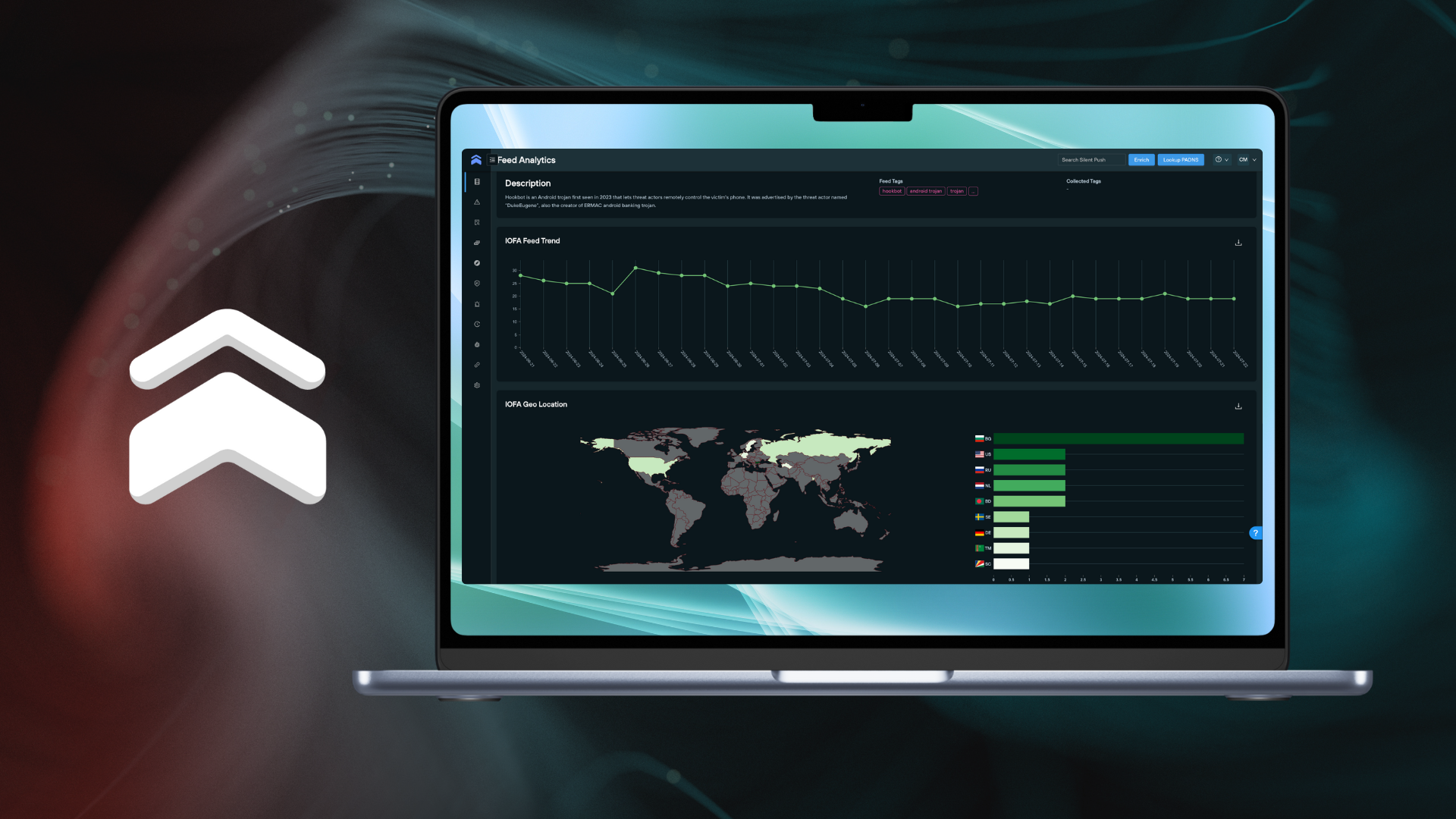
IOFA Feed Analytics
Feed Analytics allow security teams to join the dots across the IPv4/6 space, acting as an early warning system populated with infrastructure.
The Feed Analytics screen contextualizes feed data across the following categories.
Overview panel
The Overview panel provides users with basic context of the Feed structure and export formats along with shortcuts to relevant threat articles.
- Number of IOFAs: a numerical count of the IOFAs currently listed in the feed
- Last Updated: the date at which the feed was last updated
- Available export formats: including one or more of the following: CSV, JSON, TXT, RPZ, STIX
- Linked TLP Amber Report: a link to the associated threat reports produced by our threat research team
- Description of Feed: detailing the associated threat actor/s, common attack vectors and any other relevant information
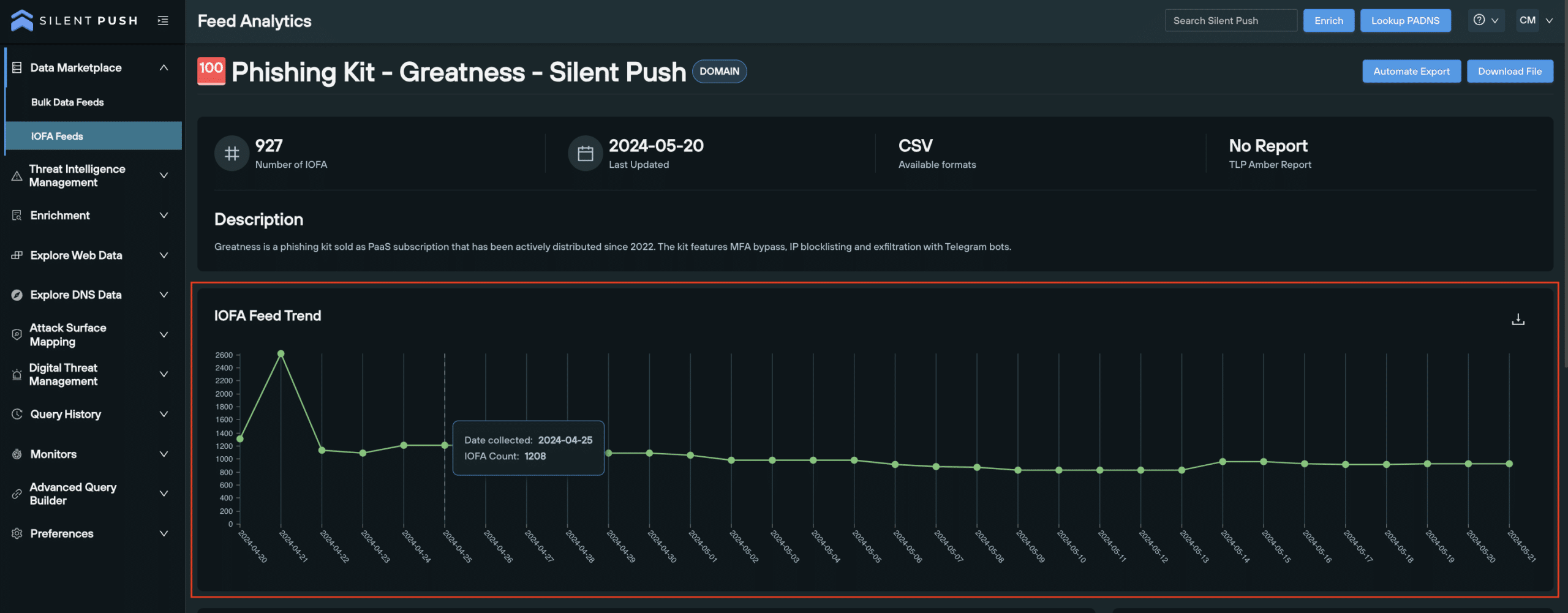
IOFA Feed Trend panel
The Feed Trend panel helps users to understand how the Feed has evolved overtime.
- Date collected: the date an individual IOFA was added to the feed
- IOFA count: the total count of IOFAs listed in the feed at a certain point in time
IOFA Geo Location
Users are able to quickly visualize the geo location of IOFAs on a world map, and download an SVG file of the image to share.
- Country source count: a numerical count of an IOFA’s source country displayed on a world map
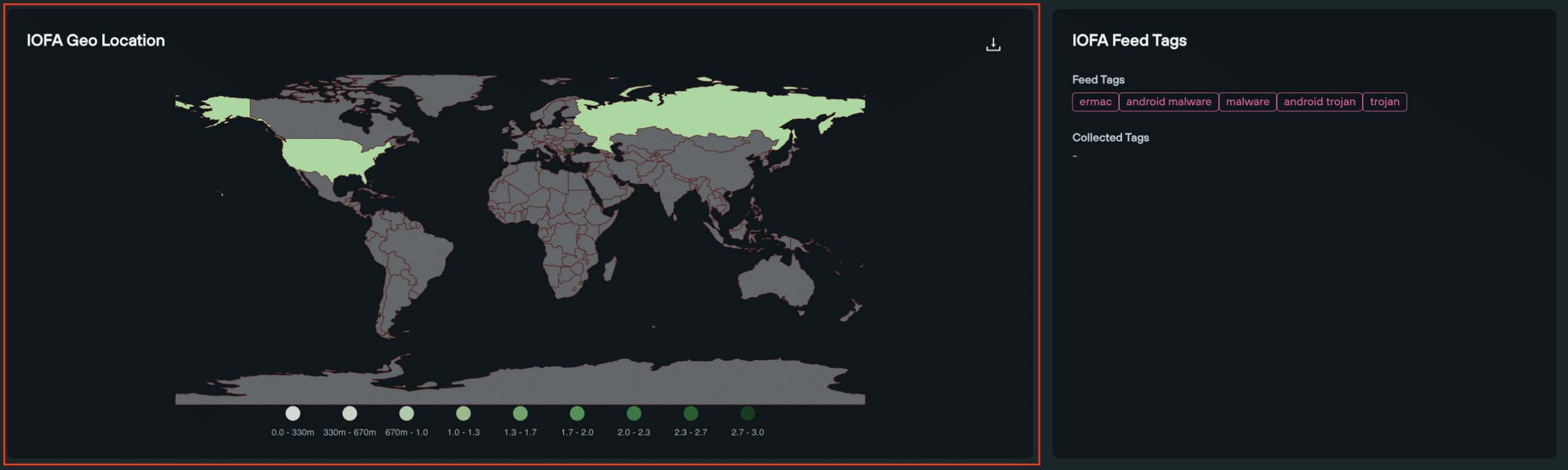
IOFA Feed Tags
Feed Tags are useful shortcuts for users to explore different threat actors or types of criminal infrastructure.
- Feed Tags: provide shortcuts to filtered results for specific threat actors or malicious infrastructure (i.e., Trojan Malware, Android Malware, Ermac etc.) on the Threat Ranking page
- Collected Tags:
IOFA Feed Analysis Indicators
Contextualizing feeds is critical in understanding patterns of behavior across a group of related IOFAs. Feed Analysis Indicators provide users with a thorough overview relating to the Feed’s average risk and repetitional scores, highlighting ‘hot spots’ or areas for concern to help map out attacker infrastructure.
- Average IP Density
- Average IP Reputation
- Average ASN Reputation
- Average Subnet Reputation
- Average Domain Age: date domain was first seen (in days)
- Average IP Diversity
- Average ASN Diversity: how frequently an IP changes between AS numbers
- Average NS Entropy: recency, frequency, and number of name server changes
- Average NS Reputation
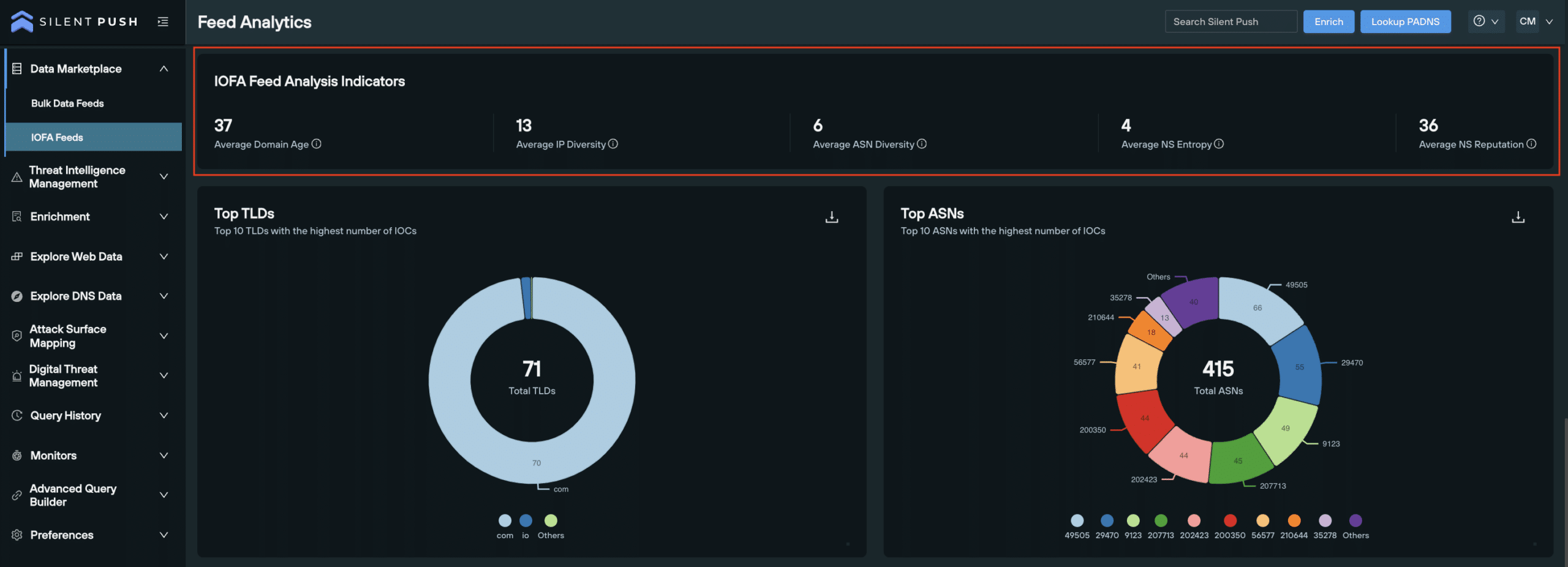
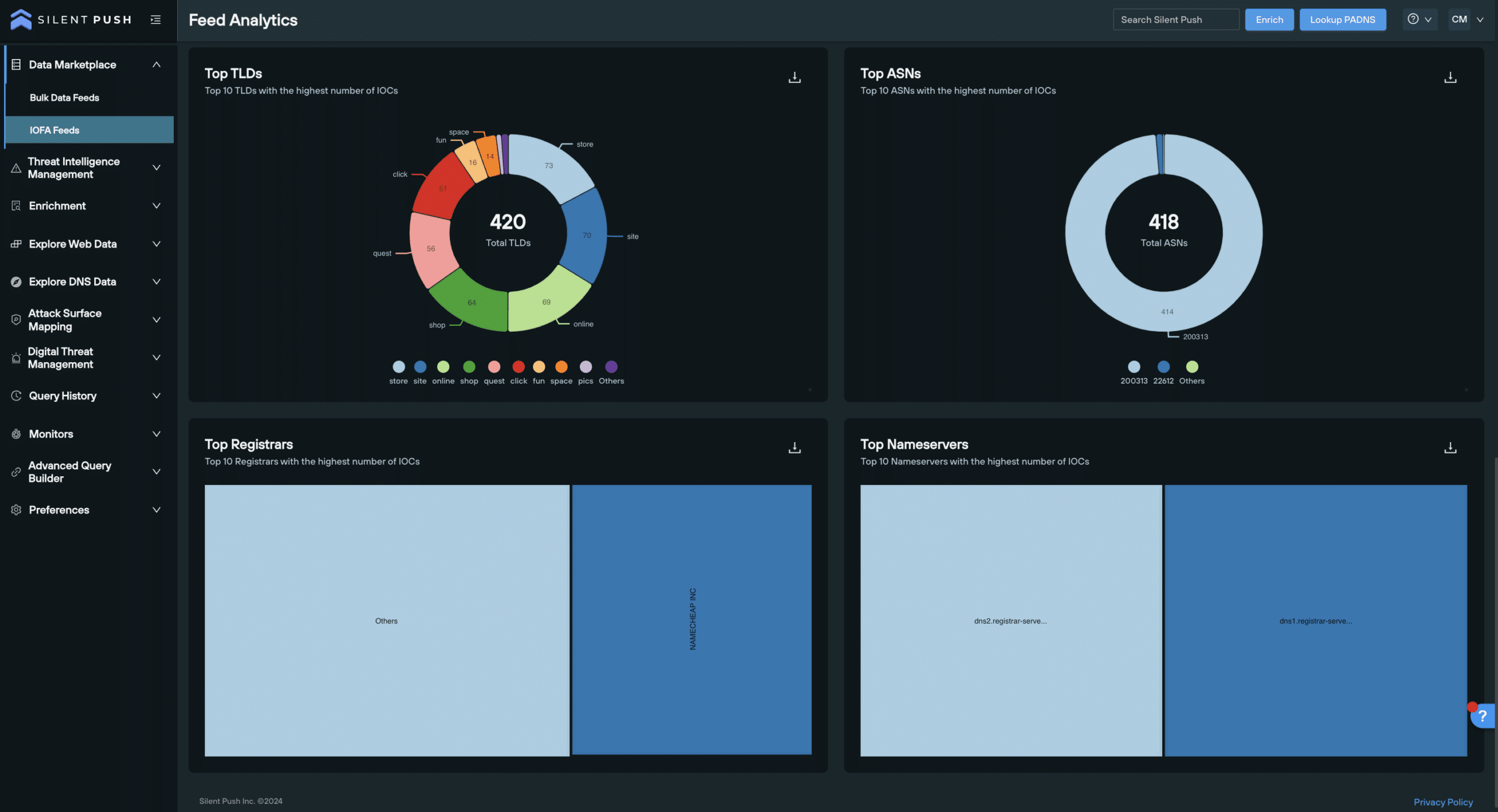
Top Ten Categories:
To help understand the size and scale of threat landscapes and patterns, our Top Ten categories provide users with information regarding:
- Top 10 TLDs: TLDs in the feed with the highest number of IOFAs
- Top 10 ASN: ASNs in the feed with the highest number of IOFAs
- Top 10 Registrars: Registrars with the highest number of IOFAs
- Top 10 Nameservers: Nameservers with the highest associated number of IOFAs
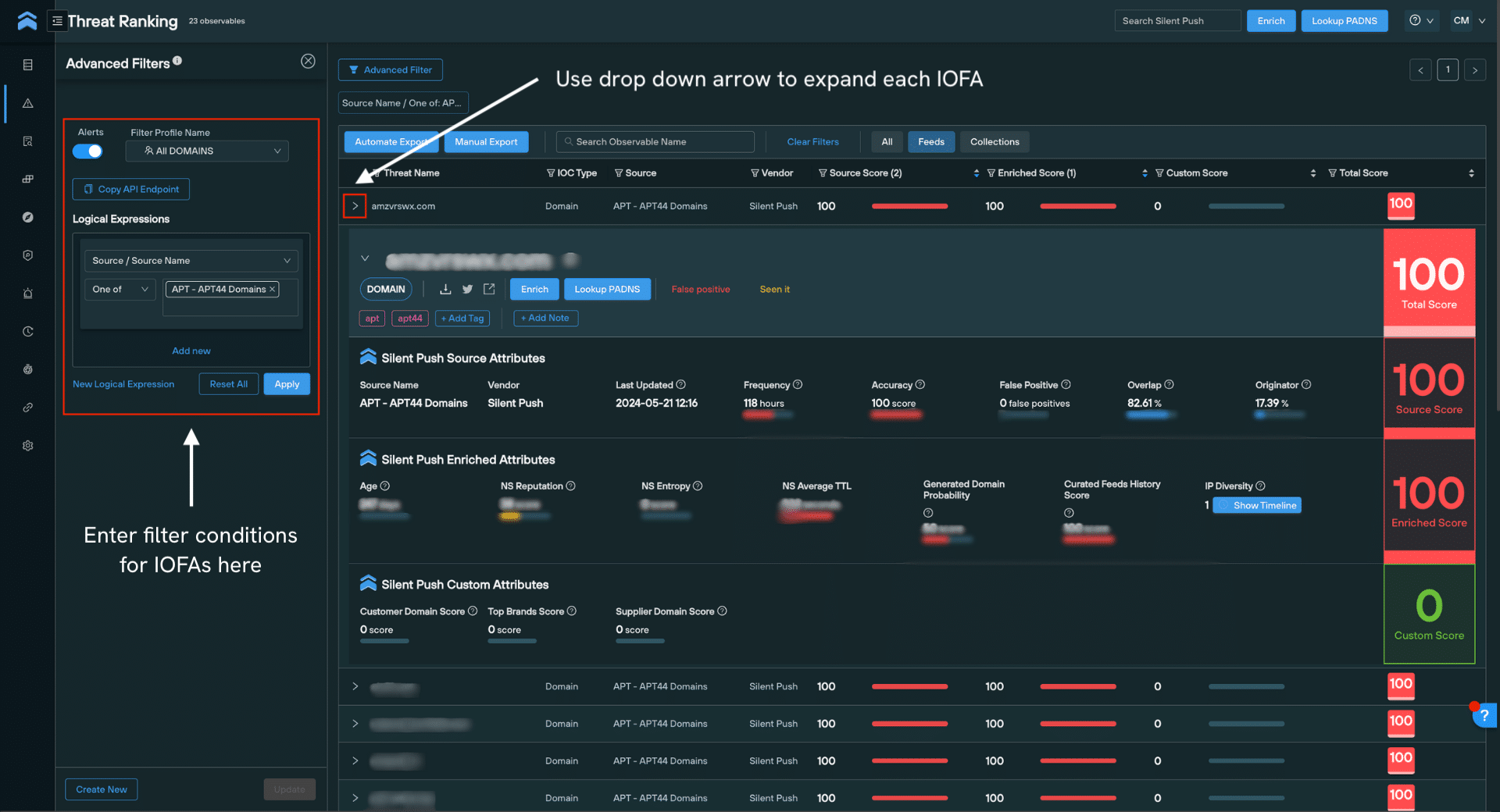
Threat Ranking
The enriched domains and IP addresses within each feed are also visible in Threat Ranking page under Threat Intelligence Management, providing you with corroborated IOFA data in one indexed and searchable screen. This page features additional risk and reputation scoring to support your analysis.
To navigate here from the IOFA Feed Analytics page, navigate to Threat Intelligence Management > Threat Ranking. Enter the specific IOFA you’d like to observe in the search bar, or, create an Advanced Filter with logical expressions to monitor a group of IOFAs.
In this view, each IOFA can be individually expanded to show detailed risk and reputation scores across three categories: Source Score, Enriched Score and Custom Score. These scores can be utilized to inform your own internal scoring systems, or act as reliable indicators of an IOFA’s maliciousness within the context of your organization.
Using IOFA Feed Analytics to improve your security posture
Now you have access to our proprietary IOFA data, how can you use it in an actionable manner to stop threats before they’re weaponized? IOFA Feed data can be easily fed into your security stack (SOAR, Microsoft Azure Sentinel, Splunk etc.) and used for purposes such as traffic blocking, quarantining, ongoing monitoring and more.
Download Feed data: File export options
IOFA Feed data can be exported in several ways, depending on how you wish to use it.
Download via manual export:
To manually export Feed data:
- From the Feed Analytics screen, select ‘Download File’.
- Export as a CSV, JSON, TXT, RPZ or STIX file.
Download via API URL:
- From the Feed Analytics screen, select ‘Automate Export’
- Select the file type required
- Click the Copy API Endpoint button. This endpoint retrieves a time-limited (3 hours) URL that you can call to download the file.
Extract code snippets for external security tools:
IOFA Feed data can also be externally fed into your security stack via Python, curl, and PHP.
After clicking ‘Automate Export’, simply select the cURL, Python or pHp tabs to copy code samples and call it from your desired security tool.
REGISTER FOR COMMUNITY EDITION
IOFA Feeds and their associated analytics are available as part of Silent Push Enterprise Edition – a powerful threat hunting and cyber defense tool used by security teams, threat analysts, and researchers. Request a demo here.
If you’d like to get a taster of the Silent Push platform, register for our free Community Edition that features 90+ data enrichment categories that you can use to track and monitor attacker activity across the global IPv4 space. Click here to sign-up for a free Community Edition account.