Infrastructure Laundering: Silent Push Exposes Cloudy Behavior Around FUNNULL CDN Renting IPs from Big Tech

Register for our upcoming threat webinar on Infrastructure Laundering on March 6 2025.
Key Findings
Silent Push is coining the term “Infrastructure Laundering” to describe a growing criminal practice our analysts have observed where threat actors operating “hosting companies” rent IP addresses from mainstream hosting providers and map them to their criminal client websites.
- Our research team was surprised to find mainstream cloud providers, such as Amazon Web Services (AWS)* and Microsoft Azure, are often seen in large-scale use by threat actors. While providers are consistently banning specific IP addresses used by the FUNNULL content delivery network (CDN), the pace is unfortunately not fast enough to keep up with processes being used to acquire the IPs.
- FUNNULL has rented over 1,200 IPs from Amazon, and nearly 200 IPs from Microsoft – nearly all have been taken down as of this writing, but new IPs are continually being acquired every few weeks.
- There are indications of FUNNULL illicitly acquiring the IPs using stolen or fraudulent accounts. However, external visibility into this process is limited.
- Silent Push’s research into the FUNNULL CDN’s activities has revealed a direct association with money laundering as a service hosted on shell websites, retail phishing schemes, and pig-butchering scams being kept online via infrastructure laundering.
- Given that it’s easier for enterprises to defend against this type of network if the services of mainstream providers are made unavailable to those criminals, our team is left to wonder: If FUNNULL has been using the same illicit IP rental schemes and CNAME mapping tactics for years, activity which is clearly visible to us as cyber threat professionals, why are cloud providers still struggling to keep up? Are cloud providers not investigating deeply enough to find illicit IP rentals in real time?
- This line of thinking led us to a few larger, and as of yet unresolved, questions around infrastructure laundering:
- If a hosting account is banned for fraud and abuse concerns, are cloud providers not investigating what content was hosted there and looking for similar content elsewhere on their network?
- How and why does an organization like FUNNULL keep renting one IP after another from mainstream providers, even if using illicit means to acquire those IPs, when they are mapping them to one of three CNAMEs?
- How come thousands of IPs have been taken down historically, but the new ones stay mapped for days or weeks without actions?
- How is it that cloud providers are unable to see or stop this in real time?
*Note: Amazon has responded to our findings with a public statement, which we have attached to the bottom of this report, along with our comments.
Table of Contents
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Account
- Background
- Exploring Infrastructure Laundering Practices
- Key Connections
- Cybersecurity Concerns
- Mapping FUNNULL CDN Scams
- Retail Scams Find a Home in Infrastructure Laundering
- Looking Ahead, Bigger Questions Loom
- Continuing to Track Infrastructure Laundering
- Mitigation
- Register for Community Edition
Executive Summary
Over the past few years, Silent Push Threat Analysts have been investigating and exposing threat actors whose crimes are not restricted to the internet but are very much a part of real-world criminal organizations. Our team is tracking this growing cyber line-blurring practice, now better known as “infrastructure laundering,” which leverages legitimate, mainstream hosting providers through intermediaries.
As we examine this particular brand of threat actor behavior, we must assess the scale of the technical infrastructure involved and critically examine the suppliers that are helping keep these organizations in business. The results have been surprising. Our analysts have discovered threat actors being enabled by mainstream cloud providers, including Amazon Web Services (AWS) and Microsoft Azure.
Both Amazon and Microsoft have essentially been fighting an uphill battle, clearly banning IPs being used by the FUNNULL CDN, yet new IPs are still showing up every few weeks. New details uncovered in the course of this reporting indicate that FUNNULL is likely using fraudulent or stolen accounts to acquire these IPs to map to their CNAMEs, and providers we have spoken to claim this wasn’t caught in real time due to visibility holes from the technical complexity of their DNS architecture.
Sign Up for a Free Silent Push Community Account
Register now for our free Community Edition to use all of the tools and queries mentioned in this blog.
Background
The concept of infrastructure laundering is relatively new in cybersecurity and cybercrime discussions and circles. However, the underlying idea—that intermediaries provide a layer of obfuscation for illicit activities—has been previously discussed in the contexts of “bulletproof hosting” and “cybercrime-as-a-service.” These services perform a similar function: offering cybercriminals a high level of anonymity and protection.
One core difference between infrastructure laundering and a bulletproof host (BPH) is that with infrastructure laundering, takedowns are expected. We’ve come to realize that the persistence of infrastructure laundering is due primarily to the aggressive efforts used to acquire fresh hosting accounts – essentially, the threat actors moving more rapidly than cloud hosts can react.
Taking obfuscation a step further, infrastructure laundering specifically highlights a distinct process wherein intermediaries (such as the FUNNULL CDN, outlined in our Triad Nexus blog) launder their infrastructure by hosting it within large, legitimate cloud platforms (such as AWS or Azure) in order to further mask its origins and criminal intent.
Infrastructure laundering also helps to keep the websites fast for global audiences by mapping the infrastructure to countless IPs located in different areas of the world—and having IPs in the U.S. is useful for a network like FUNNULL, which hosts scams targeting U.S. brands and consumers.
The similarity here to the term “money laundering” is not accidental. Whereas money laundering enables the proceeds of crimes to be used on the open market and appear to have come from a reputable source, infrastructure laundering legitimizes the sale of internet hosting services via CNAME mapping and other classical DNS techniques to map their mostly criminal client websites to IP addresses owned by credible, Western hosts, thus creating the illusion of legitimacy for unsuspecting visitors and defenders.
The criminals’ advantage when it comes to infrastructure laundering, over and above bulletproof hosting, is that the underlying hosting provider also hosts other, valid businesses on a large scale, so it is difficult for defenders to block traffic received from that cloud provider without also adversely blocking legitimate web traffic for their users. As opposed to when criminals are restricted to using bulletproof hosting services, their infrastructure can then be easily blocked without the risk of causing accidental service disruption to the defending companies’ business operations.
Exploring Infrastructure Laundering Practices
Here’s how the concept of infrastructure laundering is evolving in discussions:
Bulletproof Hosting
The practice of bulletproof hosting is described as a service provided by an internet hosting operator that is resistant to takedown efforts and is usually located in jurisdictions with more lenient regulations and/or countries where law enforcement has fewer resources to monitor and control. Hosting service providers involved in BPH support all types of unwanted activities, including but not limited to the abuse of copywritten materials, hosting of malware and botnet command and control (C2) servers, support to hate speech and misinformation, illegal gambling, pornography, and spam.
For years, bulletproof hosting providers have offered safe havens for cybercriminals by refusing or resisting takedown requests and allowing illicit activity to flourish. In traditional bulletproof hosting, the entire infrastructure is often controlled by a criminal enterprise or purpose-built for resilience against law enforcement while ever-so-coincidentally being located in countries with weak engagement with international law enforcement.
A key differentiator between BPH and infrastructure laundering is that legitimate hosts being abused to support infrastructure laundering can and do take actions to stop it. However, infrastructure laundering appears to rely on gaps between when a threat actor can use a new account to acquire another IP and the time it takes for a cloud provider to realize that IP is being used illicitly.
Layered Transactions Create Tracking Challenges
Services within the cybercrime-as-a-service (CaaS) ecosystem (such as ransomware as a service (RaaS) or phishing kits) often provide resources that criminals can lease or buy directly from other threat actors.
In infrastructure laundering, however, the key difference lies in a layered financial transaction where the primary cloud providers may not see a singular entity renting the IPs but instead have numerous “IP mules” who set up or acquire accounts and purchase IPs without transparency about who they are doing it for.
In fact, beyond shared payment methods, contact details, or other insights from internal tooling we are unaware of, the only way a cloud provider could know that FUNNULL was renting these IPs would be if they had tracked all three of the random domains FUNNULL uses for CNAME chains (funnull[.]vip, funnull01[.]vip, fn03[.]vip), and created a system to monitor newly-rented IPs being mapped to any of these CNAMEs.
Methods like this represent a unique tracking challenge, creating opportunities for threat actors to remain unseen but also allowing defenders to react in real time – provided they are aware of it.
Emerging Regulatory Concerns
Cybersecurity experts and regulators have only recently started to examine the financial and technical blind spots created by third-party intermediaries more closely. The idea that cloud hosting providers could be unwitting victims while also potentially missing opportunities to stop corporate threat actors from abusing these systems creates challenges that don’t have any easy answers.
Key Connections
Silent Push’s investigation into the FUNNULL CDN on our Triad Nexus blog revealed a large cluster of malicious infrastructure and its pivotal role in facilitating extensive cybercriminal activities, many of which are orchestrated by Chinese Triad groups. This aligns with the United Nations Office on Drugs and Crime (UNODC) 2024 Report that discusses Transnational Organized Crime, or “TOC,” and its findings on the convergence of cyber-enabled fraud, underground banking, and technological innovation in Southeast Asia.
In our FUNNULL research, Silent Push Threat Analysts discovered this network of investment and retail scam websites, along with money laundering websites, are actually hosted on a combination of numerous Western IP addresses owned by prominent hosting U.S. companies and prominent Asian hosting providers. This blending of hosting between the U.S. and Asia is significant as this could be an effort to host in locations that don’t regularly collaborate on cyber threats. The crime group also targets victims in both jurisdictions, so having hosting in those locations would improve the speed and potentially the perceived legitimacy of the websites.
Hosting Malicious Infrastructure
FUNNULL CDN has been identified as hosting over 200,000 unique hostnames, of which approximately 95% are generated through Domain Generation Algorithms (DGAs). These domains are linked to illicit activities such as investment scams and fake trading applications. Moreover, these activities are directly associated with money laundering as a service on shell gambling websites that abuse the trademarks of a dozen popular casino brands and which are available online today.
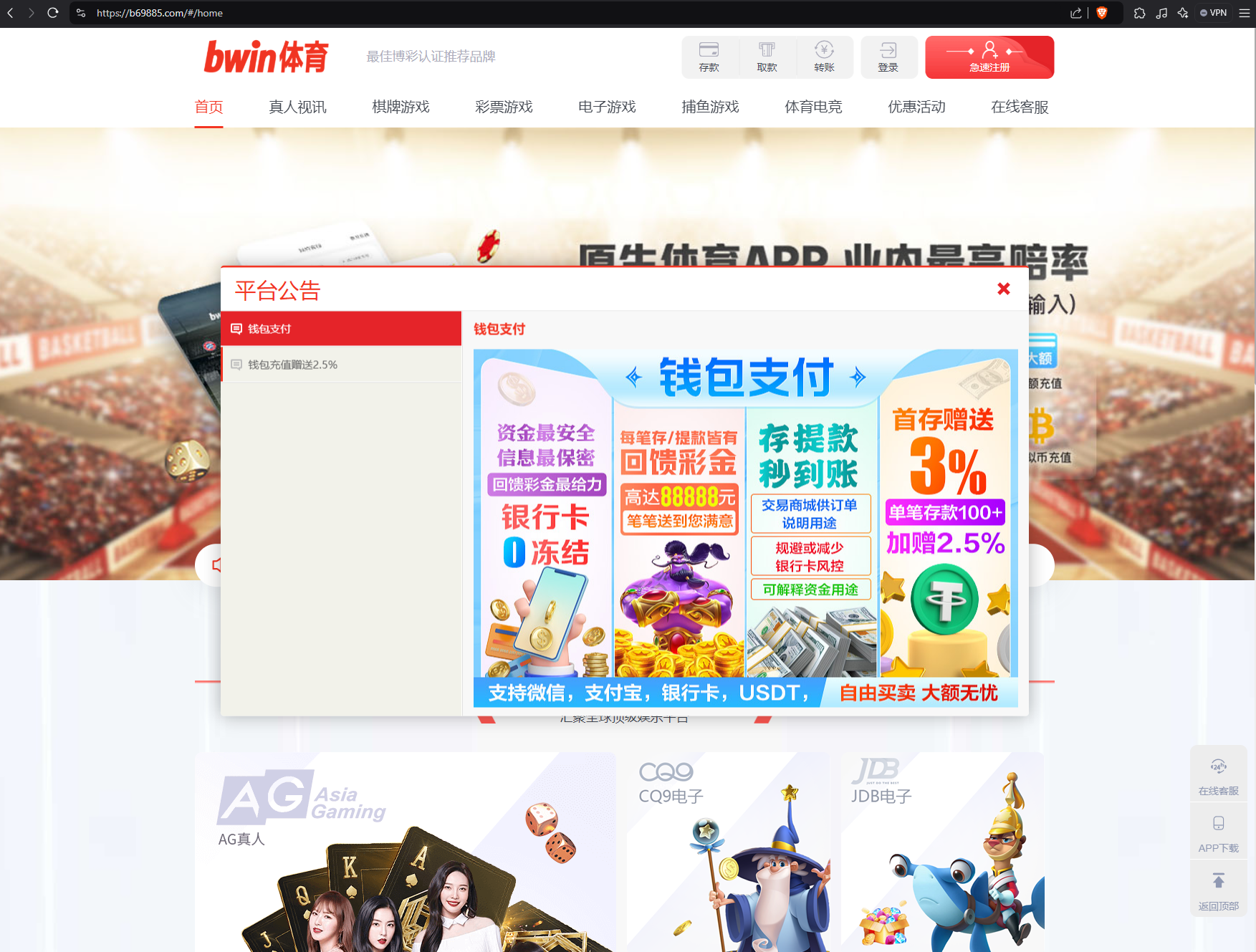
BWIN Confirms Fake FUNNULL Gambling Sites – Strengthens Money Laundering Accusations
One organization whose trademarks are being abused within the FUNNULL network is the online gambling portal Bwin. Our research into Bwin’s connection revealed that its association with FUNNULL is due to an abuse of its brand name—they have no actual relationship. Approximately a dozen other major online gambling brands’ trademarks are also being abused across tens of thousands of shell gambling websites.
One of the active Bwin spoofed sites hosted on a Microsoft IP address via FUNNULL CDN in December 2024 can be seen here:
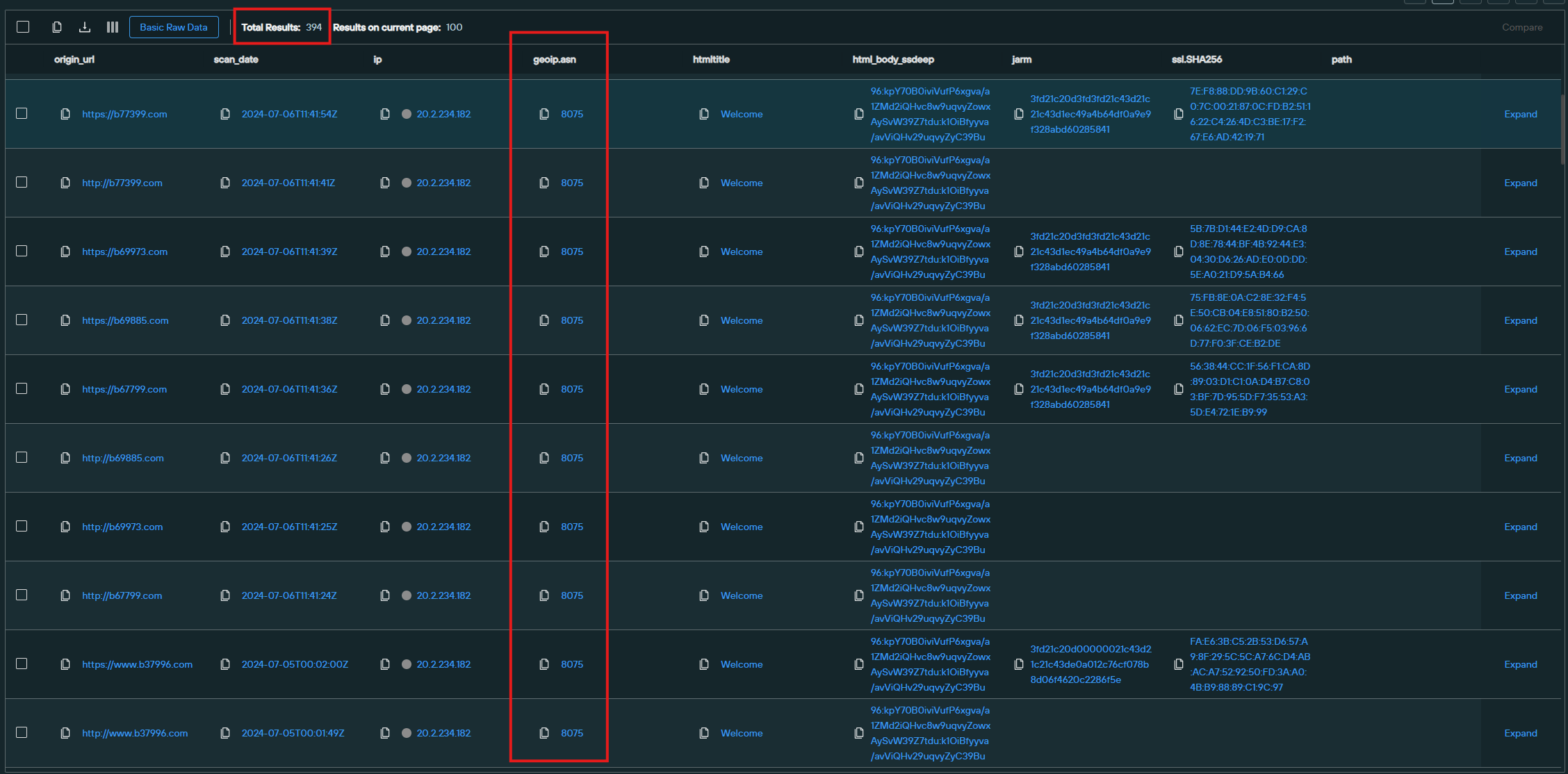
Dozens of the Bwin-impersonated sites were hosted on Microsoft’s infrastructure:
Chris Alfred, a spokesperson for Entain, Bwin’s parent company, told TechCrunch that Entain can confirm that the domain associated with FUNNULL is a fake website. Bwin does not own it and has nothing to do with it. The site owner appears to be infringing on the Bwin brand. Alfred has said they are taking action to resolve the issue and get the site removed.
Supply Chain Attacks
Earlier this year, FUNNULL’s acquisition of the popular JavaScript library polyfill[.]io led to a supply chain attack that impacted over 110,000 websites. This incident underscores the sophisticated methods these criminal networks employ to infiltrate legitimate systems, albeit sometimes for murky purposes.
Cybersecurity Concerns
The likely collaboration between entities like FUNNULL CDN and organized crime groups like the Chinese Triads exemplifies the complex and evolving nature of TOC in Southeast Asia. The fusion of technological innovation with traditional criminal activities necessitates comprehensive and coordinated efforts across international law enforcement and regulatory bodies to effectively address and mitigate these threats.
A key roadblock to stopping these cyber criminals, however, is that this large crime infrastructure uses mainstream cloud providers like AWS and Azure as part of its underlying setup and continues to rent IPs, even with apparent efforts to stop them.
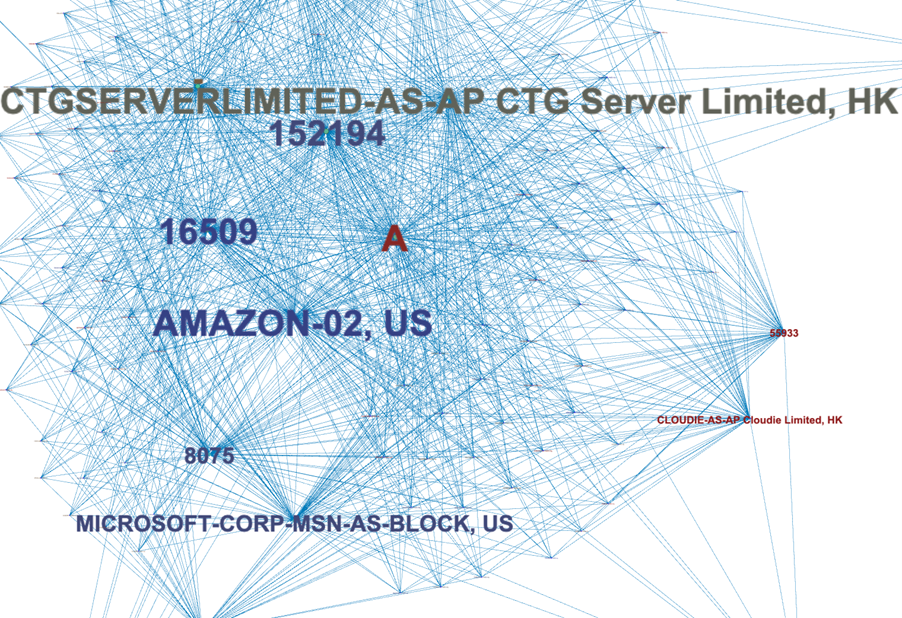
The node map below shows the main entities involved in providing FUNNULL CDN with the underlying hosting services it uses. This is a very active network, even if major cloud hosts are regularly banning IPs that are mapped into their infrastructure.
Mapping FUNNULL CDN Scams
At its peak in 2022, the investment scam infrastructure on FUNNULL CDN had thousands of active domains.
While more modest in 2024, this malicious cluster still had some active sites, including cmegrouphkpd[.]info, which has hosted a fake trading platform abusing CME Group’s brand and logo for the past two years. It only recently went offline after we published our Triad Nexus report on FUNNULL CDN.
![Screenshot of web content previously hosted on cmegrouphkpd[.]info site.](https://www.silentpush.com/wp-content/uploads/1-still-active-domain-from-Ines.png)
Having been live for over two years, the domain cmegrouphkpd[.]info also helped our team map CNAME record changes across the FUNNULL CDN.
The domain had a CNAME record pointing to *.funnull[.]vip between February and March 2022, changing to *.funnull01[.]vip between March 2022 and June 2024, and which has since then switched to *.fn03[.]vip.
![Silent Push Web Scanner search results for CNAME records found for cmegrouphkpd[.]info.](https://www.silentpush.com/wp-content/uploads/infra-laundering-cname-records-cmegrouphkpd.png)
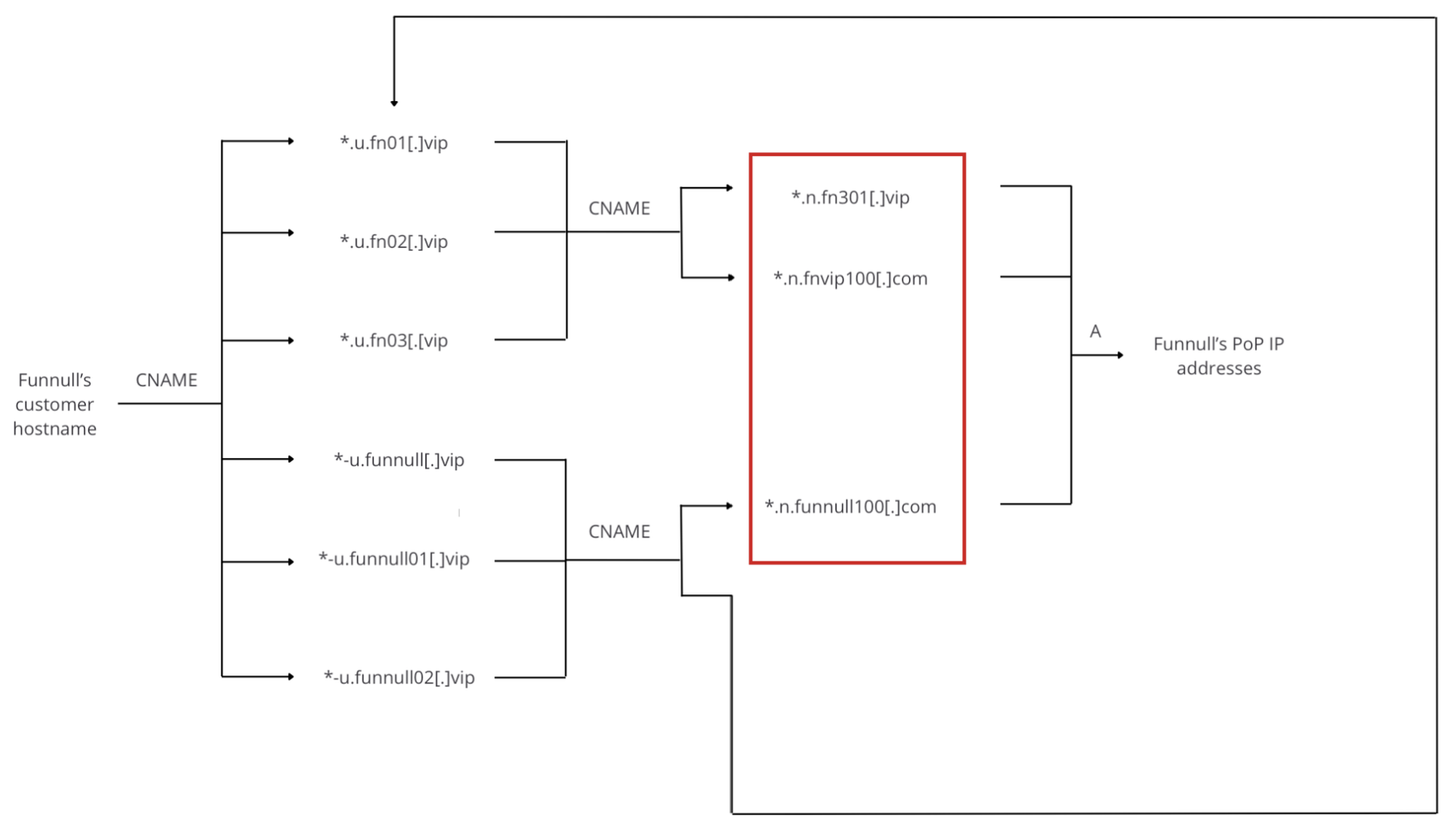
In the first CNAME hop, FUNNULL maps client domains to a CNAME record such as *.fn03[.]vip
The second CNAME hop is from the *.fn03[.]vip record mapped to another CNAME at *.fnvip100[.]com
The third CNAME hop starts at the second CNAME, fnvip100[.]com, which is then mapped to rented IP addresses.
![Silent Push Web Scanner results of a Forward CNAME lookup for 6ce0a6db.u.fn03[.]vip.](https://www.silentpush.com/wp-content/uploads/infra-laundering-cname-2nd-hop.png)
By having CNAME chains within FUNNULL’s CDN infrastructure, every time a DNS client requests the domain/hostname of a FUNNULL customer, the DNS resolver follows the resolution chain and answers with the IP address of its “Point of Presence” (PoP) with the fastest response:
![Silent Push Web Scanner search results of a DNS Forward A lookup for 0e6de73d2.n.fnvip100[.]com.](https://www.silentpush.com/wp-content/uploads/infra-laundering-dns-fwd-a-lookup-scanner-result.png)
As a result, these CNAME chains can be used to map FUNNULL’s entire customer infrastructure on its CDN and obtain the IP addresses for its entire Point of Presence network.
The three CNAME records that are needed to map rented IPs used within the FUNNULL CDN can be seen in the data flow map below, highlighted in a red box. If you conduct a forward A lookup on these CNAME records, you will get the list of rented IPs in the network.
Important Note: Listed below are the three specific CNAME records needed to map IPs currently in use within the FUNNULL CDN. Those records are:
- fn301[.]vip
- fnvip100[.]com
- funnull100[.]com
Using this CNAME chain method of mapping both the hostnames and the IPs used in the FUNNULL CDN, Silent Push Threat Analysts identified over 200,000 unique hostnames being proxied through the FUNNULL network between late September and mid-October of 2024 – with more than 95% of the hostnames created with DGAs – and 1.5 million reverse CNAME records lookups have been collected since 2021.
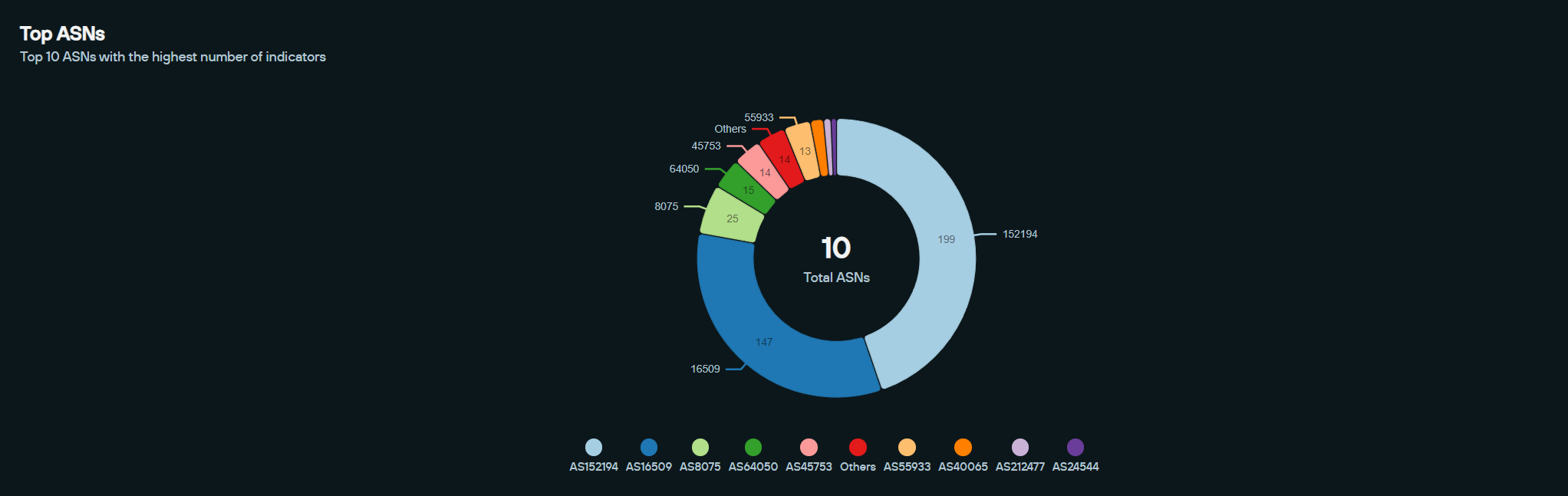
Silent Push identified close to 500 of FUNNULL’s IPs being actively used by threat actors in live campaigns, and, as we expected, a large portion were located in Asian ASN ranges, such as AS152194 (China Telecom Global), AS45753 (NETSEC-HK Netsec Limited), and AS55933 (CLOUDIE-AS-AP Cloudie Limited).
Surprisingly, however, in December 2024, we discovered nearly 40% of the FUNNULL CDN’s IP addresses belonged to AS8075 (MICROSOFT) and AS16509 (AMAZON), two major U.S.-based cloud providers.
It’s important to appreciate that FUNNULL has rented over 1,200 IPs from Amazon, and nearly 200 IPs from Microsoft – and most of those IPs only last a few weeks at most before being taken down, some lasting only days. But there is a clear and consistent pattern – FUNNULL CDN wants to continue to acquire IPs from both Amazon and Microsoft and seems willing to use illicit methods to acquire them – and appears to be succeeding regularly in their efforts.
Using Silent Push’s extensive PADNS data, we have confirmed that FUNNULL has been renting Microsoft’s IP space since at least 2021, with some of these rented IPs mapped to FUNNULL for significant periods of time.
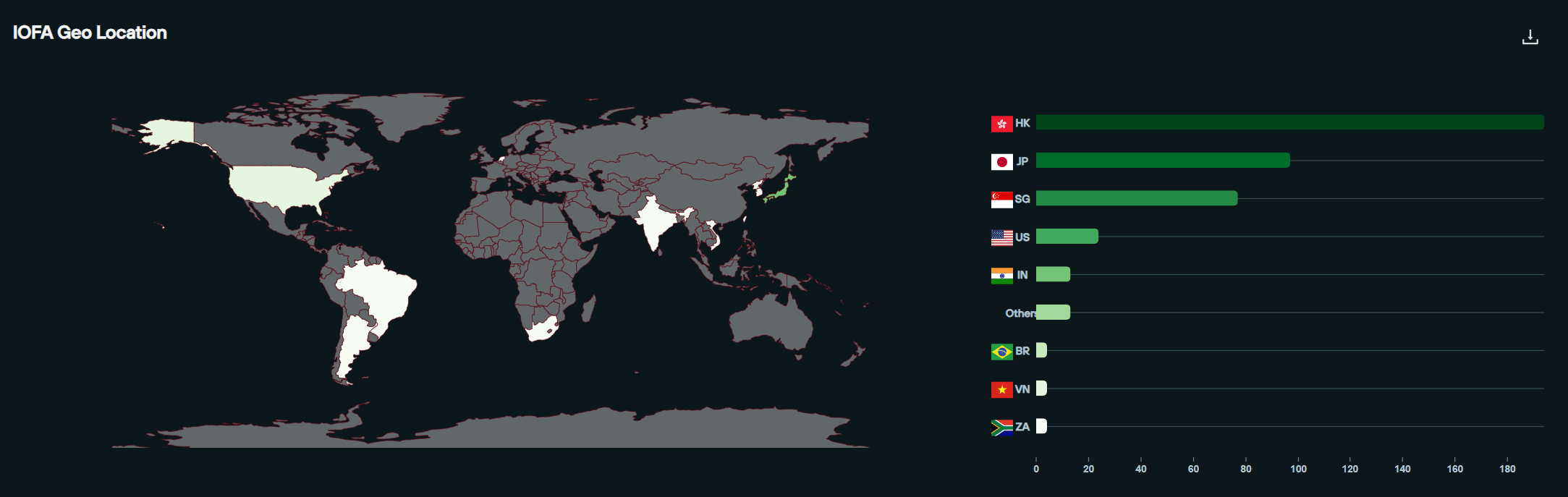
Based on a snapshot from December, across 438 IPs in the FUNNULL CDN, the vast majority are hosted in Hong Kong, Japan, and Singapore.
20 IP addresses, however, are currently hosted in the U.S.
And on any given day, even with IP takedowns and new IP addresses being added to the network regularly, it appears that FUNNULL always has some IP space in the U.S. and is constantly working to acquire more.
Retail Scams Find a Home in Infrastructure Laundering
Digging deeper into the FUNNULL CDN, our threat researchers found a campaign targeting dozens of major brands, with what appeared to be a focus on luxury fashion companies, with phishing pages hosted on the Triad Nexus FUNNULL CDN infrastructure. The phishing pages targeted multiple brands, including:
Aldo, Asada, Bonanza, Cartier, Chanel, Coach, eBay, Etsy, Gilt Groupe, Inditex, Lotte Mart, LVMH, Macy’s, Michael Kors, Neiman Marcus, OnBuy[.]com, Rakuten, Saks Fifth Avenue, Tiffany & Co., and Valentino.
An Entire CNAME Dedicated to Criminal Phishing and Investment Scam Websites
Our team discovered approximately 650 unique domains hosted on one specific FUNNULL CNAME record. This intrigued our team, as it indicated intentional segmentation broken down by each criminal client.
We soon realized that a chunk of these domains were investment scam websites such as coroexchange[.]com, seen here:
![Screenshot of content previously hosted on coroexchange[.]com.](https://www.silentpush.com/wp-content/uploads/infra-laundering-coro.png)
Beyond the investment scam sites, the other websites hosted on this CNAME all appeared to be a new retail phishing campaign targeting major Western brands, with phishing login pages such as bonanza.jdfraa[.]com.
![Screenshot of content previously hosted on bonanza.jdfraa[.]com.](https://www.silentpush.com/wp-content/uploads/infra-laundering-bonanza.png)
Our analysts also discovered another technical commonality between the phishing web pages – something that helped us find 80 separate retail phishing sites, all seemingly operated by the same threat actor. For operational security purposes, however, we’re only sharing that fingerprint with our enterprise clients and law enforcement officials to keep tabs on this network’s operations in the future.
Retail Phishing Hosted via Infrastructure Laundering on Amazon AWS and Microsoft Azure
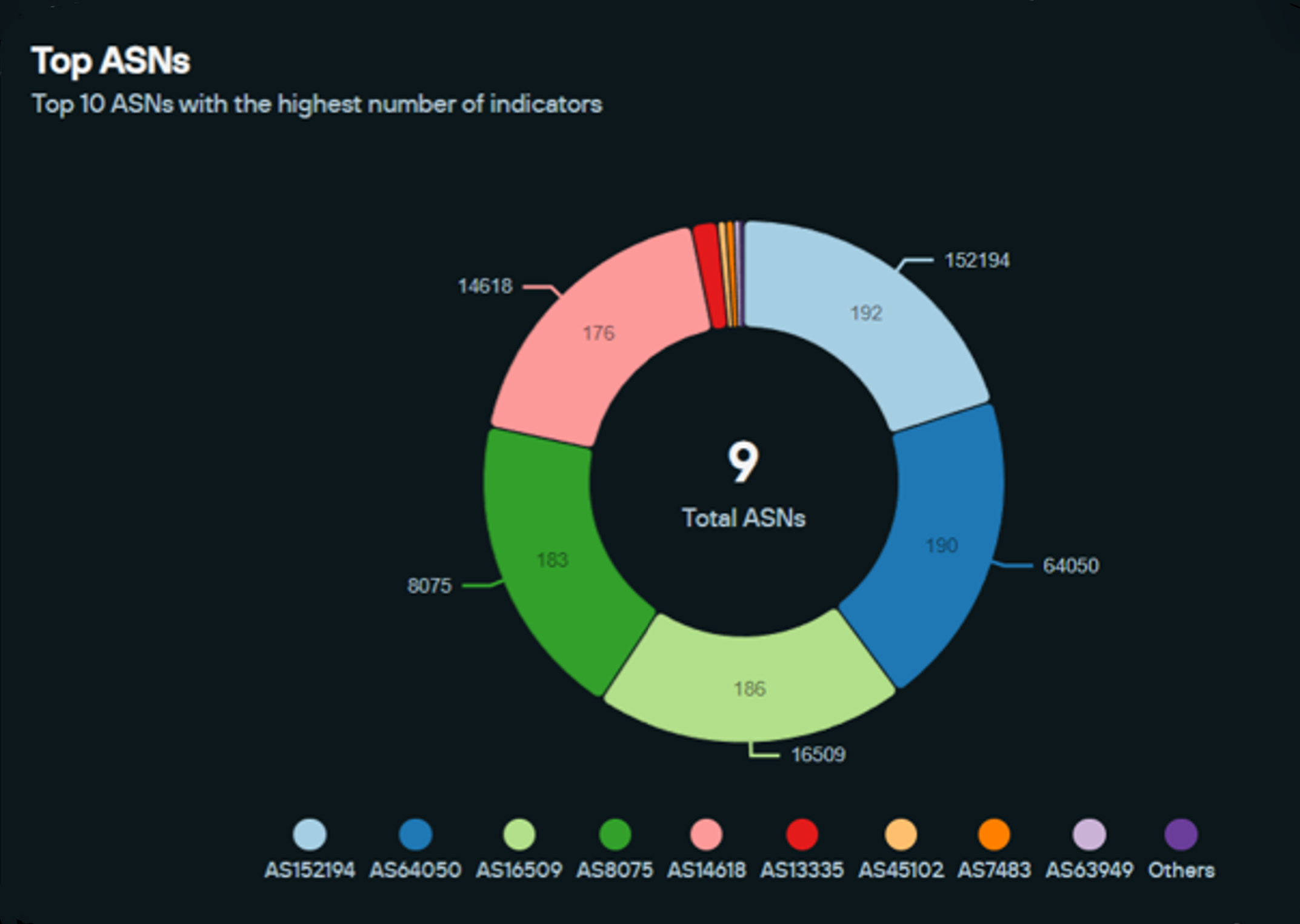
The retail phishing domains hosted on FUNNULL were seen across 9 ASNs. From highest to lowest density, they included:
- CTGSERVERLIMITED-AS-AP CTG Server Limited, HK (152194)
- BCPL-SG BGPNET Global ASN SG (64050)
- AMAZON-02 US (16509)
- MICROSOFT-CORP-MSN-AS-BLOCK US (8075)
- AMAZON-AES US (14618)
- ALIBABA-CN-NET Alibaba US Technology Co. Ltd. CN (45102)
- SKYCLOUD-NET Skycloud Computing Co. Ltd. TW (7483)
Sample of FUNNULL IP Addresses and CNAME Mapping Details
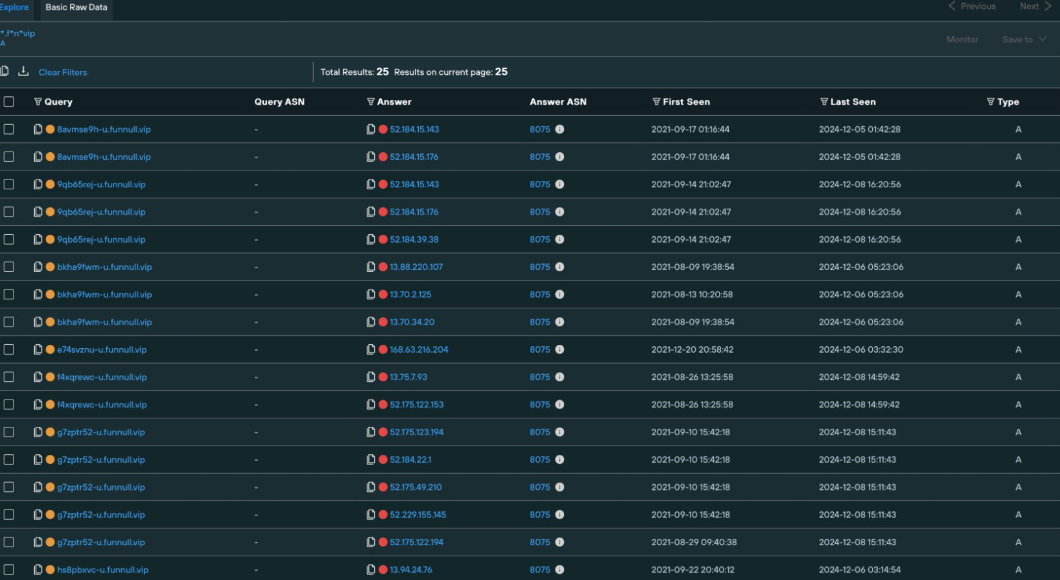
If using Silent Push to investigate FUNNULL, you can conduct a forward A lookup on the three CNAME records they are mapping to rented IP addresses:
- fn03[.]vip Query Link
- fnvip100[.]com Query Link
- funnull100[.]com Query Link
These searches are done via our “Explore Indicator DNS Data” tool, which you can see in the screenshot below:
![Screenshot of Silent Push application showing results of a Forward A lookup of *funnull100[.]com.](https://www.silentpush.com/wp-content/uploads/Infra-laundering-screenshot-of-Forward-A-lookup-funnull100-using-SP-1.png)
As mentioned extensively, it appears both Amazon and Microsoft are essentially “under attack” by FUNNULL due to efforts to use numerous accounts to acquire IP addresses. FUNNULL essentially has agents moving faster than both of the companies, but you can see the takedowns and any new IPs via the queries included above.
To facilitate ad hoc investigations for anyone who doesn’t have a Silent Push account, we’ve included a small sample in the table below of some recent IPs rented by the FUNNULL CDN, which were owned by Microsoft or Amazon.
Thanks to collaborative efforts with our research team, FUNNULL should be banned from all of these listed IPs by the time of publishing, and we would like to express our appreciation for the efforts of both Microsoft and Amazon for trying to stop this ongoing abuse of their networks.
- AS8075 (MICROSOFT)
- AS16509 (AMAZON)
| ASN | IP Address |
| 8075 | 20.197.231[.]47 |
| 8075 | 20.255.59[.]117 |
| 8075 | 20.198.57[.]52 |
| 8075 | 104.214.176[.]22 |
| 8075 | 20.189.72[.]50 |
| 8075 | 20.244.100[.]21 |
| 8075 | 4.242.33[.]86 |
| 8075 | 20.255.249[.]158 |
| 8075 | 23.102.230[.]2 |
| 8075 | 4.240.77[.]234 |
| 8075 | 52.231.111[.]19 |
| 8075 | 20.201.125[.]114 |
| 8075 | 20.244.107[.]99 |
| 8075 | 20.255.50[.]154 |
| 8075 | 4.186.60[.]206 |
| 8075 | 20.205.30[.]219 |
| 8075 | 20.255.50[.]152 |
| 8075 | 52.247.251[.]209 |
| 8075 | 98.70.33[.]48 |
| 8075 | 4.240.75[.]72 |
| 8075 | 20.205.24[.]187 |
| 8075 | 20.187.147[.]2 |
| 16509 | 18.162.61[.]241 |
| 16509 | 18.163.117[.]178 |
| 16509 | 43.198.139[.]94 |
| 16509 | 18.166.63[.]180 |
| 16509 | 43.199.45[.]50 |
| 16509 | 18.162.151[.]226 |
| 16509 | 18.163.62[.]136 |
| 16509 | 16.163.103[.]39 |
| 16509 | 43.198.71[.]66 |
| 16509 | 35.78.66[.]160 |
| 16509 | 18.162.126[.]85 |
| 16509 | 18.163.8[.]163 |
| 16509 | 35.78.207[.]138 |
| 16509 | 18.162.151[.]167 |
| 16509 | 18.163.105[.]72 |
| 16509 | 18.163.183[.]181 |
| 16509 | 13.201.230[.]164 |
| 16509 | 43.199.134[.]208 |
| 16509 | 15.220.86[.]254 |
| 16509 | 18.162.146[.]57 |
| 16509 | 43.199.135[.]180 |
| 16509 | 18.182.24[.]73 |
| 16509 | 18.166.74[.]138 |
| 16509 | 18.163.189[.]59 |
| 16509 | 18.183.220[.]150 |
| 16509 | 18.163.55[.]222 |
| 16509 | 18.162.155[.]216 |
| 16509 | 18.167.96[.]56 |
| 16509 | 18.167.84[.]151 |
| 16509 | 43.198.31[.]47 |
| 16509 | 18.167.167[.]242 |
| 16509 | 18.166.78[.]43 |
| 16509 | 18.163.102[.]152 |
| 16509 | 18.166.74[.]182 |
| 16509 | 18.163.5[.]170 |
| 16509 | 18.163.8[.]154 |
| 16509 | 13.245.28[.]4 |
| 16509 | 13.247.101[.]138 |
| 16509 | 18.163.190[.]206 |
| 16509 | 43.198.21[.]215 |
| 16509 | 18.167.120[.]251 |
| 16509 | 18.166.77[.]70 |
| 16509 | 18.163.187[.]139 |
| 16509 | 18.166.67[.]99 |
| 16509 | 43.198.74[.]22 |
| 16509 | 18.167.12[.]32 |
| 16509 | 13.250.46[.]202 |
| 16509 | 18.166.51[.]9 |
| 16509 | 18.162.125[.]133 |
| 16509 | 18.166.74[.]48 |
| 16509 | 18.162.148[.]112 |
| 16509 | 18.163.5[.]121 |
| 16509 | 43.198.137[.]209 |
| 16509 | 18.167.68[.]76 |
| 16509 | 43.198.137[.]11 |
| 16509 | 18.163.50[.]251 |
| 16509 | 18.163.190[.]57 |
| 16509 | 13.202.94[.]191 |
| 16509 | 43.198.23[.]224 |
| 16509 | 15.220.83[.]92 |
| 16509 | 18.167.96[.]97 |
| 16509 | 18.166.74[.]44 |
| 16509 | 18.162.55[.]167 |
| 16509 | 18.162.134[.]4 |
| 16509 | 18.163.185[.]209 |
| 16509 | 18.167.103[.]17 |
| 16509 | 43.207.138[.]181 |
| 16509 | 18.162.148[.]219 |
| 16509 | 18.179.5[.]144 |
| 16509 | 18.167.103[.]205 |
| 16509 | 52.66.216[.]105 |
| 16509 | 18.166.58[.]42 |
| 16509 | 18.163.101[.]77 |
| 16509 | 18.163.129[.]197 |
| 16509 | 43.199.148[.]179 |
| 16509 | 18.166.55[.]111 |
| 16509 | 18.163.111[.]84 |
| 16509 | 18.167.116[.]54 |
| 16509 | 18.183.150[.]32 |
| 16509 | 43.199.135[.]111 |
| 16509 | 43.199.147[.]105 |
| 16509 | 18.163.105[.]202 |
| 16509 | 54.250.15[.]187 |
| 16509 | 18.163.190[.]230 |
| 16509 | 43.198.137[.]198 |
| 16509 | 52.198.10[.]138 |
| 16509 | 43.198.76[.]0 |
| 16509 | 18.167.96[.]137 |
| 16509 | 54.249.86[.]54 |
| 16509 | 18.166.58[.]36 |
| 16509 | 18.166.54[.]42 |
| 16509 | 18.166.65[.]147 |
| 16509 | 43.206.105[.]218 |
| 16509 | 18.166.65[.]127 |
| 16509 | 43.199.148[.]15 |
| 16509 | 18.166.51[.]252 |
| 16509 | 18.166.67[.]208 |
| 16509 | 43.199.146[.]85 |
| 16509 | 43.207.190[.]7 |
| 16509 | 54.255.167[.]157 |
| 16509 | 43.198.73[.]27 |
| 16509 | 43.198.77[.]99 |
| 16509 | 43.206.222[.]92 |
| 16509 | 43.199.136[.]74 |
| 16509 | 43.198.78[.]80 |
| 16509 | 18.162.151[.]254 |
| 16509 | 18.163.127[.]237 |
| 16509 | 35.78.73[.]152 |
| 16509 | 3.113.19[.]235 |
| 16509 | 43.198.71[.]199 |
| 16509 | 43.198.72[.]209 |
| 16509 | 43.198.78[.]18 |
| 16509 | 18.163.105[.]140 |
| 16509 | 18.166.55[.]109 |
| 16509 | 18.163.50[.]113 |
| 16509 | 18.167.85[.]174 |
| 16509 | 18.163.190[.]4 |
Looking Ahead, Bigger Questions Loom
As we noted previously, it is much easier for enterprises to defend against this type of crime if the services of mainstream providers are made unavailable to large criminal networks like FUNNULL.
And, while we can appreciate the challenges that cloud hosts are facing from a network that is using illicit means to acquire IPs, we believe the CNAME chain mapping techniques used by FUNNULL shine a bright light on all the IPs they have secretly rented
Several Questions Remain
- If the network is so clearly visible to us as cyber threat professionals, then why are cloud providers not able to take action in near real-time?
- Is this CNAME chain to illicit IP rental strategy an architecture that should be effective at keeping websites online?
- And finally, do cloud hosts have an obligation to conduct these types of investigations themselves so that networks like FUNNULL can’t host criminal schemes for years while the cloud hosts merely play whack-a-mole with IP rental takedowns?
Amazon’s Public Statement on the Matter
“Prior to receiving a draft of this report, AWS was already aware of the activity and were suspending the fraudulently-acquired accounts that we now know were linked to the activity described by the researcher. After we received a copy of the report, we continued our investigations and suspended additional accounts. All accounts known to be linked to the activity are suspended. We can confirm that there is no current risk from this activity, and no customer action is required.
The report claims that AWS in some way enables or at least turns a blind eye to this kind of activity, and profits from it. Those claims are false. The actor involved in this activity uses fraudulent methods to temporarily acquire infrastructure, for which it never actually pays. Thus, AWS incurs damages as a result of the abusive activity.
The report promotes a new ‘infrastructure laundering’ concept, but the concept doesn’t involve laundering, a process in which something illicit or “dirty” becomes legitimate or “clean.” By using that phrase, the report insinuates that AWS is the intermediary to make the abusive activity appear legitimate and thereby harder to detect or block. That’s incorrect. Detecting the abuse of and/or blocking public IP addresses of cloud infrastructure is no more difficult than with any other public IP addresses.
When AWS’s automated or manual systems detect potential abuse, or when we receive reports of potential abuse, we act quickly to investigate and take action to stop any prohibited activity. In the event anyone suspects that AWS resources are being used for abusive activity, we encourage them to report it to AWS Trust & Safety using the report abuse form at https://support.aws.amazon.com/#/contacts/report-abuse
In this case, the authors of the report never notified AWS of the findings of their research via our easy-to-find security and abuse reporting channels. Instead, AWS first learned of their research from a journalist to whom the researchers had provided a draft. AWS had to contact the researchers proactively to obtain a draft of the report before publication.”
— End Public Statement —
Silent Push appreciates Amazon’s willingness to engage in constructive discourse on this matter. Our platform and data provide us with an excellent vantage point from which to track and monitor this type of activity at scale, as we have done for the last few years. In terms of AWS infrastructure utilized by FUNNULL, we have been tracking this threat’s use of Amazon IPs for nearly two years – during which Amazon has certainly put effort into identifying and taking down the instances their teams have uncovered.
We want to recognize that effort and share that we understand the difficulties inherent to mapping CNAME connections at this kind of scale. Particularly when new examples show up all the time, such as http[:]//43[.]198[.]25[.]172, which is actively hosted on AWS, displays the FUNNULL error page (as of this writing), and is mapped to the fn03.vip CNAME. We know it can be challenging for security teams to keep pace with the rapid emergence of new threats, but appreciate everyone’s efforts to stay informed on how criminals are attempting to obscure their activity by hiding among legitimately hosted cloud traffic.
Silent Push shines in this area, and we look forward to working with AWS on this matter in the future — from sharing our expertise in tracking criminal actors engaged in infrastructure laundering with defenders to illuminating these threats with public discussion.
Continuing to Track Infrastructure Laundering
Our team continues to track infrastructure laundering in all of its ever-evolving forms. We will report our findings to the security community as we identify new developments and other threat actors taking advantage of the practice.
We will also continue to share our research on threats we discover with law enforcement. If you happen to have any tips about threat actors participating in infrastructure laundering or engaging in other types of crime obfuscation activities, our team would love to hear from you.
Mitigation
Silent Push believes all domains associated with infrastructure laundering present some level of risk.
Our analysts construct Silent Push IOFA Feeds that provide a growing list of Indicators of Future Attack data focused on scams supported by this technique.
Silent Push Indicators of Future Attacks (IOFA) Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.
Click here to sign up for a free account.


