Threat intelligence data can broadly be described as information that’s collected, processed, and analyzed to understand potential cyber threats, and helps organizations anticipate, identify, and mitigate attacks.
In this blog, we’ll compare the two main types of threat intelligence data used by security teams – Silent Push Indicators of Future Attack (IOFA)™, and traditional Indicators of Compromise (IOC).
We’ll highlight the differences between both, and why organizations find more value in using IOFA™ as a source of threat intelligence to identify and block adversary infrastructure before an attack is launched.
What are IOCs?
IOCs are reactive cybersecurity datapoints that indicate a system has been targeted, or compromised, in a cyberattack.
IOCs are distributed using various methods, from Open-Source Intelligence (OSINT) streams, to private collection methods, licensed intelligence platforms, public forums and Advanced Persistent Threat (APT) intelligence reports.
What are Indicators of Future Attack™ (IOFA™)?
Indicators of Future Attack™ are proactive indicators (hostname, domain, IP etc.) that preemptively reveal where an attack will be launched from in the future, as well as where an attack has taken place.
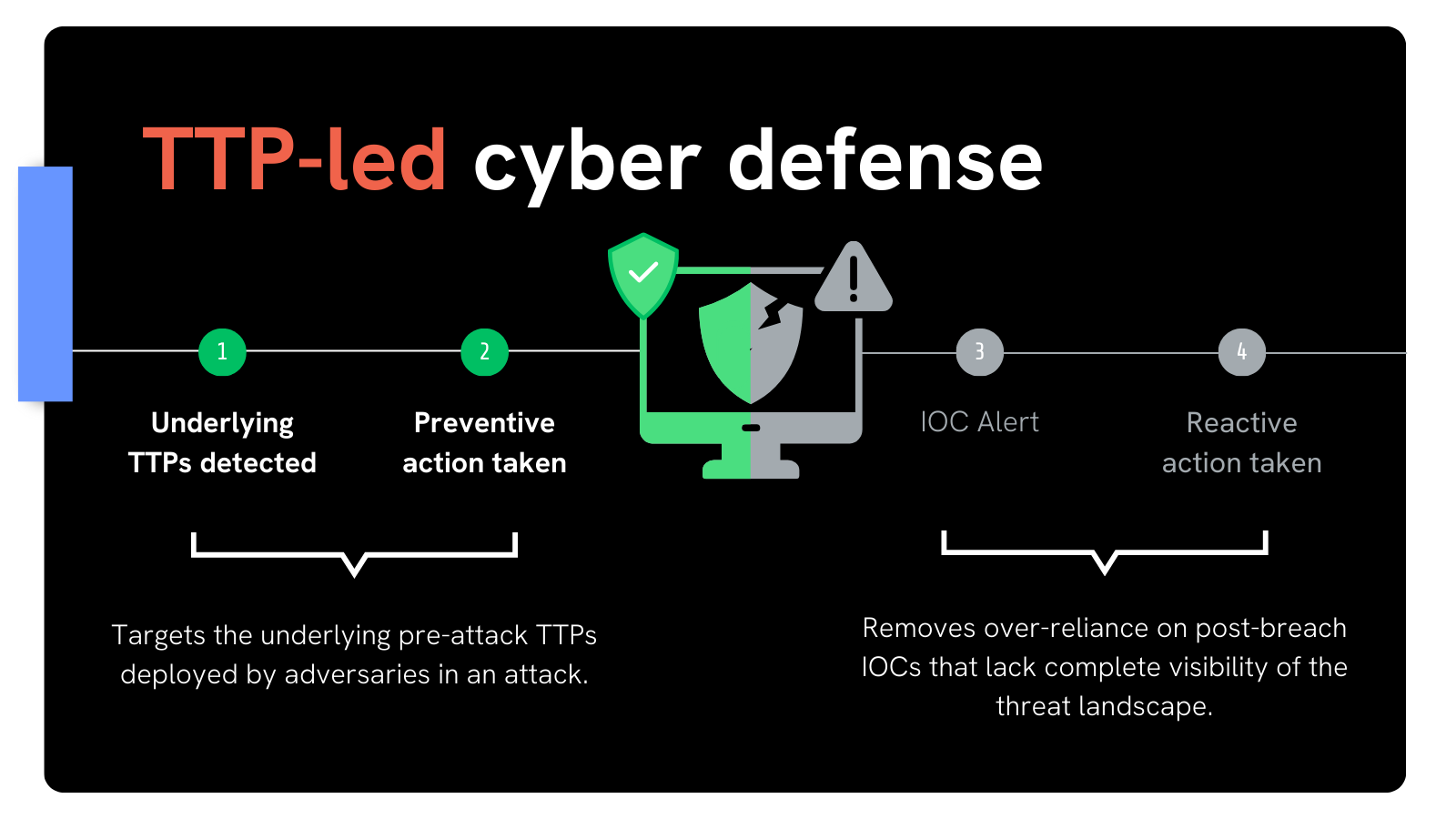
Security teams rely on IOFA™ data to target the pre-attack Tactics, Techniques and Procedures (TTPs) that govern how a threat actor is initializing and deploying their infrastructure, prior to an attack being launched.
Silent Push is the only security vendor that uses IOFA™ to detect and stop threats.

What is the main difference between Indicators of Future Attack™ and IOCs?
Using IOFA™ allows teams to shift from a reactive to proactive security operations.
Cyberattacks that originate from unknown infrastructure are inherently more difficult to block, and present a significantly higher risk.
An army prepares itself for battle based on where the enemy is located, and how they’re deploying their forces in an attack. Adversaries that disguise or hide their position are far trickier to defend against than an enemy that keeps launching an assault from the same position.
Cyber warfare is no different.
IOFA™ provide teams with actionable, finished threat intelligence that not only counteracts an ongoing attack, but allows teams to traverse the hidden elements of a threat campaign that are yet to be fully deployed, and track enemy movement across the global IP space.
IOCs do not allow security teams to easily establish where an adversary may strike next, and are instead limited to revealing where an attack has previously occurred.
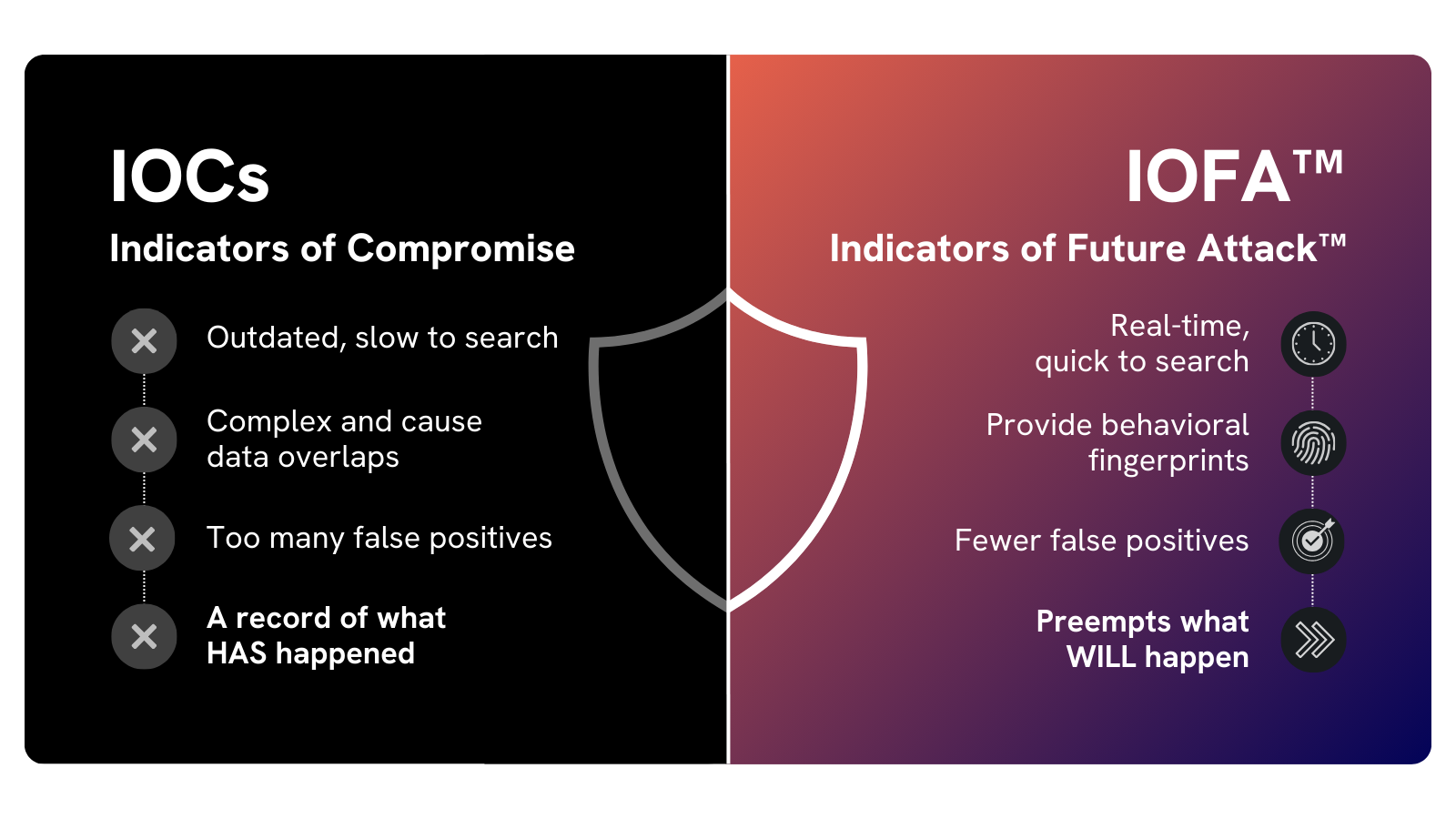
Let’s look at the key functional differences between IOFA™ and IOCs, and why IOFA™ are inherently more useful when attempting to defend against known and emerging attacks.
Enhanced threat context with Indicators of Future Attack™
An IOC is an isolated piece of data that can be used to block a domain or IP which has already been involved in an attack.
When using IOCs, teams need to enact multiple additional pivots to map out associated infrastructure and de-fragment their intelligence, which increases exposure during security incidents and pulls staff away from critical duties.
IOFA™ go one step further by automatically revealing associated hosting infrastructure, linked domains and IPs, and matching web content in such a way that provides SOC and IR teams with the ability to immediately and reliably triage information, the moment it’s received.
Searchable attributes
IOCs are accumulated from multiple distinct sources. As such, they do not feature a homogenous set of searchable attributes that can be used to quickly operationalize intelligence data, and facilitate broader discovery of potential threats.
IOFA™ are sourced, aggregated and scored by Silent Push alone. This allows us to apply 150+ attributes to each individual hostname, domain or IP that can be used across the platform to conduct one-click pivots, scans and lookups to quickly and reliably establish the relationship a single indicator has with the rest of the observable Internet.
Tracking changes in infrastructure
Attackers recycle through new domains and IPs at a rapid rate, in order to evade detection, obfuscate their attack vectors, and circumvent IOC-led cyber defense mechanisms that rely on isolated lists of post-breach IOCs.
IOFA™ act as a source of finished intelligence that – by targeting attacker TTPs which act as the thick end of the wedge – continually considers the various methods adversaries use to deploy new infrastructure (e.g. fast flux techniques, hosting changes, naming conventions, and the use of subdomains), and updates teams with real-time tactical insights that are ready to be acted upon.
These insights are then used to construct behavioral fingerprints of adversary activity that allow teams to shadow an adversary’s movements across the IP space, and block any future attempts at launching an attack using a different piece of infrastructure.
Reducing false positive
Whether it’s licensed or open-sourced, an individual IOC is provided to security teams with minimal information on where a piece of intelligence has originated from, or how relevant it is to the organization using the information.
As such, IOC-based threat feeds are noisy, and contain a high percentage of false positive domains and IPs, or outdated indicators that are no longer being used in an attack. Such intelligence is at best overvalued, or at worst, useless.
Silent Push IOFA™ feeds contain attributable true positive indicators that require zero manual intervention to validate as a reliable source of intelligence.
We deliver IOFA™ data using on a proprietary aggregation and corroboration process that provides immediately actionable intelligence, lowering an organization’s MTTD and MTTR.
Learn more about IOFA™ and our approach to preemptive threat intelligence
Silent Push is the only cybersecurity platform that uses IOFA™ to preemptively reveal pre-attack infrastructure, allowing teams to detect and block digital assaults as they emerge and before they’re launched.
If you’re interested in learning about how we can help you to protect your infrastructure from known and hidden attacks, contact us for more information.



