"Don't feed the toll troll": Silent Push tracks new threat actor (IMP-1G) engaging in SMS phishing activities, targeting US and Canadian public services. 100+ IOFA domains discovered, with only 10% known to authorities.

Executive Summary
Silent Push Threat Analysts have developed a method for locating and tracking the deployment of SMS phishing domains – a.k.a. “smishing” – from a previously unknown threat actor, who we are designating IMP-1G.
The domains involved target users of US and Canadian regional and national public services, along with a quantity of standard financial phishing domains.
Services targeted include toll roads, mass transit systems, postal services, court payments, municipal payments, and state-owned utility companies.
US states targeted include San Francisco, Massachusetts, Florida, Georgia, Illinois, Indiana, Washington, North Carolina, New York, Ohio, Pennsylvania, Texas, Kansas, South Carolina, and Tennessee.
Canadian provinces and cities targeted include Montreal, Alberta, British Colombia, Edmonton, and Ontario.
From a single origin domain, our Analysts used the Silent Push Web Scanner to expose 100+ Indicator of Future Attack (IOFA) domains, 66 of which are involved in the aforementioned government smishing activity, with only 10% known to national law enforcement in the form of seizure notices.
Additional information
This blog contains a public overview of how we located, traversed and tracked the deployment of IMP-1G’s US and Canadian government services smishing domains, and associated phishing infrastructure.
Certain key Silent Push Web Scanner data types have been omitted for OPSEC reasons. Interested parties can email [email protected] with any queries.
Silent Push Web Scanner is available as part of a free Community Edition subscription. Sign-up here.
Background
Smishing involves a threat actor sending an unsolicited SMS message to a victim’s cell phone, usually containing a malicious link to a spoofed domain that’s then used to exfiltrate data, such as identity documents or payment card information.
In April 2024, the DOJ issued a public service announcement warning the public about smishing scams targeting toll road users, following a large amount of IC3 reports:
In June 2024, the US Postal Service issued an advisory on fake package tracking messages being sent to citizens’ devices.
In May 2024, the FTC published a consumer alert detailing scam SMS messages asking users to pay an overdue toll fine.
SMS toll fraud – which features heavily in our research – involves a range of attack vectors, including the use of short codes or premium-rate phone numbers to extract money via the victim’s phone bill, and identity theft.
SMS phishing isn’t limited to users of government services. In July of last year, we published research outlining a complex brand impersonation smishing scam, targeting customers of US banks and financial institutions.
Initial intelligence report
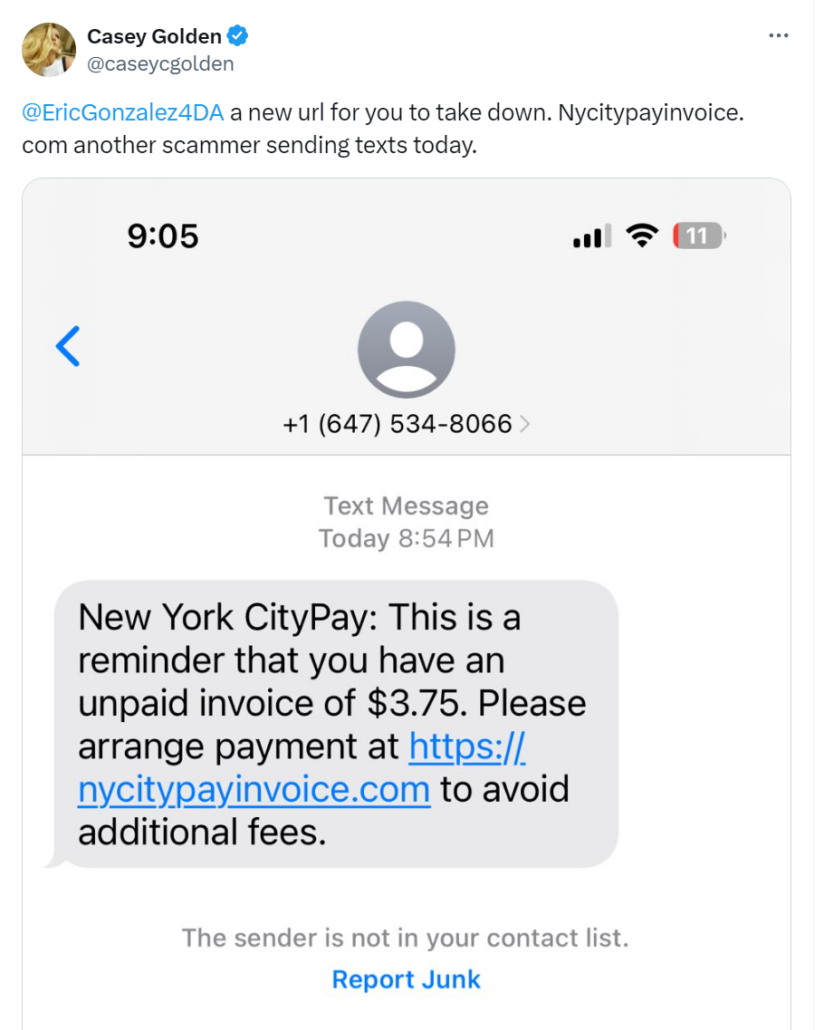
Recent reports on X linked the domain nycitypayinvoice[.]com to an SMS phishing campaign that attempted to steal users’ credit card information, via a fake NYC payment order:
The domain was subsequently seized by the Kings County District Attorney’s office:

Pivot: Tracking IMP-1G metadata
To traverse associated infrastructure, our analysts constructed a custom Silent Push Web Scanner query, using a proprietary hash value, that tracked nycitypayinvoice[.]com metadata and on-page content.
This led us to a further cluster of domains, all with shared data characteristics (that we aren’t able to divulge in a public blog), engaged in the same government payment fraud activity, including:
- southernconnectortolls[.]com
- uspsmailupdate[.]com
- gapeachpasstolls[.]com
- paturnpikeinvoices[.]com
- bcpay-infraction[.]com
- us-courtweb[.]com
Pivot: Refining the regional IMP-1G datasets
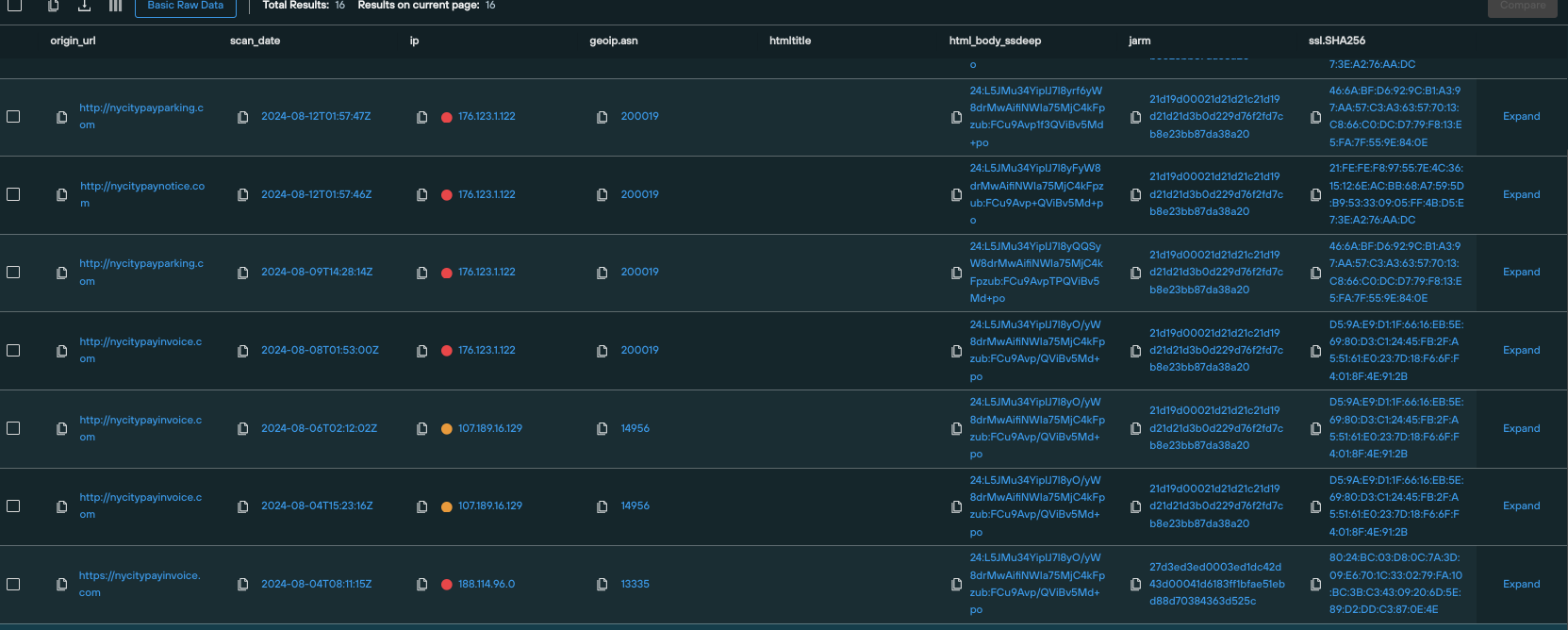
To produce regional datasets of active domains, we amended our query to focus on state-specific infrastructure, and excluded any domains that returned a 404 error.
Here’s a results set featuring active domains targeting service users in NYC:
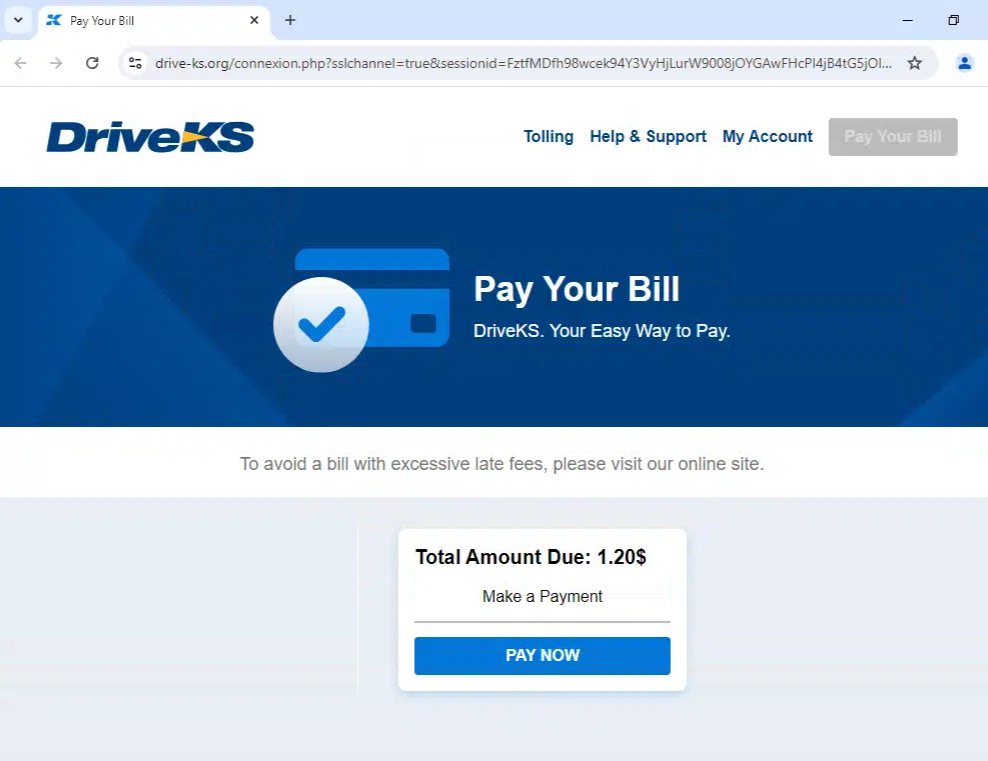
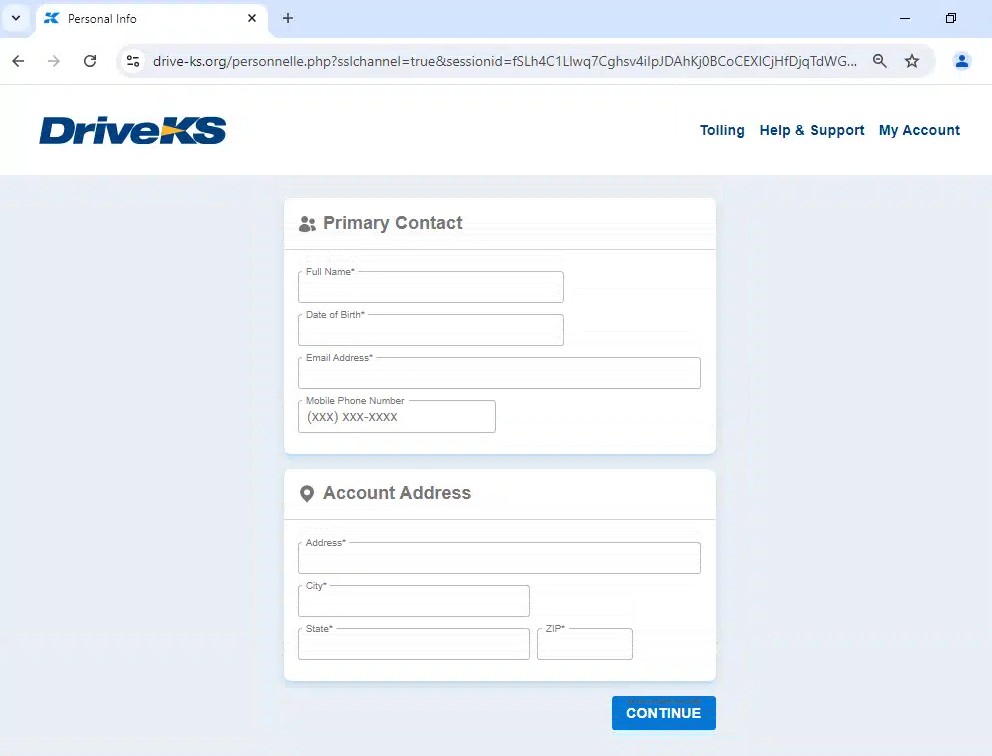
Here’s another example domain, this time targeting toll users in Kansas (drive-ks[.]org). It starts with a landing page sent from an SMS message, which then progresses to data harvesting, including payment card information:
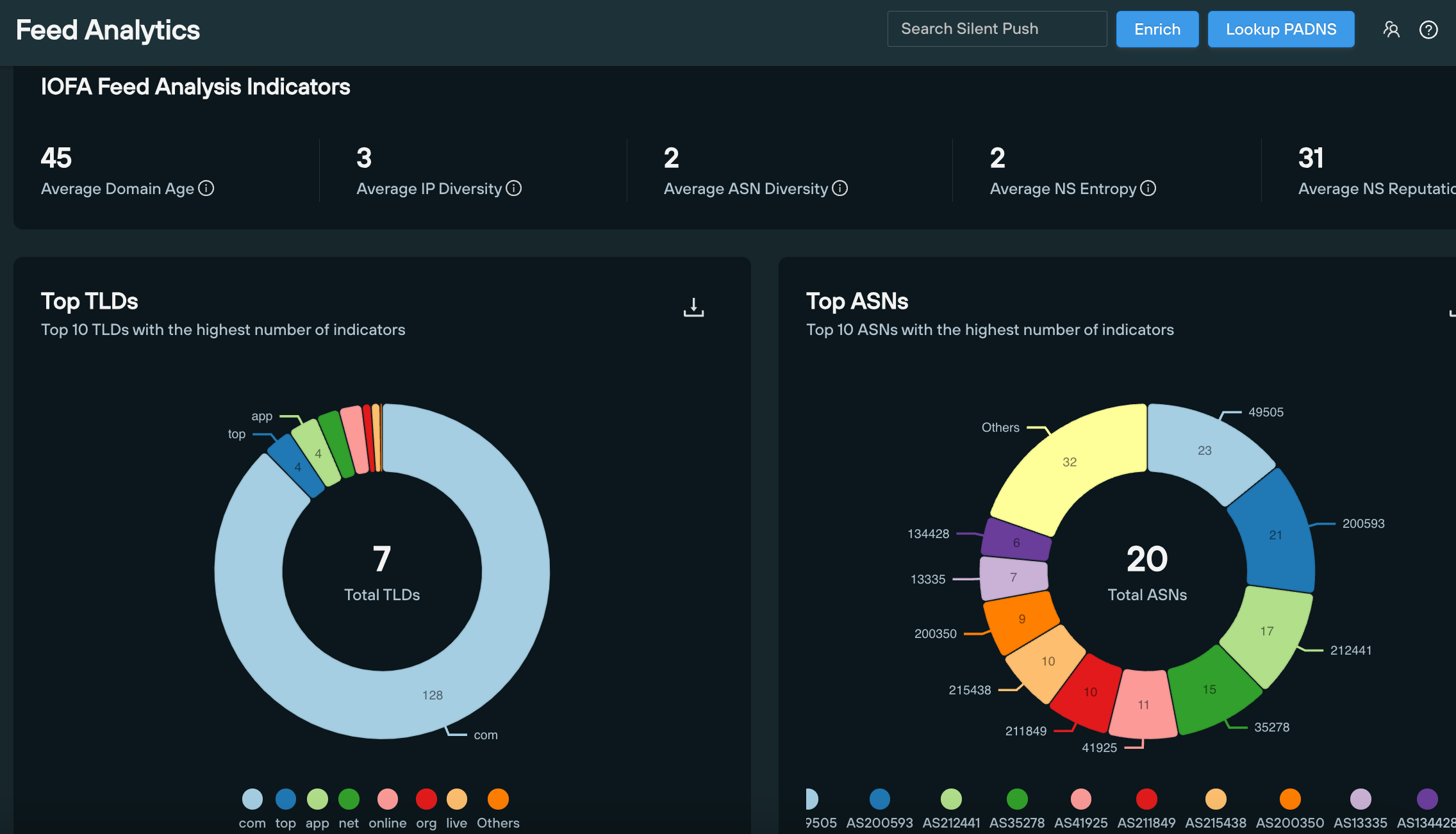
IMP-1G IOFA Feed Analysis
We’ve constructed an IOFA Feed built from the various query and scan parameters our Analysts used to track the deployment of IMP-1G’s infrastructure across the Internet.
As of this writing, our feed contains 101 active threat domains, 66 of which are involved in US and Canadian government services phishing, with the remainder (35) involved in generic financial and crypto phishing activity (see below section).
43 of the 66 government services domains target toll road and mass transit users, with the remainder dedicated to various regional and national government revenue services, including court payments, city fines and postal services.
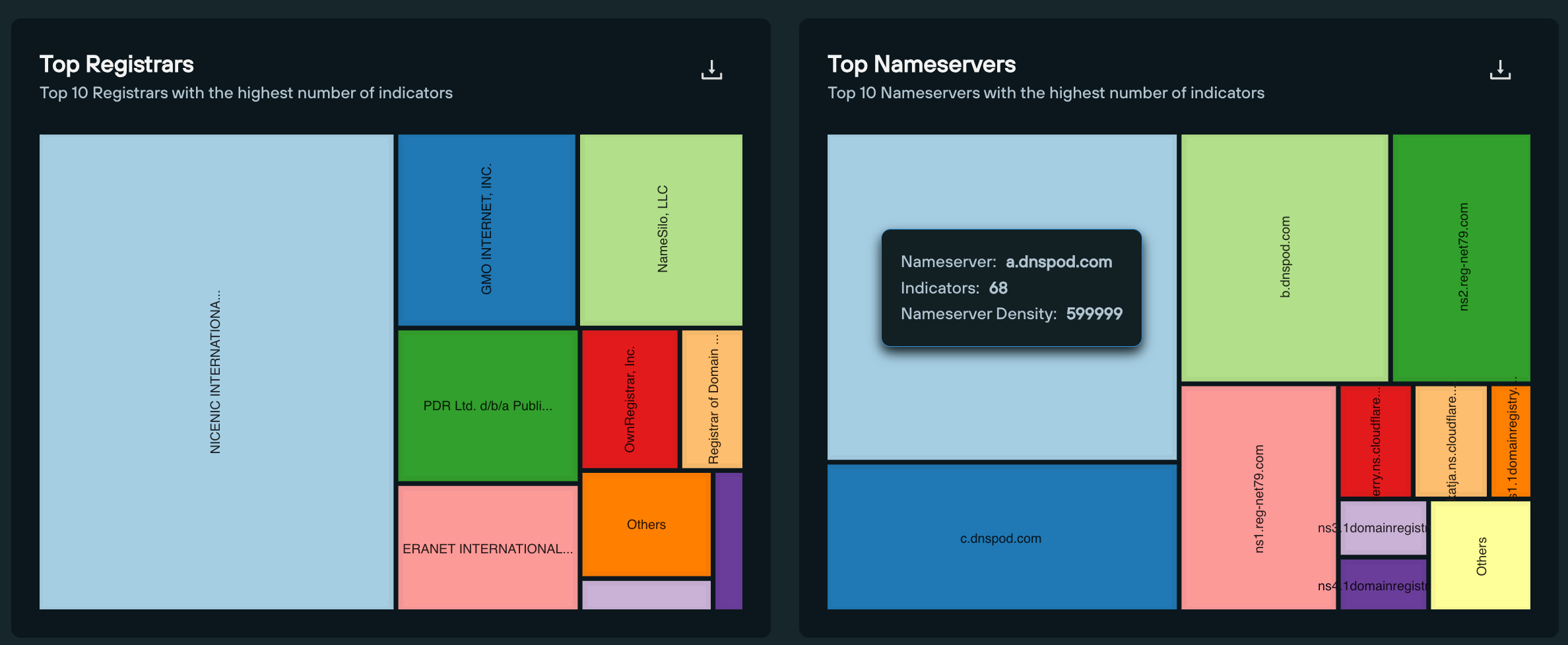
Exactly two thirds (44) of domains target US users, with 20 domains directed at Canadian services.
As of writing, only 6 of the 66 domains feature seizure notices. Meaning only 10% of IMP-1G infrastructure is known by national law enforcement agencies.
Here’s the full list of known and unknown government phishing domains, as per our research:
Unknown infrastructure
| Domain | Region | Service |
| a25-bridgepayment[.]com | Montreal | Transit |
| alberta-accounts[.]com | Alberta | Regional government |
| alberta-infractions[.]com | Alberta | Regional government |
| alberta-traffictickets[.]com | Alberta | Transit |
| bayareafastrak-fees[.]com | San Francisco | Transit |
| bayareafastrakexpresslane[.]com | San Francisco | Transit |
| bayareafastrakinvoice[.]com | San Francisco | Transit |
| bayareafastrakinvoices[.]com | San Francisco | Transit |
| bayareafastrakstolls[.]com | San Francisco | Transit |
| bayareasf-fastrak[.]com | San Francisco | Transit |
| bc-fine[.]com | British Columbia | Regional government |
| bc-infractions[.]com | British Columbia | Regional government |
| bcpay-accounts[.]com | British Columbia | Regional government |
| bcpay-infraction[.]com | British Columbia | Regional government |
| canadapost-packagecenter[.]com | Canadian Government | Postal |
| depositetransfercanada[.]com | Canadian Government | National government |
| epcor-account[.]com | Edmonton | Utilities |
| expresstollinvoice[.]com | N/A | Transit |
| ezdrivemas[.]com | Massachusetts | Transit |
| ezdrivematoll[.]com | Massachusetts | Transit |
| ezdrivematolls[.]com | Massachusetts | Transit |
| fastrak-payment[.]com | San Francisco | Transit |
| floridasunpassinvoice[.]com | Florida | Transit |
| flpayheresunpass[.]com | Florida | Transit |
| flsunpasspayhere[.]com | Florida | Transit |
| gapeachpasstolls[.]com | Georgia | Transit |
| illinoistollwayinvoice[.]com | Illinois | Transit |
| indianatollroads[.]com | Indiana | Transit |
| invoicesezdrivematolls[.]com | Massachusetts | Transit |
| mygoodtogoinvoice[.]com | Washington State | Transit |
| mysunpassinvoices[.]com | Florida | Transit |
| mysunpasstollsinvoices[.]com | Florida | Transit |
| ncquickpassinvoice[.]com | North Carolina | Transit |
| nycitypaynotice[.]com | New York City | Regional government |
| nycitypayparking[.]com | New York City | Transit |
| oh-lanes[.]com | Ohio | Transit |
| ohioturnpiketolls[.]org | Ohio | Transit |
| ontario-courtspayment[.]com | Ontario | Regional government |
| ontariocanadacourt[.]com | Ontario | Regional government |
| ontariocourts-setfines-ca[.]com | Ontario | Regional government |
| ontariocourts-webpayment[.]com | Ontario | Regional government |
| ontariowebcourt-ca[.]com | Ontario | Regional government |
| paturnpikeinvoices[.]com | Pennsylvania | Transit |
| paturnpikestolls[.]com | Pennsylvania | Transit |
| paturnpiketollsinvoices[.]com | Pennsylvania | Transit |
| pay-directnow[.]app | N/A | N/A |
| paybc-account[.]com | British Columbia | Regional government |
| paybc-fine[.]com | British Columbia | Regional government |
| paybc-infraction[.]com | British Columbia | Regional government |
| peachpasstolls[.]com | Georgia | Transit |
| peachpasstollservices[.]com | Georgia | Transit |
| revenuecanadadeposit[.]com | Canadian Government | National government |
| rmatollservices[.]com | Texas | Transit |
| service-courtus[.]com | US Government | National government |
| southernconnectortolls[.]com | South Carolina | Transit |
| sunpassinvoice[.]com | Florida | Transit |
| sunpassinvoices[.]com | Florida | Transit |
| sunpassinvoicestolls[.]com | Florida | Transit |
| sunpasstollcheckout[.]com | Florida | Transit |
| sunpasstollinvoices[.]com | Florida | Transit |
| tennessetollinvoices[.]com | Tennesse | Transit |
| texasrmatoll[.]com | Texas | Transit |
| tollon407-etr[.]com | Ontario | Transit |
| tollservicesma[.]com | Texas | Transit |
| us-courtweb[.]com | US Government | National government |
| uscourt-ticket[.]com | US Government | National government |
Seized infrastructure
| Domain | Service | Seizure authority |
| nycitypay[.]com | Regional government | Kings County District Attorney |
| nycitypayinvoice[.]com | Regional government | Kings County District Attorney |
| sunpasstollsbill[.]com | Transit | Florida Department of Law Enforcement |
| tollbymailsnyinvoice[.]com | Transit | Kings County District Attorney |
| tollsbymailnyinvoice[.]com | Transit | Kings County District Attorney |
| tollsbymailsinvoices[.]com | Transit | Kings County District Attorney |
Other IMP-1G Phishing Activity
As is usually the case with threat actors engaged in phishing activities, IMP-1G aren’t limiting themselves to public services.
Using proprietary content hashing, our researchers tracked numerous private IPs hosting IMPG-1G phishing domains with the following characteristics spread across different domain clusters:
- .shop as a TLD
- A focus on financial and crypto phishing
- Random alphanumeric subdomains and apex domains, such as: inx-132244[.]shop
- Targeted phishing activities spoofing well-known crypto brands
- Deployed from July 2024 onwards
- Hosted using popular bulletproof ASNs, such as ALEXHOST MD (200019) and PONYNET US (53667)
| IP host | Number of domains |
|---|---|
| 176.123.1[.]122 | ~100 |
| 107.189.16[.]129 | ~60 |
| 185.12.14.83 | ~80 |
| 80.249.144[.]196 | ~100 |
| 77.232.41[.]192 | ~20 |
| 91.142.78[.]221 | 6 |
| 195.133.48[.]87 | 12 |
| 62.106.66[.]180 | 38 |
| 194.36.188[.]32 | 89 |
IMP-1G crypto phishing
Our researchers were able to track IMP-1G crypto phishing infrastructure using a Silent Push hash value that identified matching content across all associated crypto sites.
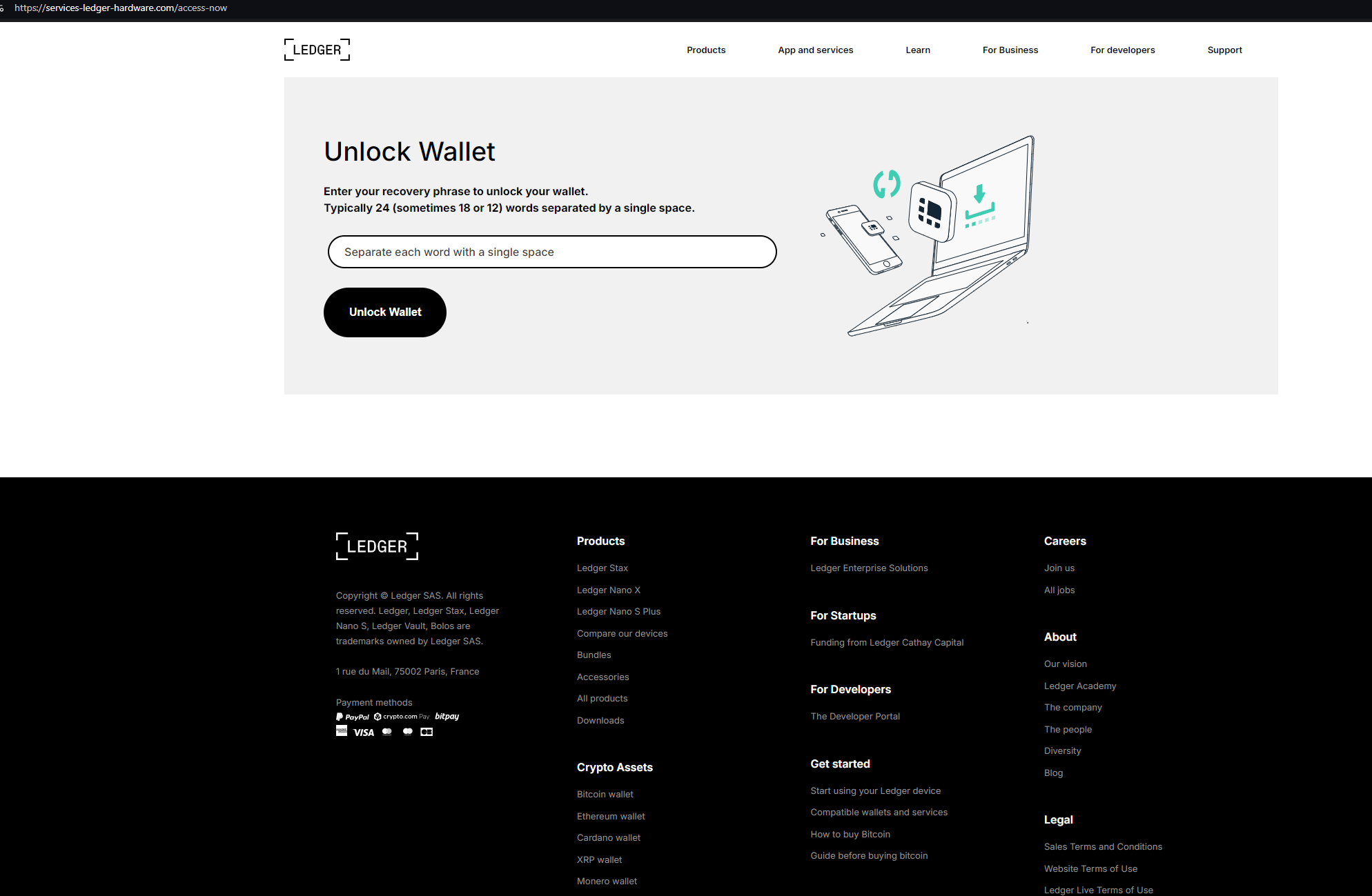
services-ledger-hardware[.]com hosts a login page attempting to phish Ledger recovery phrases and wallet data:
support-theta-token[.]com is attempting to phish users of Theta Wallet, with a pixel perfect copy of the legitimate website.
Here’s a side-by-side analysis of the two domains:
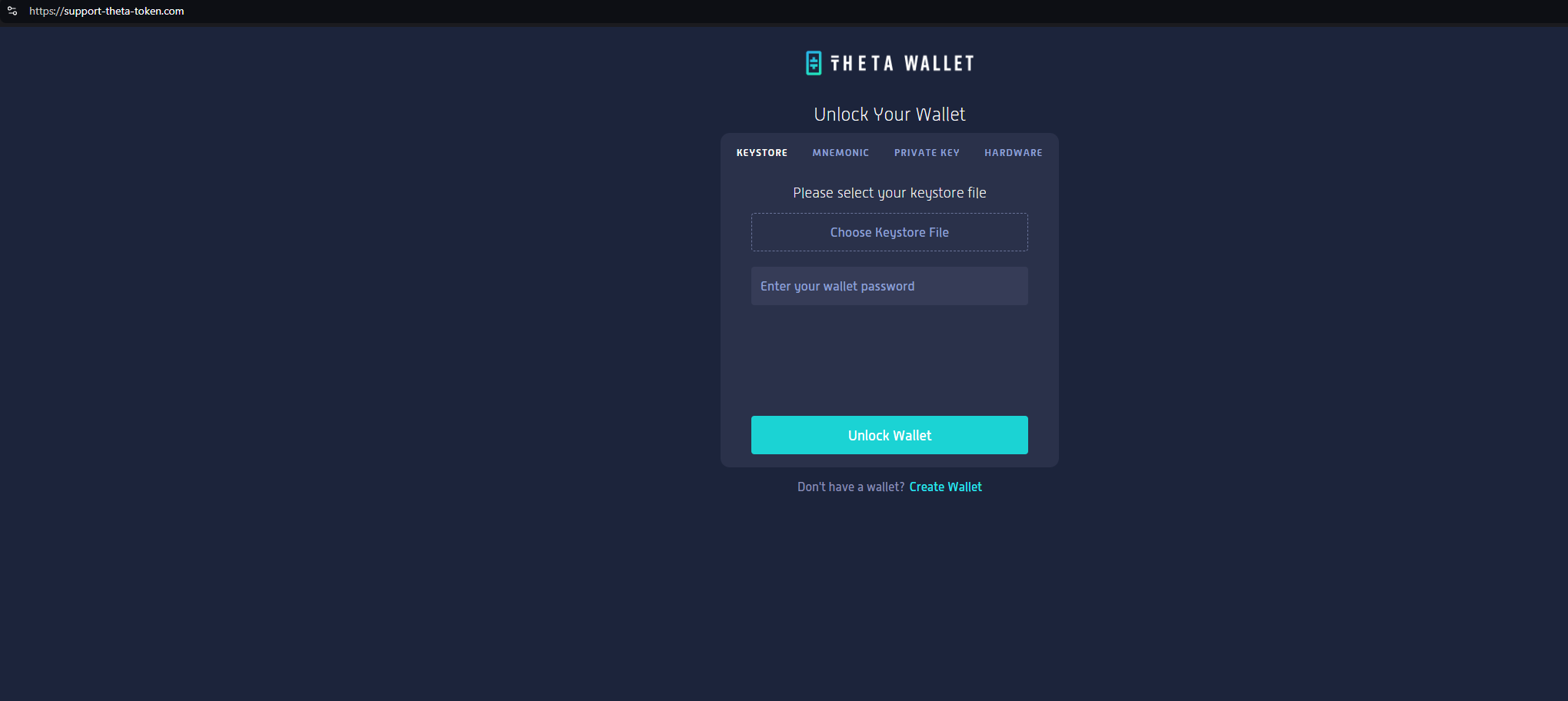
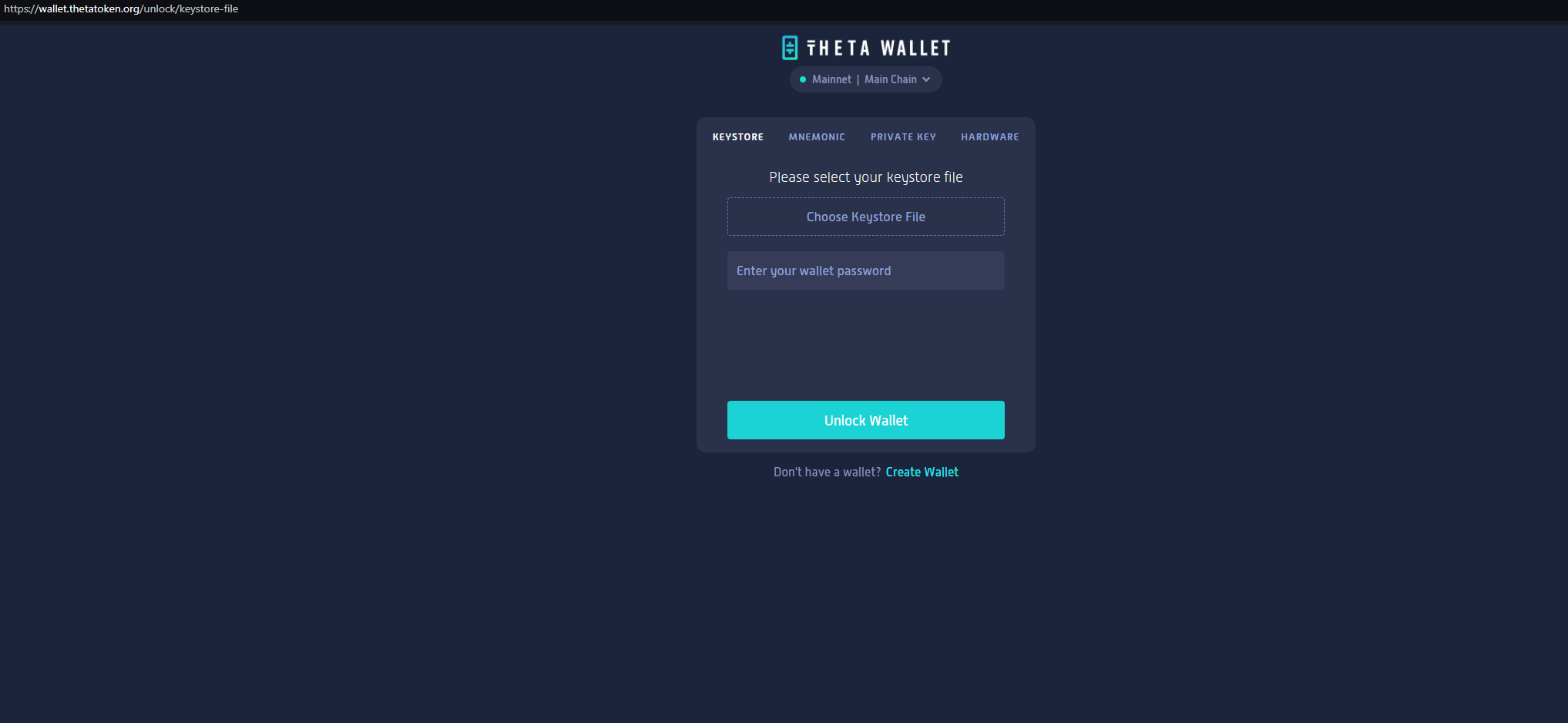
Register for a free Community Edition account
All of the queries, lookups and scans we used to locate, track and monitor IMP-1G infrastructure are available as part of Silent Push Community Edition – a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive tools.
Click here to sign up for a free account.
Enterprise users also have access to a dedicated IMP-1G IOFA Feed that contains a real time list of indicators from our research into the group.
Please reach out to us at [email protected] with any additional queries.
IMP-1G IOFAs
We’ve included the below indicators of public service smishing to aid law enforcement in their duties.
Silent Push Enterprise users have access to a dedicated IMP-1G IOFA Feed, updated in real-time with the full extent of IMP-1G indicators.
- southernconnectortolls[.]com
- uspsmailupdate[.]com
- gapeachpasstolls[.]com
- paturnpikeinvoices[.]com
- bcpay-infraction[.]com
- us-courtweb[.]com
- a25-bridgepayment[.]com
- alberta-accounts[.]com
- alberta-infractions[.]com
- alberta-traffictickets[.]com
- bayareafastrak-fees[.]com
- bayareafastrakexpresslane[.]com
- bayareafastrakinvoice[.]com
- bayareafastrakinvoices[.]com
- bayareafastrakstolls[.]com
- bayareasf-fastrak[.]com
- bc-fine[.]com
- bc-infractions[.]com
- bcpay-accounts[.]com
- bcpay-infraction[.]com
- canadapost-packagecenter[.]com
- depositetransfercanada[.]com
- epcor-account[.]com
- expresstollinvoice[.]com
- ezdrivemas[.]com
- ezdrivematoll[.]com
- ezdrivematolls[.]com
- fastrak-payment[.]com
- floridasunpassinvoice[.]com
- flpayheresunpass[.]com
- flsunpasspayhere[.]com
- gapeachpasstolls[.]com
- illinoistollwayinvoice[.]com
- indianatollroads[.]com
- invoicesezdrivematolls[.]com
- mygoodtogoinvoice[.]com
- mysunpassinvoices[.]com
- mysunpasstollsinvoices[.]com
- ncquickpassinvoice[.]com
- nycitypaynotice[.]com
- nycitypayparking[.]com
- oh-lanes[.]com
- ohioturnpiketolls[.]org
- ontario-courtspayment[.]com
- ontariocanadacourt[.]com
- ontariocourts-setfines-ca[.]com
- ontariocourts-webpayment[.]com
- ontariowebcourt-ca[.]com
- paturnpikeinvoices[.]com
- paturnpikestolls[.]com
- paturnpiketollsinvoices[.]com
- pay-directnow[.]app
- paybc-account[.]com
- paybc-fine[.]com
- paybc-infraction[.]com
- peachpasstolls[.]com
- peachpasstollservices[.]com
- revenuecanadadeposit[.]com
- rmatollservices[.]com
- service-courtus[.]com
- southernconnectortolls[.]com
- sunpassinvoice[.]com
- sunpassinvoices[.]com
- sunpassinvoicestolls[.]com
- sunpasstollcheckout[.]com
- sunpasstollinvoices[.]com
- tennessetollinvoices[.]com
- texasrmatoll[.]com
- tollon407-etr[.]com
- tollservicesma[.]com
- us-courtweb[.]com
- uscourt-ticket[.]com
- nycitypay[.]com
- nycitypayinvoice[.]com
- sunpasstollsbill[.]com
- tollbymailsnyinvoice[.]com
- tollsbymailnyinvoice[.]com
- tollsbymailsinvoices[.]com

