'Nuking the Duke': Silent Push uncovers control panel infrastructure for 24 different DukeEugene Android malware variants, including ERMAC and HOOKBOT

Executive Summary
Silent Push Threat Analysts have used fuzzy hash scans and content similarity queries to uncover 24 control panel Indicators of Future Attack (IOFA) administering MaaS services, for a range of DukeEugene variants – including ERMAC, Hook, Loot, and Pegasus – targeting users of popular mobile banking software and crypto currency exchanges.
Background
DukeEugene is the original threat actor behind the promotion of several android-based Malware-as-a-Service (MaaS) families, including both ERMAC and BlackRock, and later Hook which was published in early Jan 2023 on darknet[.]ug with bogus Russian-language commands hidden inside the malware that were later removed.
In April 2023, Duke Eugene claimed he was leaving the project for “SVO” (slang often used for Russian military service), however the project’s coder continued providing services and the HookBot builder panel’s code was leaked only three months later.
Since that leak, the proliferation of HookBot C2s offering a number of attack vectors (harvesting confidential information and login credentials, performing overlay attacks – where malware opens an active window over a legitimate program to intercept a victim’s interactions, and more) has spread wide. Even so, shared characteristics linking each of these MaaS families remain.
Additional information
This blog contains a public overview of how we at Silent Push have uncovered a host of control panels actively administering MaaS services for this range of DukeEugene-linked variants, including Ermac, Hook, Loot, and Pegasus – all targeting users of popular mobile banking software and crypto currency exchanges.
Silent Push Enterprise users have access to a dedicated TLP Amber report, containing the specific data categories and queries we used to locate and traverse DukeEugene’s infrastructure, as well 4 dedicated Android malware IOFA feeds.
Initial discovery: ERMAC control panel
While conducting research into a suspicious Russian ASN using the Silent Push Web Scanner, we discovered infrastructure linked to an ERMAC control panel.
We then constructed a Web Scanner query that took a piece of data from the ERMAC page, and scanned for all associated DukeEugene ERMAC control panels that used the same page content.
Traversing DukeEugene’s infrastructure
Once we’d mapped out the ERMAC infrastructure, we were able to hash the content, and execute a query that scanned the Internet for matching DukeEugene control panels that are 75% similar to the initial discovery.
This produced a large dataset, on which we executed further enrichment queries utilizing fuzzy hash values linked to a specific website, to confirm a host of true positive IOFAs.
This pivot then led us to other hash types and selected data categories, returning even more true positive examples of both live and dormant IOFA infrastructure.
DukeEugene control panels
We then queried the enriched data to uncover 24 DukeEugene-linked control panels (see IOFA list at the end of this blog for a sample), with the following names:
- AZAZEL
- BOTS PANEL
- CENTINEL BOT PANEL
- COMMAND
- CONSOLE
- Dashboard Seller
- Dd0XeR PANEL
- E.R.M.V.C
- HAXOR Tech Panel
- HAXORBOT PANEL
- HB RELOAD /GXC TEAM
- HOOK BOTNET
- HOOKBOT PANEL
- Hookbot Panel
- MOD
- NOTHING
- Pegasus PANEL
- SAMBOT PANEL
- Saphira Panel
- Scarab Botnet PANEL
- T-Devs Hook V2
- T-Rex PANEL
- VIP PANEL
- ZeuS
Not all of the above represent active control panels, but the naming schemas are part of our detections for this particular threat actor and are being shared here to help the community with their own defenses.
When active panels with the new HTML titles show up on live pages, they will be immediately detected and exposed by our Android malware feeds.
Control panel examples
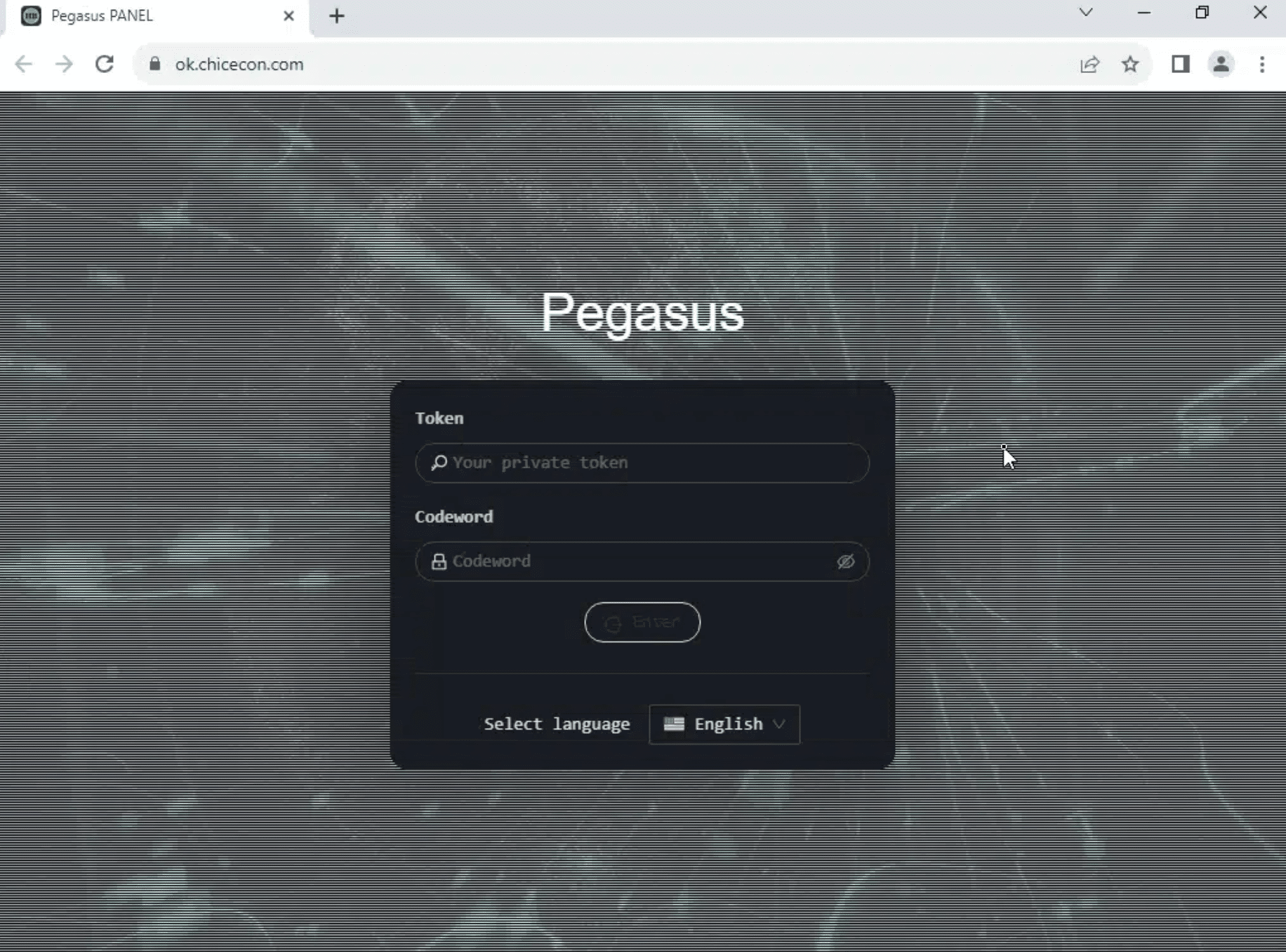
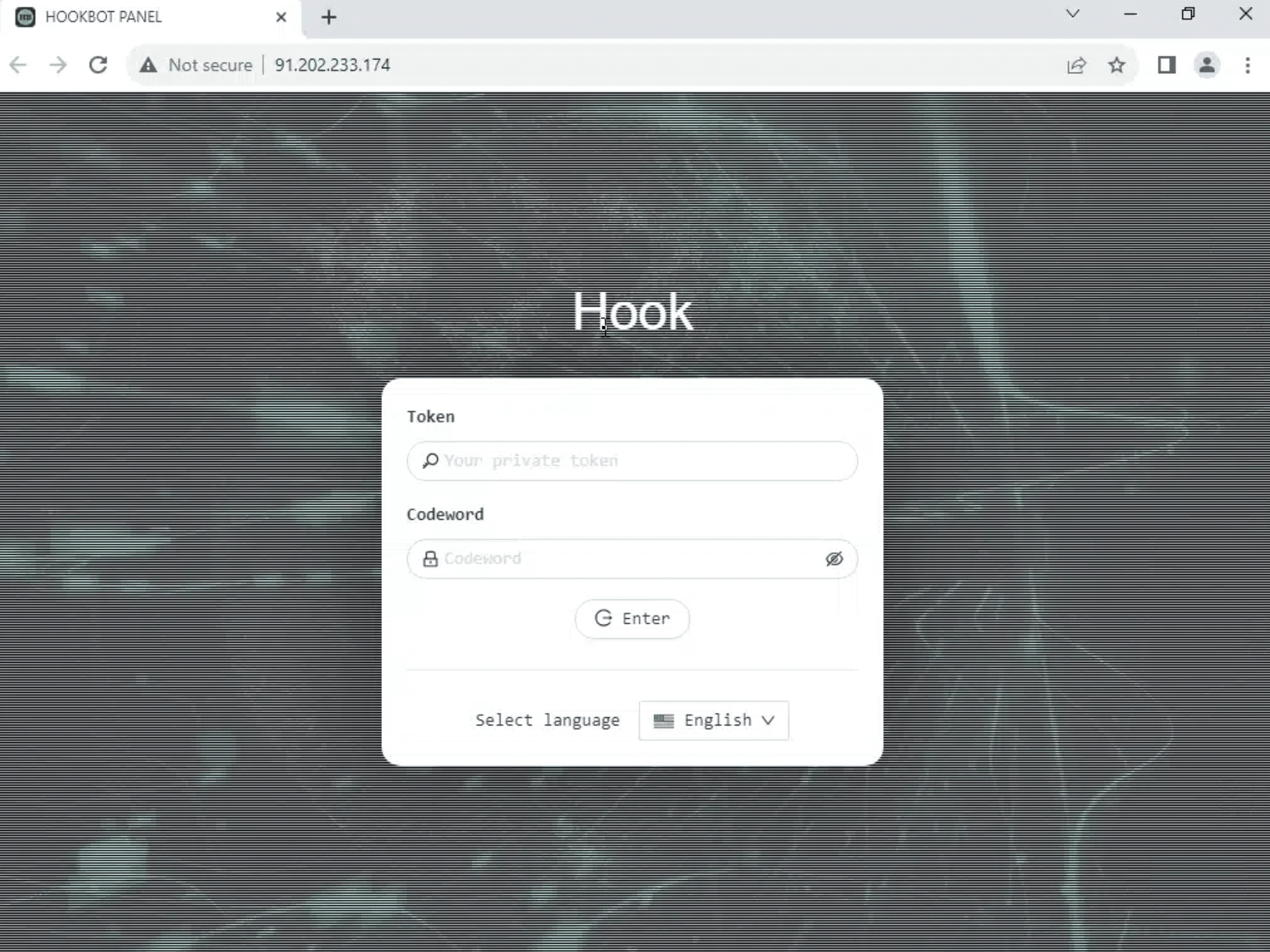
DukeEugene Mitigation
All domains and IP IOFAs gathered from this research are populated in the following Silent Push IOFA feeds, which are constantly updated:
- Android Malware – Duke Eugene Cluster
- Android Malware – Ermac IPs
- Android Malware – Hookbot Domains
- Android Malware – Hookbot IPs
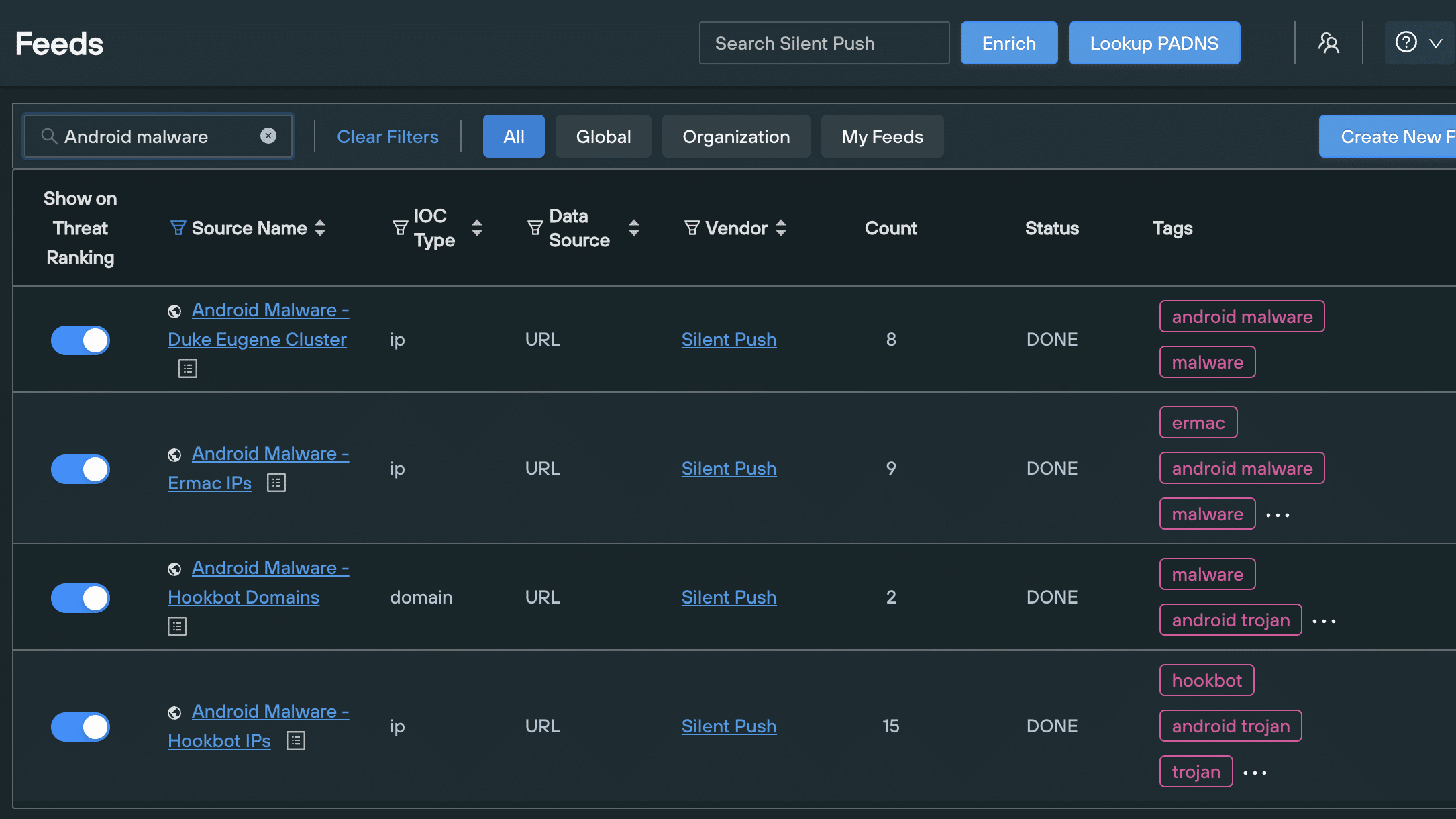
Silent Push Enterprise users can use data from the above feeds in three ways:
- Automated download of a data snapshot, using the ‘Automate Export’ button.
- Use a dynamic API for real time ingestion, using the ‘Manual Export’ button.
- Filter each feed using custom filter profiles.
Sample of DukeEugene IOFAs
Note: A full list of domain and IP IOFAs linked to our DukeEugene research can be accessed via a Silent Push Enterprise subscription, across 4 dedicated Android malware feeds. This sample is provided to our readers to aid in their detections.
HookBot control panel IPs
140.99.130[.]21
147.45.47[.]40
185.196.10[.]211
185.208.158[.]109
185.208.158[.]112
185.208.158[.]47
ERMAC control panel IPs
146.103.45[.]72
147.45.47[.]40
159.100.14[.]22
185.216.70[.]189
51.103.213[.]218

