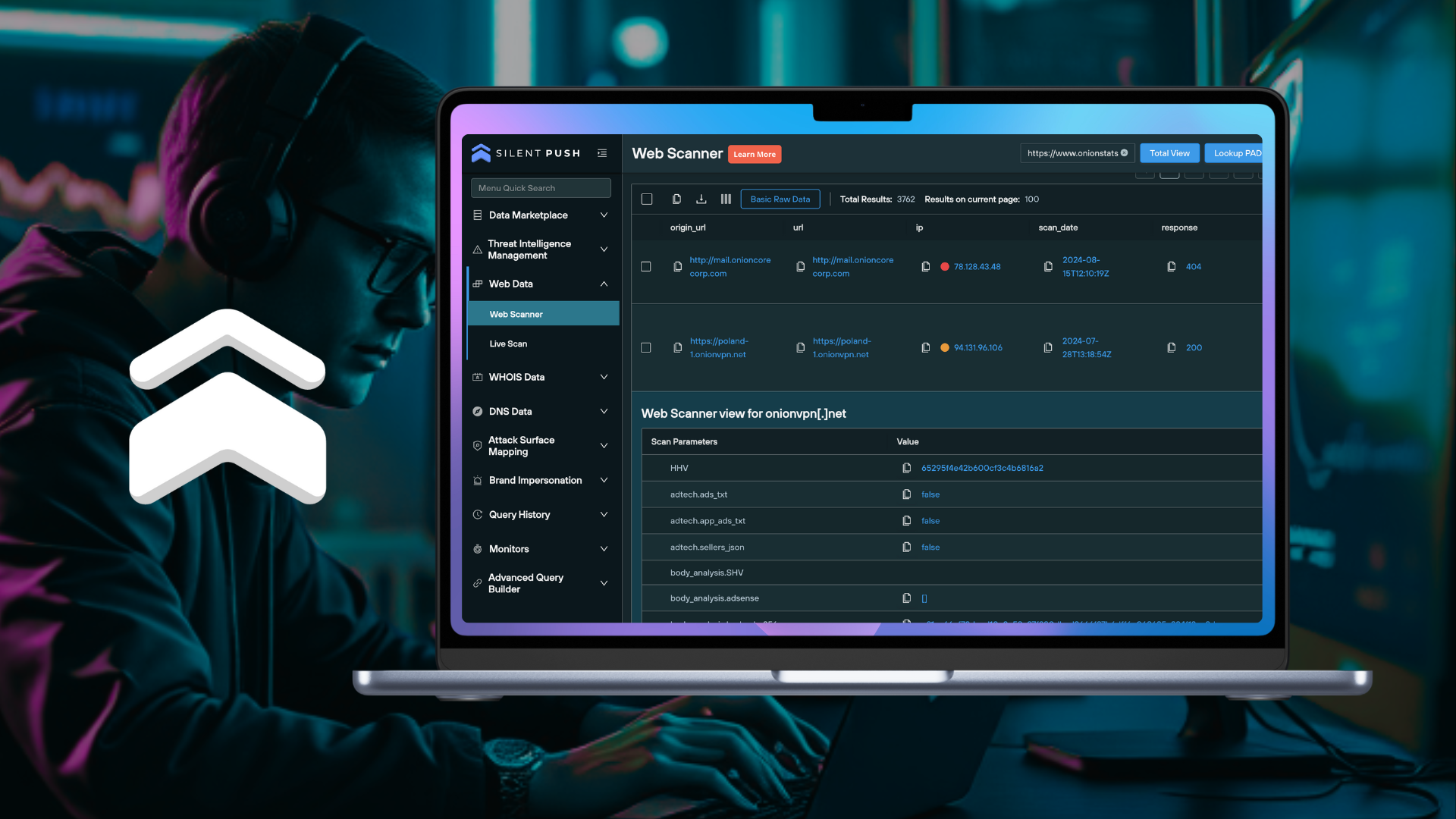
In this blog, we’ll demonstrate how you can use Silent Push Community Edition to scan across the dark web using 50+ unique parameters, and obtain timestamped intelligence that reveals Tor infrastructure linked to activity on the public web.
Sign-up to Silent Push Community Edition.
Silent Push Community Edition is a free threat hunting and cyber defense tool featuring a range of advanced queries and lookups – built on a powerful first-party database of enriched DNS data – that allows users to locate known and hidden threat infrastructure on the public web and dark web.
What is the dark web?
The dark web is a hidden corner of the internet that is not accessible through standard browsers and search engines.
Dark websites reside on the the deep web, which refers to all online content that is not indexed for search, such as private databases, online banking sites, and password-protected content.
Domains on the dark web are commonly referred to as “onion” sites, due to the the top-level domain “.onion” that’s used by websites on the Tor network – a specialized web browser used to navigate the dark web, that serves the vast majority of hidden websites.
Other dark web top-level domains do exist – such as .i2p on the Invisible Internet Project Network – but for the purposes of this blog, we’re going to focus on the Tor network.
Dark web anonymity
Onion sites use “hidden services” and encryption methods that rely on Tor’s built-in directory to locate and load a website, instead of the standard DNS resolution methods used to navigate the public web.
This complex routing scheme provides a high level of anonymity for anyone who uses the dark web, making it a digital haven for cybercriminals involved in all manner of threat activity – including the selling of confidential company data obtained during a security breach, typically as part of a ransomware attack
Dark web marketplaces
Stolen data is offered for sale on the dark web in exchange for cryptocurrency, on illegal marketplaces – such as the infamous Silk Road site that was shut down by the FBI and Europol in 2013 – along with drugs, counterfeit goods, access to illegal software, and other illicit services.
Dark web scanning and threat hunting
Due to the sheer volume of illegal activity it hosts, the dark web can be reliably called a “target rich environment”, but its architecture makes it incredibly difficult for law enforcement and security teams to proactively locate threat infrastructure on the Tor network as they would do on the public internet, and investigate Advanced Persistent Threat (APT) groups that take advantage of the dark web’s secretive and decentralized nature.
Scanning vs. Monitoring
Cybersecurity tools that monitor .onion sites for stolen data and authentication details are relatively commonplace, even within small scale IT support operations, but these utilities are limited to passive searches that don’t allow security teams to hunt for specific elements of dark web infrastructure linked to a set of identifiable Tactics, Techniques and Procedures.
Dark web scanning in Silent Push Community Edition
Dark web scanning in Silent Push is the process of proactively locating (rather than passively monitoring) Tor sites linked to threat activity that targets an organisation, brand, or supply chain, and allows teams to make attributable links between .onion sites and associated clear web activity, aiding in the public identification criminal behaviour.
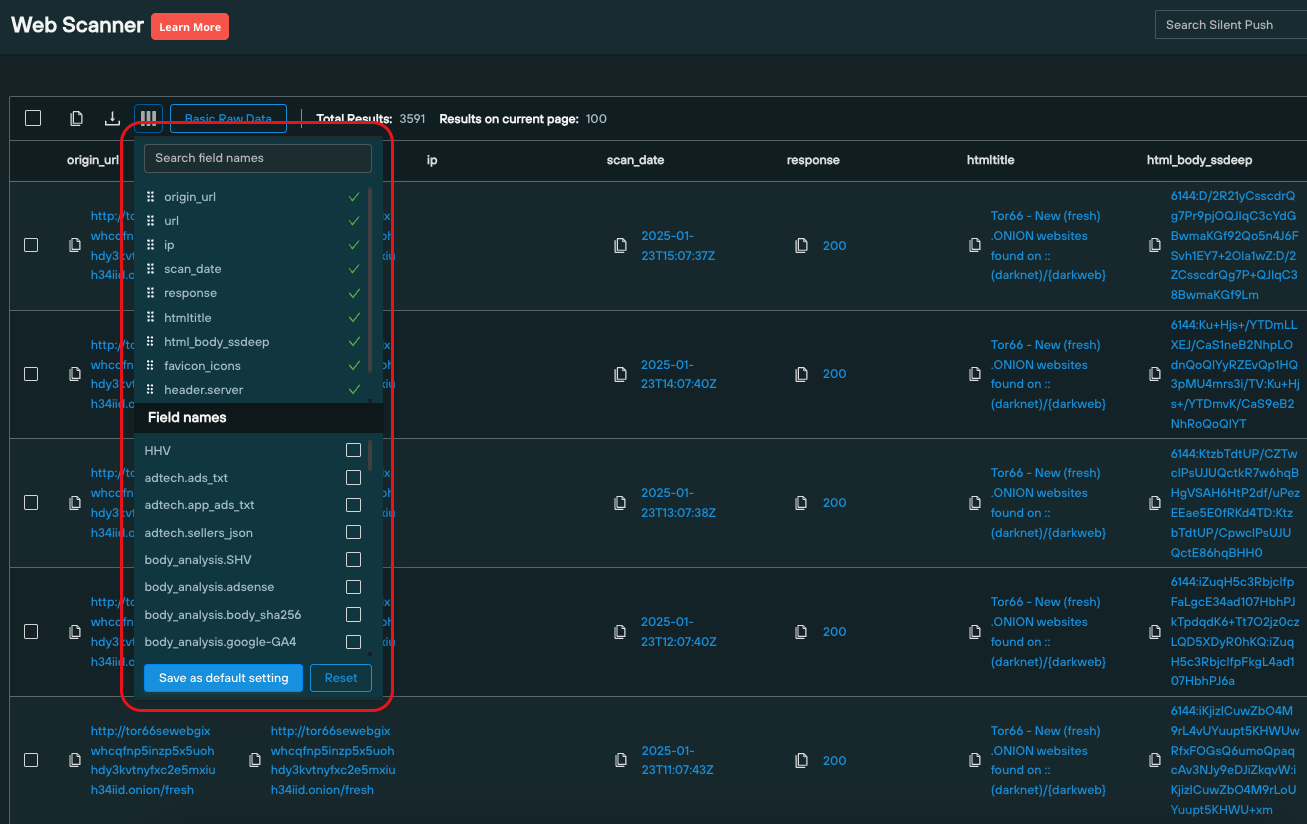
Silent Push Community Edition contains a dedicated dark web scanning utility that breaks .onion sites down into 50+ categories (including HTML body data, the favicon used, a real-time snapshot, and a range of JavaScript parameters) that mirror the parameters we use to collect data on standard public websites, which can be searched across within the same tool – Silent Push Web Scanner.
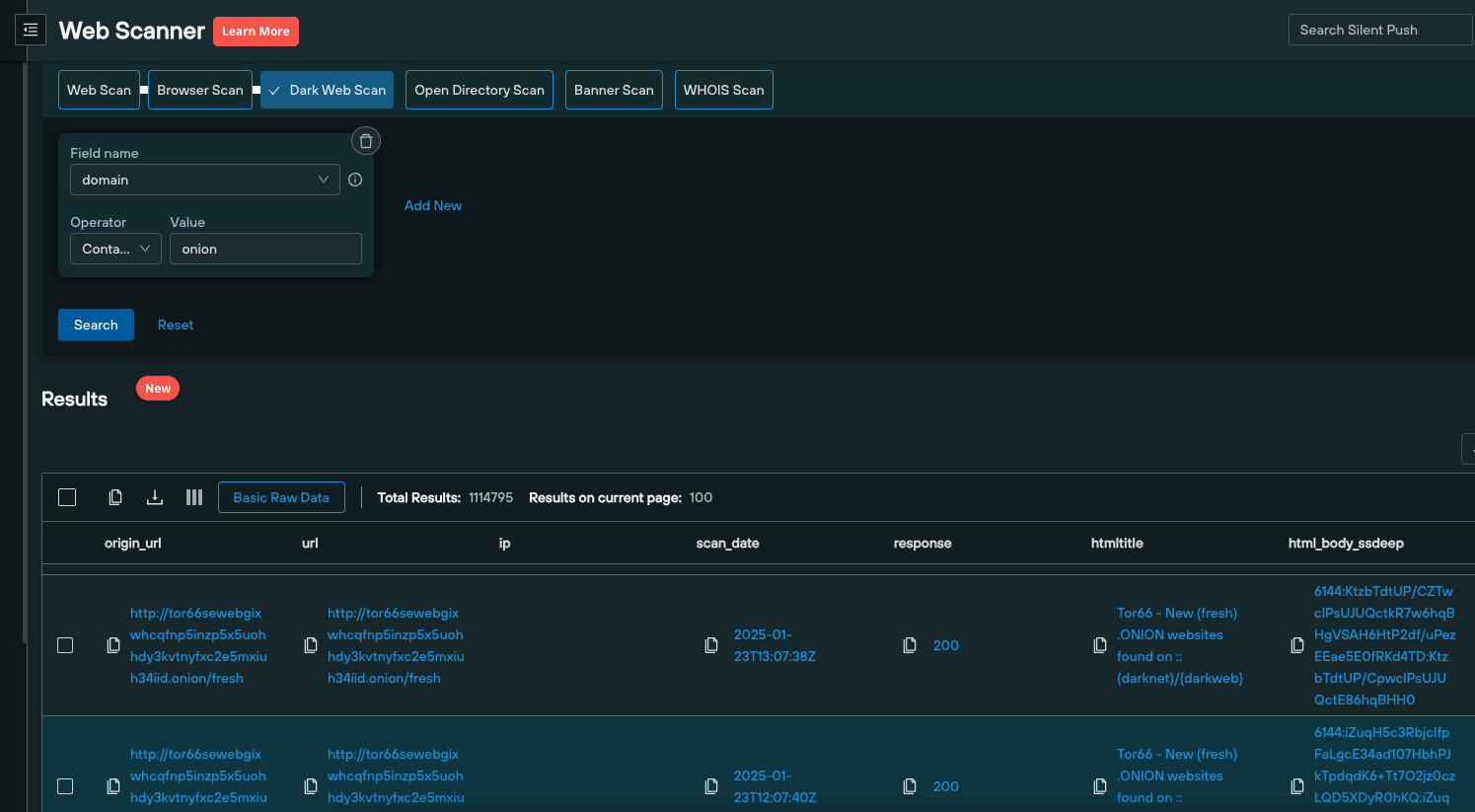
This allows teams to create a behavioral fingerprint of attacker activity that can be used to search across historic and real-time clear web and Tor website datasets for matching content, using a single query, to facilitate the public unmasking of dark web threat activity.
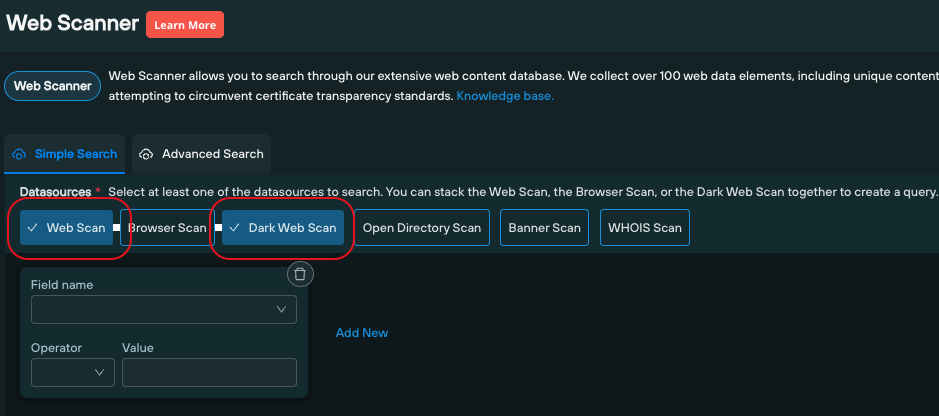
Let’s take a look at a few examples…
Dark web scanning example: Favicon unmasking
Here’s a .onion site selling illegal access to PayPal and eBay accounts.
First, we executed a Live Scan to gather a real-time screenshot, and capture additional on-page data to use in a pivot:
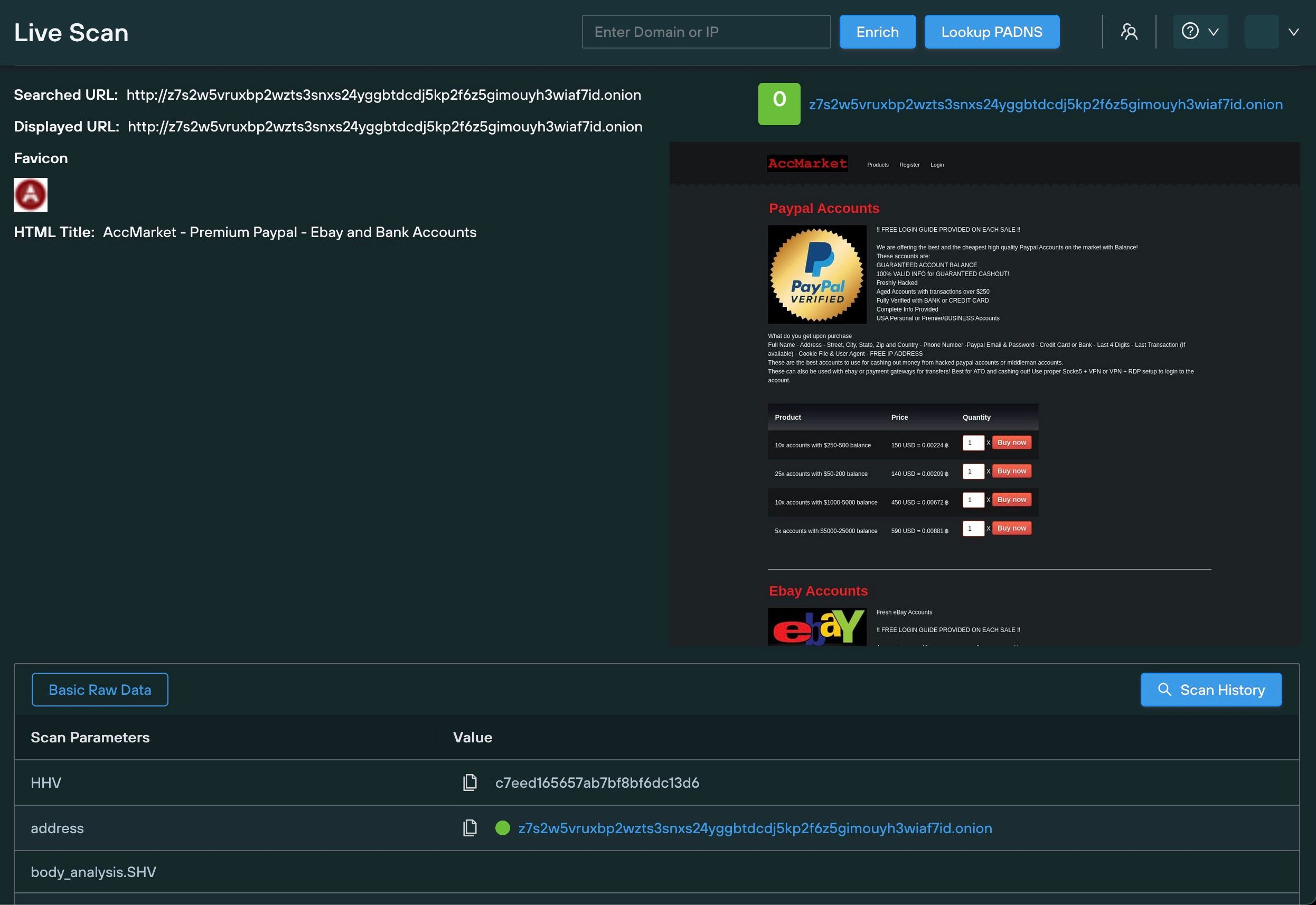
Once we’d established a dataset, we executed a Web Scanner query that cross-referenced the MD5 hash of the dark web favicon with our public web dataset, to find matching results, including an IP address linked to an Apache server:
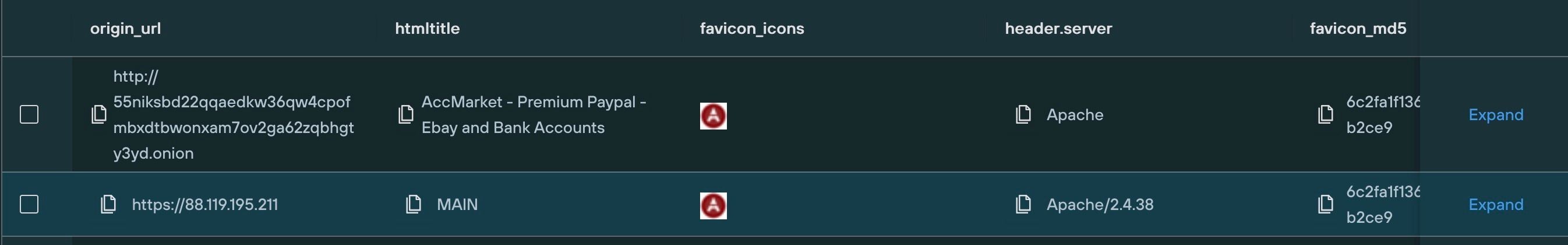
Based on the distinctiveness of the hash – and the absence of any other IPs associated with this particular favicon – it’s possible that the public IP hosts the hidden Tor service in question.
We’ve used this Tor site and favicon as an example, but any piece of on-page data can be utilized.
Dark web scanning example: JavaScript unmasking
Unique JavaScript hashes are another effective pivot point.
Our aggregation engine generates a searchable hash value of all JavaScript files referenced on a dark web or public web page, allowing teams to systematically search across both datasets simultaneously for JavaScript elements shared by Tor sites and standard websites.
In this example, we’ve located a .onion site containing a unique JavaScript MD5 hash (using the “body_analysis.js_sha256” field), and executed a query that locates a public web site containing the exact same JavaScript code:
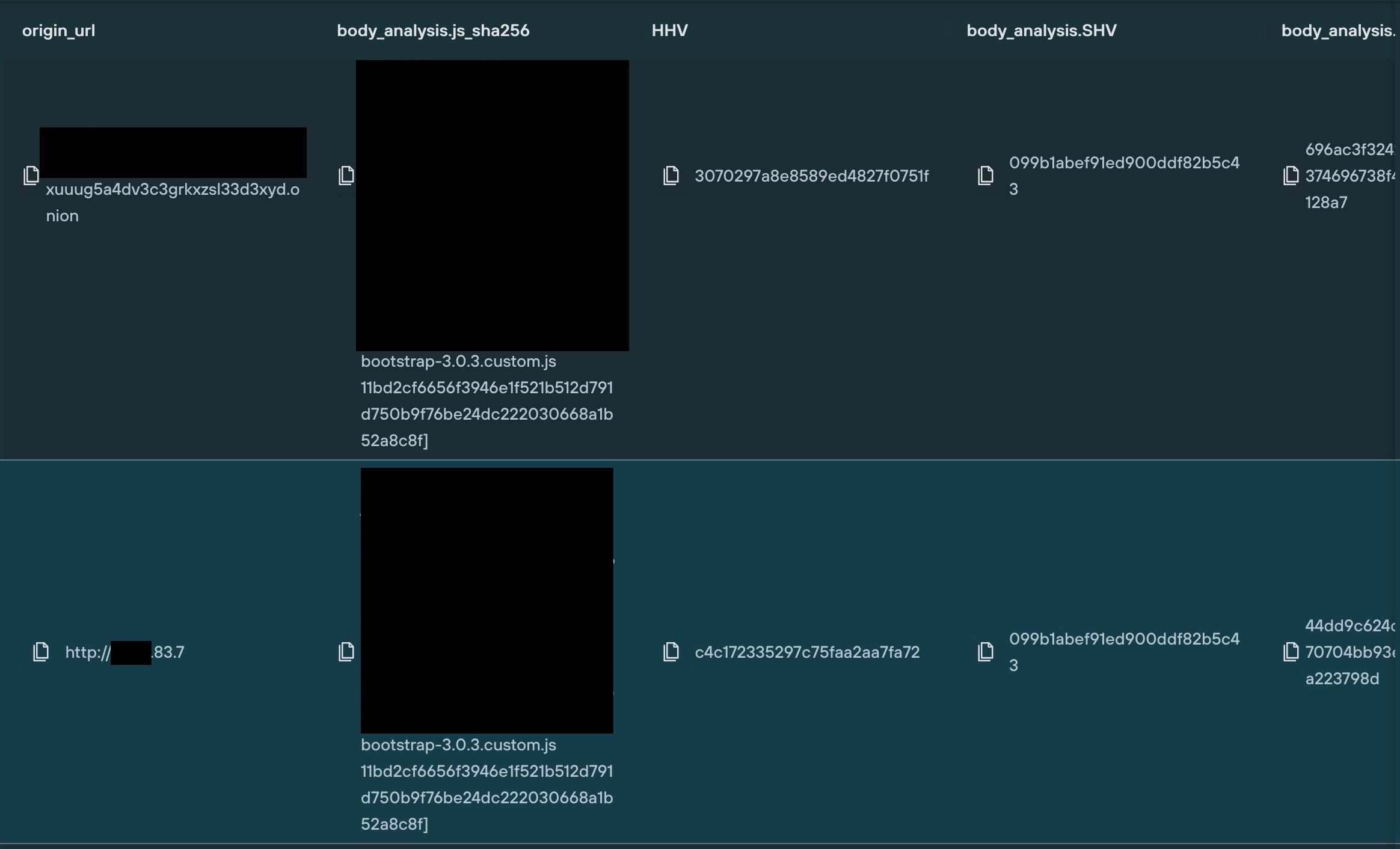
Historic dark web scanning at scale
Silent Push Community Edition dark web scanning provides timestamped results sets of all the .onion sites we collect data on, so that security teams can evaluate attacker behaviour over time, and analyze how threat infrastructure is being modified to avoid detection.
Here’s an example that includes multiple snapshots of a .onion site taken on the same day:
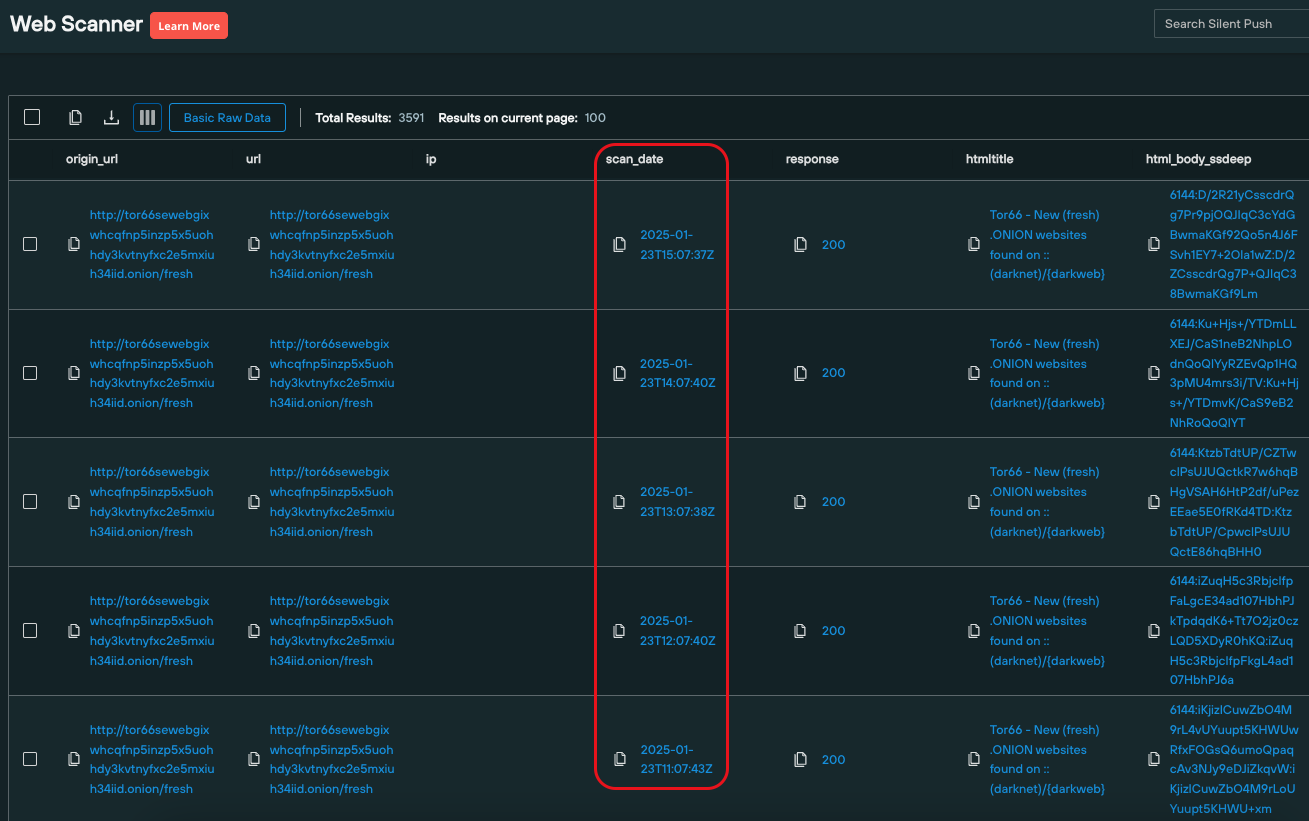
Dark web scanning results sets can also be amended to include or exclude any number of specified data categories, to drill down into hidden infrastructure for identifiable content and make tangible links with public domains.
Fields can also be searched independently of other categories, for quicker access to critical intelligence.
Sign-up to Silent Push Community Edition.
Silent Push Community Edition is a free threat hunting and cyber defense tool featuring a range of advanced queries and lookups – built on a powerful first-party database of enriched DNS data – that allows users to locate known and hidden threat infrastructure on the public web and dark web.