ClickFix malware: Silent Push tracks 2,000+ domains and IPs affected by WordPress fake browser update infostealers.

Executive Summary
Silent Push Threat Analysts have discovered 2000+ unique domains that are affected by the ClickFix/ClearFake fake browser update malware.
Our team has constructed two Bulk Data Feeds that track affected domains in real time, using a Silent Push Web Scanner query that scans domain metadata for infected domains and IPs.
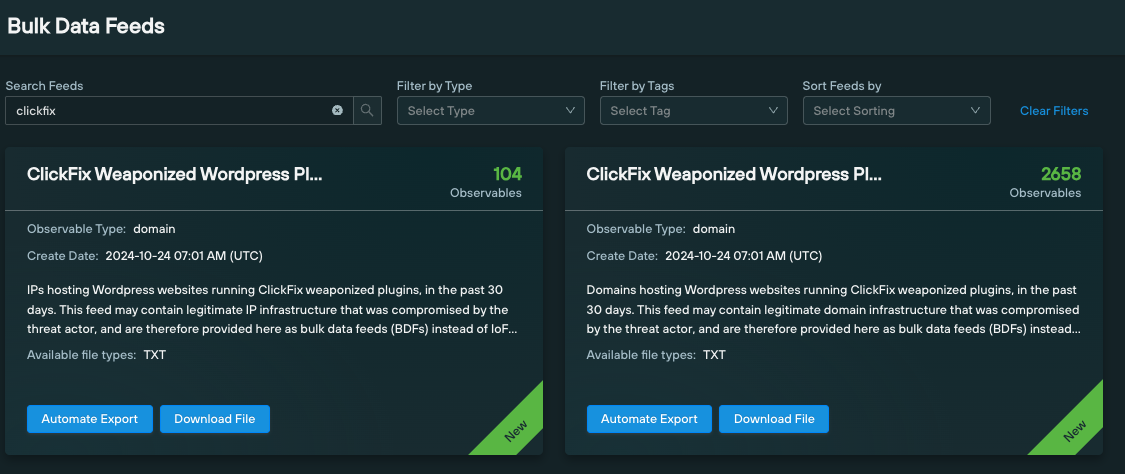
As of writing, we have identified ClickFix JavaScript code as being active on 2,658 domains, across 104 IP addresses.
Silent Push Enterprise users can ingest this data into their security stack, and use it to identify the ClickFix exploit within their existing detection protocols.
Background
Last week, GoDaddy researchers discovered a major increase in “swarms” of malicious WordPress plugins that infect compromised websites with fake browser update pop-ups, which use blockchain technology to distribute malware such as Lumma Stealer.
Lumma (also known as LummaC2) is an information stealer that’s been available on the dark web as Malware-as-a-Service since 2022. Last year, we published a blog exposing Lumma threat activity, and its links to Russian threat activity.
ClickFix attack chain
Affected websites are compromised by threat actors obtaining back-end access to WordPress control panels (usually via stolen credentials), and installing plugins that inject JavaScript containing the aforementioned ClickFix/ClearFix malware.
ClickFix Web Scanner query
GoDaddy researchers have identified the following malicious plugins as carrying the JavaScript payload:
| Plugin name | Injected script |
| Admin Bar Customizer | admin-bar-customizer/abc-script.js |
| Advanced User Manager | advanced-user-manager/aum-script.js |
| Advanced Widget Manage | advanced-widget-manage/awm-script.js |
| Content Blocker | content-blocker/cb-script.js |
| Custom CSS Injector | custom-css-injector/cci-script.js |
| Custom Footer Generator | custom-footer-generator/cfg-script.js |
| Custom Login Styler | custom-login-styler/cls-script.js |
| Dynamic Sidebar Manager | dynamic-sidebar-manager/dsm-script.js |
| Easy Themes Manager | easy-themes-manager/script.js |
| Form Builder Pro | form-builder-pro/fbp-script.js |
| Quick Cache Cleaner | quick-cache-cleaner/qcc-script.js |
| Responsive Menu Builder | responsive-menu-builder/rmb-script.js |
| SEO Optimizer Pro | seo-optimizer-pro/sop-script.js |
| Simple Post Enhancer | simple-post-enhancer/spe-script.js |
| Social Media Integrator | social-media-integrator/smi-script.js |
Silent Push Web Scanner collects data on all public facing websites, including HTML titles and body content, certificates, favicons and server data, and allows users to execute queries that return linked malicious infrastructure using 100+ categories.
Our team used the above JavaScript plugins to execute a Silent Push Web Scanner query using the following syntax, that located all affected websites active after September 20:
body_analysis.js_sha256 = ["admin-bar-customizer/abc-script.js ", "advanced-user-manager/aum-script.js ", "advanced-widget-manage/awm-script.js ", "content-blocker/cb-script.js ", "custom-css-injector/cci-script.js ", "custom-footer-generator/cfg-script.js ", "custom-login-styler/cls-script.js ", "dynamic-sidebar-manager/dsm-script.js ", "easy-themes-manager/script.js ", "form-builder-pro/fbp-script.js ", "quick-cache-cleaner/qcc-script.js ", "responsive-menu-builder/rmb-script.js ", "seo-optimizer-pro/sop-script.js ", "simple-post-enhancer/spe-script.js ", "social-media-integrator/smi-script.js "] AND scan_date > "2024-09-20"Here’s a quick tutorial video on how to execute basic and advanced web content and DNS queries using Silent Push Web Scanner.
Silent Push Web Scanner is available across all subscription types. Sign up for a free Community Edition account, to start using it.
ClickFix Bulk Data Feeds
Silent Push Bulk Data Feeds – available as part of a Silent Push Enterprise subscription – are dynamic lists of domains, IPs, URLs, and nameservers that are exportable as a text file, or as an API endpoint.
Bulk Data Feeds are distinct from IOFA Feeds, in that they can contain non-malicious indicators.
Feeds are categorized by data type, and contain information on important changes and additions across the global IPv4/6 range that organizations can use to inform their detection protocols – e.g. a list of new nameservers, IPFS nodes, and of new country code top level domains (ccTLDS).
We’ve populated two dedicated ClickFix Bulk Data Feeds with vulnerable domains and IPs obtained from the above query, so that organizations can easily identify all the domains currently affected by the explot:
Mitigation
Silent Push Web Scanner is available as part of a free Community Edition account. You can use the above query parameters to scan for affected ClearFix infrastructure, and add in additional data fields to create custom detection protocols based on your organizational requirements.
For tips on how to get started, Watch our Web Scanner video tutorial.
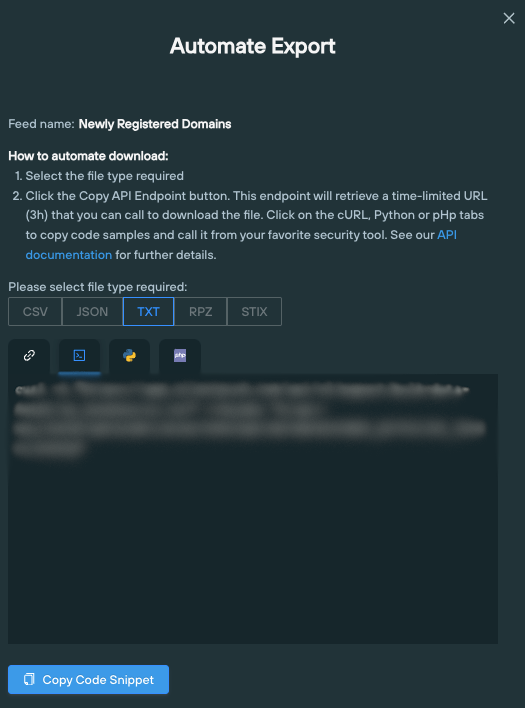
Silent Push Enterprise users can ingest Bulk Data Feeds into their security stack using a range of endpoint export options, by clicking the ‘Automate Export’ button
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign-up for a free account


