New Phishing Campaign Uses Browser-in-the-Browser Attacks to Target Video Gamers/Counter-Strike 2 Players

Key Findings
- Silent Push Threat Analysts have discovered a new phishing campaign using complex browser-in-the-browser (BitB) phishing attacks. These attacks involve fake but realistic-looking browser pop-up windows that serve as convincing lures to get victims to log into their scams.
- Our observations thus far indicate the threat actor is attempting to phish accounts from the “Steam” Gaming Platform (steampowered[.]com) with the likely intention of reselling them to unsuspecting buyers through online marketplaces. All the websites we found were in English, with the exception of one Chinese site, which was in Mandarin with some English words.
- This sophisticated campaign primarily targets Counter-Strike 2 players while abusing the brand and identities of the pro eSports team Navi.
- Our threat analyst team is making some of the technical fingerprints we’ve observed this threat actor using public to provide education on the issue, increase awareness, and enable external researchers to track the threat actor’s sites.
Table of contents
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Edition Account
- Background
- Targeting Team Navi
- Fake Browser Pop-Up Window
- Promoting the Phishing Site Containing a BitB Attack
- Browser-in-the-Browser Attacks
- Targeting Steam Accounts
- Staying Alert to BitB Attacks: Look for the Fake URL Bar
- How to Track These Threats with Real Queries
- Continuing to Track Phishing Campaigns
- Mitigation
- Register for Community Edition
- Sample List of IOFAs from this Campaign
Executive Summary
Our research team has discovered an active phishing campaign targeting players of the multi-player video game Counter-Strike 2. Along with attempts to compromise players’ Steam accounts, part of the campaign’s attack tactics also includes abusing the names of a professional eSports team called Navi.
Built around the creation of seemingly convincing fake browser pop-up windows that prominently display the URL of the real website, the campaign’s goal is to make a visitor feel safe, believing the pop-up windows are part of the actual (real) sites. Once the potential victim tries to log into the fake Steam portal, the threat actor steals the credentials and likely attempts to take over the account for later resale.
All of the websites our team has found so far were in English save one Chinese site, simplegive[.]cn, which was created in Mandarin, with some English wording, and used the top-level domain (TLD) “.cn”
We want to use the discovery of this threat against gamers as an opportunity to introduce our readers to the free Silent Push Community Edition to get started with threat detection, protection, and prevention.
Sign Up for a Free Silent Push Community Edition Account
Register now for our free Community Edition to use all of the tools and queries highlighted in this blog.
Background
Browser-in-the-browser attacks are simple but clever phishing techniques. Threat actors emulate trusted services with fake pop-up windows that resemble the actual login pages. While many theoretical attacks describe browser-in-the-browser tactics, it’s rare to actually catch a threat actor deploying this process.
The new phishing campaign our team discovered targets Counter-Strike 2, a free-to-play tactical first-person shooter game developed and published by Valve. Designed as counter-terrorists-versus-terrorists play, Counter-Strike 2 was released in September 2023 for Windows and Linux on the Steam digital distribution service and storefront. Also developed by Valve, Steam is the largest digital distribution platform for PC games, and public reports estimate it to have 75% of the market share.
From our team’s research thus far, it appears these threat actors created phishing kits targeting Steam, Counter-Strike 2, and the Navi esports team after conducting research into gaming communities.
Targeting Team Navi
The threat actor behind the new phishing campaign singled out the professional eSports team Navi to “feature” in its attacks. The screenshot below shows the threat actor’s phishing web page offering a “free case” – essentially video game skins as a lure:
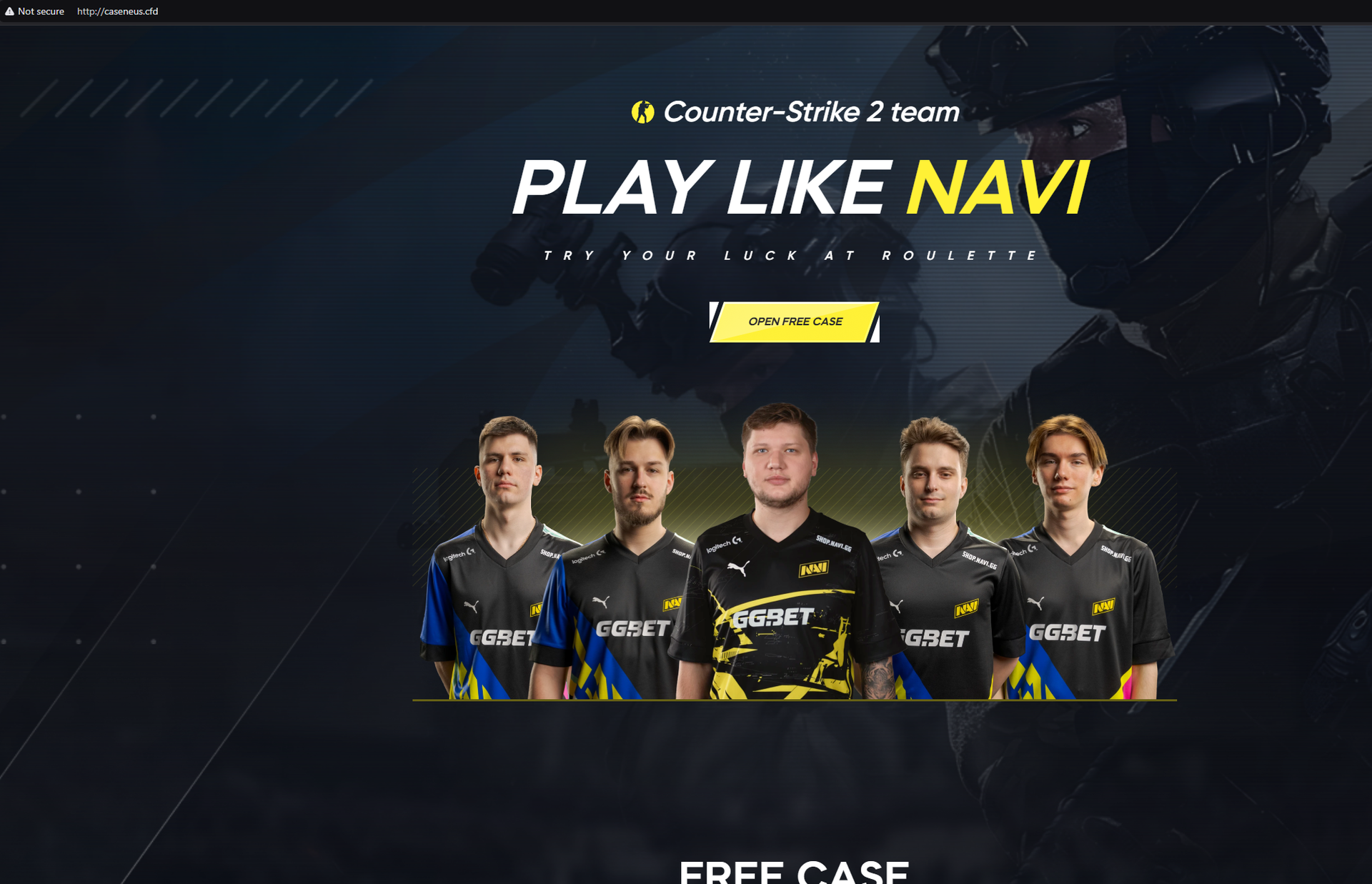
caseneus[.]cfd

Fake Browser Pop-Up Window
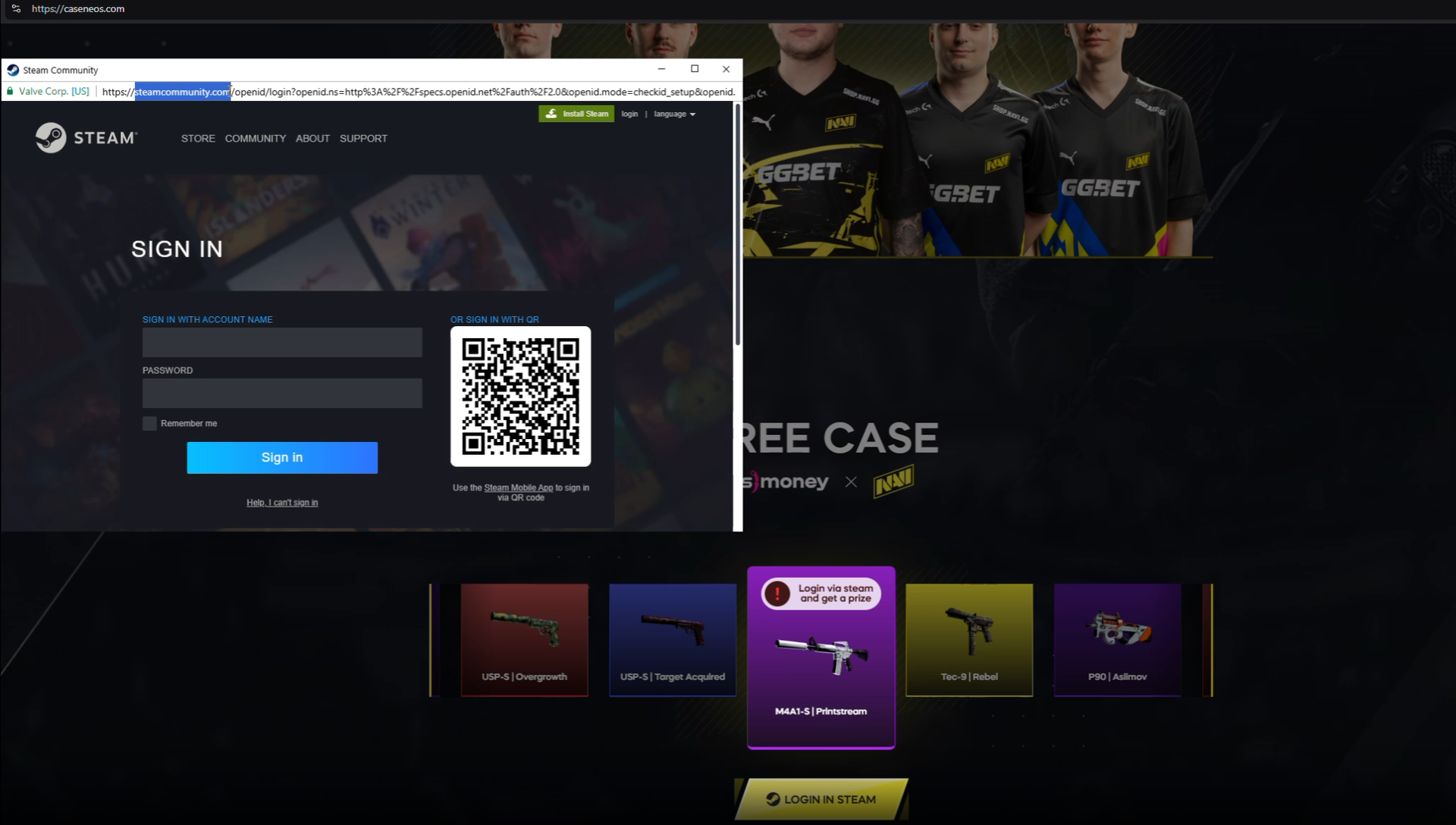
Promoting the Phishing Site Containing a BitB Attack
As referenced previously, our threat team was particularly interested in this phishing effort (watch the video below to larne more) because the threat actor is using a “Browser in the Browser” orchestrated attack. In the attack, the URL of the real site (in this case, Steam) is prominently displayed, leading someone to believe it’s a real pop-up window for logging in.
That window looks like this:
The threat actor behind this is also trying to spread their phishing scheme on YouTube. Posts like the one highlighted below from January 2025 got over 600 likes on YouTube (a potentially purchased level of engagement) – in promoting their scam domain: caserevs[.]com.
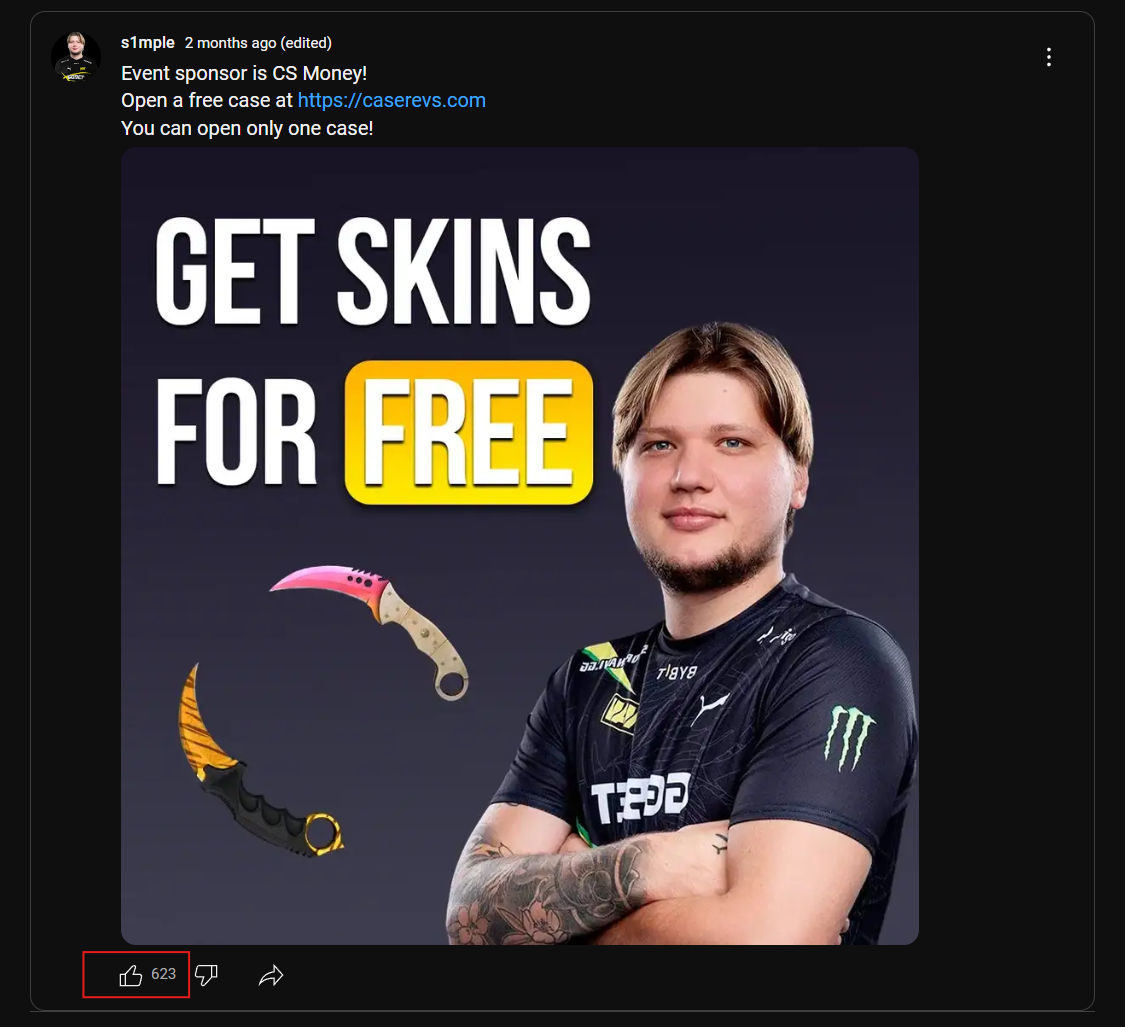
Browser-in-the-Browser Attacks
Various threat actors have launched browser-in-the-browser attacks sporadically over the last few years. However, it’s still interesting to see when these BitB attacks are found, as they indicate a threat actor who carefully studies complex phishing methods.
Potential victims who experience these phishing attacks in the wild receive a much more convincing lure than a suspicious login form on a random domain, potentially making them more effective.
These types of attacks were heavily studied a few years ago, with researchers like mrd0x largely initiating the discussion with their open-source example and larger write-up.
In June 2024, a credible BitB campaign was launched targeting Steam users from the pages[.]dev domain first reported on Reddit. The pages[.]dev domain is a Cloudflare product for hosting content, and anyone can create content there, making it a common location our threat team has seen for threat actors spinning up malicious infrastructure. Silent Push enterprise clients have access to a feed of domains with publicly rentable subdomains, and we encourage defenders to alert or block requests to these domains.
Our team believes new BitB phishing attacks will continue targeting Steam users throughout 2025. As the attacks continue, other networks and brands will likely be included as new targets.
Targeting Steam Accounts
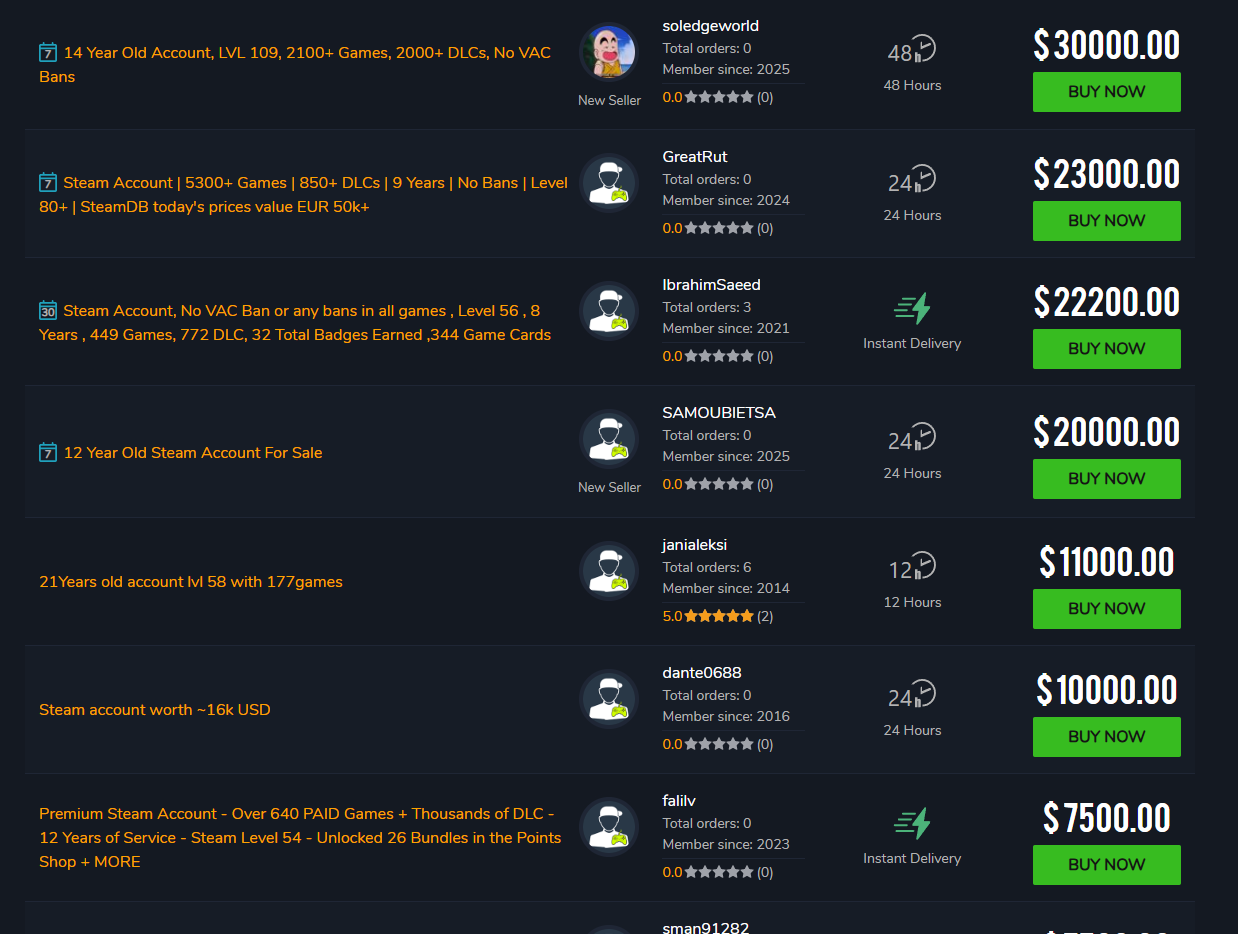
It might initially seem odd for a threat actor to target Steam accounts. However, when they contain a substantial number of games, these accounts can sell for tens of thousands of dollars. Our research team found many websites, such as playerauctions[.]com, that sell Steam accounts. Threat actors may simply be trying to sell their illicitly acquired Steam accounts on potentially lucrative sites like these.
The screenshot below, playerauctions[.]com/steam-account/?SortField=highest-price, shows the price range of Steam accounts listed for sale.
Staying Alert to BitB Attacks: Look for the Fake URL Bar
BitB attacks are most convincing against desktop users, as the pop-ups are built to be viewed on larger resolutions. The threat actors behind this current video game phishing BitB effort didn’t bother to create convincing mobile-optimized phishing pages, which indicates the targeting here follows that pattern.
Legitimate windows, including pop-ups, can be maximized, minimized, and moved outside the browser window. However, fake pop-ups, such as the login windows in the BitB phishing scheme, cannot be maximized, minimized, or moved outside the browser window even though victims can “interact” with the URL bar of the fake pop-up.
Our team encourages people to look for fake URL bars in any login pop-ups. If you see a URL bar, always try to drag that window outside the browser you’re viewing. This is the best way to easily confirm that the pop-up is real, and therefore, the URL bar would correctly display the URL of the pop-up. Otherwise, you could be experiencing a fake pop-up window related to a potential BitB attack.
If you happen to get phished by a BitB attack, we recommend immediately changing the credentials associated with the relevant account as well as taking note of any other details the threat actors may have scraped for use from that account.
How to Track These Threats with Real Queries
Cybercriminals are always inventing new methods to steal users’ credentials, inject malware, and generally cause cyber mayhem. The good news is that Silent Push specializes in preemptive threat intelligence to prevent that.
Individuals interested in using our platform to protect themselves or their organization can sign up for a free Silent Push Community Edition account.
Getting Started with Silent Push
The Silent Push Web Scanner is one of our most popular and easy-to-use tools. We’ll be using that for several of the queries below. But first, a look at our Total View insights!
Exploring a Dedicated IP Address via Total View
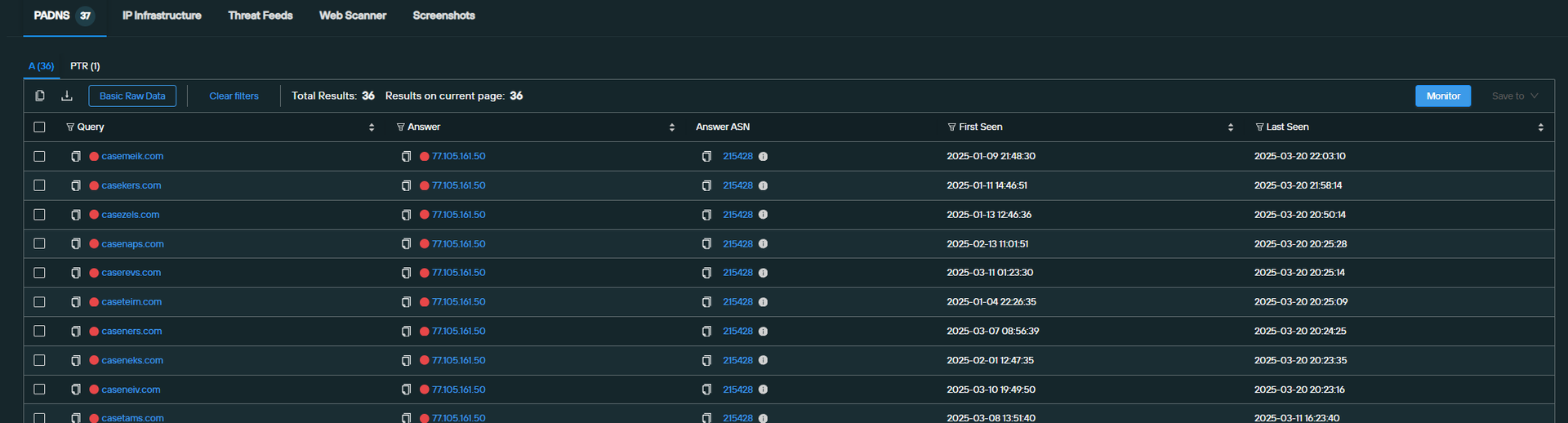
The BitB phishing campaign uses a dedicated IP address to host their scams.
Silent Push Total View Dedicated IP Link
- 77.105.161[.]50
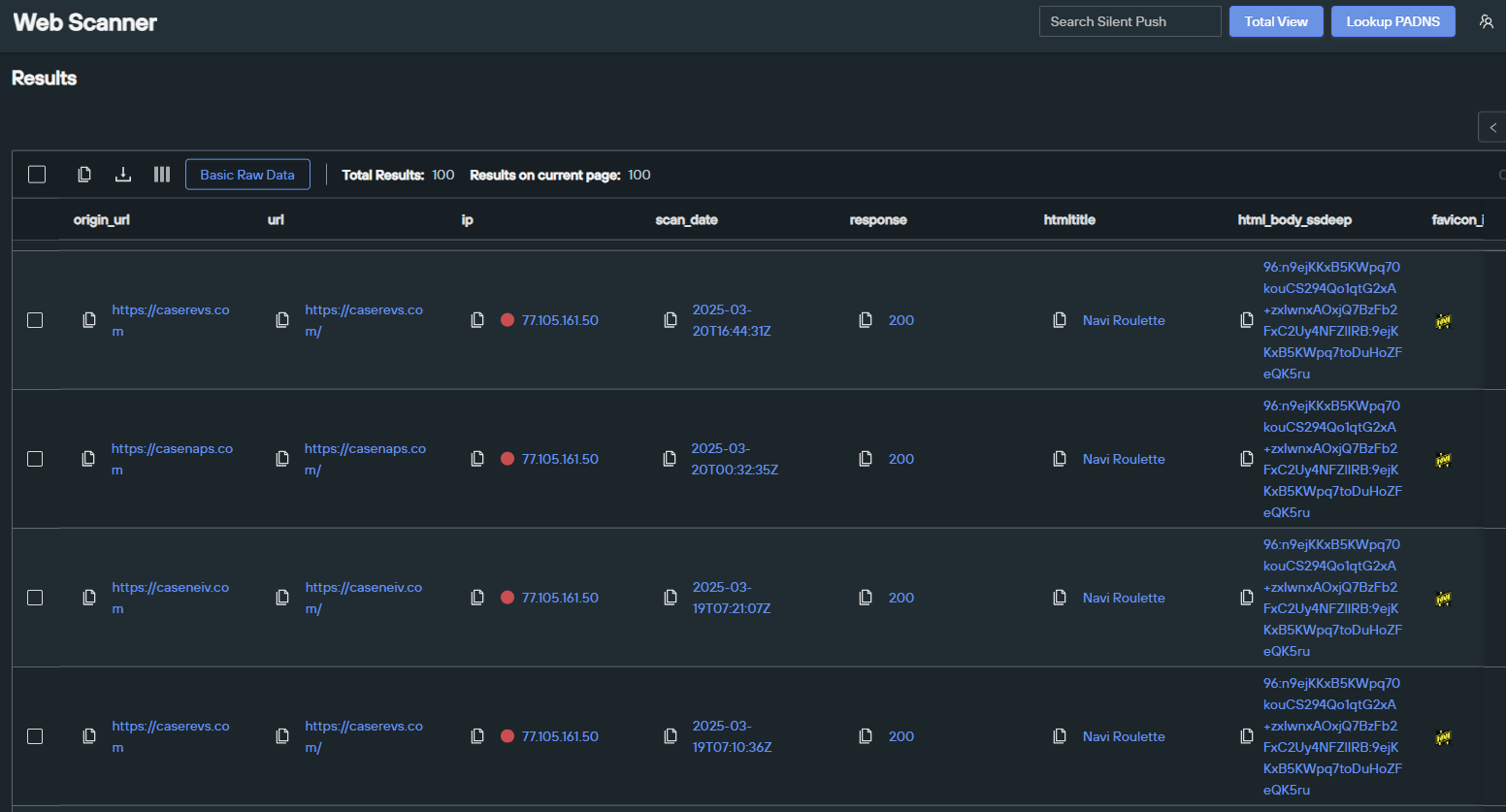
The threat actor also reuses a simple template across each of these sites, which includes reused JavaScript. We can look for this JavaScript by searching against our “body_analysis.SHV” field in the Web Scanner, which excels in pinpointing groups of perfect matches.
Here’s the SHV query for tracking this BitB campaign:
Silent Push Web Scanner body_analysis.SHV search query link
- datasource = [“webscan”] AND body_analysis.SHV = “ece6e86b76285b0373fd5806c4”
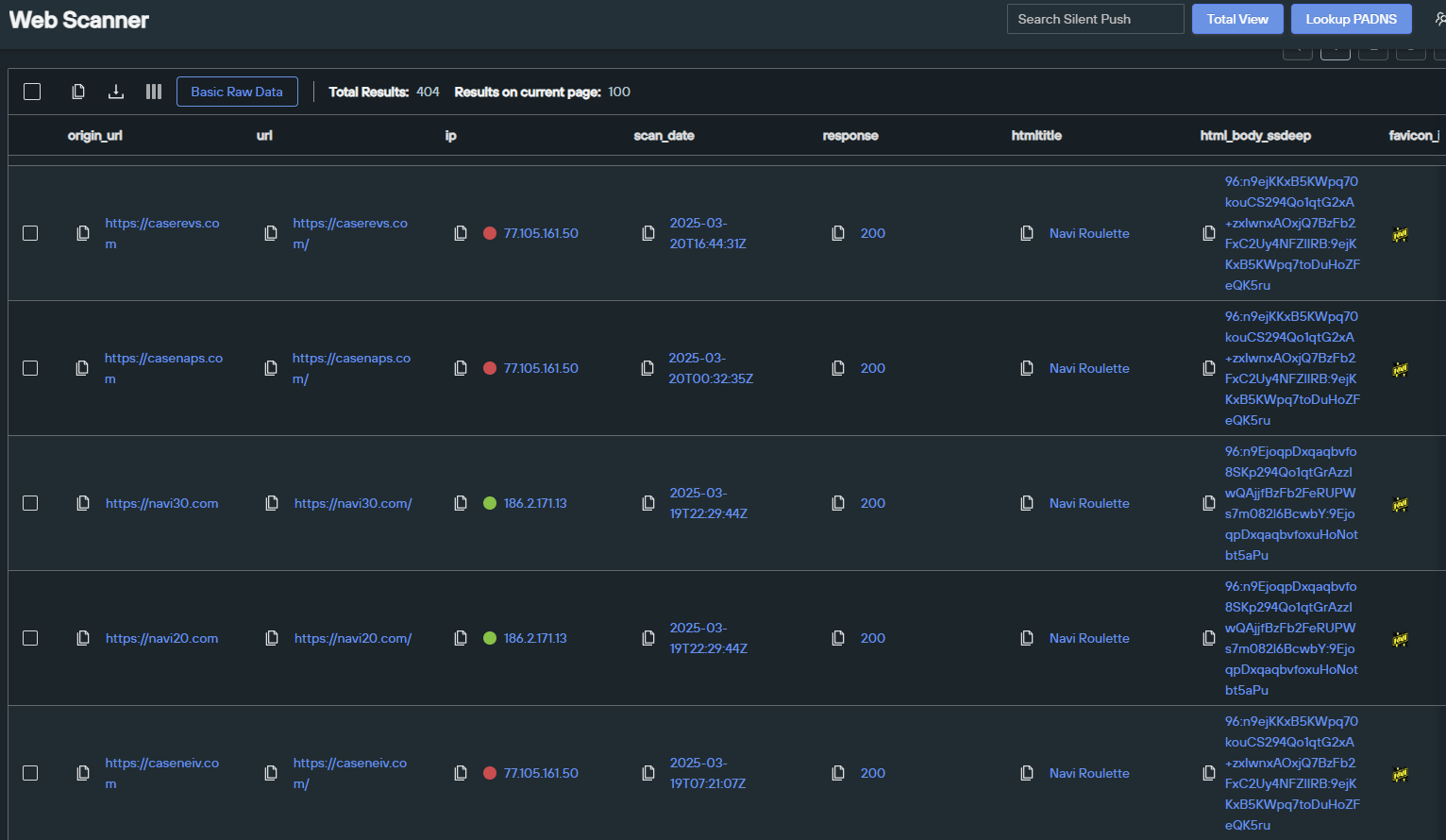
The threat actor also happens to be reusing an HTML title across all of their sites—something we can easily search against in the Web Scanner. Here’s that query:
Silent Push Web Scanner HTML Title = “Navi Roulette” search query link
- datasource = [“webscan”] AND htmltitle = “Navi Roulette”
Continuing to Track Phishing Campaigns
Our team continues to track numerous types of phishing campaigns. As we identify new developments, we will report our findings to the security community.
We will also continue to share our research on threats we discover with law enforcement. If you have any tips about threat actors engaging in criminal activities, our team would love to hear from you.
Mitigation
Silent Push believes all domains associated with BitB phishing campaigns represent some level of risk.
Our analysts have constructed a series of Silent Push IOFA Feeds that provide a growing list of Indicators of Future Attacks focused on these types of phishing efforts.
Silent Push Indicator of Future Attack (IOFA) Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform that offers advanced offensive and defensive lookups, web content queries, and enriched data types.
Sample List of IOFAs from this Campaign
Silent Push is sharing a sample list of the IOFAs we have associated with the BitB phishing campaign to support ongoing efforts within the community. Our enterprise users have access to an IOFA feed currently containing many times this number, with more being added in real time as our investigation continues.
- caserevs[.]com
- caseneiv[.]com
- casenaps[.]com
- caseners[.]com
- caseneiv[.]com
- simplegive[.]cn
- caseneus[.]cfd


