Brand impersonation attacks: TTPs, countermeasures and what the security industry gets wrong.

Summary
Brand impersonation remains a persistent existential threat to the financial and reputational livelihood of businesses across the globe, regardless of size, revenue or sector.
Whilst threat actors are more likely to impersonate brands that command a high degree of trust among consumers and businesses – especially those within the financial and cloud services sector – no organisation is truly safe.
Threat actors view impersonation as a means to exploit the good name and commercial standing of well-established companies, gaining the trust of users who are less vigilant than they usually would be, given the brand names involved.
Inadequate solutions
Cloud-based security platforms are available that target individual elements of an impersonation campaign – DNS records, website content, and security architecture (certificates) – but the industry has thus far failed to offer a unified, end-to-end solution that encompasses all the constituent parts of a firm’s ability to defend itself against online impersonation.
Let’s take a look at the individual TTPs threat actors use to impersonate brands, what questions you should be asking your current security provider, and how Silent Push can help through our centralized Brand Impersonation Protection service.
Domain name impersonation
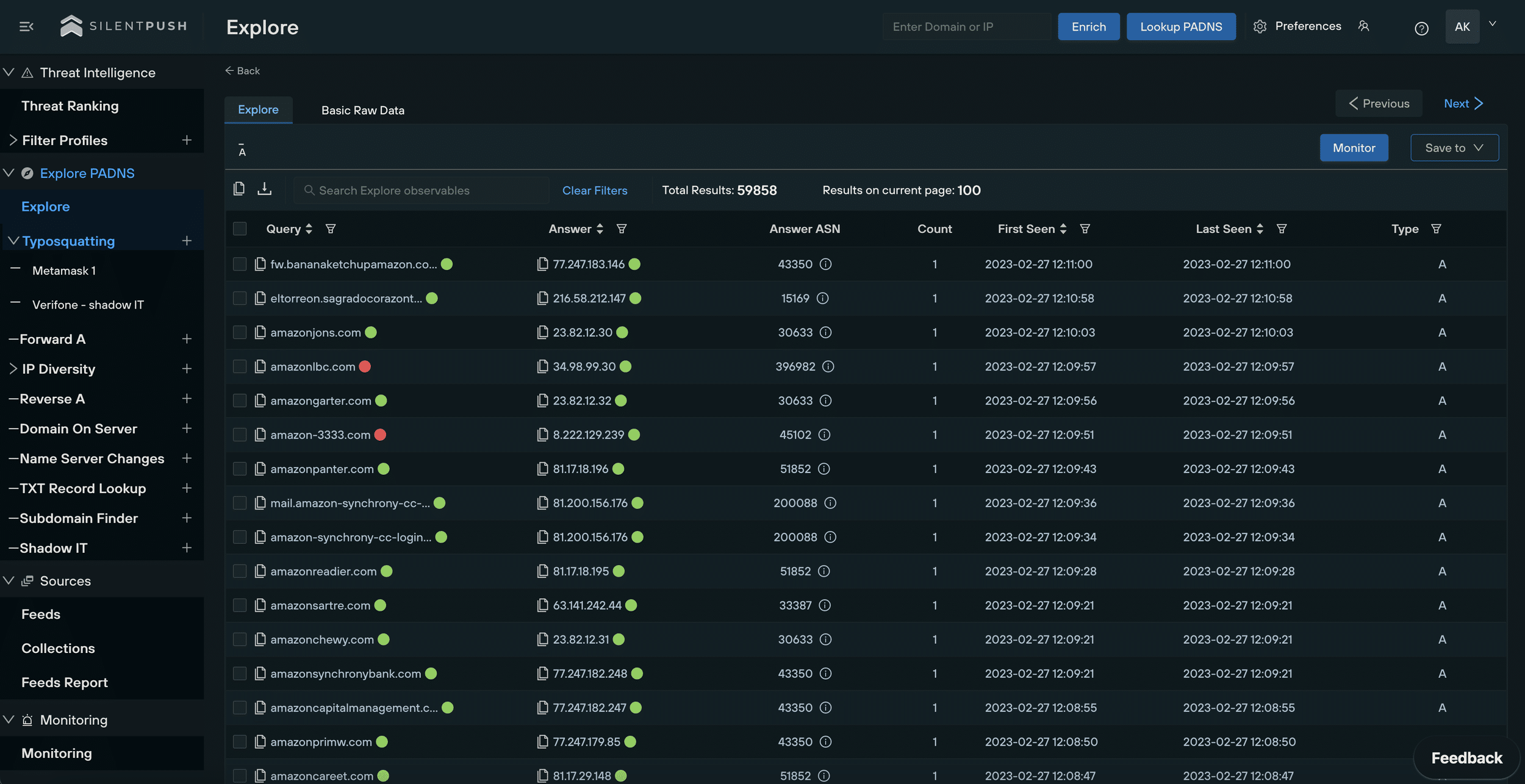
The most common scenario covered by most anti-impersonation solutions is domain name impersonation – a tactic that involves threat actors registering a domain name that is alphanumerically similar to your own domain.
Typosquatting and regex searches
Standalone typosquatting services monitor new domains for registrations that meet certain criteria, usually with a similar string of numbers and characters to the legitimate domain, e.g. examp1e[.]com being used to impersonate example[.]com.
If your domain is 4 characters or less, generally speaking, results will not be fit for purpose unless you’re also able to conduct a regex search that offers granular analysis of potential threats – a form of advanced searching that looks for specific naming patterns, instead of using whole domain or nameserver names.
Example regex pattern: ^g[^\.o]ogle[a-z]{1,}\.[a-z]{1,}$
The above query returns results for google, followed by any characters (before the top-level domain), and also any single characters that replace the first o.
The returned data is highly specific to the target domain, with zero erroneous or irrelevant returns.
Subdomain enumeration
Any digital threat management platform worth its salt needs to include a function that monitors subdomains, as well as root domains and TLDs.
Let’s take a look at the anatomy of https://www.silentpush.com
- https:// – Protocol
- www. – Subdomain
- silentpush.com – Root domain
Your security provider needs to be checking for impersonation campaigns that target not only your root domain but also typosquats on your subdomain too. Cybercriminals view subdomains as low-hanging fruit, due in part to the inattention they receive from most digital threat monitoring platforms.
Email Impersonation
MX (Mail Exchange) records
Threat actors impersonate email domains using MX records in a technique called ‘spoofing’. Spoofing involves forging email headers so that communication appears to come from a trusted sender.
MX records are DNS records that specify which mail server is responsible for handling emails for a particular domain. By spoofing the MX record, the attacker can make it appear as though the email is coming from a legitimate sender’s mail server, even if it is not.
Here’s a common attack vector:
- The attacker sets up a fake email server and creates an email address that appears to be from a legitimate sender, such as helpdesk@randombank[.]com.
- The attacker spoofs the MX record for randombank[.]com so that it points to their own fake email server, rather than the actual mail server for randombank[.]com.
- When a recipient receives an email from helpdesk@randombank[.]com, their email client checks the MX record for randombank[.]com to determine which mail server to use. Since the attacker has spoofed the MX record, the email client sends the email to the attacker’s fake email server instead of the legitimate mail server for randombank[.]com.
- The attacker’s email server receives the email and is free to exploit the data in numerous ways – they may forward it on to a legitimate mail server to avoid suspicion, or modify the contents of the email to include malicious links or attachments.
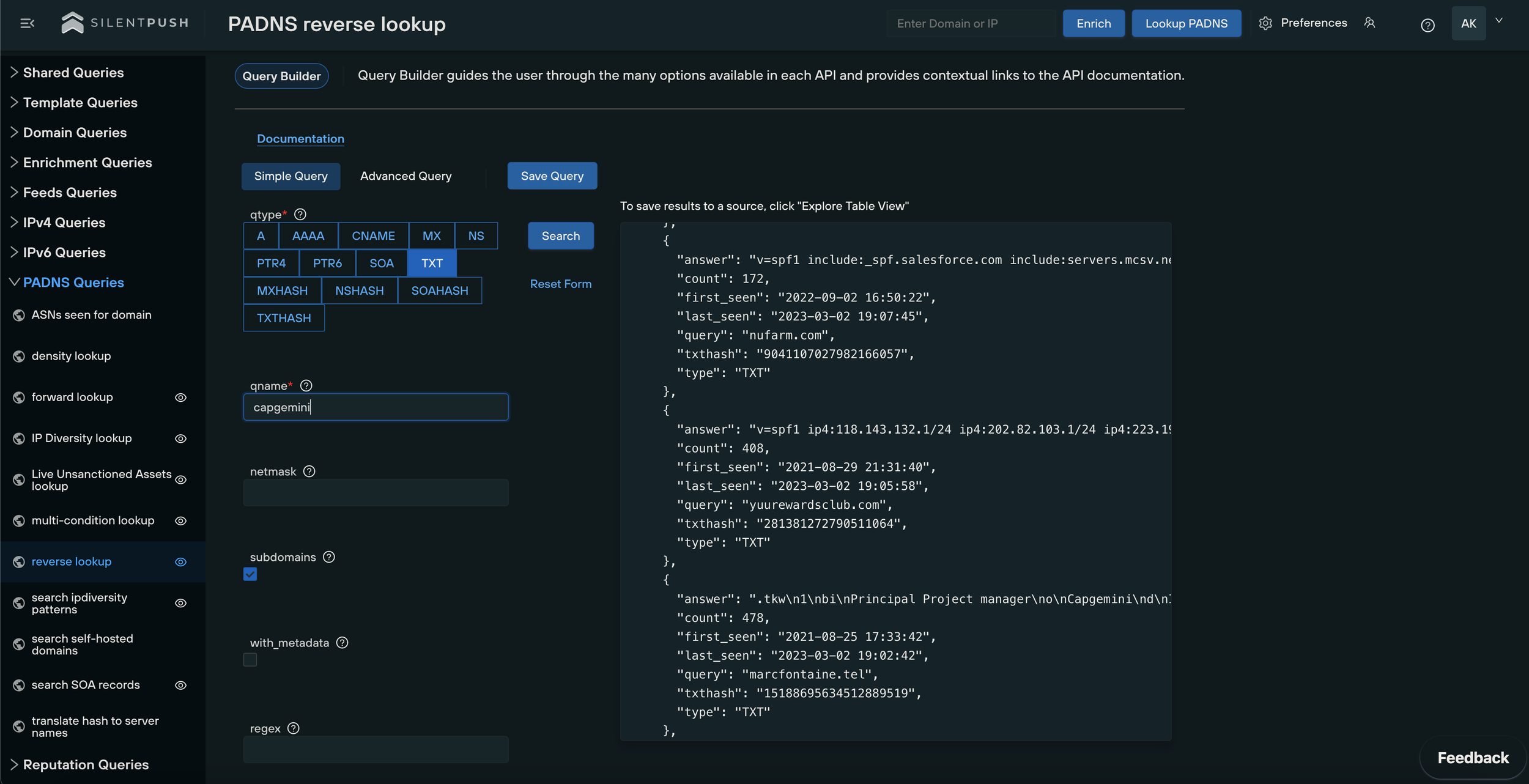
TXT records
MX record exploits are commonly used to propagate business email compromise or supply chain fraud and are often used in combination with TXT spoofing.
Threat actors engage in TXT (Text) spoofing to add an additional layer of legitimacy to the fake email.
Here’s an example of how hackers can use email domain spoofing with TXT records to impersonate email domains, using the above domain as an example:
- The attacker creates a new TXT record for randombank[.]com that includes a special string of text, known as a DKIM (DomainKeys Identified Mail) signature. This signature is designed to prove that the email is legitimate and has not been tampered with.
- The attacker sends an email from [email protected] that includes the DKIM signature in the email header. The recipient’s email client checks the TXT record for randombank[.]com to confirm that the email is legitimate.
- Since the attacker has created a fake TXT record with a valid DKIM signature, the email appears to be legitimate to the recipient’s email client. The recipient is therefore more likely to trust the email and is far more included to click on malicious links or open attachments that contain malware.
By using email domain spoofing with TXT records, threat actors increase the perceived legitimacy of their phishing emails, making it more likely that the recipient will fall for their scam.
It’s important for organizations to deploy countermeasures that provide MX and TXT record searches as standard. If these features are lacking, risk levels are considerably higher.
Spoofed content
Content can broadly be described as the information contained within a web page, as seen by the person who is viewing it.
Threat actors cast their nets far and wide in their attempts to redirect traffic and fool users into believing a fake website is in fact legitimate. These efforts are not limited to back-end DNS exploits. Cybercriminals go to great lengths to replicate the look and feel of popular online brands.
Let’s take a look at two prominent TTPs – favicons and content similarity.
Favicons
Favicons are small icons that appear in the browser’s address bar and next to the website name in tabs. They are usually associated with a specific website or brand, and can be used by threat actors to create a sense of legitimacy for fake websites that host malware or are designed to harvest credentials.
Here’s an example of how threat actors use favicons to impersonate brands:
- The threat actor creates a fake website that looks similar to a legitimate domain, using a similar domain name (see above), design, and content.
- The threat actor creates a favicon that is similar or identical to the favicon of the legitimate website they are trying to impersonate. This is easily achieved by copying the legitimate favicon and making subtle alterations.
- The copied favicon is enabled on the fake website, increasing its legitimacy in the eyes of the user.
Favicon phishing is notoriously difficult to detect, as the visual similarity between the fake favicon and the legitimate one can be subtle. Counteracting favicon spoofing is a fine art. Most digital threat management platforms struggle to deal with the complexities involved, and businesses are often left exposed by poorly performing or non-existent favicon search functions.
Content similarity
Threat actors use templates to re-purpose malicious content across hundreds of spoofed domains. Images are included that mimic legitimate graphics, page layouts are similar and text placement resembles the original domain.
Content impersonation services need to extend beyond favicons and certificate queries. Corporate defenses need to include similarity searches that flag malicious on-screen content masquerading as a legitimate website.
Certificate impersonation
A digital certificate is an electronic document that verifies the identity of a website or online service and encrypts communications between the user and the website.
By impersonating the digital certificate of a legitimate website or service, threat actors deceive users into thinking that they are interacting with a legitimate website or service when they are actually interacting with a fake one.
Threat actors can create their own fake digital certificates that mimic the legitimate certificate of an established brand, which are then used to create fake websites that host malicious content.
Subdomain takeovers and SSL certificates
A subdomain takeover occurs when hackers gain unfettered access to one or more subdomains within an organization’s DNS records, usually caused by poor housekeeping and inadequate third-party service management.
Once a subdomain has been captured, threat actors are able to generate valid SSL certificates using a legitimate certificate authority, which dramatically increases legitimacy in the eyes of any potential victim.
Unless you’re able to perform a quick and comprehensive search for certificates similar or identical to your brand’s name that aren’t hosted on trusted infrastructure (i.e. created or hosted by threat actors), then your public DNS presence is significantly more at risk of being compromised.
Silent Push brand impersonation defense tools
Our platform contains an exhaustive list of queries that combat all the constituent TTPs of a brand spoofing attack, without the need to utilise numerous distinct platforms, with varying results depending on how each one approaches digital threat management.
Silent Push contains a set of role-based impersonation detection tools that leave no stone unturned, and shine a light on your online presence in ways that are all too often overlooked by brands and other security vendors alike.
All of our queries are designed to be used in unison with one another from a centralized, user-friendly UX, offering enriched data that shines a light on your public DNS presence in ways that no other security platform can match:
- Favicon searches
- Content similarity searches
- TXT record queries
- Certificate queries
- MX record searches
Take advantage of Silent Push’s vast array of threat defense tools by signing up for our free Community App.