We recently published a blog that uncovered an online retail scam involving popular brands such as Ralph Lauren, Nike, Adidas, and Prada.
As promised, our analysts have conducted further research, and we’d like to share what we’ve discovered.
To extract money from unsuspecting users, the operation uses three distinct phishing/social engineering techniques:
- Redirection to a PayPal page, with an attacker-controlled recipient email.
- Catphishing users with a PayPal invoice.
- Harvesting data to a local or intermediate server.
In our first blog, we described how the attackers skim payment card details and PII to a malicious server.
Let’s take a look at how the scam uses PayPal to extract money – either via direct payment or through a legitimate PayPal invoice.
Method 1 – Redirection to a PayPal payment page
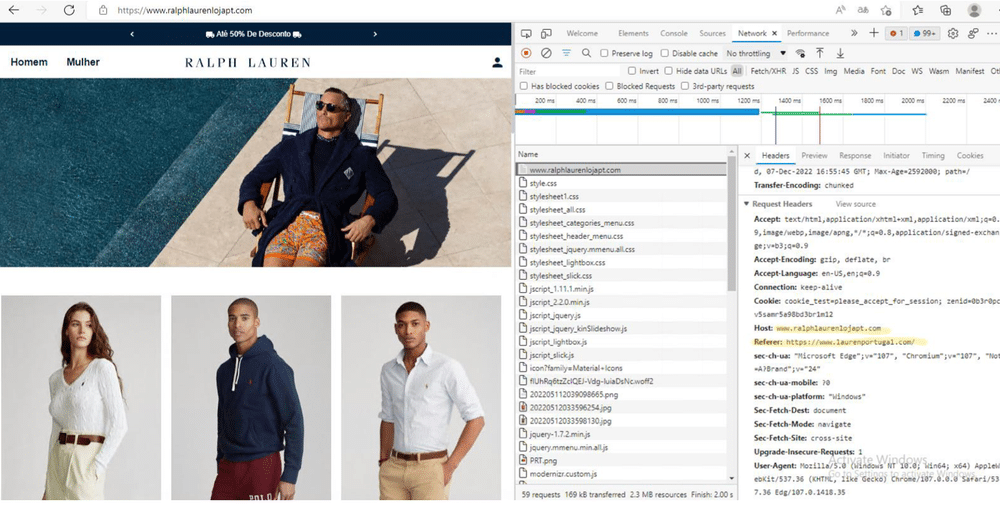
After they’ve been fooled into visiting a hoax website, the user is prompted to enter personal information into a web form to create an ‘account’.
They’re then redirected to a payment page, such as the one below:
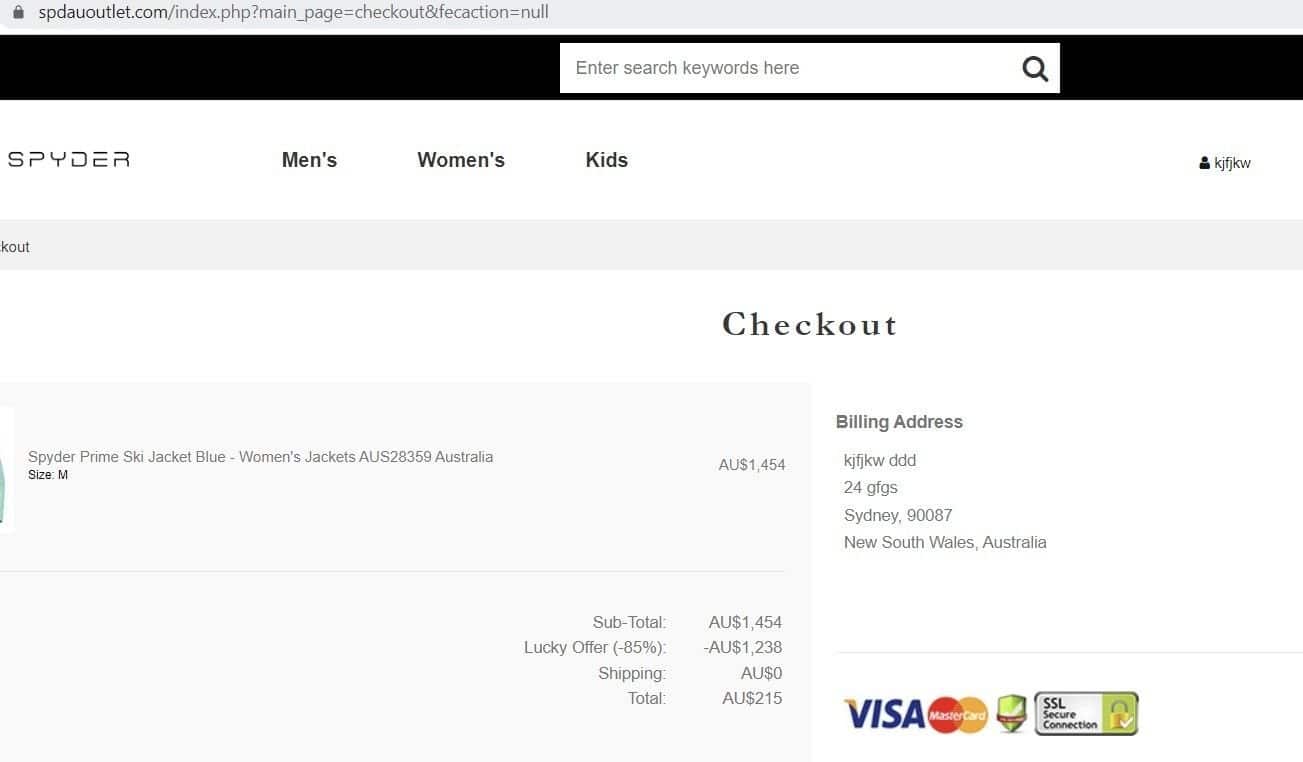
Once the user has entered their payment card details, the site redirects them to a PayPal login page, with the order ID and amount to be debited included as pre-configured parameters.
The minimum order amount appears to be $95-$99, with smaller orders following a different redirection path.
The attackers also don’t bother calculating an exact order amount. Once a minimum order threshold of $95-$99 is reached, any exceeding amount is ignored.
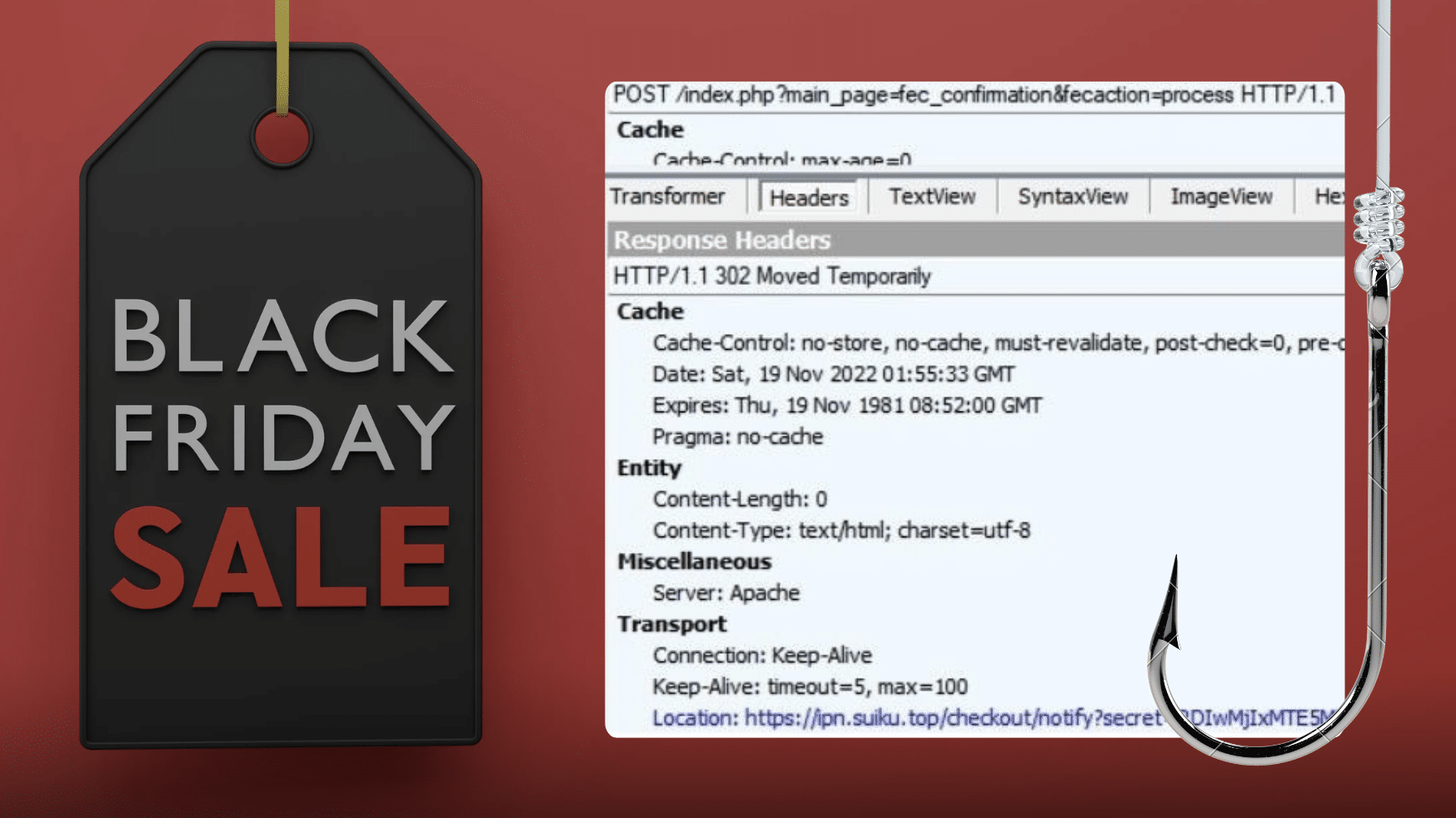
After analyzing the POST request generated by the card submission, we discovered that users are routed through another URL (belonging to ipn.suiku[.]top) before arriving at PayPal:
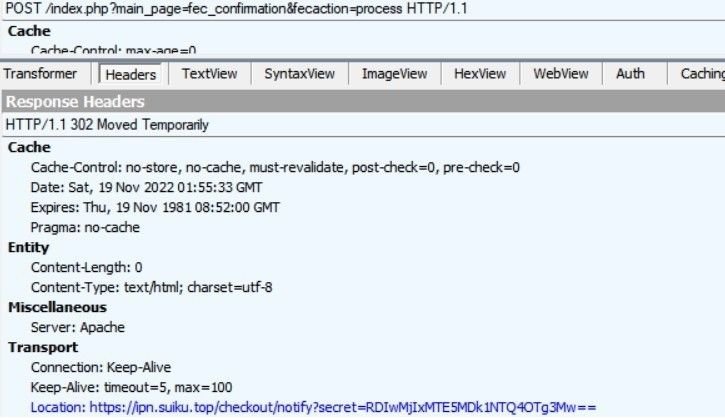
The URL then populates a PayPal page, with an attacker-controlled recipient email (see below for a list of associated emails) and the amount to be debited pre-loaded via a few lines of code:
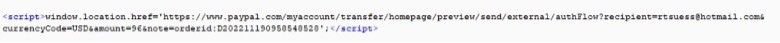
Method 2 – Legitimate PayPal invoices
Instead of relying solely on payment card details, some of the sites use a legitimate PayPal invoice to extract money from unsuspecting users.
This type of technique should immediately raise concerns. Online consumer checkouts rarely – if ever – request payment via an invoice. Such methods of payment are almost exclusively reserved for B2B transactions.
This fake Reebok checkout page generates a PayPal invoice for $97, rather than asking for a direct card payment:

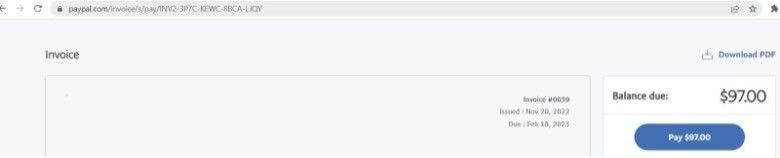
Once users agree to pay the invoice, they’re then redirected to a PayPal login page to complete the transaction, as seen in method 1 above.
When analyzing the POST request code from a traffic capture after the checkout form has been submitted, we can see that the invoice page URL is directly embedded in the HTML:
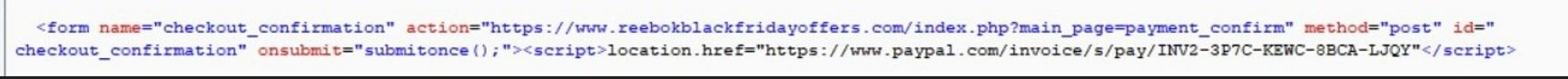
Next steps…
We’re adding a custom threat feed to the Silent Push platform that paid subscribers can use to stay one step ahead of the scam. We’ll also be passing our findings on to PayPal.
PayPal has safeguards in place that remind users of the need to be vigilant online, but as we’ve seen, this group of threat actors is casting their net far and wide with a variety of attack vectors that exploit some of the biggest names in online retail.
Visit silentpush.com for more information on how Silent Push can help to protect your infrastructure in the run-up to the holidays.
Register for the Community version to take advantage of the largest free library of SaaS-based threat defense tools available anywhere in the world.
IoC list
Email accounts associated with the scam
- dhepzrgwnuq@hotmail[.]com
- wmwtvcdv@hotmail[.]com
- rtsuess@hotmail[.]com