Data enrichment allows security teams to pinpoint the origin, function and risk level of a domain, IP address, or Autonomous System (AS).
ASN enrichment returns multiple categories and sub-categories that provide significantly greater context than standard DNS lookups and queries are able to achieve.
In this blog, we’ll explore the concept of ASN enrichment via Silent Push. We’ll take you through how to enrich an ASN using the Silent Push console, what data is returned, our risk scoring methodology and how to turn enriched ASN data into actionable intelligence.
What are Autonomous Systems?
Just like a post office manages the mail it receives and delivers, Autonomous Systems manage a specified set of IP addresses, using a routing policy that dictates how traffic moves to and from their IP space to enable the efficient exchange of information across the globe.
In a hierarchical sense, Autonomous Systems identify entire networks, while subnets are divisions within those networks, managed by the AS itself.
Autonomous System Numbers
An Autonomous System Number (ASN) is a unique numerical identifier (e.g. 5483), displayed as a 16 or 32 bit number, that allows networks to communicate with each other, and ensure that data packets are routed correctly.
Like a digital license plate, ASNs can be used by security analysts to attribute malicious activity to certain actors, or map relationships across an attack chain (i.e., between organizations, hosting providers and service providers).
What role do Autonomous Systems play in CTI?
ASN analysis features prominently throughout a range of threat hunting and cyber defense workflows.
Security teams search across ASN data to join the dots across the global IP space in a variety of ways, from establishing a geographical picture of where threats may be originating from, to behavioral analysis, internal scoring methodologies and general risk-based countermeasures.
These use cases, however, are not without their challanges. Analysts are faced with the obstacle of incomplete AS datasets that only provide a basic level of information, without the requisite categorization of risk levels, subnets and interval-based analysis that shine a light on malicious activity in amongst an ocean of irrelevant and distracting data.
Data independence
What if a security analyst was able to enrich ASN data to provide all of this this information one place, from ASN reputation scoring to the parameters of each subnet address associated with an AS?
Silent Push achieves this by using our own first-party intelligence data that’s collected, clustered, scored and delivered without third-party intervention.
This allows us to add an infinite amount of context to each ASN that we encounter, drill down into actionable data, and provide this information alongside other key observables via an integrated console, saving valuable time and resources for frontline security teams and researchers across a range of CTI workflows.
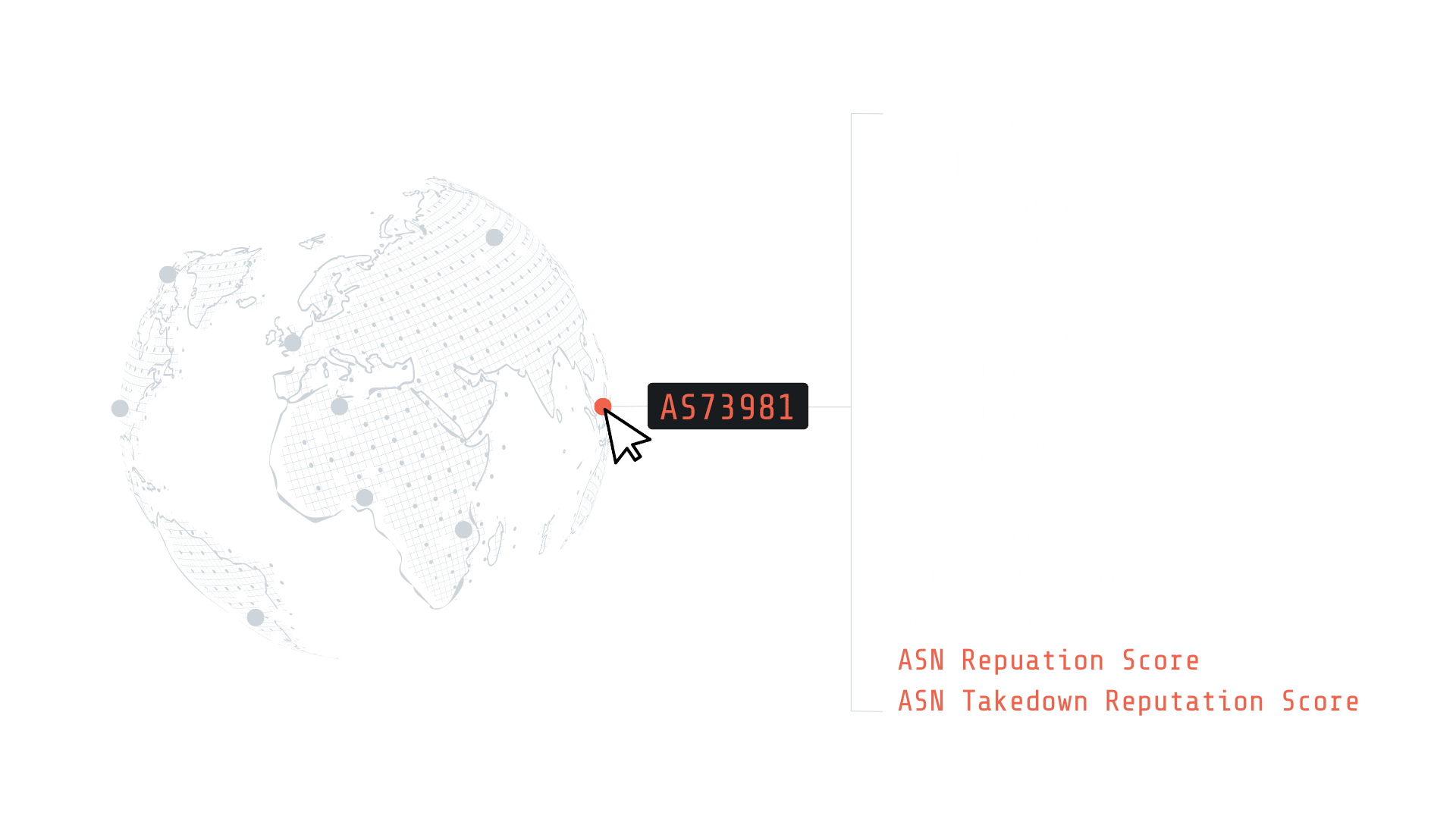
Accessing ASN Enrichment in Silent Push
There are two ways to enrich an ASN in Silent Push:
If you do NOT know the ASN
Enrich a domain or IP address and pivot into enrichment from the returned ASN.
If you DO know the ASN
Enter the ASN directly into the search bar, and click Enrich
ASN enrichment categories
1. Highlights
ASN Enrichment Highlights are shown at the top of the ASN Enrichment page.
These are a group of scores and numerical values that act as reliable indicators of an ASN’s risk level.
ASN enrichment Highlights include:
- ASN Reputation
- ASN Takedown Reputation
- Active IPs
- Active Subnets
- AS Name
- Average Density
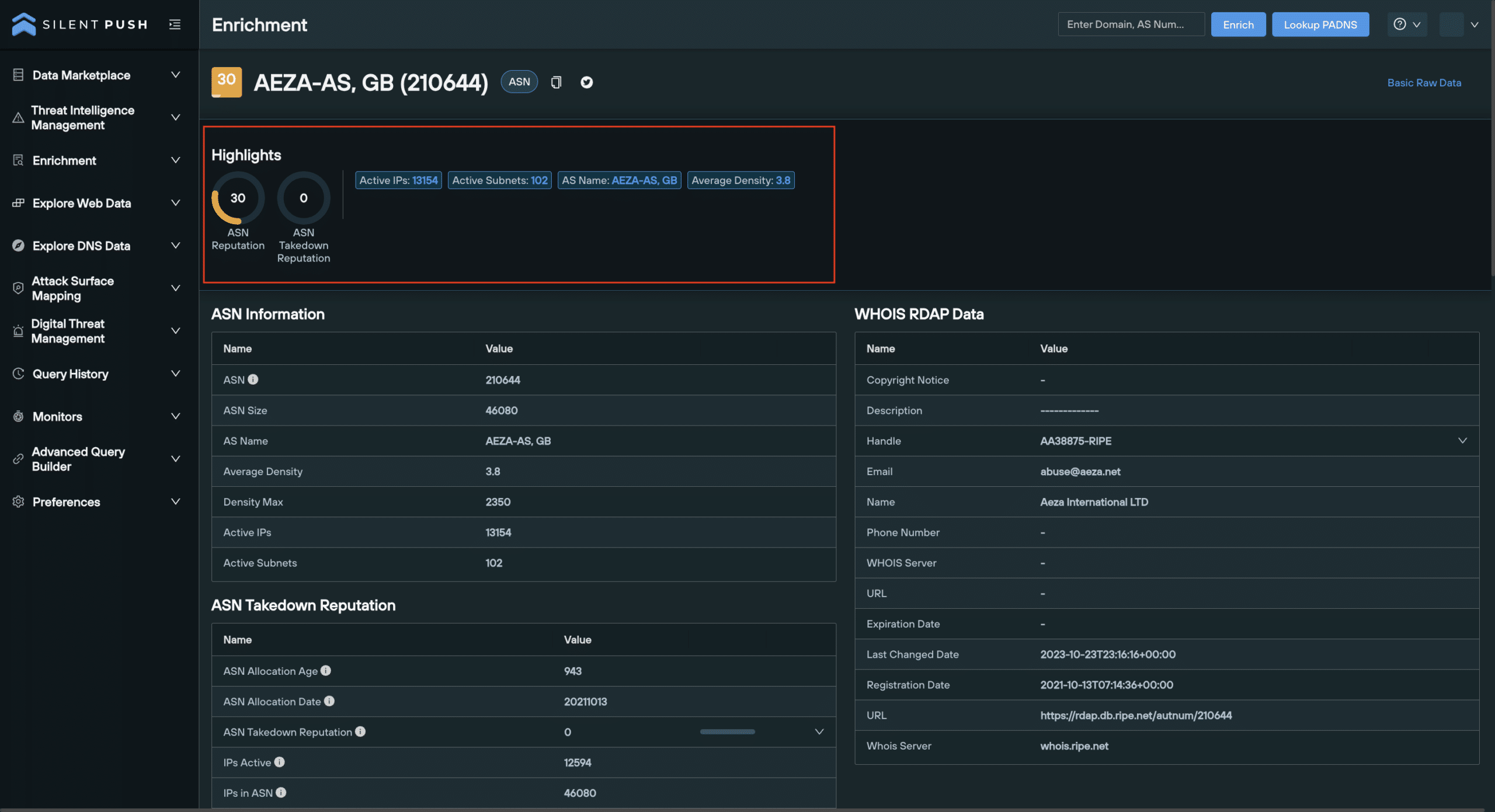
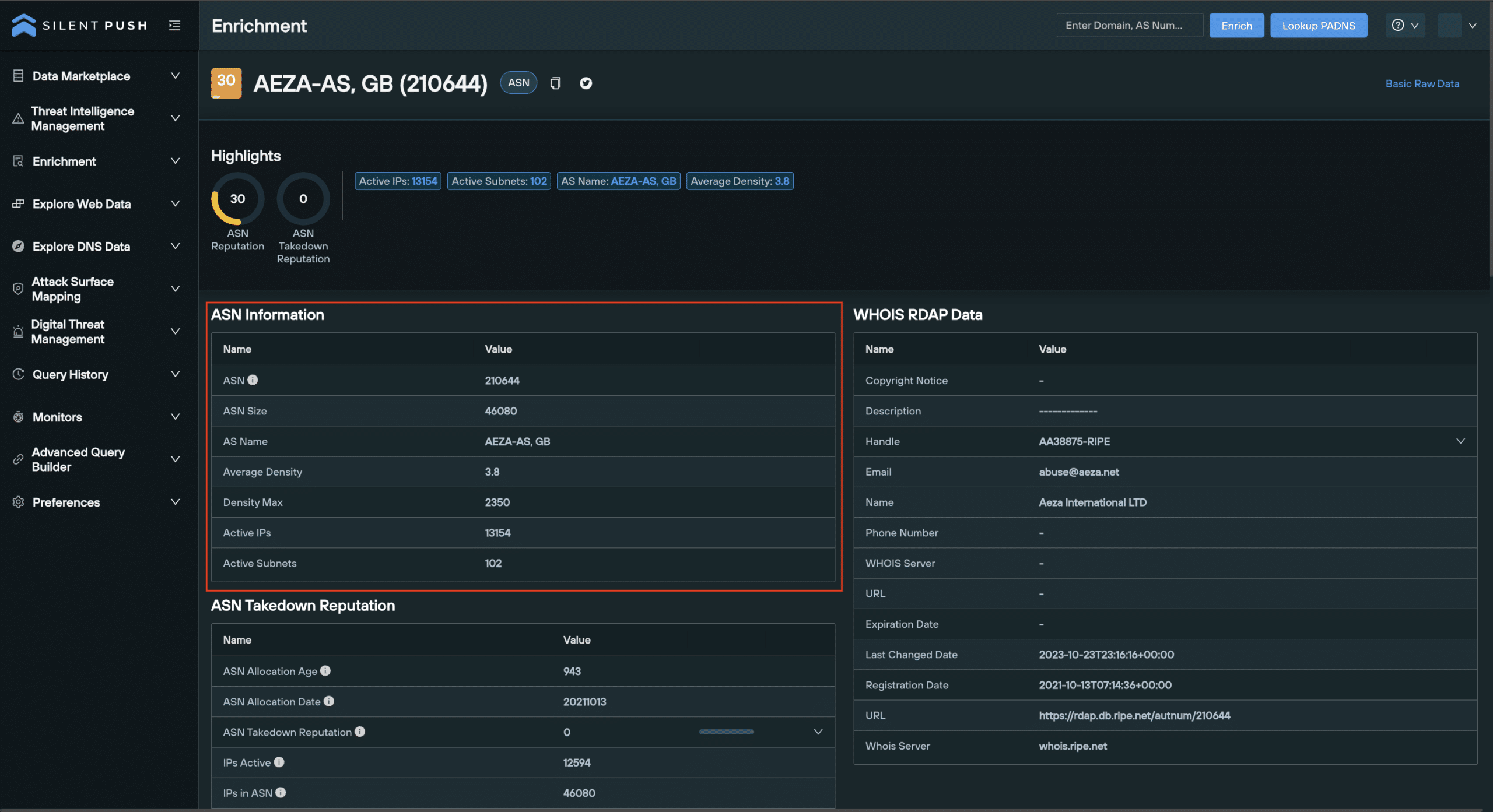
2. ASN Information
The ASN Information category does does exactly what it says on the tin. It gives a basic overview of the enriched ASN, including its unique identifier number, size, provider name, density, maximum density, active IPs and active subnets.
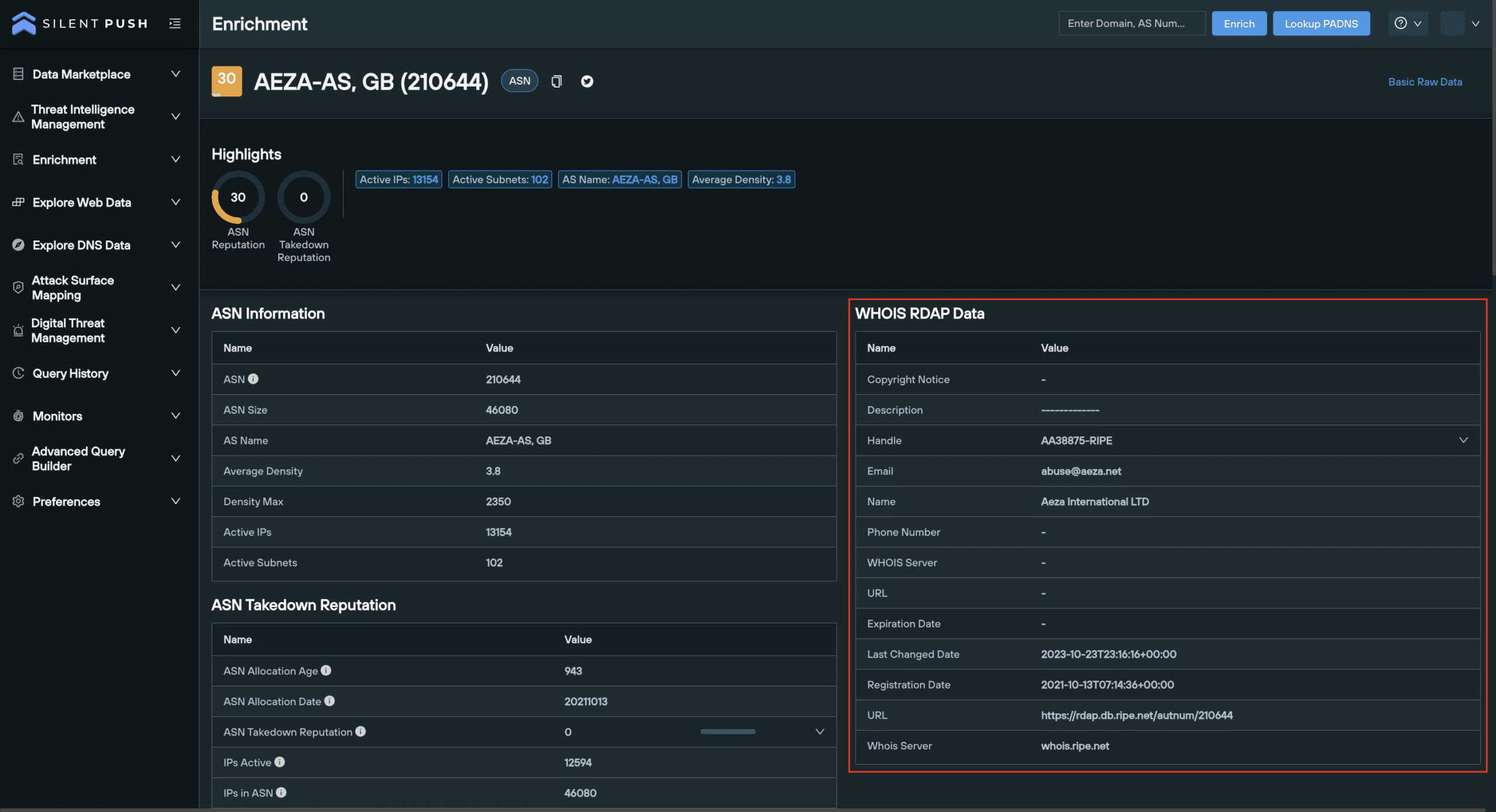
2. WHOIS RDAP data
The WHOIS RDAP category returns administrative data pulled from WHOIS and RDAP registration lookups in one centralized location, presented alongside other key data types.
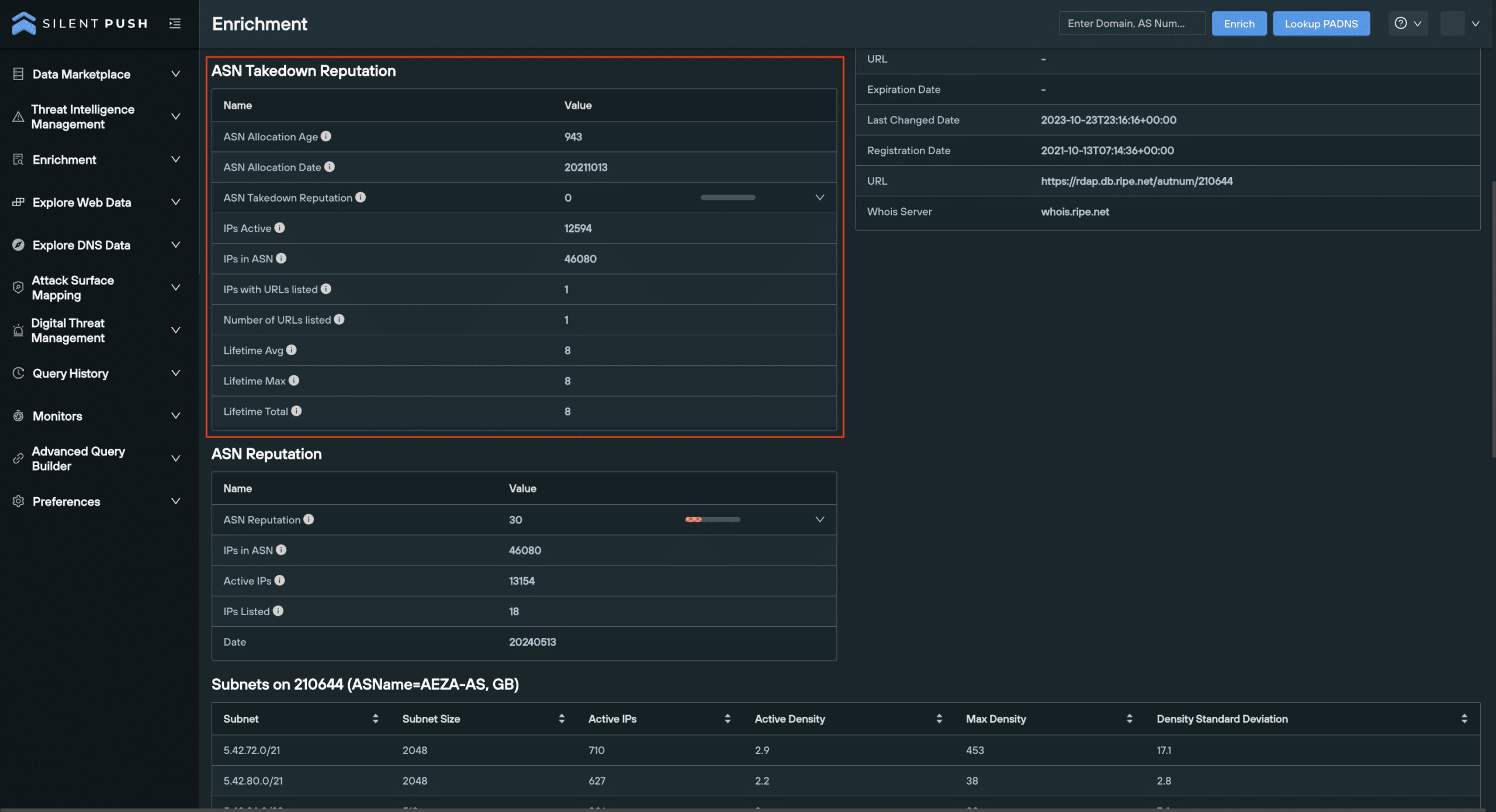
3. ASN Takedown reputation
ASN takedowns play a critical role in protecting the digital assets of an organization.
The ASN Takedown Reputation category details how efficiently malicious domains are being removed on the ASN.
ASN Allocation Age indicates the age of the ASN number in days, and the ASN Allocation Date indicates precisely when the Internet Assigned Numbers Authority (IANA) allocated the ASN.
The ASN Takedown Reputation Score is a Silent Push invention that measures the ability and willingness of a network’s service provider to take action to mitigate cyber threats associated with the network.
The score is calculated using a combination of attributes, including the service provider’s history of responding to abuse reports, and the time it takes to mitigate malicious activity associated with their network.
- A high takedown reputation score indicates that network provider is more likely to take swift action in mitigating malicious activity associated with their network
- A low takedown reputation score indicates the network provider is less likely to be responsive or effective at mitigating known threat activity.
4. ASN reputation
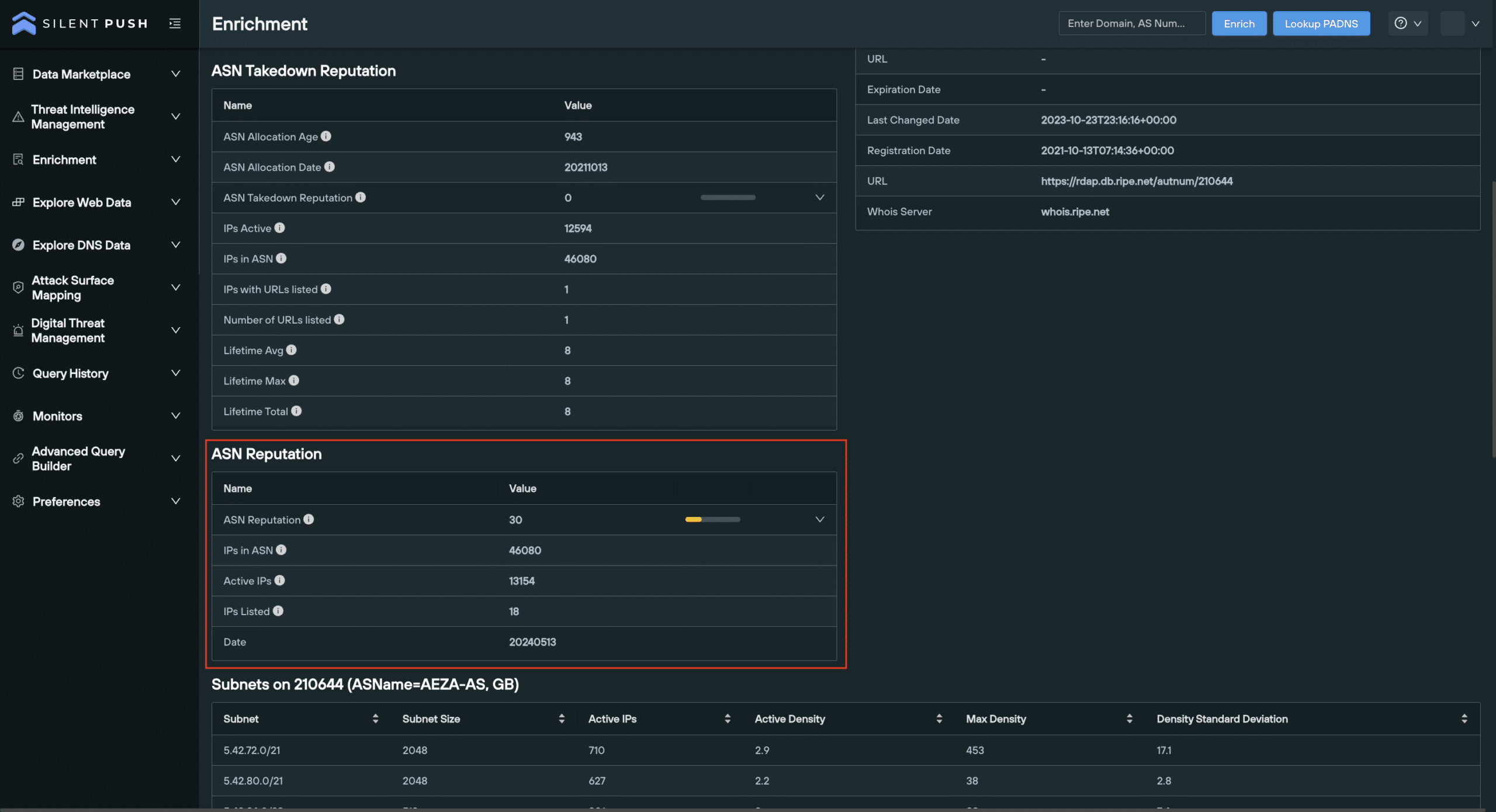
The ASN Reputation indicates the trustworthiness and legitimacy of the IPs associated a particular ASN. It’s calculated using the ratio of blacklisted IPs, taken from from the total number of IPs that have been observed as being active within an ASN, in the last 30 days.
- A high score suggests that an ASN has a large amount of blacklisted IP addresses associated with its network.
- A low score indicates the ASN has is a minimal amount of blacklisted IP addresses associated with its network, and that the ASN is likely trustworthy.
5. Active Subnets
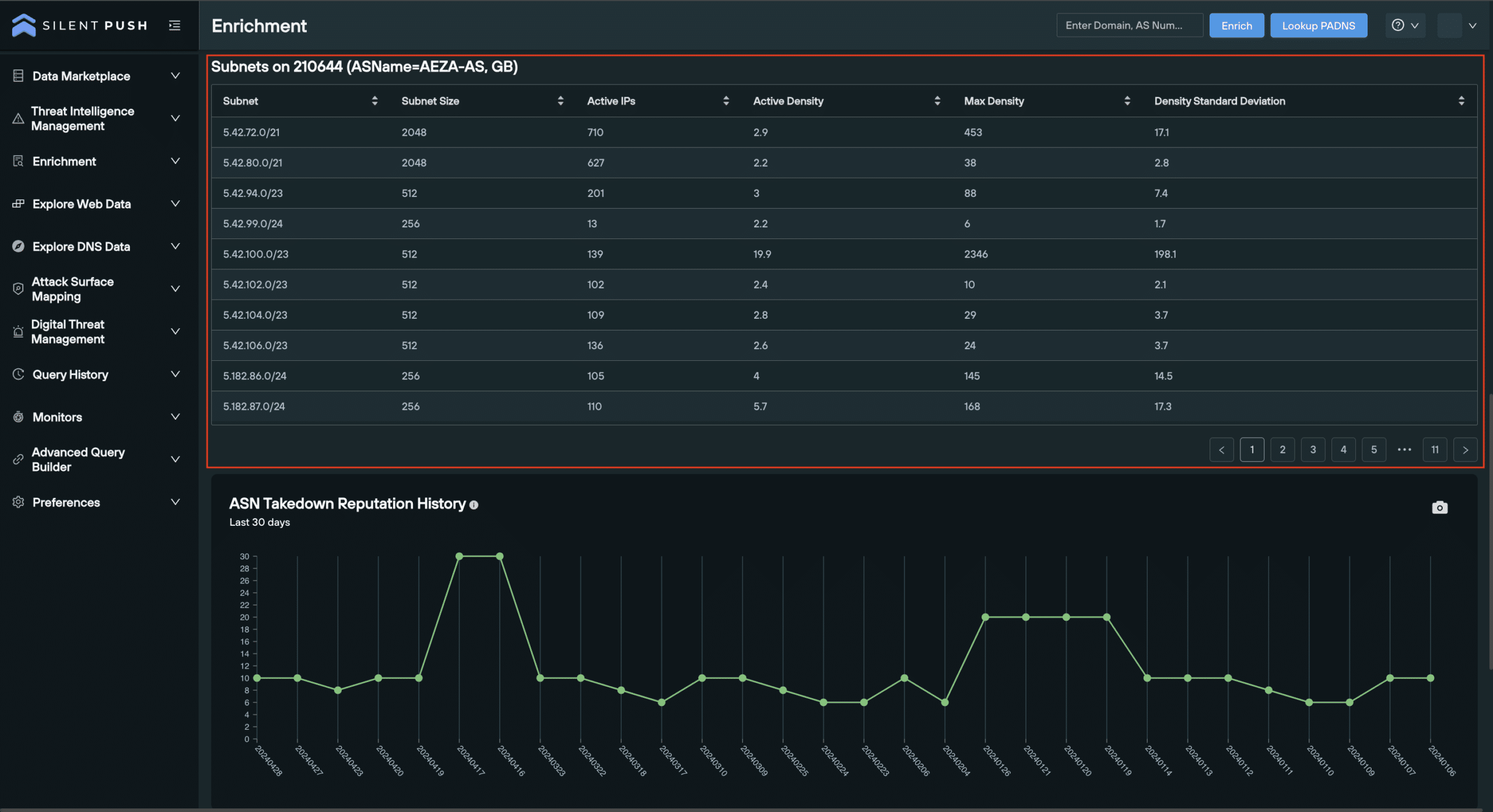
This category highlights all active subnets associated with the ASN.
It details the size of the subnet, active IPs on the subnet, active density, max density and density standard deviation. This helps security teams map out the scope of an ASN’s subnets, and monitor for suspicious activity.
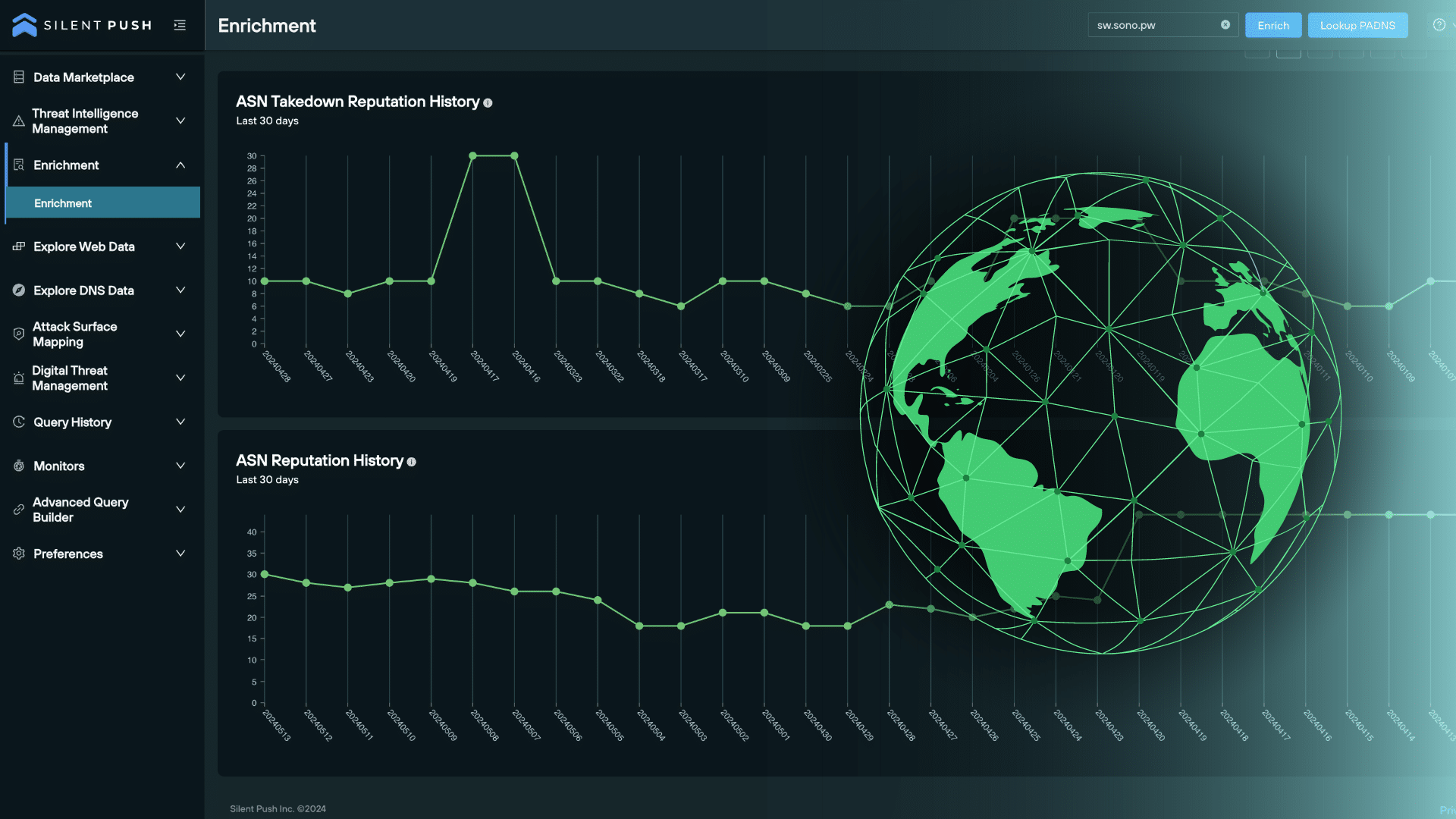
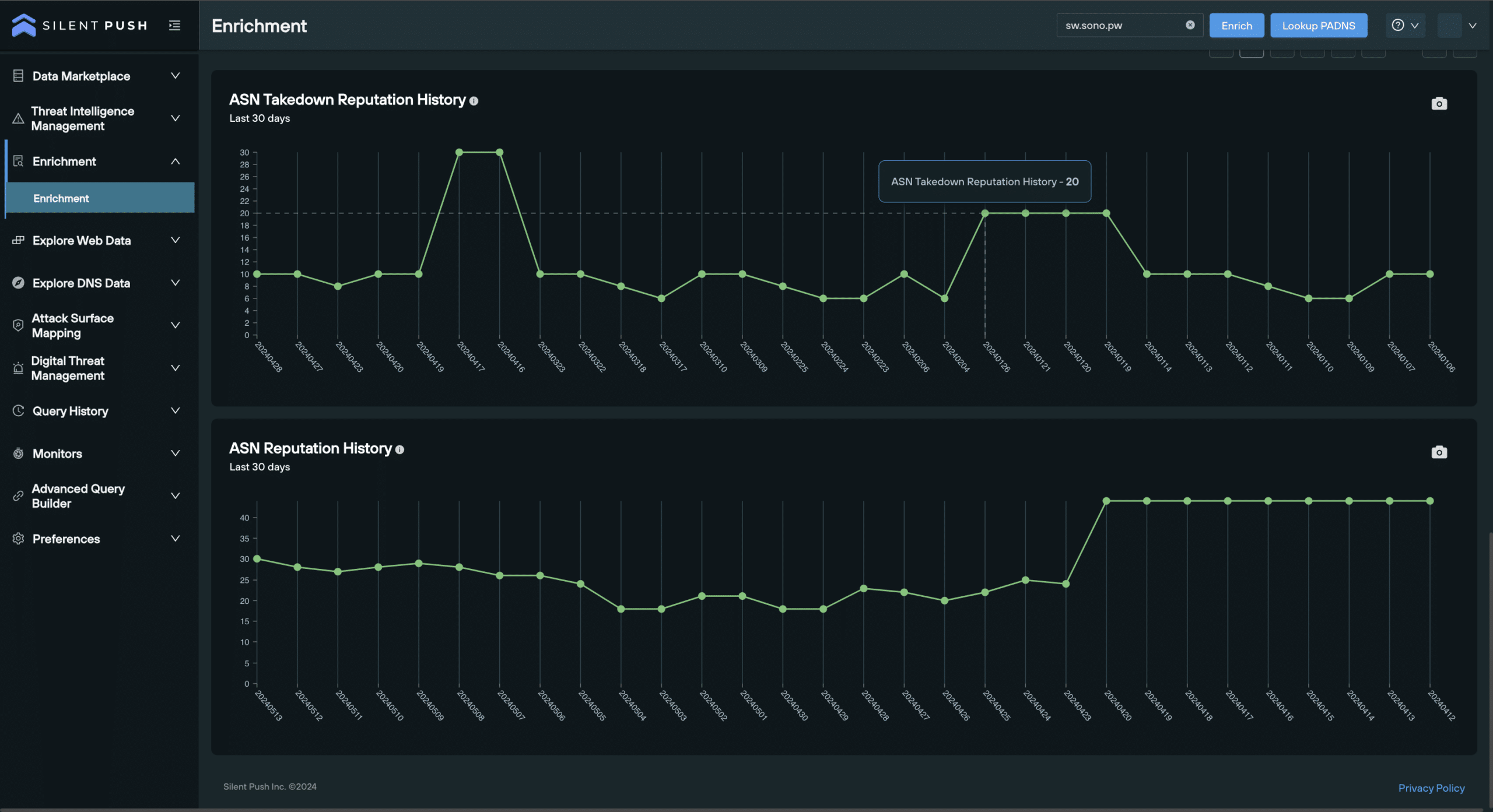
6. Graphical data
The ASN Takedown Reputation History and ASN Reputation History graphs provide a visual timeline that maps out the risk level associated with a specific ASN over a set period of time, providing further context for teams looking to asses the risk level associated with a given ASN.
Register for Community Edition
ASN Enrichment is available as part of Silent Push Community Edition – a free threat hunting and cyber defense tool used by security teams, threat analysts, and researchers that features 90+ data enrichment categories that you can use to track and monitor attacker activity across the global IPv4 space.
Click the button below to sign-up for a free account.