Key Findings
- Silent Push Threat Analysts have discovered that the Araneida Scanner – which appears to be based in part on a cracked version of Acunetix, a popular web app vulnerability testing tool – is being used by threat actors for illegal purposes.
- Beyond Araneida, our threat analysts found another cracked tool, with a login panel in Mandarin, that is likely also abusing a cracked version of Acunetix software for launching reconnaissance for future attacks.
- Our investigation was prompted by one of our partners sharing information on a reconnaissance effort made against them.
- Update 12.19.24: After Silent Push analysts shared our research with Brian Krebs of Krebs on Security, he published a report that connects the owner of Araneida to a software developer living in Ankara, Turkey. Read more at “Web Hacking Service ‘Araneida’ Tied to Turkish IT Firm“
- Key Findings
- Executive Summary
- Sign Up for a Free Silent Push Community Account
- Background
- Initial Intelligence: Suspicious Website Scanning
- First Public Mentions of Araneida & Acunetix in 2023
- Investigating Araneida
- Chinese Portals Likely Using a Cracked Acunetix Scanner
- Other Threat Actors Abusing Acunetix
- Continuing to Track Cracked Acunetix / Araneida Scanner
- Mitigation
- Register for Community Edition
- Sample Indicators of Future Attacks (IOFAs)
Executive Summary
Silent Push Threat Analysts have discovered that the Araneida Scanner, which appears to be based in part on a cracked version of Acunetix, a popular web app vulnerability testing tool, is being used for illegal purposes, including conducting offensive reconnaissance on potential target sites, scraping user data, and finding vulnerabilities for exploitation.
Araneida was recently used in a reconnaissance effort against one of our partners, which is what initially prompted our investigation.
Additional investigation has indicated that third parties are promoting Araneida on platforms such as Telegram and selling hundreds of thousands of stolen credential sets.
The Telegram channel provides guidance on using the tool for malicious purposes. Some threat actors using the Araneida scanner boast of taking over thousands of websites, using funds obtained from malicious activities to buy luxury cars, and reveling in wreaking chaos on tech websites.
Silent Push Enterprise users have access to two dedicated IOFA Feeds containing all the true positive domains and IP addresses we have gathered during our research.
For operational security reasons, we are unable to share the exact specifics of each query and pivots utilized. Silent Push Enterprise customers have access to a dedicated Araneida Scanner TLP: Amber report, which contains the relevant data types and pivot points we used to track the infrastructure referenced in this blog.
Sign Up for a Free Silent Push Community Account
Register for our free Community Edition to use all of the tools and queries mentioned in this blog.
Background
Silent Push Threat Analysts received intelligence from a partner organization that identified an aggressive scanning effort on their website using an IP address previously associated with a FIN7 campaign. However, we didn’t have full confidence that FIN7 controlled the IP address at the time of the scanning. The IP address featured specific metadata, “Araneida Customer Panel,” which we quickly confirmed was a key to uncovering more unique IP addresses hosting this service.
Our team discovered that a scanning tool called “Araneida – WebApp Scanner” is being publicly sold and used by threat actors to conduct offensive reconnaissance on potential target websites, scrape user data, and find vulnerabilities for exploitation.
We also discovered another cracked tool that is owned by an entity that uses Mandarin on its login page and an HTML title in Mandarin. Silent Push Threat Analysts haven’t found a public sales process for this product yet, but the same Chinese-language panel has been hosted on 20 unique IP addresses, indicating some diversity in deployments.
Both appear to be based on cracked, unauthorized versions of Acunetix, a popular web app vulnerability testing tool.
Araneida was recently used in a reconnaissance effort against one of our partners, which initiated our current investigation. Both Araneida and the Chinese language panel using this cracked enterprise software could be used for reconnaissance prior to launching sophisticated offensive attacks.
Our team has executed granular content scans in the Silent Push Web Scanner to locate and traverse Indicators Of Future Attacks (IOFAs) related to the cracked Acunetix control panel infrastructure.
Araneida admins are also actively marketing the tool’s criminal capabilities on Telegram and selling hundreds of thousands of credential sets stolen through Araneida.
Both threat actors are using legacy Acunetix SSL certificates on active control panels, which provides a solid pivot for finding some of this infrastructure, particularly from the Chinese threat actors.
The Araneida Scanner has a unique setup that is important for defenders to understand in order to detect and block:
- After acquiring the Araneida Scanner, a user is given the client as a Windows executable (.exe) file.
- The user installs the executable file, logs into the Araneida client, and is directed to follow specific steps to set up the scanner.
- Araneida is a noisy scanner. If the tool is being used against any of your hosts, you will see requests attempting to connect to various endpoints and making requests to random URLs associated with specific CMS/products:
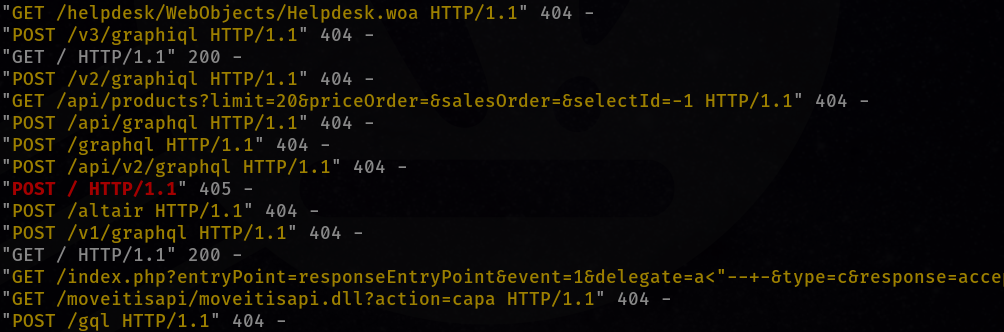
Initial Intelligence: Suspicious Website Scanning
Based on the intelligence shared with us by a partner regarding the aggressive scanning effort, our team began researching an IP address that had hosted content and specific metadata.
We quickly confirmed the data and that additional websites were using this unique Araneida hosting service. Further investigation of these websites revealed they shared proprietary information associated with Acunetix.
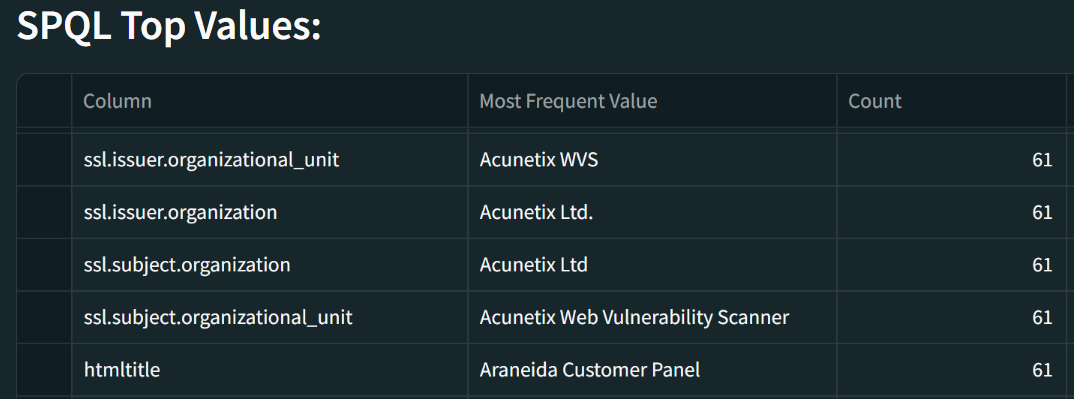
The utility used to scan our partner’s network featured the name “Araneida” but also used information from Acunetix, suggesting the presence of cracked software.
After making this assumption, our team contacted the Invicti team, which owns the Acunetix product, and they quickly confirmed our suspicions.
The Invicti team confirmed that a cracked version of Acunetix was being sold. They also confirmed that there were no impacts on their clients—the integrity of data at Invicti was never at risk, and this is an isolated incident.
We appreciated the Invicti team’s quick and transparent confirmation and the additional details they provided.
First Public Mentions of Araneida & Acunetix in 2023
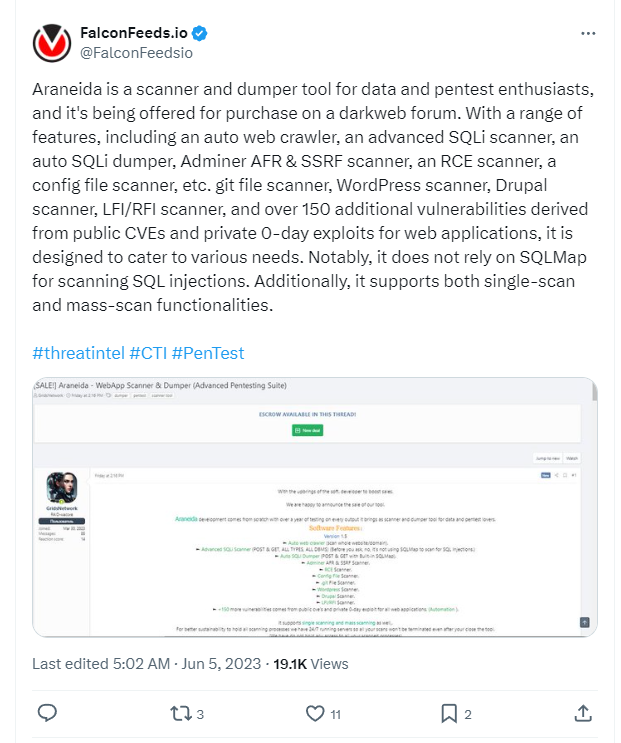
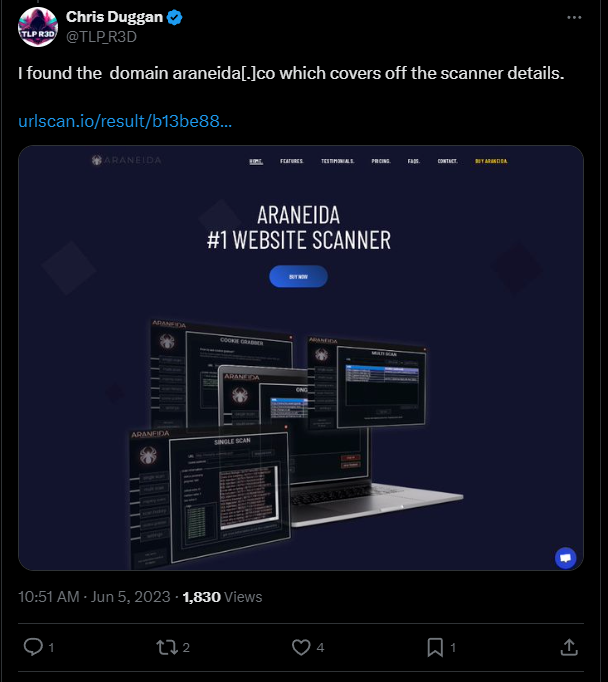
Several threat intelligence vendors and researchers discussed Araneida publicly on June 5, 2023, with FalconFeeds[.]io apparently being the first to share details:
On the same day, Chris Duggan of TLP R3D Intelligence was the first to connect Araneida to Acunetix:
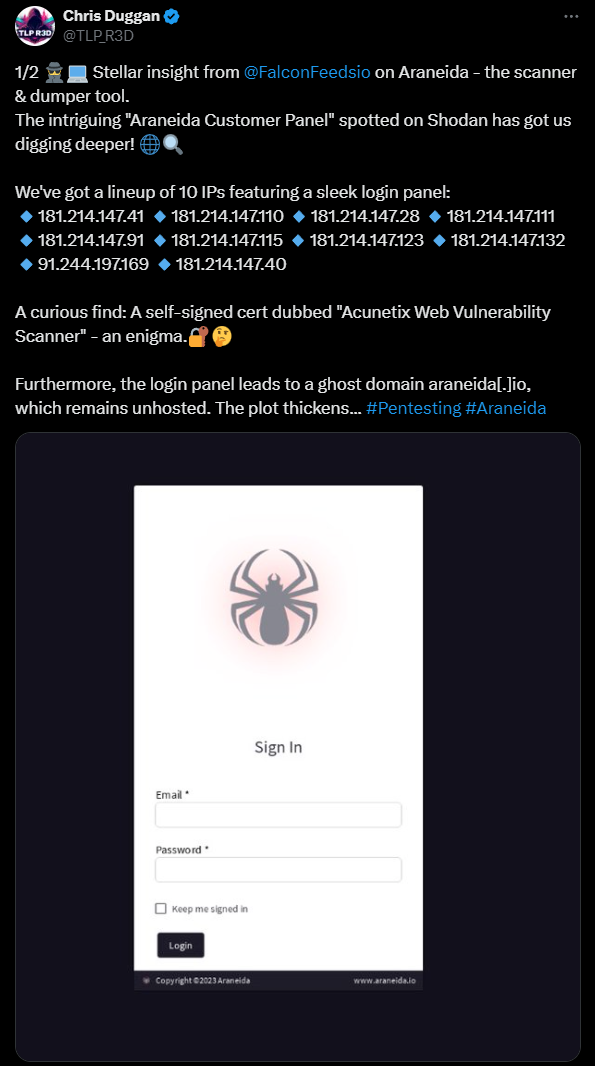
Duggan was also the first to flag the domain that is still selling the Araneida Scanner: araneida[.]co
Investigating Araneida
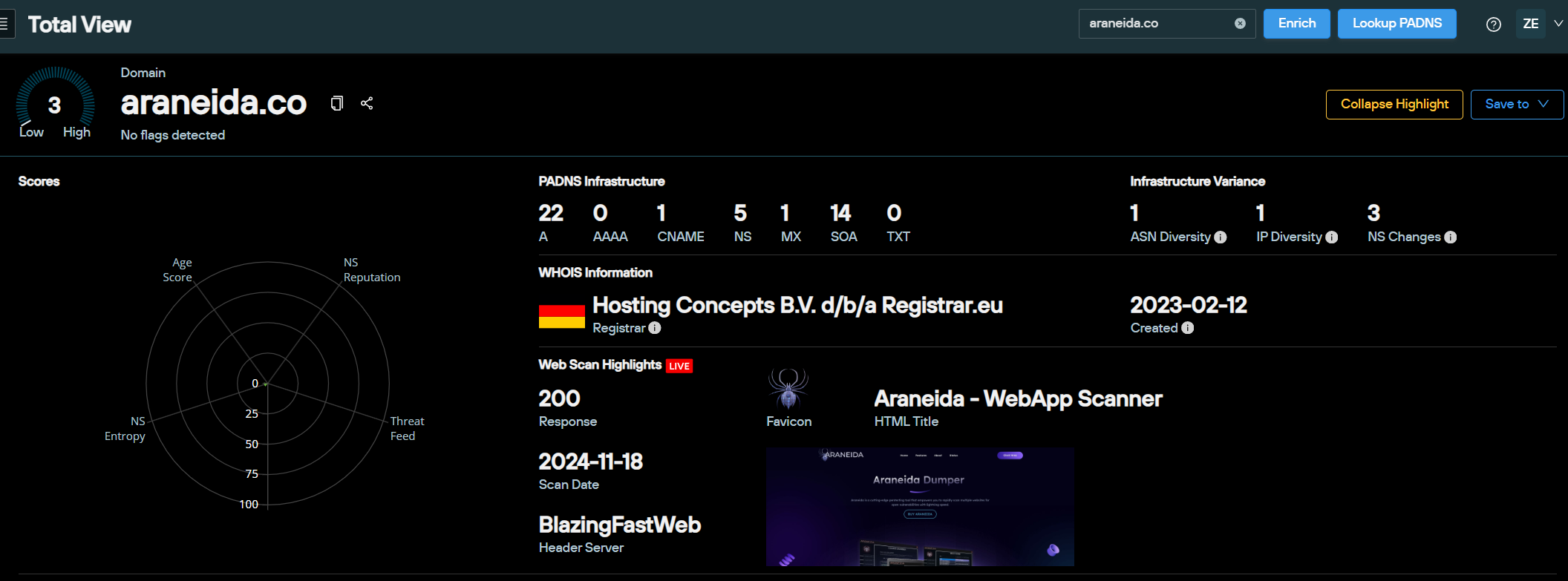
Our team was able to determine that the Araneida Scanner is still being sold in 2024 via araneida[.]co, which was a domain created in February 2023:
Inside the scanner product, this is what the client looks like after login:
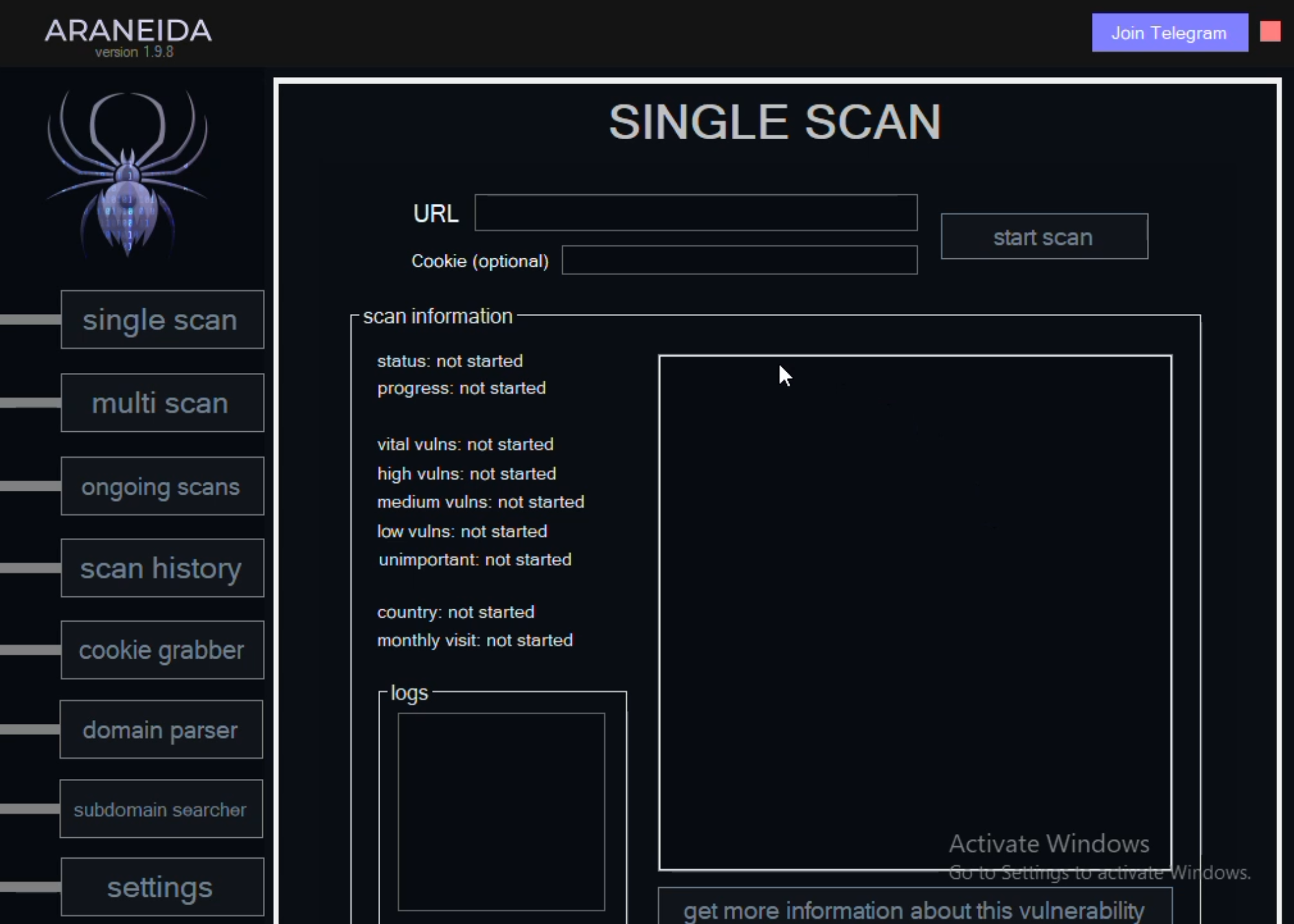
This is a brief video showing the features in the Araneida Scanner:
The video clip above highlights features in the Araneida scanning product
Between September 2023 and March 2024, 36 unique IP addresses hosted a page referencing the “Araneida Customer Panel.” The fact that we hadn’t seen any results since March 2024 indicated that the network operators changed their deployment behaviors.
During the course of our research, we realized there was a second threat actor beyond Araneida likely using a cracked version of Acunetix.
Araneida Telegram Channel
The cracked software has nearly 500 members in their Telegram channel at t[.]me/araneida_official.
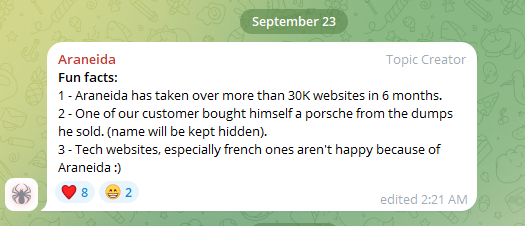
The Telegram channel provides guidance on how to use the tool for malicious purposes and boasts of having “taken over more than 30K websites in 6 months,” with operators using the funds obtained to buy “a Porsche from the dumps he sold,” and claims that “Tech websites, especially french ones aren’t happy because of Araneida :) “
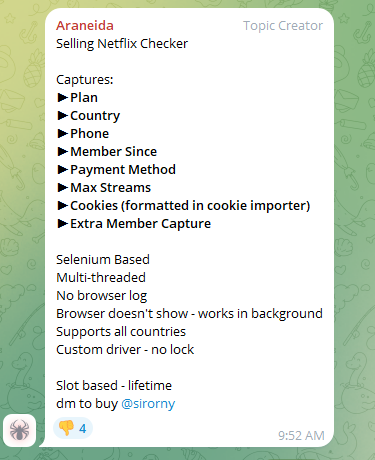
In July 2024, the Telegram channel admins also promoted a Selenium-based “Netflix Checker” tool, which scrapes cookies, payment information, and personal details from Netflix accounts:
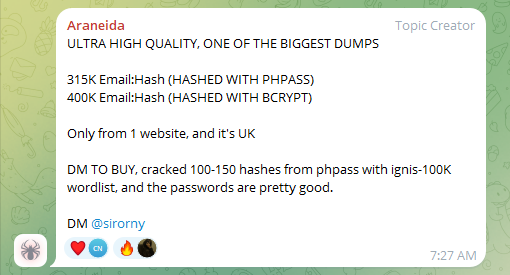
The Telegram channel operators also sell email and password dumps that are likely acquired using their tool, such as the example (below) with hundreds of thousands of login credentials obtained from a UK website:
Chinese Portals Likely Using a Cracked Acunetix Scanner
Continuing our research soon led to the identification of a version of the hosts with the legacy Acunetix SSL, which used Mandarin on their login page.
The first results for this legacy Acunetix SSL on a page with Mandarin language appeared in 2023, and many of the websites are still live, hosting a login portal (as of December 2024):
The page translated into English:
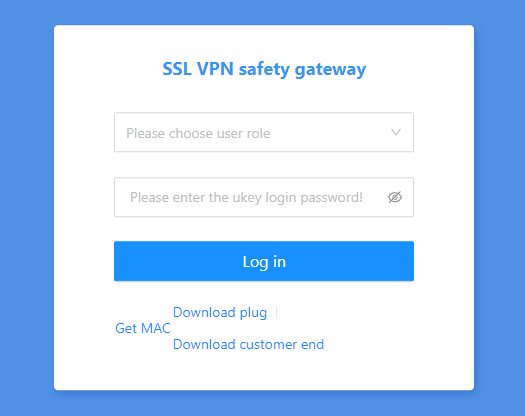
On these login pages, there are two files available for download. One file appears to be a “plugin” labeled “UkeyService_pre” and the other is labeled “Customer End” with a .exe file called “FlkVPN“
These hosts feature a self-signed SSL certificate issued by Acunetix three years ago, which appears to be different from the certificates used on the legitimate Acunetix corporate infrastructure:
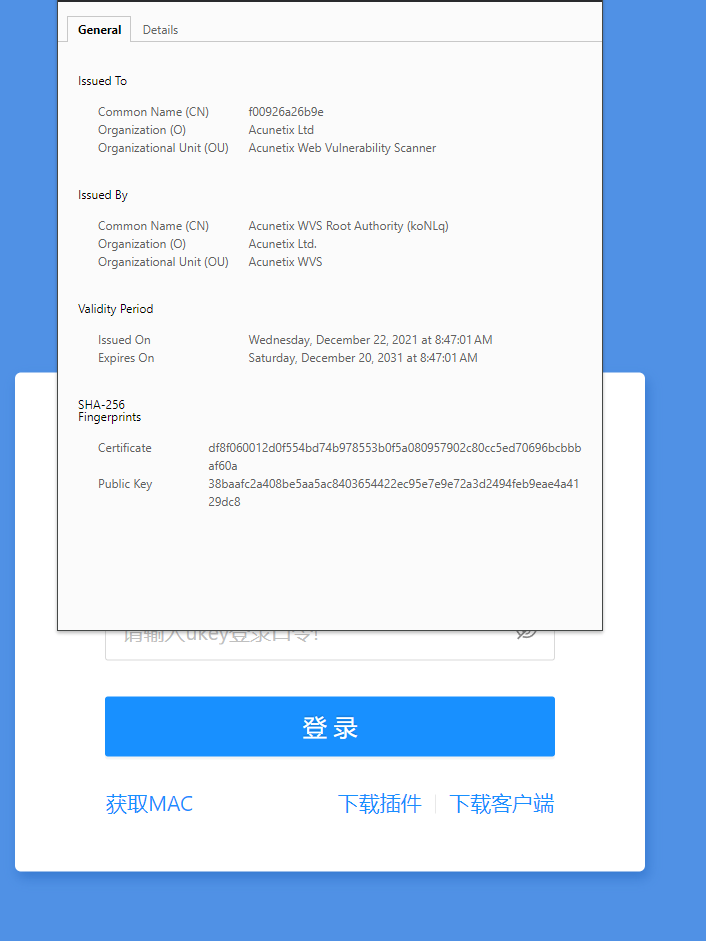
Other Threat Actors Abusing Acunetix
Several instances of threat actors misusing Acunetix have been reported since as recently as 2020.
In November 2020, a joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) reported that an Iranian advanced persistent threat (APT) actor was using an Acunetix vulnerability scanner to target U.S. state and election websites to obtain voter registration data.
In March 2024, Lumen reported that the Faceless proxy service had one IP address being used as a relay to communicate with “Moon and/or Faceless C2s” and that it had an Acunetix web vulnerability scanner service running on two ports.
More recently, in May 2024, APT41, the Chinese Cyber threat actors, were highlighted by Natto Thoughts in using Acunetix in their offensive reconnaissance efforts. Natto Thoughts cited a U.S. Department of Health and Human Services Health Sector Cybersecurity Coordination Center (HC3) report, which lists Acunetix as the first “well-known security tool” used by APT41:
“APT41 also uses well-known security tools, such as Acunetix, Nmap, JexBoss, Sqlmap, a customized version of Cobalt Strike, and fofa[.]su, which is roughly a Chinese equivalent of the popular website Shodan.
To conduct reconnaissance, they are known to use the previously-mentioned Acunetix and Nmap, as well as Sqlmap, OneForAll, subdomain3, subDomainsBrute, and Sublist3r. They frequently use spear-phishing as an infection vector, but are also heavily reliant on SQL injections to initially penetrate a target organization.”
The Chinese organizations using a cracked version of Acunetix could be associated with APT41 but we currently have no additional details connecting the efforts.
Continuing to Track Cracked Acunetix / Araneida Scanner
Silent Push threat researchers will continue to observe and monitor changes to this actor’s infrastructure. New discoveries and TTP changes will be immediately reflected in our feeds.
We’ve also published a TLP: Amber report for Enterprise users that contains links to the specific queries we’ve used to identify and traverse the cracked Acunetix Scanner infrastructure—including proprietary queries and specific analysis that we have omitted from this blog.
Mitigation
Silent Push believes all cracked Acunetix Scanner hosts offer some level of risk.
Our analysts have constructed a Silent Push IOFA Feed that provides a list of Araneida Scanner Indicator of Future Attack domains focused on their scams, along with an IOFA Feed containing suspect Araneida Scanner IP addresses.
Silent Push IOFA Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign up for a free account.
Sample Indicators of Future Attacks (IOFAs)
157.254.237[.]94
163.5.169[.]250
163.5.169[.]45
163.5.210[.]49
163.5.32[.]179
163.5.32[.]202
163.5.32[.]203
163.5.32[.]204
163.5.32[.]72
205.234.181[.]204
23.26.77[.]145



