Silent Push tracks threat actor targeting UK banks in ongoing AnyDesk social engineering campaign

Silent Push threat analysts are currently tracking a campaign that uses fake websites and social engineering to serve a copy of the AnyDesk remote access software to Windows and macOS users, that is then being used to steal data and money once installed on a victim’s machine.
Brands targeted include UK banks HSBC, Natwest, Lloyds, Santander, and Virgin Money, as well as the antivirus company Avast, cryptocurrency wallet provider Ledger, and online bank Wise.
Background
AnyDesk is a Remote Monitoring & Management (RMM) package that provides a connection between two devices, with 1-to-1 screen sharing that allows a remote user to view and control offsite computers and mobile devices.
Legitimate remote access software has a history of being exploited by tech support scammers to propagate a range of digital fraud.
Two years ago, our analysts discovered a network of threat activity masquerading as numerous global brand names, and infecting machines with a malicious file disguised as the popular remote monitoring tool, WinDesk.Client.exe.
AnyDesk attacker TTPs
In the campaign, threat actors use social engineering, spoofed websites and phishing tactics to trick users into downloading a version of AnyDesk via a generic online help link:
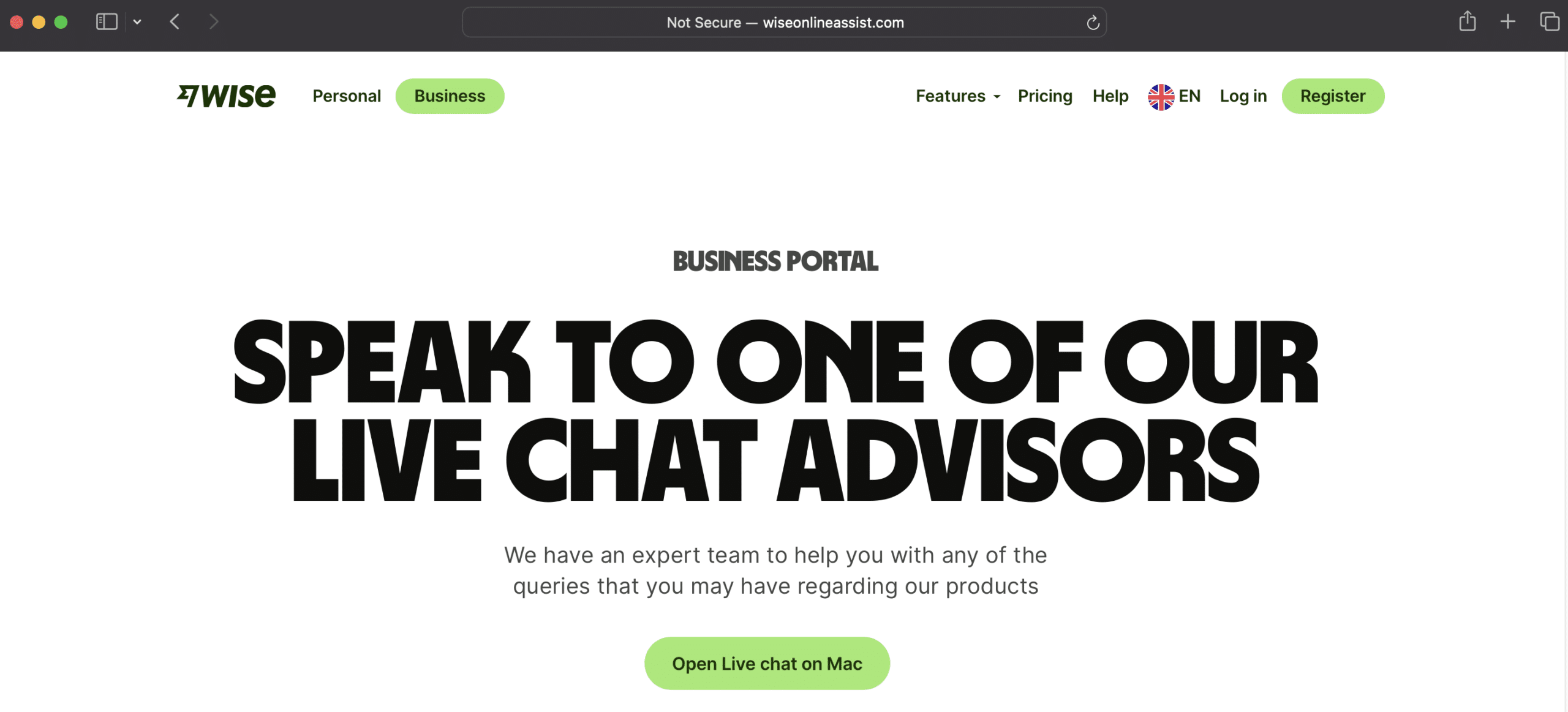
Once the threat actor has remote control of a victims machine, they are able to propagate all manner of attacks, from data theft to financial fraud, including accessing the victim’s bank account.
Previously covered by Threatdown in May 2024, our research indicates that linked activity by an unknown threat group is ongoing, with new domains being registered every week.
Locating AnyDesk threat infrastructure
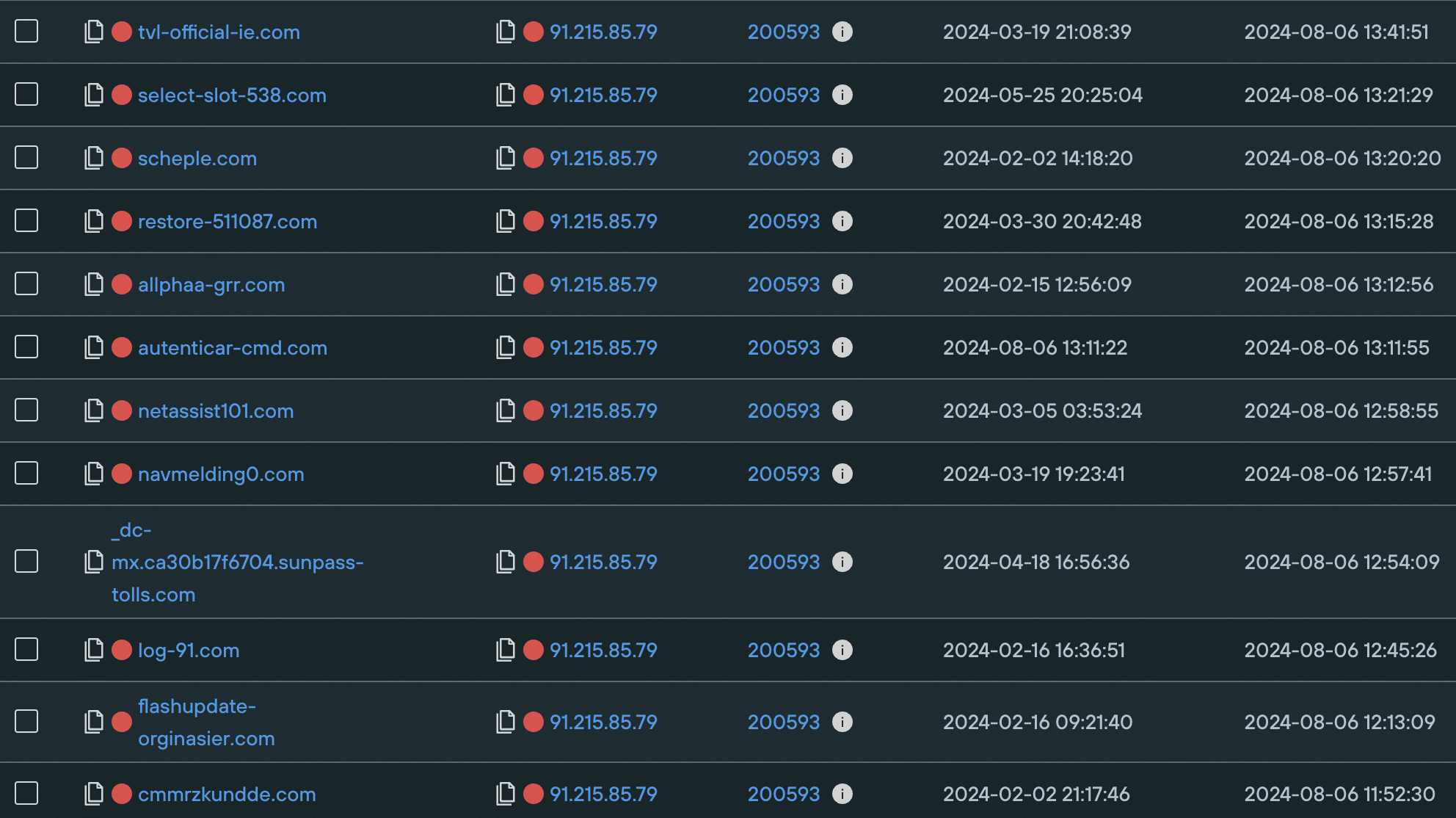
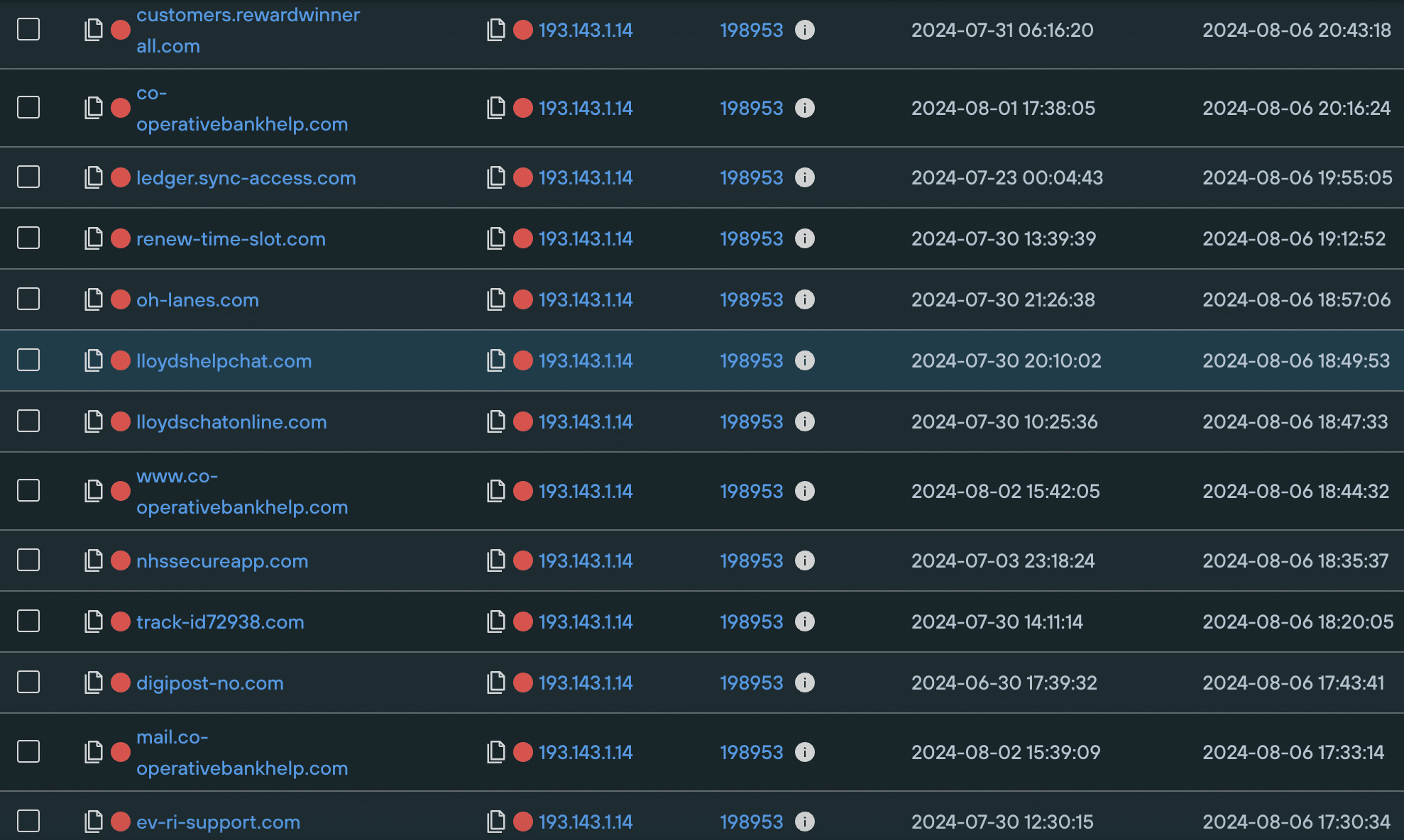
We discovered that most of the domains involved in the campaign are hosted on 91.215.85[.]79 and 193.143.1[.]14, both of which are in Russia and have a long history of malicious activity, with a large number of suspect domains hosted on each.
Executing a Domains Hosted On IP query proves that both IPs are involved in large-scale fake online help activity, going back months.
Here’s a sample of domains hosted on each, with their associated risk score:
The attacker-controlled websites we discovered impersonate different companies by closely mimicking the legitimate brand websites.
We were able to use Silent Push Web Scanner to execute granular content scans that identified groups of domains targeting the same brand, by applying proprietary fuzzy hash values that identified linked infrastructure through on-page content.
Our analysts were also able to map out associated infrastructure by analyzing the way that AnyDesk.exe is served as a file to the user. Our scans identified naming conventions contained within the file metadata, that linked the executable to a particular brand, and generated a traceable hash value.
Creating a behavioural fingerprint
By combining these two factors – on-page fuzzy hash values and executable metadata – we were able to create a unified Silent Push Web Scanner query that maps out AnyDesk phishing infrastructure across all the brands involved.*
After running the query, we noticed that all of the true positive results were hosted on two Russian ASNs:
- AS198953
- AS200593
This provided us with additional parameters to further narrow our Web Scanner search, and create a single behavioral fingerprint that only returns true positive domains engaged in past and present AnyDesk phishing activity.
*Please note that we are unable to share the specifics of each query in a public blog, for operational security reasons. For exact details of the Web Scanner parameters used, please contact [email protected]
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, that we used to track AnyDesk phishing activity, along with all the other threat campaigns covered in our other research blogs.
Click here to sign-up for a free account.
IOFAs
- 91.215.85.79
- 193.143.1.14
- anz-help[.]com
- anz-livechatsupport[.]com
- anzsupport-livechat[.]com
- avastcsw[.]com avastcv[.]com
- avastga[.]com avastnw[.]com
- avastpst[.]com avastsf[.]com
- avastsgp[.]com
- avastsp[.]com
- avastvx[.]com
- bankofirelandhelpportal[.]com
- bankofirelandonlinehelp[.]com
- barclays-online-support[.]com
- barclayswebhelp[.]com
- boi-chat[.]com
- boi-support[.]com
- boihelponline[.]com
- boionlinehelp[.]com
- cooponlinechat[.]com
- ezjay-krasivo[.]ru
- helpbusinessonline-boi[.]com
- hsbchelp[.]com
- hsbchelponline[.]com
- hsbcliveportal[.]com
- ledger-webapp[.]com
- ledgerhelponline[.]com
- ledgerhelpwithmydevice[.]com
- ledgeronlinehelp[.]com
- liveapp-support[.]com
- lloydsbankhelp[.]com
- natwestchat[.]com
- natwestchathelp[.]com
- natwestlivechathelp[.]com
- natwestonlinesupport[.]com
- remotesupport[.]help
- virginmoney-chat[.]com
- virginmoney-chatonline[.]com
- virginmoney-help[.]com
- virginmoney-online[.]com
- virginmoney-onlinechat[.]com
- virginmoneychatonline[.]com
- virginmoneylivehelp[.]com
- virginmoneyonlinechat[.]com
- viriginmoneychatonline[.]com
- wise-chatonline[.]com
- wisebanksupport[.]com


