Table of contents
- Summary
- What is ISO 27001:2022 Annex A Control 5.7?
- Why is ISO 27001:2022 Annex A Control 5.7 important for an organization’s security posture?
- Achieving 27001:2022 Annex A Control 5.7 using Silent Push Enterprise
- 1. Facilitating informed actions to minimize risk
- The three layers of threat intelligence
- 3. Threat intelligence characteristics
Summary
In this blog, we’ll explain how you can achieve ISO 27001:2022 Annex A Control 5.7 certification using a Silent Push Enterprise subscription, by receiving pre-scored, pre-enriched and pre-aggregated domain, IP and web content data at source.
Our platform is designed to fulfil each of the stipulations listed in ISO 27001:2022 Annex A Control 5.7, and provide you with compliant threat intelligence data out-of-the-box, that’s ingestible across your entire security stack, with no additional resource required to achieve full ISO adherence.
To access some of the features mentioned in this blog for free, register for our Community Edition here.
What is ISO 27001:2022 Annex A Control 5.7?
To safeguard information security, organizations need to proactively identify and assess potential cyber threats that are both specific and non-specific to their operation.
In practice, this involves gathering, analyzing, and interpreting data on cyber risks, via a practice known as threat intelligence.
ISO 27001:2022 Annex A Control 5.7 provides a structured framework that helps organizations understand their specific threat landscape and attack surface, enabling them to implement appropriate security measures and mitigate any potential damage that can be caused by a security incident, including:
- Ransomware
- Financial theft
- Data theft
- Reputational damage
- Operational disruption
Why is ISO 27001:2022 Annex A Control 5.7 important for an organization’s security posture?
Effective information security management involves obtaining a clear understanding of the threat landscape. ISO 27001 provides a strategic framework for mitigating risks by helping organizations identify and mitigate potential and realized attacks.
By leveraging ISO 27001 Annex A control 5.7, organizations can accurately assess their vulnerabilities and implement appropriate safeguards.
This allows security teams to develop robust DNS defenses, and incident response and recovery plans, while ensuring their overall security posture aligns with evolving threats.
Achieving 27001:2022 Annex A Control 5.7 using Silent Push Enterprise
Satisfying the conditions set out in ISO 27001:2022 Annex A Control 5.7 means obtaining an informed, real-time view of your intelligence streams, so that your organization’s security posture is as robust as it can be at any given point in time, and the impact of any incoming threats is minimized or negated entirely.
ISO 27001-compliant Indicators of Future Attack (IOFA)
Silent Push Enterprise provides organizations with enriched domain, IP and content-based IOFAs that reveal where an attack is coming from, rather than legacy intellgence sources that rely on point-in-time indicators of where an attack has been.
Powered by the world’s most expansive, accurate and timely DNS and web content scanning and aggregation engine, Silent Push allows you to achieve ISO 27001:2022 Annex A Control 5.7 objectives at source, by providing threat intelligence that is relevant, insightful, contextual and immediately actionable with zero manual intervention required.
Integration with security tools
Silent Push data is instantly transferable into your organization’s security risk management processes as finished, ISO 27001-compliant threat intelligence data, either as a raw data source or as a preventative measure that bolsters the automated defense capabilities of traditional security controls such as firewalls, anti-malware solutions, and intrusion detection systems.
ISO 27001:2022 Annex A Control 5.7 compatibility extends to the suite of SOAR, SIEM and IR tools that an organization uses to run their day-to-day security operation.
Our IOFA data can be ingested using an API surface that facilitates a range of native integrations – including Splunk SOAR, Tines, Torq and ThreatConnect – that maintain ISO compliance throughout your security stack, wherever Silent Push data is utilized.
1. Facilitating informed actions to minimize risk
ISO 27001:2022 Annex A Control 5.7 places an emphasis on organizations performing “informed” actions on threat intelligence data, in order to minimize risk.
On a basic level, this requires threat intelligence data to be delivered with sufficient context, so that security automation processes are able to act instantly, and with greater accuracy, in order to prevent emerging attacks.
You can use Silent Push to automate data collection and analysis across different toolsets, and access pre-enriched threat intelligence that requires zero additional resources to convert threat intelligence into ISO compliant, actionable data.
Silent Push applies 100+ enrichment categories to each individual domain and IPv4/6 address we scan.
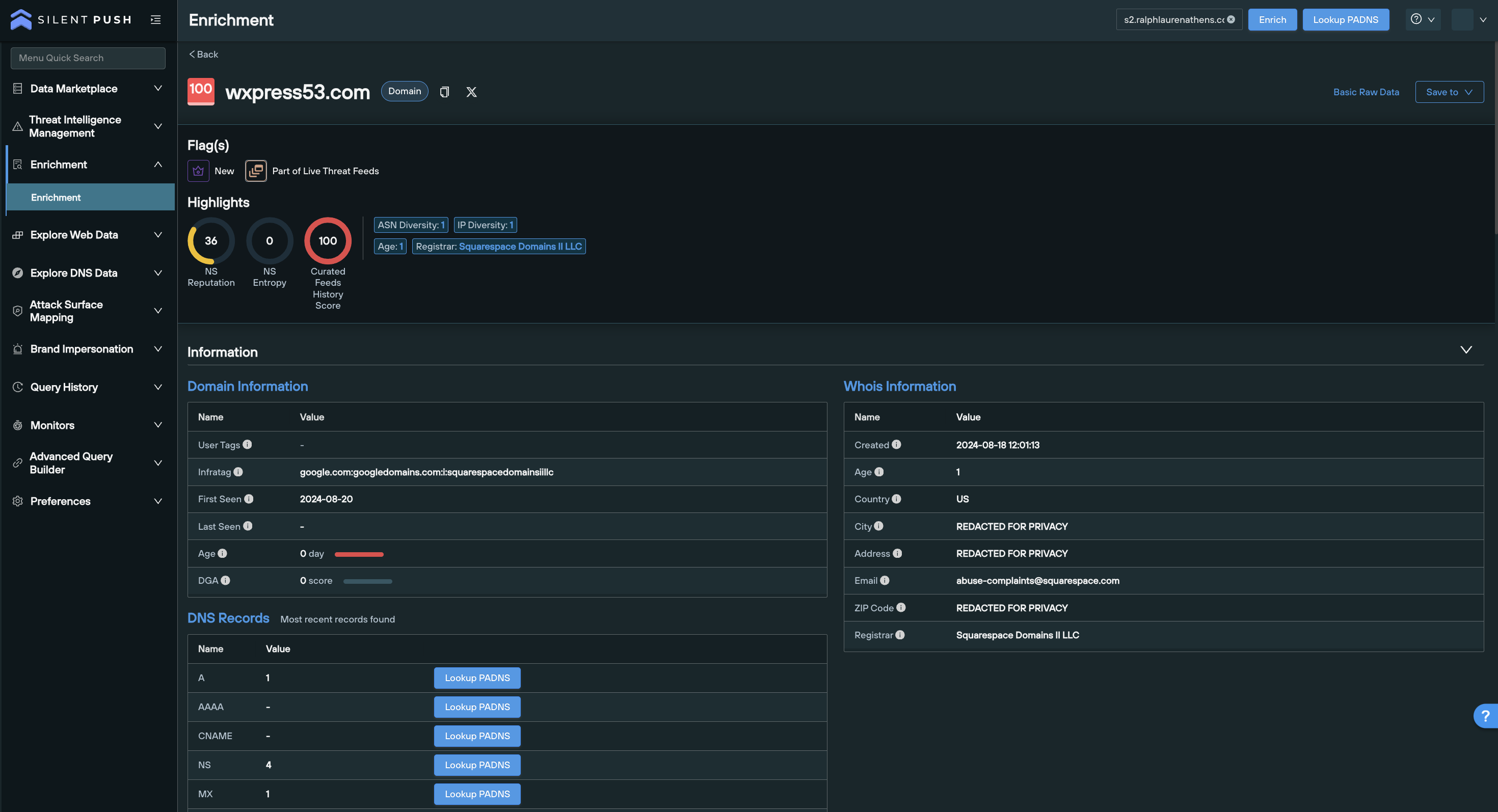
Websites, ASNs, nameservers and infrastructure clusters are scored, tagged, categorized and delivered into your stack with a wealth of supporting information that removes the need for security teams to spend countless hours turning intelligence data into compliant lists of domains and IPs.
This constant automated cycle of scanning, aggregation and delivery allows for instant detection of linked infrastructure related to your organizational attack surface and supply chain operation, without the need for extensive secondary analysis.
The three layers of threat intelligence
ISO 27001:2022 Annex A Control 5.7 asks organizations to categorize intelligence into three distinct layers, all of which should be considered when forming an information security posture.
1.1 Strategic threat intelligence
“Strategic” threat intelligence provides a broad overview of emerging threats, including the types of adversaries, region-specific factors, and attacks they employ.
Silent Push Enterprise subscribers have access to threat-specific TLP Amber reports, compiled by Silent Push Threat Analysts, that outline the characteristics of APT-related attacks, and how different attacker motives can be counteracted using targeted queries and scans, including links to relevant datasets.
IOFAs are tagged at source with characteristics that immediately identify a piece of infrastructure – or groups of related infrastructure – as belonging to a particular adversary, campaign, or geographic region (including state-sponsored activities).
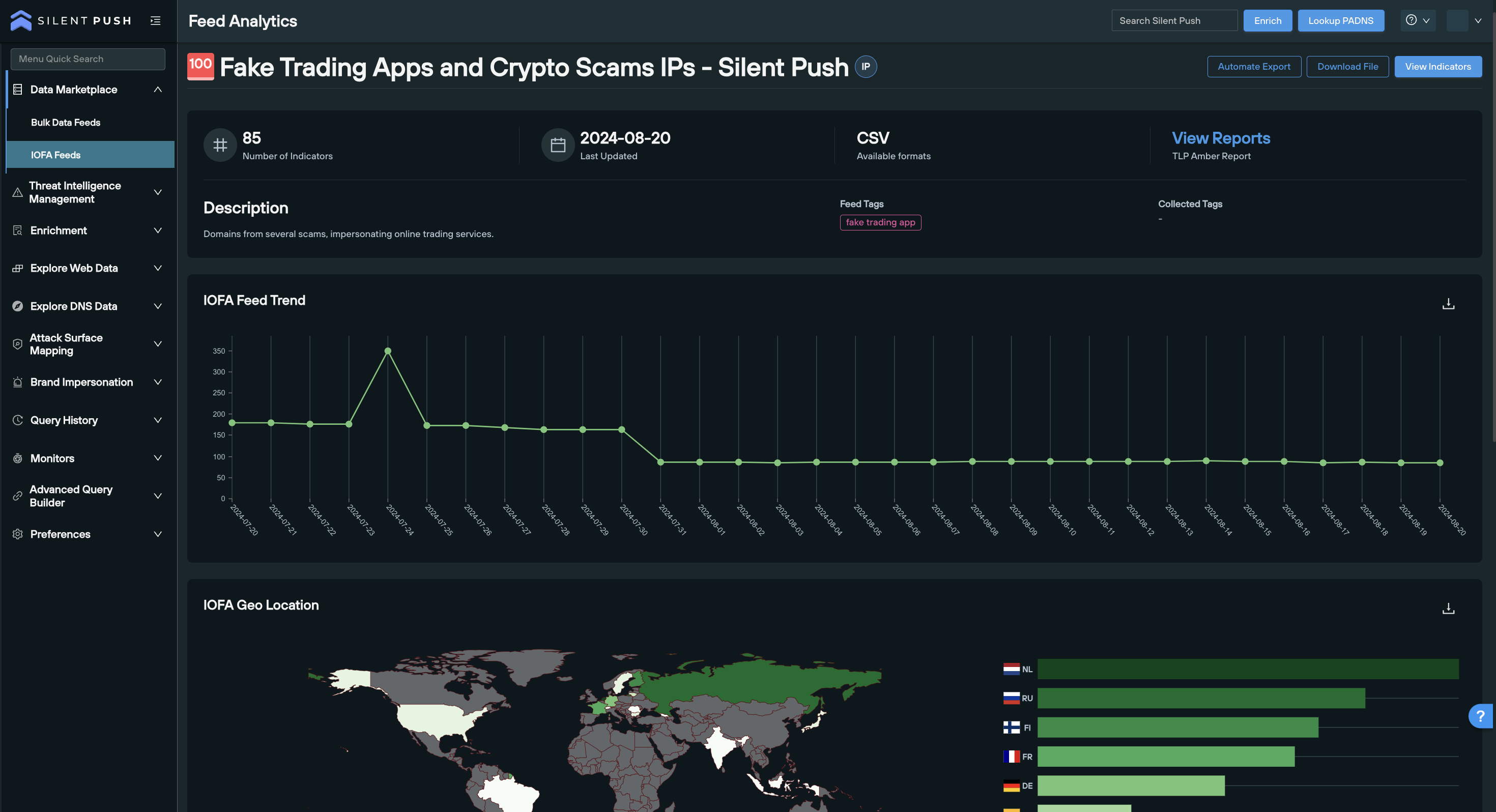
This information is identified on the back-end of the platform before it’s delivered into your security stack, providing you with an instantly compliant, automated, actionable intelligence stream delivered out-of-the-box.
1.2 Tactical threat intelligence
“Tactical” threat intelligence delves deeper into the specific techniques, tools and procedures (TTPs) used by attackers.
Silent Push provides timely, accurate and complete threat intelligence datasets that are uniquely designed to identify, track and monitor emerging TTPs and pre-weaponized infrastructure using a combination of threat-specific Early Detection Feeds, ranked domain and IP data,
Threat actors assemble their infrastructure using a series of traceable patterns. Owning and controlling our own data allows us to add an infinite amount of context to each observable that we collect, and where there are patterns to be found, make those links across the global IP space and darkweb, to produce actionable intelligence.
1.3 Operational threat intelligence
“Operational” threat intelligence offers granular insight into ongoing attacks,
ISO 27001:2022 Annex A Control 5.7 requires threat intelligence to be delivered in the form of actionable technical indicators that aid in detection and response.
We conduct billions of daily DNS and on-page lookups across the IPv4 and IPv6 spaces, and darkweb, and feed this data into the platform within self-contained spaces that are designed to work in harmony with one another, to produce instant, automated results.
The UI features a range of one-click pivot points that gives your teams access to all the intelligence they require to map out attacker infrastructure, regardless of how it’s being obfuscated, where it’s hosted, or what form it’s taking.
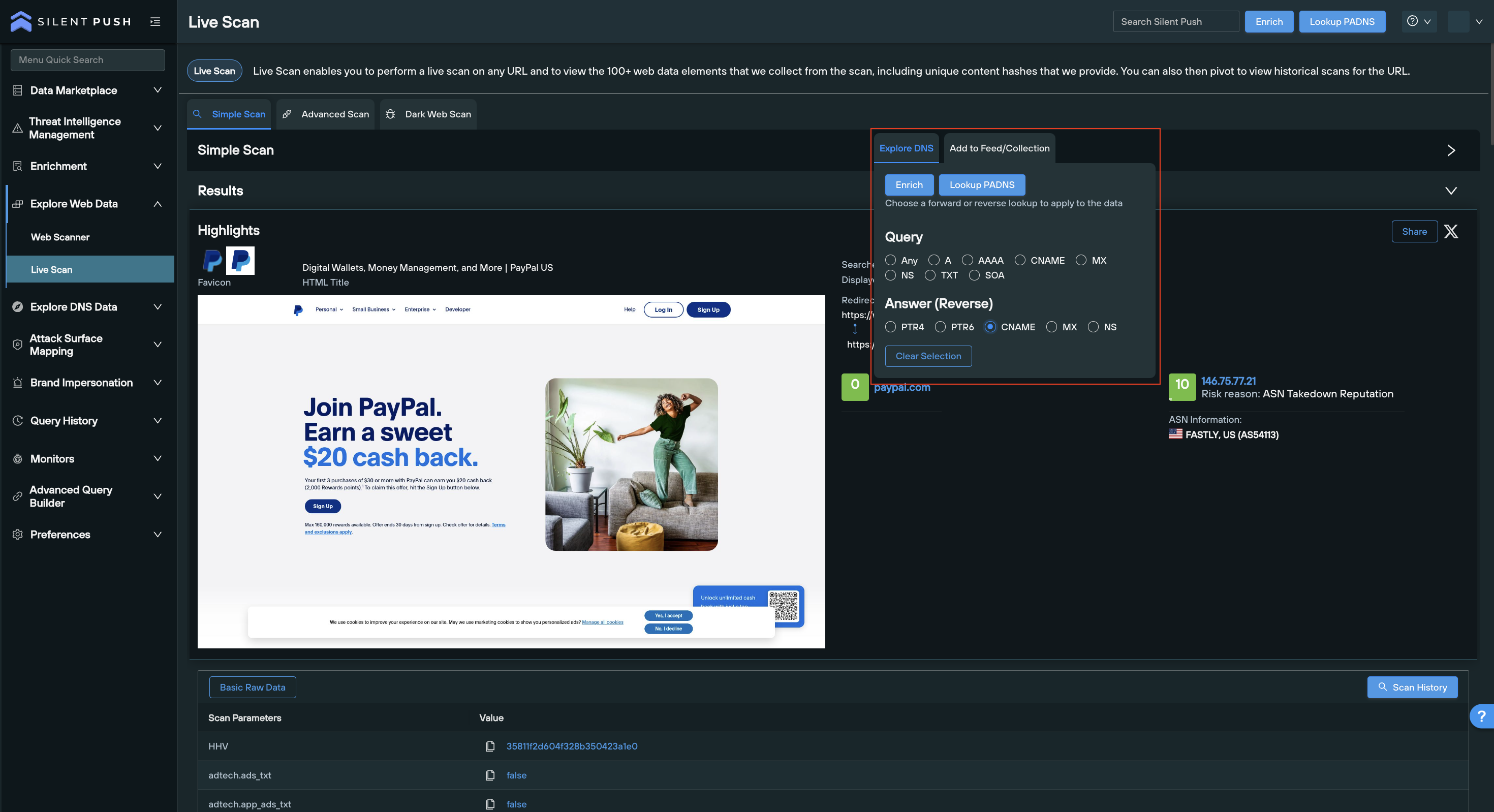
3. Threat intelligence characteristics
ISO 27001:2022 Annex A Control 5.7 stipulates that threat intelligence should be:
3.1 Relevant
Threat intelligence maintains “relevancy” when it’s uniquely tailored to protect the organization that’s using it.
Silent Push Enterprise allows you to execute highly-detailed, granular scans and queries which cut out the noise, eliminate false positives at source, and satisfy ISO compliance protocols by only delivering intelligence that is relevant to your organization, or threat hunting activities.
Proprietary features such as Filter Profiles, scanning emulation, custom threat feeds, and organizational asset lists deliver pre-filtered, compliant datasets at the click of a button, that cater to a multitude of internal job roles.
3.2 Insightful
Insightful intelligence provides an organization with an accurate and detailed understanding of any given threat landscape.
To map out attacker infrastructure, Silent Push collects and delivers information across 100+ domain and IP enrichment categories, that satisfy the compliance need for insightful intelligence, and offers additional insight into an observable’s presence on the Internet, including:
- Risk and reputation scores
- Web content (headers, hash values, on-page data)
- Certificates
- Geographic location
- Passive DNS data
3.3 Contextual
Threat intelligence benefits from context when the information provided is based on when events occurred, where they occured, and how they relate to previous events.
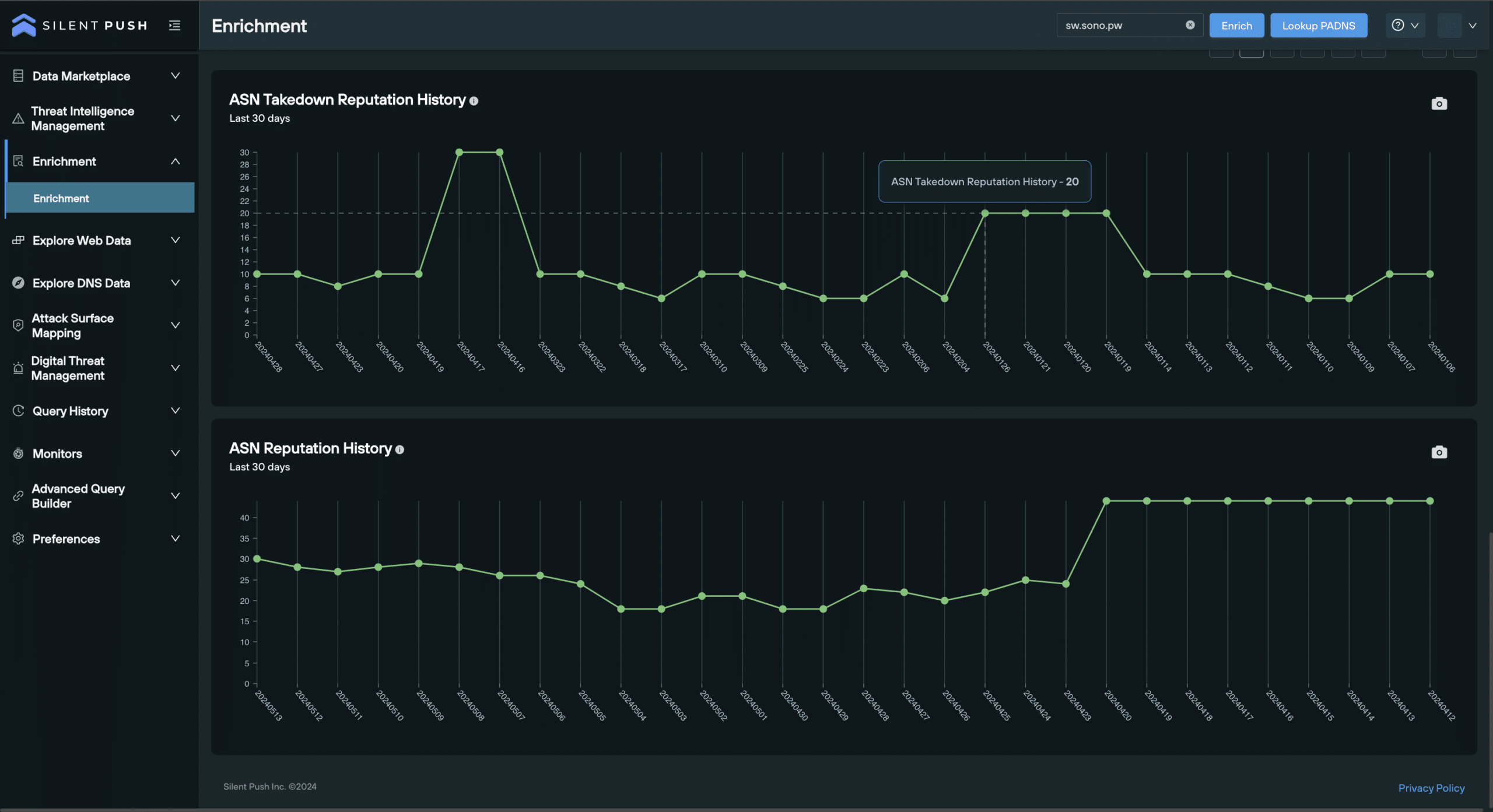
All of our data is delivered timestamped, with the underlying infrastructure associated with a single piece of data – e.g. nameservers, ASNs, and hosting providers – clearly accessible, so that security teams are able to track a domain or IP’s journey across the clearnet and darkweb, including all associated reputation scores.
3.4 Actionable
A piece of intelligence data is considered actionable if it can be acted upon quickly, and efficiently, by the individuals tasked with analyzing it.
Silent Push is “data independent”, meaning that we don’t rely on other vendors or third parties to provide us with DNS or web content data.
This enables us to deliver compliant intelligence with a range of variables built-in, in such a way that makes any one data point pivotable from another across multiple distinct threat intelligence datasets.
Request a demo
Get in touch today, and let us show you how we can help your organization achieve ISO 27001:2022 Annex A Control 5.7 compliance using a Silent Push Enterprise subscription.
Register for Community Edition
Silent Push Community Edition is a free threat hunting and cyber defense platform used by researchers, defenders and threat hunters, featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.



