Google Advertising Out to Lunch? Simple Pivots Catch an Ongoing Malvertising Campaign Hiding in Plain Sight
Key Findings
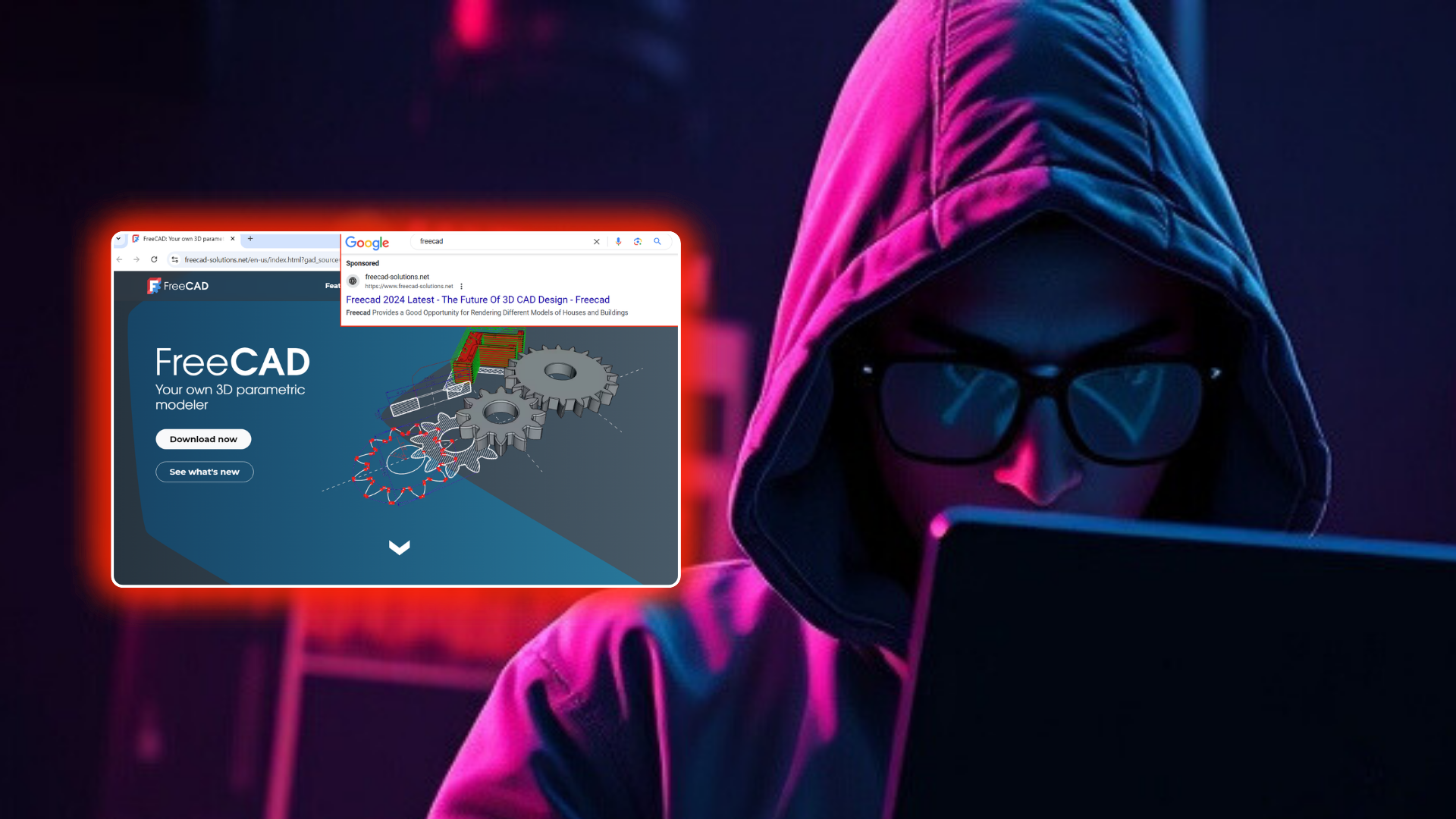
- Silent Push Threat Analysts have caught a threat actor’s ongoing series of malvertising campaigns blatantly abusing Google Search ads to target graphic design professionals.
- We documented at least 10 malvertising campaigns hosted exclusively on two IP addresses: 185.11.61[.]243 and 185.147.124[.]110.
- Together with our research partners, we found that the sites from the two IP addresses were being launched in Google Search advertising campaigns, and all of them led to malicious downloads.
Executive Summary
When it comes to tracking threat actors, Silent Push Threat Analysts understand this process can be complex, and it’s not uncommon for certain organizations to track one threat actor more effectively than others. These types of cases generally occur due to gaps in visibility or a lack of access to certain intelligence.
Conducting a simple process to look up which IP address is hosting a domain and then investigating that IP address for other similar domains, however, is not a complex task. It’s a beginner pivot, something any junior threat analyst can accomplish.
And yet, it appears that the Google advertising team is not even going that far to stop a series of malvertising campaigns that have been going on for nearly a month, targeting graphic design professionals.
Domains have been launched day after day, week after week, since at least November 13, 2024, for malvertising campaigns hosted on two dedicated IP addresses: 185.11.61[.]243 and 185.147.124[.]110.
Sites stemming from these two IP ranges are being launched in Google Search advertising campaigns, and all lead to a variety of malicious downloads, according to our research partners.
In the last month, Silent Push Threat Analysts have documented at least ten distinct malvertising campaigns, launched via Google ads, that make use of domains mapped to one of these two IP ranges.
Sign up for a free Silent Push Community account
Register for our free Community Edition to use all of the tools and queries mentioned in this blog.
Dedicated Ranges Clearly Owned by a Single Threat Actor
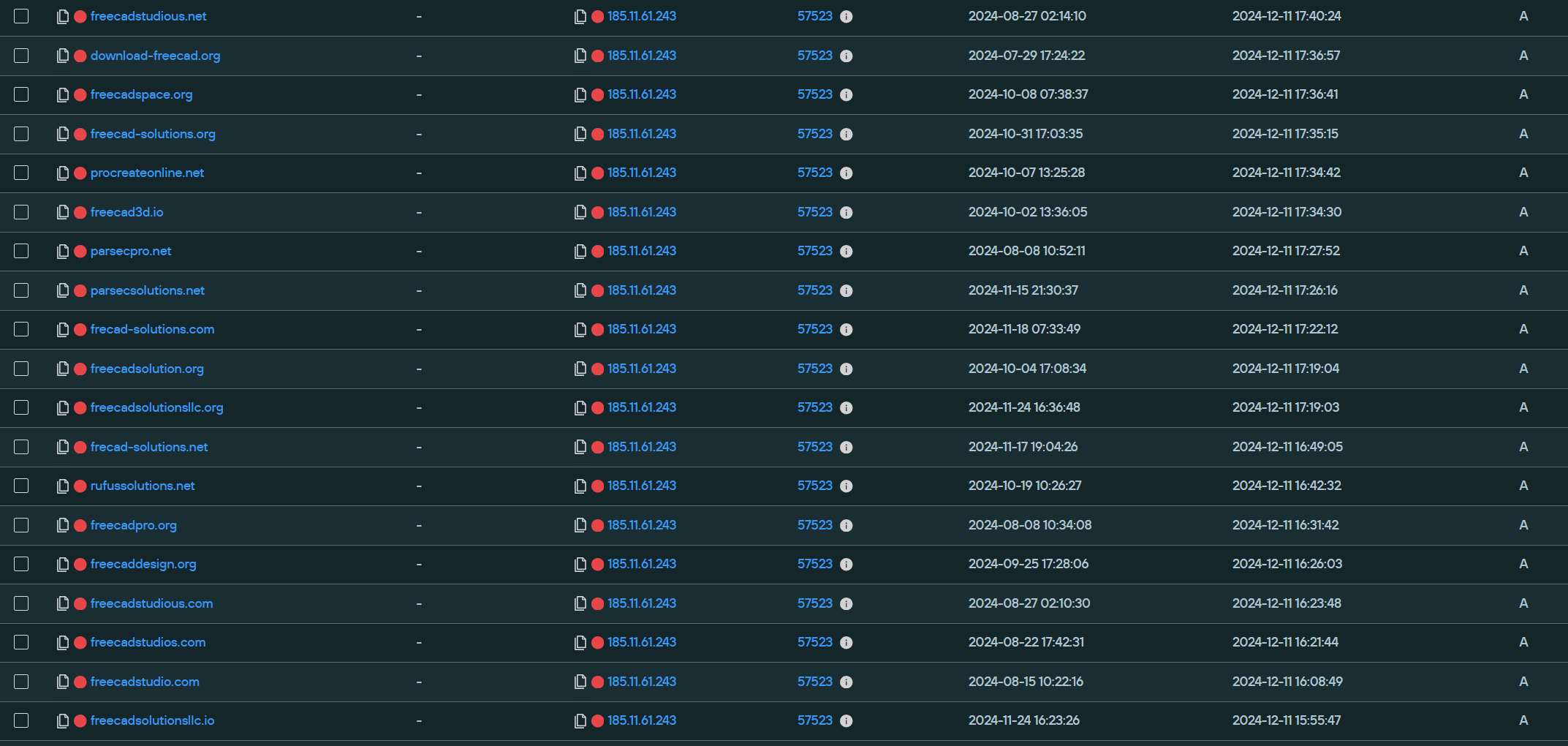
Starting with the first IP address 185.11.61[.]243, at the time of this writing, 109 unique domains were mapped to it, all seemingly for this graphic design/CAD malvertising campaign. The first domains were added on July 29, 2024, and the most recent domains mapped to it were from November 25, 2024:
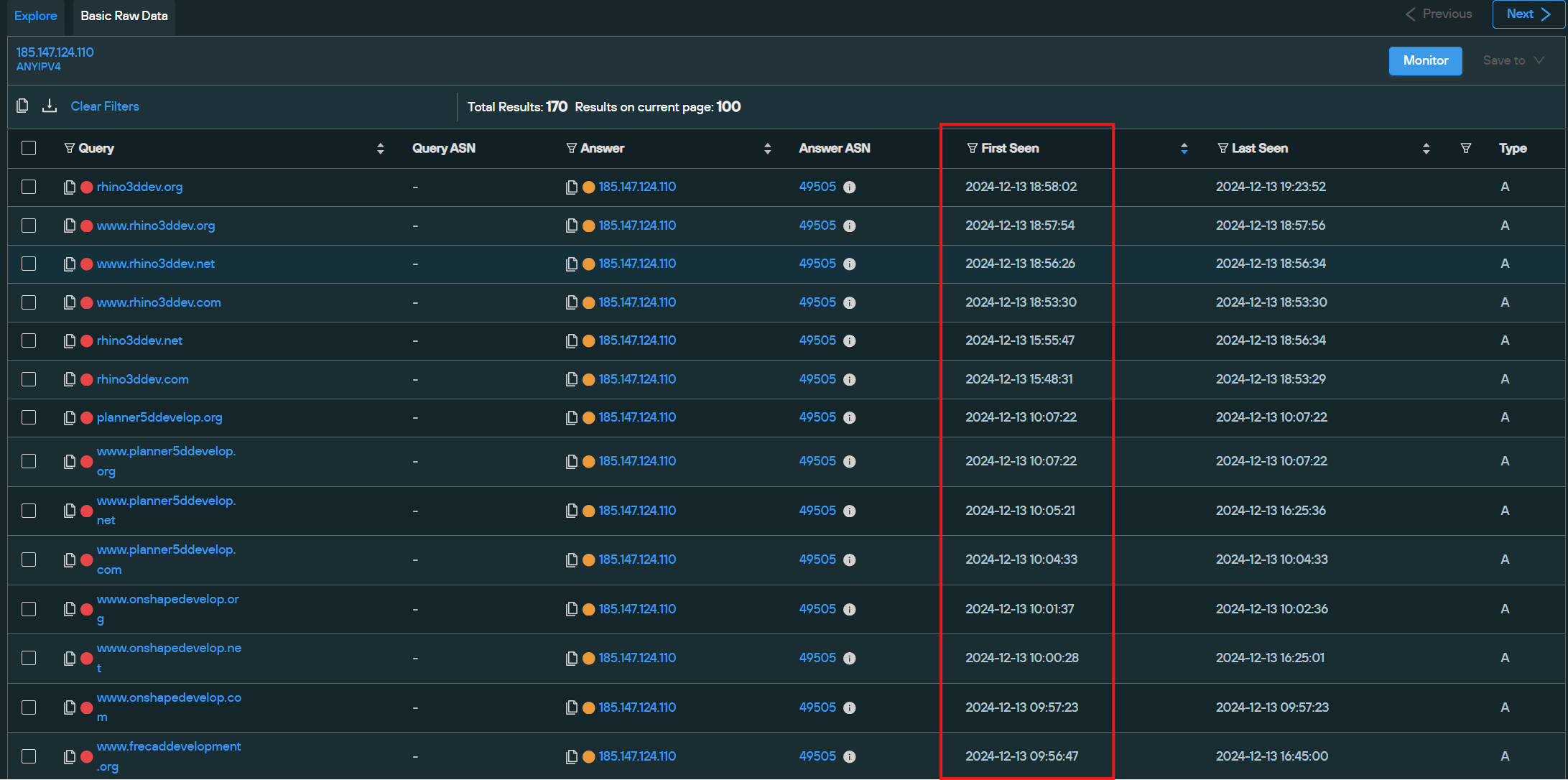
Meanwhile, 185.147.124[.]110 currently has 85 unique domains mapped to it, with the first domains added on November 25, 2024, and the newest domains mapped as recently as December 13, 2024:
Breakdown of Graphic Design Malvertising Campaigns on Google Search
On November 13, 2024, the malvertising campaign first launched with frecadsolutions[.]com, hosted on 185.11.61[.]243 since November 6, 2024. From here, we noticed that the IP address hosted dozens of other similar domains and assumed they could be for similar malvertising purposes.
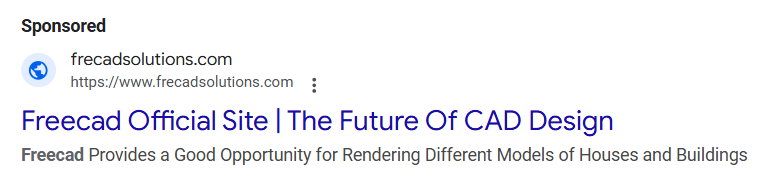
On November 14, 2024, a malvertising campaign was launched using frecadsolutions[.]cc (note the subtle TLD difference of “cc” vs. “com”), which had also been hosted on 185.11.61[.]243 since November 6, 2024. This made use of Bitbucket for its malicious download, which is normally a legitimate file hosting site.
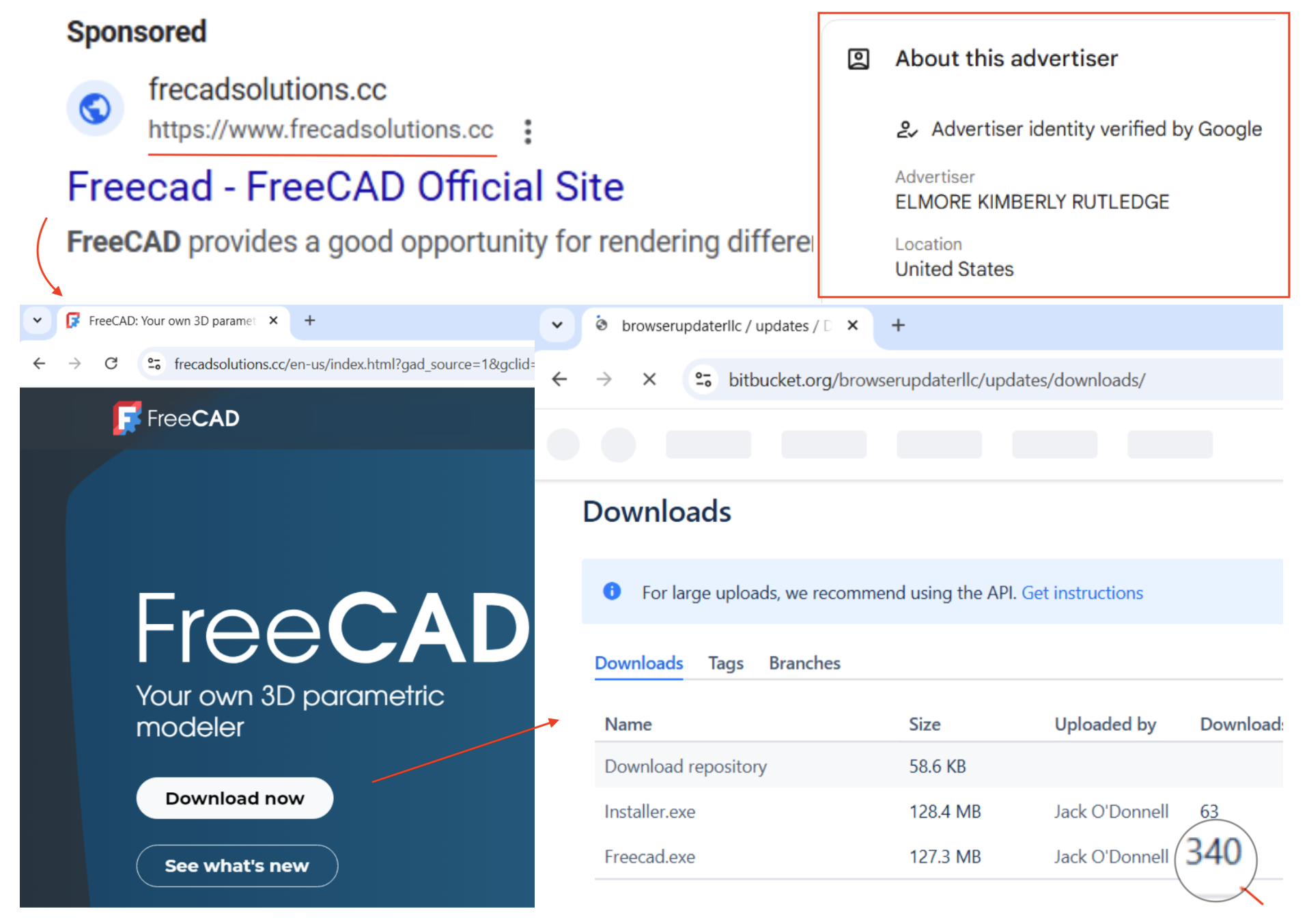
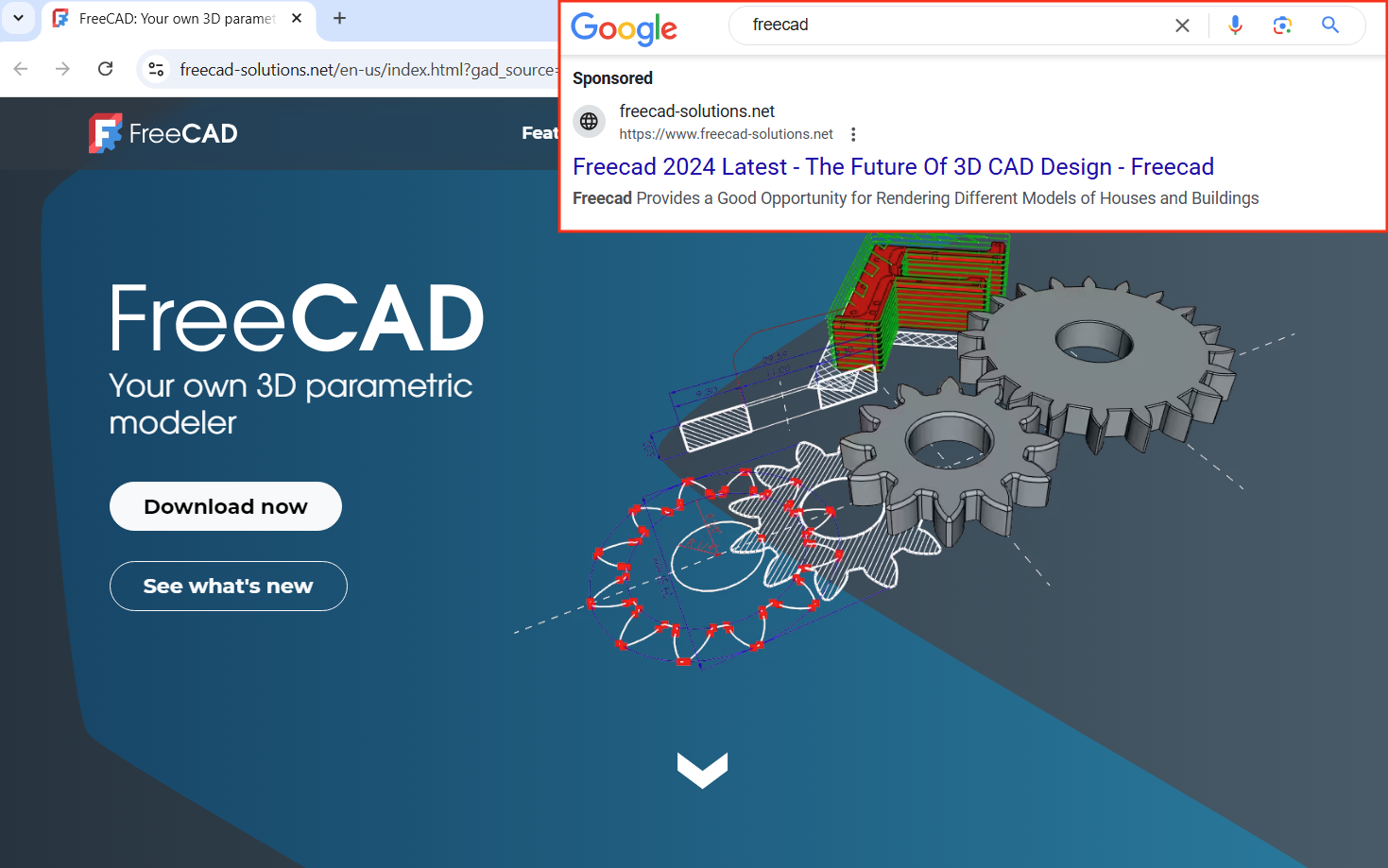
On November 26, 2024, a malvertising campaign was launched on freecad-solutions[.]net, which had been hosted on 185.11.61[.]243 from November 1, 2024 to November 26, 2024, and then moved to 185.147.124[.]110, where it has since remained.
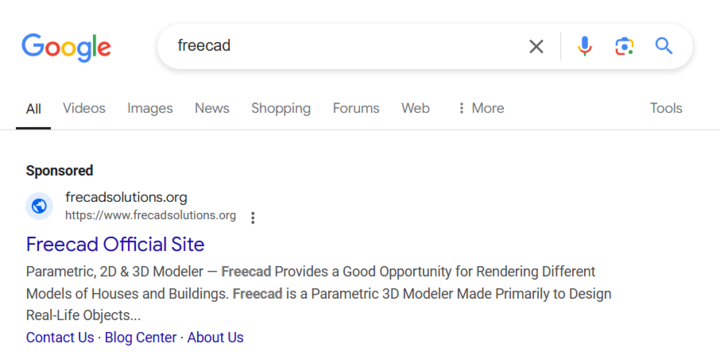
On November 27, 2024, a malvertising campaign was launched on frecadsolutions[.]org, which had been hosted on 185.11.61[.]243 from November 6, 2024 to November 26, 2024, and then moved to 185.147.124[.]110, where it has since remained.
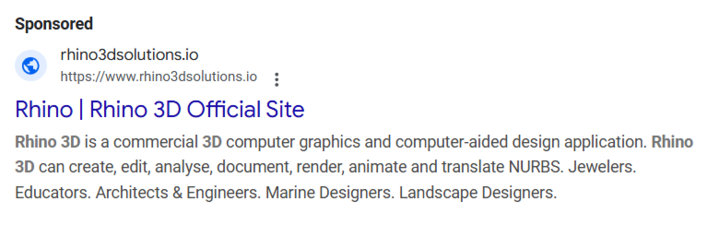
On November 27, 2024, a malvertising campaign was launched with rhino3dsolutions[.]io, which had been hosted on 185.11.61[.]243 from November 17, 2024, to November 26, 2024, and then on 185.147.124[.]110 from November 26, 2024, to present.
On November 27, 2024, a malvertising campaign was launched with rhino3dsolutions[.]org, which had been hosted on 185.11.61[.]243 from November 18, 2024, to November 26, 2024, and then on 185.147.124[.]110 from November 27, 2024, to present.
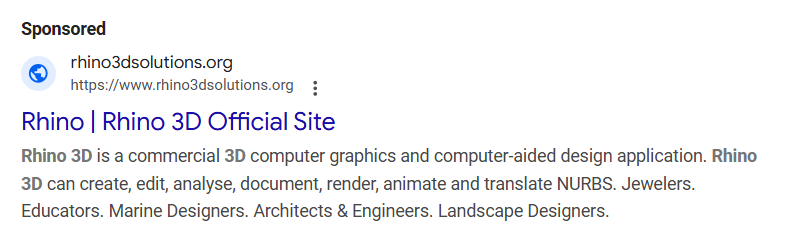
On November 27, 2024, a malvertising campaign was launched with rhino3dsolutions[.]net, which had been hosted on 185.11.61[.]243 from November 17, 2024, to November 26, 2024, and then on 185.147.124[.]110 from November 26, 2024 to present.
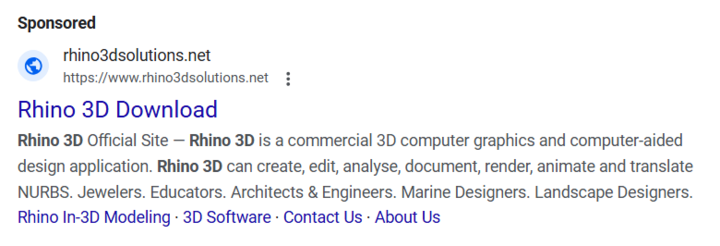
On December 5, 2024, a malvertising campaign was launched with planner5design[.]net, which had been hosted on 185.147.124[.]110 from December 1, 2024 to December 6, 2024.
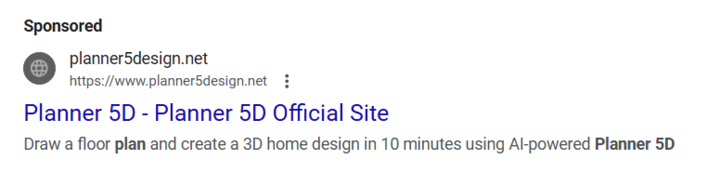
On December 9, 2024, a malvertising campaign was launched with onshape3d[.]org, which had been hosted on 185.147.124[.]110 from December 1, 2024, to present.
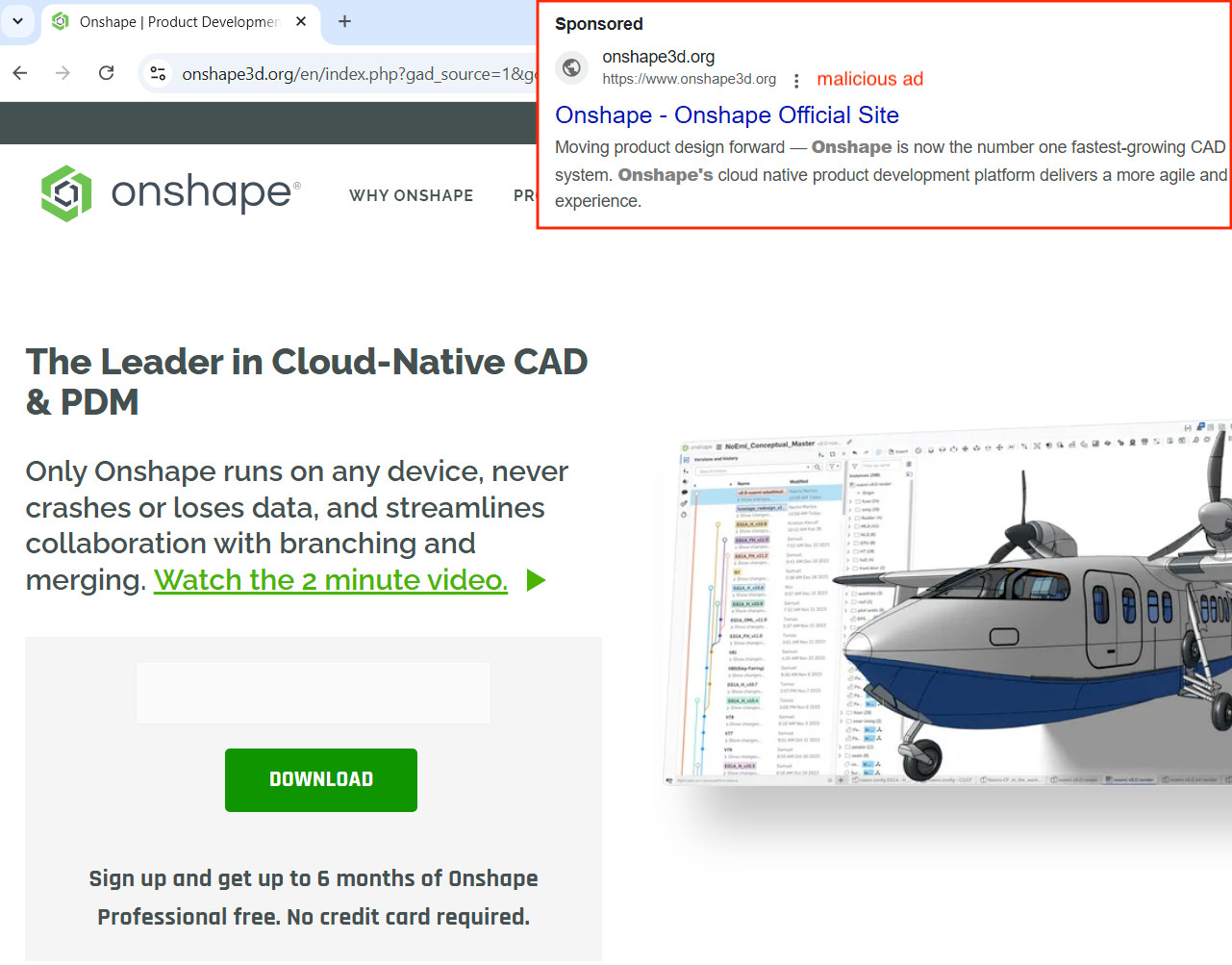
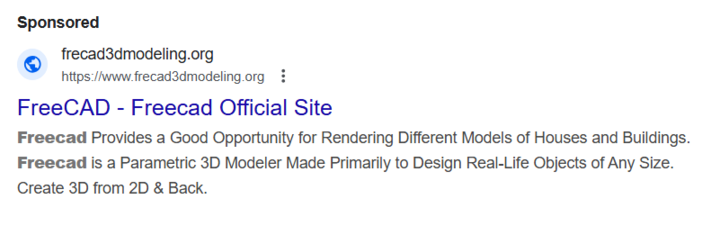
On December 10, 2024, a malvertising campaign was launched with frecad3dmodeling[.]org that had been hosted on 185.147.124[.]110 from December 8, 2024, to present.
Special Thanks to Our Research Partners
Silent Push analysts would like to thank the collaboration with our research partners who initially highlighted these malvertising domains. While we don’t have complete visibility into these malvertising efforts and don’t currently have any malware analysis to share just yet, we certainly have the data to pivot into their hosting infrastructure. By partnering together in trusted research-sharing circles, we’re able to find and highlight complex threats such as these – and for those efforts, we salute you.
If you are interested in joining a research-sharing effort or simply have interesting threats to share that you would like our help with, please feel free to reach out to us at info@silentpush[.]com.
Mitigation
Silent Push believes all malvertising domains pose significant risks, especially to corporate environments.
Our analysts have constructed a Silent Push IOFA Feed that provides a list of Indicators of Future Attack domains focused on malvertising, along with an IOFA Feed containing suspect Malvertising IPs.
Silent Push IOFA Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push Web Scanner and Live Scan.
Click here to sign up for a free account.
Indicators of Future Attacks (IOFAs)
Here is a sample list of IOFAs – our full list is available for enterprise users. Silent Push Enterprise clients have access to a domain and IP feed containing this malvertising infrastructure.
- 185.147.124[.]110
- 185.11.61[.]243
- calibrebook[.]com
- calibrebook[.]net
- frecad3dmodeling[.]net
- frecad3dmodeling[.]org
- frecad3dsolutions[.]com
- frecad3d-solutions[.]com
- frecad-3dsolutions[.]com
- frecad3d-solutions[.]net
- frecad-3dsolutions[.]net
- frecad3dsolutions[.]org
- frecad-3dsolutions[.]org
- frecaddevelop[.]com
- frecaddevelop[.]org
- frecaddevelopment[.]com
- frecaddevelopment[.]net
- frecaddevelopment[.]org
- frecadmodeling[.]com
- frecadmodeling[.]net
- frecadmodeling[.]org
- frecadsolution[.]net
- frecadsolutions[.]cc
- frecadsolutions[.]org
- frecad-solutions[.]org
- freecad3dsolution[.]net
- freecad3dsolutions[.]com
- freecadblog[.]com
- freecadblog[.]io
- freecadblog[.]net
- freecadblogs[.]net
- freecad-solutions[.]net
- freecadsolutionsllc[.]com
- freeecadmodeling[.]net
- onshape3d[.]com
- onshape3d[.]org
- onshapedev[.]net
- onshapedevelop[.]com
- onshapedevelop[.]net
- onshapedevelop[.]org
- planner5ddevelop[.]com
- planner5ddevelop[.]net
- planner5design[.]com
- planner5design[.]net
- planner5designs[.]com
- planner5designs[.]org
- recad3dsolutions[.]org
- rhino3dsolutions[.]io
- rhino3dsolutions[.]net
- rhino3dsolutions[.]org
- rhinoceros-3d[.]com


