Key Findings
- Silent Push Threat Analysts began tracking a campaign we are calling “Payroll Pirates” for their use of a payroll redirection phishing scam after receiving a helpful tip from a research-sharing organization.
- Our team observed the following patterns used by this threat actor group:
- Buying search ads with brand keywords to return sponsored phishing websites at the top of search results.
- Website builders to rapidly create domains for the campaign.
- Regular use of phishing sites behind an /online directory – and efforts to match the directory structure of targeted corporate entities.
Executive Summary
Silent Push Threat Analysts have been hunting a malicious threat actor group we’re calling “Payroll Pirates. ” The group is responsible for an ongoing human resources (HR) payroll redirection phishing scam against numerous organizations’ employees. Workday customers have been a primary target at high-profile victim companies, many of which we have redacted for privacy.
While many of the HR phishing websites we are tracking are currently down, in part due to our outreach efforts, we’re creating these feeds and sharing this research due to the scale and sophistication of the effort and the likelihood that it will continue. Our threat research team continues to monitor this campaign, alerting our clients and their organizations to help protect them from costly attacks by these nefarious threat actors.
Silent Push Enterprise users have access to two dedicated IOFA Feeds containing all the true positive domains and IPs we gathered during our research.
For operational security reasons, we are unable to share the exact specifics of each query and pivots utilized. Silent Push Enterprise customers have access to a dedicated Payroll Pirates TLP: Amber report, which contains the relevant data types and pivot points we used to track the infrastructure referenced in this blog.
Sign up for Community Edition
Silent Push Community Edition is a free threat hunting, DNS, and scanning toolkit that contains all the queries and lookups we used to locate and traverse the infrastructure included in this blog.
Background
Silent Push Threat Analysts have been hunting a malicious threat actor group we’re calling “Payroll Pirates,” responsible for an ongoing malicious campaign targeting companies’ employees with human resources (HR) phishing scams to carry out payroll redirects. We have identified hundreds of domains primarily focused on Workday users and high-profile organizations, including the California Employment Development Department (EDD), Kaiser Permanente, Macy’s, New York Life, and Roche.
The threat actors have been utilizing malicious search advertising campaigns with sponsored phishing websites and spoofed HR pages via Google to lure unsuspecting victims into providing access to their employee portals. Armed with additional credential information, such as social security numbers likely obtained from underground forums, once the scammers get into an employee’s portal account, they change the individual’s banking information to redirect funds to a fraudulent bank account, which the threat actors control.
Website builders, including Leadpages, Mobirise, Wix, and potentially others, are being used to create domains in the campaign to aid in rapid setup. Our threat research team found dedicated IP ranges connected to entirely new pools of infrastructure and observed tactical shifts aligning with specific timeframes. The phishing content is typically hosted among the threat actor’s preferred registrars, Dynadot, Porkbun, and Namecheap.
This threat was originally shared with Silent Push analysts from a research-sharing organization. Malwarebytes has written about this threat publicly and how it targeted Lowes by using a custom directory structure to match the real Lowes HR portal page structure and further increase the credibility of the phishing site. We haven’t seen this same behavior widely, but we believe some organizations could see custom directories and page structures associated with their phishing kits.

Initial Intelligence Gathering
Some of the phishing sites built with Mobirise have domains that appear to be set up for phishing corporate targets with titles like “Welcome to Roche Login” – but without a live phishing page.

The site mentalroccehget[.]com has the same properties as the known malicious result website andandorconnect[.]com, and its host (Cloudflare) and provider (Google) are also identical.
Unemployment Portal Phishing
Using the same host, among other values, as both andandorconnect[.]com and mentalroccehget[.]com, we found a new flavor of their phishing kit located at guideulca[.]com targeting an unemployment portal in California.

Analyzing potential phishing sites
When analyzing a potential phishing site, myinstitehr[.]com, we noticed strange language on the homepage: “These programs offer support for personal and professional challenges, providing resources for mental health, financial advice, and other forms of assistance.” This same language can be found on macyinsidehr[.]com, which also hosts a phishing page.
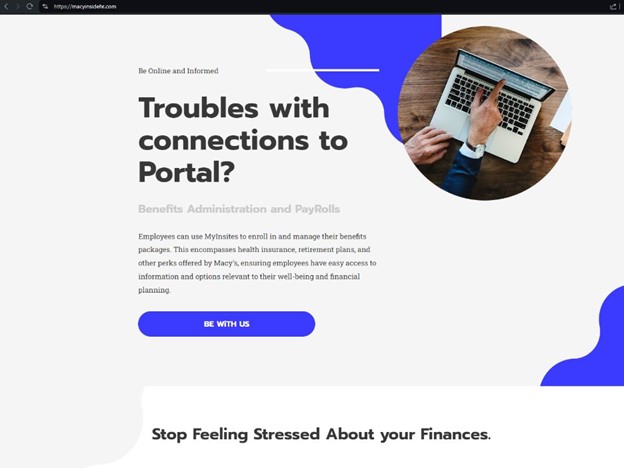
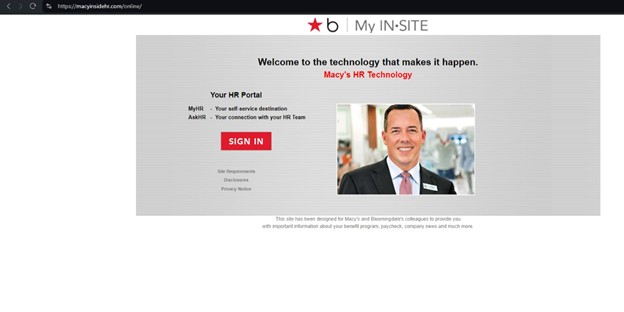
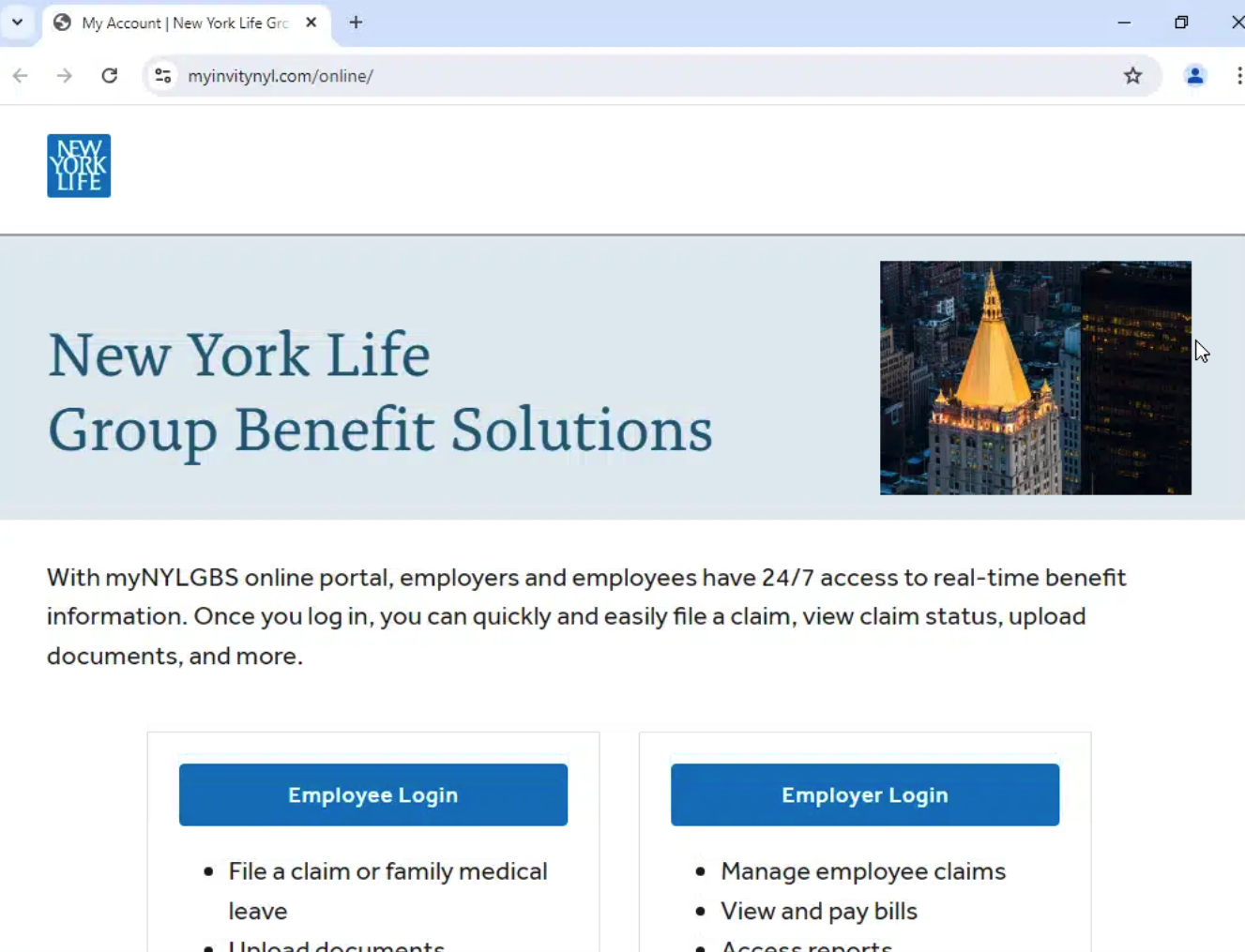
Examining an active phishing page targeting New York Life, we found it was hosted via Leadpages, another website builder.
Searching further returned more domains related to this campaign:
New domains found:
- hrocneddiwserv[.]com
- myhrkp[.]website
- myidmlogin[.]world
- myidmportal[.]site
- mypayaramark[.]online
Starting with the new domains: hrocneddiwserv[.]com, myhrkp[.]website, myidmlogin[.]world, myidmportal[.]site, and mypayaramark[.]online, we saw that a couple of them had the HTML title “MyPay” before changing it to “hrkp.”
Repeating the search, but this time with the filter “MyPay” returned very interesting results:
- bambookjo[.]world
- essmyykroogeerinfo[.]com
- homedepotwithease[.]com
- hraccesskalser[.]com
- hrocneddiwserv[.]com
- myescrochjesikurl[.]com
- mygbsnuyinow[.]com
- myidmlogin[.]world
- myinfominkogrerstat[.]com
- etc.
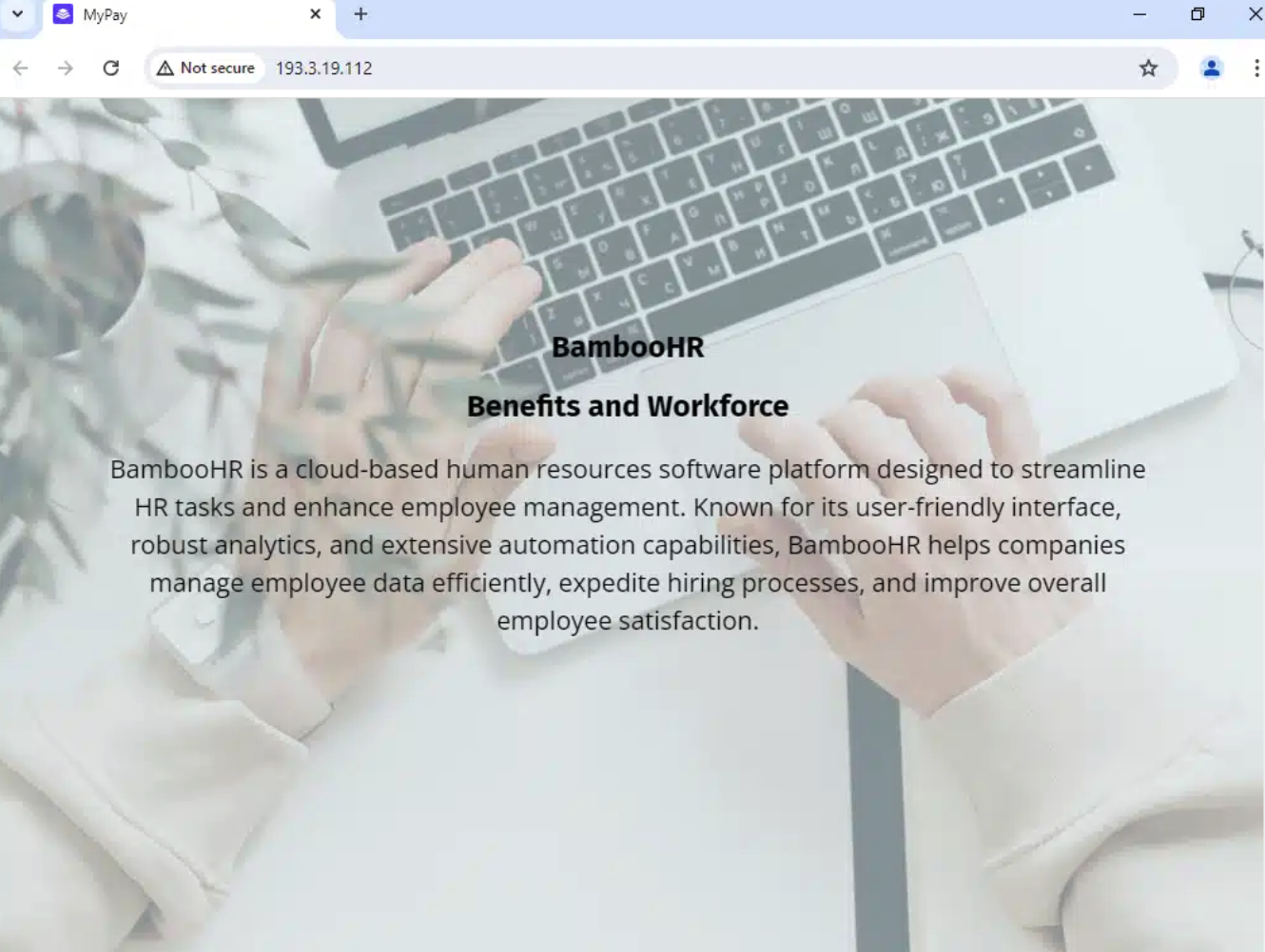
From the “MyPay” filter, the most interesting part lies within one particular result. Not a domain, but an IP address: 193.3.19[.]112 on AS50340(SELECTEL-MSK, RU).
Direct access to the IP showed an HR-themed page that mentions “BambooHR” (example below).
Pivot: Dedicated IP Range
This IP address, 193.3.19[.]112, which hosted the BambooHR content on the root directory path, had a new domain mapped to it recently: myrocshe[.]com – which also had a phishing page targeting Roche:
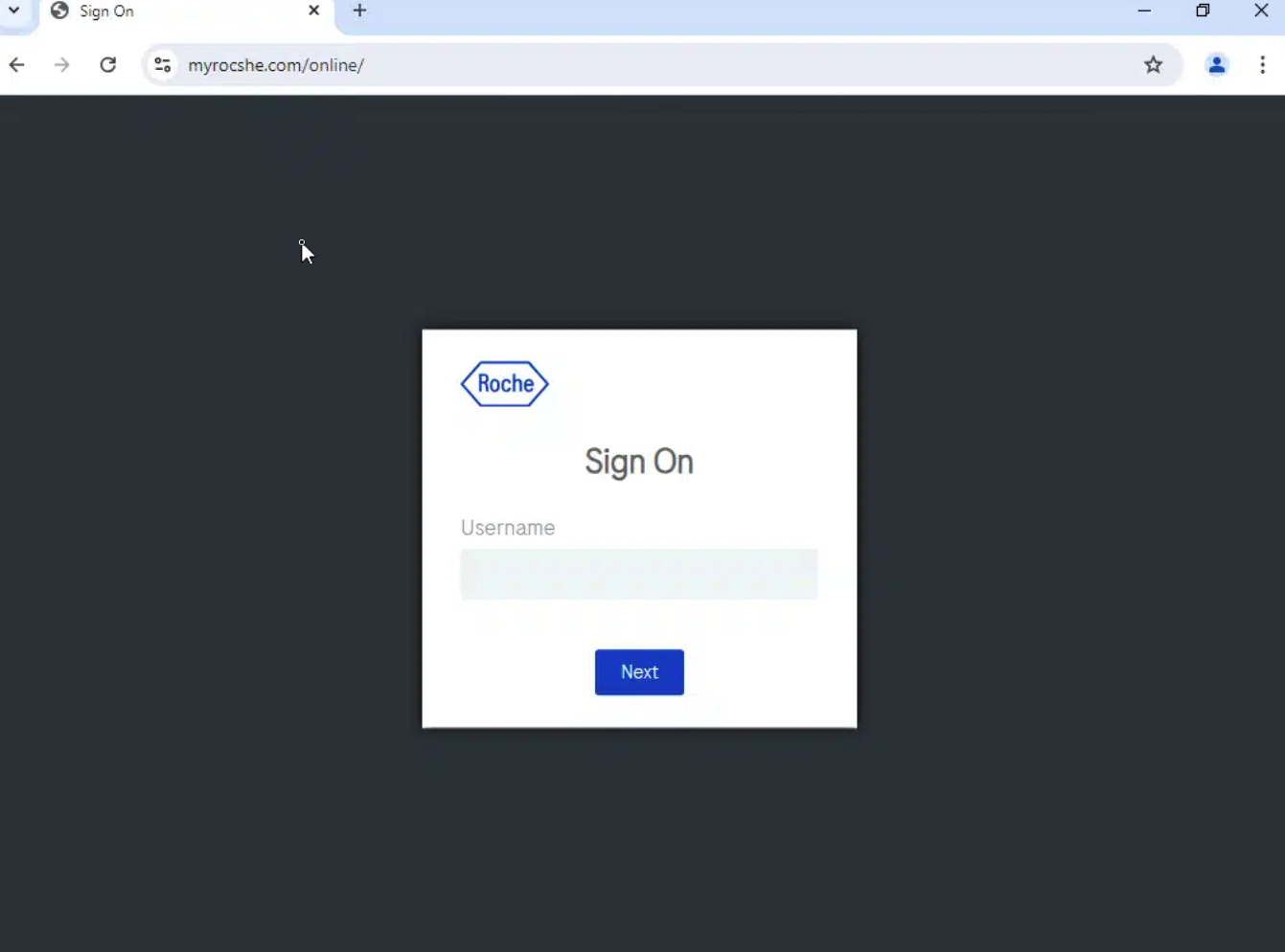
The phishing site targeting Roche was registered on Dynadot the week of August 11, 2024, and Silent Push was able to catch it before the threat actors had time to proxy it through Cloudflare.
Analyzing historical scans featuring this IP address, 193.3.19[.]112, we see the threat actor was running an Unemployment Benefits scam targeting Kroger Grocery before switching to payroll phishing and that they seem to have changed to Mobirise templates after the second quarter of 2024.

Phishing Content on the Root
The majority of the domains found so far only hosted the phishing page on the /online path, but we noticed when we rescanned hraccesskalser[.]com, it returned a poorly crafted Kaiser phishing page:
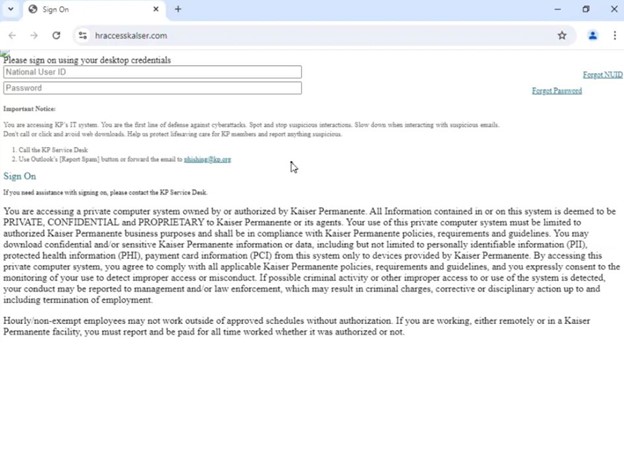
An additional proprietary fingerprint used by these threat actors was queried, returning a large pool of similar results. We haven’t definitively proven these bank phishing sites are directly connected to the payroll redirection scheme yet, but they are clearly malicious and potentially created by the same threat actors.
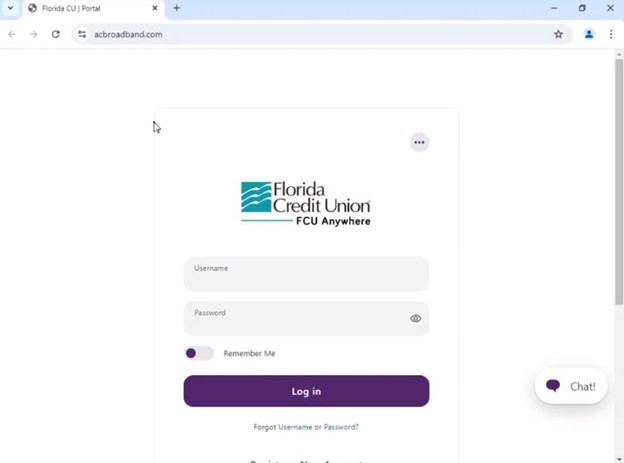
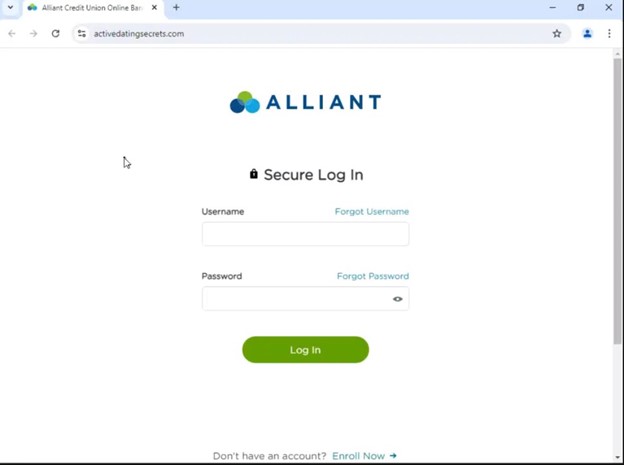
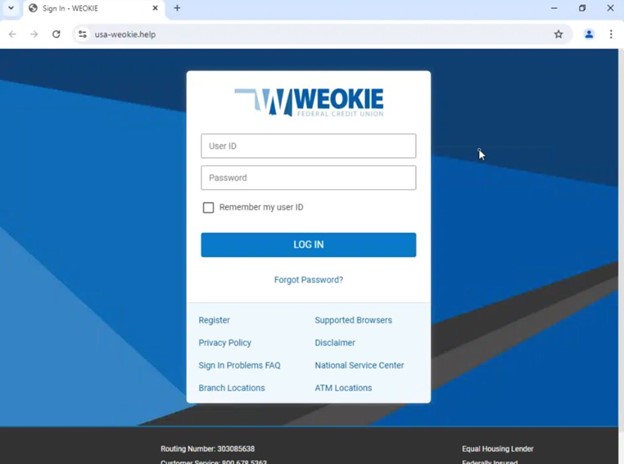
Monitoring for New Domains
We set up monitors to find new domains that matched our existing queries tracking this campaign. This allows us to keep track of the actors as they continue adding to their network. Within just a few hours of running these monitors, we picked up over 100 new domains, likely related to this campaign.
A brief sample list is below:
- ineedtobeconnected[.]com
- infokroger[.]com
- kaperollsitegh[.]info
- kpemployee[.]online
- mapayempluhcmsr[.]site
- marriottcsi[.]com
- myaccesspayemplust[.]online
- myaldihr[.]space
- myaramapayregh[.]online
- myemployeeconnectiones[.]site
- etc.
Additional Information
Silent Push will continue to track the Payroll Pirates threat actors’ activity and report our findings to the security community. For operational security, some of the information in this public blog has been omitted.
We’ve also published a TLP Amber report for Enterprise users that contains links to the specific queries we’ve used to identify and traverse the Payroll Redirects’ infrastructure—including proprietary queries that we’ve omitted from this blog for operational security reasons.
Mitigation
Silent Push believes all Payroll Redirects domains offer some level of risk.
Our analysts have constructed a Silent Push IOFA Feed that provides a partial list of Payroll Pirates Indicator of Future Attack domains focused on their scams, along with an IOFA Feed containing suspect Payroll Pirates IPs.
Silent Push IOFA Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types, including Silent Push WebScanner and Live Scan.
Click here to sign up for a free account.
Indicators of Future Attacks (IOFAs)
Here is a sample list of IOFAs – our full list is available for enterprise users. Silent Push Enterprise clients have access to a domain and IP feed containing the Payroll Pirates’ infrastructure.
- ajtxloginpage[.]com
- aldiemployeeportales[.]site
- aldihelpemployees[.]info
- aldiwebresoresetcpayls[.]online
- aldyemployeepwt[.]site
- ampliploysment[.]online
- andandorconnect[.]com
- apulyhcmplugaph[.]online
- bambochoop[.]website
- bambookjo[.]world
- basabamoon[.]life
- benefitify[.]me
- ccokrootit[.]com
- claimantcoremacca[.]com
- claimmassachusetsa[.]com
- consumerbenefithelp[.]com
- datsmabfonli[.]org
- emplhfxportales[.]online
- employeeconnectdc[.]one
- employeeconnectdc[.]shop
- employeeconnectdc[.]top
- employeehrconnectest[.]website
- employeeconnest[.]site
- employeeportallog[.]click
- employeeportallog[.]shop
- employeeselfhubs[.]com
- essecroggeed[.]com
- essmyaccounkrugser[.]com
- essmyykroogeerinfo[.]com
- esspayroll[.]top
- expopersonview[.]com
- fcpsmunisemployeeconectst[.]online
- feedaccountmacruker[.]com
- feegkrigers[.]com
- guideulca[.]com
- henrydevaney46.wixsite[.]com
- homedepotwithease[.]com
- hraccesskalser[.]com
- hrocneddiwserv[.]com
- ineedtobeconnected[.]com
- infokroger[.]com
- joblessconnect[.]net
- kaperollsitegh[.]info
- kixaccessrohce[.]com
- kpemployee[.]online
- macyinsidehr[.]com
- mapayempluhcmsr[.]site
- marriottcsi[.]com
- myaccesspayemplust[.]online
- myaldihr[.]space
- myaramapayregh[.]online
- myemployeeconnectiones[.]site
- mentalroccehget[.]com
- myescrochjesikurl[.]com
- mygbsnuyinow[.]com
- myhrkp[.]website
- myidmlogin[.]world
- myidmportal[.]site
- myinstitehr[.]com
- myinvitynyl[.]com
- mynewyorklgbsonline[.]org
- mypayararis[.]top
- mypayaramark[.]online
- myrocshe[.]com
- myinfominkogrerstat[.]com
- ulmasaabenefittoday[.]com
- unemplick[.]com
- utaxwust[.]com
- uvctaxsnat[.]com



