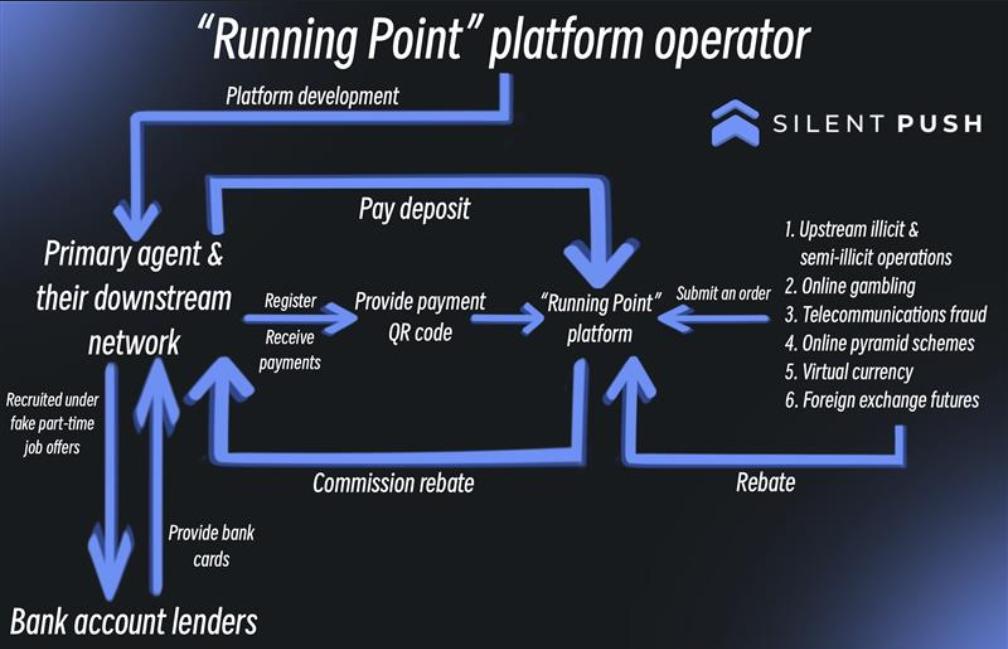
- Key findings
- Executive summary
- Background
- Join the Silent Push Community
- FUNNULL and fake trading apps
- FUNNULL’s CDN, rising up from corrupted soil
- Additional hostname analysis
- Suncity Group connections
- Network payments promotion (“跑分”) via FUNNULL GitHub repo
- FUNNULL and Tether crypto
- Retail phishing scam hosted on FUNNULL
- Polyfill supply chain scandal affects 110,000+ websites, raises additional questions about FUNNULL
- Additional information
- Mitigation
- Register for Community Edition
- Triad Nexus Observables / Indicators of Future Attacks (IOFAs)
Key findings
- Silent Push has been tracking FUNNULL, a Chinese Content Delivery Network (CDN) hosting persistent criminal campaigns, including investment scams, fake trading apps, and suspect gambling networks, for over two years
- We’re dubbing FUNNULL’s malicious domain cluster “Triad Nexus“
- 200,000 unique hostnames proxied through FUNNULL, with a +95% DGA ratio
- Thousands of suspect gambling websites hosted on FUNNULL containing the Suncity Group branding – an organization with ties to the Lazarus crime group
- Polyfill JavaScript library exploits being used in a supply chain attack, that impacted more than 110,000 of the top websites on the internet
- FUNNULL-hosted retail phishing scams discovered targeting major brands
Executive summary
This is the first in a series of blogs on a deep-dive investigation into Triad Nexus – our term for a large cluster of malicious infrastructure related to FUNNULL’s CDN.
In the past month, our Threat Research Team has identified more than 200,000 unique hostnames being proxied through FUNNULL, with more than 95% of the proxied hostnames created using Domain Generation Algorithms (DGAs)—a formula used for creating large amounts of domains.
Silent Push research has also revealed a connection between the Suncity Group – named in a 2024 UN report for laundering millions of dollars for the North Korean Lazarus Group – and Tether, the cryptocurrency of choice for suspect gambling sites serving East and Southeast Asia.
FUNNULL CDN was caught in a separate scandal earlier in 2024, after acquiring polyfill[.]io – the popular open source JavaScript library. Months later, they were linked to a supply chain attack against some mobile users on sites that still had the polyfill JS, redirecting them to an online “Asian gambling site.” More than 110,000 websites have been impacted.
Our Threat Analysts have also uncovered a new FUNNULL-hosted phishing scam, focused on retail and luxury fashion companies targeting major brands.
The findings outlined in this blog allow the research community to map FUNNULL’s malicious infrastructure, and provide avenues for additional research.
For operational security reasons, Silent Push is unable to share the exact specifics of each query and pivot utilized in a public blog. Silent Push Enterprise customers have access to a TLP Amber report containing all the relevant data types and pivot points we used to track FUNNULL’s infrastructure.
Background
Silent Push Threat Analysts first observed FUNNULL, a Chinese content delivery network (CDN) company, during research we began in 2022.
Our research uncovered a large cluster of fake trading apps impersonating well-known financial organizations that were part of a worldwide financial fraud campaign.
During the course of that research, we tracked FUNNULL hosting investment scams; discovered an alleged association with money laundering organizations; and mapped the hosting of thousands of algorithmically generated domains for low-quality suspect gambling sites, mostly in Mandarin, with the majority based in Macau.
DGAs are formulas used for creating bulk domains. Typically, DGAs result in domains that have a hyper-specific format, for example, apple2peanut4bread6[.]suffix – which would likely be created by a DGA formula that took three simple words/foods from a dictionary and then combined them with a random number between each word.
Other formulas combine a series of letters or numbers in unique ways. A huge portion of the domains on FUNNULL are merely a series of numbers, such as 7419255[.]com.
A large chunk (95%) of the 200,000 FUNNULL domains we discovered during our research are structured in this way.
We also discovered a site template connected to a developer working with FUNNULL, mirrored live (as of this report) on a domain hosted on a FUNNULL-owned IP range. The template promotes a “money-moving” network, that appears to be a money laundering service.
Further analysis of Telegram channels used by this network uncovers messages mentioning many of the suspect gambling brands with websites hosted on the FUNNULL CDN.
Suncity Group (and other online operators targeting Chinese markets) may be hosting their gambling websites behind randomly generated domain names due to the Great Firewall’s domain-based approach to blocking.
It’s also possible that criminals within China are purposefully mirroring their suspect gambling content across thousands of domains to prevent CCP authorities from blocking their websites and, subsequently, their access to cross-border money flows.
Thousands of suspect gambling websites hosted on FUNNULL prominently feature Tether promotions. Frequently used to move money in and out of China—and allegedly for gambling and laundering money—Tether (or USDT) is considered to be the “cryptocurrency of choice” for suspect gambling sites in China. Tether is banned in some countries because of its appeal to transnational organized crime groups, especially for running suspect gambling in Southeast Asia, where officials struggle to keep up with illicit financial flows.
Silent Push is also following FUNNULL CDN’s acquisition of polyfill[.]io, a JavaScript library that was integrated into 110,000 websites, including some of the largest commercial and government organizations in the world. In June 2024, FUNNULL was accused of propagating supply chain attacks against mobile users, and using polyfill.io in the attack chain.
So-called “bulletproof hosts,” enable malicious infrastructure to remain online by ignoring requests to take down suspicious or malicious sites. FUNNULL CDN does not currently provide a clear process for handling takedown requests on its website, but it does feature an interesting quote to describe its network: “Behind a cute name, there is a violent beast standing.”
We’ve also uncovered a retail scam campaign, hosted through FUNNULL, that uses phishing login pages to target major retail and luxury Western fashion brands. Targeted brands include Aldo, Asda, Bonanza, Cartier, Chanel, Coach, eBay, Etsy, Gilt Groupe, Inditex, Lotte Mart, LVMH, Macy’s, Michael Kors, Neiman Marcus, OnBuy[.]com, Rakuten, Saks Fifth Avenue, Tiffany & Co., and Valentino.
Sign up for a free Silent Push Community account
Register for our free Community Edition to use all of the tools and queries mentioned in this blog.
FUNNULL and fake trading apps
During a 2022 Silent Push investigation into a domain involved in investment fraud, our team uncovered a large cluster of fake trading apps impersonating well-known financial organizations, including the Australian Securities Exchange (ASX), Coinbase, CoinSmart, eToro, and Nasdaq.
This same investigation uncovered fake financial job scams employing pig butchering techniques, and this is when our analysts first came across several malicious networks hosted on the FUNNULL CDN infrastructure.
Our Triad Nexus research discovered this is not a lone cluster of activity but is, in fact, part of a global financial fraud campaign.
FUNNULL’s CDN: rising up from corrupted soil
A large portion of the fake trading apps we reported on were using FUNNULL to host their malicious content, with CNAME records pointing at vk6a2rmn-u.funnull[.]vip.
If we perform a reverse lookup on that CNAME, we see approximately 2,000 domains involved in the 2022 scam. It appears the threat actors are now shifting to 6ce0a6db.u.fn03[.]vip, but its size is considerably smaller.
When updating our FUNNULL research for 2024, we discovered that this same malicious cluster, while reduced in scope, still has a couple of active hostnames, including cmegrouphkpd[.]info (pictured below), which has hosted a fake trading platform abusing CME Group’s brand for the past two years.
Until recently, a near identical version of this site was hosted at hiflyk47344[.]top.
The timeline can be seen via current and historical CNAME records, which for cmegrouphkpd[.]info shows it had a record pointing to vk6a2rmn-u.funnull[.]vip between February and March 2022, changing to vk6a2rmn-u.funnull01[.]vip between March 2022 and June 2024, and since then, switching to 6ce0a6db.u.fn03[.]vip.
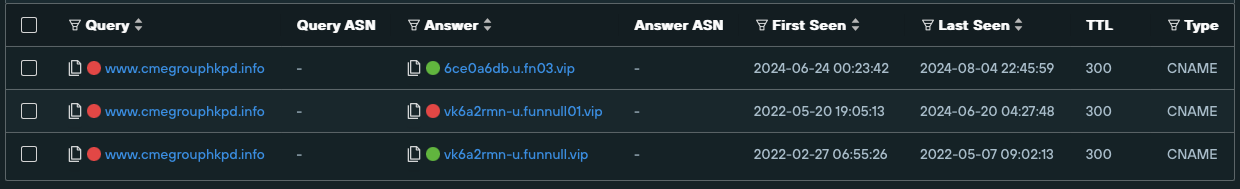
cmegrouphkpd[.]infoThe apex domains seen in the Answer fields of these CNAME records – funnull[.]vip, funnull01[.]vip and fn03[.]vip – are all part of FUNNULL’s CDN infrastructure.
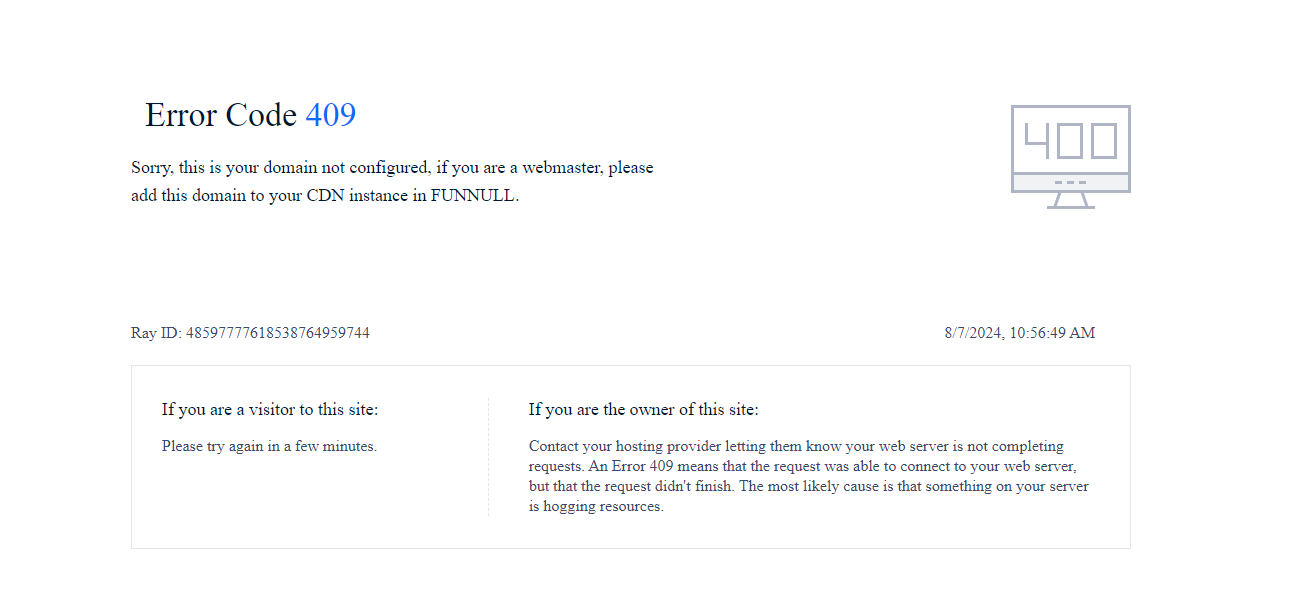
When navigating to a domain not completely configured to work with the FUNNULL CDN, an error page with a consistent theme referencing “FUNNULL” renders, which looks like this:
By having a CNAME record pointing to FUNNULL’s CDN infrastructure, every time a DNS client requests the hostname of a FUNNULL customer, the DNS resolver follows the resolution chain and redirects to the CDN, which answers with the IP address of its “Point of Presence” (PoP) with the fastest response, as seen below:
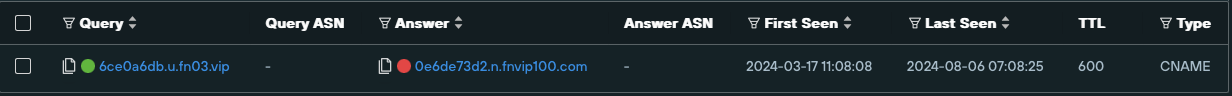
cmegrouphkpd[.]info name resolution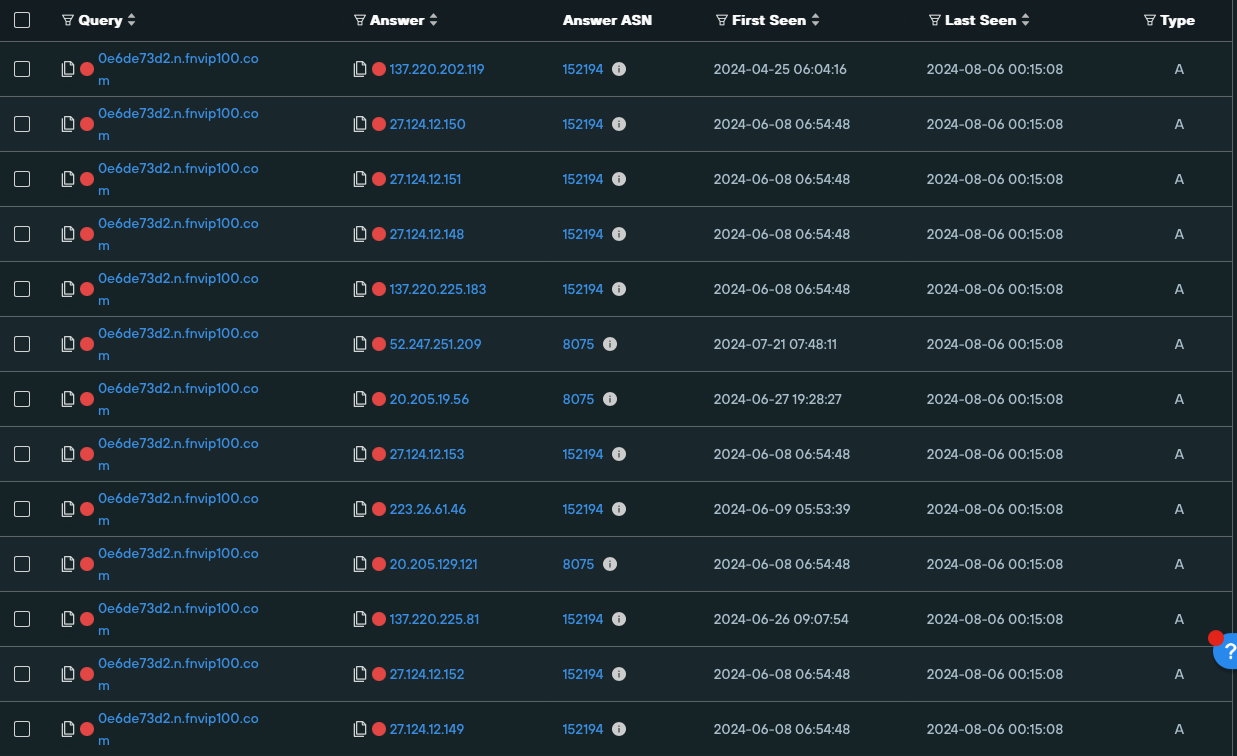
cmegrouphkpd[.]info’s name resolutionAdditional hostname analysis
As a result, these CNAME chains can be used to map FUNNULL’s entire customer infrastructure on its CDN and obtain the IP addresses of its PoP network.
We identified over 200,000 unique hostnames being proxied through this network over the past month alone, and 1.5 million reverse CNAME records/lookups have been collected since 2021.
FUNNULL CNAME chains
Here is a diagram of the FUNNULL CNAME chains:
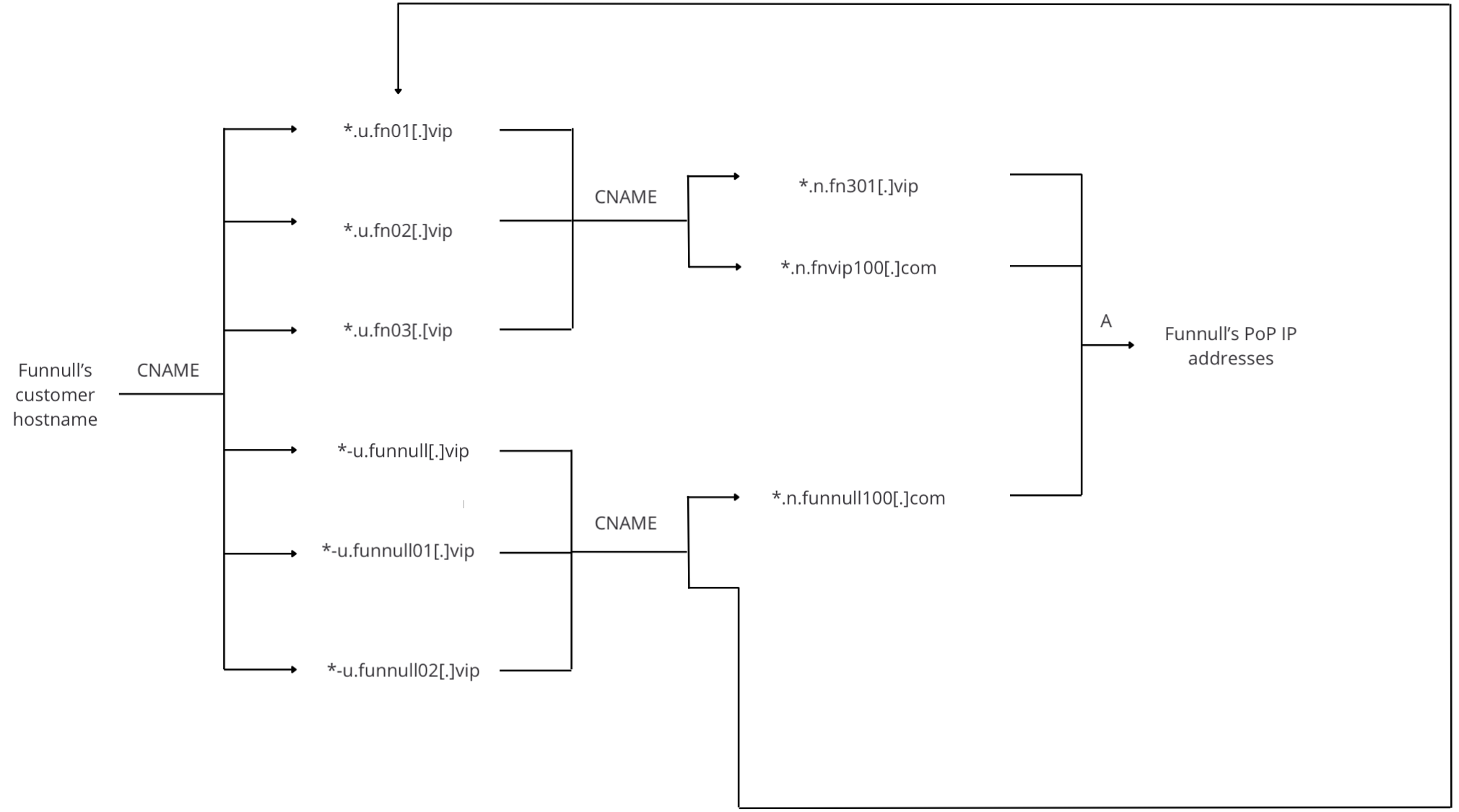
Utilizing the Silent Push platform to perform a high-level CNAME lookup of the hostnames leveraging this system, our analysis revealed that more than 95% of the hostnames were created with DGAs containing mostly numeric characters, with a few optional letters.
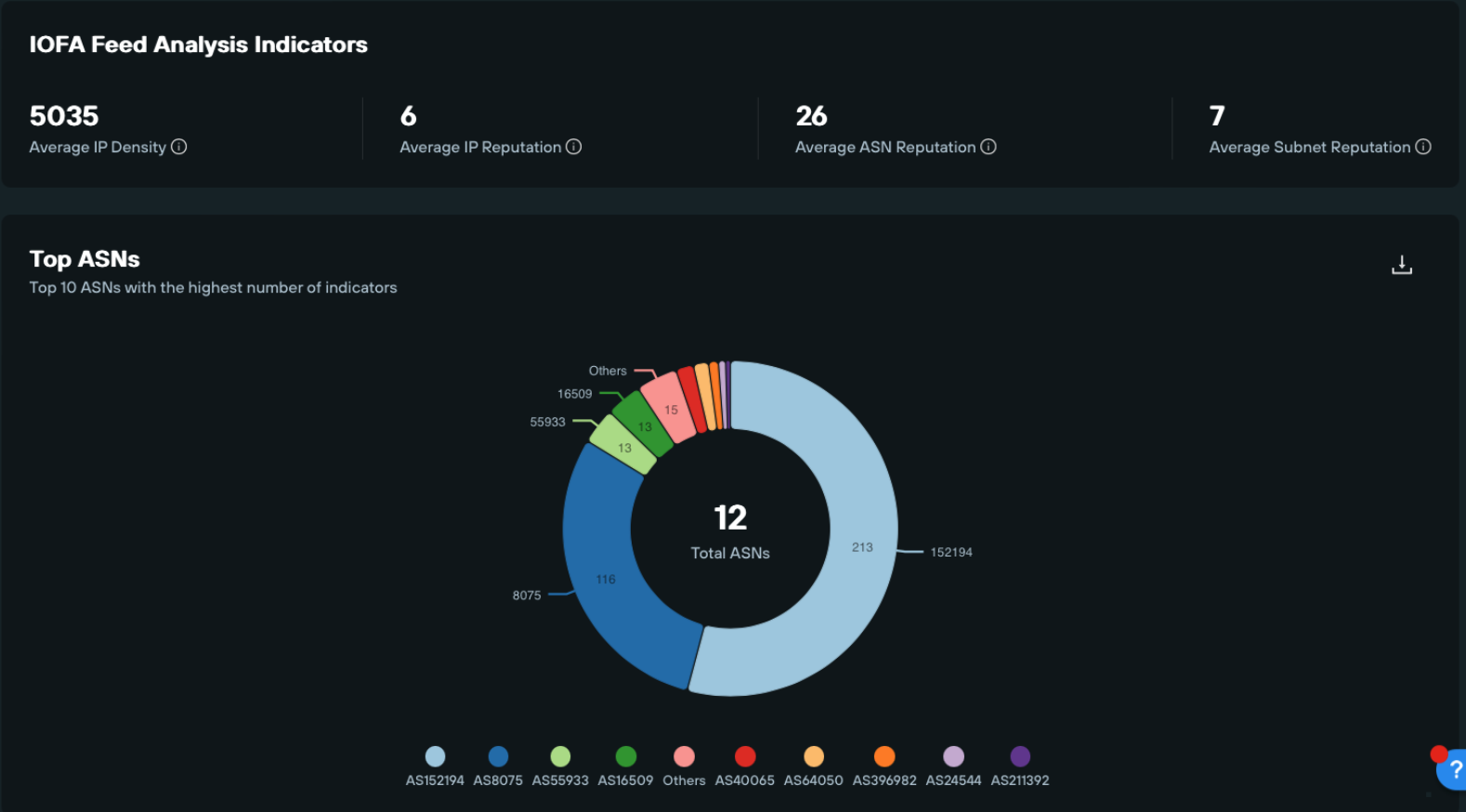
Silent Push identified close to 500 of FUNNULL’s PoP active in the last week and, as expected, a large portion of these were located in Asian ASNs, such as AS152194 (China Telecom Global), AS45753(NETSEC-HK Netsec Limited), and AS55933 CLOUDIE-AS-AP Cloudie Limited, among others.
Surprisingly, during our investigation, we discovered that nearly 40% of the CDN’s PoPs were IP addresses belonging to AS8075(MICROSOFT C) and AS16509(AMAZON), two major US-based cloud providers.
Using Silent Push’s extensive PADNS data, we confirmed that FUNNULL has been renting Microsoft’s IP space and using it to accelerate its customers’ infrastructure, since at least 2021.
Across the FUNNULL CDN, our team found tens of thousands of suspect gambling websites.
The number of distinct brands hosted on this infrastructure—roughly a dozen—was exceedingly low compared to the total number of websites collected in this grouping, which was around 40,000.
Our team was able to segment this grouping of suspect gambling sites based on the brand favicons used, and use this data to determine how many sites feature each brand:
| Percentage | Organization | Favicons | |||
|---|---|---|---|---|---|
| 34% | Venetian Macau |  | |||
| 26% | Macau Grand Lisboa |  |  |  | |
| 16% | Suncity Group (太阳城集团) | ||||
| 8% | Kaiyuan Chess and Cards (开元棋牌) | ||||
| 6% | Macau Crown Casino |  | |||
| 10% | Sands MACAO, Bet365, Bwin Sports, Lottery Network Entertainment Company, Fake Trading Apps, Adult Themed Apps, mirror jump pages, among others | | | | |
All of these brands appeared to have ties with the suspect gambling and betting industries.* The brands above are hosting thousands of mirrored instances of their sites, almost exclusively in Mandarin Chinese.
*During the course of the research, the brands listed here were reached out to for comments. It appears that Bwin is the only company who responded, and directly refuted any involvement in these websites. If any brands listed here have questions or concerns, we’re happy to add additional clarifying information.
An in-depth look at FUNNULL’s corporate brand
The FUNNULL CDN appears to be marketed via several URLs, including: “funnull[.]com” and “funnull[.]io”.
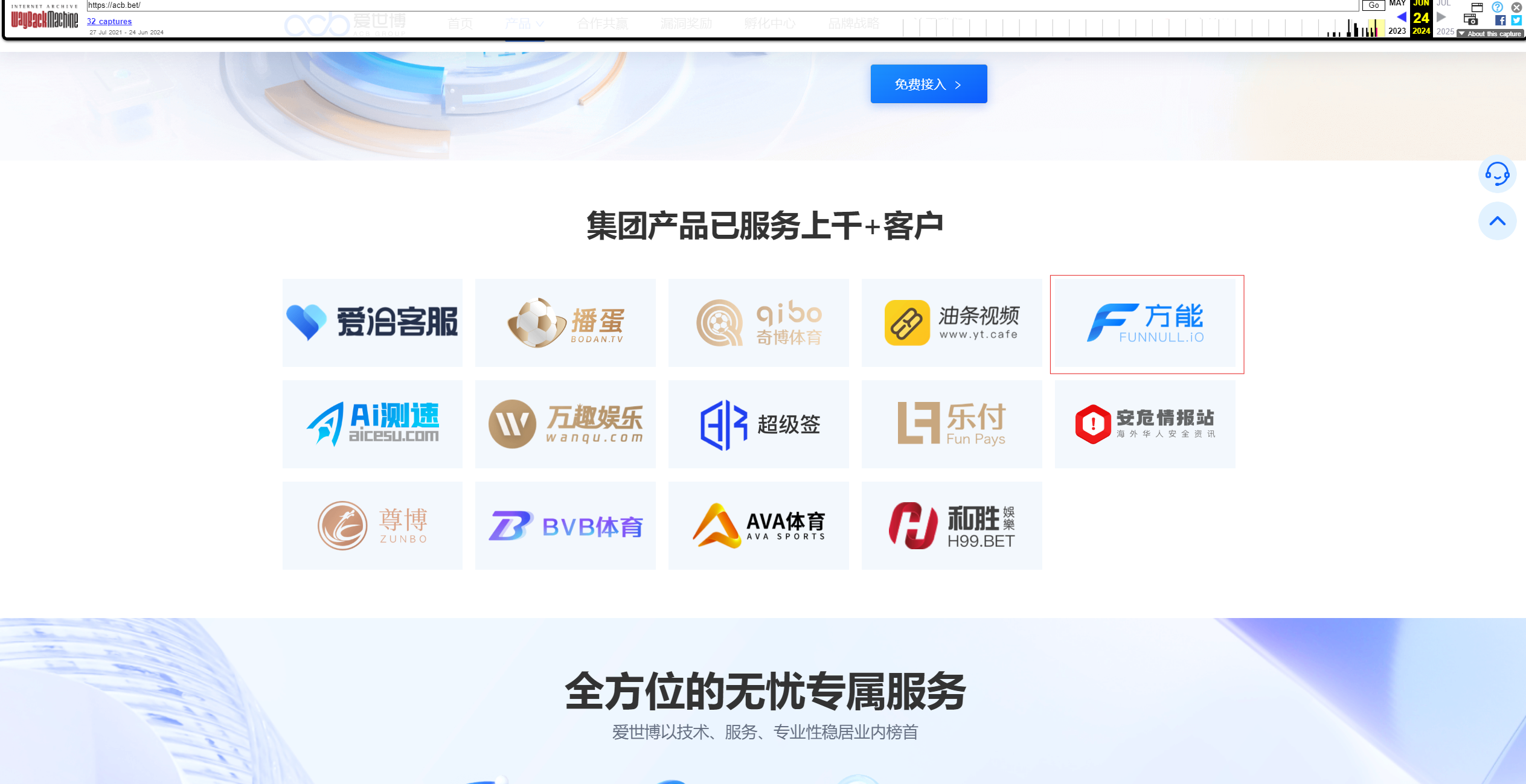
Prior to the polyfill[.]io supply chain campaign, ACB Group – the parent company that owns FUNNULL’s CDN – had a public webpage at “acb[.]bet,” which is currently offline. A copy of the site from earlier in 2024 can still be accessed using the Way Back Machine.
In this screenshot of the homepage, ACB Group claims to own Funnull[.]io and several other sports and betting brands.
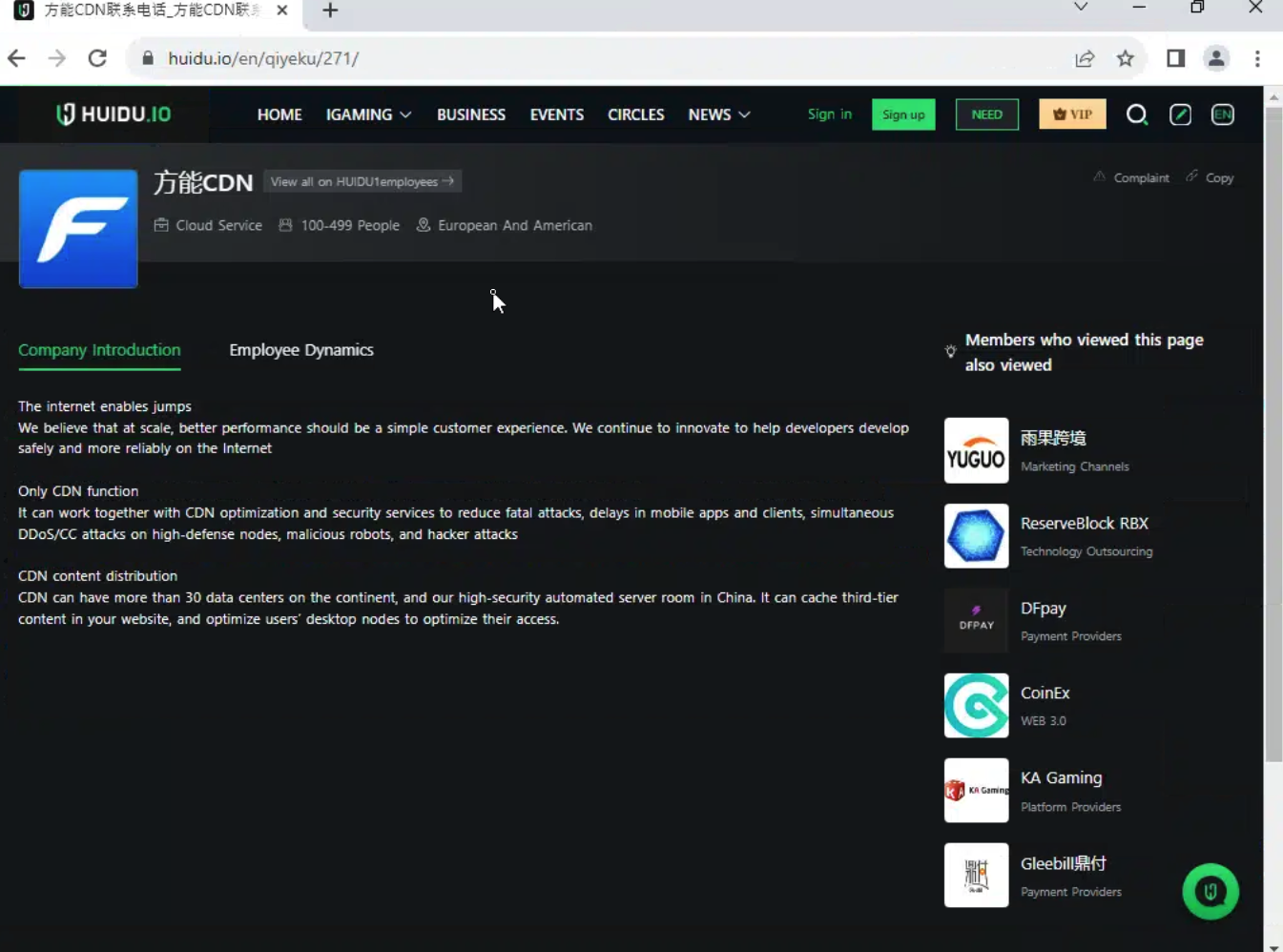
A web entry we found on HUIDU, an information hub for the online gaming industry, included a “Company Introduction” for FUNNULL’s CDN where they noted FUNNULL has server operations within China, writing, “CDN can have more than 30 data centers on the continent and our high-security automated server room in China.”
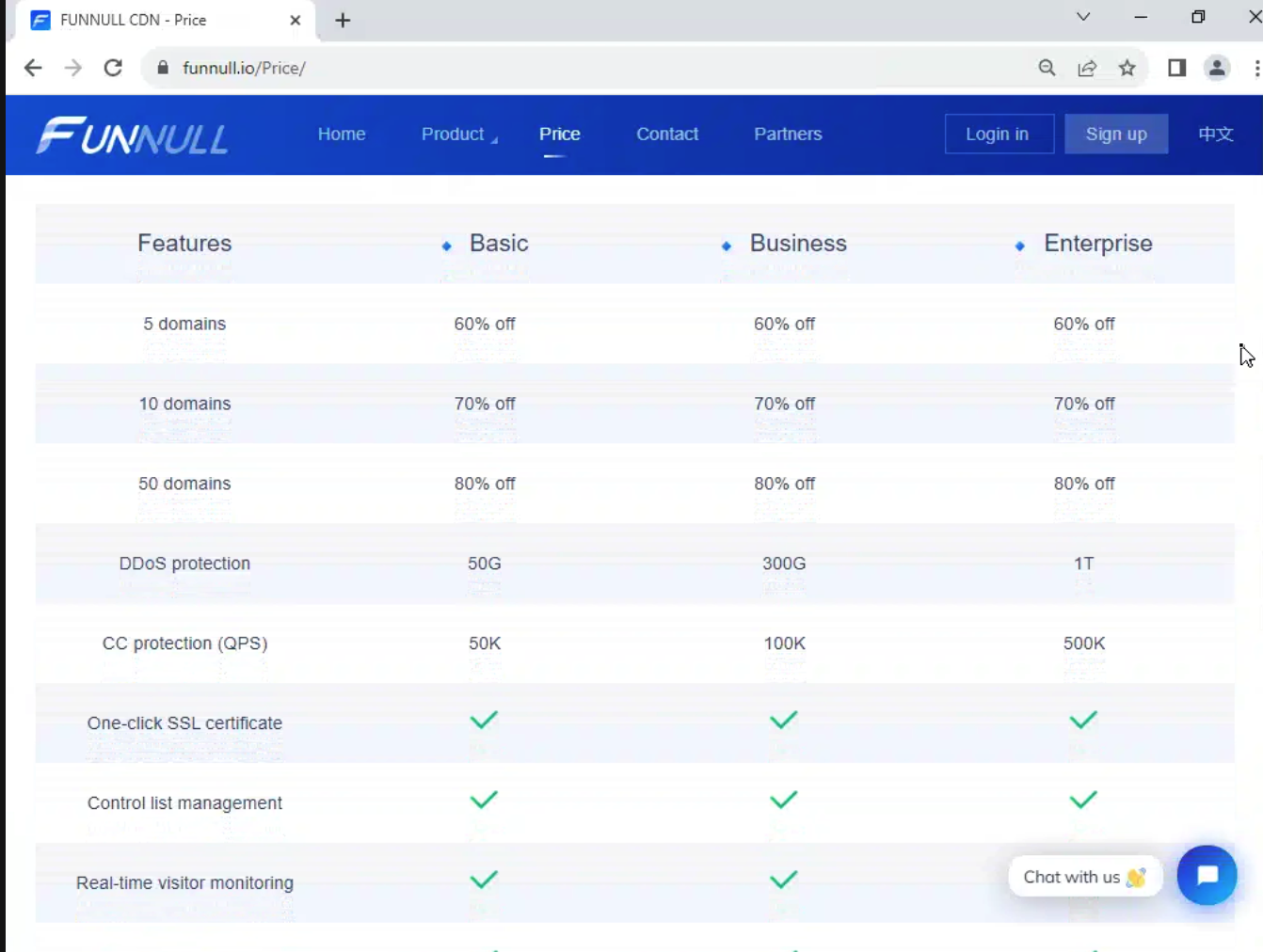
FUNNULL’s CDN pricing page suggests a unique business model that likely only appeals to very specific types of organizations.
The pricing includes three tiers for managing a single domain, with different amounts of bandwidth per tier, yet immediately below these options are details about bulk domain management, with 80% discounted rates for clients with 50 domains or more.
Suncity Group connections
Silent Push Researchers noticed that “Suncity Group” is one of the organizations whose logo and branding is present on a sizeable number (thousands) of gambling websites hosted on FUNNULL.
Suncity Group is alleged to have built a money laundering/underground banking system that processed $100 billion USD in illegal bets and laundered $40 billion for criminals.
According to Reuters/Hong Kong, in writing about a state-backed report, Suncity is (was) Macau’s biggest junket operator of VIP gambling rooms around Asia.
With the exception of Macau, where Chinese nationals are permitted to bet in physical gambling establishments and a few legal state-sponsored lottery activities, gambling is illegal in mainland China. The report stated that Suncity enabled Chinese players to bet online, utilizing underground banks to move capital out of the country.
Suncity Group denied having online gaming operations, and issued a statement that “It didn’t operate any online gaming business and all its operations were permitted under local government regulations,” according to Reuters.
Macau’s gaming regulator stated that online gambling in Macau is illegal and violations of local laws and regulations would prompt the bureau to “take serious action.”
One report about Suncity Group, “Underground Banking and Money Laundering Methods,” in the January 2024 United Nations Office on Drugs and Crime (UNODC) goes into great details about the extent of Suncity’s illegal gaming activities, and further underscores our research.
Macau Special Administrative Region (SAR) of China-based junket mogul and Suncity Group CEO Alvin Chau was sentenced to 18 years in prison last year. Thirty-six other company individuals connected to the Chau-led syndicate were also indicted.
Suncity Group was also forced to pay a $3.1 billion USD fine. During the UNODC investigation, it was credibly alleged that Chau was a member of the Chinese transnational crime syndicate Triad, and his group laundered $19 million USD for Lazarus Group. Money laundering via online gambling sites is considered a serious crime, and Silent Push researchers noted the screenshot below from the U.N. report looks markedly similar to the Suncity Group sites seen live on FUNNULL.
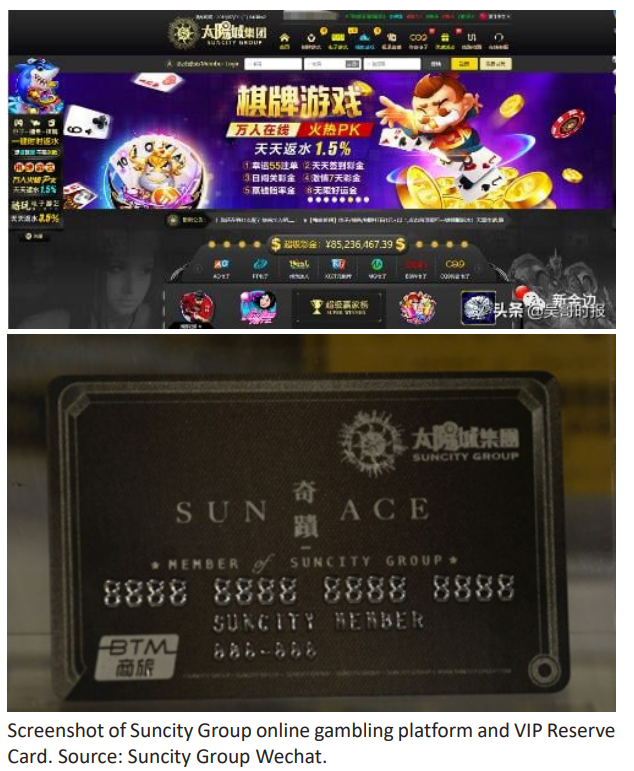
Suncity Group-related infrastructure accounted for more than 6,500 unique DGA hostnames.
Further analysis of a Suncity website – t25556[.]com – reveals another domain embedded on the page below the QR codes: “6289[.]com”
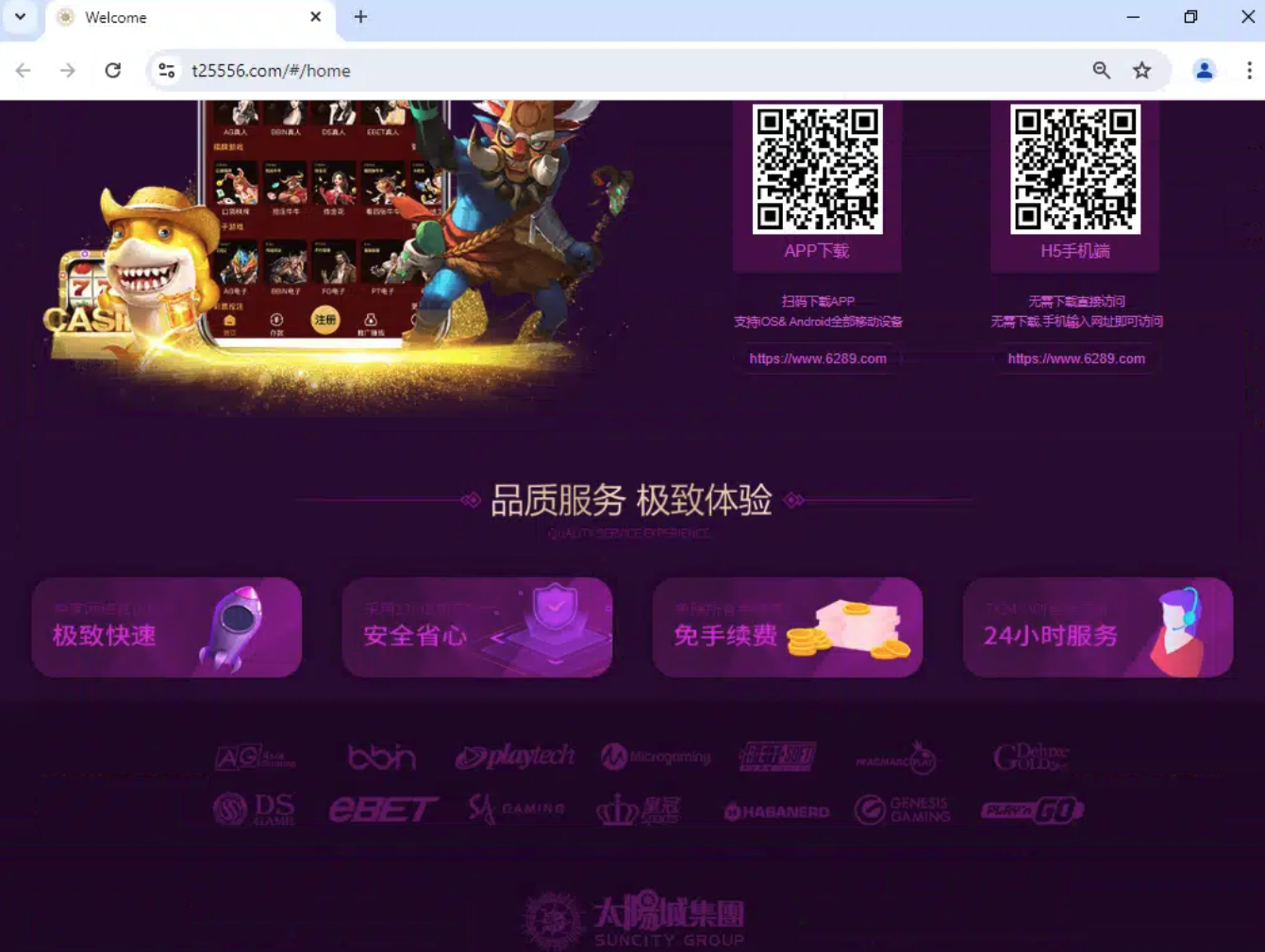
When accessed, this triggers a redirect chain through “threevip[.]cc/?u=6289[.]com,” eventually ending up on “15991t[.]com/,” a page used to list the active mirrors serving the Suncity Group’s gambling campaign:
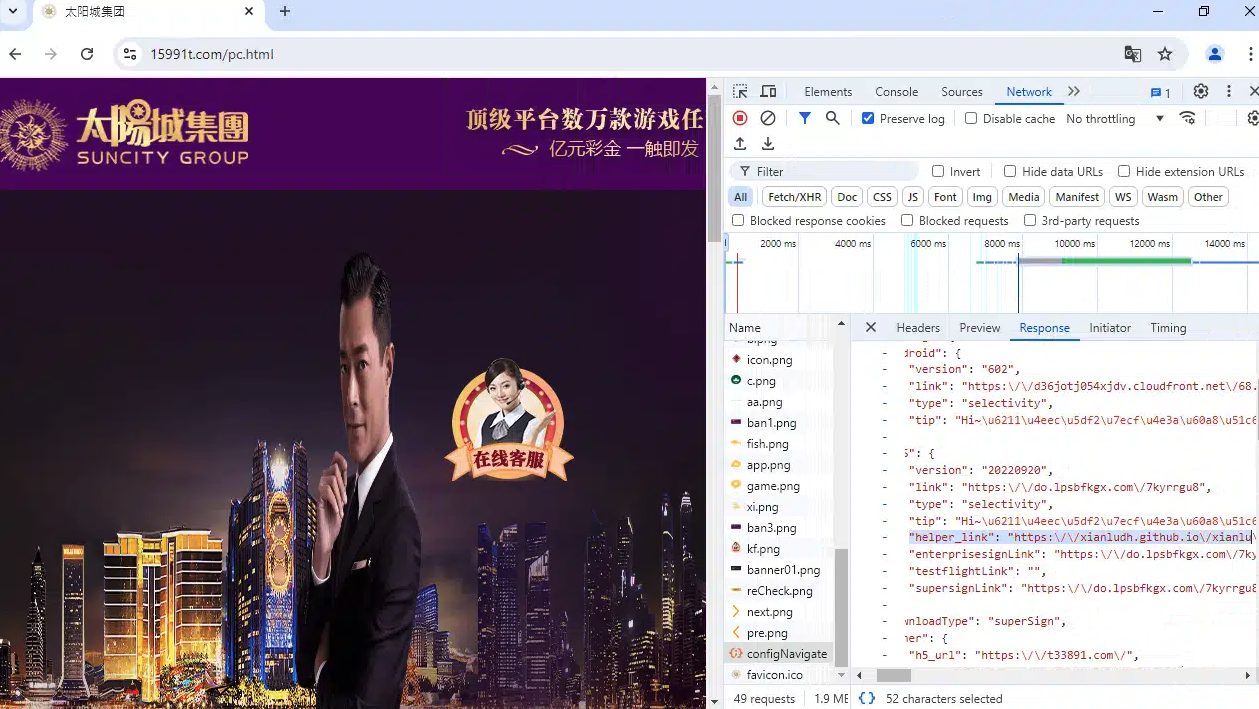
Analyzing the final hostname also revealsed an endpoint responsible for returning the configurations for that page, including a list of active mirrors as well as a GitHub account listed in the “helper_link” field, as seen below:
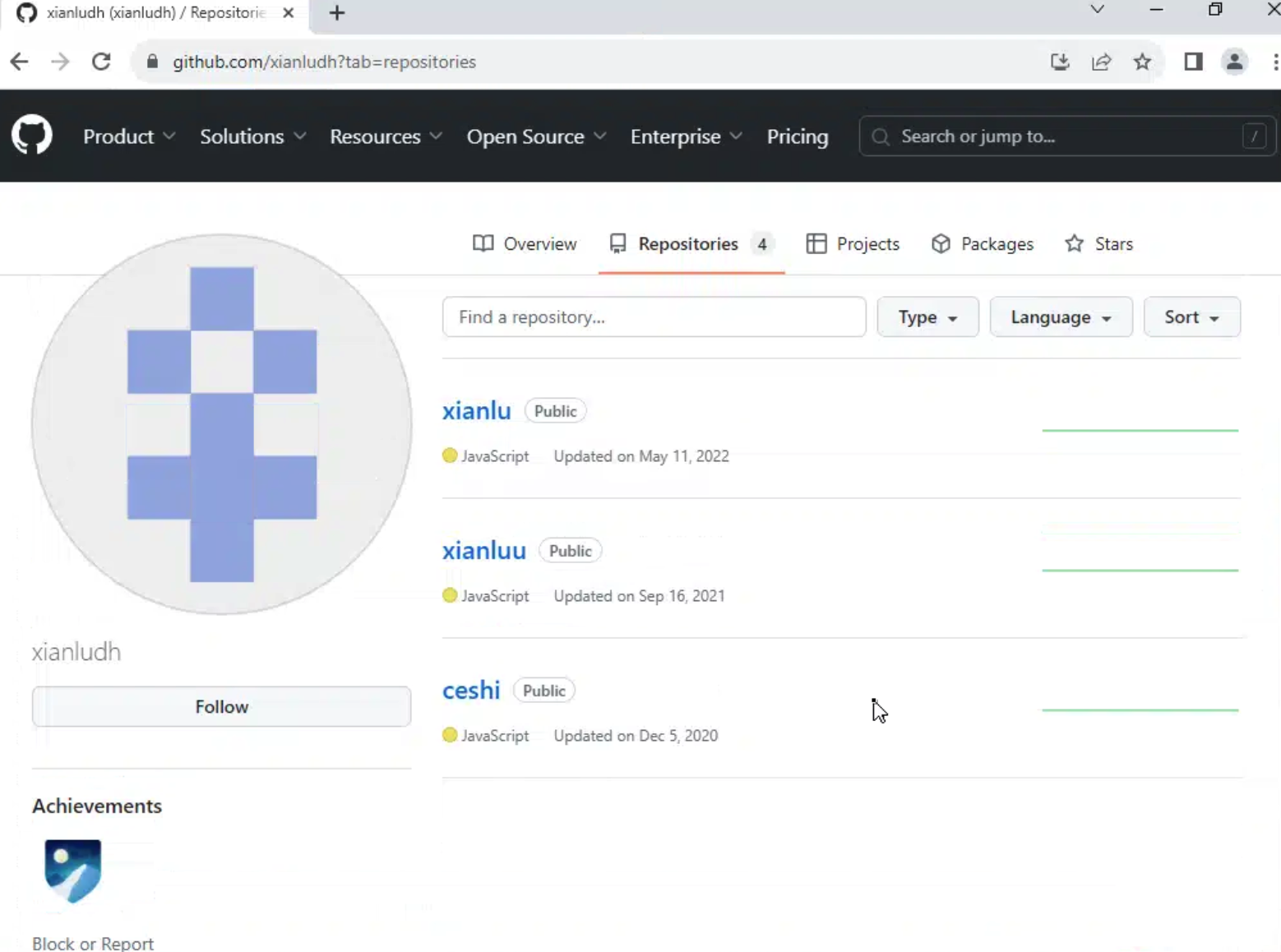
Browsing the Github account, we found three public repositories (github[.]com/xianludh?tab=repositories) containing templates used by sites hosted on FUNNULL.
Surprisingly, the repositories contain source code for hundreds of suspect gambling applications, including the brands we had seen being proxied through FUNNULL. This suggests they were derived from a common template or were potentially coded by the same developer.
Within one of the GitHub repositories owned by the user “xianludh” is a series of templates that mention various online gambling brands, highlighted above. You can see one of the Suncity templates here (xianludh.github[.]io/xianlu/xiufu/741/) and the code can be viewed here (github[.]com/xianludh/xianlu/tree/master/xiufu/741).
This template isn’t an exact match to the current Suncity websites hosted on FUNNULL, but the public GitHub files are three years old.
It’s possible that the GitHub user “xianludh”— referenced in the ‘helper_link’ field within FUNNULL-hosted pages—may have older code still publicly hosted on GitHub, while using updated code on the live websites hosted on FUNNULL.
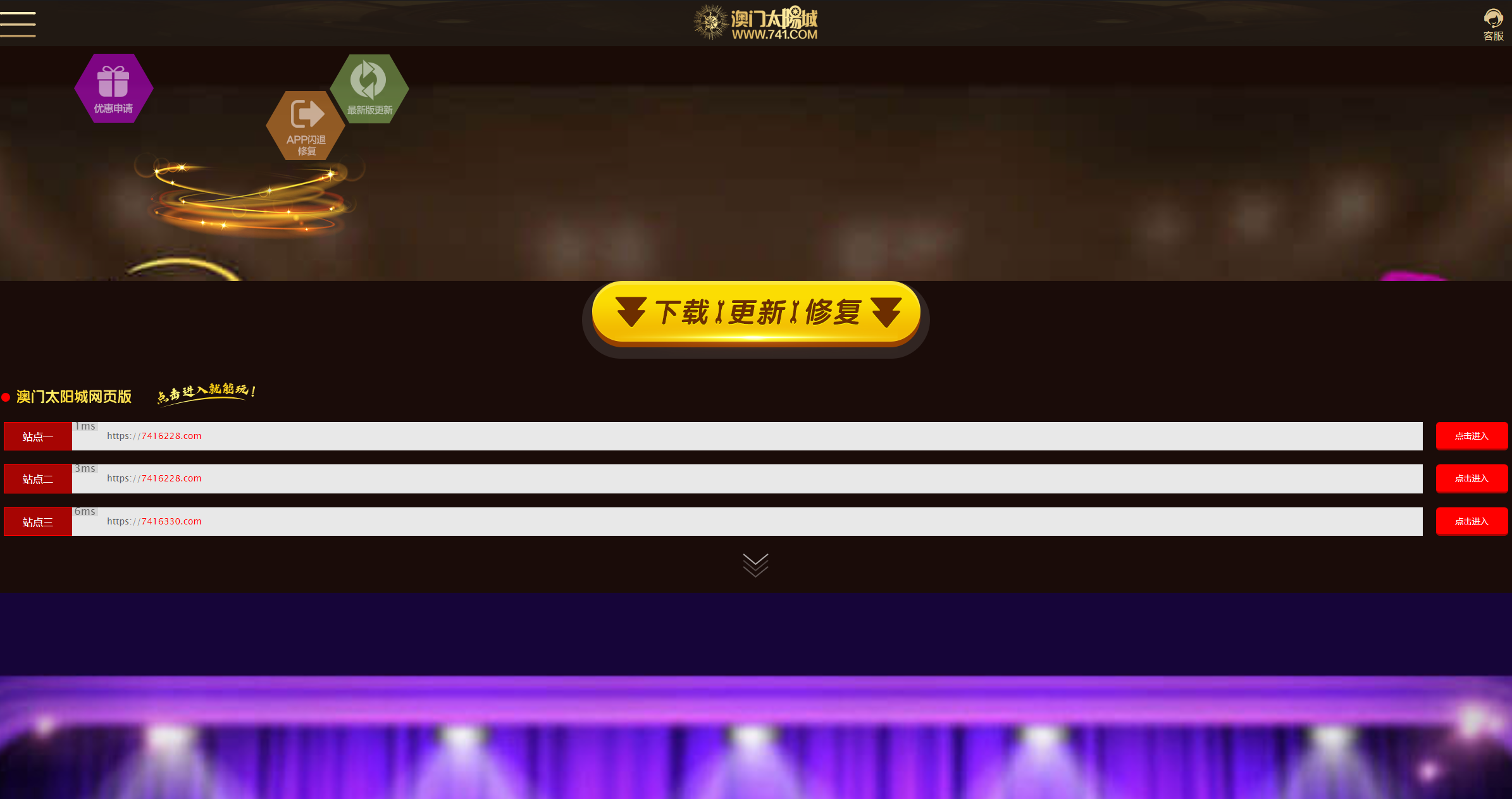
Other code repositories in the “xianludh” account contain additional Suncity gaming templates, along with templates for various other types of sites hosted on FUNNULL.
It would appear that one organization (or individual) is creating a large portion of the templates for sites hosted on FUNNULL.

Network payments promotion (“跑分”) via FUNNULL GitHub rep
Our Analysts discovered that one of the pages within the “xianludh” GitHub repository had some very specific and interesting language, containing the phrase “跑分” – criminal jargon for money laundering – along with details in Mandarin about what appears to be a “money-moving[laundering]” network.
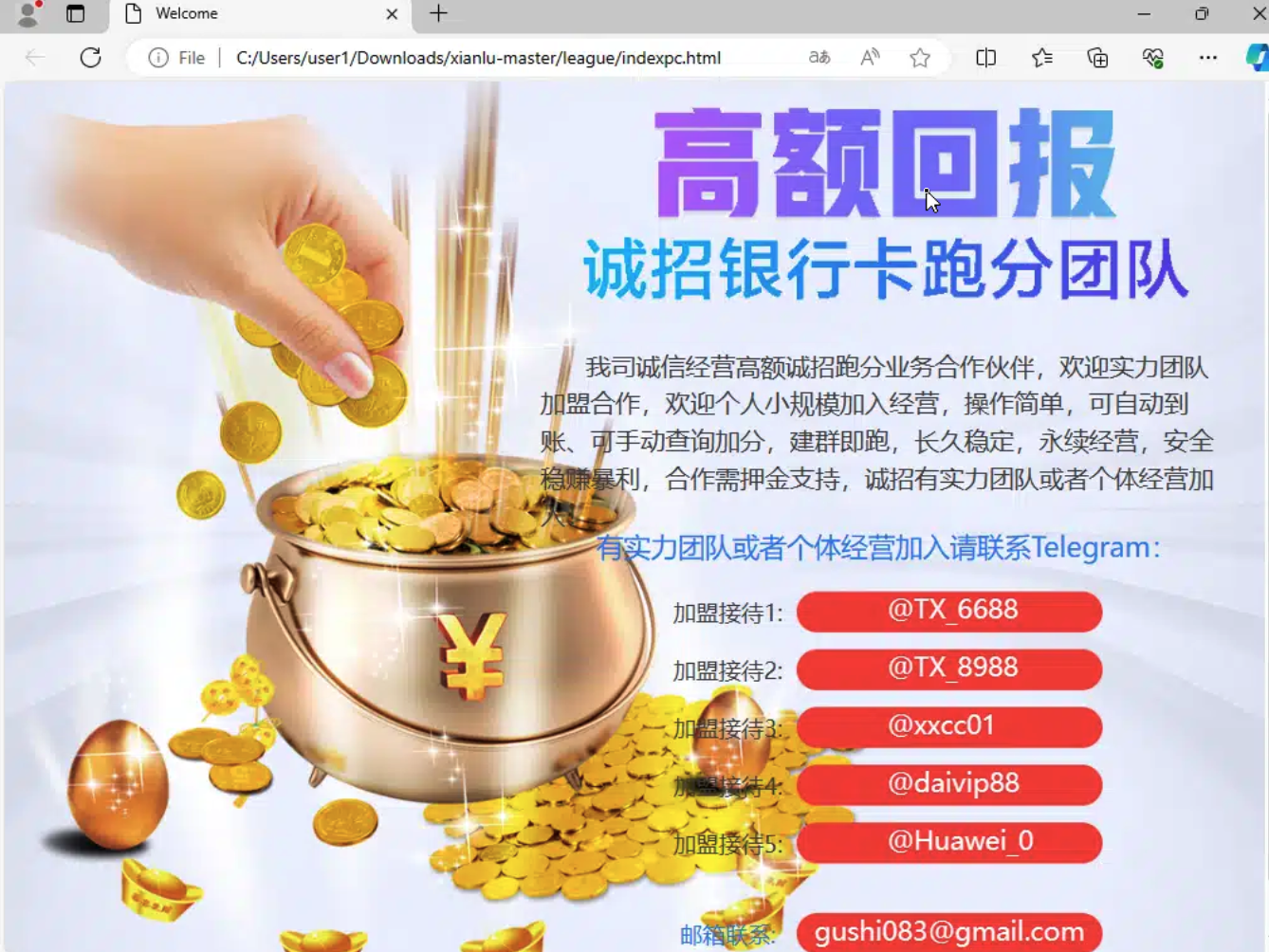
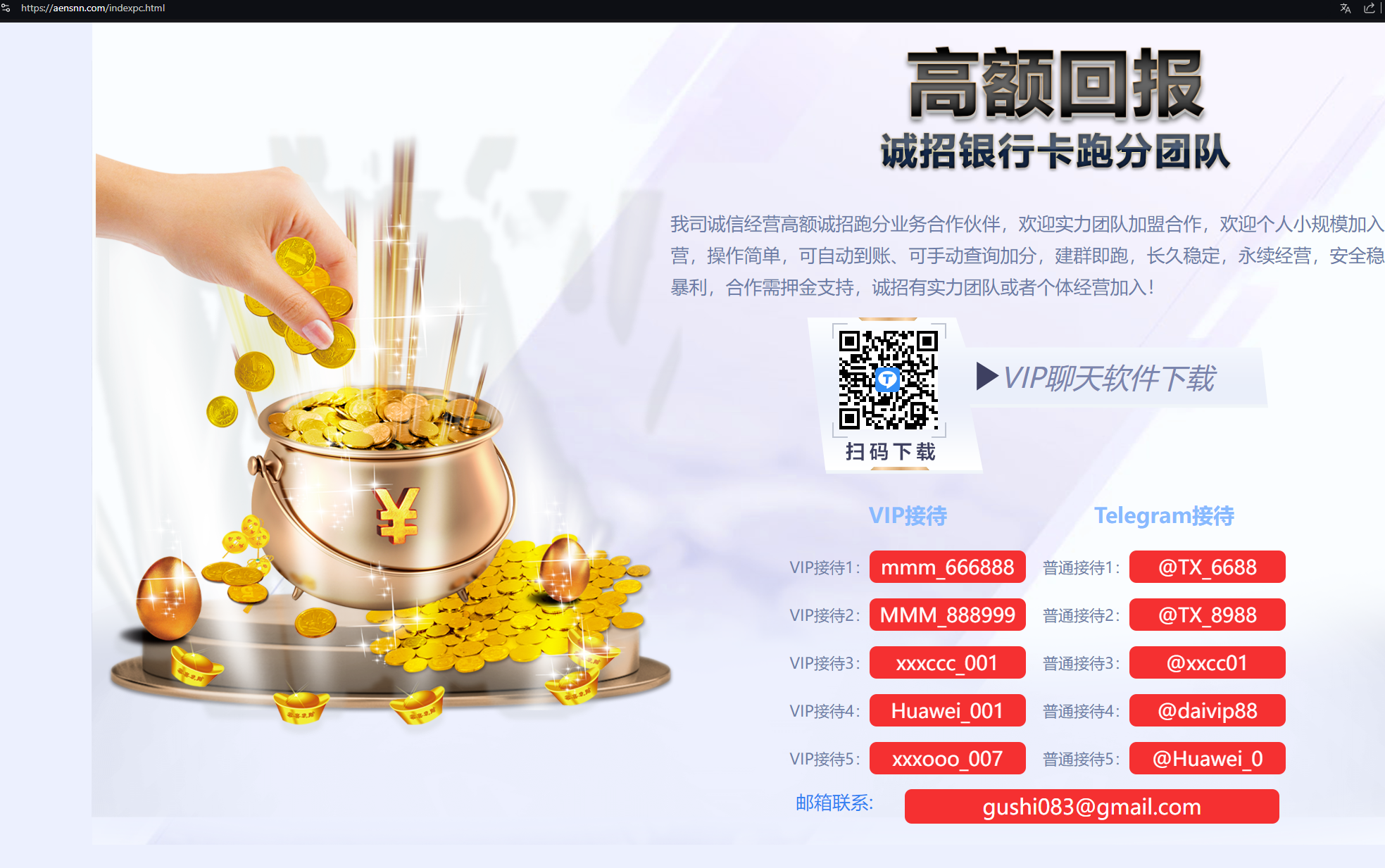
The page in the GitHub repository also included links to several live Telegram channels, as well as a Gmail address:
- t[.]me/TX_6688
- t[.]me/TX_8988
- t[.]me/xxcc01
- t[.]me/daivip88
- t[.]me/Huawei_0
- gushi083@gmail[.]com
After accessing the Telegram links, our team roughly translated the relevant introduction messages, which confirmed further links to the so-called “money-moving” networks:

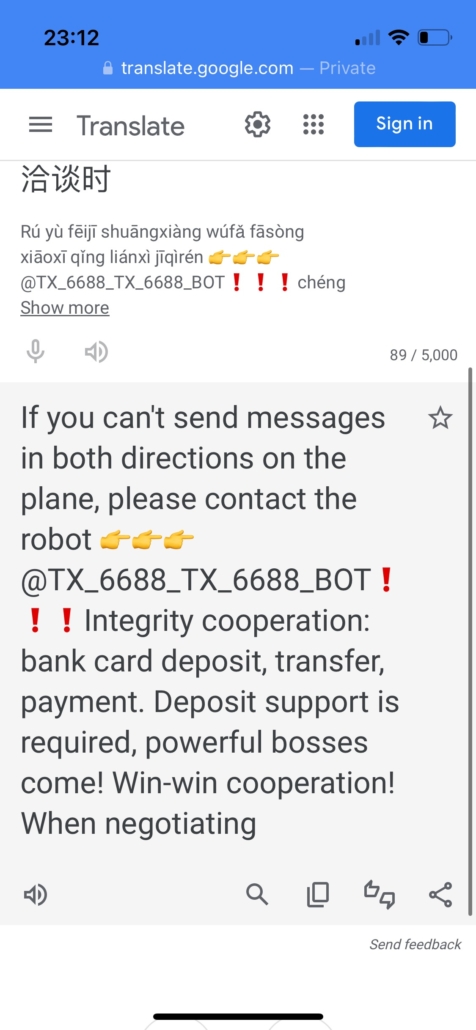
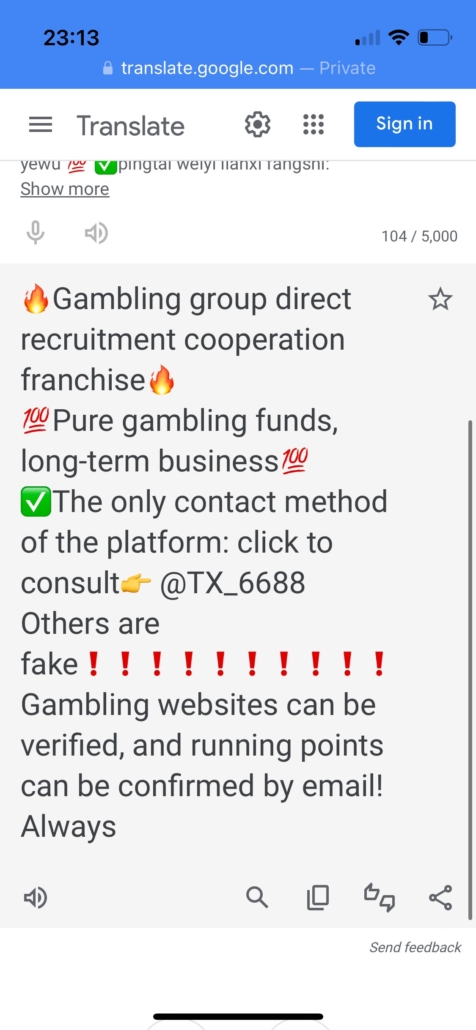
Note: The live version of this site promoting a money-moving network is hosted on a FUNNULL IP Address.
Our researchers checked the five Telegram channels to see which sites might link to these channels, and found that aensnn[.]com is on 137.220.202[.]236 – a FUNNULL IP.
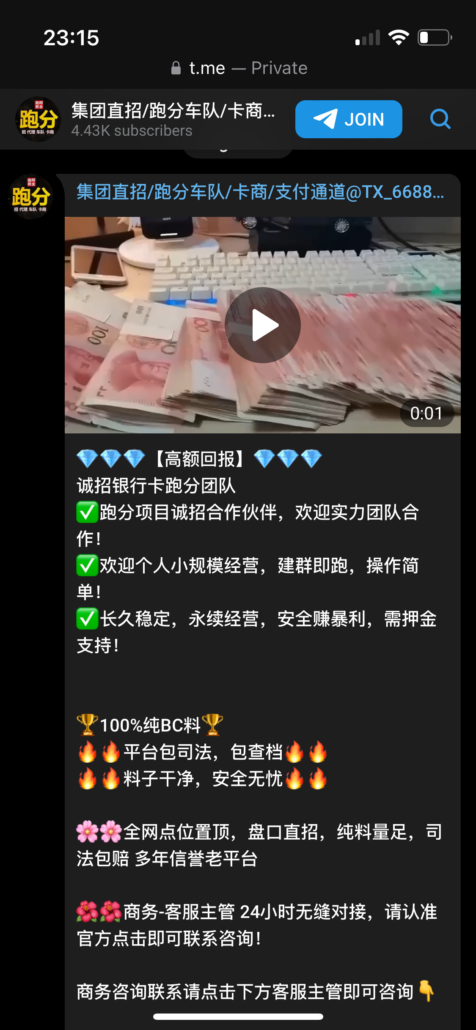
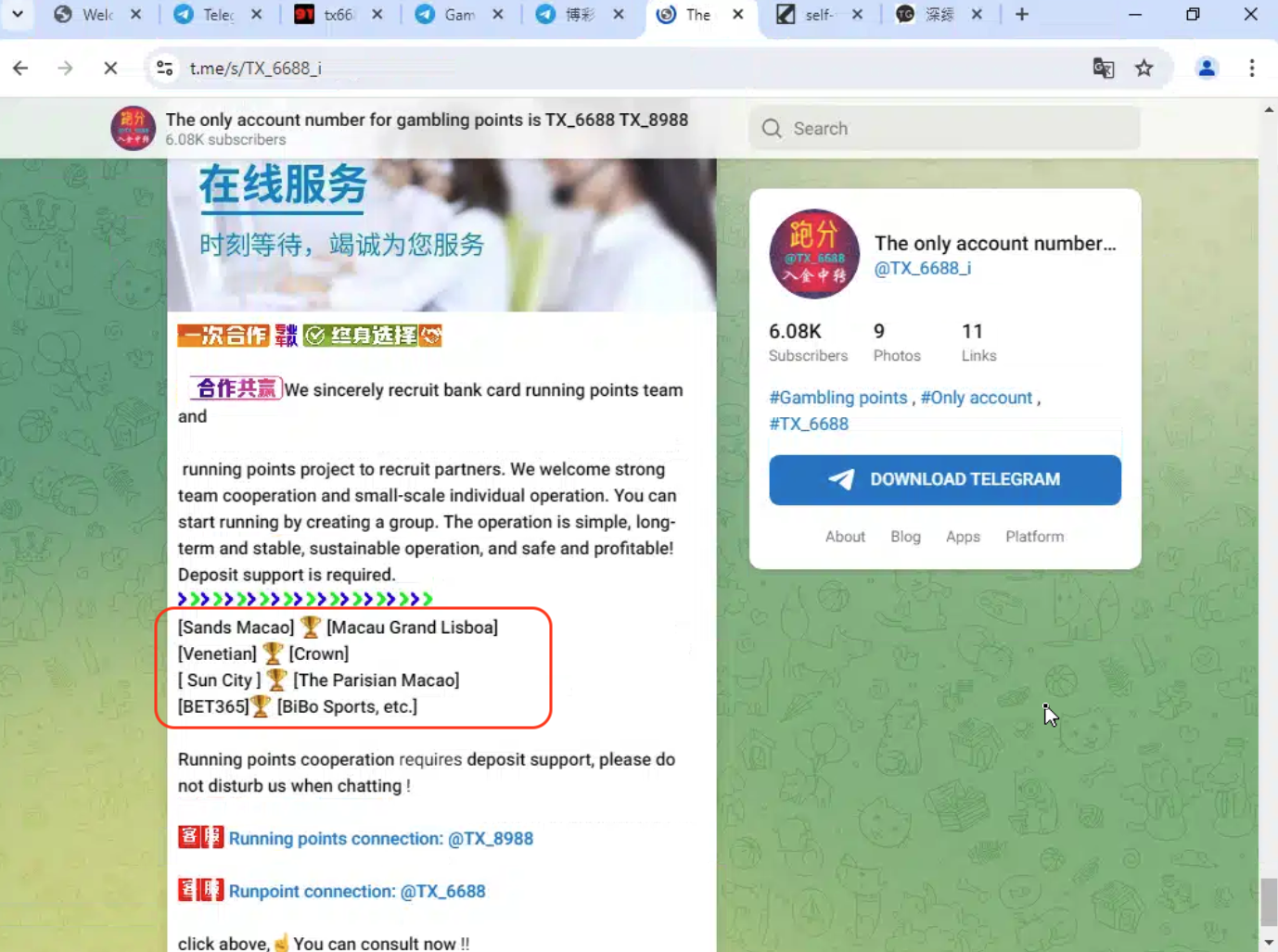
Our team was also able to find a Telegram channel (t[.]me/s/TX_6688_i) with the same profile photo and partially the same “6688” name, which has public content that lists some of the brands seen on the suspect gambling websites hosted on FUNNULL.
Their August 28th promo message translated into English via Google Translate reads:
“Cheng Zhao Bank Card Running Sub Team“
Sincerely recruit partners for running sub-projects, welcome strength teamwork, welcome individuals to operate on a small scale, build groups and run, simple operations, long-term stability, sustainable operations, and make huge profits safely! Deposit support is required.
[Macau Jinsha] [Macau New Portuguese ]
[Venetian ] [Crown ]
[Too sun City ] [Macao Parisian ]
[BET365 ] [Bingbo Sports, etc. ]
Running cooperation , Deposit support, don’t disturb ! “
FUNNULL and Tether crypto
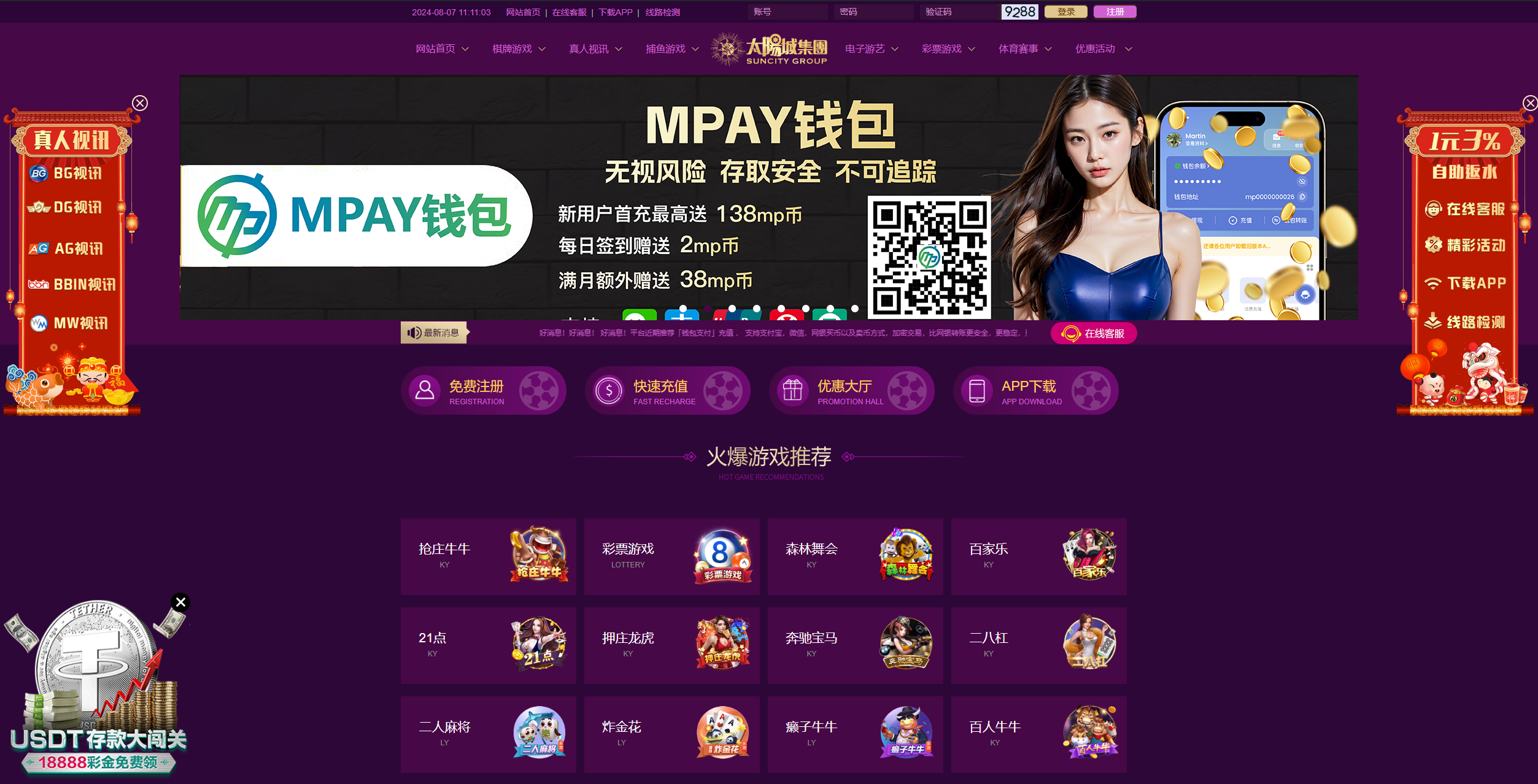
Silent Push Researchers manually reviewing Suncity gambling websites discovered that most sites included a prompt for a Tether/USDT deposit program, which you can see in the bottom left of this screenshot:
Retail phishing scam hosted on FUNNULL
Our Analysts also found a FUNNULL CDN phishing scam, targeting top retail brands.
At least 20 major brands, mostly focused on retail and luxury fashion companies, are being targeted with phishing login pages hosted on FUNNULL, including:
Aldo, Asda, Bonanza, Cartier, Chanel, Coach, eBay, Etsy, Gilt Groupe, Inditex, Lotte Mart, LVMH, Macy’s, Michael Kors, Neiman Marcus, OnBuy[.]com, Rakuten, Saks Fifth Avenue, Tiffany & Co., and Valentino.
| Brand | CNAME Record | Example | Other domains targeting the same brand in this campaign |
|---|---|---|---|
| Aldo | 12abb97f.u.fn03[.]vip | aldo.shopaldo1[.]com 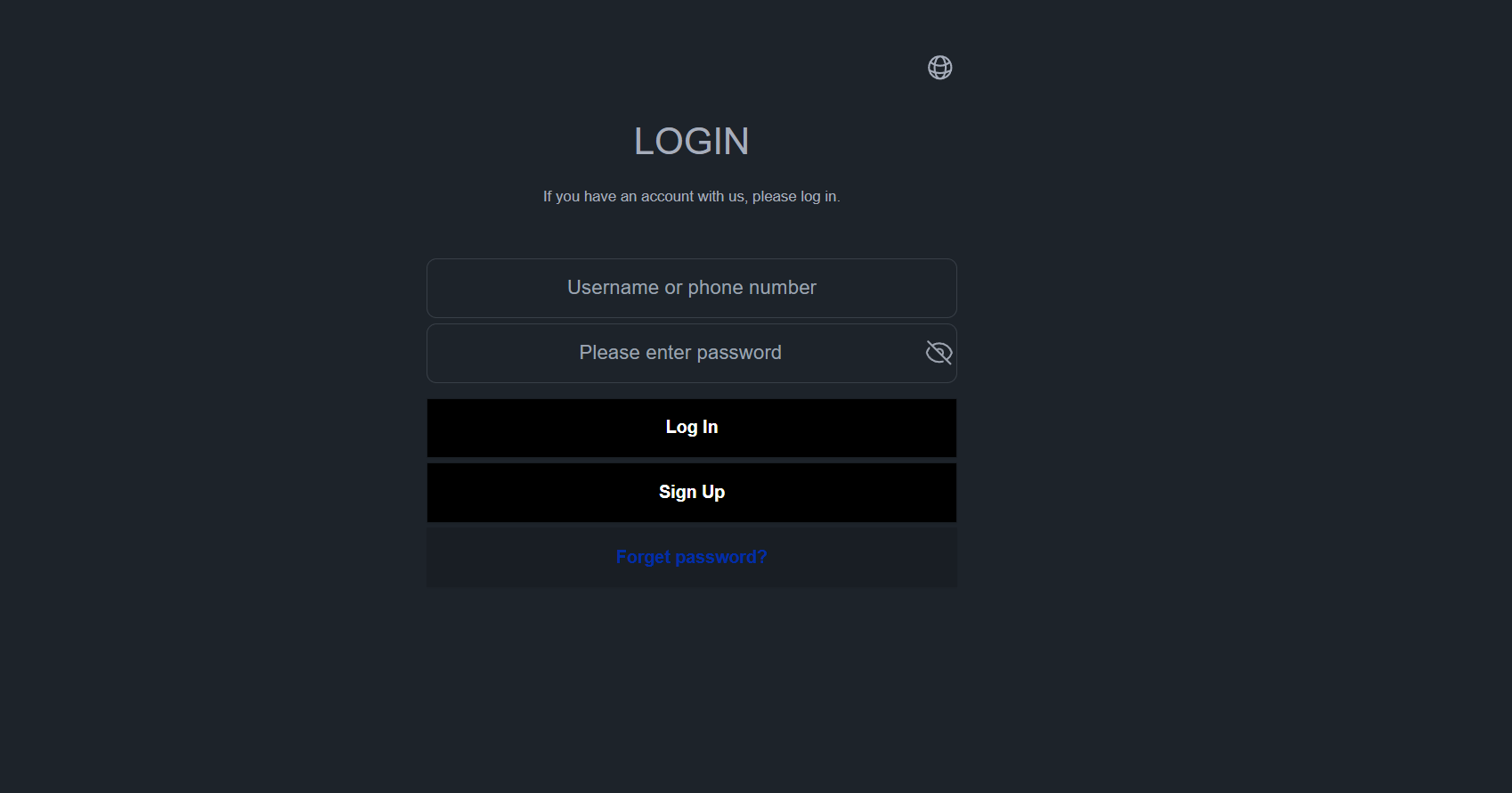 | aldosopy[.]comh5[.]aldosop[.]com… |
| Asda | 12abb97f.u.fn03[.]vip | asda.aseasda[.]com 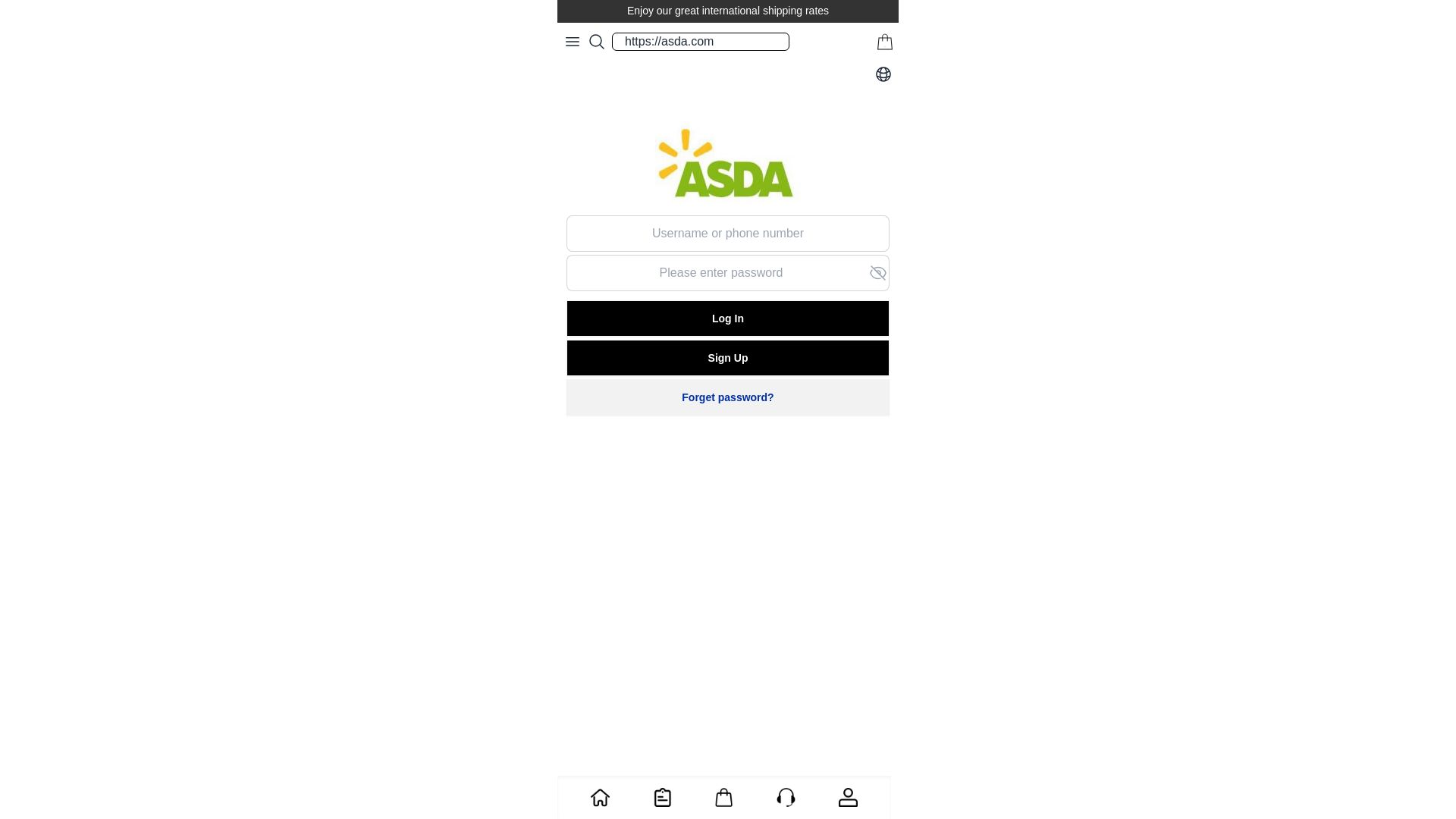 | asda[.]assedda[.]comasda[.]assedaa[.]com… |
| Michael Kors | 12abb97f.u.fn03[.]vip | bcbdsgs[.]com 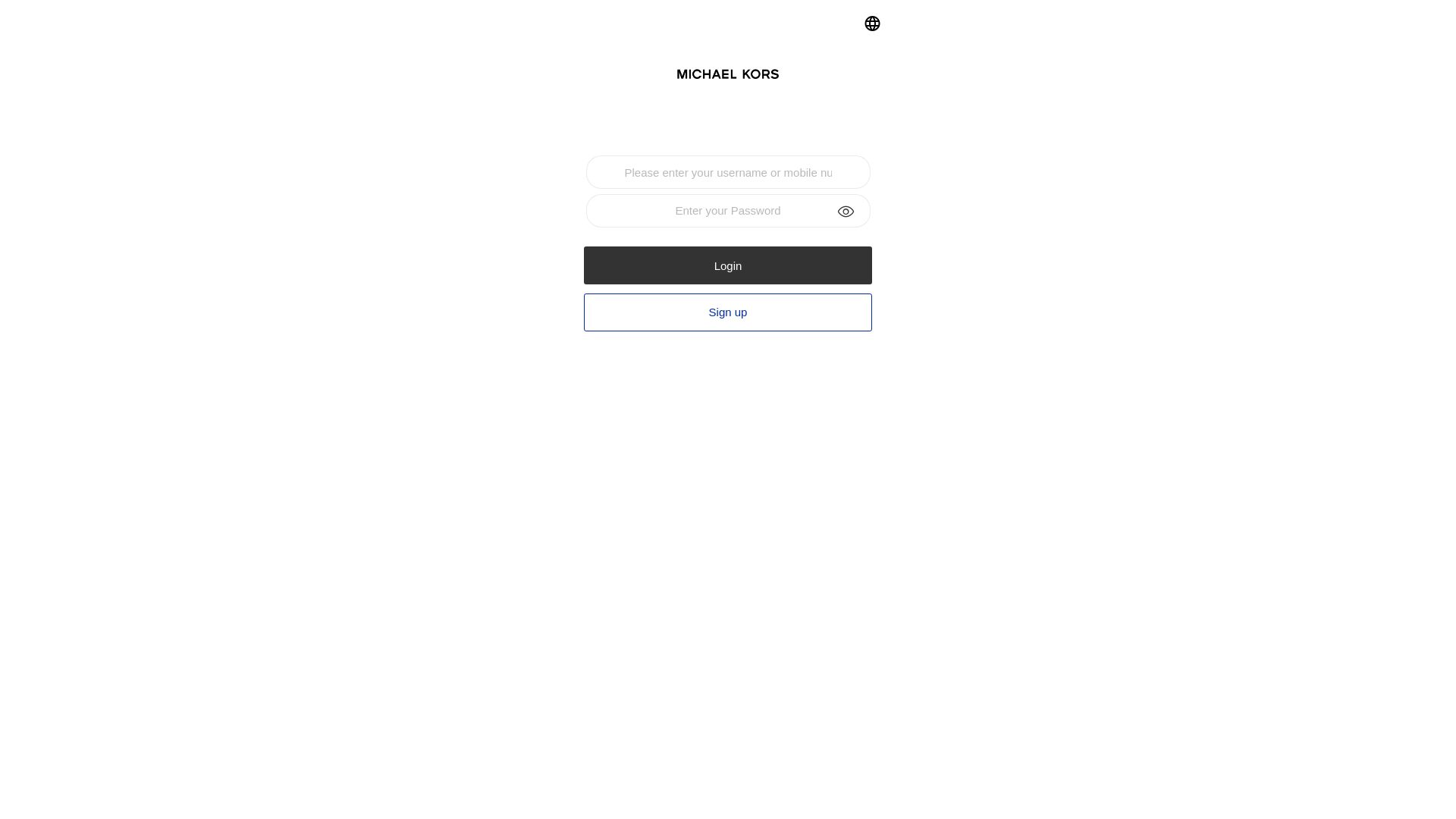 | |
| Bonanza | 12abb97f.u.fn03[.]vip | bonanza.jdfraa[.]com  | jdfraa[.]shopjdfroa[.]com… |
| Cartier | 12abb97f.u.fn03[.]vip | cartier.cartierate[.]com  | |
| Cash Rewards | 12abb97f.u.fn03[.]vip | casher.cashewargi[.]com 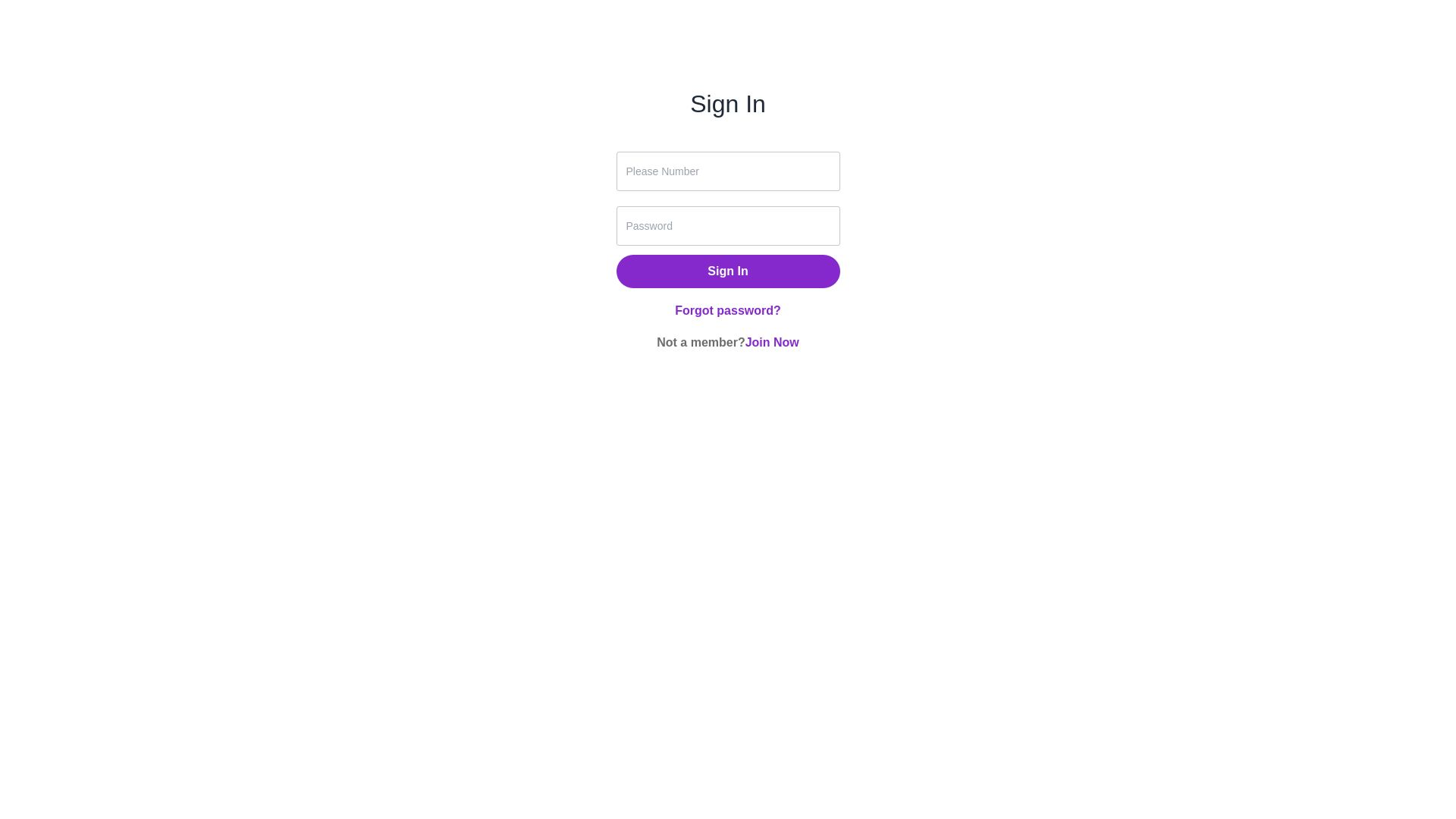 | |
| Chanel | 12abb97f.u.fn03[.]vip | cjmall01[.]com  | |
| Rakuten | 12abb97f.u.fn03[.]vip | ebate.ebatshop[.]com 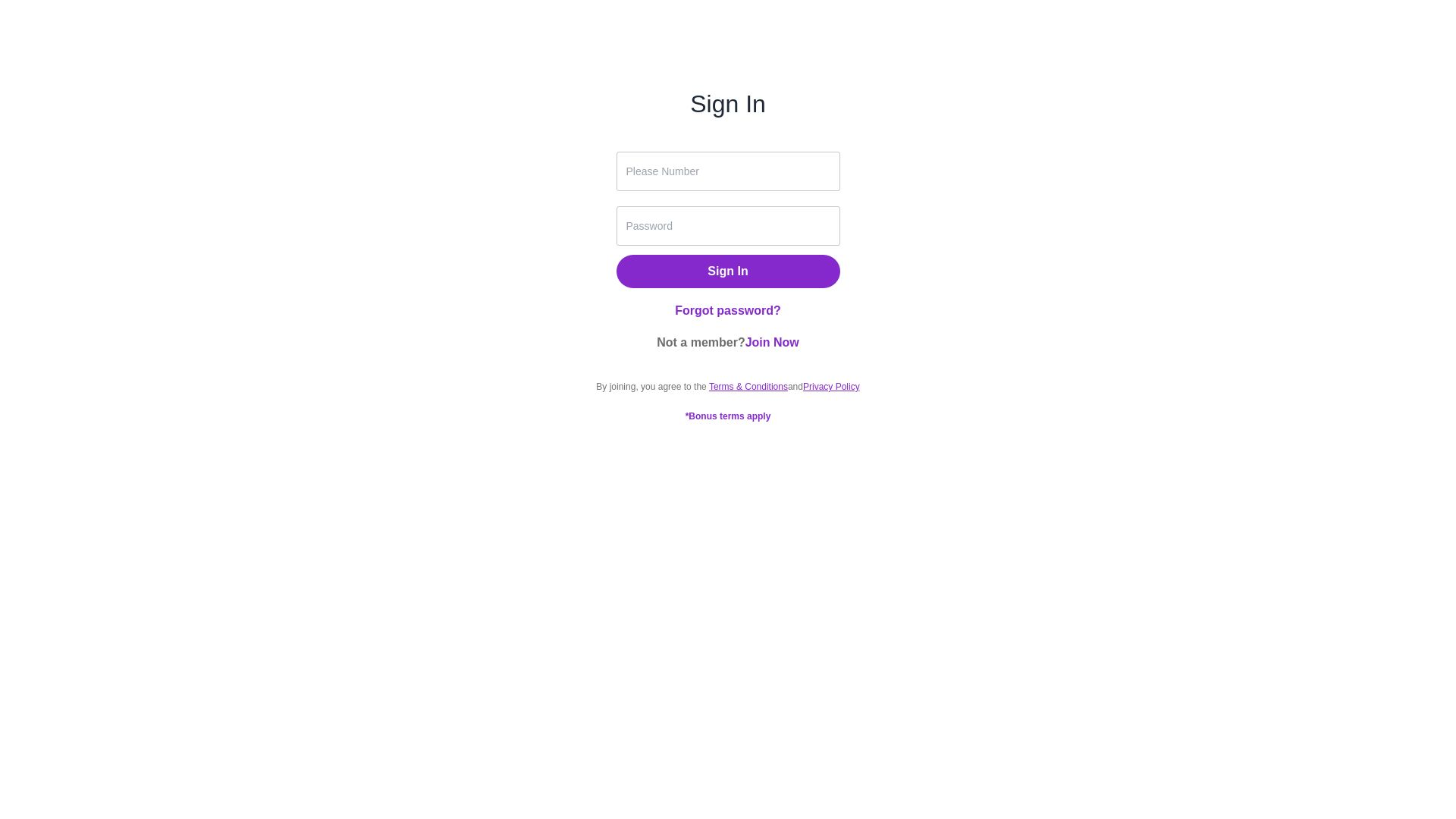 | |
| Ebay | 12abb97f.u.fn03[.]vip | ebay.ebayshoo[.]com 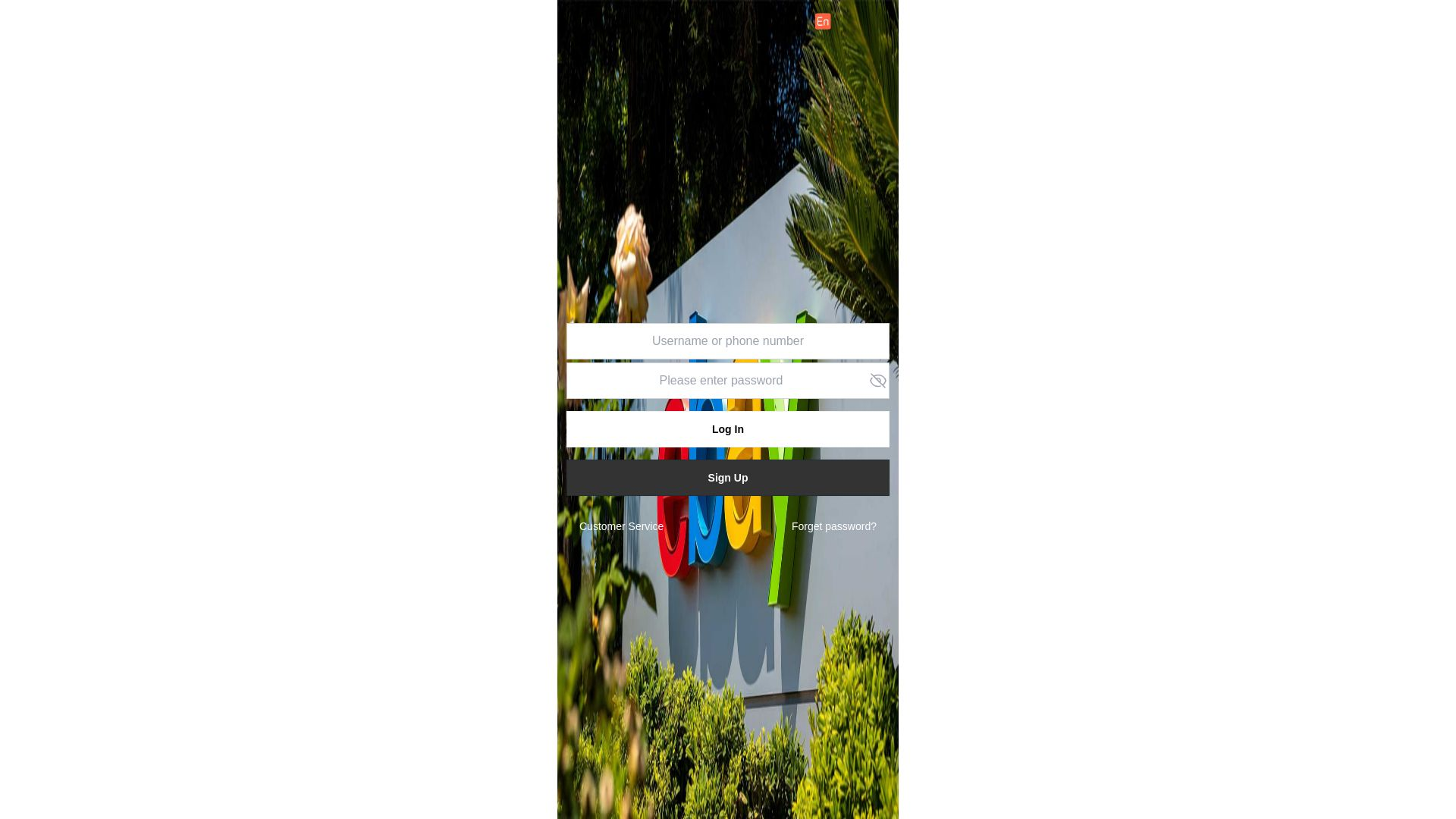 | eby[.]ebayshos[.]comeby[.]ebanyshop[.]com… |
| Etsy | 12abb97f.u.fn03[.]vip | etsy.etsyshop1[.]com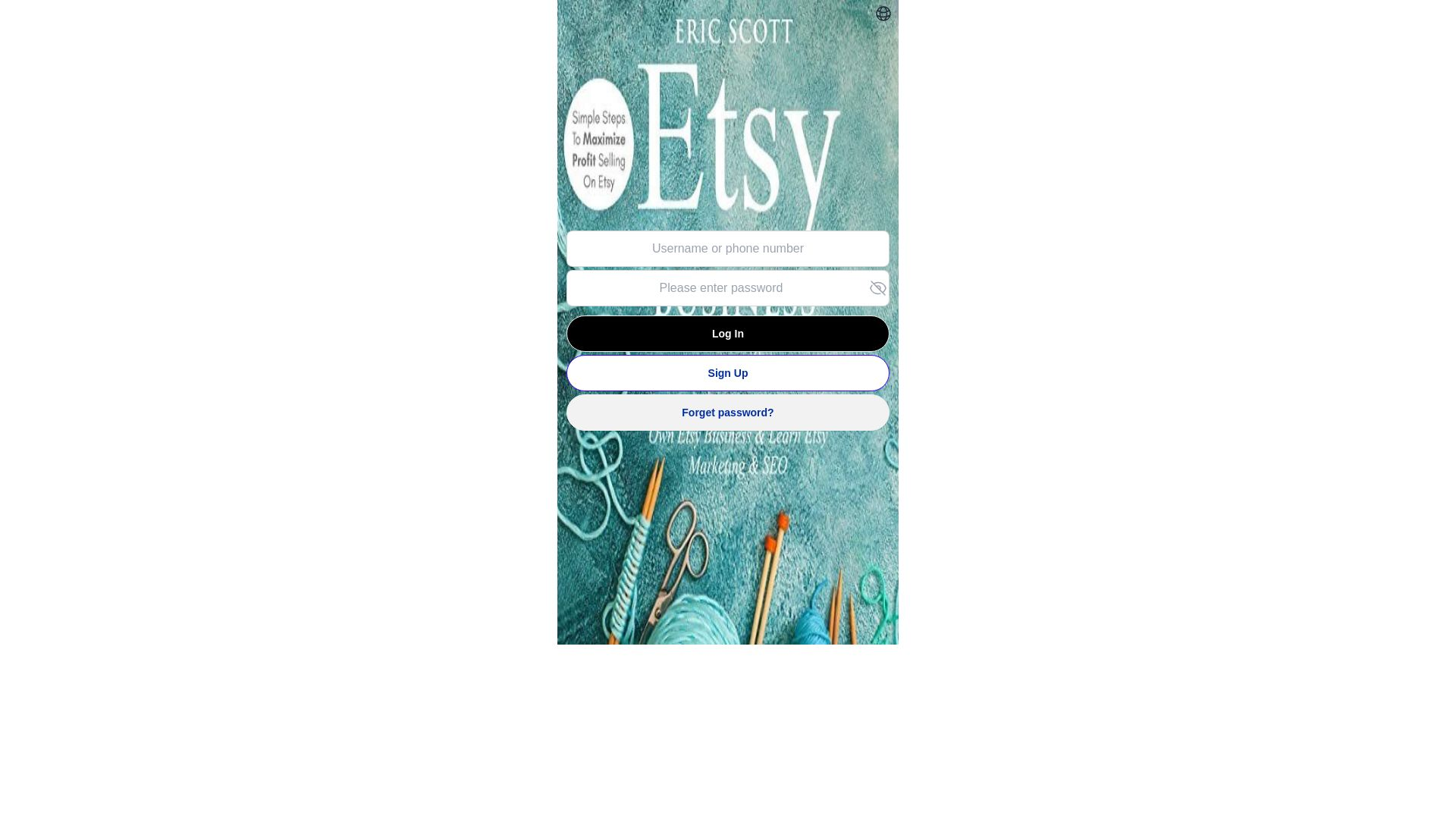 | |
| Macy’s | 12abb97f.u.fn03[.]vip | haodeac[.]com  | |
| Lotte Mart | 12abb97f.u.fn03[.]vip | lotasea[.]com 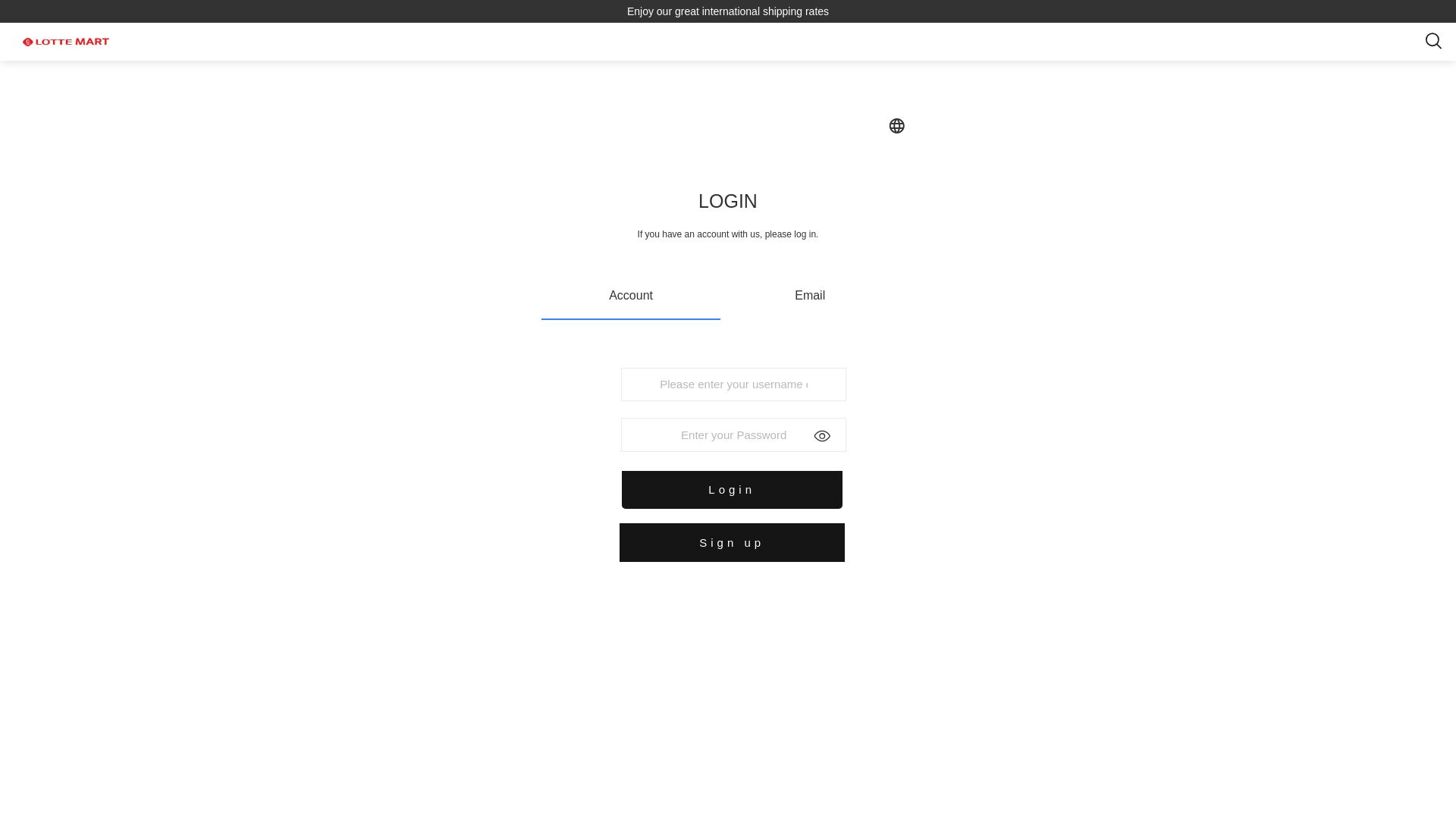 | |
| Neiman Marcus | 12abb97f.u.fn03[.]vip | marcus.marcudk[.]com 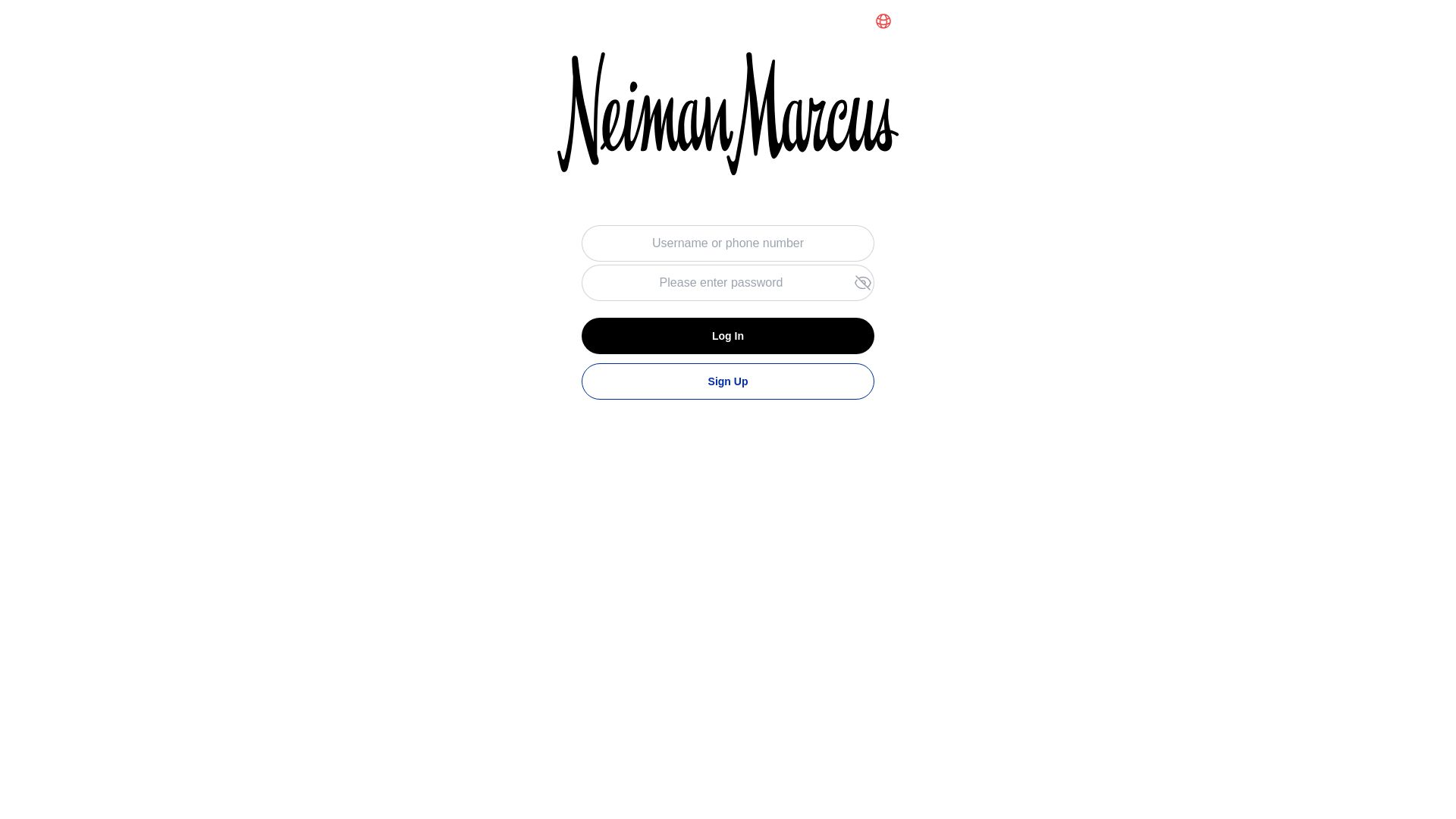 | marcus[.]marcudk[.]netmarcus[.]marcufu[.]net… |
| Tiffany & Co | 12abb97f.u.fn03[.]vip | tiffa.tiffyfy[.]net 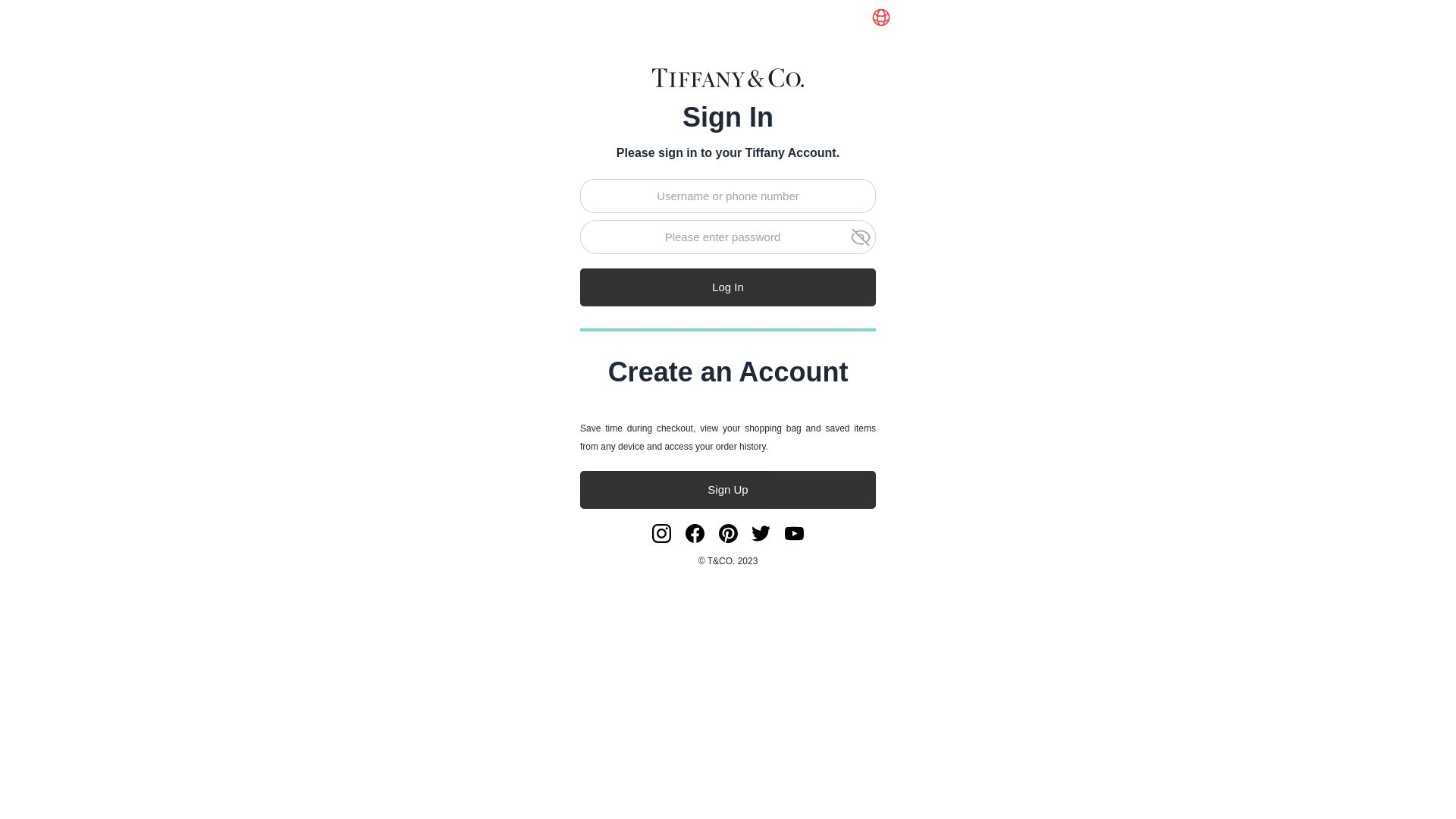 | |
| OnBuy[.]com | sonbuyre[.]com | sonbuyue[.]comsonbuyue[.]net… | |
| Saks Fifth Avenue | sakoffhue[.]com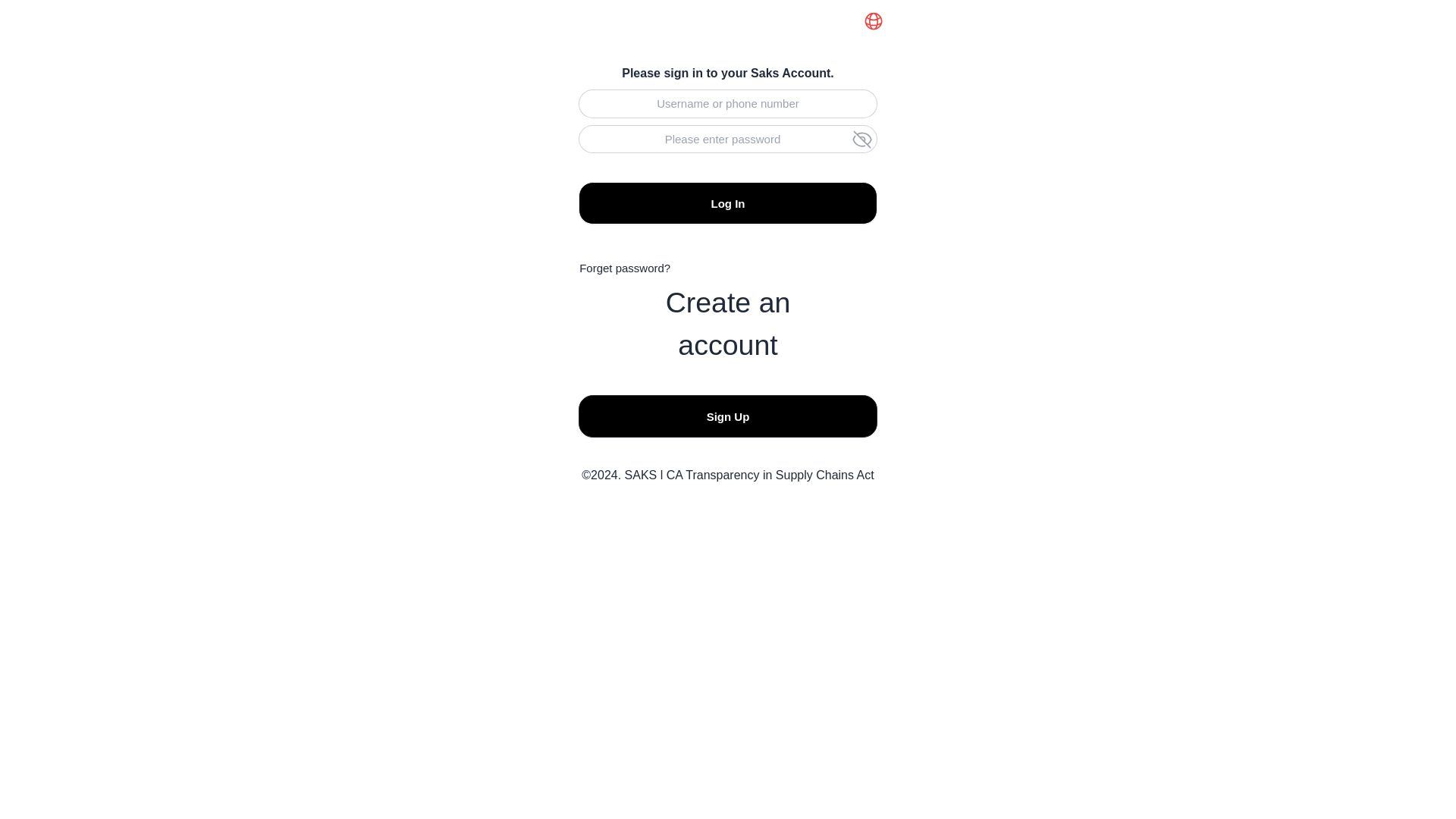 | sakoffirg[.]comsakofforg[.]net… | |
| Gilt Groupe | giltql[.]net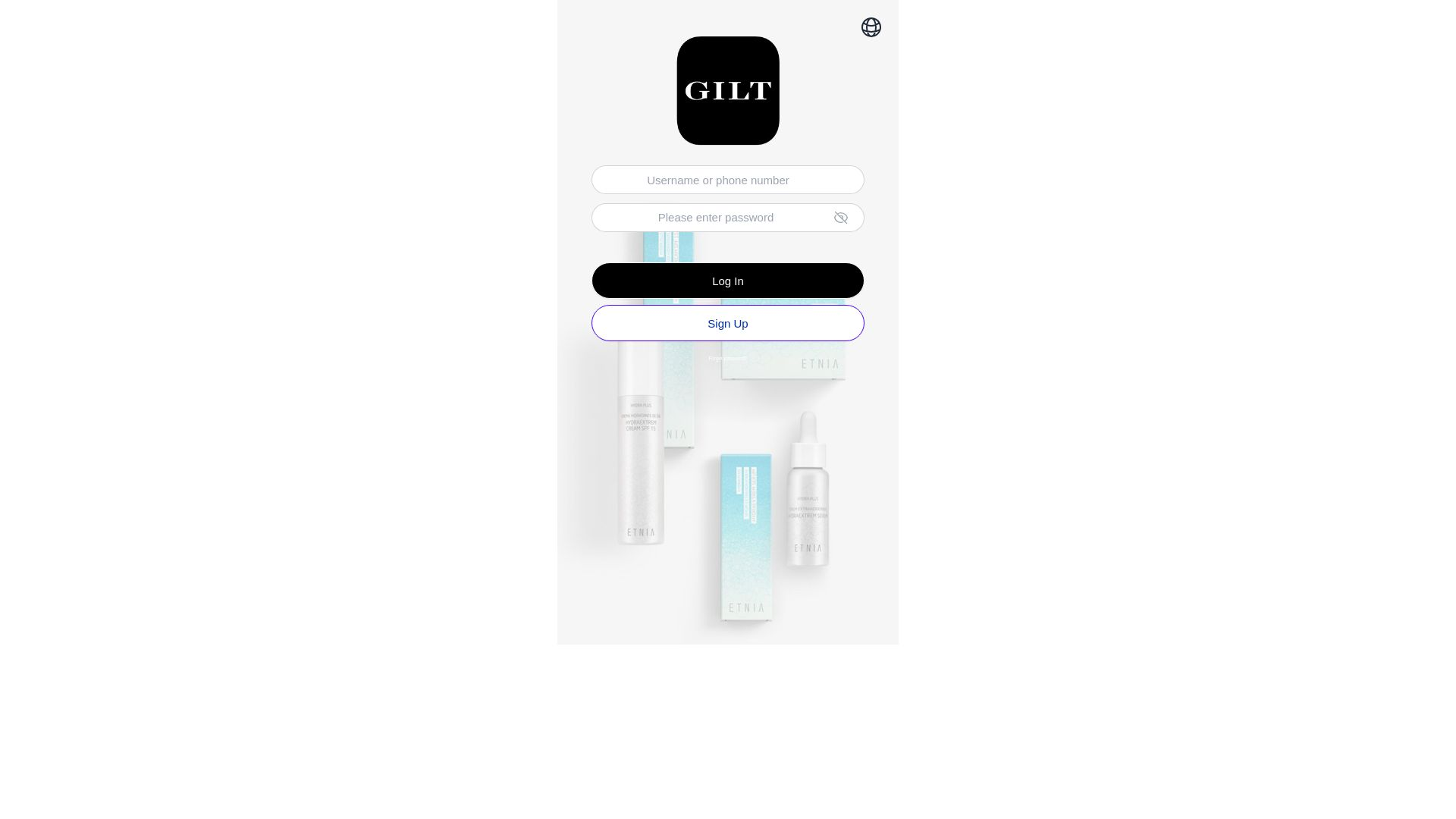 | giltbl[.]comgiltql[.]com | |
| Coach | coachoph[.]com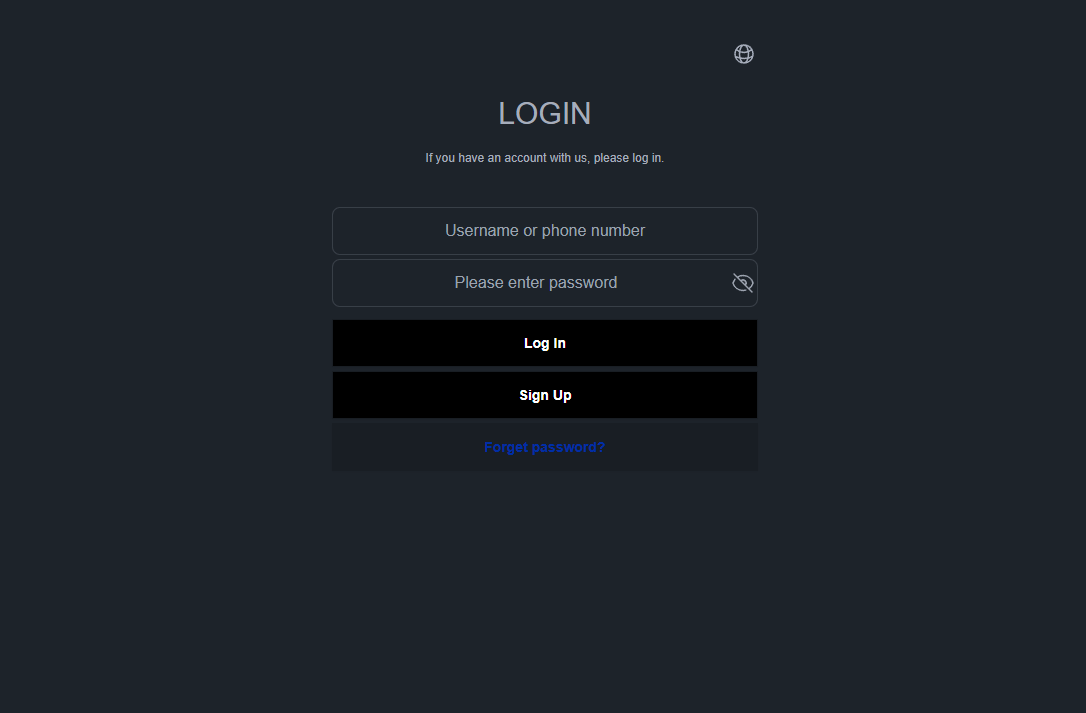 | coachbir[.]comcoachoig[.]com | |
| LVMH | milvmhshop[.]com | slvmgo[.]netslvmgo[.]com… | |
| Inditex (inditex[.]com) | inditetx[.]net | inditetx[.]topinditetx[.]com… | |
| Valentino | valentinogtm[.]com |
Phishing threat actor
Our team discovered approximately 650 unique domains hosted on one specific FUNNULL CNAME: 12abb97f.u.fn03[.]vip
We soon realized that a chunk of these were pig butchering/investment phishing login pages, such as coroexchange[.]com:
Beyond the pig butchering sites, the only other websites hosted on this CNAME all appeared to be a new retail phishing campaign targeting major Western brands, with phishing login pages such as bonanza.jdfraa[.]com:

Phishing kit similarities
The phishing websites attempt to capture user credentials. Many of these phishing pages are hosted within a subdomain and on a specific page—attempting to access the root domain results in a 404 error.
The sites are also built using similar code (we are sharing more details about this privately with our Enterprise customers and law enforcement), and have similar server response codes.
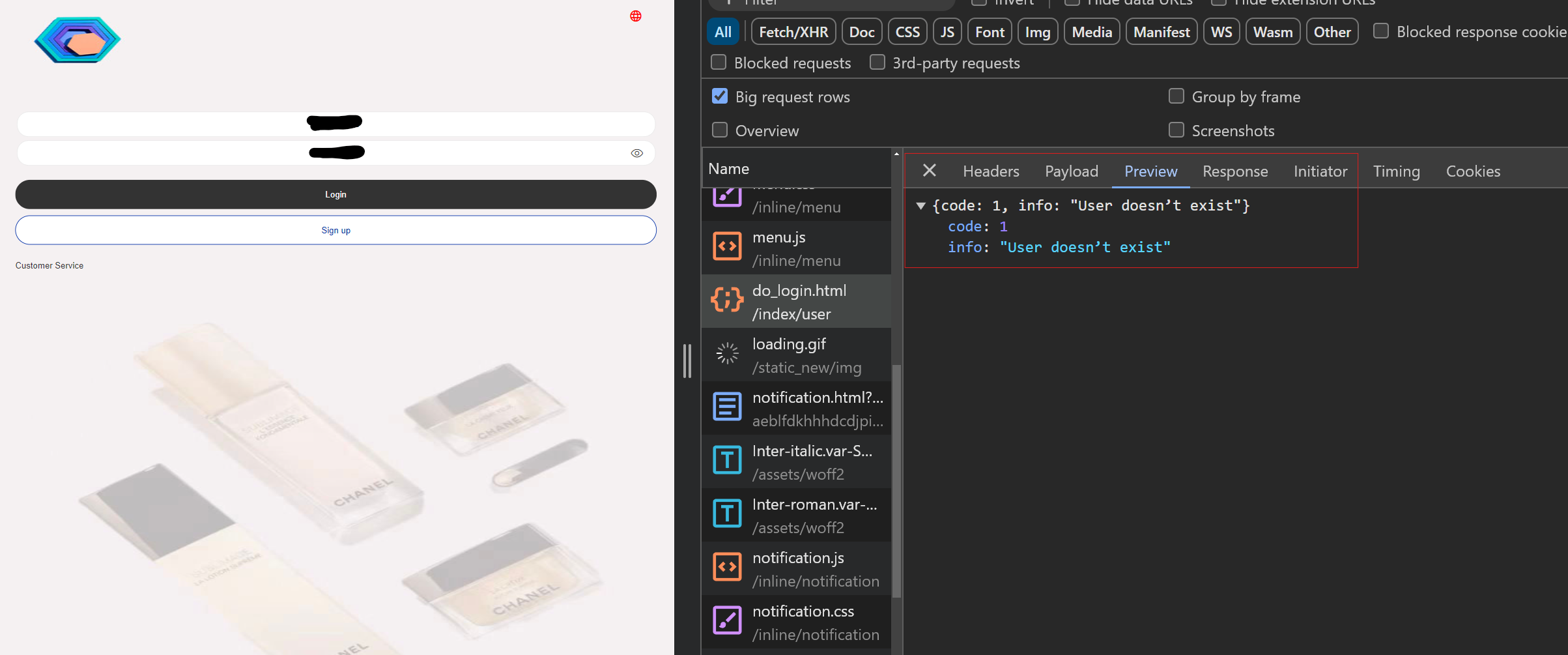
On the Chanel phishing page (cjmall01[.]com/index/user/logins.html), as soon as you enter login credentials and submit the form, a request is made to the “do” endpoint “/do_login.html” within the same /user directory. The request includes a payload with the username and password, and the response includes the message “User doesn’t exist.”
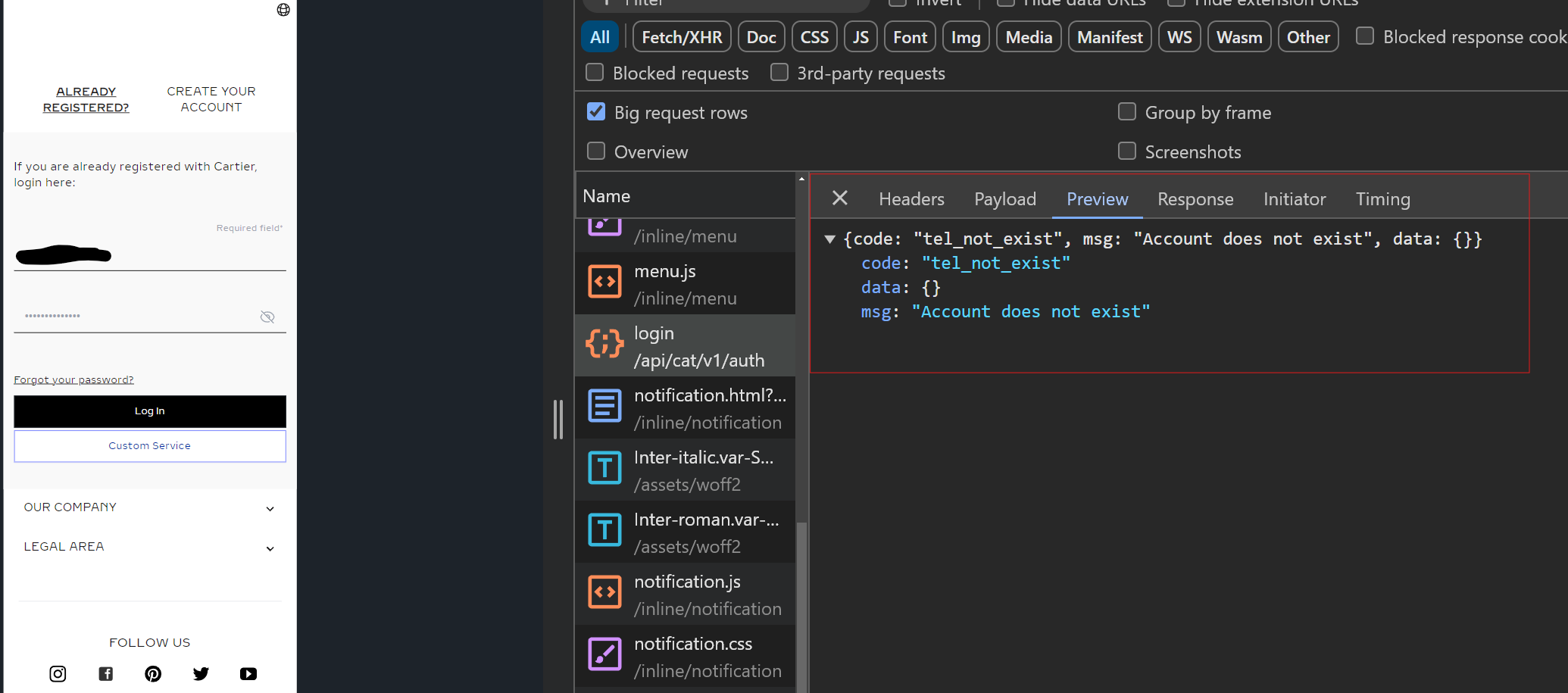
On the Cartier phishing page (cartier.cartierate[.]com/login), as soon as you enter login credentials and submit the form, a request is made to an “auth” login endpoint (cartier.cartierate[.]com/api/cat/v1/auth/login).
The request includes a payload with the username and password, and the response includes the message “Account does not exist”, with a code for “tel_not_exist.”
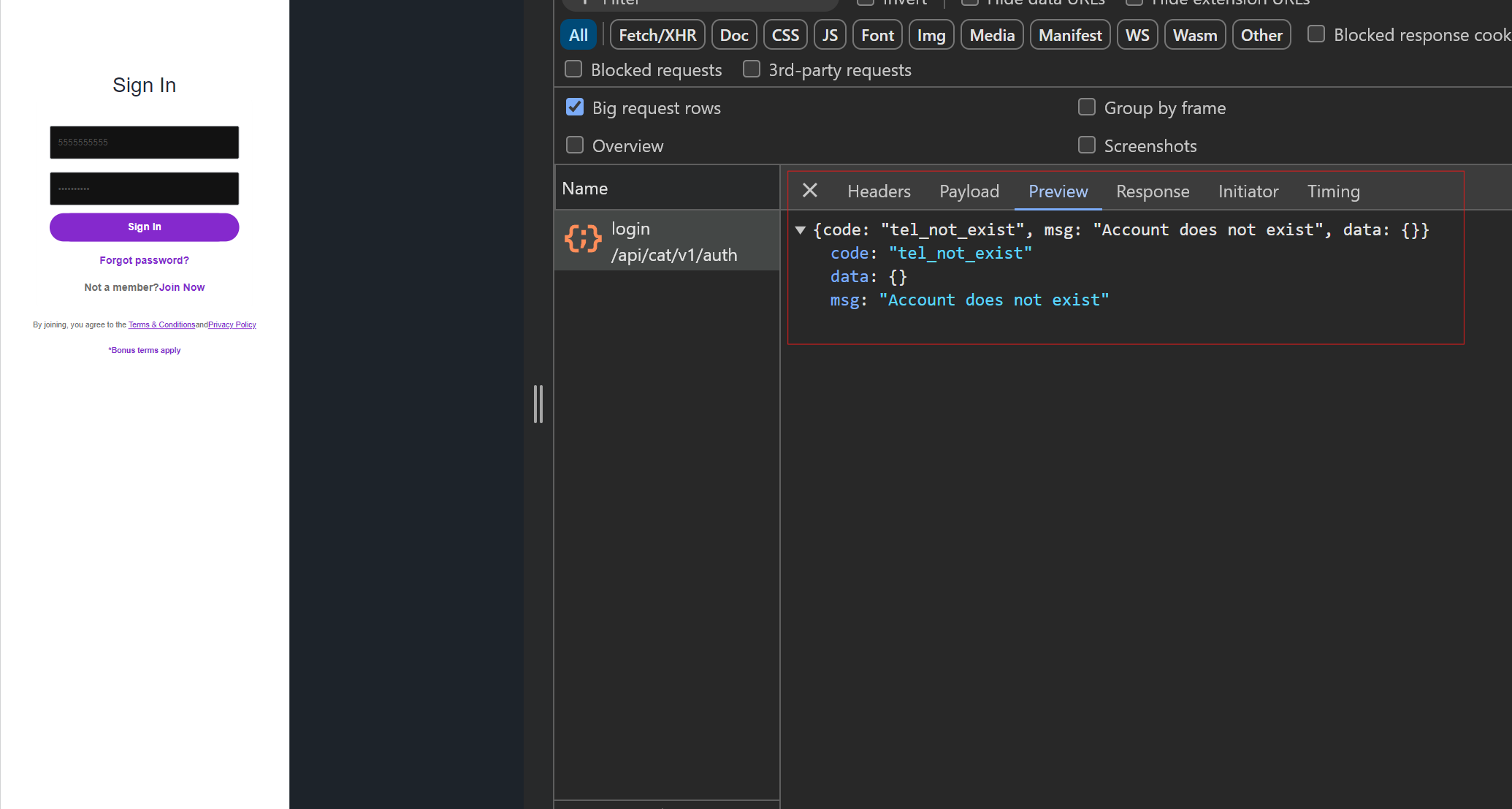
Entering login credentials and submitting the form at the Rakuten phishing page (ebate.ebatshop[.]com/login), makes a request to an “auth” login endpoint (ebate.ebatshop[.]com/api/cat/v1/auth/login).
The page and directory structure of “/API/cat/v1/auth/login”, the request with a payload containing the username and password, and the response message are all the same as those seen on the Cartier phishing page – further indicating a common threat actor behind these FUNNULL-hosted retail phishing websites.
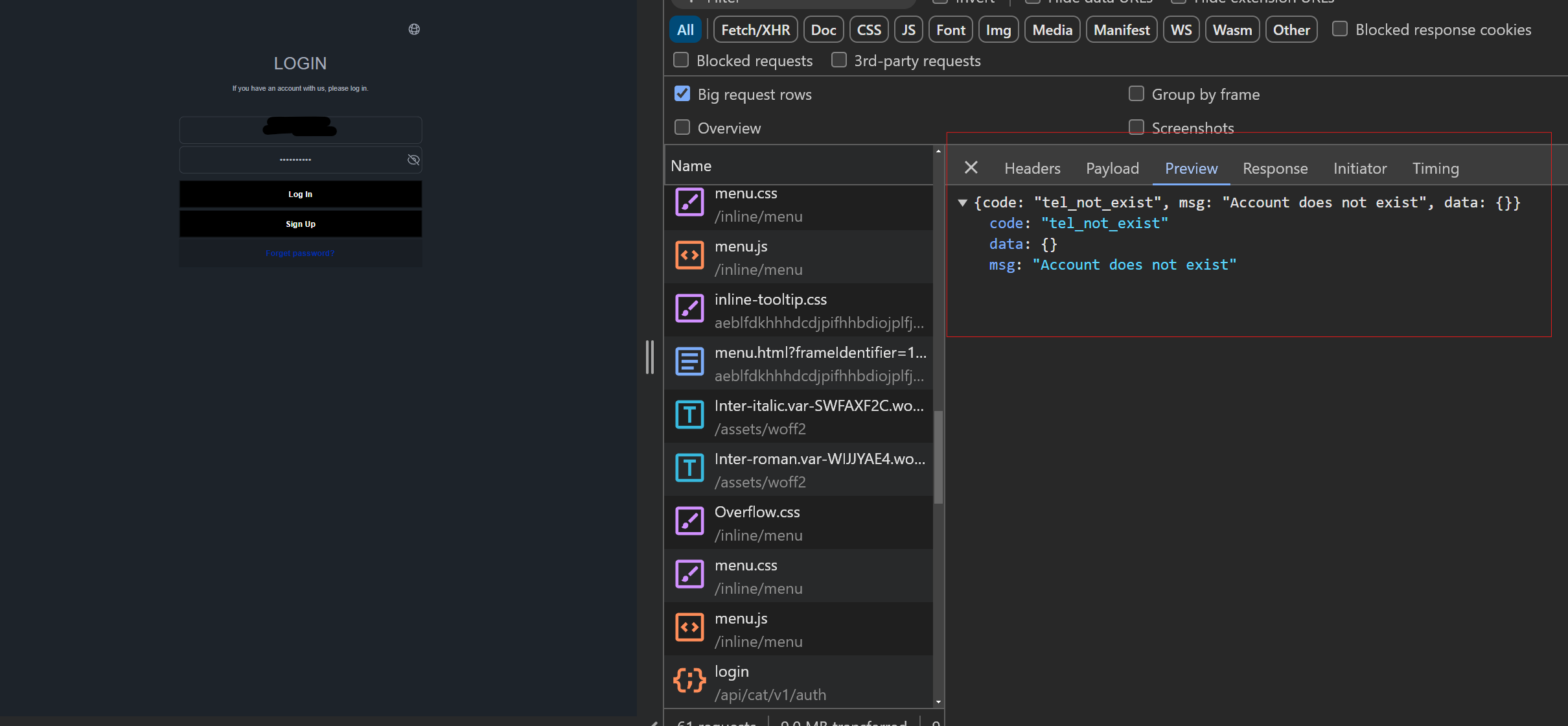
The Aldo phishing page (aldo.shopaldo1[.]com/login) and request results made to the “auth” login endpoint (aldo.shopaldo1[.]com/api/cat/v1/auth/login) also yield the same page, directory structure of “/api/cat/v1/auth/login”, message, and code as seen on the Cartier and Rakuten phishing pages.
Our Analysts discovered one final commonality between these phishing web pages which further cements our hypothesis that they are operated by the same threat actor.
For operational security purposes, however, we are only sharing this information with our Enterprise clients and law enforcement.
Polyfill supply chain scandal affects 110,000+ websites, raises additional questions about FUNNULL
In February 2024, FUNNULL took over polyfill[.]io, a legacy domain used for JavaScript code embedded into hundreds of thousands of the biggest websites on the Internet.
FUNNULL modified the JavaScript polyfill[.]js to inject malware onto mobile devices. A few months later, the first reports of malicious redirects fired through this JavaScript/domain were made public.
The Founder of SanSec, Willem de Groot, whose company was the first to report about the malicious polyfill[.]io redirections, clarified on Twitter that the redirections were to an Asian gambling website, writing, “Except for some laughably bad monetization? They controlled 110k sites, but redirected mobile users to an Asian gambling site.”
More than 110,000 websites that have polyfill[.]js library embedded in their systems have been affected by the polyfill[.]io supply chain attack, which redirects some mobile users to an “Asian gambling website.”
While popular CDNs (such as Cloudflare, Fastly, or Amazon Cloudfront) play legitimate roles in routing traffic across the internet, less reputable CDNs can add a layer of complexity to rooting out malicious threat actors. With no clear process provided on its website, FUNNULL CDN makes takedown requests of suspicious sites more difficult – if not impossible – to secure.
Bleeping Computer reported that when polyfill[.]io was purchased, project developer Andrew Betts warned that he never owned the polyfill[.]io site and advised all websites to remove it immediately. To reduce the risk of a potential supply chain attack, Cloudflare and Fastly set up their own mirrors of the polyfill[.]io service so websites could use a trusted service.
Google is actively blocking ads for e-commerce sites that use the polyfill[.]js library. It issued a statement about the vulnerability, “Protecting our users is our top priority. We detected a security issue recently that may affect websites using certain third-party libraries. To help potentially impacted advertisers secure their websites, we have been proactively sharing information on how to quickly mitigate the issue.”
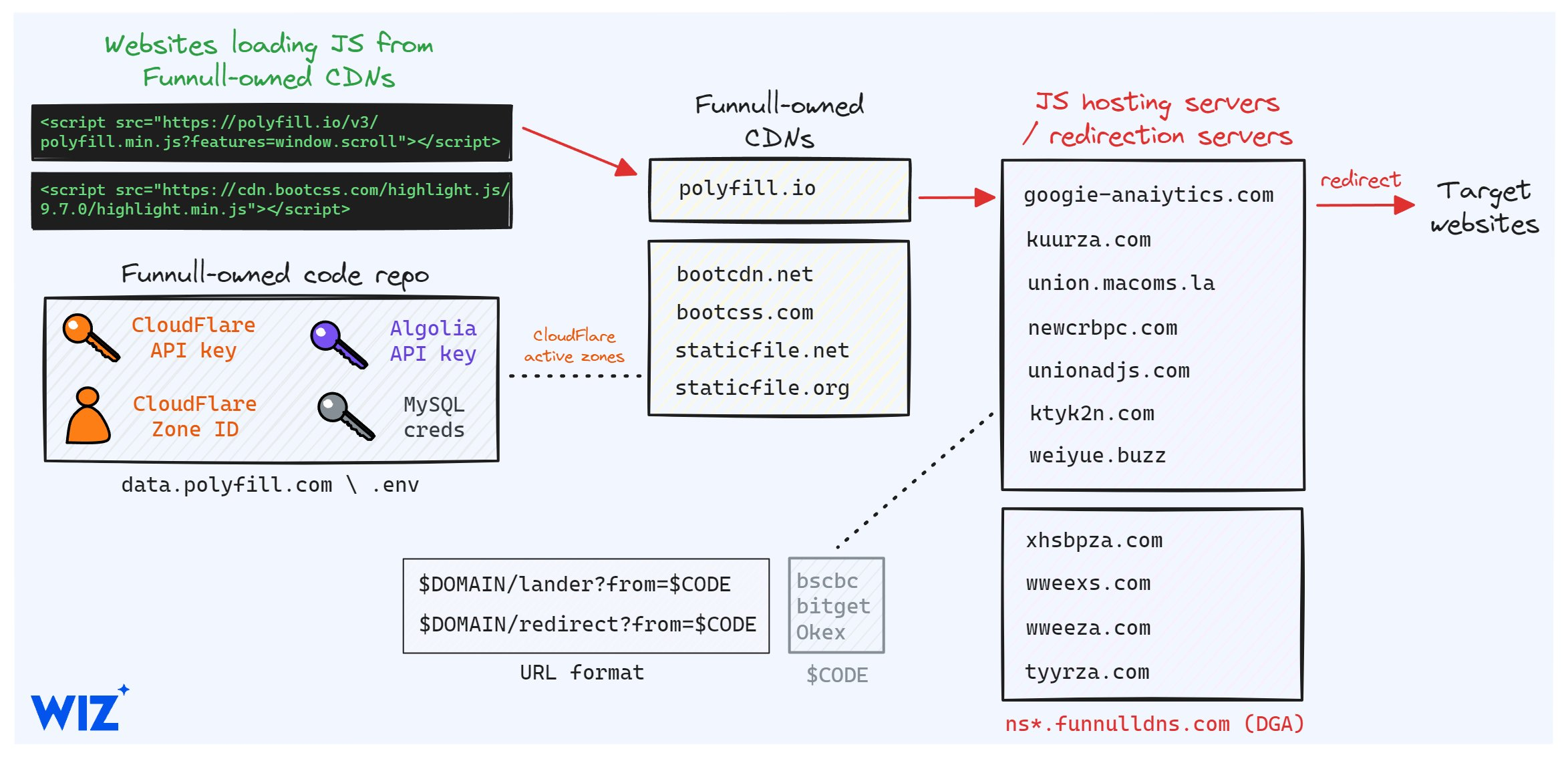
Cybersecurity company Wiz mapped out the details of the FUNNULL CDN infrastructure seen in these malicious redirections. The same organization that owned polyfill[.]io also owned four similar sites for hosting developer resources: bootcdn[.]net, bootcss[.]com, staticfile[.]net, and staticfile[.]org. As of this writing, malicious redirects were not documented on the four other domains.
Additional information
We’re continuing to track FUNNULL CDN’s activity, and we’ll be reporting our findings to the security community in a series of follow-up reports.
We’ve also published a TLP Amber report for Enterprise users that contains links to the specific queries we’ve used to identify and traverse Triad Nexus’ FUNNULL CDN’s infrastructure—including proprietary queries that we’ve omitted from this blog for operational security reasons.
Mitigation
Silent Push believes all FUNNULL domains offer some level of risk.
Our analysts have constructed a Silent Push IOFA Feed that provides a partial list of FUNNULL Indicator of Future Attack domains focused on their scams, along with an IOFA Feed containing suspect FUNNULL IPs.
Silent Push IOFA Feeds are available as part of an Enterprise subscription. Enterprise users can ingest IOFA Feed data into their security stack to inform their detection protocols, or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
Register for Community Edition
Silent Push Community Edition is a free threat-hunting and cyber defense platform featuring a range of advanced offensive and defensive lookups, web content queries, and enriched data types.
Click here to sign up for a free account.
Triad Nexus Indicators of Future Attacks (IOFAs)
Here is a sample list of IOFAs – our full list is available for enterprise users. Silent Push Enterprise clients have access to a domain and IP feed containing all the FUNNULL infrastructure.
- vk6a2rmn-u.funnull[.]vip
- 6ce0a6db.u.fn03[.]vip
- vk6a2rmn-u.funnull01[.]vip
- 6ce0a6db.u.fn03[.]vip
- www.cmegrouphkpd[.]info
- funnull[.]vip
- funnull01[.]vip
- fn03[.]vip
- acb[.]bet
- hiflyk47344[.]top
- Polyfill[.]io
- 6289[.]com
- threevip[.]cc/?u=6289[.]com
- 15991t[.]com/
- 12abb97f.u.fn03[.]vip
- aldo.shopaldo1[.]com
- aldosopy[.]com
- h5[.]aldosop[.]com
- asda.aseasda[.]com
- asda[.]assedda[.]com
- asda[.]assedaa[.]com
- bcbdsgs[.]com
- bonanza.jdfraa[.]com
- jdfraa[.]shop
- jdfroa[.]com
- cartier.cartierate[.]com
- casher.cashewargi[.]com
- cjmall01[.]com
- ebate.ebatshop[.]com
- ebay.ebayshoo[.]com
- eby[.]ebayshos[.]com
- eby[.]ebanyshop[.]com
- etsy.etsyshop1[.]com
- haodeac[.]com
- lotasea[.]com
- marcus.marcudk[.]com
- marcus[.]marcudk[.]net
- marcus[.]marcufu[.]net
- tiffa.tiffyfy[.]net
- sonbuyre[.]com
- sonbuyue[.]com
- sonbuyue[.]net
- sakoffhue[.]com
- sakoffirg[.]com
- sakofforg[.]net
- giltql[.]net
- giltbl[.]com
- giltql[.]com
- coachoph[.]com
- coachbir[.]com
- coachoig[.]com
- milvmhshop[.]com
- slvmgo[.]net
- slvmgo[.]com
- inditetx[.]net
- inditetx[.]top
- inditetx[.]com
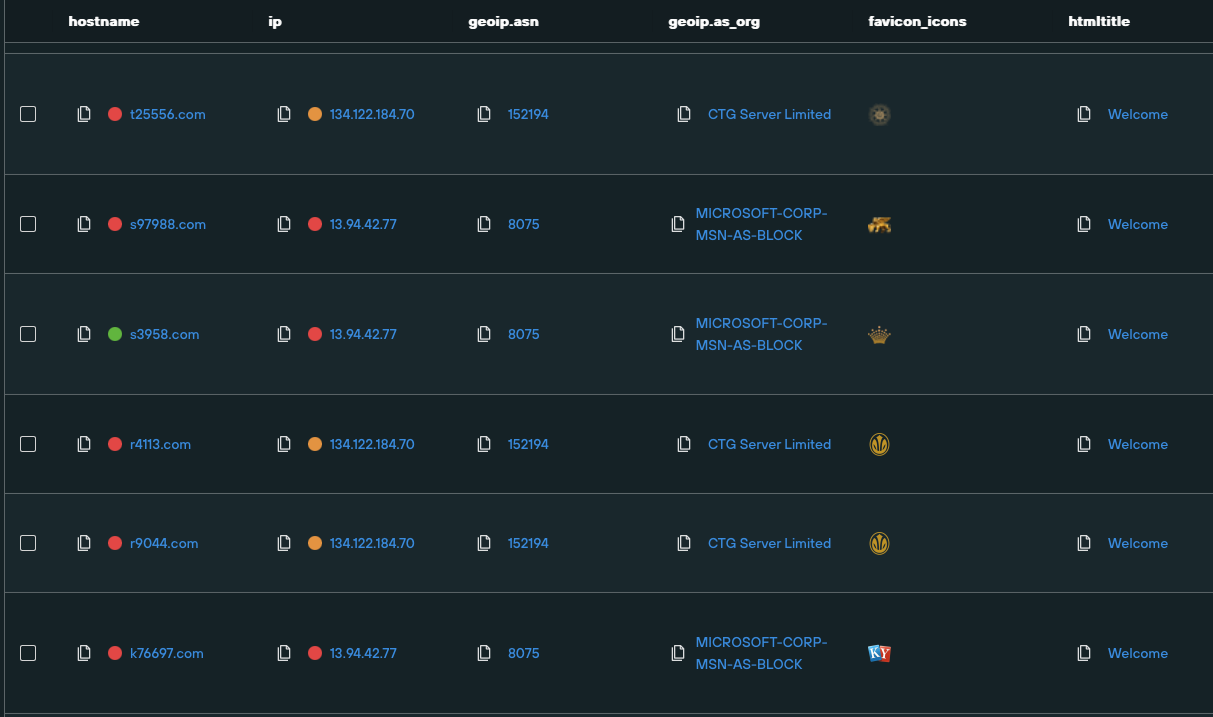
- t25556[.]com
- s97988[.]com
- s3958[.]com
- r4113[.]com
- r0944[.]com
- k76697[.]com
- valentinogtm[.]com


