Data enrichment is a threat intelligence mechanism that allows security teams to pinpoint the origin, function and risk level of a domain or IP address, by applying multiple categories and sub-categories that provide up to 10x more context than standard DNS lookups and queries are able to provide.
Enrichment is less about volume, and more about creating meaningful relationships between billions of disparate data points. Each enrichment category is designed to help defenders and threat hunters track attacker infrastructure across the IPv4 and IPv6 space.
Stale, unenriched DNS data cannot be truly relied upon as an actionable intelligence source. Security teams who don’t perform data enrichment as part of their threat analysis procedures are working with incomplete datasets, which can lead to flawed decision making and a higher risk of intrusion.
Data enrichment using Silent Push
To map out attacker infrastructure, Silent Push collects information across 100+ domain and IP enrichment categories that contextualize an observable’s presence on the Internet, including risk level, web content (headers, hash values, on-page data), certificates, geographic location, passive DNS data, and the reputation of associated infrastructure.
Data enrichment outputs Indicators of Future Attack (IOFAs) – intelligence data that tells security teams where an attack is coming FROM, rather than where it’s BEEN.
Defenders and threat hunters are able to use enriched data to join the dots across the global IPv4 and IPv6 space, and track the underlying infrastructure behind an attack, rather than relying on publicly available post-breach IOCs that rely on a single point in time.
Summary
In this blog, we’ll show you how to enrich a domain or IP, what each enrichment category means, and how to use enriched data in a live environment.
Data independence
We’re often asked how we are able to provide so much categorization for each piece of observable data. We achieve this by collecting and owning our own first-party data, via a concept we call ‘data independence’.
Controlling our own data allows us to add a near-infinite amount of context, and produce operationalized intelligence that’s adaptable to a range of workflows.
Security teams typically have to use somewhere in the region of three to four vendor platforms to gather intelligence. Data enrichment outputs self-contained searchable spaces relating to specific attack vectors, that require zero third-party intervention to turn into useable intelligence.
How to perform data enrichment using Silent Push
Data enrichment can be done in two ways, and is available for both Community and Enterprise users:
- From the search bar on the top right of the platform
- Via the Enrichment menu
Here’s a short YouTube video that covers the basics of how to enrich an observable, and how to interpret the data.
Data enrichment categories
We spread out data enrichment across six bitesize categories, each with its own part to play in telling a story about a domain or IP:
- ‘Enrichment Highlights’
- ‘Basic Information’
- ‘Enriched Attributes’
- ‘Custom Attributes’
- ‘Live Threat Feeds’
- ‘Scan Data’
Each category contains both standardized data, and categorization that is unique to Silent Push. Most of our data enrichment categories aren’t available anywhere else, without performing a considerable amount of supplementary analysis
Let’s take a look at each Enrichment category in turn…
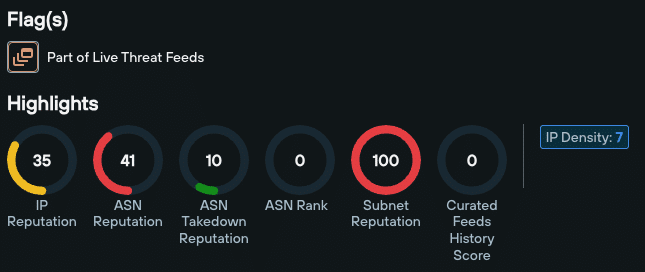
1. ‘Enrichment Highlights’
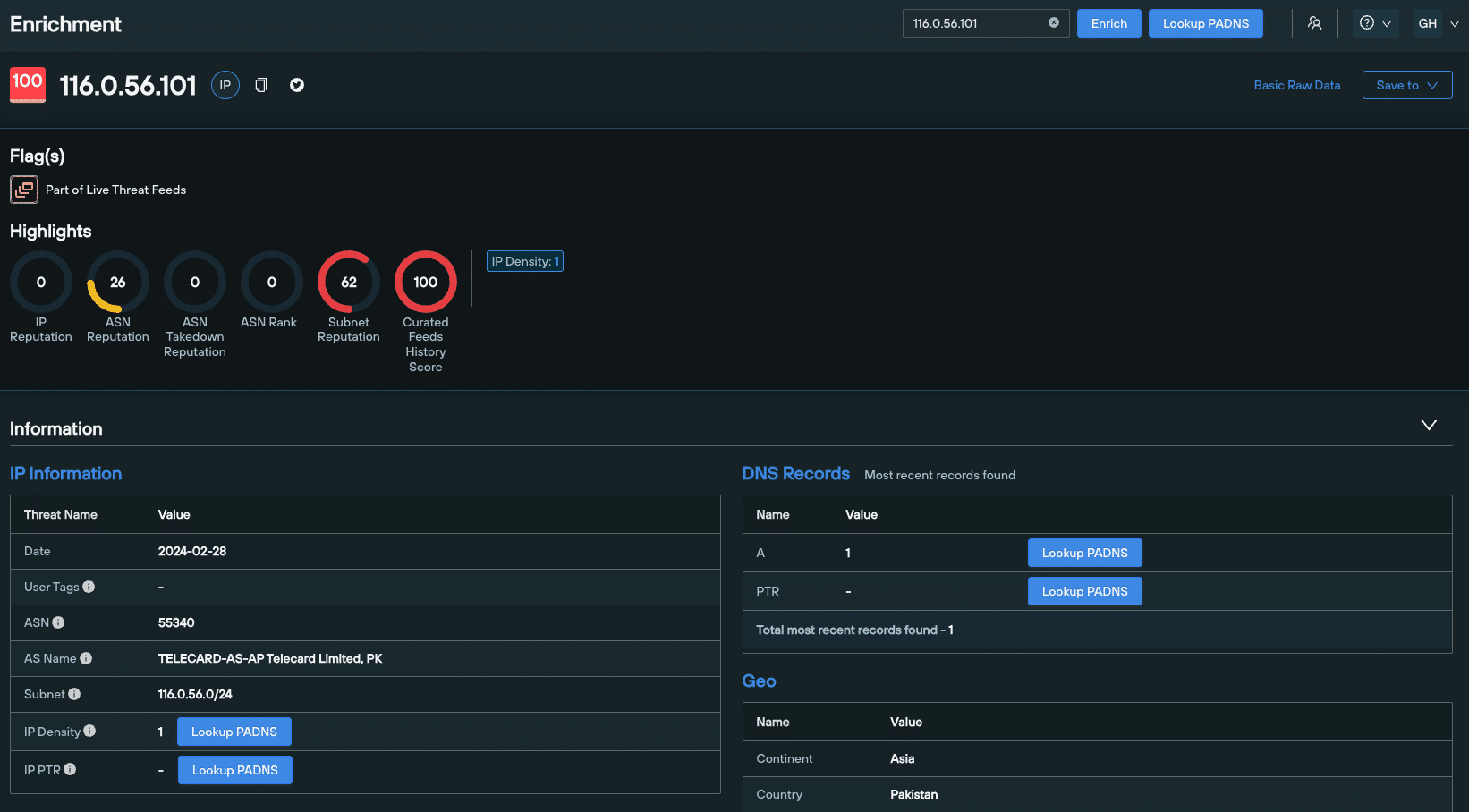
Enrichment Highlights appear at the very top of the Enrichment page. These are a family of scores and numerical values tailored to the enriched data type, that act as reliable indicators of an observable’s risk level.
Data enrichment highlights differ based on the type of observable you’re working with – i.e. a domain or an IPv4/v6 address.
Domain data enrichment highlights include:
- IP reputation
- ASN reputation
- ASN takedown reputation
- ASN Rank
- Subnet reputation
- Curated Feeds History Score
- IP density
- Open S3 buckets
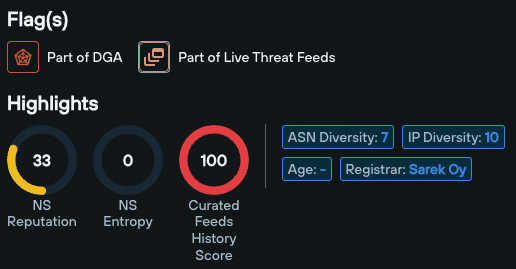
IP data enrichment highlights include:
- NS Reputation
- NS Entropy
- Curated Feeds History Score
- ASN Diversity
- IP Diversity
- Age
- Registrar
- Open S3 buckets
2. ‘Basic Information’
The Domain/IP Information data enrichment sub-category does what it says on the tin – it tells you when a domain or IP was first seen, last seen, its age, and an infratag that summarizes key information.
For domains, WHOIS Information provides standard WHOIS data, related to age, ownership and geographic location.
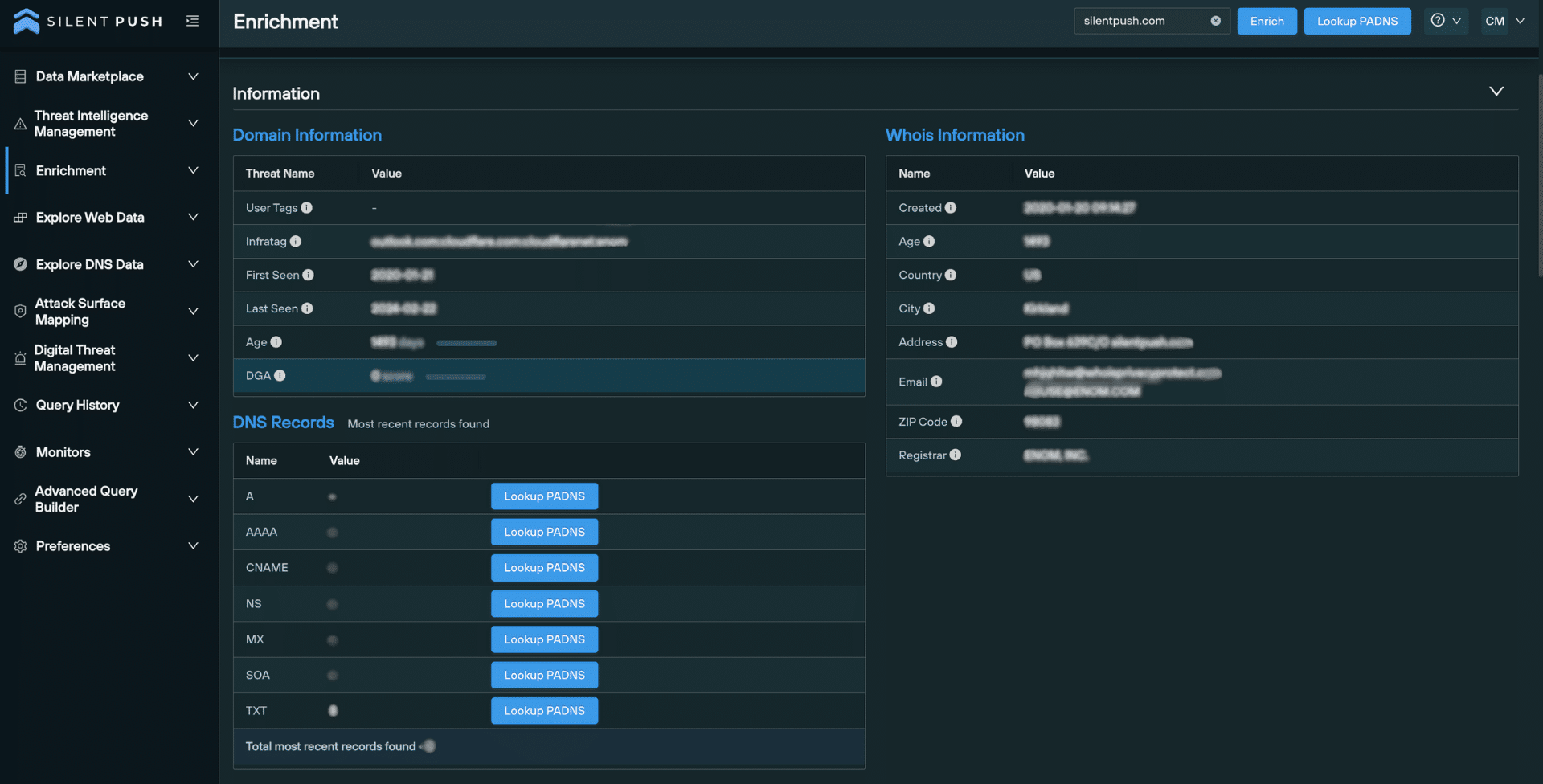
For IP addresses, the Geo sub-category lists the continent, country, and country code.
The DNS Records category details displays a numerical count of visible DNS records per type, and allows you to perform additional passive DNS lookups with one click.
3. ‘Enriched Attributes’
Enriched Attributes outlines a domain or IP’s relationship with the rest of the Internet, including the hosting infrastructure its used over time, its appearance in threat feeds, and how often it’s jumped between nameservers:
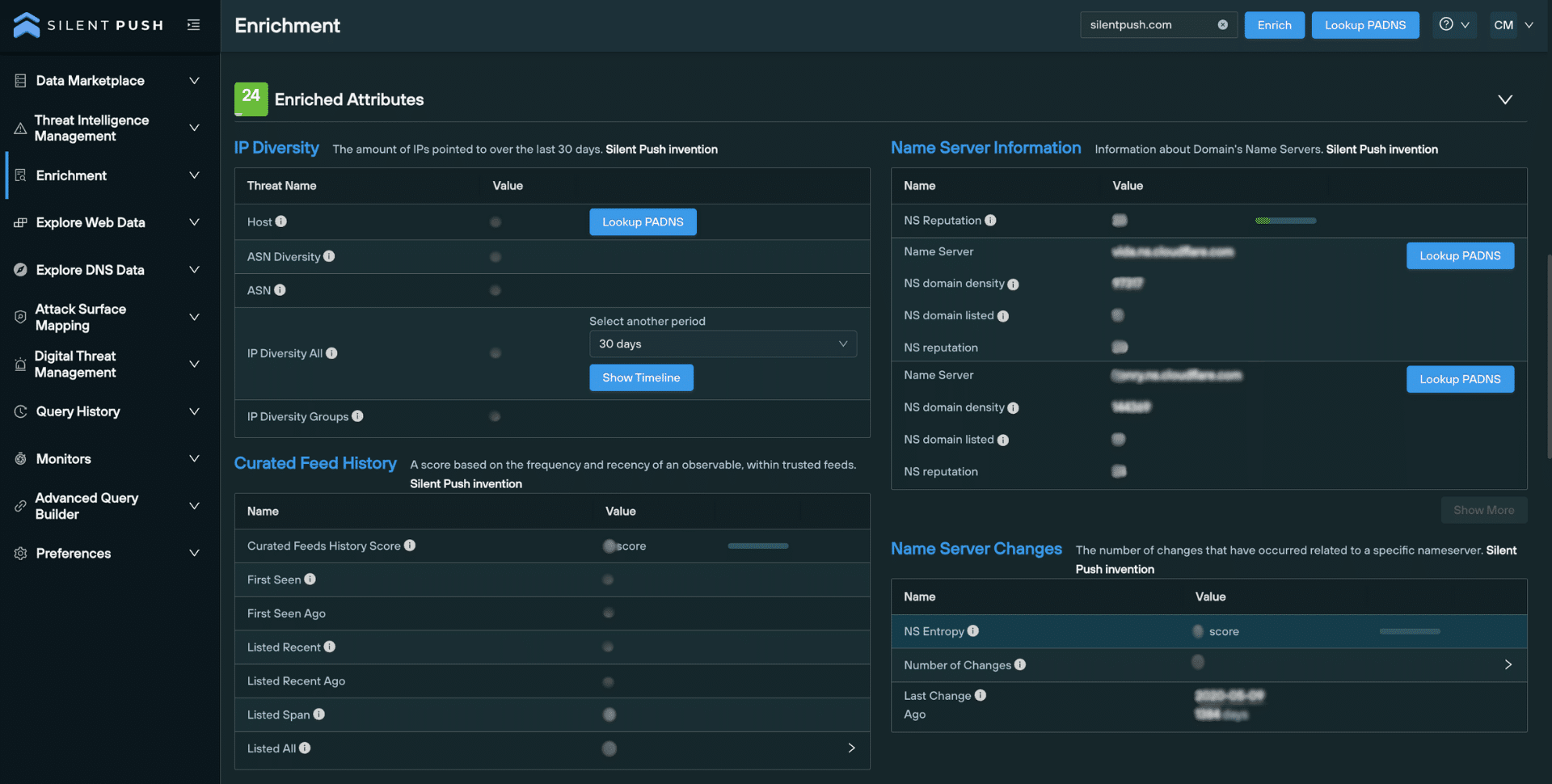
IP Diversity lists the number of unique IP addresses associated with a domain, over a period of time.
Nameserver Information provides info specific to each nameserver used by a domain, including reputation and the number of domains it hosts.
The Nameserver Changes section contains data that shows how often a domain has hopped between nameservers.
Curated Feed History allows you to establish the frequency and recency of an observable’s presence within trusted threat feeds.
4. ‘Custom Attributes’
The Custom Attributes section allows you to specify custom scores that reflect an observable’s risk level, relative to your organization or supply chain’s operation and assets.
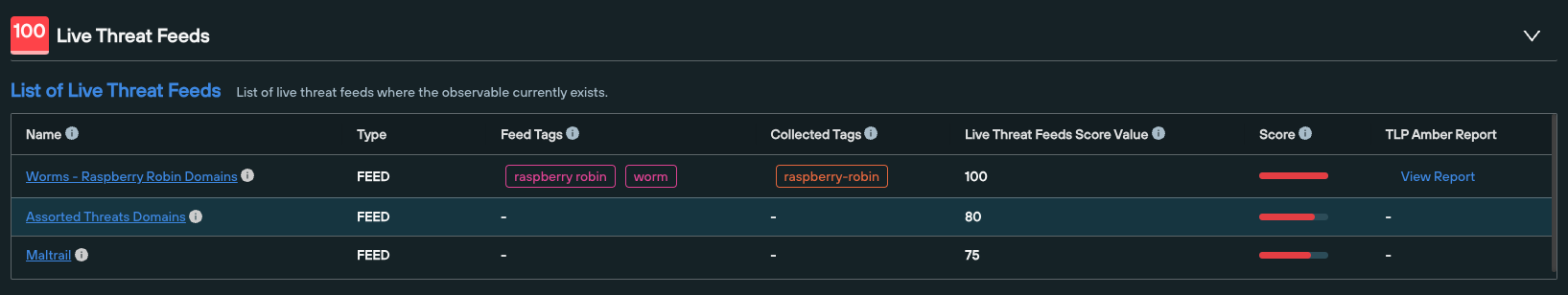
5. ‘Live Threat Feeds’
This category provides a list of feeds that feature a given domain or IP, including any associated TLP Amber reports. This helps security teams validate the risk level of an observable across the IPv4 and IPv6 space, particularly if it appears within multiple feeds.
6. ‘Scan Data’
Scan Data enrichment pulls intelligence from Silent Push’s passive web content database, including certificates, HTML body and title data, favicon hash values and header information.
You can use this data to perform additional pivots that instantly detect matching infrastructure, and hunt for domains that are attempting to circumvent global certificate standards.
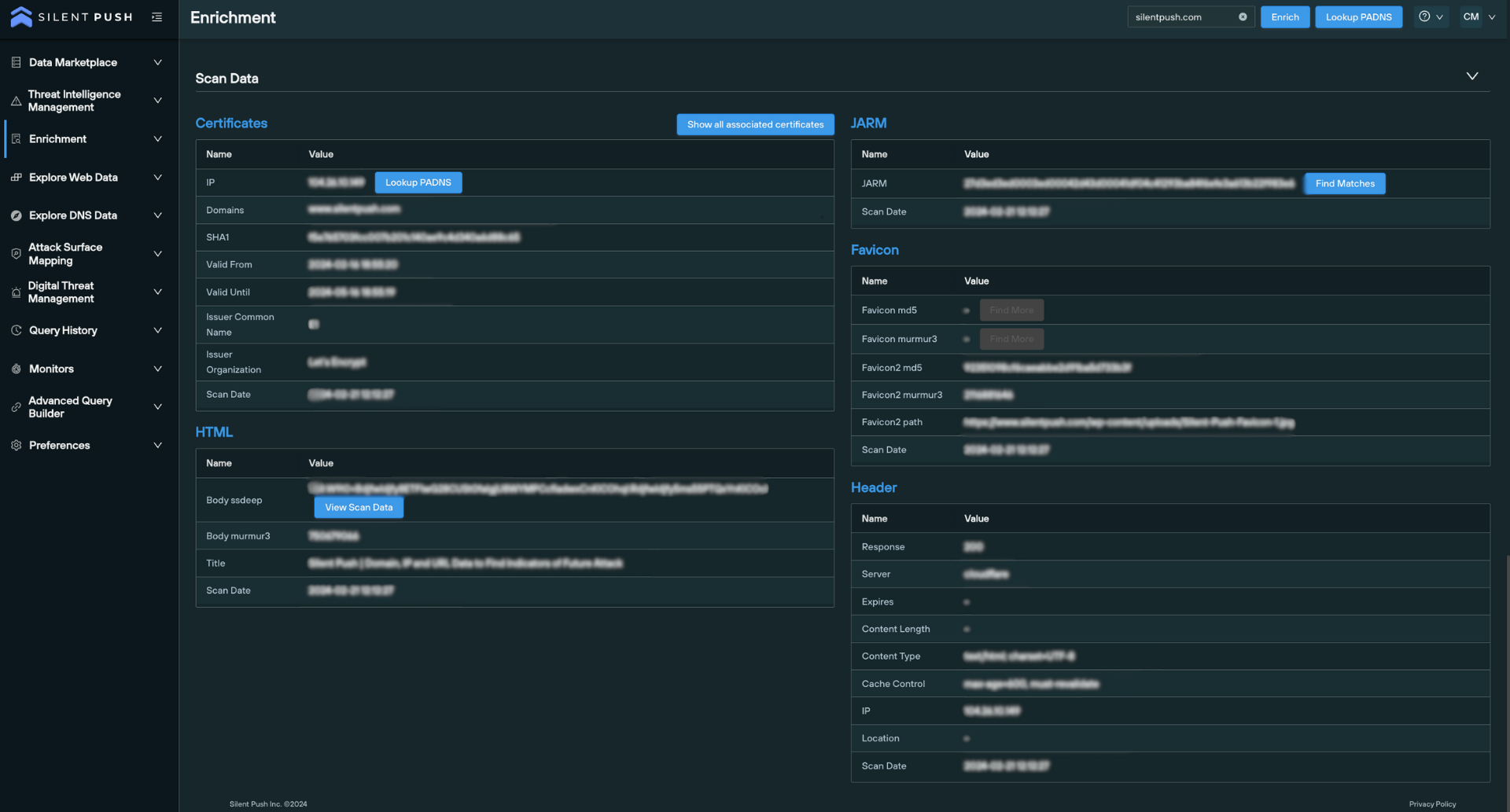
Scan data is an integral part of not only the Enrichment feature, but our entire first-party dataset. The Silent Push Web Scanner uses scan data to return query results across 100+ field names, including header values, body data and favicon hash values, and SSL data.
Data enrichment as operationalized intelligence
While there’s no doubt that data enrichment provides a number of benefits in and of itself, it’s just as important to ensure the enrichment process fits into your existing workflows.
You can use our API and custom query language to integrate any of the above enriched data types with your existing security stack, providing a near-infinite level of context for billions of observable domains and IPs across the IPv4 and IPv6 range.
Similar to Silent Push passive DNS lookups, you can pivot across, share, save and monitor enriched data, all from a single screen.
Register for Silent Push Community Edition
Data enrichment is available as part of Silent Push Community Edition – a free threat hunting and cyber defense tool used by security teams, threat analysts, and researchers that features 100+ data enrichment categories that you can use to track and monitor attacker activity across the global IPv4 and IPv6 space.
Click the button below to sign-up for a free account.