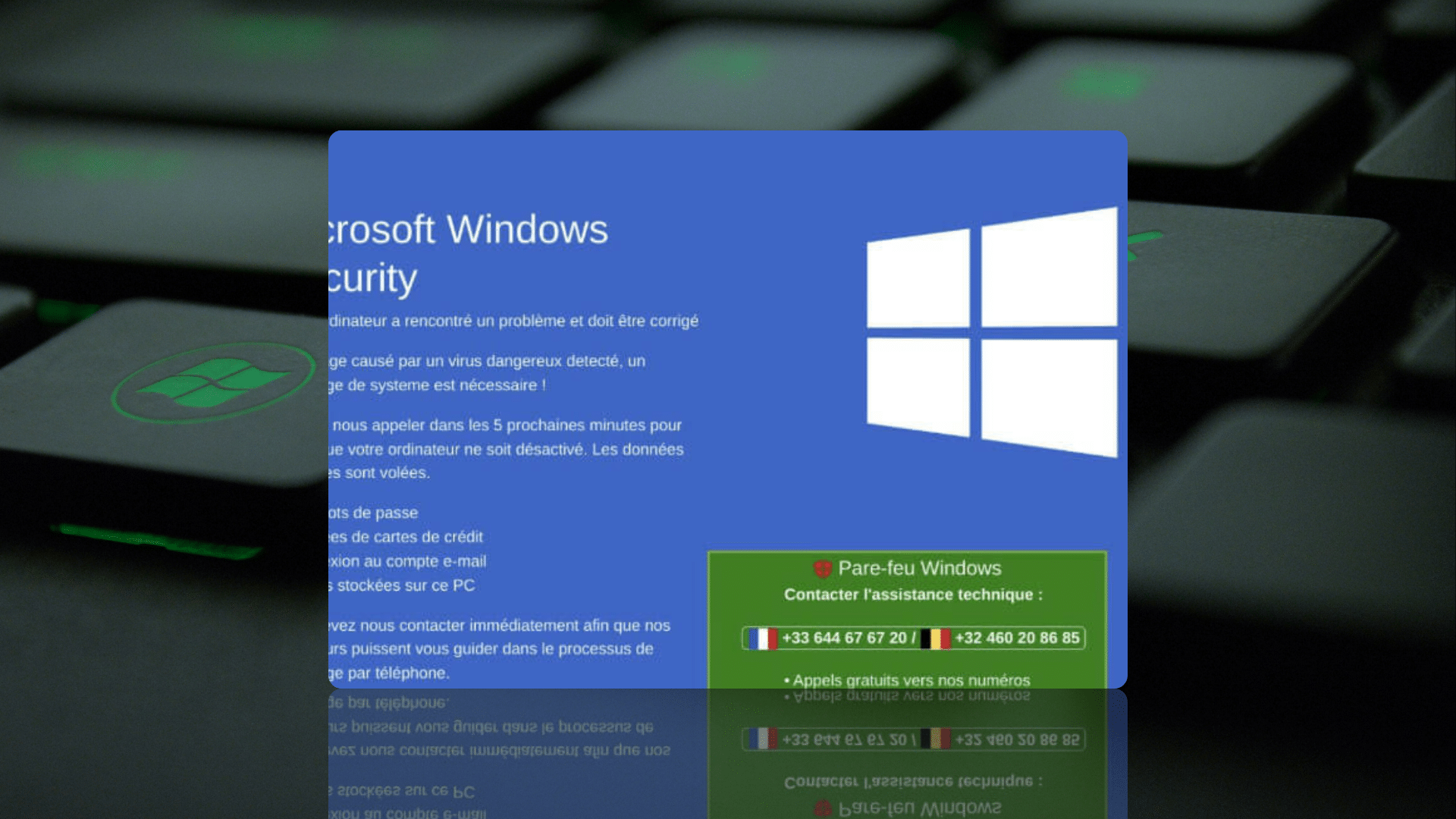
Background
Malwarebytes recently published a blog post uncovering a malvertisment campaign that used domain cloaking tactics to redirect users to fake Microsoft Windows Defender support pages, that act as a front for a tech support scam.
Our Threat Analysts have conducted further research and discovered that the majority of malicious domains included in the report’s IoCs were hosted on the same four IP addresses, featuring similar network IDs:
- 188.114.97[.]3
- 188.114.97[.]2
- 188.114.96[.]12
- 188.114.96[.]2
Using Silent Push to reveal additional IoCs
Through enriched scans of the threat actor’s public DNS information, we uncovered a large amount of previously unexplored data, along with IoCs relating to the original campaign – both on the same IP ranges and hosted on separate infrastructure.
Our research uncovered numerous additional attack vectors, not limited to the original tech support scam.
We found a variety of fake support page formats, malicious executables and fake browser extensions, suggesting a far broader threat landscape than that which was included in Malwarebyte’s original report.
Let’s take a look at what we found, and how we found it.
Navigating the attackers’ domain infrastructure
To target previously undocumented IoCs, we performed a customised scan of the above IPs, which flagged olalee[.]sbs as a malicious domain:
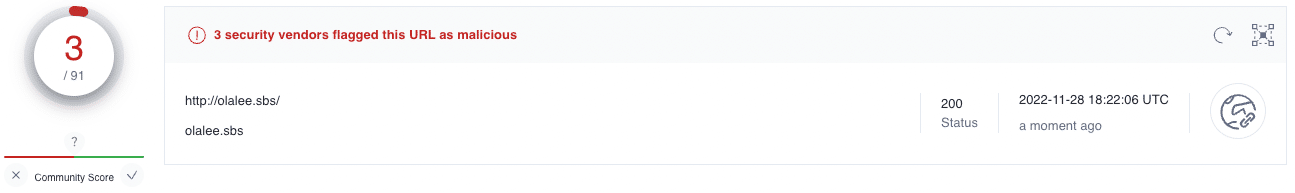
olalee[.]sbs redirects to 51.159.142[.]92, providing us with an entire subnet to investigate.
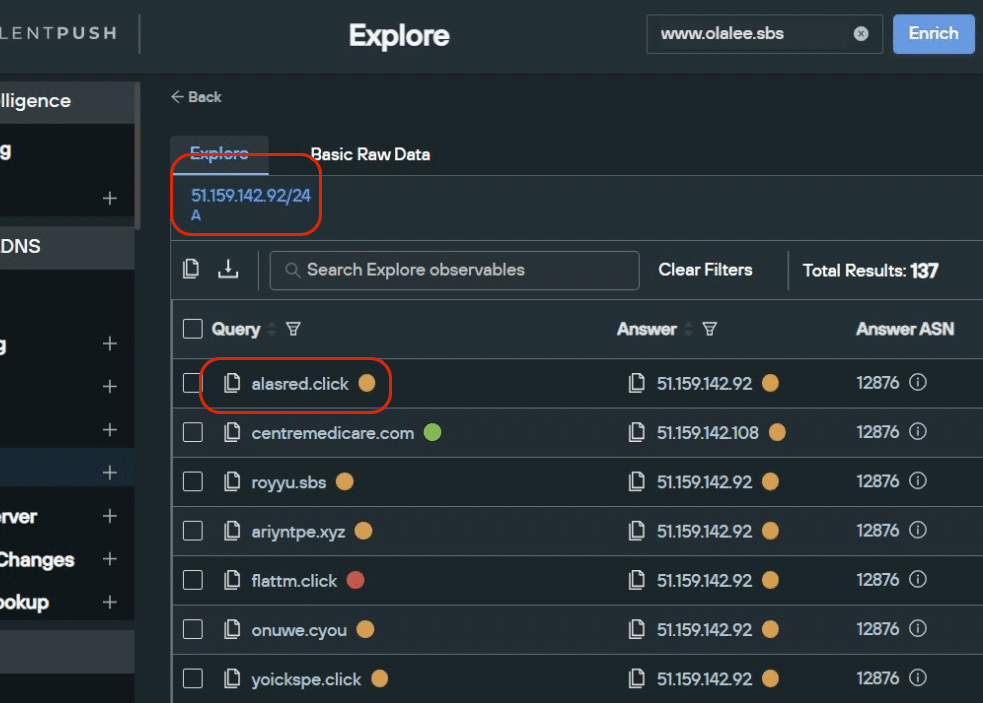
Exploring the threat landscape using Silent Push Reverse A record lookups
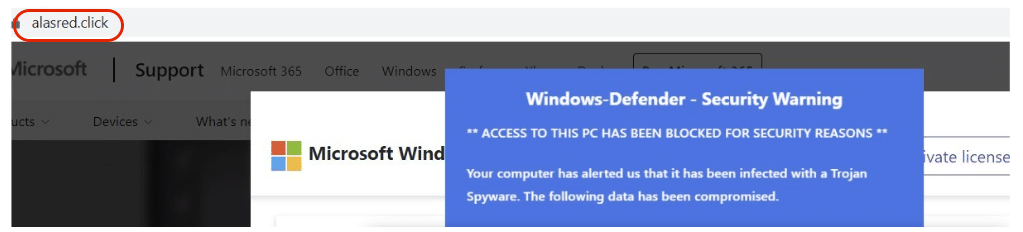
Using Silent Push’s Reverse A lookup tool (available on our free Community app), we discovered that all TLDs on the 51.159.142[.]92 subnet containing the characters .xyz, .sbs, .click, .cfd, and .cyou hosted malicious campaigns on their associated domain names (see below example):
We also discovered another group of TLDs – .ga, .gq and .tk – either currently residing on 188.114.9x.x (see above), 104.21.17.x and 172.67.176.x, or showing evidence of having used those particular groups of network IDs at some point in the past.
Legitimate hosting platforms affected
The attacker’s infrastructure isn’t limited to suspect hosting sites. We found evidence of fake tech support pages set up through well-known hosting providers such as Cloudflare (originalcenter.pages[.]dev), 000WebHost (unnourished-region.000webhostapp[.]com) and Netlify (microsoft-windows[.]netlify.app):

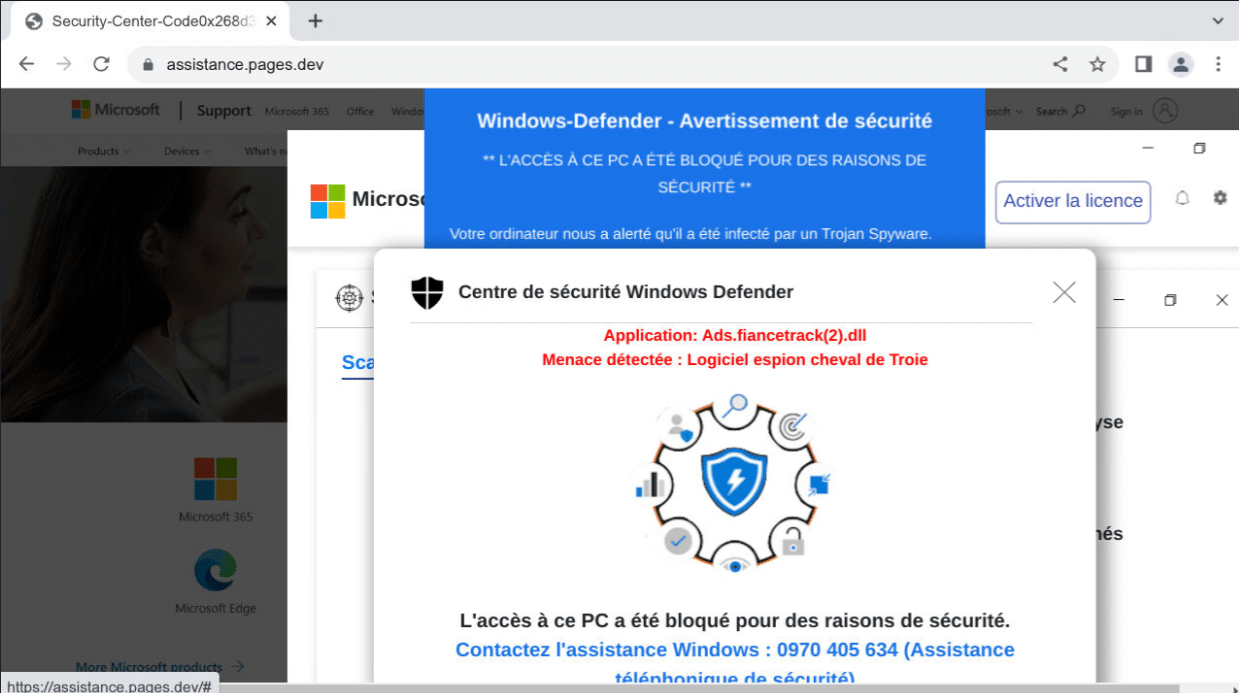
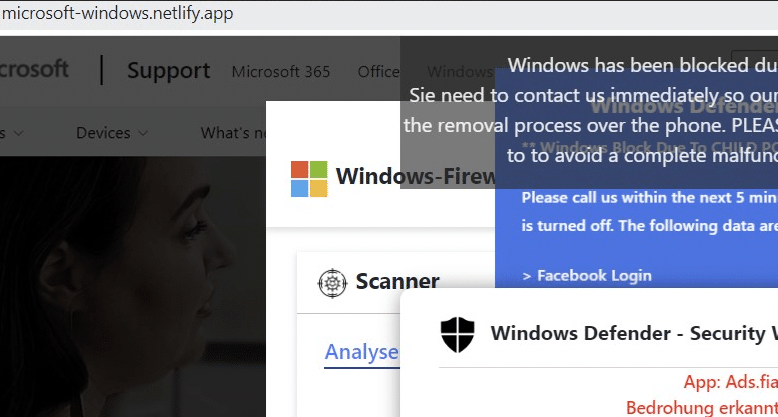
Analysing the malicious installers
As we navigated through the threat actors’ public DNS infrastructure, we encountered domains that played host to a variety of malicious activities, including fake executable installers, fake browsers and hoax Chrome extensions, with many of the scam domains being passed off as safe by security vendors (see below).
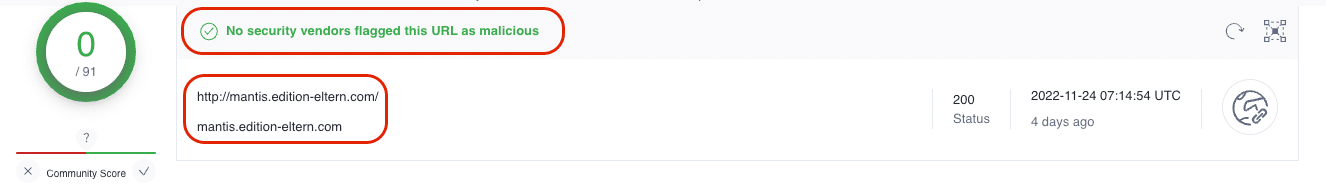
Example installer domain – mantis.edition-eltern[.]com
During our research, we came across mantis.edition-eltern[.]com, masquerading as an Asian discussion forum with branding similar to the now-defunct Yahoo Answers, which shut down in May 2021:
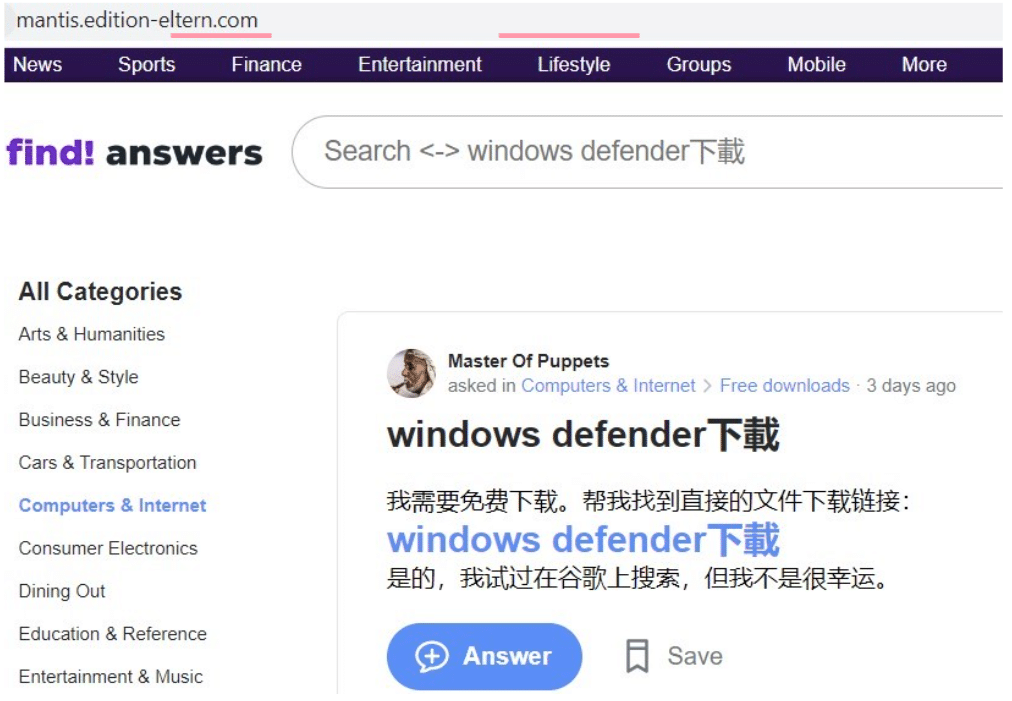
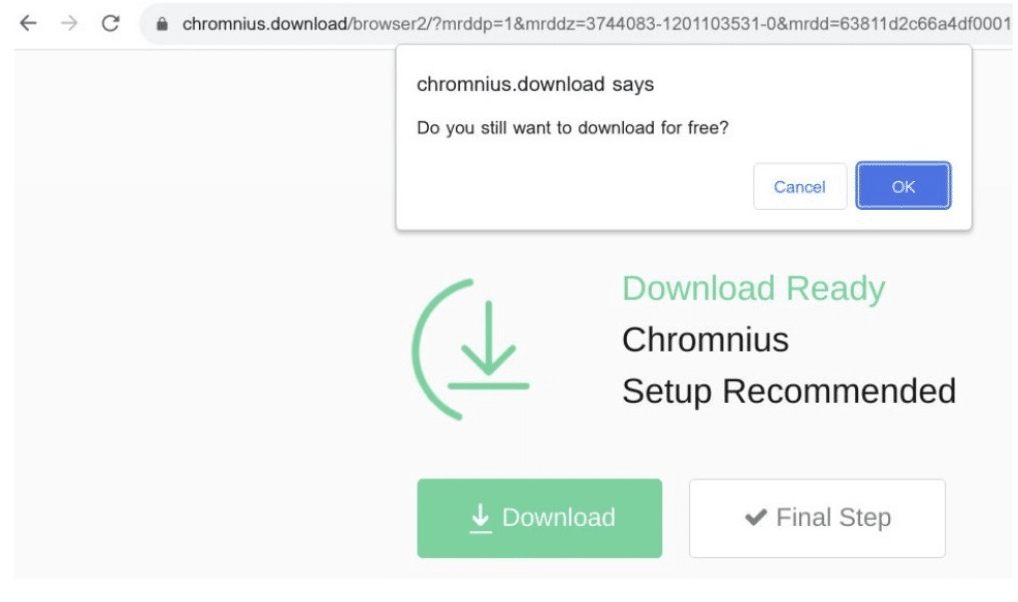
Following the ‘Windows Defender’ link, users are redirected to the below site, prompting a download of what appears to be a Windows Defender installer:

Once clicked, the ‘Download Now’ button redirects again to a malicious Chrome extension:
Querying mantis.edition-eltern[.]com across 91 security vendors returned zero flags:
The Chrome extension fared slightly worse, but only just, appearing in a solitary vendor’s list of malicious apps:

Picking apart the installer’s functions
After conducting further analysis of ChromSetup.exe, we discovered several malicious characteristics:
- An invalid signer

- Forcefully adding itself as a Chrome extension through registry changes:
REG ADD "HKLM\SOFTWARE\Policies\Google\Chrome\ExtensionInstallAllowlist" /v "1" /t REG_SZ /d pejhfhcoekcajgokallhmklcjkkeemgj /f
- Initiating a Chrome instance after the extension has been installed, without a corresponding startup window:
"C:\Program Files\Google\Chrome\Application\chrome.exe" --profile-directory="Default" --load-extension="C:\apps-helper" --no-startup-window
- Using Powershell commands to create its own text file, in a local directory, and adding the file to ‘Powershell ExecutionPolicy Bypass’, allowing the extension to ignore a built-in safety feature that controls the conditions under which PowerShell loads configuration files and runs scripts.
Powershell.exe -ExecutionPolicy Bypass -File C:\Users\Admin\AppData\Local\Temp\is-60CAT.tmp\\chrome.ps1
Other installer-based attack vectors
Some other installers we encountered masqueraded as adblockers, streaming applications and even standalone web browsers:
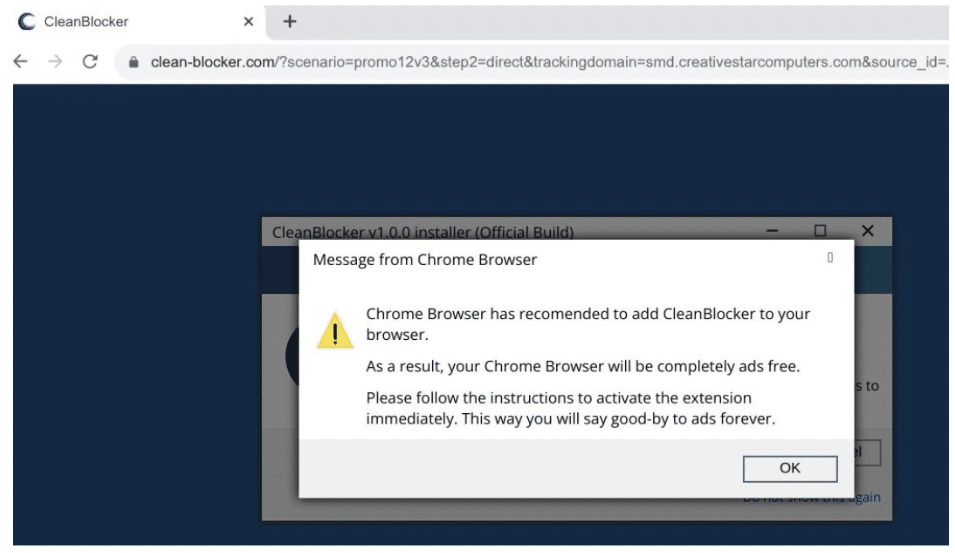
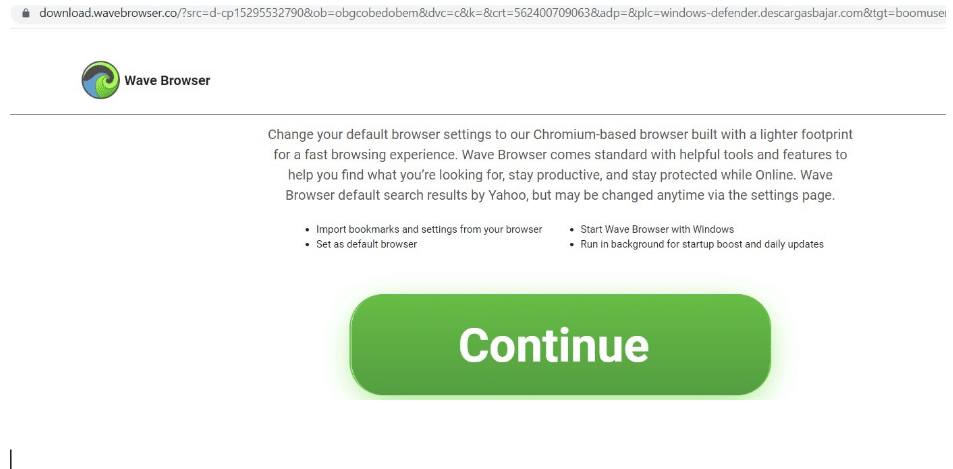
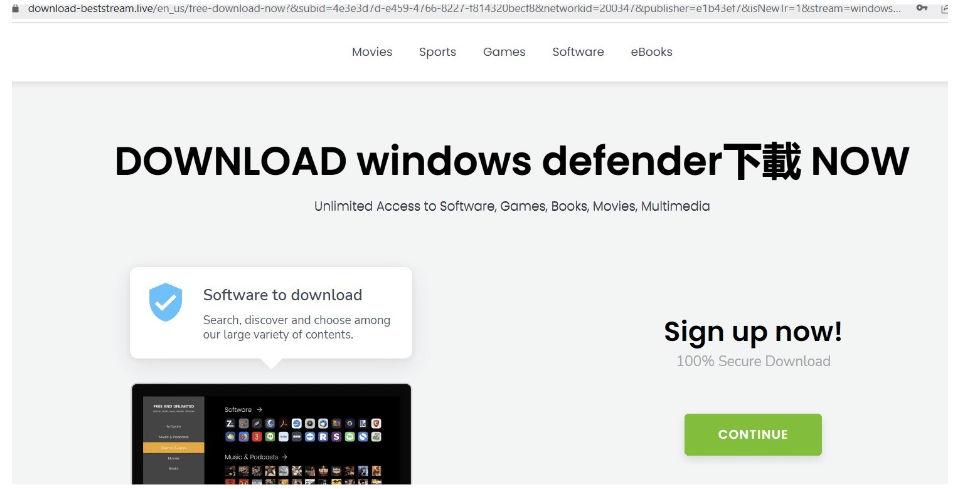
The attackers haven’t limited themselves to malicious software downloads.
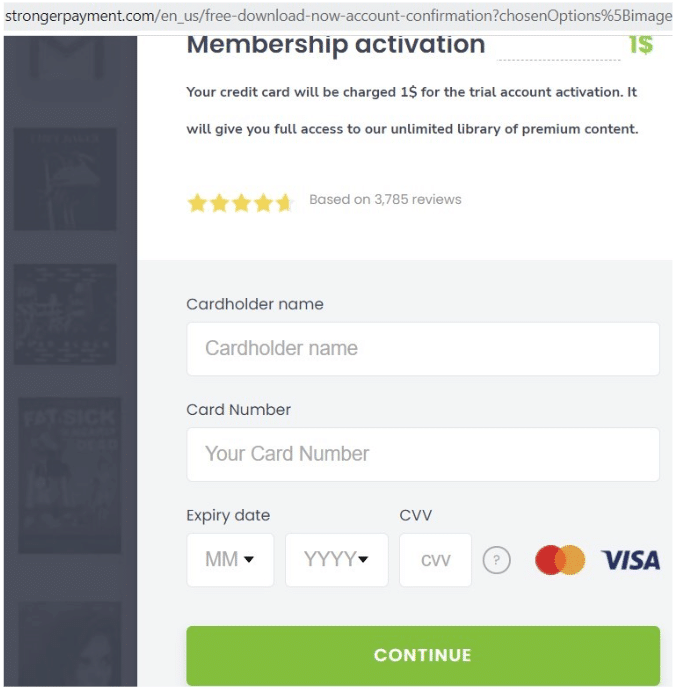
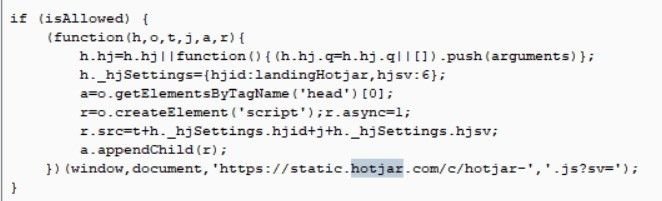
There’s also evidence of hoax payment portals (redirected from the above streaming site) that initiate browser-hijacking sessions, and embed adware such as static.hotjar:
Uncovering other fake support campaigns
Using enriched data harvested from our daily scans of millions of domains across the entire IPv4 range, we performed further granular searches that identified numerous other fake support pages.
These pages differ visually from the original Windows Defender campaign (or attempt to spoof another vendor entirely) but feature the same angle of attack – a hoax tech support line.
Here’s an example featuring a different language, and an EU telephone number:

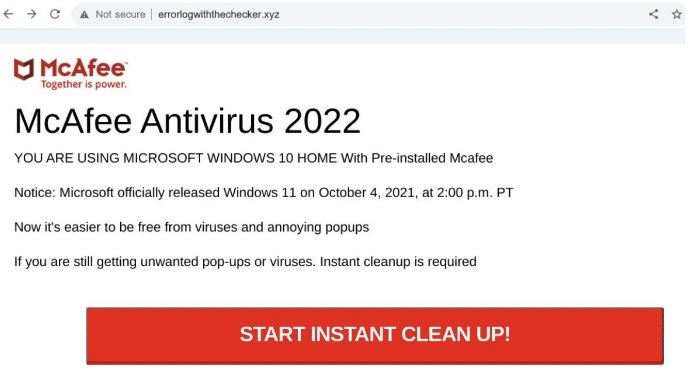
Other examples show the attackers targeting McAfee, instead of Microsoft:
Silent Push custom threat feeds
We’ve passed our research on to all the affected organisations – including the legitimate hosting providers that are being used to host malicious content.
We’re currently in the process of creating a custom feed that lists all associated malicious infrastructure, that paid subscribers can integrate with their existing security stack, ensuring early detection and enabling proactive monitoring of the attack surface with data that isn’t seen in other global feeds.
Follow us on LinkedIn and Twitter for weekly threat intelligence updates and research.
To download our free Community app – the largest free library of SaaS-based threat defence tools available anywhere in the world, including some of the queries we’ve mentioned in this report – visit Silent Push Community App — Silent Push Threat Intelligence
Indicators of Compromise
Websites and domains
- lovetechie[.]com
- mail.supporttechwin[.]net/
- microsoft-windows[.]netlify.app
- microsoft-windows-defender-offline.descargasbajar[.]com
- mantis.edition-eltern[.]com
- windows-defender-hub-1.downloadsgeeks[.]com
- windows-defender-hub-1.down4you[.]software
- assistance.pages[.]dev
- unnourished-region.000webhostapp[.]com
- lugyt2[.]tk
- hellboylucy509.000webhostapp[.]com
- originalcenter.pages[.]dev
- falernian-plane.000webhostapp[.]com
- royyu[.]SBS
- lugyt2[.]tk
- alasred[.]click
- fasertshop[.]online
- futuresystemerrors.thevalueformoneywithsolar[.]com
- hellboylucy509.000webhostapp[.]com
- supporttech-win[.]com
- supportfr.pages[.]dev
- gakey.axoneday[.]xyz
- www.olalee[.]sbs
- microsoft-windows.netlify[.]app
- thanforestacion[.]xyz
- hollowpe[.]xyz
- shoughpe[.]xyz
- parfaype[.]xyz
- pishcds[.]xyz
- goalsamsunet[.]xyz
- ariyntpe[.]xyz
- oyezsre[.]cyou
- asafry[.]cyou
- guyle[.]cyou
- eighred[.]xyz
- onuwe[.]cyou
- tyorr[.]cyou
- enoighpe[.]xyz
- kandoura[.]xyz
- opakia[.]xyz
- jogay[.]SBS
- fronttm[.]SBS
- playtm[.]sbs
- queentm[.]sbs
- yeartm[.]sbs
- leoorr[.]sbs
- nedlee[.]sbs
- quothape[.]click
- flattm[.]click
- uhsdl[.]click
- yoickspe[.]click
- pridetm[.]click
- shirttm[.]click
- edlin[.]click
- hartowpe[.]click
- jaykey[.]click
- tiletm[.]click
- alasred[.]click
- hurrahpe[.]click
- begonepe[.]click
- shapetm[.]click
- bofry[.]click
- oraltm[.]click
- misttm[.]click
- royyu[.]sbs
- valgay[.]sbs
- filltm[.]sbs
- olalee[.]sbs
- leakim[.]click
- ringtm[.]click
- alray[.]click
- aunttm[.]click
- evamay[.]click
- papertm[.]click
- halli[.]click
- tylee[.]sbs
- eliray[.]sbs
- bokim[.]sbs
- pamho[.]click
- nedpee[.]sbs
- sallin[.]cfd
- wmday[.]cfd
- guylam[.]cfd
- wavetm[.]cfd
- kneetm[.]cfd
- sailtm[.]cfd
- asafox[.]cfd
- cordtm[.]cfd
- ridertm[.]cfd
- leegay[.]cfd
- buyertm[.]cfd
- iuyw[.]cfd
- egadsre[.]cfd
- eventtm[.]cfd
- goaltm[.]cfd
- dutytm[.]cfd
- louwu[.]cfd
- leoorr[.]cfd
- angertm[.]cfd
- joliu[.]cfd
- loufox[.]cfd
- alorr[.]cfd
- errorlogwiththechecker[.]xyz/
- rodmay[.]sbs
- taawatchtuttlect[.]tk
- compcadisp[.]ga
- exarber[.]gq
- taoriohaybras[.]tk
- cepphonand[.]gq
- tranmalirilinkwor[.]tk
- arbalsafedager[.]tk
- nestibufecomsoft[.]cf
- preseptic[.]tk
- mispnonpstarcupimcomp[.]tk